- Windows Server
- 22 December 2023 at 11:41 UTC
-

- 1/5
When you want to deploy certificates in a multinational, it's very interesting to create a root CA and several secondary CAs (one per country or geographical location).
Thus, this makes it possible to distribute the load on different certification authorities and above all to limit the problems in the event of compromise of the private key of one of your secondary (subordinate) certification authorities.
- Prerequisites
- Install standalone root CA (at corporate headquarters)
- Install enterprise secondary CAs (at each physical site)
- Configure standalone root CA
- Storing standalone root CA information in Active Directory
- Change autonomous root CA CDP and AIA publishing locations
- Publish your standalone root CA information to your Active Directory
- Configure enterprise sub-certificates (at each physical site)
- Submit requests from your subordinate CAs to your root CA
- Export certificates from your subordinate CAs
- Install enterprise sub-CA certificates
- Enterprise sub-CA information in Active Directory
- Force replication of Active Directory data between different sites
- Certification authorities recognized by your client PCs
- Use by default the authority present on your Active Directory site
- Request a certificate from the mmc console
1. Prerequisites
For this tutorial, we will use an already configured multi-site Active Directory infrastructure.
As explained in the tutorial mentioned above, we therefore have 2 physical sites (a 1st site in Brussels and a 2nd in Paris) with 2 domain controllers per physical site.
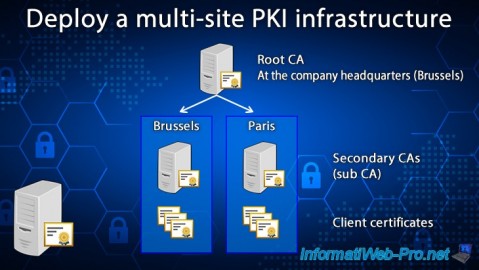
When you deploy a PKI infrastructure in a multinational, you can only have one root CA.
You will therefore deploy it at the headquarters of your company.
Also, for security reasons, you should use a standalone root CA that will need to stay offline and then shut down most of the time. This makes it possible to best secure his private key.
To start, we will deploy a standalone root CA on a server named "brux-root-ca" which will be a member of a workgroup. This autonomous root certification authority will therefore be deployed at your company's headquarters (in our case, in Brussels).
Then, at each physical site, you will deploy an enterprise subordinate CA, whose certificate will be signed by your standalone root CA.
Note : to better understand how standalone root CAs and enterprise sub CAs work, we recommend reading our "WS 2016 - AD CS - Install and configure a root CA and a secondary CA" tutorial first.
Indeed, once you have understood the concepts explained in the tutorial mentioned above, you will be able to deploy these certification authorities more easily in a multinational.
2. Install standalone root CA (at corporate headquarters)
To get started, install your standalone root CA at your company headquarters.
Warning : per Microsoft's recommendations, you will need to install the standalone root CA on a server that will remain offline.
This means that it must remain in a workgroup and NOT be a member of an Active Directory domain.
Indeed, in the case of joining an Active Directory domain, the secure channel between your server and your domain controller will necessarily be broken one day, since the server will have remained offline for too long.
Hence the fact that you only see the NETBIOS name "brux-root-ca" in our case for this server.
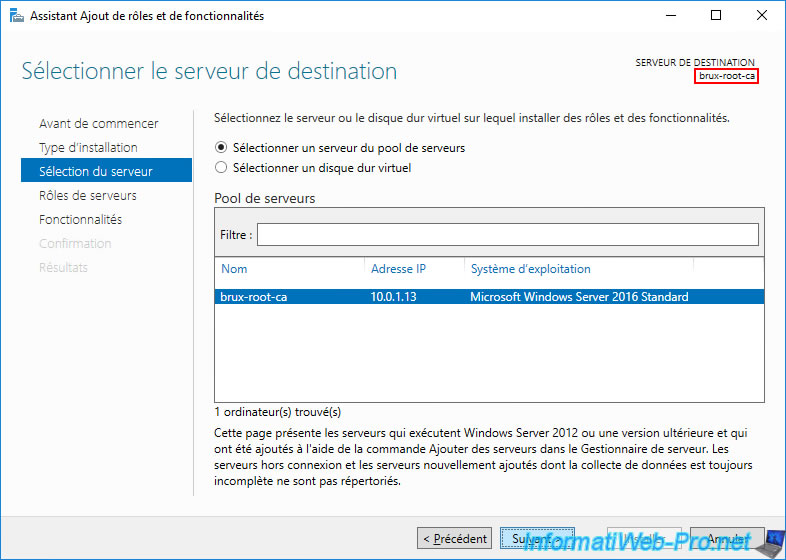
Install Active Directory Certificate Services.
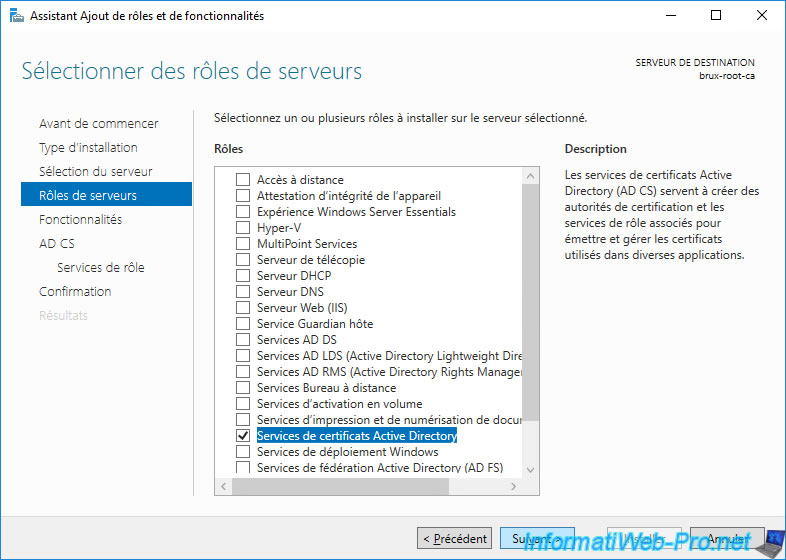
Install only the "Certification Authority" role service.
Note : since your standalone root CA will remain offline, the other role services (which are accessible through the network) are unnecessary.
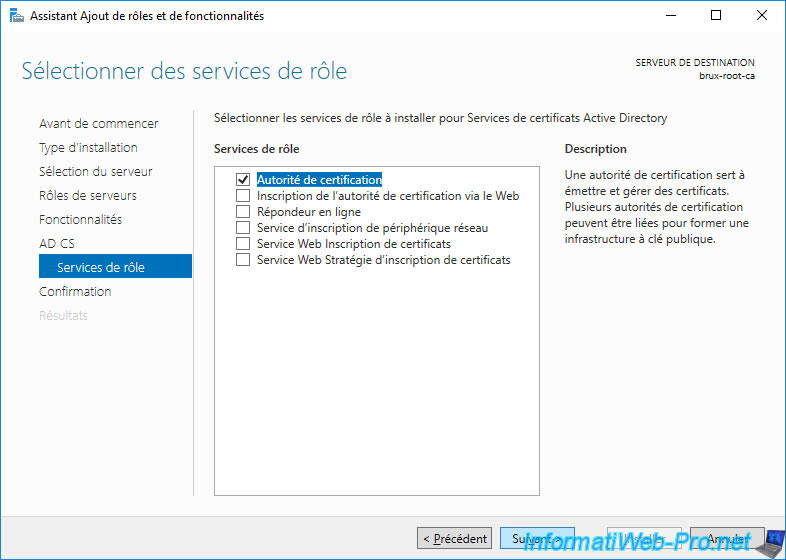
Active Directory Certificate Services has been installed.
Leave this window open and don't click on the displayed link right away.
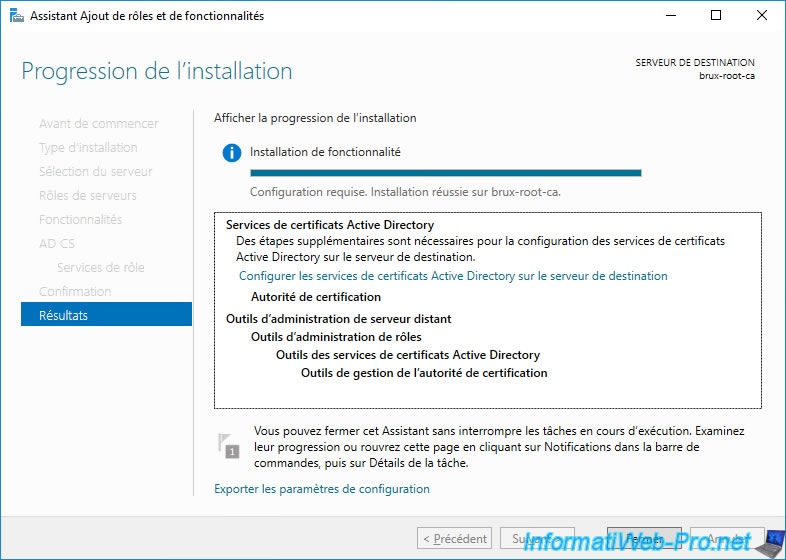
3. Install enterprise secondary CAs (at each physical site)
On each physical site, install Active Directory Certificate Services and select at least the "Certification Authority" role service.
Important : since these are enterprise sub-CAs, our servers are already linked to our Active Directory domain.
We are installing a 1st secondary enterprise certification authority in Brussels on our "brux-sub-ca.informatiweb.lan" server.
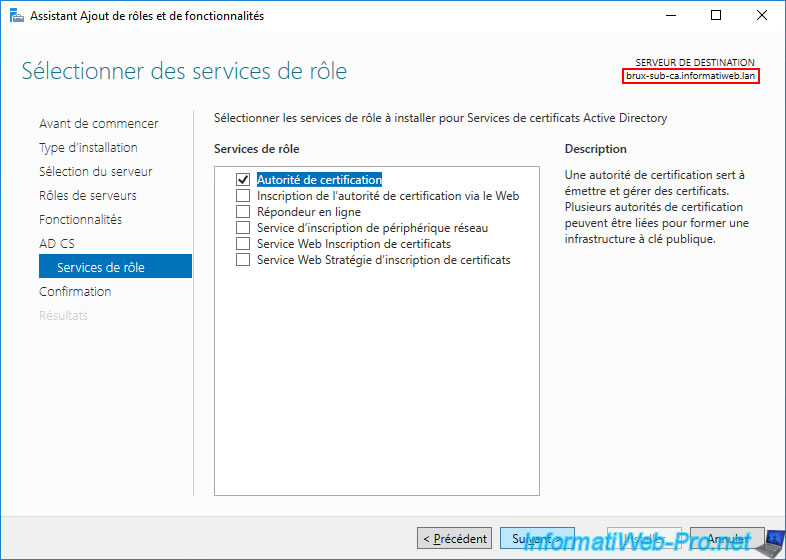
Then, we install a 2nd secondary enterprise certification authority in Paris on our "paris-sub-ca.informatiweb.lan" server.
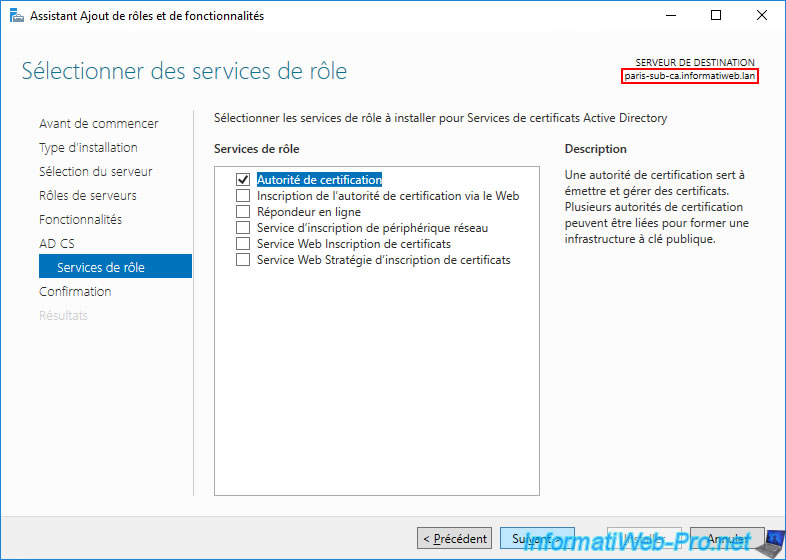
Active Directory Certificate Services have been installed on our 2 servers.
Again, leave this window open and don't click on the displayed link right away.
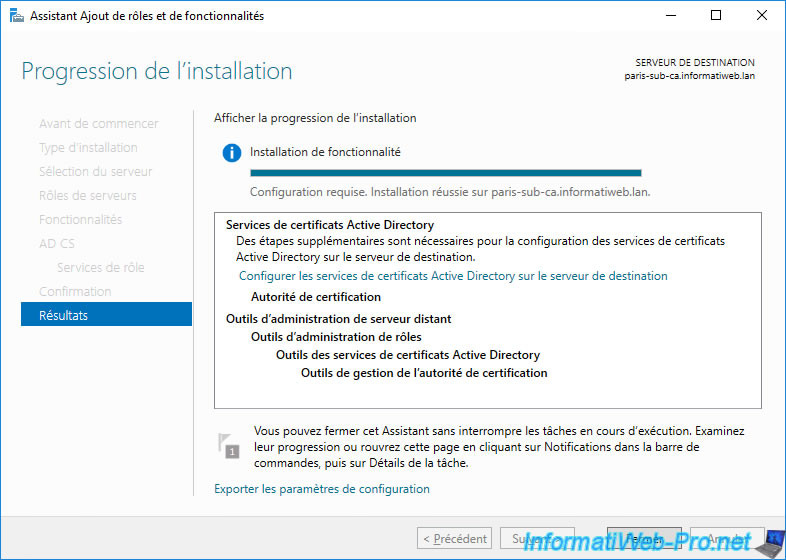
4. Configure standalone root CA
On your future standalone root CA, click the "Configure Active Directory Certificate Services ..." link displayed by the Add Roles and Features Wizard.
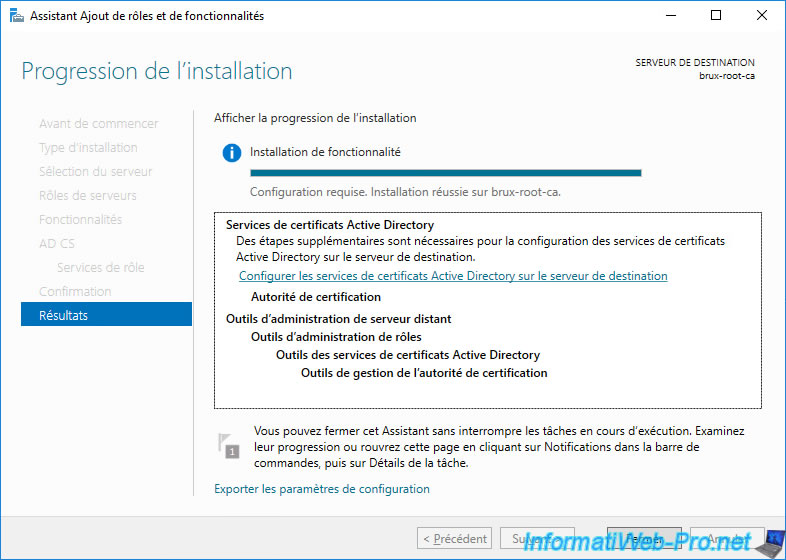
The "AD CS Configuration" wizard appears.
Of course, the configuration will be done with the local Administrator account of this server.
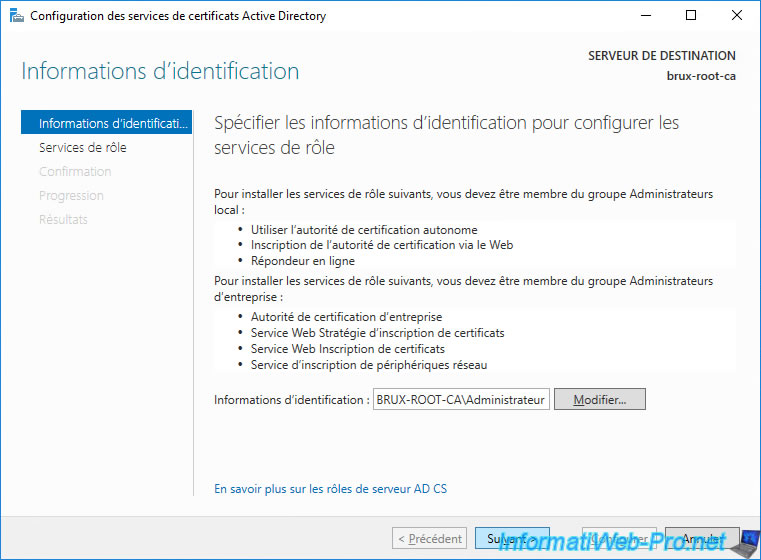
Check the "Certification Authority" box and click Next.
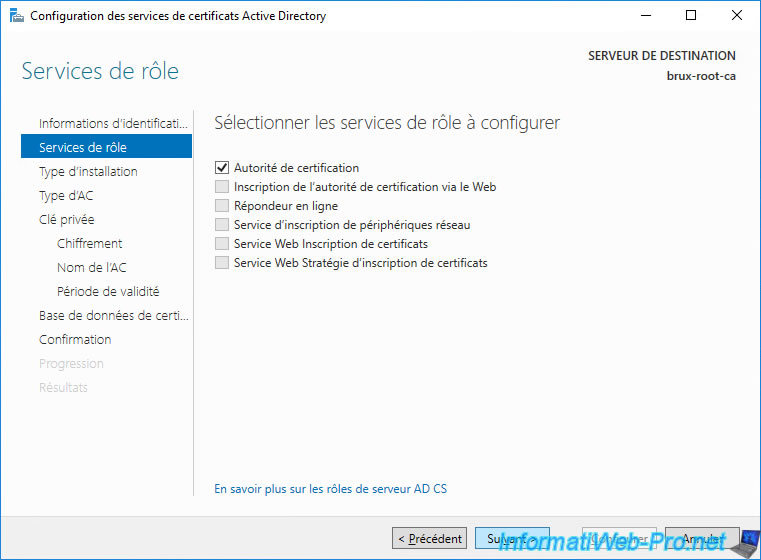
Select "Standalone CA".
Note : the "Enterprise CA" option is grayed out because your server is in a workgroup and not in an Active Directory domain.
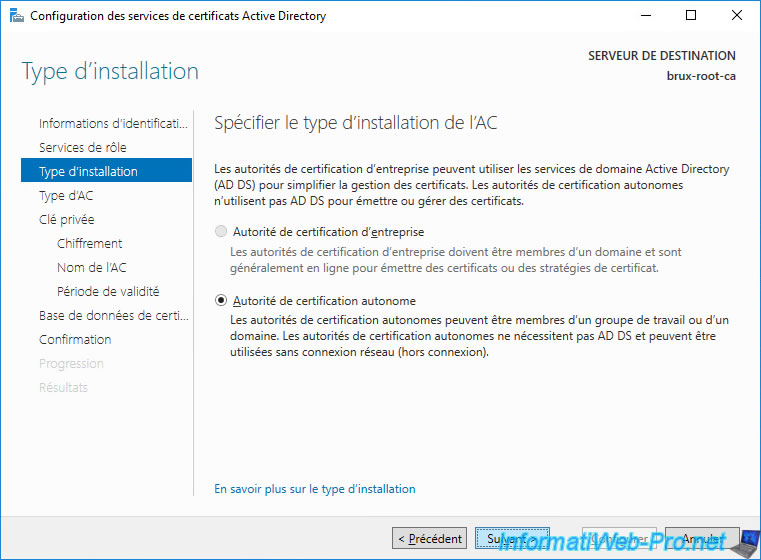
Select "Root CA".
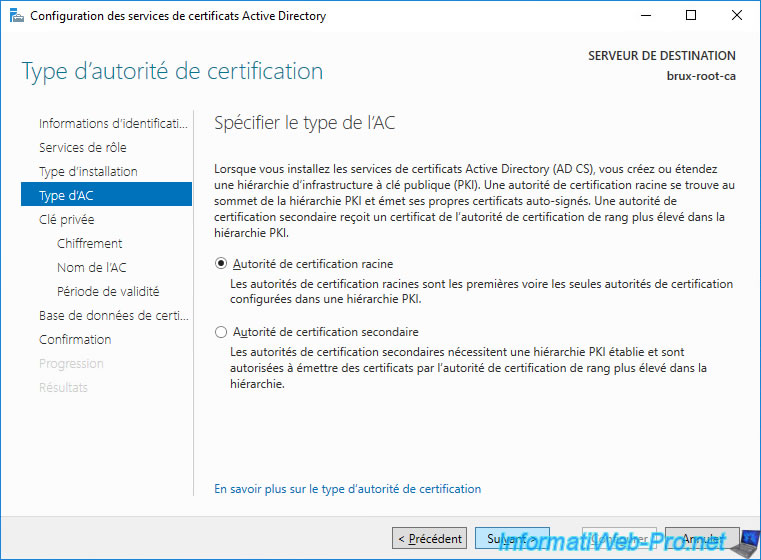
Select "Create a new private key" since this is a new CA.
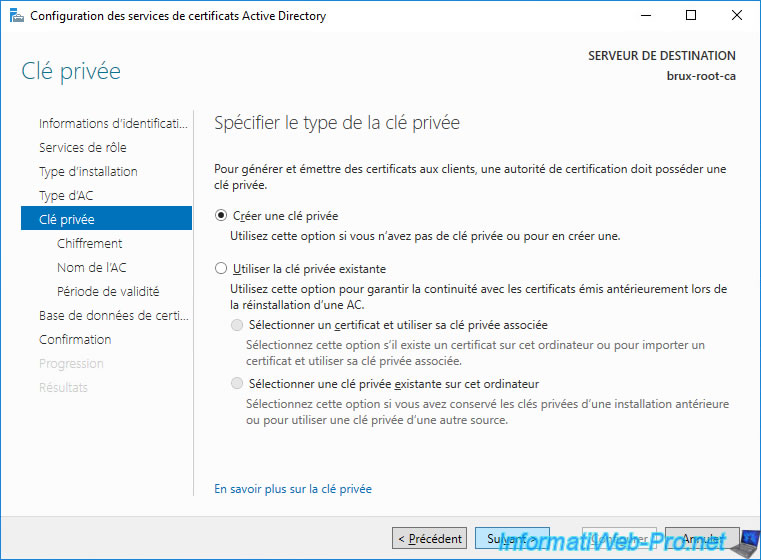
Leave the default encryption options.
For more information about these encryption options, refer to our "WS 2016 - AD CS - What is a CA and install an enterprise CA" tutorial.
Warning : do NOT use SHA1, as this algorithm is currently detected as insecure.
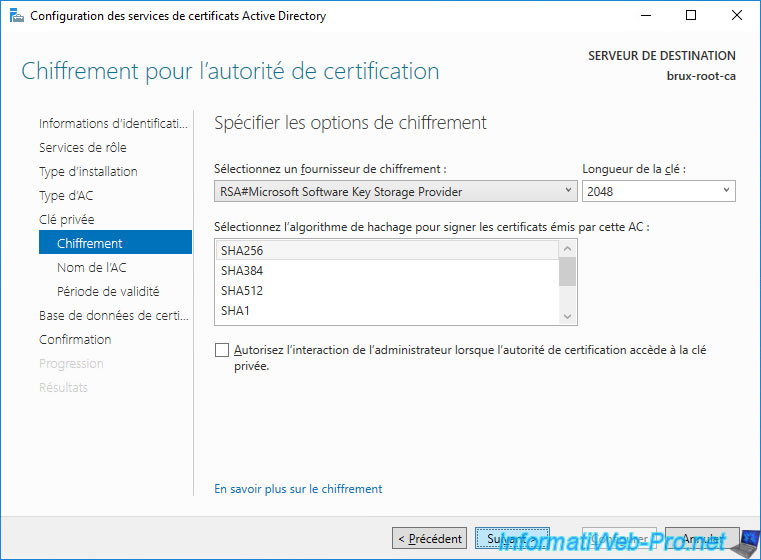
Provide a name for your root CA.
In our case, we named it "InformatiWeb Root CA (Brux)" since it is our root certification authority and it's located at our company headquarters (in Brussels).
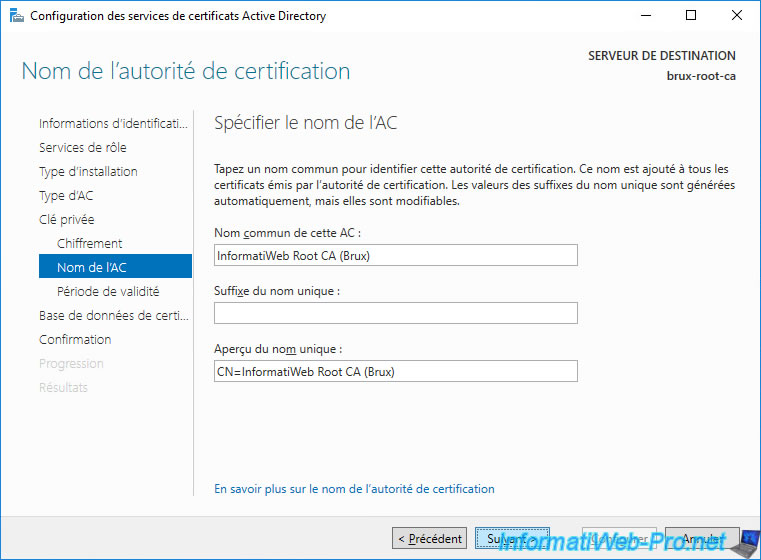
Specify a sufficient validity period for your root CA, as certificates issued by this CA will not be valid beyond this validity period.
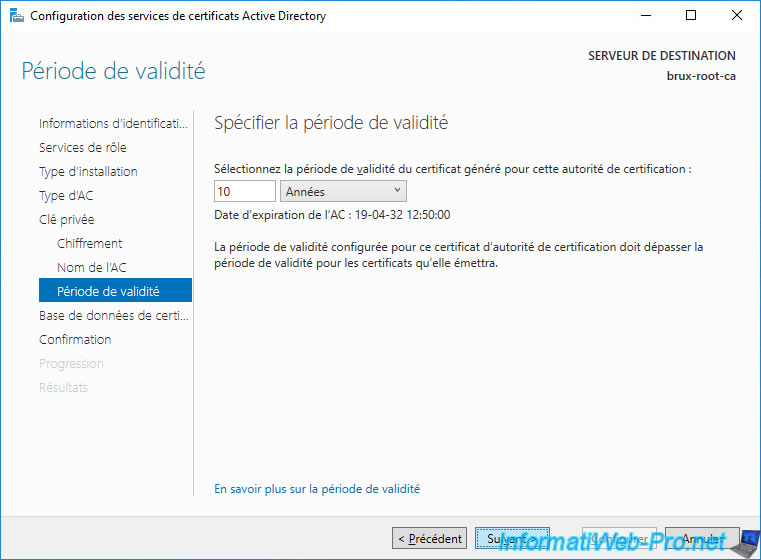
Leave the default database locations.
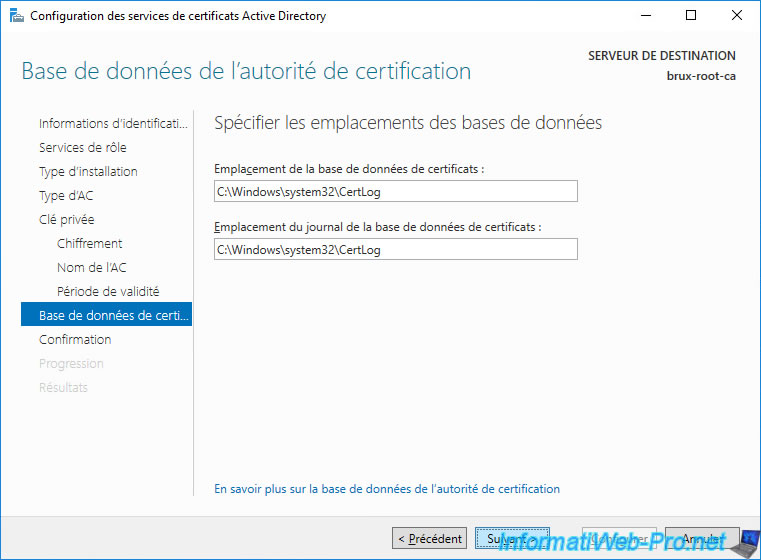
A summary of your standalone root CA configuration appears.
Click Configure.
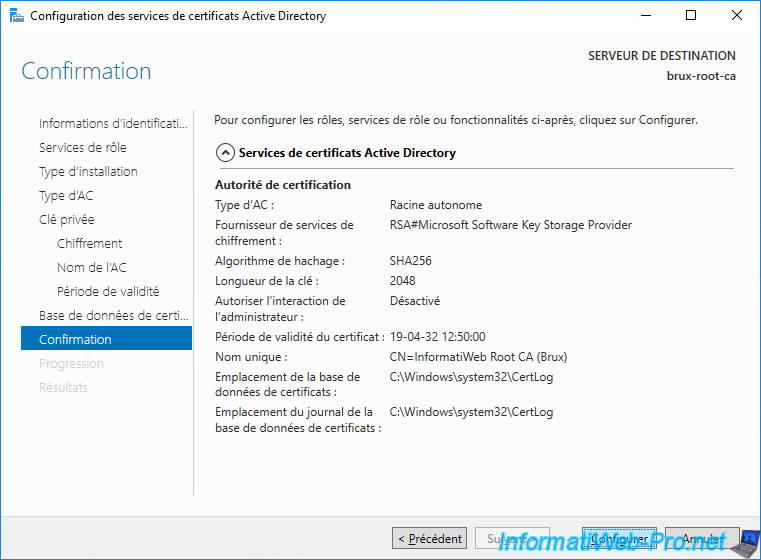
Once the configuration is complete, the "Configuration succeeded" status will appear.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

You must be logged in to post a comment