- Articles
- 26 January 2024 at 09:57 UTC
-

- 1/3
SafeNet Authentication Client (SAC) is a free software developed by Thales Group that allows you to manage your smart cards.
Note that this program is only necessary to manage your smart cards : modify its PIN codes, manually manage the certificates it contains, ...
In most cases, including enrolling certificates on your smart card from the "mmc" console, you will only need the "SafeNet Minidriver".
- Where to download SafeNet Authentication Client (SAC) ?
- Install SafeNet Authentication Client (SAC)
- SafeNet Authentication Client (SAC) features
- View token / smart card information (View Token Info)
- Advanced view
- User certificates
- Manually import a certificate to your token/smartcard from your computer/server's certificate store
- Manually import a certificate on your token / smart card from a file (.pfx, .p12 or .cer)
- Manually import a certification authority (CA) certificate to your token/smartcard
- Delete a certificate stored on your token / smart card
- Settings regarding the different PIN codes
- About SafeNet Authentication Client (SAC)
- View SafeNet Authentication Client Help
- Go to the official Thales website
1. Where to download SafeNet Authentication Client (SAC) ?
When you order smart cards manufactured by Thales Group, you can obtain the SafeNet Authentication Client (SAC) program free of charge by contacting the intermediary from whom you ordered them.
In our case, we ordered our smart cards from Cardelya.fr.
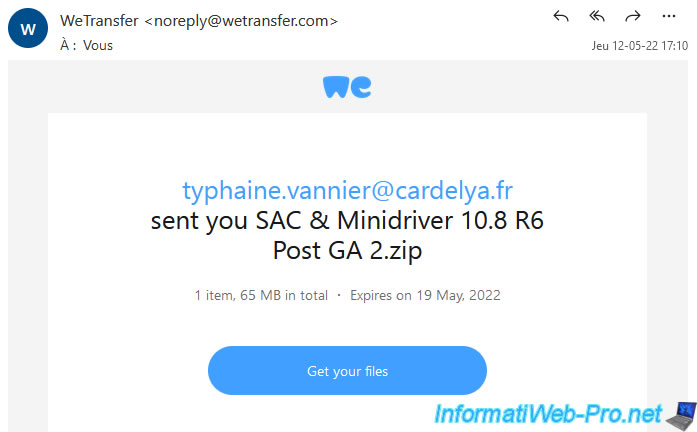
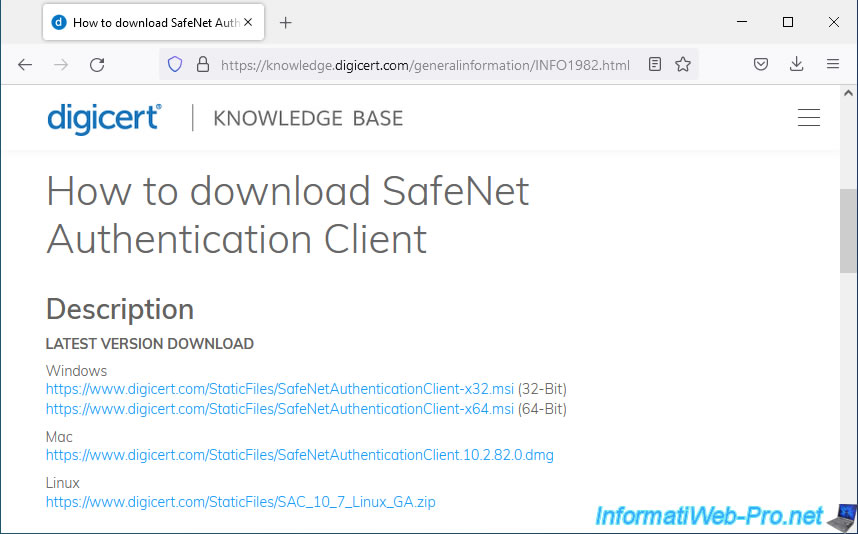
If necessary, to avoid recontacting your intermediary each time SafeNet Authentication Client (SAC) is updated, you can easily download it from the "How to download SafeNet Authentication Client" page of the official site of digicert (a certification authority recognized by default by all computers / servers on Windows / Windows Server).
2. Install SafeNet Authentication Client (SAC)
Launch the SafeNet Authentication Client (SAC) installation file : SafeNetAuthenticationClient-x64-10.8-R6.msi.
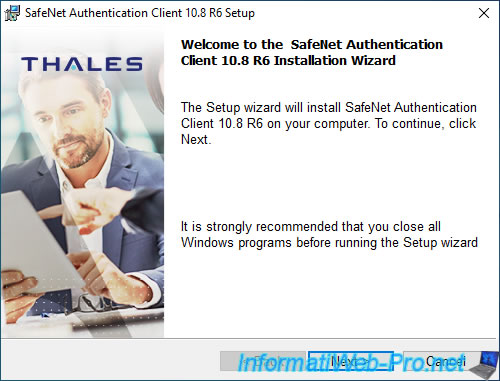
The "SafeNet Authentication Client 10.8 R6 Setup" installer appears.
Click Next.
Preferably, select the "English" language to be able to easily obtain help if necessary thanks to the PDF in English provided (once the program is installed).
SafeNet Authentication Client (SAC) installs like any other program.
As you can see, the installer offers you 2 interfaces.
Select the appropriate one for your case.
Info : for native integration on Windows 10 and Windows Server 2016, you will use "Microsoft Minidriver".
Click Install.
Wait while the SafeNet Authentication Client (SAC) installs.
SafeNet Authentication Client (SAC) is installed.
Click Finish.
In the taskbar, you will see a small icon (representing a medal) appear next to the time.
Note that this is greyed out when your smart card reader is not plugged in or when no smart card is inserted in it.
![]()
If you right-click on this icon, you will see several options appear, including the "Tools" option.
This option opens the "SafeNet Authentication Client (SAC)" program.
If the "Tools" option is not available in your case, you have only installed the driver (SafeNet Minidriver) and not this "SafeNet Authentication Client (SAC)" program.
Indeed, when you install the "SafeNet Minidriver" driver, the same icon appears, but you don't have access to the program allowing you to manage your smart card.
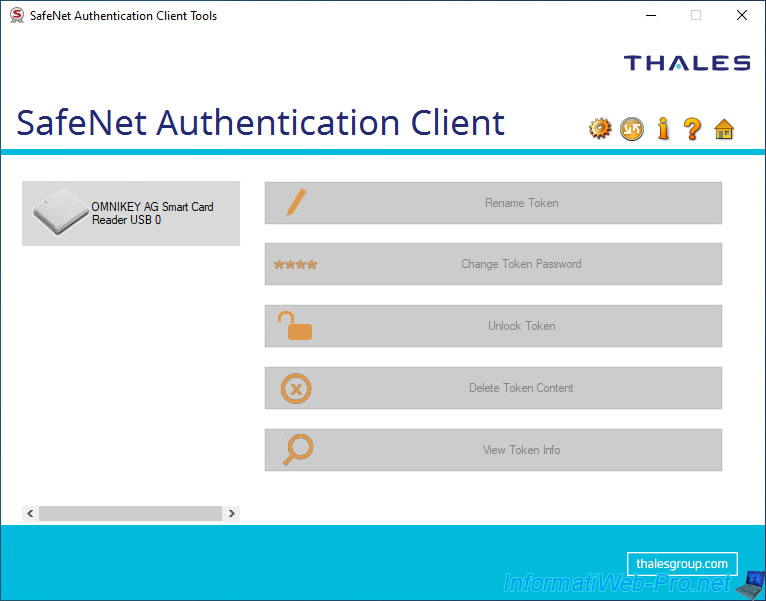
If you click on "Tools", you will see the "SafeNet Authentication Client Tools" window appear.
As you can see, at the moment SafeNet Authentication Client (SAC) detects our "HID OMNIKEY 3121" smart card reader as "OMNIKEY AG Smart Card Reader USB 0".
When no smart card is inserted in your smart card reader, all options to the right are grayed out.
If you click on "About" from the icon visible in the taskbar, you can easily know the version of SafeNet Authentication Client (SAC).
You will also have a link to the official Thales website and a button to check if the SafeNet Authentication Client (SAC) binaries have not been modified by malware.
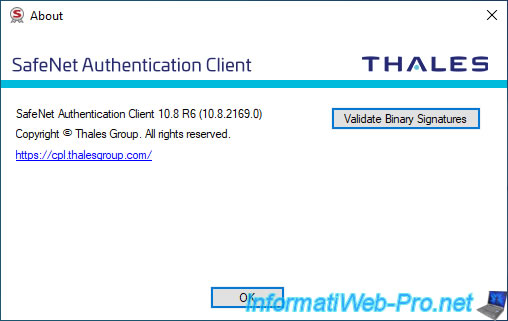
If you click on the "Validate Binary Signatures" button, the "No binaries are at risk" message should appear.
3. SafeNet Authentication Client (SAC) features
Once you have inserted a smart card (manufactured by Thales Group) into your smart card reader, 3 additional options will appear in the context menu of the icon present in the taskbar.
- Change Token Password : allows you to change the password (user PIN code) of the token / smart card.
For SafeNet eTokens, the default password is : 1234567890.
For IDPrime smart cards, the default password is : 0000. - Unlock Token : allows you to unlock a SafeNet eToken or an IDPrime smart card IF an administrator password (Admin PIN) was defined when it was initialized.
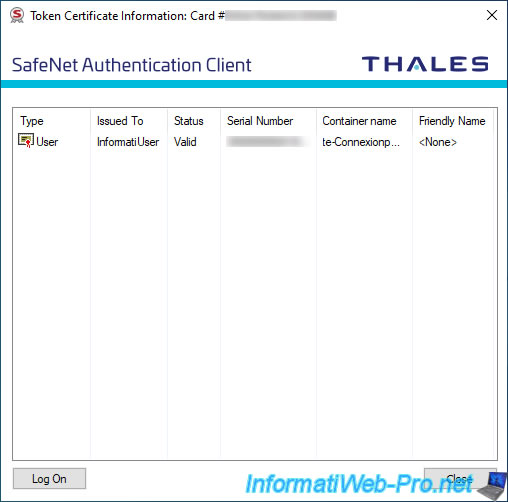
A token / smart card is locked when the user enters the wrong password (user PIN) several times. - Certificate Information : allows you to view the certificates you have stored on your smart card (if applicable)
![]()
In the "Token Certificate Information Card #" window, you will see the list of certificates present on your smart card with :
- Type : the type of certificate. In our case, a certificate for the user (User).
- Issued To : user to whom this certificate was issued.
- Status : indicates whether this certificate is valid or not.
- Serial Number : serial number of this certificate.
- Container name : information about the certificate template used.
In our case, it's a certificate based on the "Smartcard Logon" template. - Friendly Name : friendly name given in the certificate (if applicable).
In our case, we have already written a certificate on our smart card which allows us to connect as InformatiUser on a computer or server thanks to this one.
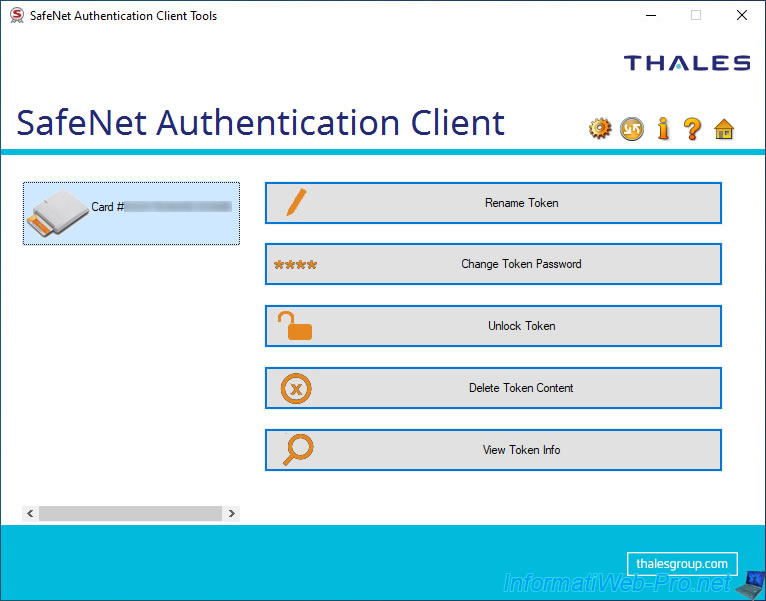
If you click on the "Tools" option of the icon present in the taskbar, you will see the "SafeNet Authentication Client Tools" window appear with the list of card readers connected to your computer / server on the left.
If your smart card reader is empty, its name appears and the icon is grey.
If a smart card is in your smart card reader, your smart card name will appear and you will see an orange smart card on the icon displayed.
Select your smart card reader on the left to use the options available on the right :
- Rename Token : rename your smart card.
By default, its name is "Card #[serial number (PKCS#11) thereof]". - Change Token Password : change the password (user PIN code) of your token / smart card.
- Unlock Token : unlock the token / smart card in the event that it's locked due to a number of unsuccessful attempts on the password (user PIN code) of your token / smart card.
- Delete Token Content : allows you to delete deletable data from your smart card.
- View Token Info : allows you to get lots of system information about your token/smartcard.
3.1. View token / smart card information (View Token Info)
To get information about your smart card reader and your token / smart card in it, click : View Token Info.
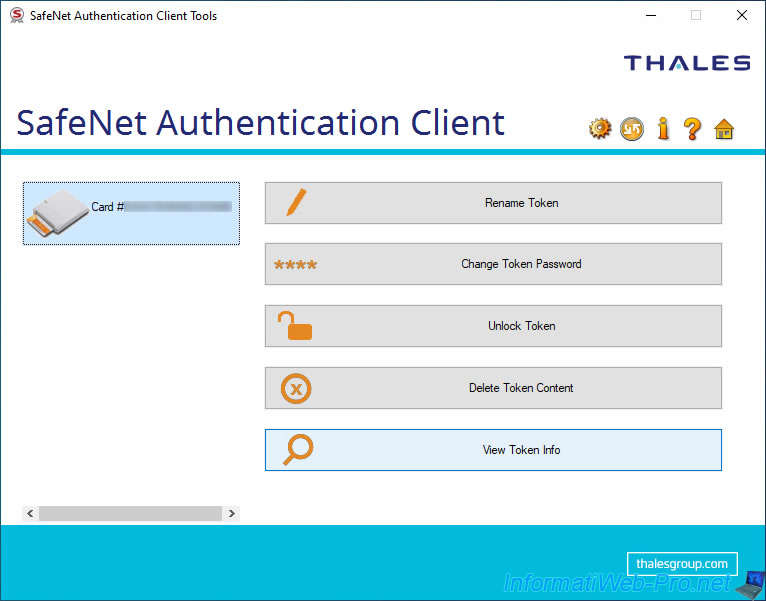
In the "Token Information: Card #..." window that appears, you will find these informations :
- Token name : the name of your token / smart card.
Default : Card #[serial number (PKCS#11) thereof]. - Token category : indicates that it's a hardware token.
- Reader name : name of the smart card reader detected by SAC.
In our case, our "HID OMNIKEY 3121" smart card reader appears under the name "OMNIKEY AG Smart Card Reader USB 0". - Serial Number (PKCS#11) : token / smart card serial number
- Free space (minimum estimated) : free space on your token / smart card.
- Card ID (GUID) : unique identifier (GUID) of your token / smart card.
- Product name : name/model of your token / smart card.
In our case, it's a "THALES IDPrime MD940" smart card. - Card type : range (series) of your smart card.
In our case : IDPrime. - Applet Version : applet version.
In our case : IDPrime Java Applet 4.4.2.A. - Mask version : his mask version.
- Token Password : indicates if a user password (user PIN) is present for this token / smartcard.
- Token Password retries remaining : number of tries remaining for the user password (user PIN) of your token / smart card.
If this number is 0, your token/smartcard is locked.
However, your token/smartcard can be unlocked using the admin PIN if this was set when initializing your token/smartcard. - Maximum Token Password retries : maximum number of retries for the user password (user PIN code) of the token / smart card.
- Token Password expiration : indicates whether the user password (user PIN) of the token / smart card expires or not.
- Administrator Password : indicates whether an administrator password (administrator PIN) was set on your token / smartcard when it was initialized.
This is important, because it allows in particular to unlock a token / smart card in the event that the user has blocked his smart card by reaching the maximum number of failed attempts on his user password (user PIN code). - Administrator Password retries remaining : remaining number of attempts for the administrator password (administrator PIN) of your token / smart card.
Warning : if this number reaches zero, the token / smart card will be permanently blocked and it will therefore be permanently unusable.
Additionally, Thales (formerly Gemalto) doesn't replace blocked tokens/smartcards.
It's therefore important to be careful when entering the administrator password (administrator PIN code) to avoid making your token / smart card permanently unusable. - Maximum administrator Password retries : maximum number of attempts for the administrator password (administrator PIN) of the token / smart card (if this password / PIN was defined during the initialization of your token / smart card).
- FIPS Profile : indicates the FIPS profile (FIPS security level) supported by your token / smartcard (if available).
- Common Criteria (CC) Profile : indicates the certifications of this token/smartcard.
In our case : CC EAL5+ / PP QSCD. - Token unlock objects : indicates that this token/smartcard can be unlocked with the administrator password (administrator PIN).
- Digital Signature PIN retries remaining : number of tries remaining for digital signature PIN.
- Digital Signature PIN maximum retries : maximum number of tries for this digital signature PIN.
This PIN code is used for signature operations via the PKCS#11 library. - Digital Signature PUK retries remaining : number of remaining tries for digital signature PUK code.
- Digital Signature PUK maximum retries : maximum number of tries for this digital signature PUK code.
This PUK code is used to unlock the associated PIN code (Digital Signature PIN). - Sign padding on-board : indicates if the "sign padding" is performed on the card for more security or not.
This feature is supported by Java tokens. - Supported key size : supported key size for the certificates you want to store on this token/smartcard.
In our case : 4096 bits.
The higher the key size, the more secure it will be. But the larger the key size, the more time and CPU resources the encryption/decryption process will take. - ECC : indicates whether or not ECC (Elliptic Curve Cryptography) certificates are supported by your token / smartcard.
ECC is supported by eTokens and IDPrime smart cards. - CSP : indicates the Cryptographic Service Provider supported.
In our case : eToken Base Cryptographic Provider. - KSP : indicates the Key Storage Provider supported.
In our case : SafeNet Smart Card Key Storage Provider.
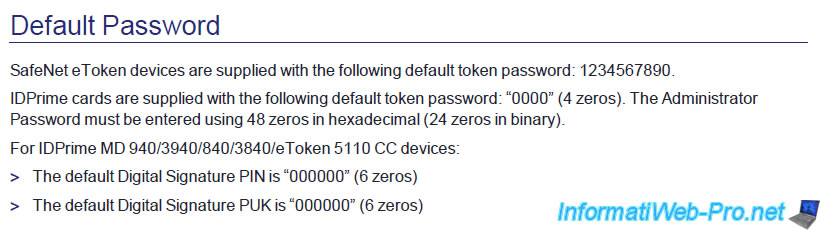
In the case of THALES IDPrime 940/3940/840/3840 smart cards and eTokens 5110 CC, the 4 default PIN codes are :
- user password (user PIN) : 0000
- administrator password (administrator PIN) : 0000...0000 (24 zeros in binary, so 48 zeros in hexadecimal)
- Digital Signature PIN code : 000000
- Digital Signature PUK code : 000000
Source : SafeNet Authentication Client 10.8 R6 Post GA (2) - WINDOWS RELEASE NOTES (page 5).
Please note : as a reminder, 5 unsuccessful attempts on the administrator password (administrator PIN code) will permanently block your smart card and Thales (Gemalto) will not replace it.
Sources :
- the help (in PDF format) available by clicking on the "?" of this "SafeNet Authentication Client (SAC)" program (version 10.8 R6 in our case)
- SafeNet Authentication Client (Windows-Linux-Mac) Version 9.0 (GA) - Administrator's Guide (PAGE 233)
- SafeNet IDPrime 940 (data sheet)
Share this tutorial
To see also
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them
-
Windows Server 1/5/2024
WS 2016 - AD CS - Create a recovery agent to recover certificates


You must be logged in to post a comment