Deploy a multi-site PKI infrastructure on Windows Server 2016
- Windows Server
- 22 December 2023 at 11:41 UTC
-

- 4/5
12. Enterprise sub-CA information in Active Directory
If you reopen the "Active Directory Sites and Services" console, you will see that data about your enterprise certification authorities has been automatically stored in your Active Directory infrastructure.
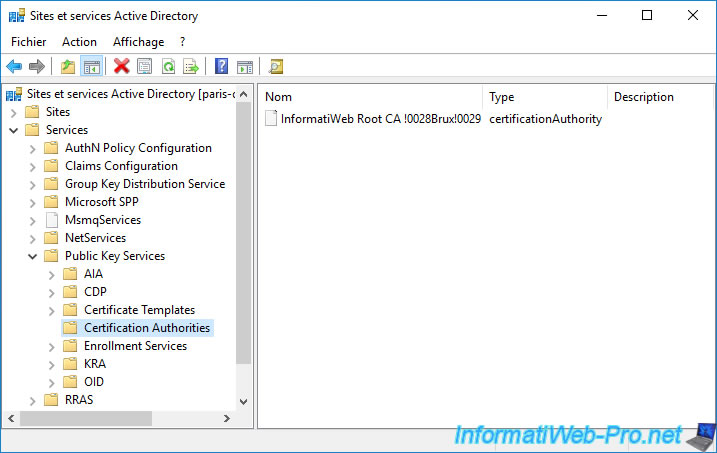
If you go to the "Services -> Public Key Services -> Certification Authorities" folder, you will only see your standalone root CA.
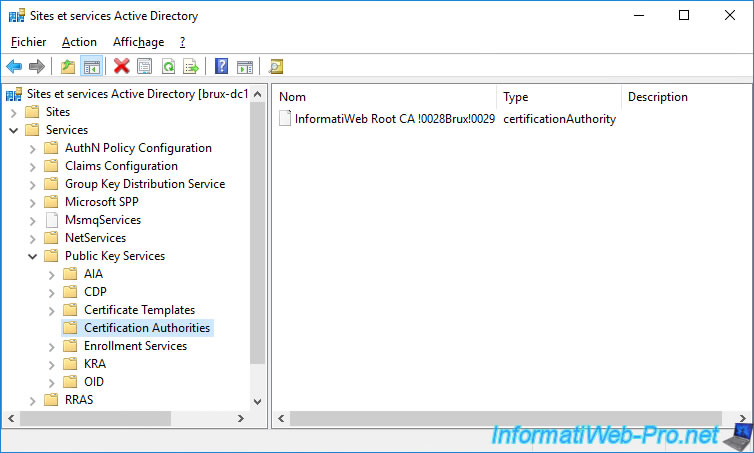
On the other hand, if you go to the "Services -> Public Key Services -> AIA" folder, you will see that your root certificate authority will appear, as well as a secondary certificate authority.
However, as you can see, we only see CAs located in Brussels (in our case), because we opened this console on our "brux-dc1" server.
Given that the replication of Active Directory data is not instantaneous between different Active Directory sites, it's normal that the certification authority of the remote site (Paris in our case) doesn't appear for the moment.
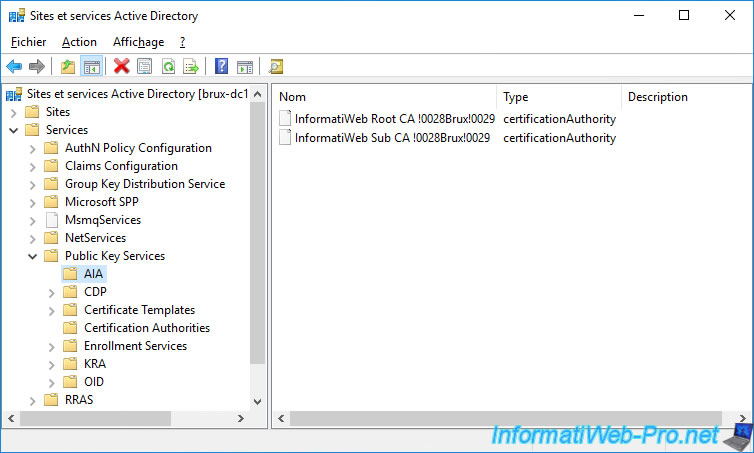
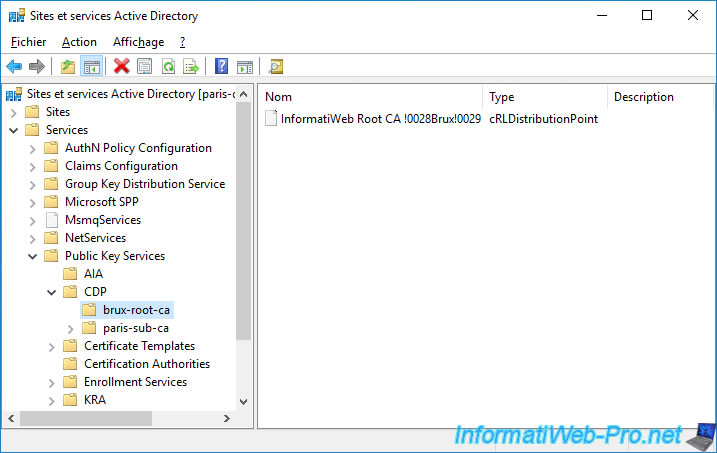
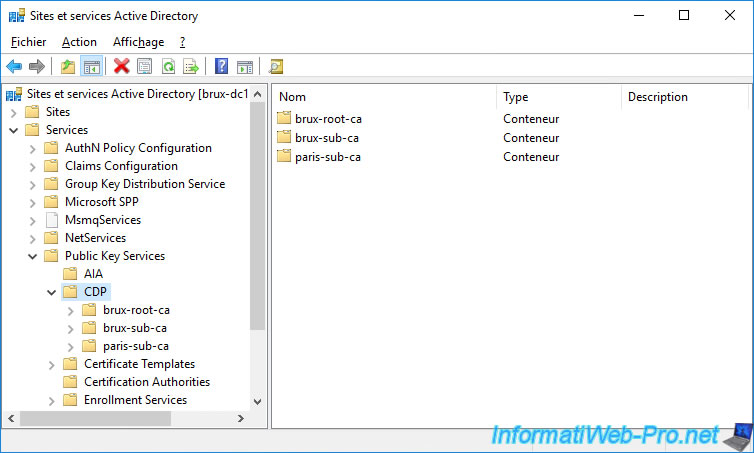
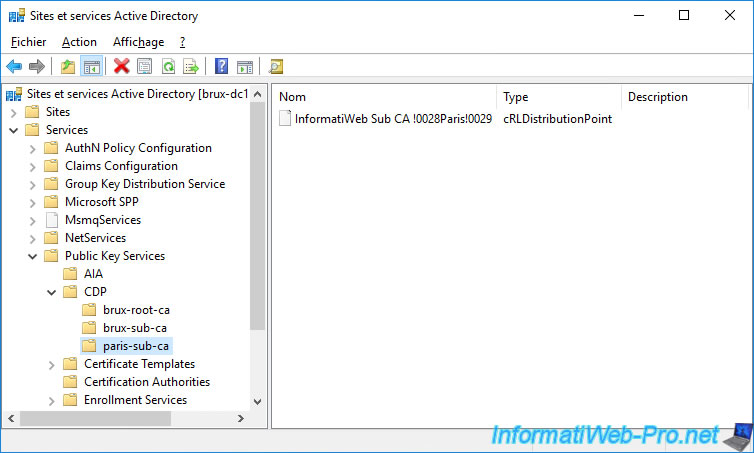
In the "Services -> Public Key Services -> CDP" folder, you will find 2 folders :
- a "brux-root-ca" folder containing the revocation list of our root certification authority located in Brussels
- a "brux-sub-ca" folder containing the revocation list of our secondary certification authority located in Brussels
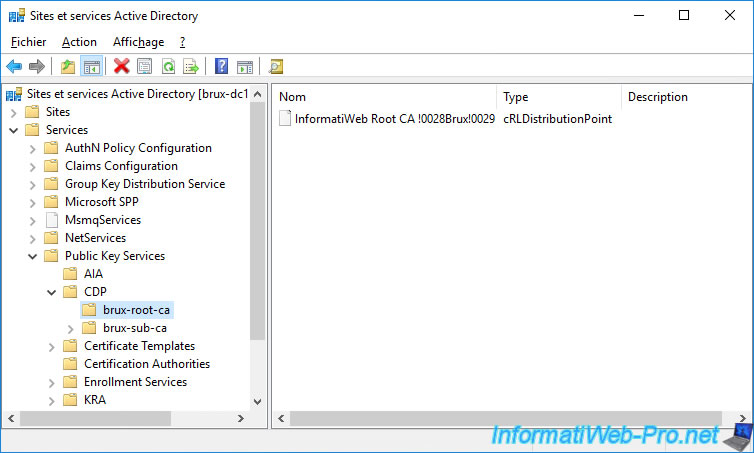
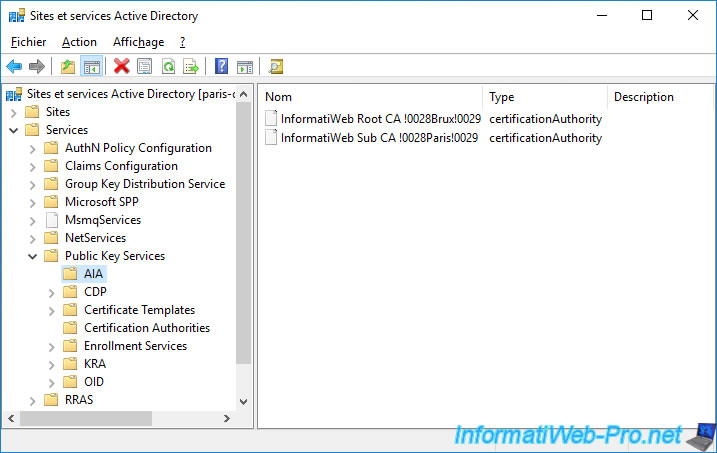
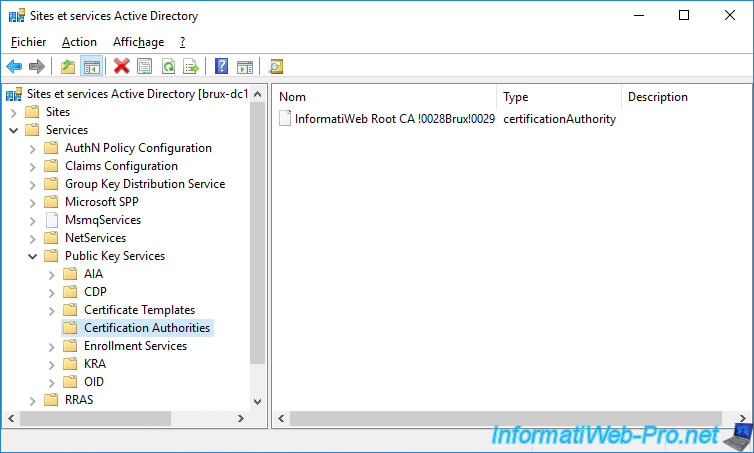
If we open this console on a domain controller of the remote site, we can see that our root certification authority is present in the "Certification Authorities" folder.
In the "AIA" folder, we can see our root CA from Brussels and the secondary CA from Paris.
On the other hand, the secondary certification authority of Brussels doesn't appear for the moment, because the data has not yet been replicated by Active Directory from Brussels.
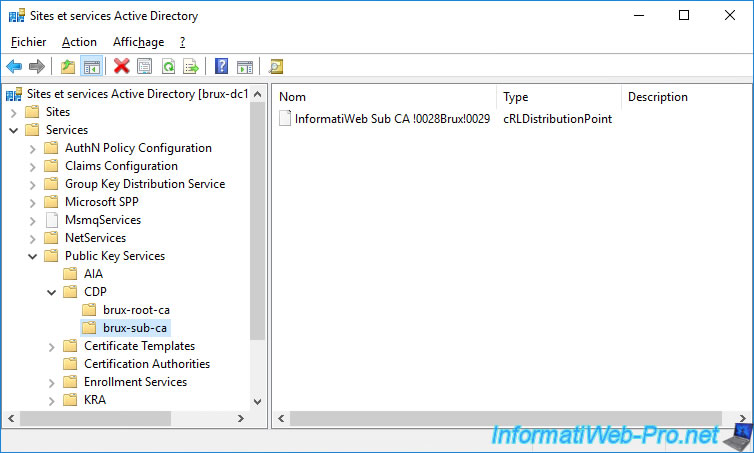
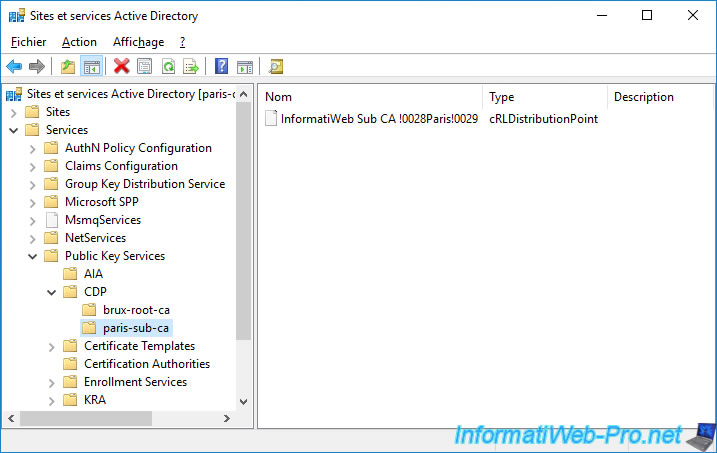
In the "CDP" folder, we can see :
- brux-root-ca : the certificate revocation list of our root certification authority
- paris-sub-ca : the certificate revocation list of our secondary certification authority
13. Force replication of Active Directory data between different sites
As you have seen previously :
- infomation about the secondary certification authority of Brussels is present for the moment only in Brussels
- infomation about the secondary certification authority of Paris is present for the moment only in Paris
For the data of your 2 secondary certification authorities to be present regardless of the Active Directory site where you are, all you have to do is wait or force the replication of data from one Active Directory site to another.
To do this, open the "Active Directory Sites and Services" console and select :
- on the left : the "NTDS Settings" node of the domain controller to update
- on the right : the line corresponding to the source domain controller which contains the data you are missing on the domain controller selected on the left.
In our case, we are going to update our "brux-dc1" domain controller from the "paris-dc1" domain controller.
To do this, right-click on the connection object on the right and click : Replicate Now.
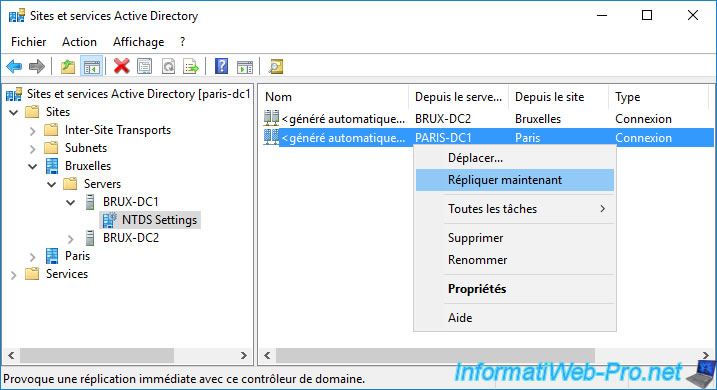
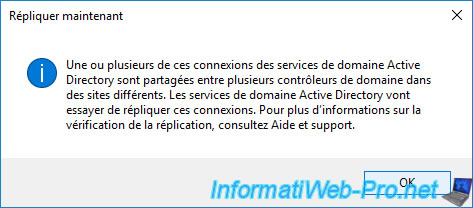
As you can see, Active Directory Domain Services will try to replicate these connections.
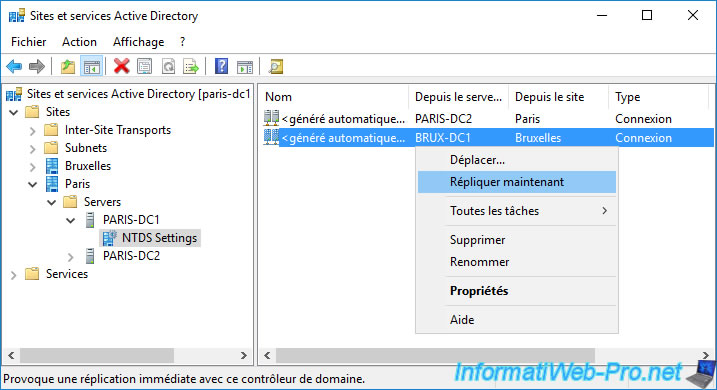
Do the same to also replicate the data in the other direction.
Thus, what is only in Paris will be copied in Brussels and what is only in Brussels will be copied in Paris.
In the end, you will have the information for Paris and Brussels on your 2 physical sites.
Important : replication is not instantaneous. You may have to wait up to 1 minute for data to be fully replicated from one Active Directory site to another.
Once the Active Directory data is replicated, you will see your root certification authority appear in the "Certification Authorities" folder.
In the "Services -> Public Key Services -> AIA" folder, you will see :
- your root CA.
In our case : InformatiWeb Root CA (Brux). - your secondary CAs.
In our case : InformatiWeb Sub CA (Brux) and InformatiWeb Sub CA (Paris).
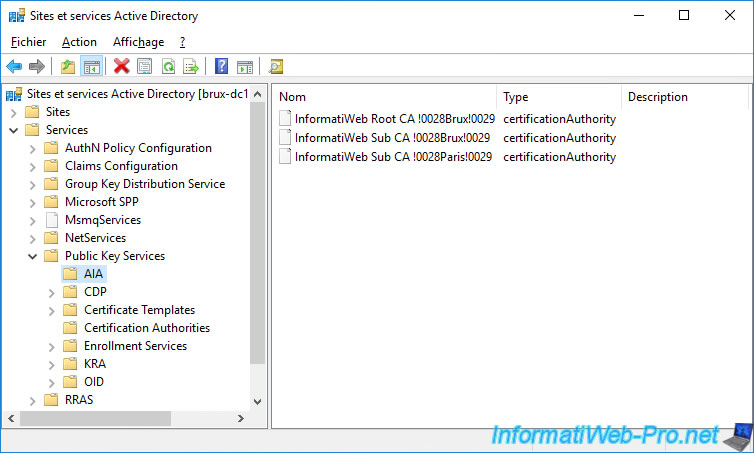
In the "Services -> Public Key Services -> CDP" folder, you will find 3 folders :
- one for the root CA.
In our case : brux-root-ca. - 2 more for your secondary CAs.
In our case : brux-sub-ca and paris-sub-ca.
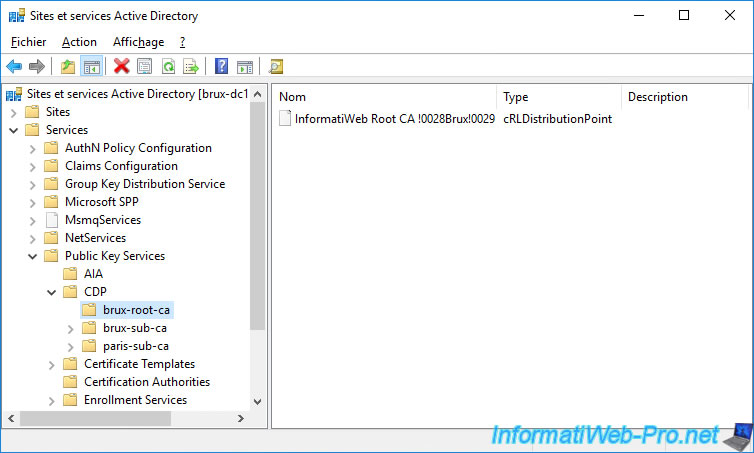
In the "brux-root-ca" folder, we find the certificate revocation list of our root certification authority located in Brussels.
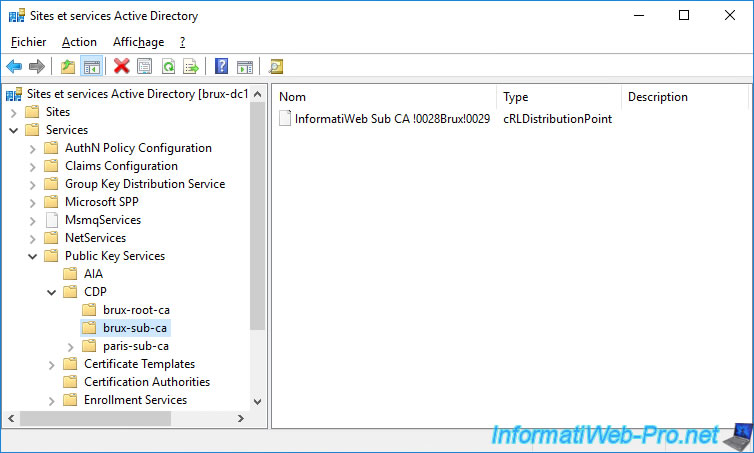
In the "brux-sub-ca" folder, we find the certificate revocation list of our secondary certificate authority located in Brussels.
And finally, in the "paris-sub-ca" folder, we find the certificate revocation list of our secondary certification authority located in Paris.
14. Certification authorities recognized by your client PCs
Now that all the information concerning your certification authority is on all the Active Directory sites of your infrastructure, restart your client PCs if necessary, then open an "mmc" console.
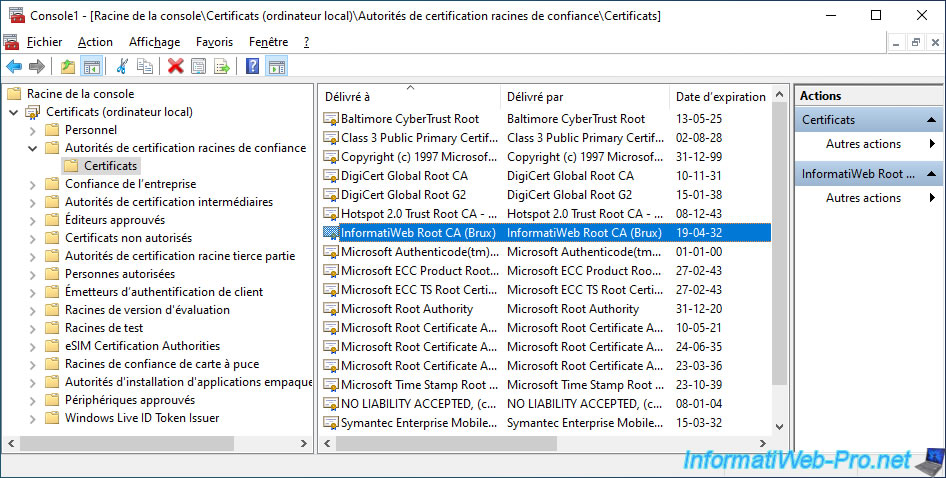
In this "mmc" console, add the "Certificates" component for the local computer or the current user (depending on your rights on this client PC) and go to the "Trusted Root Certification Authorities" folder.
As you can see, your standalone root CA certificate is in this certificate list.
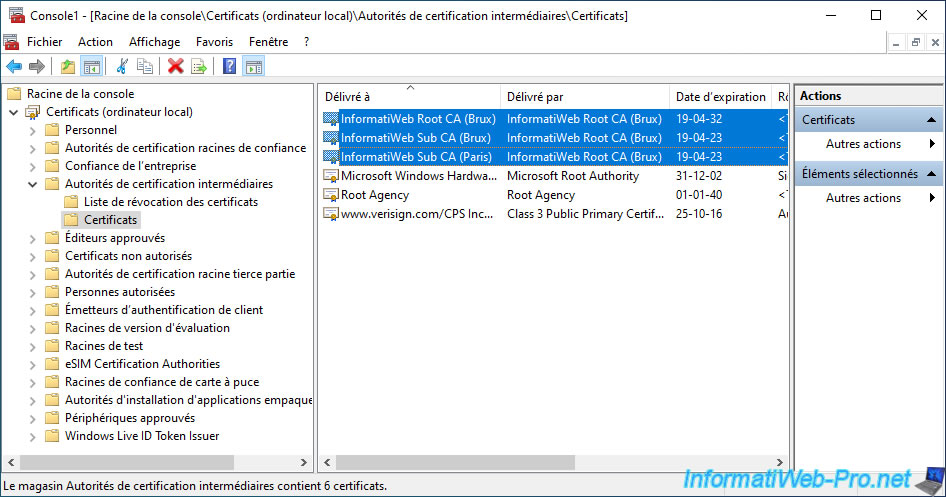
If you go to the "Intermediate Certification Authorities" folder, you will find your standalone root CA's certificate, as well as those of your enterprise subordinate CAs.
Your client PCs and your servers therefore trust the certificates issued by your various certification authorities.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment