- Windows Server
- 15 September 2023 at 15:39 UTC
-

- 1/5
In your company, it's important to secure the connection to your various servers and services to prevent a malicious person from being able to recover or alter sensitive information passing through the network.
To do this, you will need to create a certification authority (CA) to be able to secure these free of charge thanks to the certificates that you will issue (deliver) via it.
- What is a certificate authority (CA) ?
- Standalone or enterprise CA ?
- Configuration used
- Prepare the CAPolicy.inf file before installing the CA
- Install enterprise certificate authority
- Initial configuration of your certificate authority
- Revocation list
- Enable auditing of your certificate authority (CA)
- View your CA's certificate
- Automatic distribution of your CA certificate via Active Directory
- Request a user certificate (example)
1. What is a certificate authority (CA) ?
1.1. What is a certificate authority (CA) used for ?
A certification authority allows you to enroll (issue) certificates which will be valid in your company and which will allow you to secure the connection to your various servers and services : website, mail server, hypervisor, ...
Once your certificates have been enrolled (issued) and installed on your various servers or services, the data can no longer be intercepted or even modified by a third party without an error occurring. This will warn you if there is a problem with the certificate used or with the data received.
In addition, this will also allow you to authenticate the server, computer or user concerned. This way, you will be sure to connect to the right server or service or talk to the right person.
Otherwise, a warning will be displayed. Which, in business, should put you on the alert.
1.2. The problem with self-signed certificates
When you install a new service that can be secured with an SSL certificate, a self-signed certificate may already be installed to secure the connection to this service.
However, using a self-signed certificate will always cause a default warning since it's never from a CA your computer trusts. Indeed, a self-signed certificate is a certificate that the server has issued to itself.
A self-signed certificate is therefore never valid and you will always have to add an exception (in your web browser, for example) to ignore this problem.
It's therefore important to replace it with a certificate from your certification authority so that you can really trust it and also benefit from the possibility of revoking this certificate in the event of a problem.
Thus, access to the service concerned is blocked, because the administrator considers that this certificate has been stolen or that the server protected with it has been compromised by a hacker.
Important : the use of a valid certificate (from an internal or commercial certificate authority) may be required by different services.
Indeed, the use of self-signed certificates will, for example, pose a problem with Microsoft's RDS (Remote Desktop Services) technology and with Citrix's virtualization technologies.
2. Standalone or enterprise CA ?
When you install your CA, you will see that the wizard will offer you to create a standalone or enterprise CA.
2.1. Standalone CA
A standalone CA can be installed on a server that is in a workgroup (therefore NOT linked to an Active Directory domain) and is usually taken offline afterwards for security reasons.
Warning : although a standalone certification authority can be linked to an Active Directory domain (even if it doesn't add any feature to it), it is strongly discouraged to do so if you plan to keep this certification authority offline too long.
Indeed, if you do so, the secure channel linked to the functioning of Active Directory which allowed this server to communicate with your Active Directory infrastructure will be broken. This is because the password used internally for this secure channel will be different on your server acting as a standalone CA and on your Active Directory domain controller.
If necessary, refer to our tutorial : WS 2016 - AD DS - Reset a computer account.
2.2. Enterprise CA
An enterprise CA should be installed only on an Active Directory domain-joined server.
Indeed, a company certification authority can use the trust relationships of your Active Directory infrastructure to, for example, obtain information on a client (server, computer or user) automatically or manually requesting a certificate. It can also automatically distribute its certification authority certificate to the various servers and computers in your company so that they automatically trust the certificates it issues.
Using an enterprise certificate authority also allows you to use certificate templates, automatically enroll certificates (for example, via group policies (GPOs)), as well as archive keys.
Which is not possible with a standalone CA.
Additionally, everyone in your domain will automatically trust your enterprise CA.
You will also notice that your CA and its certificate templates will be stored in the "Configuration" partition of your Active Directory infrastructure.
3. Configuration used
For this tutorial, you will need 3 machines (2 servers and 1 computer):
- an Active Directory domain controller
- a server linked to your Active Directory domain where you will install the enterprise certification authority (as explained later in this tutorial).
- a client PC on Windows 10 (version 2004 in our case)
Note that in the case of a test environment, you could install the CA on the server already acting as an Active Directory domain controller to save a server (or virtual machine). Although this is not recommended.
Important : in production, it's strongly discouraged to install a certification authority on the same server as your domain controller to avoid various problems:
- Certificate Authority on DC - Microsoft TechNet
- Is there a good reason not to install AD Certificate Services on a 2008 domain controller ? - Microsoft TechNet
4. Prepare the CAPolicy.inf file before installing the CA
Although optional, you can pre-configure many options that will be used when installing your CA on Windows Server.
The advantage of this file is that it allows you to configure many options, some of which are not configurable from your certification authority's configuration wizard.
To do this, open Notepad as an administrator.
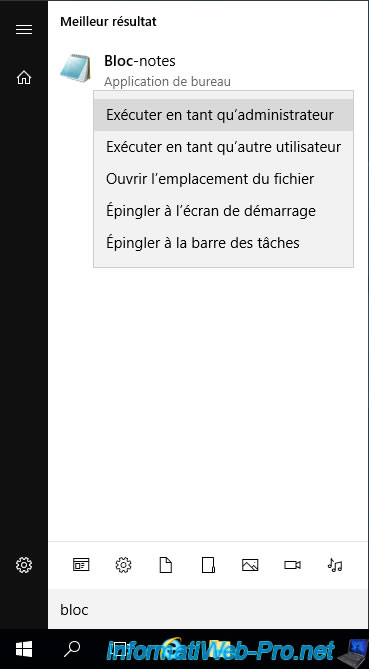
If you want to use this "CAPolicy.inf" configuration file, be aware that the only mandatory section (to be indicated first in this file) is the "Version" section with the "Signature" attribute, the value of which will always be "$Windows NT$".
For the example, we have defined the "certsrv_server" section which allows you to define :
- RenewalKeyLength : the size of the key that will be used when renewing the CA certificate. For example : 2048-bit.
You could also use a 4096-bit key to improve security, but first make sure that your various applications and servers support this key size.
Warning : if you specify a renewal size different from the one you will define during the installation of your certification authority, all issued certificates will have to be reissued. - RenewalValidityPeriod : the unit of the CA certificate renewal period.
For example : "Years". - RenewalValidityPeriodUnits : the CA certificate renewal period value.
In this case : 5 years (thanks to the unit defined previously).
To know all the settings available for this "CAPolicy.inf" configuration file, refer to the "CAPolicy.inf Syntax" page of the official Microsoft documentation.
In our case, it looks like this:
Plain Text
[Version] Signature="$Windows NT$" [certsrv_server] RenewalKeyLength=2048 RenewalValidityPeriod=Years RenewalValidityPeriodUnits=5
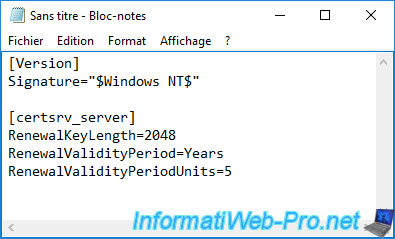
Then, click "File -> Save As" and navigate to the "%systemroot%" folder (which corresponds to the "C:\Windows" folder).
Provide "CAPolicy.inf" as the filename and make sure to select these options for the file to be created correctly :
- Save as type : All Files
- Encoding : ANSI
Now, click Save.
5. Install enterprise certificate authority
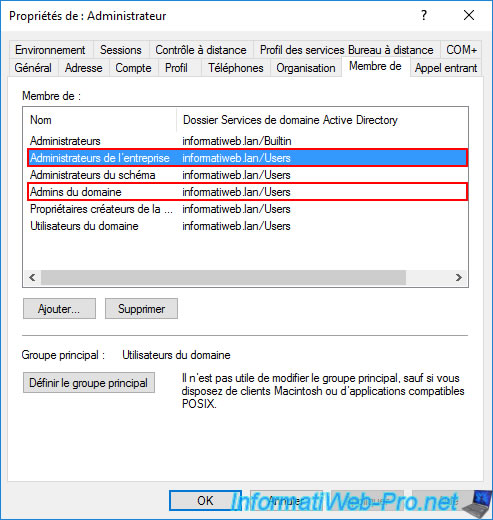
To install the "Active Directory Certificate Services" role (and therefore your certification authority), you must first log in with an account that is part of the "Enterprise Admins" and "Domain Admins" groups (for the root Active Directory domain).
In our case, we will use the "Administrator" account of the domain.
Launch the server manager and click on the link : Add roles and features.
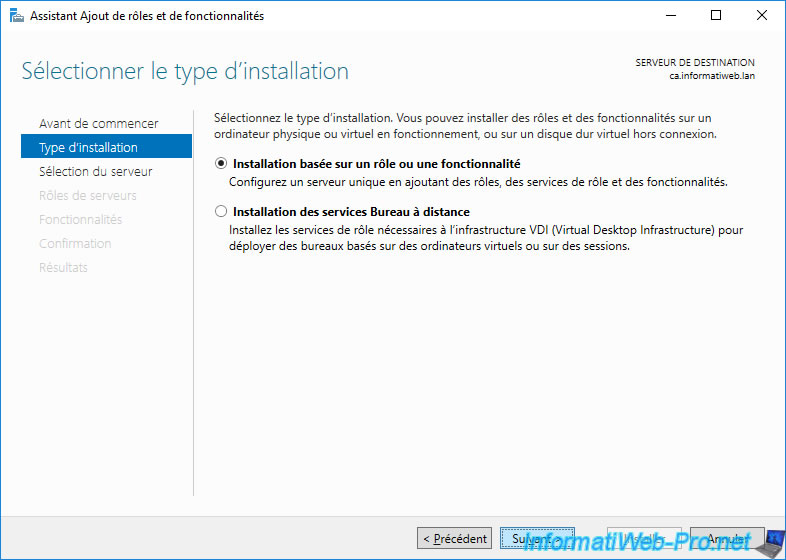
Select "Role-based or feature-based installation".
Click Next.
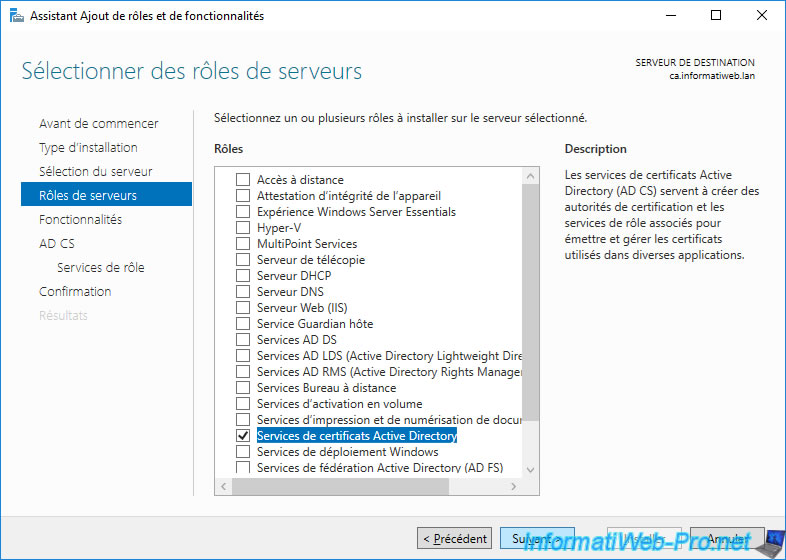
Install the "Active Directory Certificate Services" role (which corresponds to "AD CS" as you can see in its description).
No feature to install for this role.
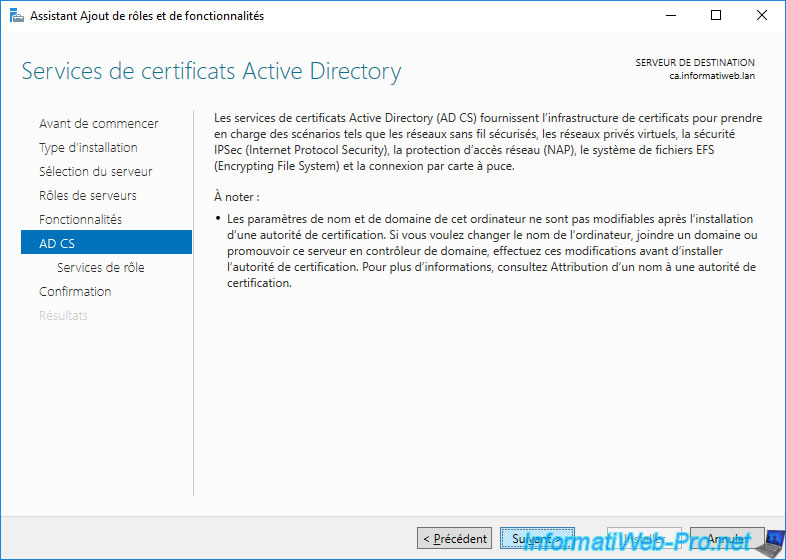
A description of the "Active Directory Certificate Services" (AD CS) role appears.
As you can see, the certificates will allow you to :
- create secure wireless (Wi-Fi) networks
- create VPN (virtual private network) tunnels that are always secure, especially via IPSec (Internet Protocol Security)
- protect network access (NAP)
- encrypt and decrypt data without other people being able to read your data thanks to the EFS file system (Encrypting File System)
- use smart cards (in which user certificates will be stored)
Warning : as indicated in this description, the name of this server, as well as its connection to your Active Directory domain, can't be modified once the certification authority is installed.
Indeed, its name will be part of the link allowing clients to consult your revocation lists and its binding to the Active Directory domain allows it to store different information (such as the certificate templates created by default and its certification authority certificate for that your client trust him).
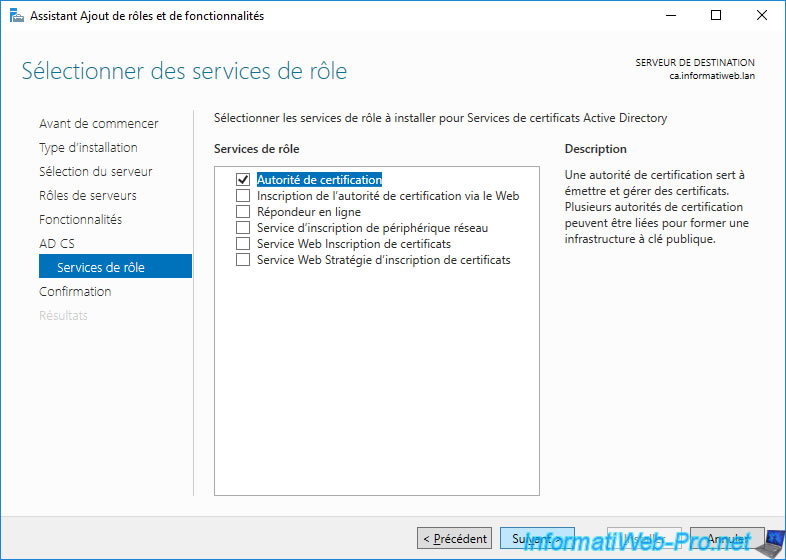
Important : to install a certification authority, the mandatory role service is : Certification Authority.
The other services offered allow you to add different features to it, but are not mandatory.
- Certification Authority : main component allowing in particular to issue (deliver) certificates, but also to manage them (certificates issued, certificates revoked, ...).
These certificates may be issued to secure access to servers, computers or to authenticate (verify the identity) of users. - Certification Authority Web Enrollment : allows you to enroll (issue) or renew certificates via a web interface, as well as provide access to your CA's certificate revocation lists via HTTP or HTTPS protocols.
- Online Responder : allows a client to check the validity of a certificate using the OCSP protocol rather than downloading many revocation lists (CRL).
- Network Device Enrollment Service : issuing (delivering) certificates to network devices (such as routers, for example).
- Certificate Enrollment Web Service : allows computers and users to obtain or renew certificates without being members of an Active Directory domain or while temporarily outside the company.
- Certificate Enrollment Policy Web Service : a role service used by the previous role service (Certificate Enrollment Web Service) to enable computers and users who are not members of an AD domain or who are temporarily outside of the company to obtain or renew certificates based on a policy.
Click on : Install.
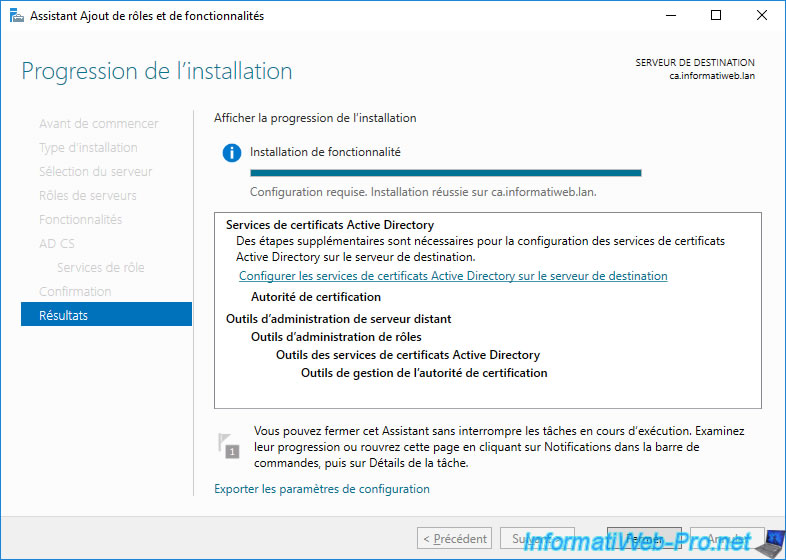
Wait while Active Directory Certificate Services (AD CS) installs.
Wait while Active Directory Certificate Services (AD CS) installs.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them


You must be logged in to post a comment