Deploy a multi-site PKI infrastructure on Windows Server 2016
- Windows Server
- 22 December 2023 at 11:41 UTC
-

- 3/5
9. Submit requests from your subordinate CAs to your root CA
Transfer the certificate requests created on your secondary enterprise CAs to your standalone root CA using an USB key (for example).
Then, on your standalone root CA, open the "Certification Authority" console and right-click "All Tasks -> Submit new request" on its name.
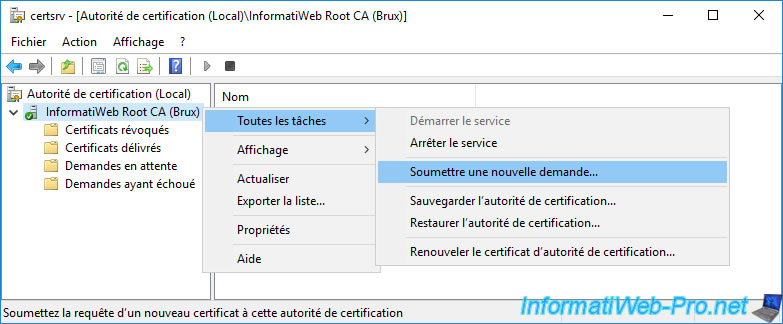
Select the certificate request for your 1st subordinate enterprise CA and click Open.
Then, do the same with the certificate request for your 2nd subordinate enterprise CA.
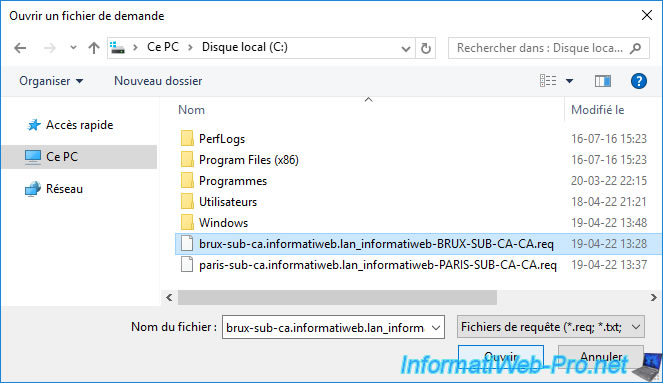
Once certificate requests have been submitted to your standalone root CA, you will need to validate them manually from the "Pending Requests" folder.
To do this, right-click on a pending certificate request and click : All Tasks -> Issue.
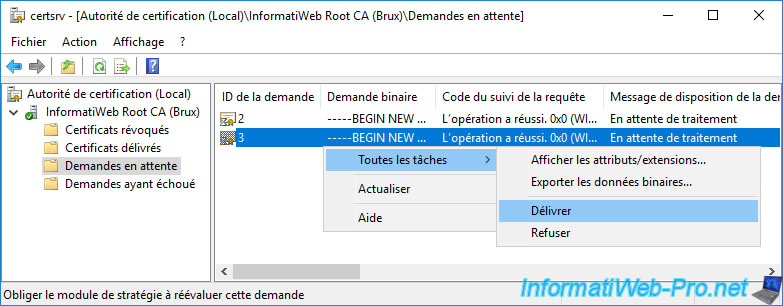
Once you have validated your 2 certificate requests, you will find the corresponding certificates in the "Issued Certificates" folder.
As you can see, the certificate template used by these certificates is "SubCA" (that is : sub CA or secondary CA or subordinate CA).
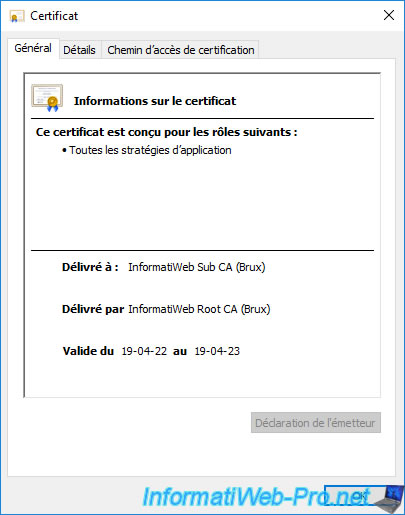
If you double click on the 1st certificate, you will see that it was issued to your 1st enterprise subordinate CA by your standalone root CA.
In our case, it's the certificate issued to our Brussels secondary certification authority "InformatiWeb Sub CA (Brux)".
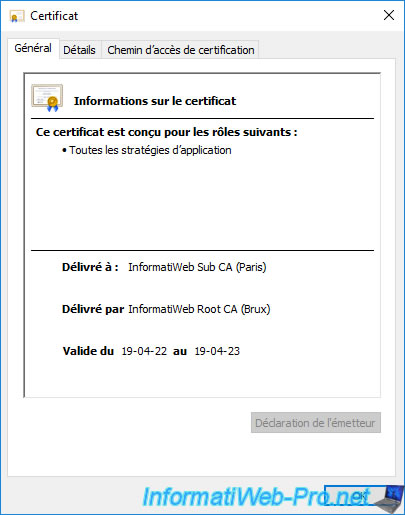
The 2nd certificate is that of your 2nd secondary (subordinate) CA.
In our case, it's the one located in Paris : InformatiWeb Sub CA (Paris).
10. Export certificates from your subordinate CAs
To be able to use your subordinate CAs, you will need to import their certificates to them.
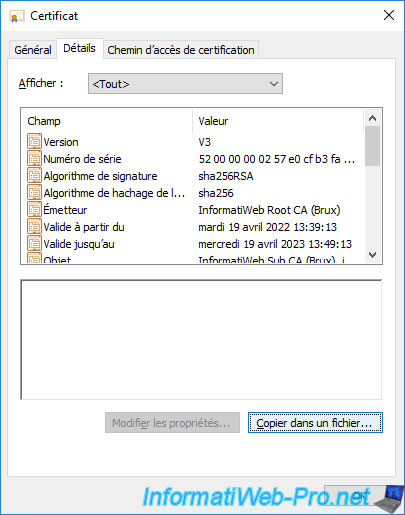
To do this, go to the "Details" tab of each open certificate (as explained previously) and click on the "Copy to File" button.
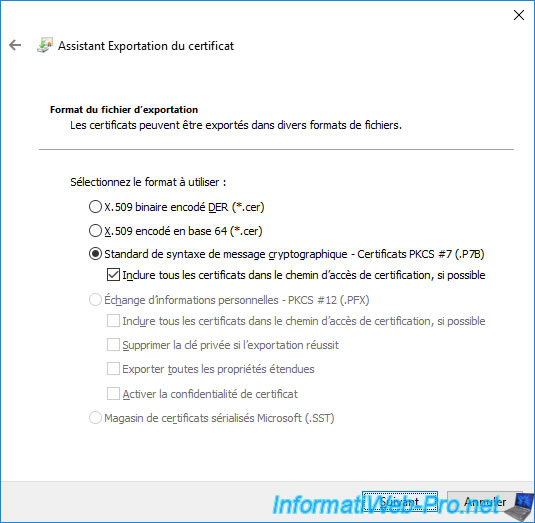
The certificate export wizard appears.
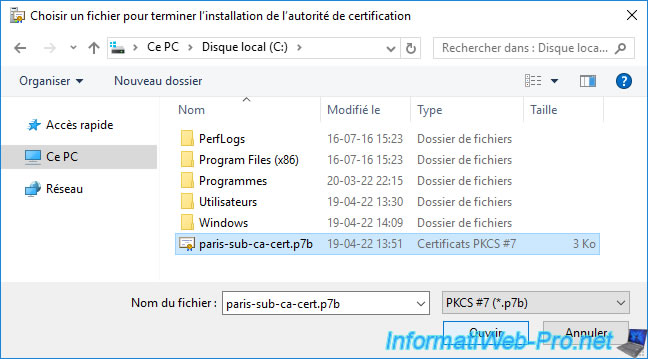
Select "Cryptographic Message Syntax Standard - PKCS #7 Certificates (.P7B)", check the "Include all certificates in the certification path ..." box and click Next.
Note : you must use this ".p7b" format, because it's the one expected by the "Certification Authority" console that you will use later on your secondary enterprise certification authorities.
The certificates have been exported.
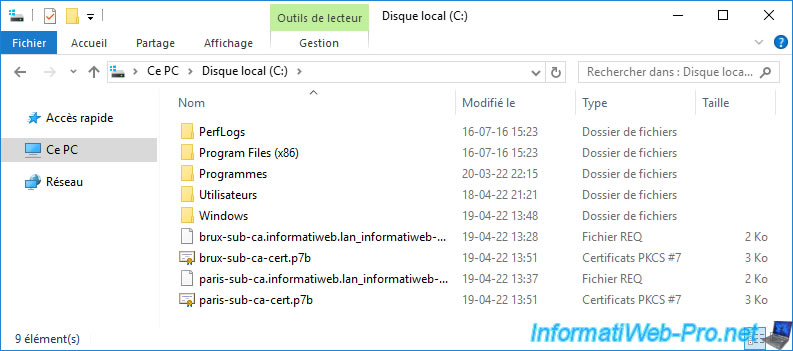
11. Install enterprise sub-CA certificates
To get started, transfer the certificates exported from your standalone root CA to your enterprise subordinate CAs.
Then, on these subordinate CAs, open the "Certification Authority" console and right-click "All Tasks -> Install CA Certificate" on their names.
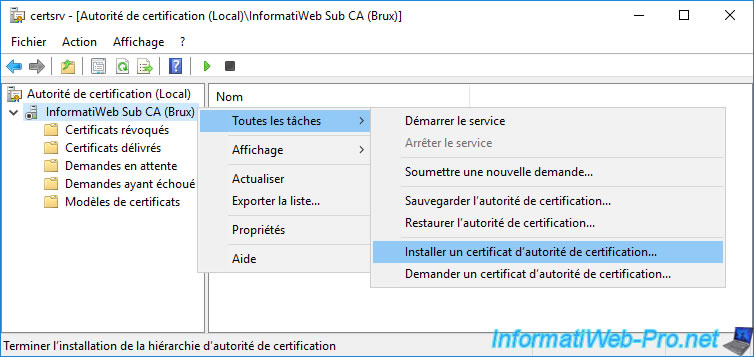
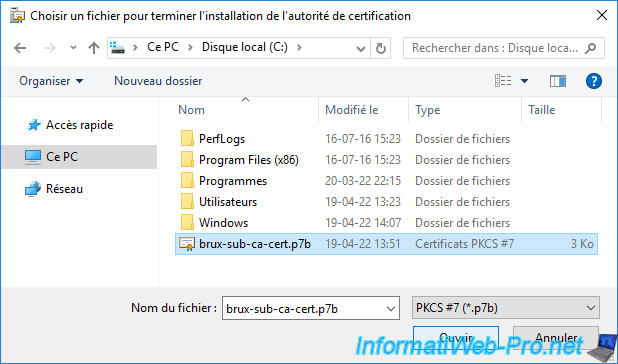
On each certification authority, select the corresponding certificate previously exported in ".p7b" format.
Once your subordinate CA's certificate is installed, right-click "All Tasks -> Start Service" on its name.
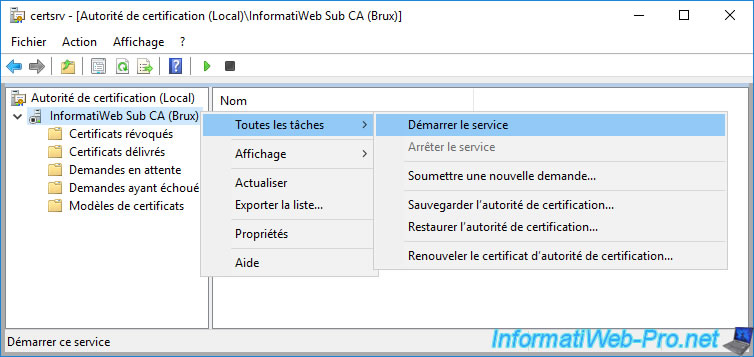
Your subordinate CA is up and running.
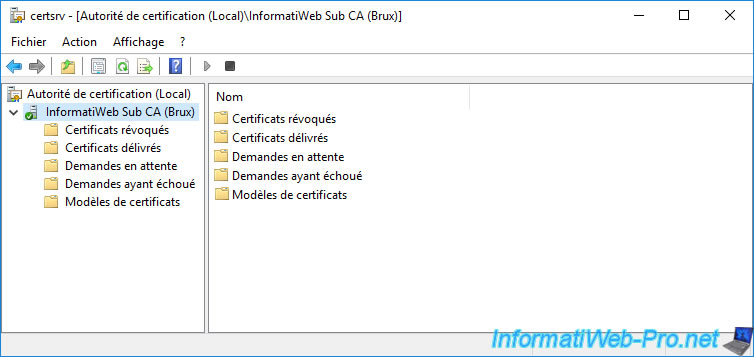
Don't forget to install the certificate of your 2nd subordinate enterprise CA.
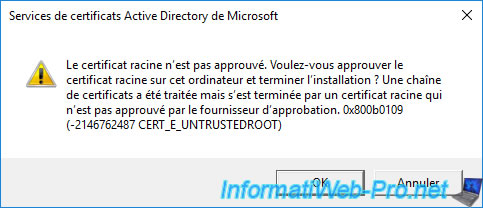
Given that the root certification authority is located on a physical site (in our case : Brussels) and that this 2nd subordinate certification authority is located on another physical site (in our case : Paris), it's possible that the certificate from your root CA has not yet arrived at your subordinate CA.
To solve the problem, force the replication of data on your Active Directory infrastructure using the connection objects visible via the "Active Directory Sites and Services" console or manually import the certificate of your root certification authority into the "Trusted Root Certification Authorities" from your enterprise sub-certificate authority.
Then, this problem will disappear.
Plain Text
The root certificate is untrusted. Do you wish to trust the root certificate on this machine and complete the installation? A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT).
Once the CA certificate is installed, you will need to start this CA.
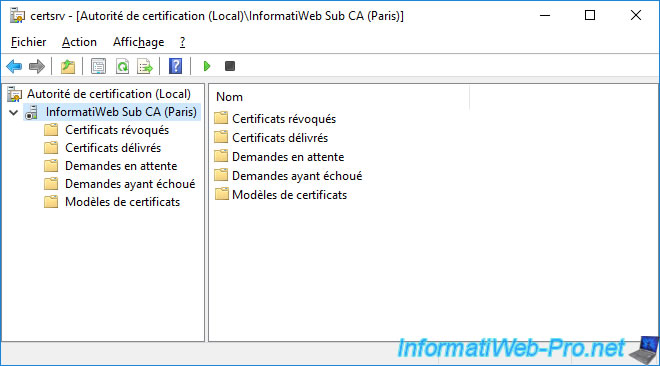
To do this, right-click "All Tasks -> Start Service" on its name or click the "Play" icon.
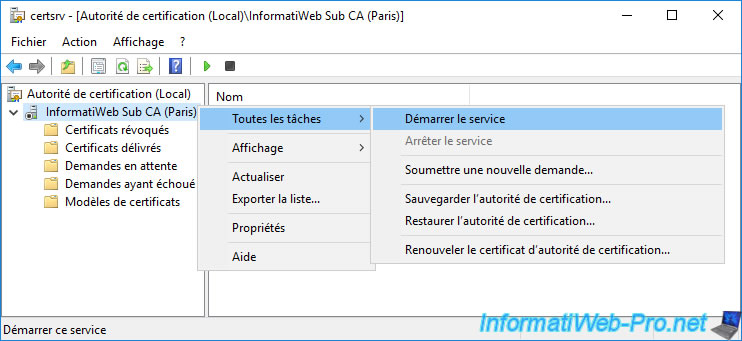
Your 2nd subordinate enterprise CA has started.
As you can see, your 2nd subordinate CA's certificate is valid and was issued by your root CA.
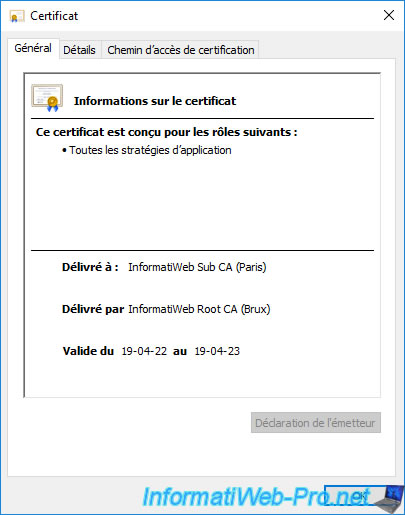
If you go to the "Certification Path" tab, you will see that this secondary CA certificate is valid.
If you select the root certificate, you will see that this is also valid.
Warning : if your root CA's certificate becomes invalid (if it expires, for example), your subordinate CA's certificate and its certificates will also become invalid.
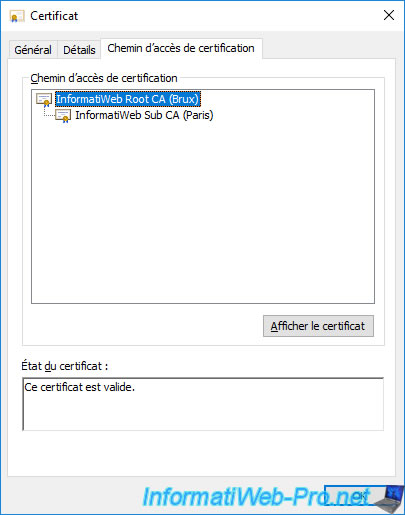
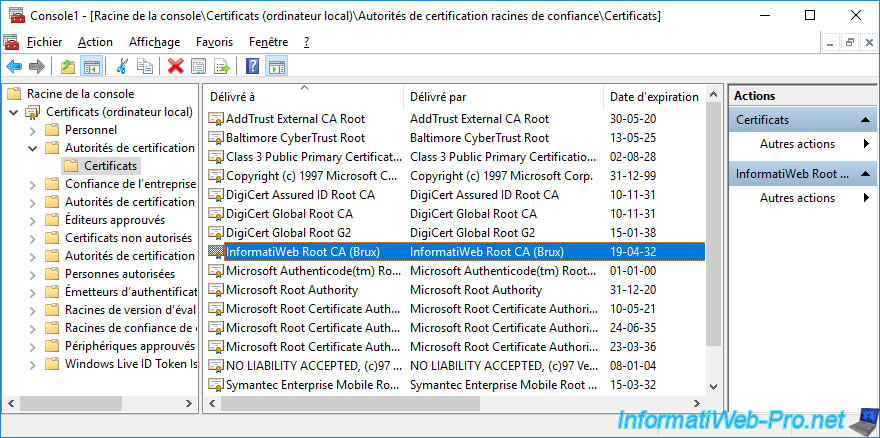
As you can see, your root CA's certificate is part of your enterprise subordinate CA's trusted root CAs.
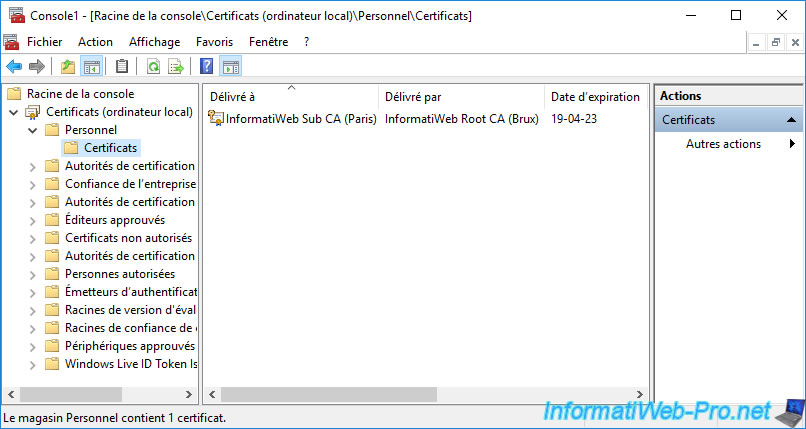
In your "Personal" certificate store, you will see the certificate of your secondary CA appear.
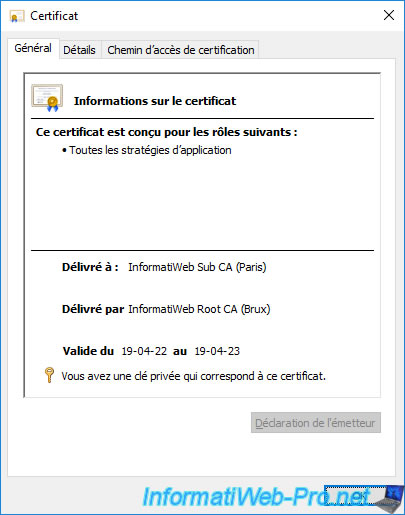
As you can see, now that your enterprise subordinate CA certificate is installed, its associated private key is also present.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment