Secure access to VMware vCenter Server (VCSA) over HTTPS on VMware vSphere 6.7
- VMware
- 25 October 2024 at 11:03 UTC
-

- 4/7
7. Replace VMware vCenter Server machine SSL certificate
Now that you have the certificate and private key needed to secure access to your VMware vCenter Server (VCSA), click the "Actions -> Replace" link for the "__MACHINE_CERT" machine SSL certificate.
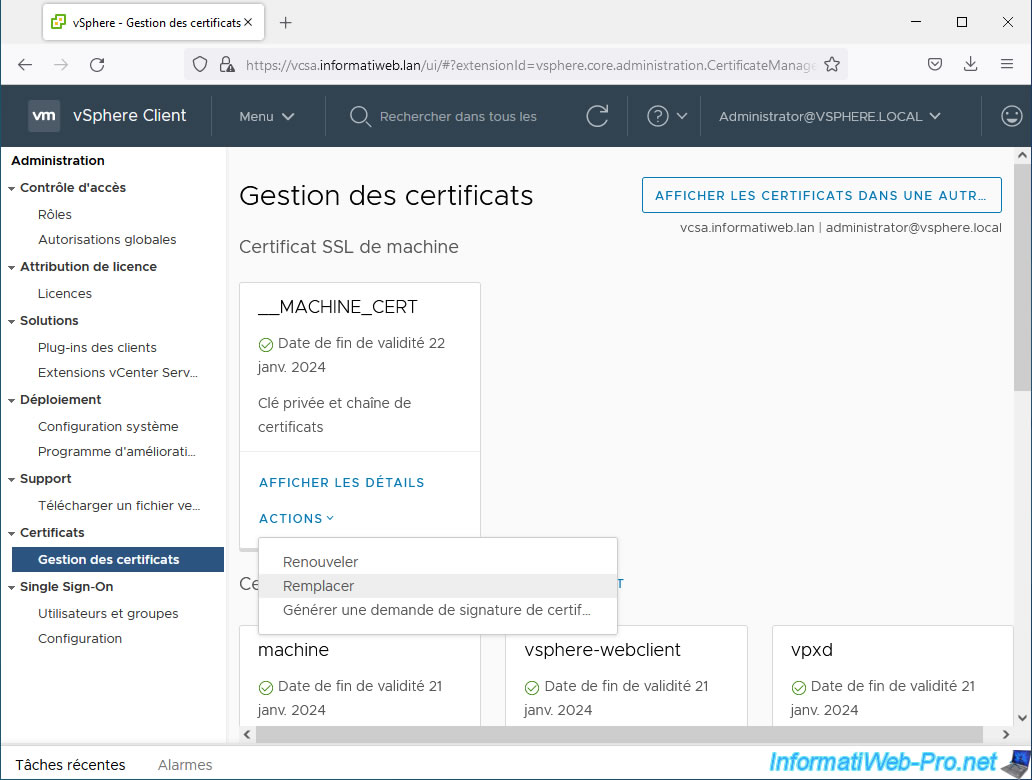
In the "Replace Certificate" window that appears, click on the 1st "Browse" button for the "Certificate Chain" option.
As you can see, VMware supports the formats: .cer, .pem and .crt.
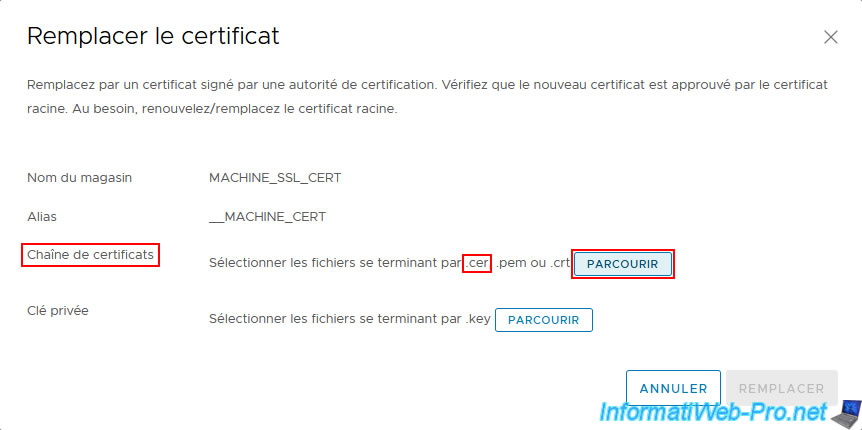
Select the certificate issued for your VMware vCenter Server previously converted from ".p7b" to ".cer" format and click Open.
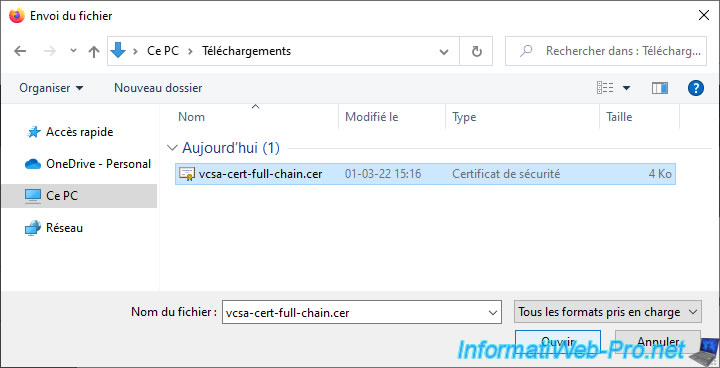
Next, click the 2nd "Browse" button for the "Private Key" option.
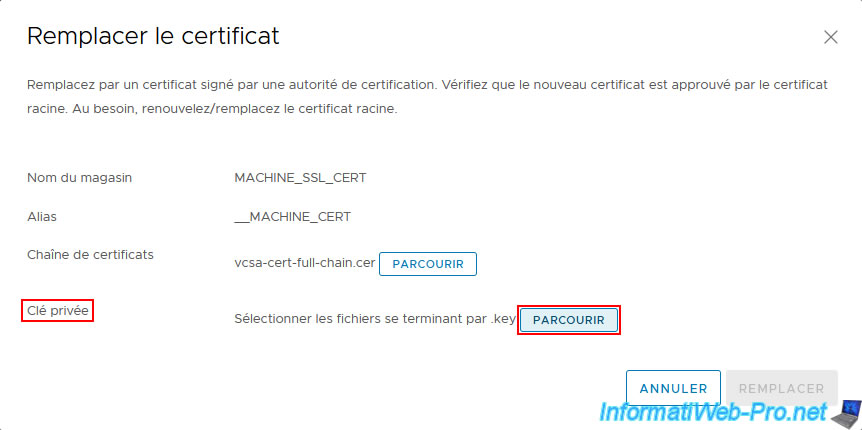
Select the "vcsa-private-key.key" file created previously and click Open.
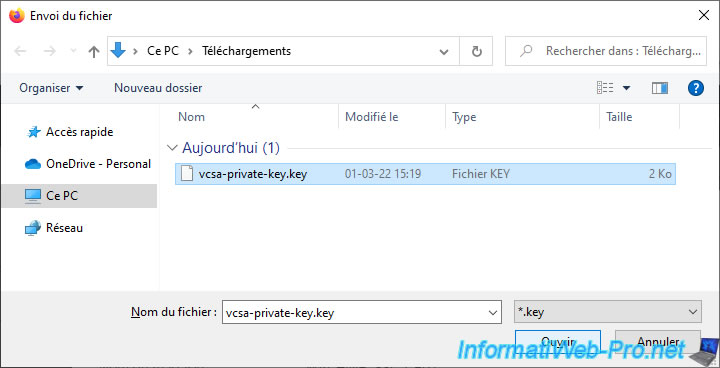
Now that the 2 necessary files have been selected, click Replace.
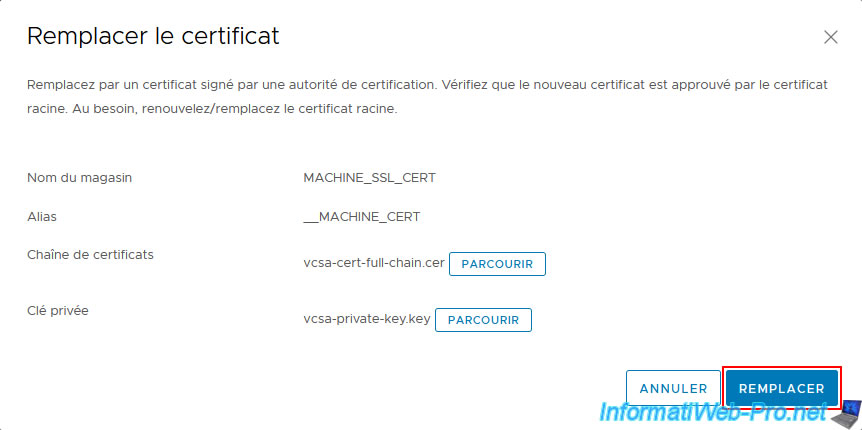
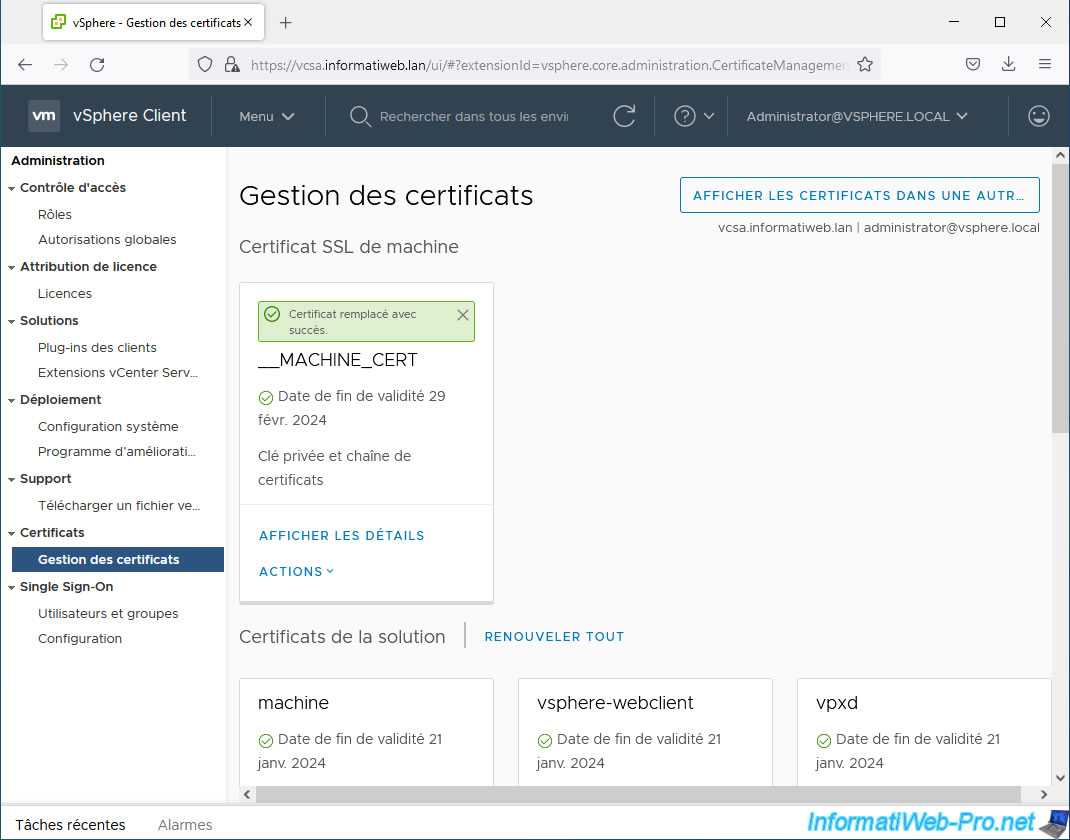
If this goes well, the message "Success, certificate replaced".
Click the "View details" link for the "__MACHINE_CERT" certificate you just replaced.
If that fails, refresh the page and try again. It happens that it fails the first time.
Otherwise, check that the selected files are correct and the formats supported.
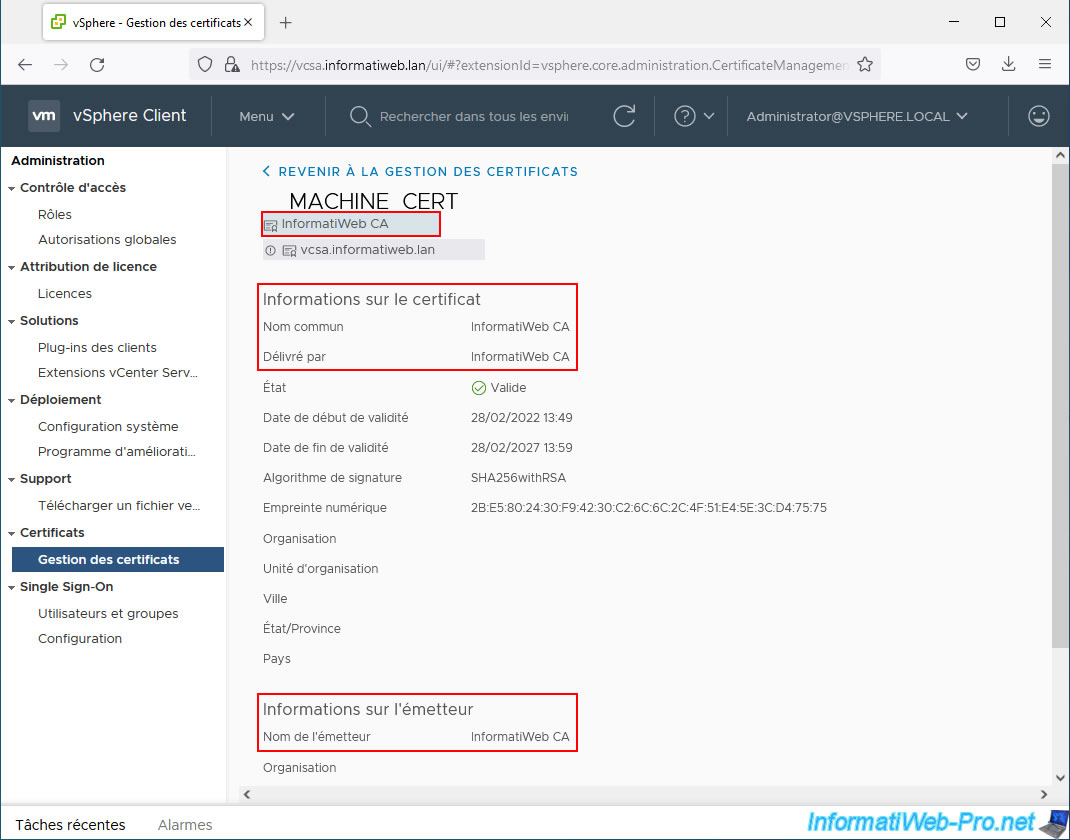
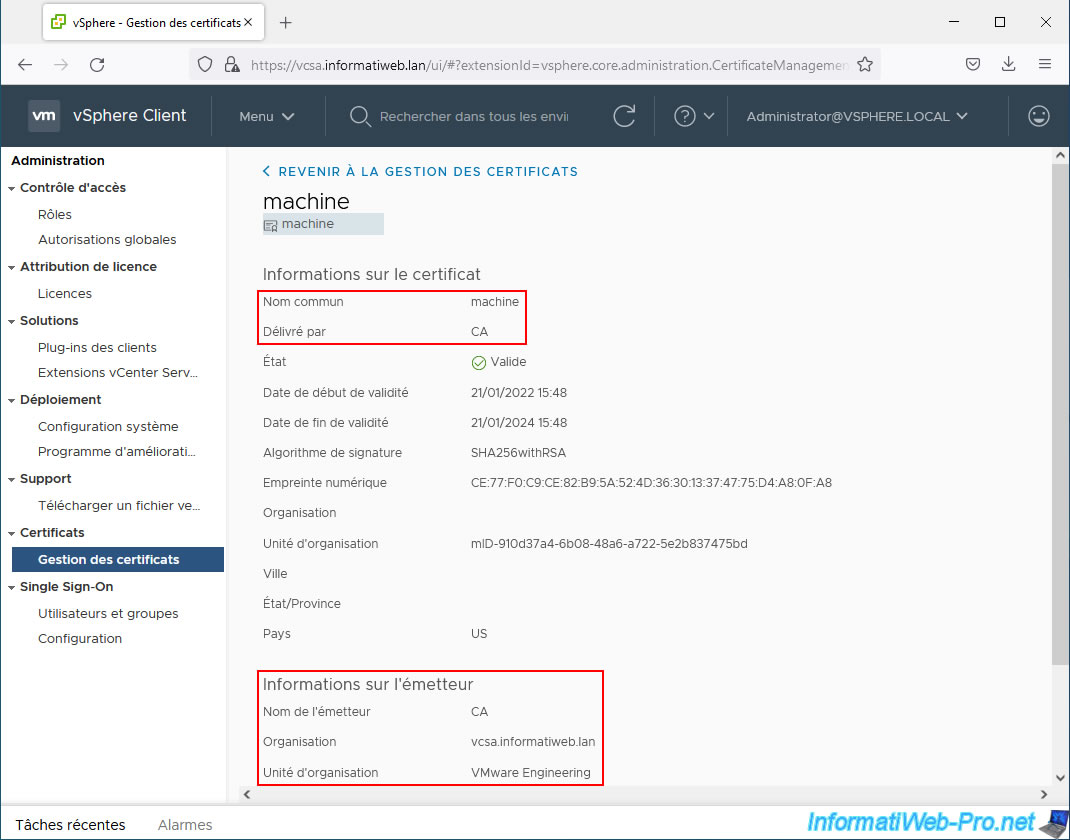
As you can see, the "__MACHINE_CERT" certificate is valid for the domain name of your server (common name: vcsa.informatiweb.lan) and was issued by your own certification authority (issued by: InformatiWeb CA).
You will also see the other information indicated when creating the certificate signing request appear here.
At the bottom of the page, you will also find information about the issuer (your certification authority that issued this certificate).
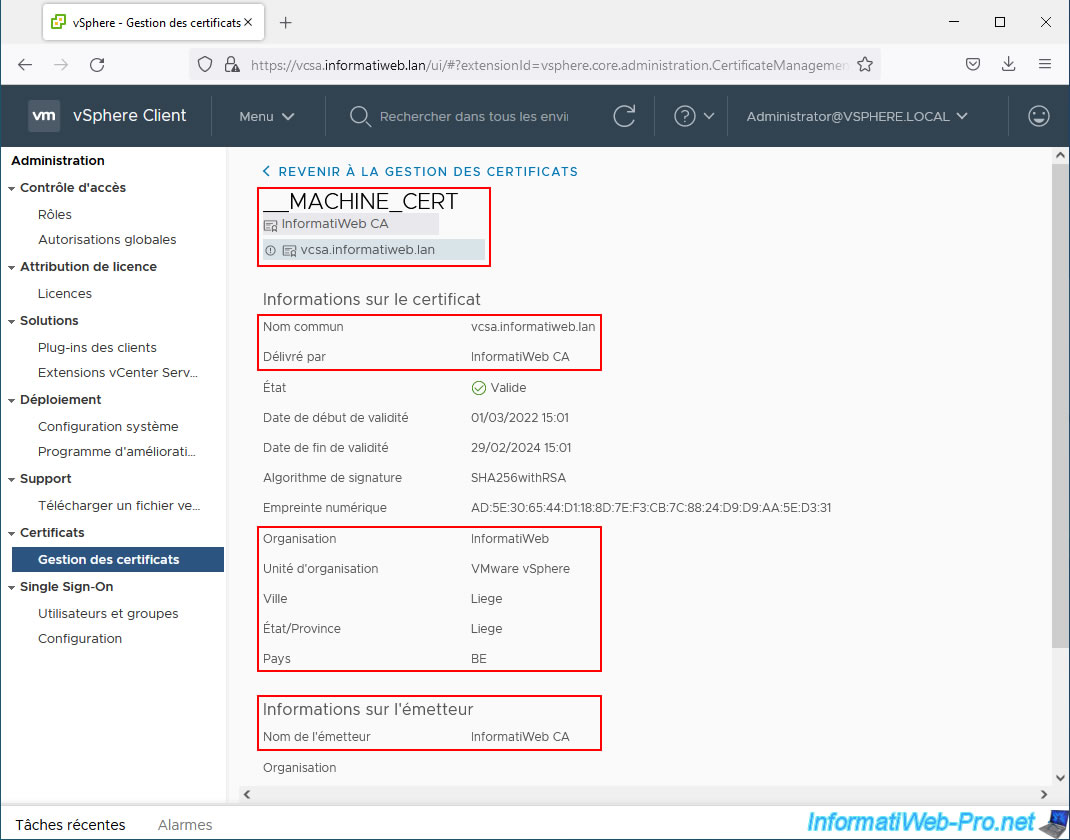
To view your certificate authority's certificate information, you can also click on the name of your authority (just below the "__MACHINE_CERT" title).
Of course, since this is a root CA, the certificate common name and issuer name are the same.
8. Renew SSL certificates used internally by VMware vSphere (optional)
On the "Certificate Management" page, you will also find a "Solution Certificates" section.
As explained in step "2. Managing certificates on VMware vCenter Server (VCSA)" of this tutorial, VMware vSphere uses several certificates:
- one for the web client of your VMware vCenter Server (VCSA) and which corresponds to the "__MACHINE_CERT" certificate that you have just replaced with a valid SSL certificate from your own certification authority.
- 4 other SSL certificates used internally to secure the connection between its different components.
However, these are not accessible from the outside. These 4 certificates are those present in this "Solution Certificates" section.
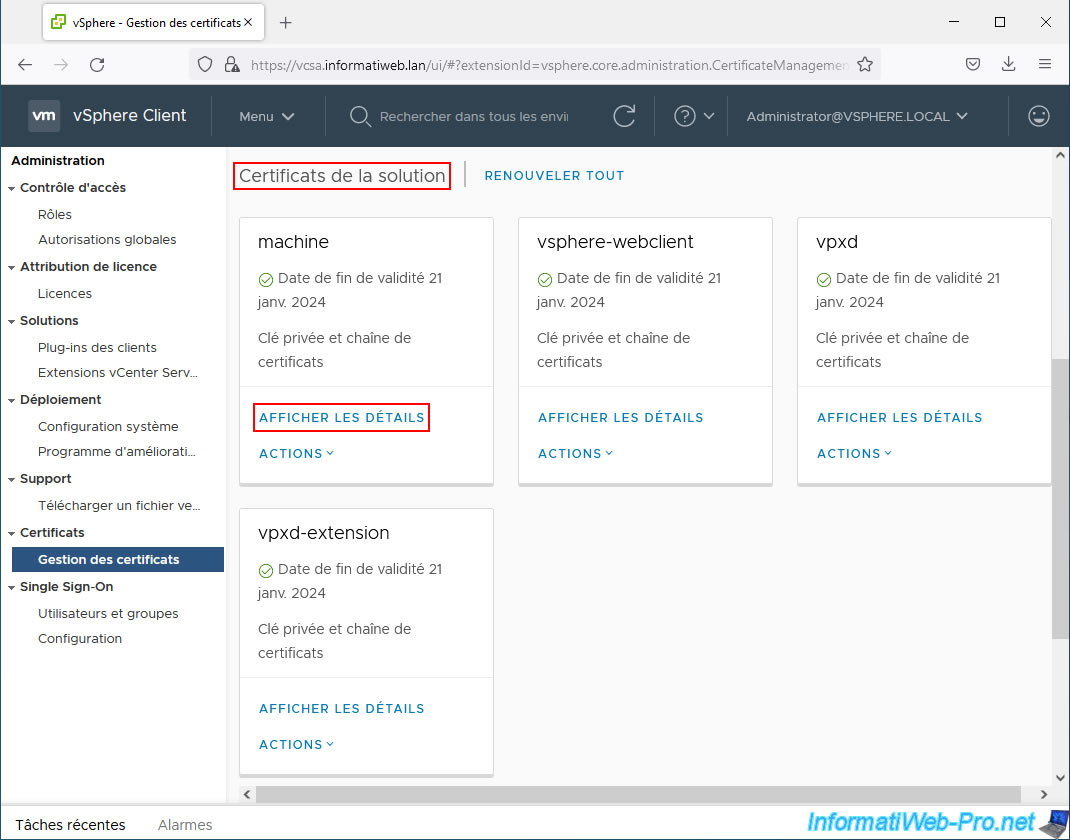
As you can see, VMware vCenter Server Solution (VCSA) certificates are always issued by "CA".
In other words, these certificates are issued by the "VMCA" certification authority described previously and which your VMware vCenter Server (VCSA) trusts by default.
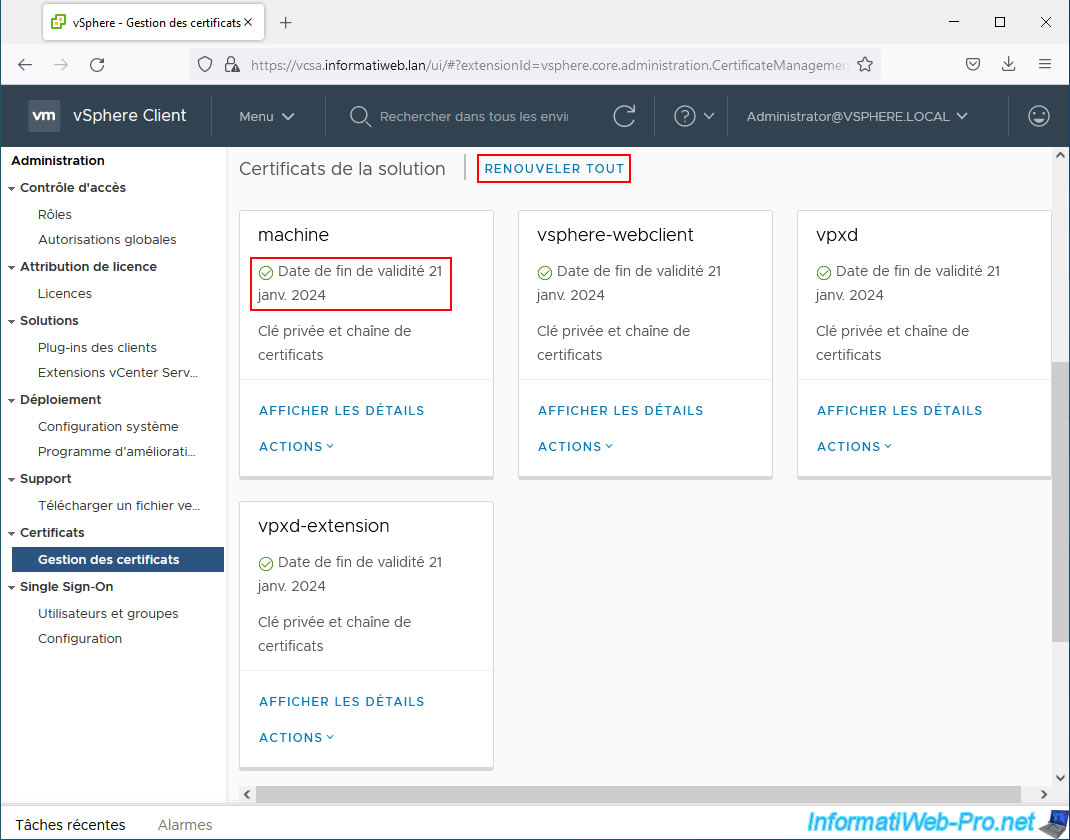
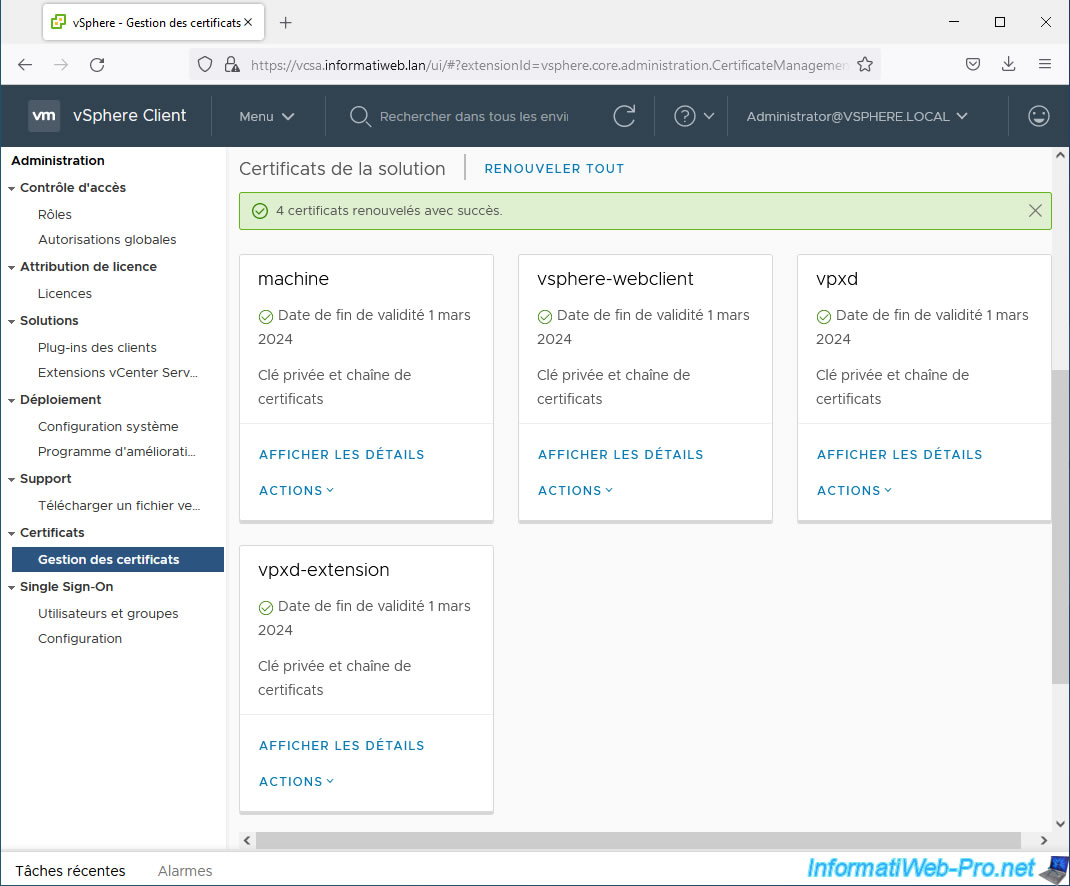
If you wish, you can manually renew these certificates by clicking on the "Renew all" link to extend their expiration date.
Confirm the renewal of these certificates.
As specified here, these certificates will be issued using the currently configured VMCA root certificate.
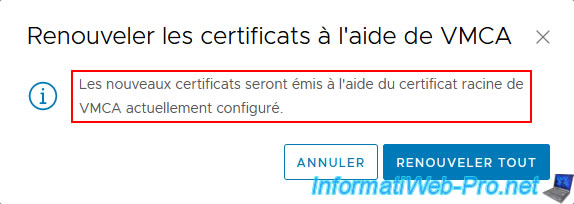
The message "Success, 4 certificates renewed" appears.
9. Export your certificate authority's certificate
So that your client computers and servers can verify the validity and therefore trust the certificates issued by your certification authority, the certificate of your certification authority must be part of their trusted root certification authorities.
To do this, on the server where your certification authority is installed:
- launch an mmc console
- go to menu: File -> Add/Remove Snap-in
- add the component: Certificates
- select: Computer account
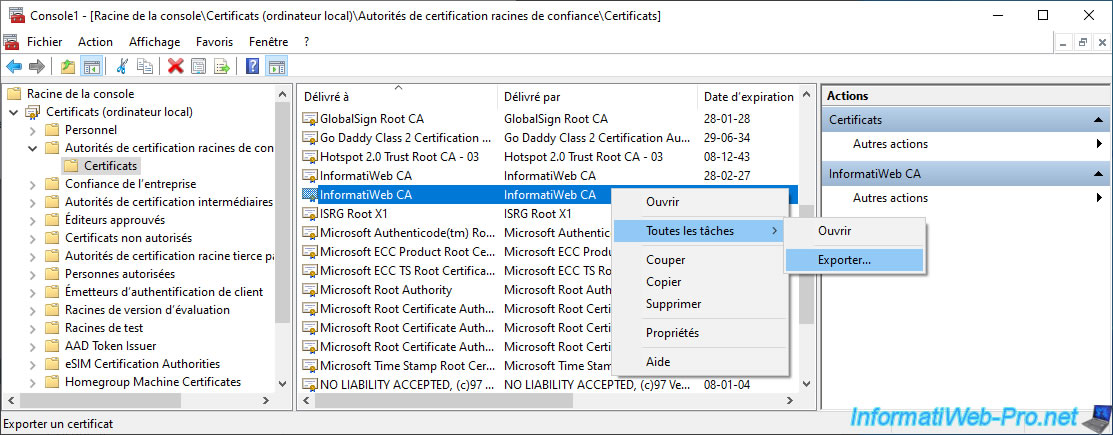
Next, go to the "Trusted Root Certification Authorities -> Certificates" folder and right-click "All Tasks -> Export" on the name of your own root certification authority.
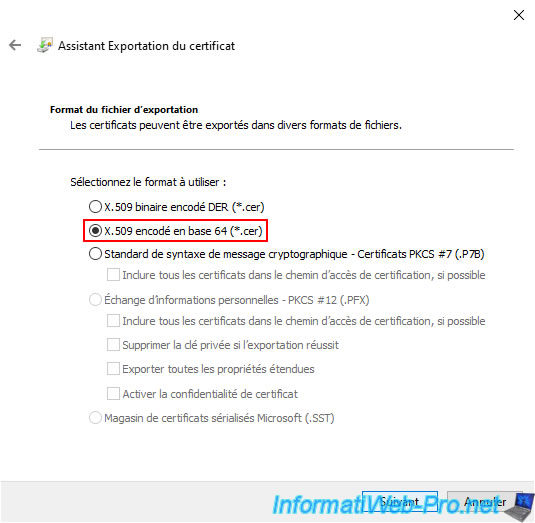
In the Certificate Export Wizard that appears, select "X.509 encoded in base 64 (*.cer)" to obtain the certificate in PEM format. Because you will need it on your computers and servers on Windows (Server), but also on your VMware vCenter Server (VCSA).
Note: only the certificate will be exported since it is in the ".cer" format. The associated private key will therefore not be exported.
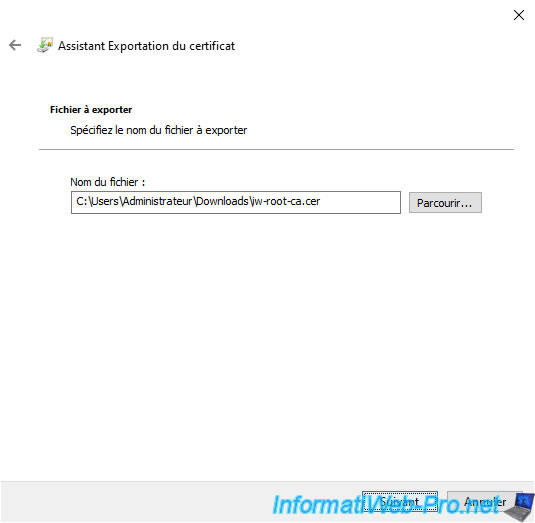
Click the "Browse" button and provide a name for this certificate.
In our case: iw-root-ca.cer.
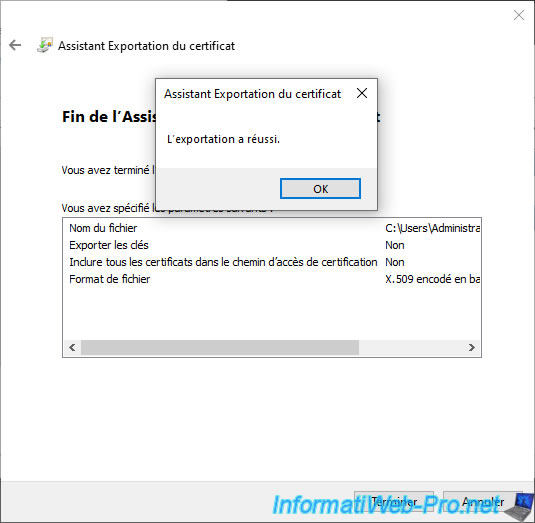
The certificate has been exported.
For your company's computers and servers to consider certificates from your certificate authority as valid, it is important to import your certificate authority's certificate into their "Trusted Root Certification Authorities" store. .
To do this, you can do it manually on the desired computer or server using the "Certificates" component of the MMC console or distribute it to all your computers and servers using group policies.
To do this, refer to the step "Distribute the certificate to the Active Directory clients" of our tutorial "WS 2012 / 2012 R2 - Create an enterprise root CA".
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

No comment