- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 25 December 2024 at 09:56 UTC
-

On VMware vSphere, you have the ability to create virtual standard switches (vSS), as well as virtual distributed switches (vDS).
In this article you will see the advantages, differences and working principle of these virtual distributed switches (vDS).
Warning : the use of virtual distributed switches (vDS) requires an "Enterprise Plus" edition of VMware vSphere.
- Virtual Standard Switches (vSS)
- Virtual Distributed Switches (vDS)
- Feature comparison of Standard (vSS) and Distributed (vDS) Virtual Switches
1. Virtual Standard Switches (vSS)
When you install your first hypervisor on VMware ESXi, a virtual standard switch (vSS) is created by default on it.
This allows, in summary, to make the connection between the virtual network and the physical network, as explained previously in our article: VMware ESXi 6.7 - Basics of network management on VMware ESXi.
When using the web interface of your VMware ESXi hypervisor, this is the only type of virtual switch you can create.
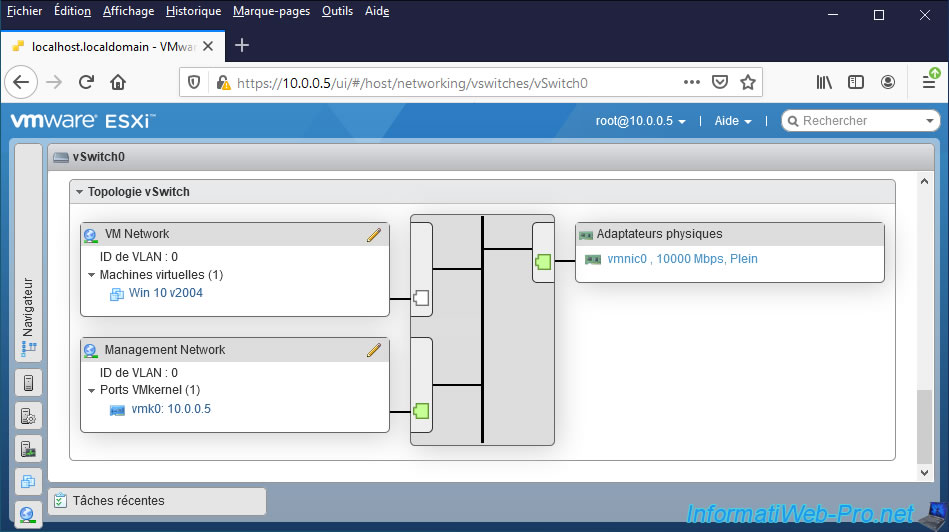
However, as you might expect, when using Virtual Standard Switches (vSS), you must create and configure them on each VMware ESXi hypervisor.
Which can quickly become unmanageable or even a source of error if you want to create a VMware virtual infrastructure with numerous hypervisors on VMware ESXi.
Indeed, if you one day have to modify a parameter on one of the virtual standard switches (vSS) and you forget to make this same modification on the other virtual standard switch (vSS), a problem may arise one day when a virtual machine will be migrated from one VMware ESXi host to another.
2. Virtual Distributed Switches (vDS)
Thanks to the "Enterprise Plus" edition of VMware vSphere, you also have the possibility of creating virtual distributed switches (vDS) from the VMware vCenter Server (VCSA) that you have previously installed and configured.
Indeed, in a professional VMware virtual infrastructure, you no longer manage your VMware ESXi hosts one by one. But rather centrally from the VMware vSphere Client of your VMware vCenter Server (VCSA) to which your VMware ESXi hosts are linked.
The main benefit of a vSphere Distributed Switch (vDS) is that it allows you to centralize the management of your virtual switch, as well as its distributed port groups.
When you create a virtual distributed switch (vDS) from your VMware vCenter Server (VCSA), you also have the ability to monitor and control whether the configuration is correct for all VMware ESXi hosts that you add to this virtual distributed switch (vDS).
Limits:
- each VMware vCenter Server can support up to 128 virtual distributed switches (vDS).
- each virtual distributed switch (vDS) can support up to 500 hosts.
2.1. Architecture of a Virtual Distributed Switch (vDS)
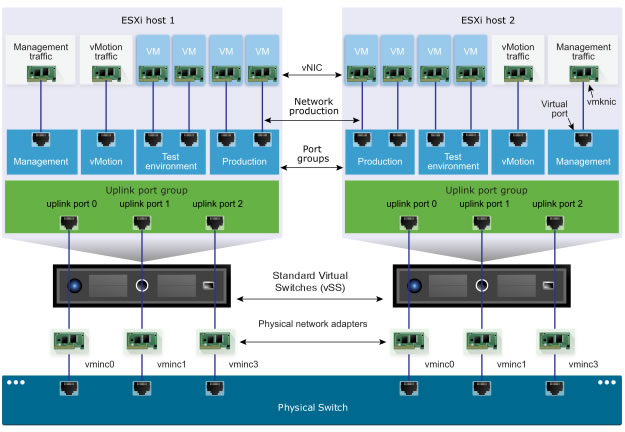
As you can see in the diagram below (created by VMware), a virtual switch is made up of 2 logical sections:
- a management plane: control structure used to configure the corresponding data plane.
- a data plane: this corresponds to the "Host Proxy Switch" which implements the features of switching, tagging and packet filtering, ... on the VMware ESXi hosts that you will add to your virtual distributed switch (vDS).
No matter what type of virtual switch you create, it always has the 2 plans mentioned above.
In the case of a standard virtual switch (vSS), these 2 plans are located in the same place (on your VMware ESXi hypervisor).
You can therefore create and configure this type of switch on each VMware ESXi hypervisor where you want to use it.
Which means that each virtual standard switch (vSS) is independent and they must be configured and updated separately.
In the case of a virtual distributed switch (vDS), you can see that the management plane is on your VMware vCenter Server (VCSA) since it is on this central server that you will configure your distributed virtual switch (vDS).
The associated data plane (which corresponds to "Host Proxy Switch") will be created on each VMware ESXi host added to your distributed virtual switch. Then, the host proxy switch of each VMware ESXi host will be updated automatically from the virtual distributed switch (vDS) configured on your VMware vCenter Server (VCSA).
Note that because the data plane is defined at each VMware ESXi host and is simply updated automatically from the management plane configured on the VMware vCenter Server (VCSA), an outage or outage of the VMware vCenter Server (VCSA) server will not pose any problem for the correct functioning of the network on your VMware ESXi hosts.
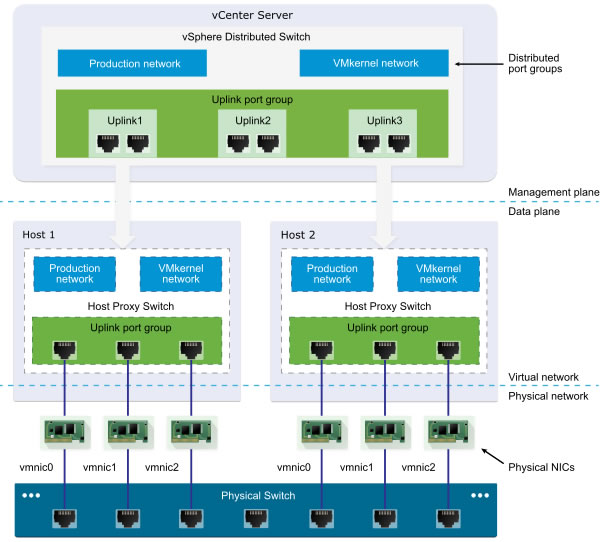
2.2. Uplink port groups (physical NICs)
Virtual Distributed Switches (vDS) have an abstraction layer to configure the proper networking of multiple hosts by taking into account all of their physical network cards, virtual machines, and VMkernel adapters (VMkernel interfaces).
When you used virtual standard switches (vSS) on a VMware ESXi host, you had to assign physical network adapters (vmnicX) from the affected VMware ESXi host for physical network access.
From the moment you use a virtual distributed switch (vDS), a host proxy switch is created on each desired VMware ESXi host (as explained previously).
Which involves the use of uplink port groups (or "dvUplink port groups") which allows grouping the desired physical network cards from different hosts that are connected to the same physical network.
By default, when creating a virtual distributed switch (vDS), an uplink port group is already created.
In the case of a virtual distributed switch (vDS), an uplink is a pattern that you will use to map the physical NICs of other VMware ESXi hosts that are connected to the same physical network.
Thus, migrating a virtual machine from one VMware ESXi host to another with the same virtual distributed switch (vDS) will not pose any network problems since the virtual machine will still have access to the same physical network via a physical network card of the destination host.
With these uplink port groups, the load balancing (NIC teaming) and failover policies that you define for your uplinks can be automatically applied on the physical network cards (vmnicX) of the host proxy switches present on your different VMware ESXi hosts.
2.3. Distributed port group (virtual networks for VMs)
As with standard virtual switches (vSS), you will find the notion of port group on your distributed virtual switch (vDS).
Although these are now called distributed port groups since you create them once on your virtual distributed switch (vDS) on your VMware vCenter Server (VCSA) and the port groups will then be created and automatically updated on your different VMware ESXi hosts.
These distributed port groups again allow you to manage the network traffic of your virtual machines and VMkernel adapters (VMkernel interfaces) and again have a network label.
But, since you are on VMware vCenter Server (VCSA), it is necessary that this network label be unique per data center (DC).
For the available parameters, you will find the network card association (NIC teaming) and failover strategies, the security options (promiscuity, ...), the notion of VLAN, ...
Note that the number of distributed ports of host proxy switches varies dynamically to optimize resource utilization on your VMware ESXi hosts. The limit on this number of ports varies depending on the maximum number of virtual machines your VMware ESXi host can handle.
2.4. Managing network traffic on a Virtual Distributed Switch (vDS)
As you can see in the diagram below, there are 2 VMware ESXi hosts with 3 physical NICs per host.
In the example below, you can see that:
- There is a single virtual distributed switch (vDS) used by 2 VMware ESXi hosts.
- Each host has a VMkernel interface (default: for management traffic) which is connected to the distributed port group "VMkernel Network".
- the virtual machines on these hosts are connected to the "VM Network" distributed port group.
- There is an uplink port group with 3 uplinks.
- Each host has 3 NICs (vmnic0, vmnic1 and vmnic2) which are respectively assigned as uplink 1, 2 and 3 in the uplink port group.
The important thing is that all physical network cards assigned to an uplink are connected on the same physical network.
Which means that if you configure the "VM Network" distributed port group to use uplinks 1 and 2, your virtual machines' network traffic will always go out through the physical NIC "vmnic0" or "vmnic1" of one of your VMware ESXi hosts.
Network traffic from your virtual machines and VMkernel adapters (vmkX) to the physical network will therefore simply depend on the NIC teaming and load balancing policies configured on your distributed port groups ("VM Network" and "VMkernel Network" in the example below).
This will also depend on the port numbers allocated to the different virtual ports in your distributed port groups and the ports in your uplink port group.
As you can see, when you create a distributed virtual switch, it first allocates ports to your distributed port groups ("VM Network" and "VMkernel Network" in the example below), then continuous dialing for your hosts' uplinks in the order in which you add your hosts to this switch.
In the example below, you can see that this virtual distributed switch (vDS) has 10 ports numbered 1 to 10.
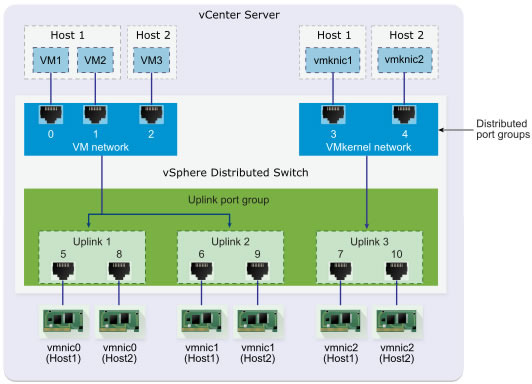
On each of your hosts, network traffic from your virtual machines and VMkernel adapters (VMkernel interfaces) will use ports allocated by your virtual distributed switch (vDS) to access the physical network (if necessary).
In the example below, you only see a schema of the host proxy switch automatically created on host 1 from the virtual distributed switch (vDS) configured on your VMware vCenter Server.
In this example, a packet sent by VM2 will first pass through port 1 allocated to the "VM Network" distributed port group.
Then, given that uplinks 1 and 2 are assigned to the distributed port group "VM Network", the packet will be able to pass through port 5 or 6 and therefore respectively through the network card "vmnic0" or "vmnic1" of this host 1.
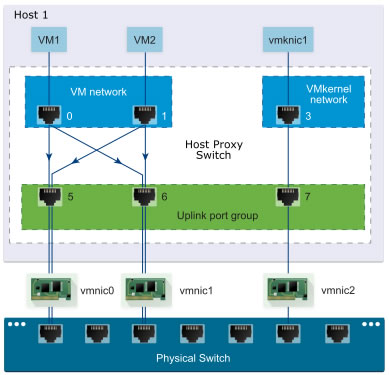
To learn more about virtual distributed switch (vDS) architecture, visit the "vSphere Distributed Switch Architecture - VMware Docs" page in the official VMware documentation where the diagrams used in our article are taken.
3. Feature comparison of Standard (vSS) and Distributed (vDS) Virtual Switches
3.1. Features common to Virtual Standard (vSS) and Distributed (vDS) Switches
All Virtual Standard Switch (vSS) features below are also available on Virtual Distributed Switches (vDS):
- Level 2 switch (L2): virtual switches support level 2 frames ("data link" layer = "layer 2" of the OSI model).
- VLAN segmentation: you can use VLANs to isolate multiple networks on the same virtual switch.
This is possible thanks to the "VLAN ID" option available in the port group settings (on vSS) or distributed port groups (on vDS). - IPv6 support: virtual switches support TCP/IP version 6 in addition to IPv4.
- 802.1Q tagging: the 802.1Q standard is an IEEE standard which allows you to modify a network frame to be able to use several VLANs on the same physical network link.
- NIC teaming: allows multiple NICs to be teamed together as an uplink to benefit from load balancing and/or fault tolerance.
- Outbound traffic shaping: allows you to limit bandwidth usage (for outbound traffic only).
3.2. Additional Virtual Distributed Switch (vDS) features
Virtual Distributed Switches (vDS) have the features mentioned above, as well as those below:
- Inbound traffic shaping: allows you to limit bandwidth usage (for inbound traffic only).
Which means that on a vDS, you will be able to limit the bandwidth for inbound and outbound traffic. - Virtual Machine Network Port Blocking: allows you to block network traffic on certain ports and specify conditions for this blocking. Which can, for example, make it easy to block ping (ICMP) for security reasons.
- Private VLANs (pVLAN): allows you to create sub-VLANs within an existing VLAN. In addition, they can be configured in different ways so that virtual machines that are members of the same private VLAN can communicate with each other or not.
- Load-based association: a policy to best distribute the load based on network traffic to prevent one uplink (dvUplink) from being saturated while another is currently down.
However, this strategy is not used by default. It's up to you to choose it if you wish. - Datacenter-level management: means you can create and manage your virtual distributed switches (vDS) from the VMware vSphere Client on your VMware vCenter Server (VCSA) to manage the network of your VMware ESXi hosts.
- vSphere vMotion migration over a network: allows you to also migrate the network port state of the virtual machine so that the port statistics for a virtual machine remain consistent even when migrating the virtual machine.
This is also a prerequisite for stateful monitoring that can be configured on one of the firewalls. - Policy Settings by Port: allows you to modify a policy for a specific port.
- Port Status Monitoring: allows you to monitor ports separately.
- NetFlow: protocol developed by Cisco to collect data regarding network traffic to see what is happening there via a NetFlow collector.
- Port Mirroring: sends a copy of traffic from one network port to another network port.
This makes it possible to monitor the network traffic of a virtual machine via another machine using a sniffer, for example.
With Virtual Distributed Switches (vDS), you will be able to:
- configure virtual switches, distributed port groups, and all other network settings related to these virtual distributed switches (vDS) centrally.
- check the network configuration between your VMware vSphere virtual infrastructure and your physical network centrally.
So if a VLAN is correctly configured for a NIC on one of your VMware ESXI hosts, but not on the other hosts, you will know immediately. - manage network adapter teaming (network link aggregation) via Link Aggregation Control Protocol (LACP).
Virtual Distributed Switches (vDS) also make it easier for you to monitor and troubleshoot your network issues with:
- to the RSPAN and ERSPAN protocols: the RSPAN and ERSPAN protocols are protocols derived from the SPAN protocol.
- The Switch Port Analyzer (SPAN) protocol is a network traffic analysis protocol originally available on Cisco switches.
The SPAN protocol allows you to copy traffic from one or more ports of a switch to send it to one or more other ports of the same switch. - The RSPAN (Remote SPAN) protocol allows network traffic to be copied from one or more ports of one or more switches to send it to another switch which would be dedicated to analyzing network traffic, for example.
This is done on layer 2. - The ERSPAN (Encapsulated Remote SPAN) protocol encapsulates the RSPAN protocol explained previously and this time allows the copied network traffic to be sent to a machine with an IP address.
In this case, this is done at layer 3, hence the data sent can be routed to a device with an IP address.
- The Switch Port Analyzer (SPAN) protocol is a network traffic analysis protocol originally available on Cisco switches.
- to the IPFIX protocol (IP Flow Information Export) which is an IETF standard which is derived from Netflow (which is also supported).
These technologies make it easy to collect data about network traffic passing over your virtual distributed switch (vDS). Which makes it easier to monitor and troubleshoot your network issues or application issues. - SNMPv3: SNMPv3 (Simple Network Management Protocol) is a protocol for monitoring IP network devices.
- backing up and restoring a previously backed up network configuration.
So, in the event of a problem following incorrect handling, you will simply need to restore this backup. - Network-based Coredump (Netdump): a protocol running over UDP used to transport images from the kernel's central memory to a server.
- CDP: Cisco Discovery Protocol (CDP) allows the vSphere administrator to obtain information about the Cisco physical switch (if applicable) from the VMware vCenter Server (VCSA).
But, this can also be true the other way around. This will allow the Cisco switch administrator to obtain information regarding the vSS or vDS virtual switch. - LLDP: Link Layer Discovery Protocol (LLDP) allows vSphere administrators to know which port on a physical switch a specific virtual distributed switch (vDS) is connected to.
This also allows the vSphere administrator to obtain information about the physical switch, such as: the name of the switch, its description, the version of iOS (the operating system for Cisco switches), ...
This is convenient if you want to use VLANs, because you can contact the administrator of the physical switch and ask them to configure the desired VLAN for this or that port of the physical switch.
Finally, virtual distributed switches (vDS) also allow you to benefit from advanced vSphere networking features:
- VMware vSphere Network I/O Control (NIOC): allows you to manage the allocation of bandwidth to your virtual machines by defining shares, limits and/or bandwidth reservations.
So, if your configuration is correct, a virtual machine will not be able to saturate your host's bandwidth. This ensures the availability of your various services hosted on your virtual VMware infrastructure. - maintaining the network state of a virtual machine even if it is migrated from one VMware ESXi host to another.
This makes it easier to monitor them, as well as configure any firewalls since its network state will be preserved. - SR-IOV support: SR-IOV (Single Root I/O Virtualization) support allows a virtual machine to directly use a physical network card. This reduces latency at the network level since your virtual machine will be able to directly access the physical network without going through the VMkernel.
- Bridge Protocol Data Unit (BPDU) packet filtering: prevents virtual machines from sending BPDU packets to the physical switch. This prevents a virtual machine from being able to bring down your physical switch following the creation of a network loop.
Sources :
- VMware Load-Based Teaming (LBT) Performance - VMware VROOM! Performance Blog
- Private VLAN (PVLAN) on vNetwork Distributed Switch - Concept Overview (1010691) - VMware KB
- VMware® vNetwork Distributed Switch: Migration and Configuration - VMware white paper (page 4)
- vSphere Distributed Switch - VMware
- Understanding SPAN,RSPAN,and ERSPAN - Cisco Community
- Enable Cisco Discovery Protocol on a vSphere Distributed Switch - VMware Docs
- Enable Link Layer Discovery Protocol on a vSphere Distributed Switch - VMware Docs
Share this tutorial
To see also
-

VMware 6/22/2022
VMware ESXi 6.7 - Secure the server with a SSL certificate
-
VMware 11/22/2024
VMware vSphere 6.7 - Migrate VMs via SvMotion (migrate VM storage)
-

VMware 7/3/2024
VMware vSphere 6.7 - Scheduled tasks
-

VMware 6/28/2024
VMware vSphere 6.7 - Tasks and events

You must be logged in to post a comment