Secure access to VMware vCenter Server (VCSA) over HTTPS on VMware vSphere 6.7
- VMware
- 25 October 2024 at 11:03 UTC
-

- 5/7
10. Add your certificate authority's certificate to your vCenter Server's trusted root certificates (VCSA)
For your VMware vCenter Server to continue to function correctly with your new SSL certificate, the certificate of your certification authority (from which the new "__MACHINE_CERT" certificate comes) must be in its trusted root certificates.
To do this, next to the title "Trusted Root Certificates", click: Add.
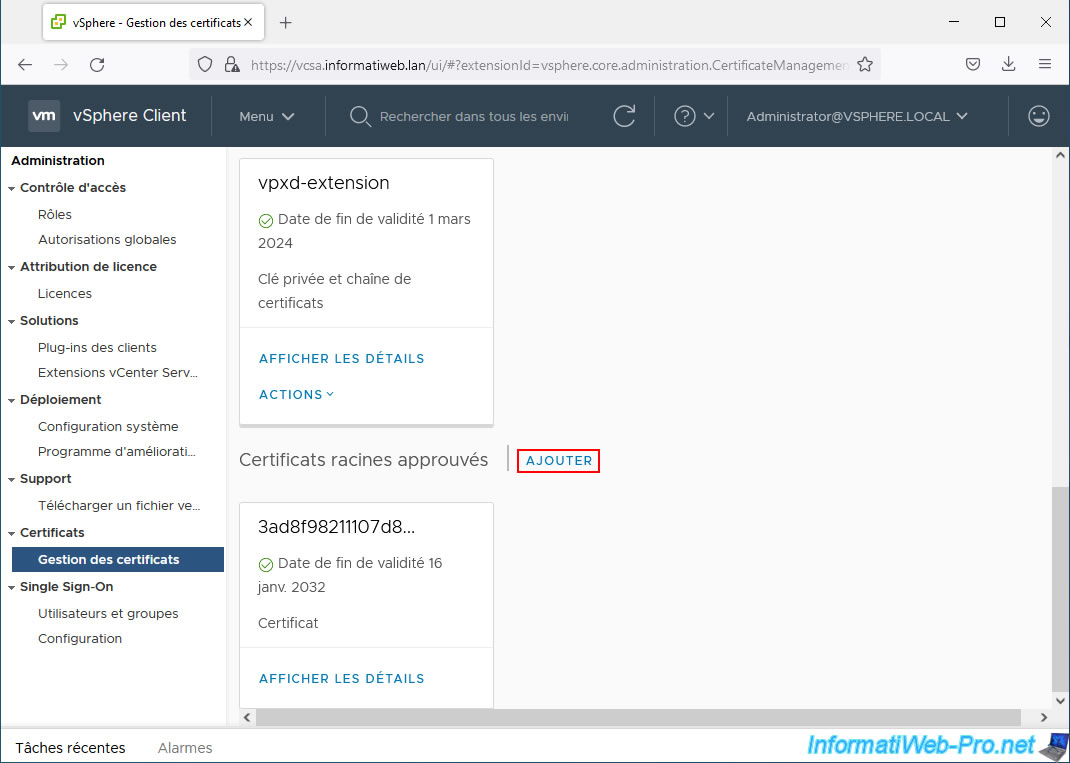
In the "Add Trusted Root Certificate" window, click the "Browse" button.
Important : in our case, our "__MACHINE_CERT" certificate comes from a root certification authority.
So there is only one certificate. However, if it comes from a secondary (or subordinate) certification authority, you will need to select a file containing the entire chain of trust up to the corresponding root certification authority.

In our case, we select the certificate of our certification authority "iw-root-ca.cer" exported previously.
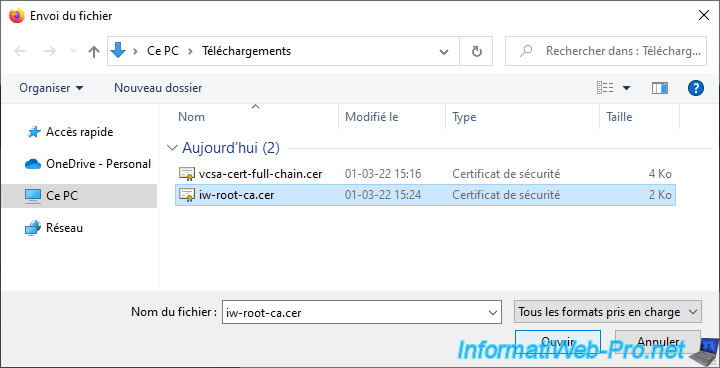
Once the certificate is selected, click Add.

The added root certificate appears in the "Trusted Root Certificates" section of your VMware vCenter Server (VCSA).
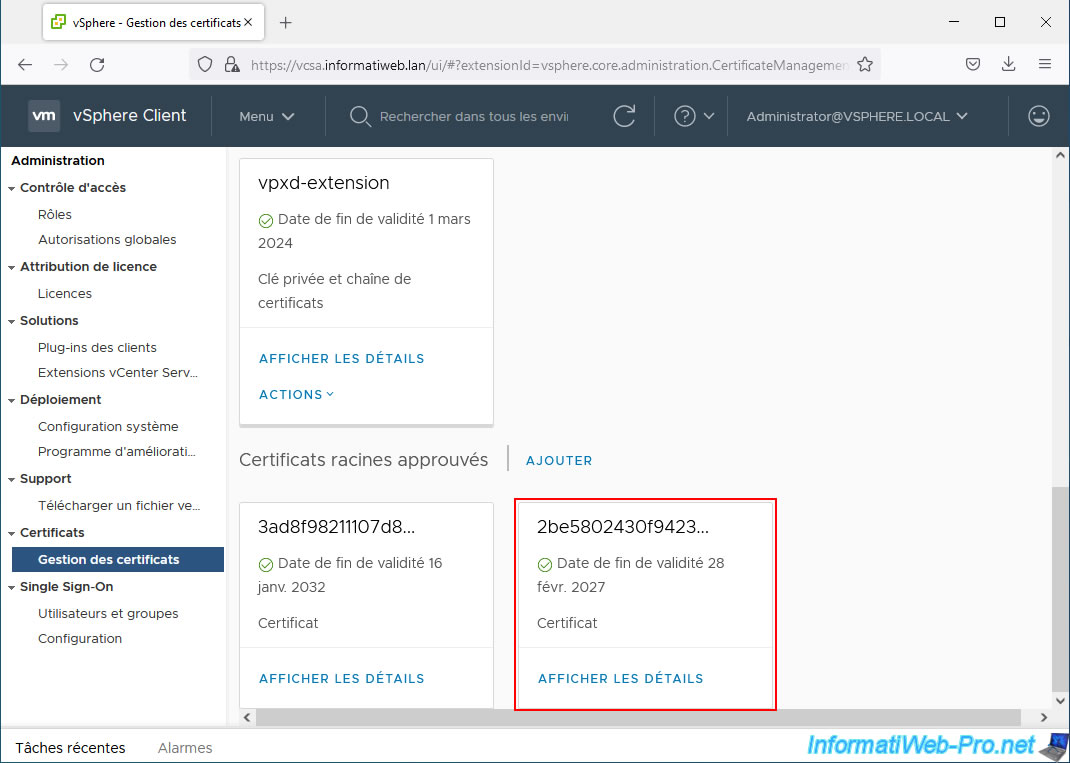
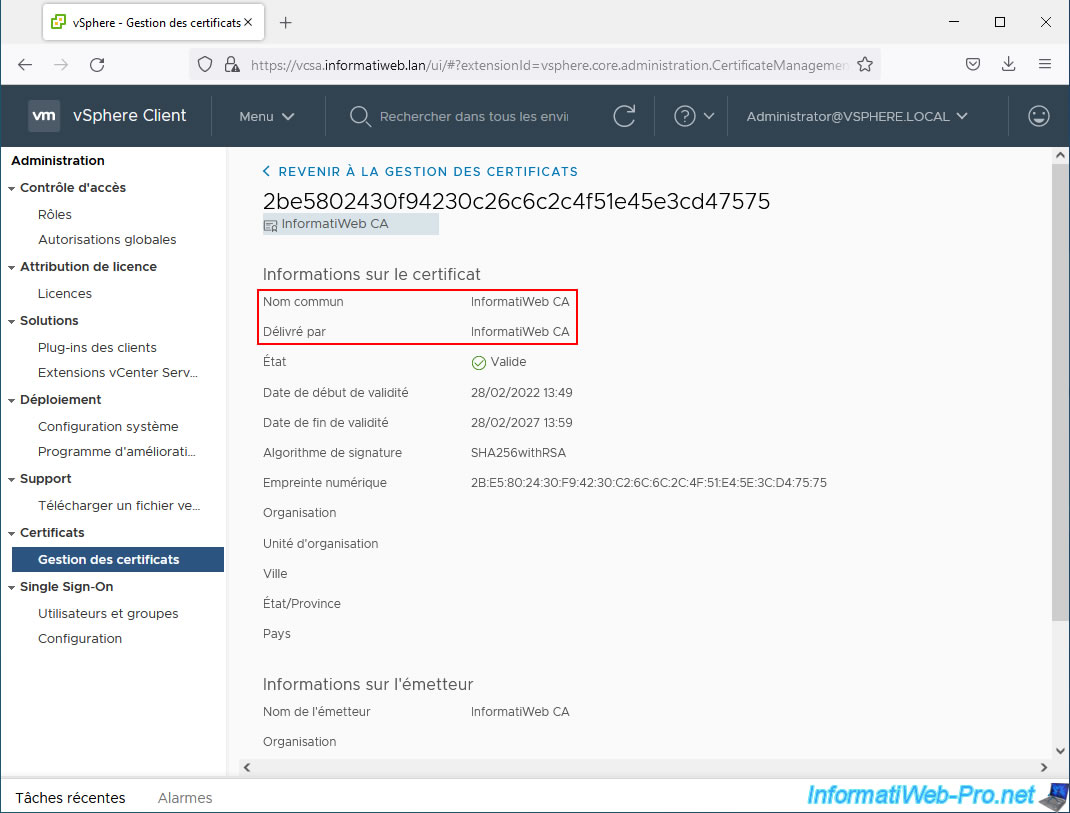
If you click on the "View details" link for the added certificate, you will see the name of your certification authority appear for the "Common name" and "Issued by" lines.
11. New SSL certificate not taken into account
If you looked at the icon in the address bar of your web browser, you must have noticed that it was telling you that there was still a security problem with your VMware vCenter Server (VCSA) .
Indeed, with Mozilla Firefox (for example), you will see that the status "Insecure connection" appears.
Click on this status displayed in red.
Then click: Remove exception.
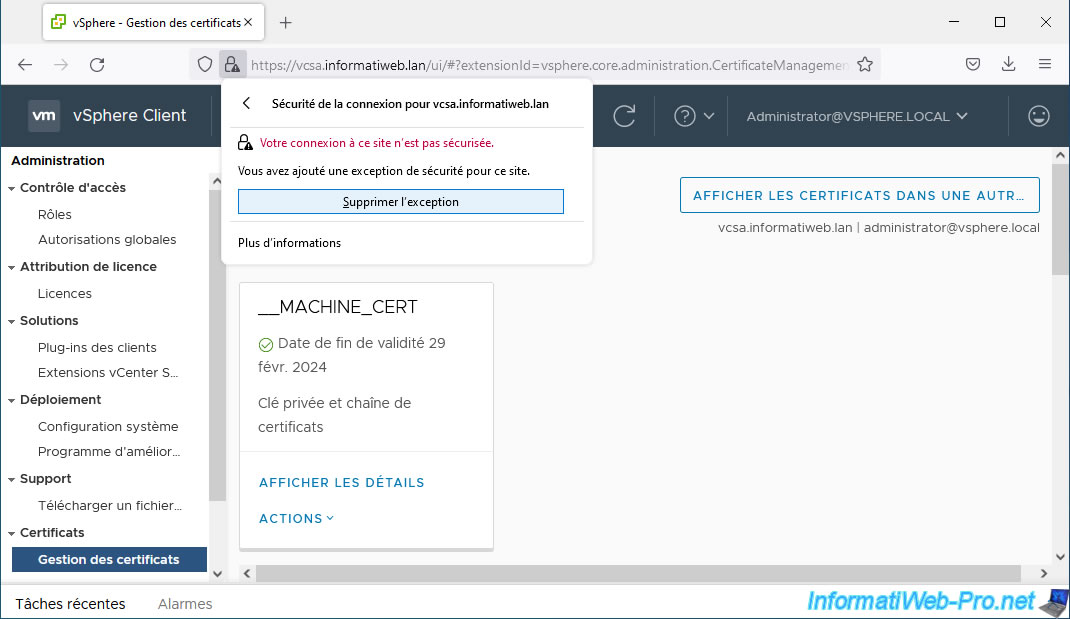
As you can see, your web browser (Firefox in this case) tells you that the certificate issuer is unknown and that the associated error code is: SEC_ERROR_UNKNOWN_ISSUER.
Click the "View Certificate" link to see why.
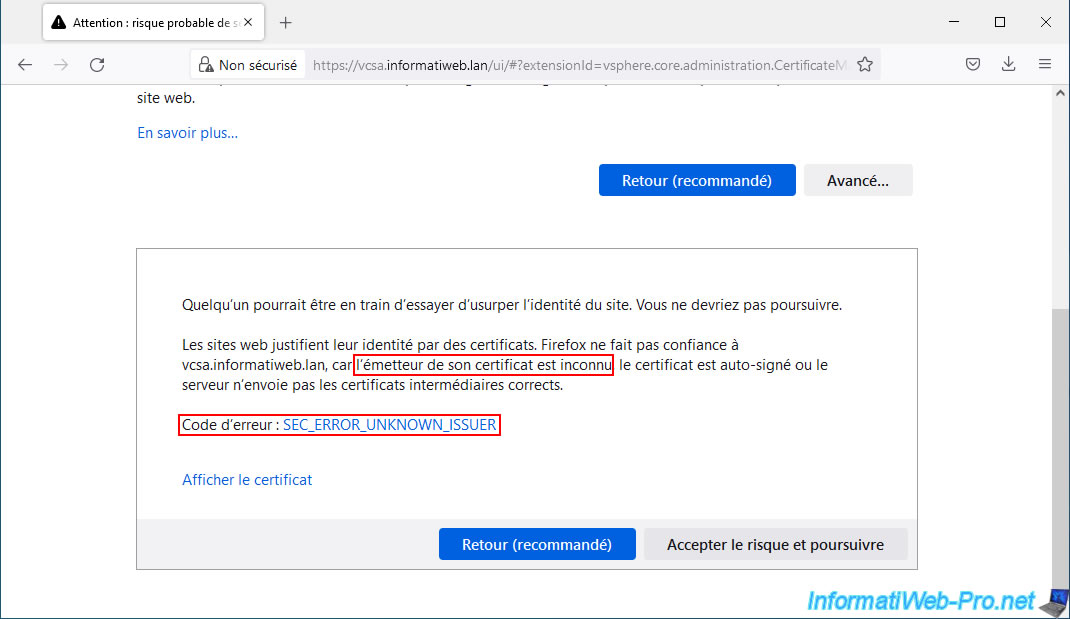
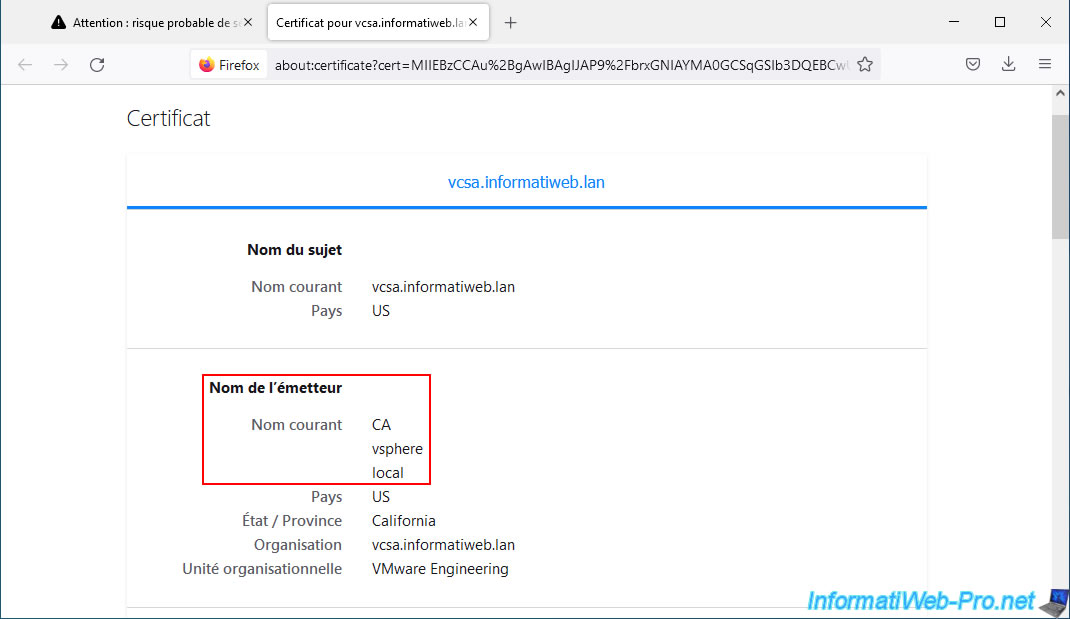
As you can see, your VMware vCenter Server (VCSA) still uses the previous certificate that was issued by VMCA (hence the common name of the issuer "CA vsphere local" which is displayed here).
12. Update the SSL certificate used by VMware vCenter Server (VCSA)
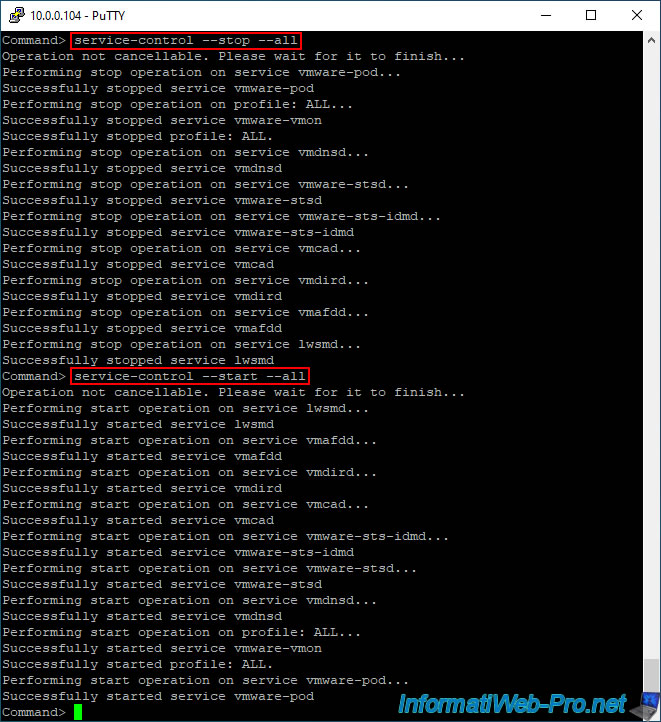
For your VMware vCenter Server (VCSA) server to use your new SSL certificate signed by your own certificate authority, you must restart all services on your server.
Note that restarting all its services is faster than completely restarting your VCSA virtual machine.
To do this, connect via SSH to your VMware vCenter Server (VCSA) using PuTTY (for example) and type the commands:
Bash
service-control --stop --all service-control --start --all
Important : make sure you are in your VCSA appliance's shell (the prefix displayed should be "Command>") and not in its BASH Linux shell (the prefix displayed would be "root@vcsa ... #").
Note: it will take a few minutes to restart all services on your server.
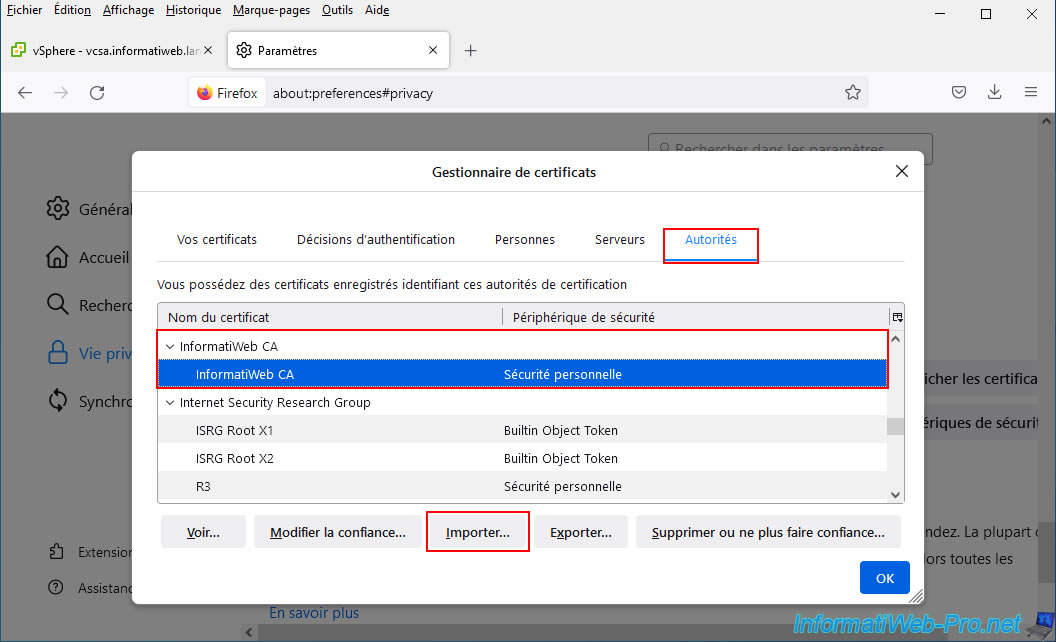
If you use Mozilla Firefox as your web browser, make sure you have imported your certificate authority's certificate into its certificate manager.
To do this, go to: Tools -> Settings -> Privacy & Security -> "Certificates" section -> "View Certificates" button.
Then click on the "Import" button
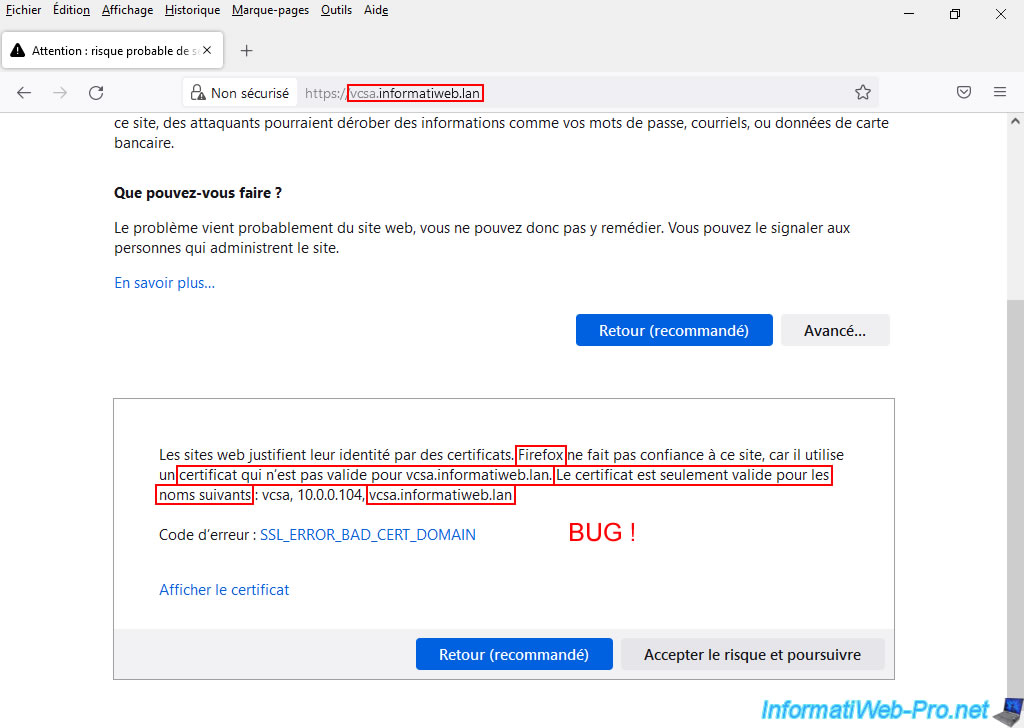
In a particular case, it happens that Mozilla Firefox tells you that your certificate is not valid for the domain name indicated in its address bar, because it is only valid for this same domain name.
Which is a very strange error. Here is the proof below.
Plain Text
... Firefox does not trust this site because it uses a certificate that is not valid for vcsa.informatiweb.lan. The certificate is only valid for the following names: vcsa, 10.0.0.104, vcsa.informatiweb.lan. Error code: SSL_ERROR_BAD_CERT_DOMAIN.
In reality, to get around this problem, simply regenerate this certificate by indicating at least the fully qualified domain name ("vcsa.informatiweb.lan" in this case) first for the list of valid DNS domain names for this certificate.
In the certificate signing request that you can generate from your VMware vCenter Server (VCSA), this corresponds to the "Subject Alternative Name (Optional)" field.
If you followed our tutorial correctly, you should not encounter this problem. Indeed, we told you to indicate the full domain name first, then to indicate the short name and the IP address (optional) after.
To get around this problem in our case, we therefore indicated "vcsa.informatiweb.lan, vcsa, 10.0.0.104" in the "Subject Alternative Name (Optional)" field of the "Generate Certificate Signing Request (CSR)" form.
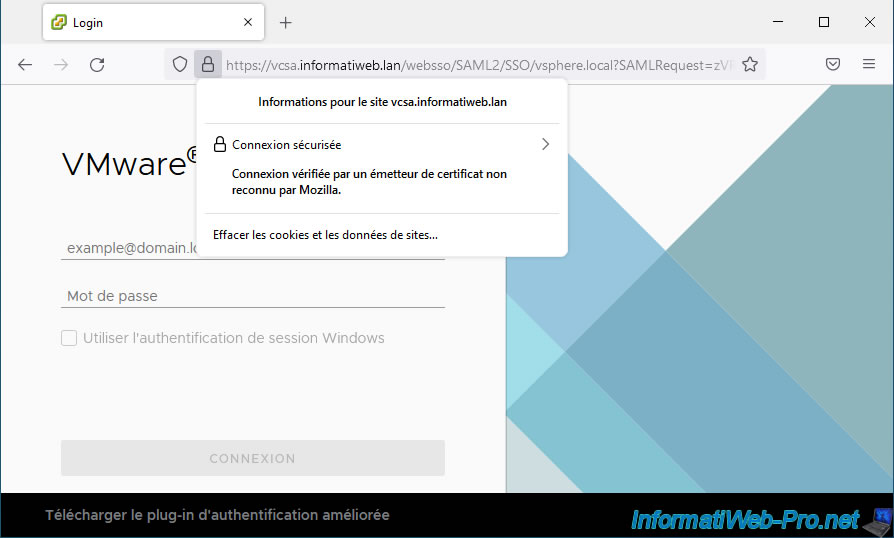
In our case, given that the fully qualified domain name (vcsa.informatiweb.lan) of our VMware vCenter Server (VCSA) is listed first in the list of alternative DNS names for which this certificate must also be valid, this problem does not happen.
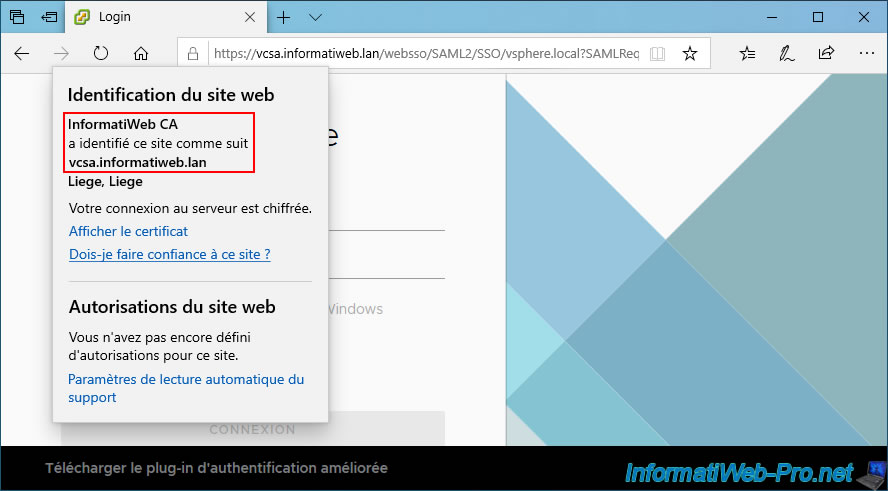
If you click on the padlock icon in the address bar of Mozilla Firefox, you will see that this web browser tells you that the connection is secure.
Note: the message "Connection verified by an unrecognized certificate issuer" indicates that this certificate is valid in your case, but that it was not signed by a certification authority recognized by default by Mozilla Firefox (worldwide).
This happens when you use a certificate signed by your own certificate authority whose root certificate you have imported into the Mozilla Firefox certificate manager.
If you click on the "Secure Connection" status displayed, you will see that the SSL certificate used by this site has been verified by your certificate authority.
Once again, Mozilla tells you that it does not recognize the certificate issuer since it is yours and not a real certificate authority recognized on the Internet.
Plain Text
Mozilla does not recognize this certificate issuer. It may have been added from your operating system or by an administrator.
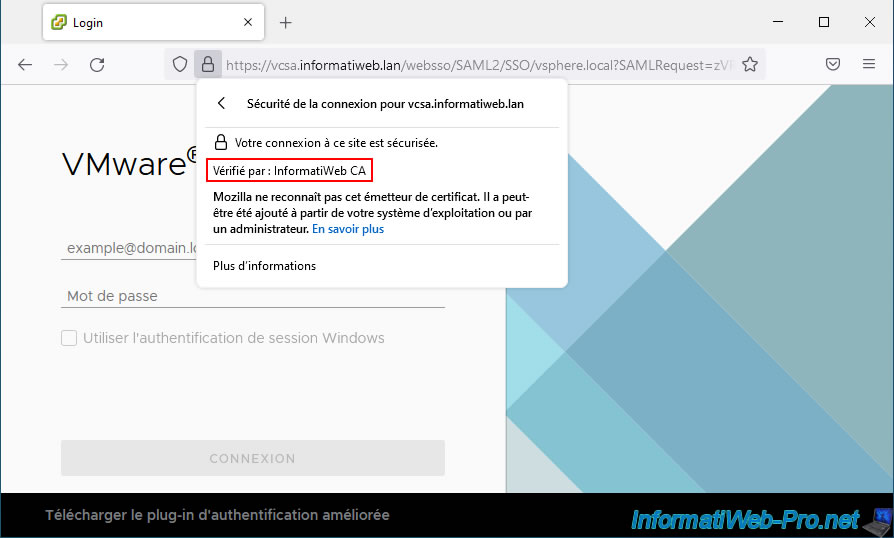
If you click "More information", a "Page information - https://..." window will appear with a "View certificate" button.
Click this button.
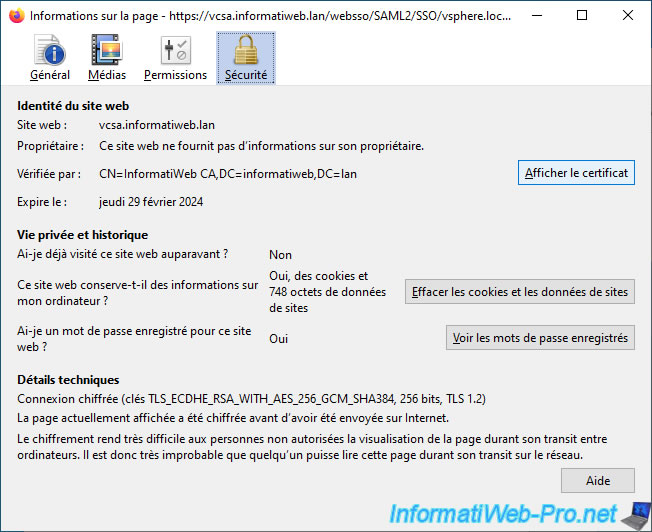
As you can see, the SSL certificate used is now the one issued by your own certificate authority.
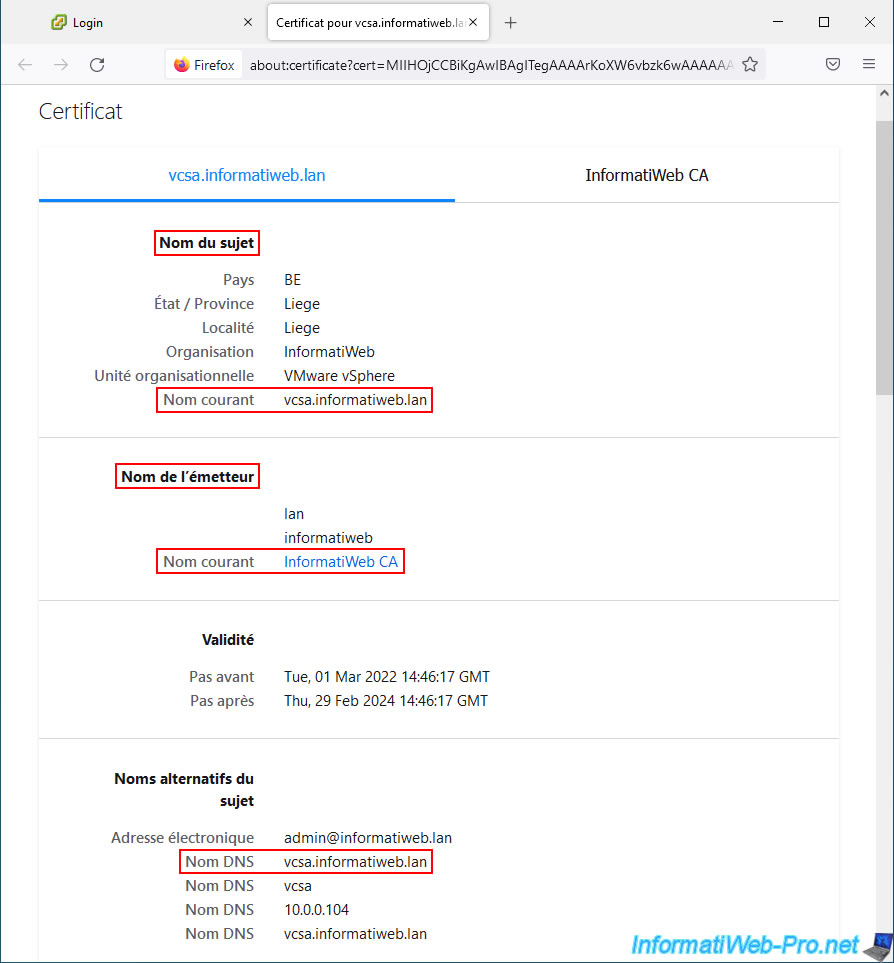
If you click on the 2nd tab, you will be able to obtain information concerning the issuer (the certification authority) which issued this certificate.
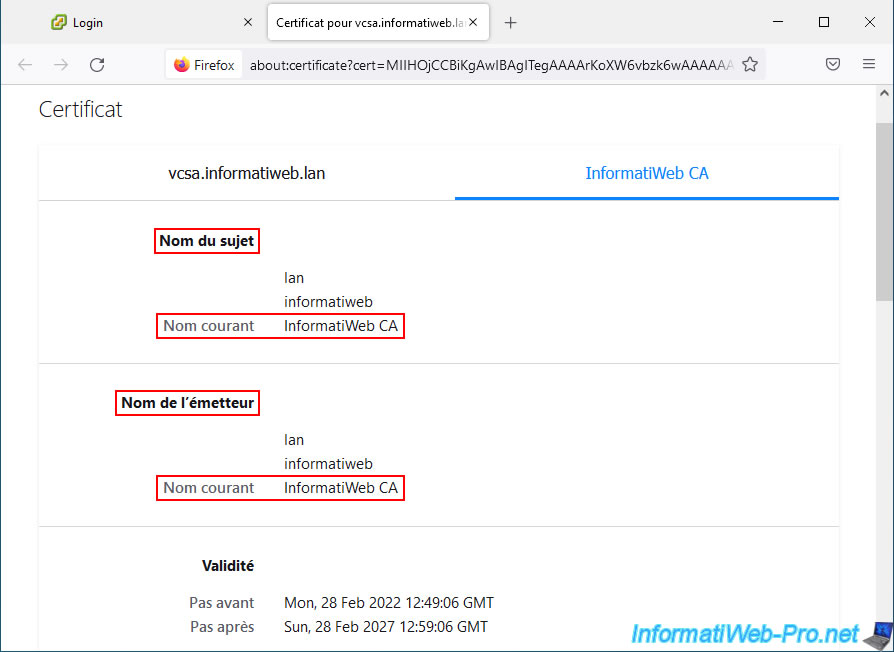
On Google Chrome, this will work without problems (if your certificate authority certificate is in the "Trusted Root Certification Authority" certificate store on your Windows computer or Windows Server).

On Microsoft Edge, the principle will be the same as with Google Chrome.
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

No comment