Create an enterprise root certification authority (Root CA PKI) on Windows Server 2012 / 2012 R2
- Windows Server
- AD CS
- 04 January 2015 at 10:57 UTC
-

- 2/4
New tutorial available for Windows Server 2016: WS 2016 - AD CS - What is a CA and install an enterprise CA.
4. Request a Certificate
To request a certificate (to be signed by your certification authority), open the console (which was saved on your desktop at the end of point 2) and go to "Personal -> Certificates." Right-click and click on "All Tasks -> Request new certificate".
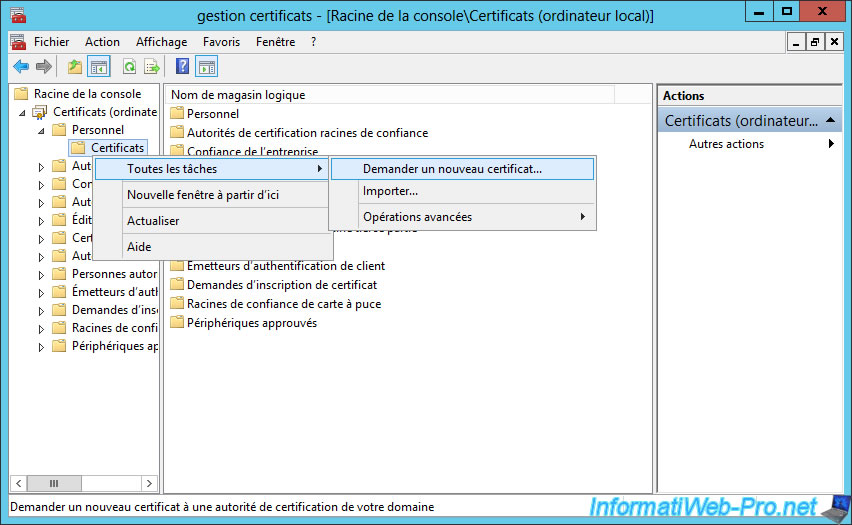
The "Certificate Enrollment" is displayed.
Skip this step.
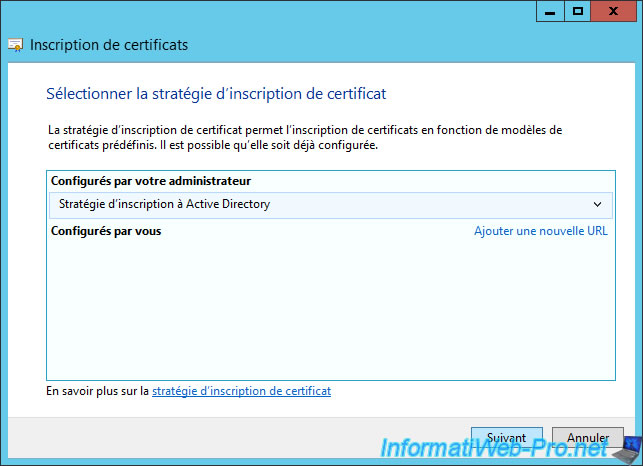
Select your new template and click the link "Registration for this certificate requires additional information".
Note : If your new certificate template isn't shown, you probably forgot to change the permissions in the "Security" tab when creating your certificate template.
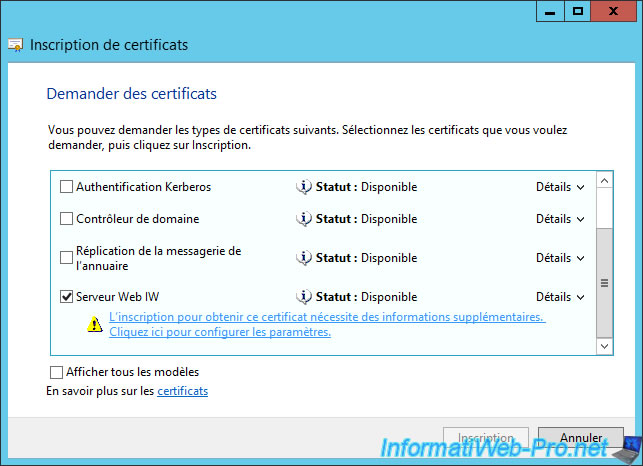
Because this certificate is used to verify the address of a website, you must specify the domain name of your computer as the "common name".
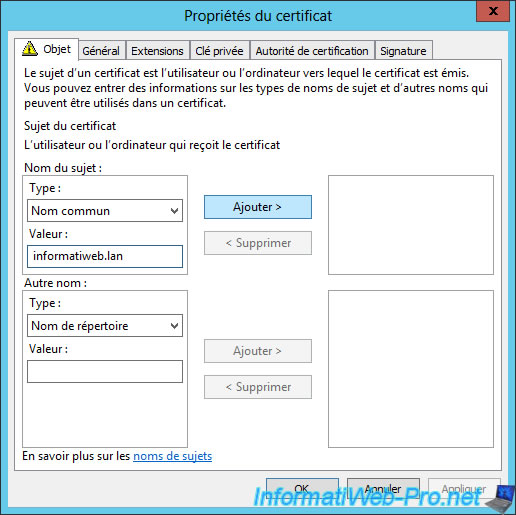
Then, you can add more information in the certificate if you want. For example: We have added the name of the organization : "InformatiWeb".
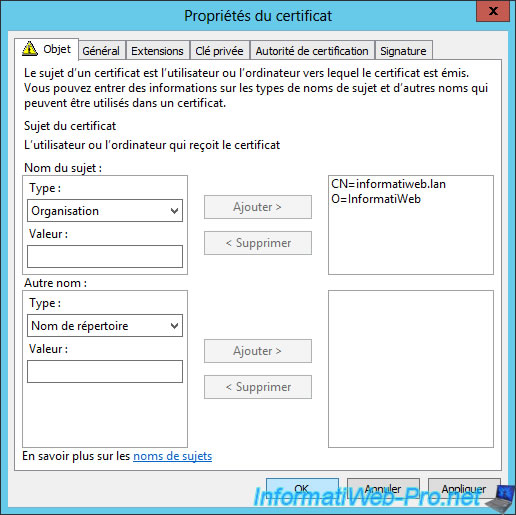
The blue link has disappeared. Click on "Register".
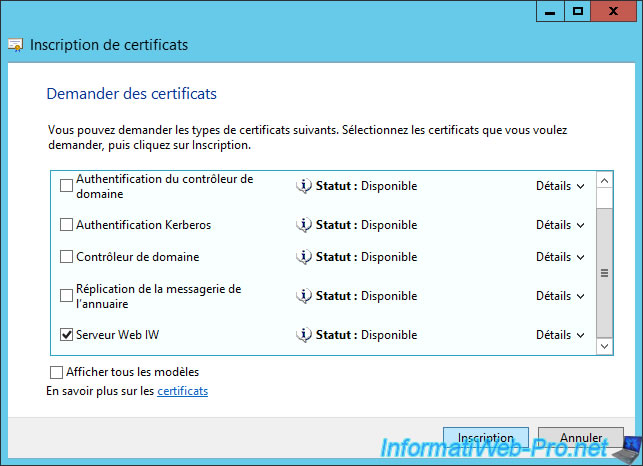
If all goes well, the creation of the certificate will be made without problems.
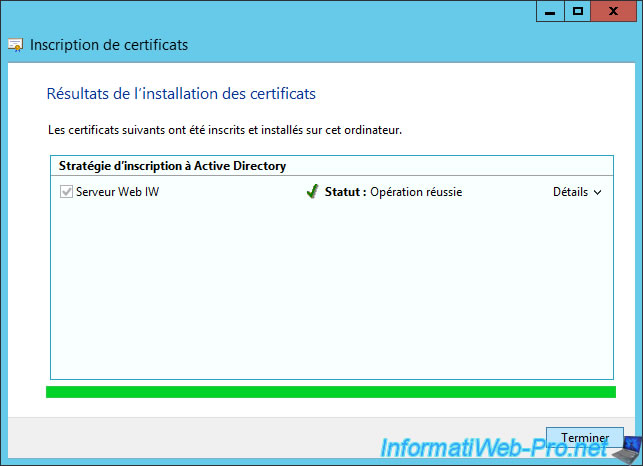
Here is our newly signed certificate (or delivered) by our certification authority.
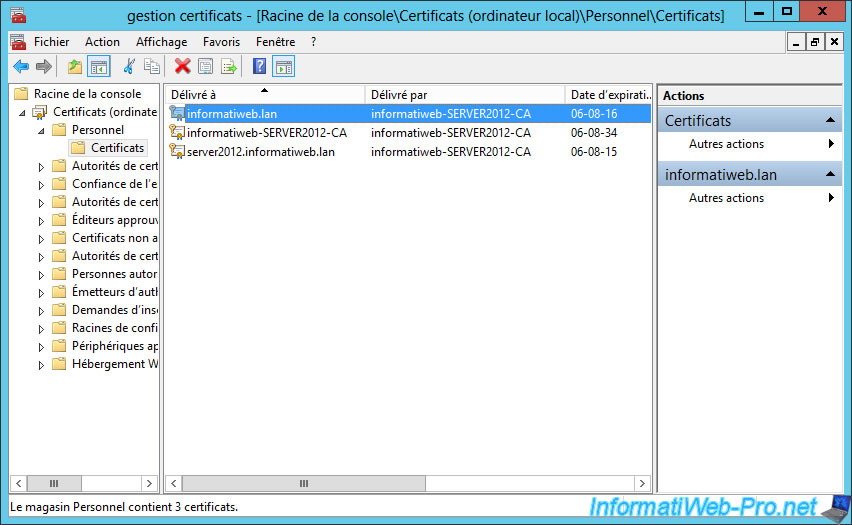
5. Protect the IIS Web server with the generated certificate
Now that we have our certificate, we'll show you how to secure your IIS web server using this certificate.
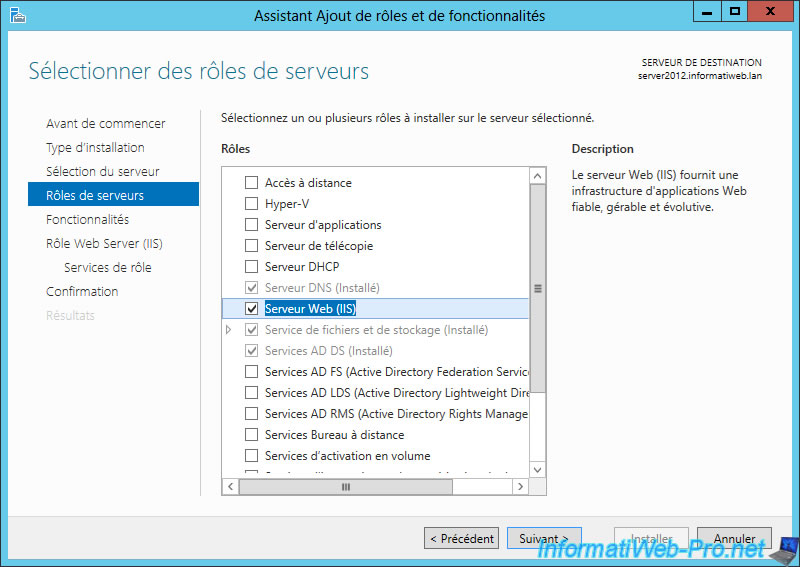
If you have not installed a web server on your server, just install the role "Web Server (IIS)" and leave the rest by default.
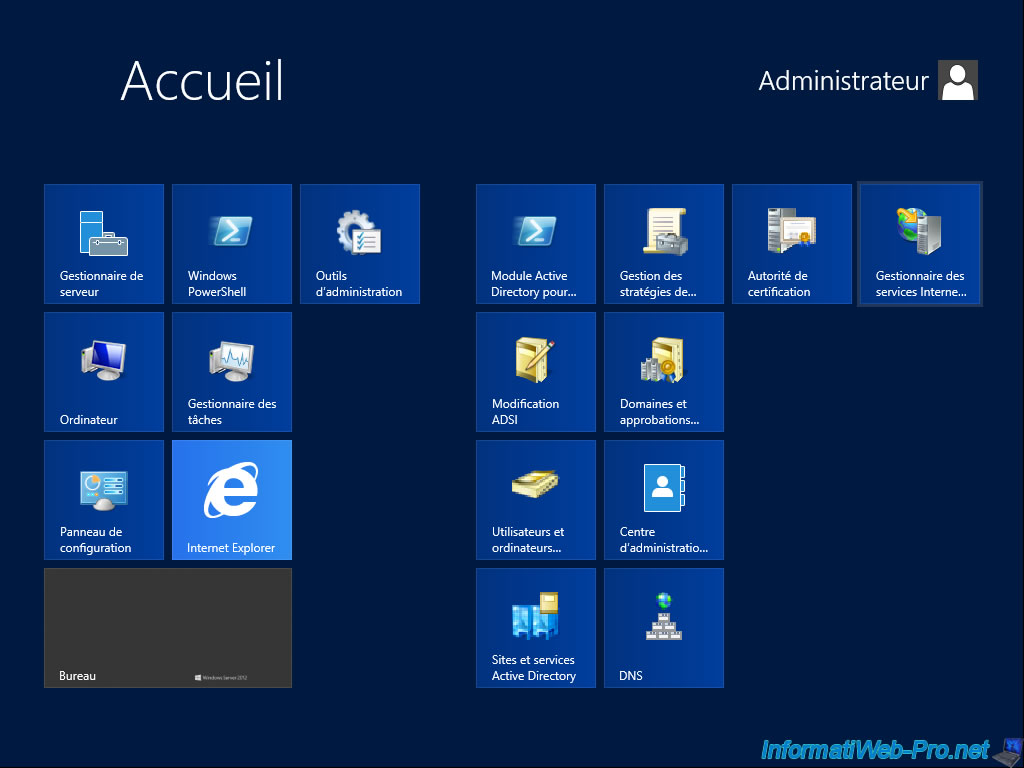
Then, in the touch interface, run the Internet Service Manager (IIS).
Note : For Windows Server 2012 R2, you must first click the arrow at the bottom left to find this shortcut.
If this message appears, click "No".
Select the website that you want to secure. In our case, this will be the default (Default Web Site).
Then, in the right column, click on "Connections".
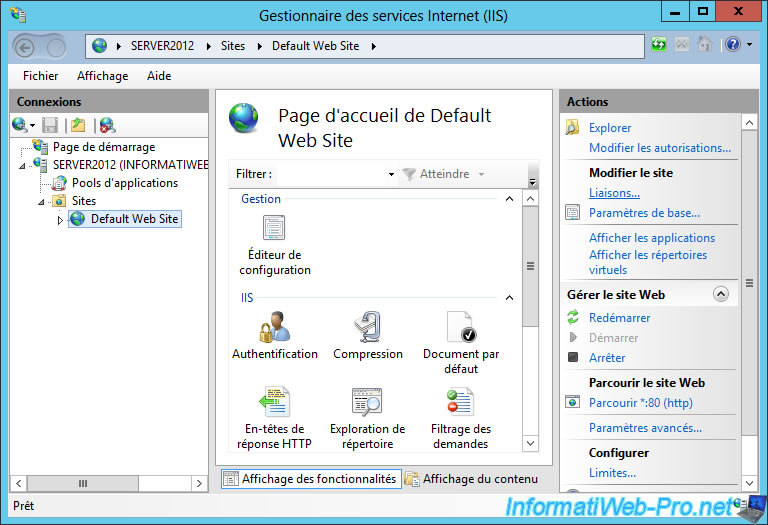
Click "Add" to add the HTTPS port.
Note : If this already exists, select it and click "Edit".
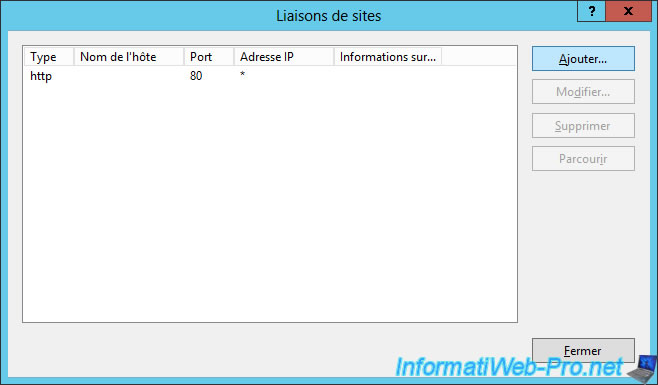
Select "https" (port 443 by default) and select your certificate from the "SSL Certificate" list.
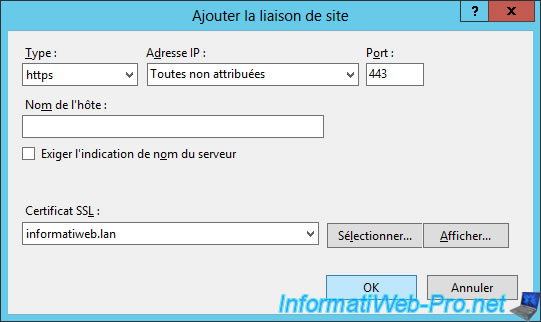
Now, type your domain name in the "Internet Explorer" browser on your server and click the little padlock that appears in the address bar.
As you can see, your browser does not display a warning about your certificate because it is signed by your certification authority.
Since the certificate of your certification authority is in the list of trusted authorities on your server, the certificate is considered valid.
Important : Mozilla Firefox will display a warning because it uses its own certificate store. So, you will need to import the certificate of your authority in the certificate store of Mozilla Firefox for this warning also disappears from this web browser.
Note : on Windows Server 2012 R2, this page is different. With this version of Windows, you'll have a page called "Internet Information Services" with a blue background.
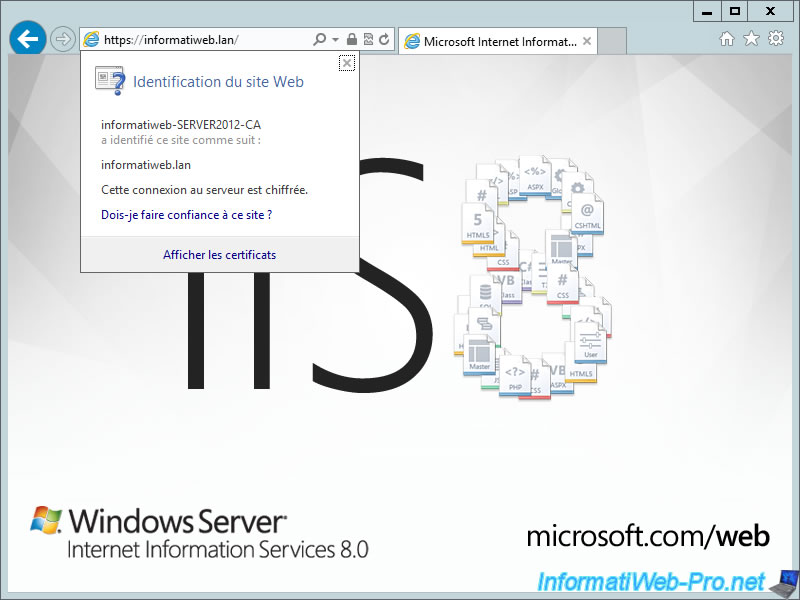
6. Distribute the certificate to the Active Directory clients
Because we have created an Active Directory on our server, we can modify group policies for our customers receive the certificate of our certification authority. Thus, our customers can access our intranet (website accessible only in an internal network) securely and without warning about the certificate.
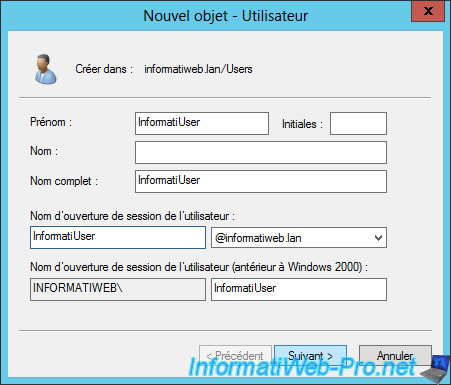
To begin, create a user in your Active Directory.
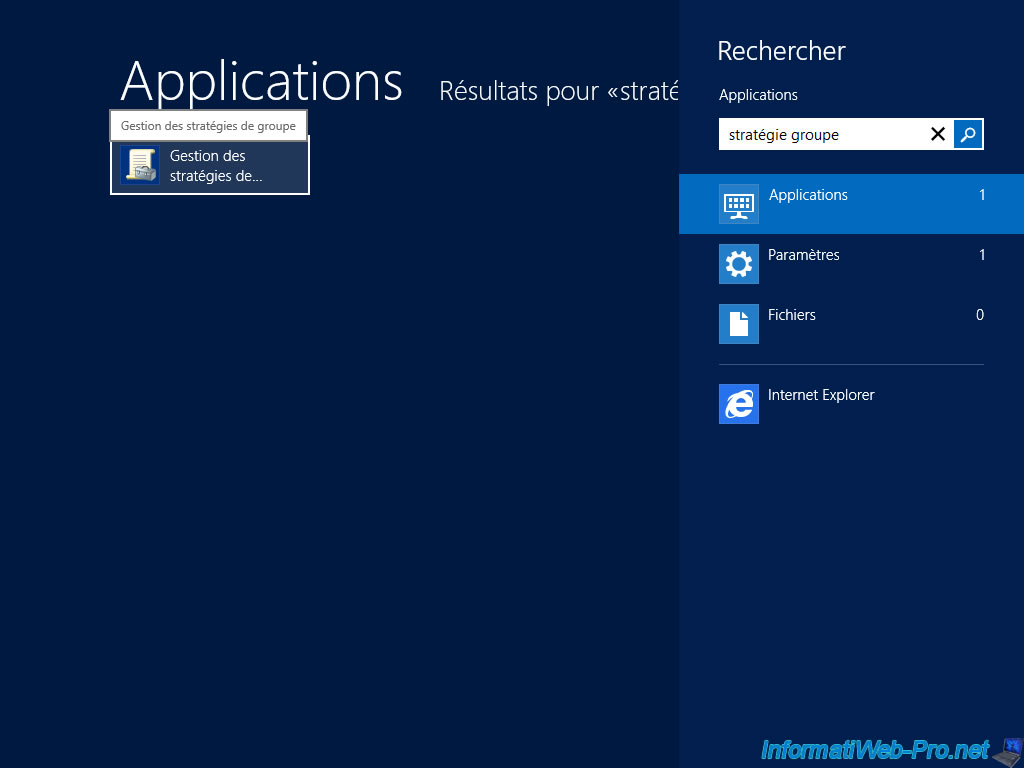
Then, in the touch interface, search for "Group Policy" and click "Manage Group Policy".
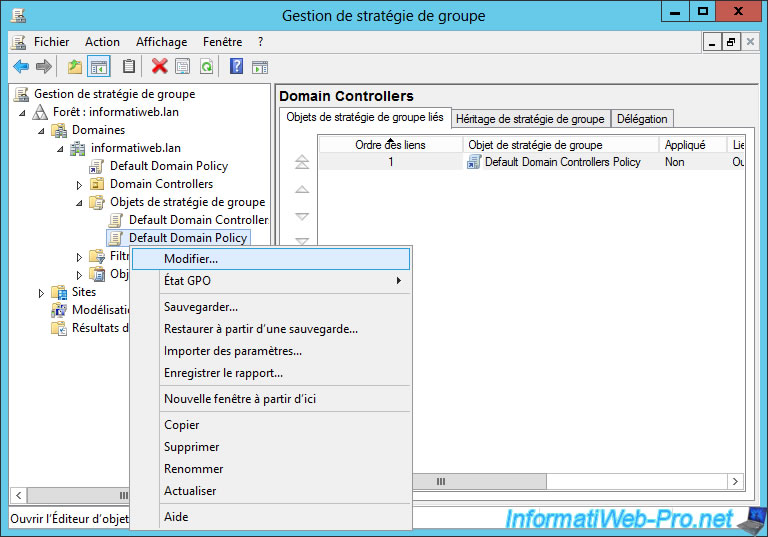
In this window, go to "Forest : ... -> Domains -> [your domain name] -> Group Policy Objects -> Default Domain Policy.
Then, right-click on "Default Domain Policy" and click "Edit".
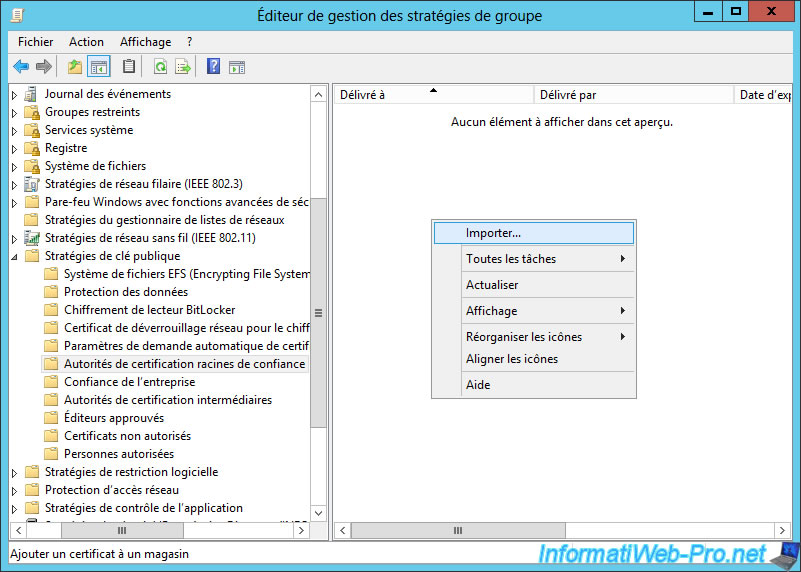
The "Group Policy Management Editor" will allow us to change the settings about our domain.
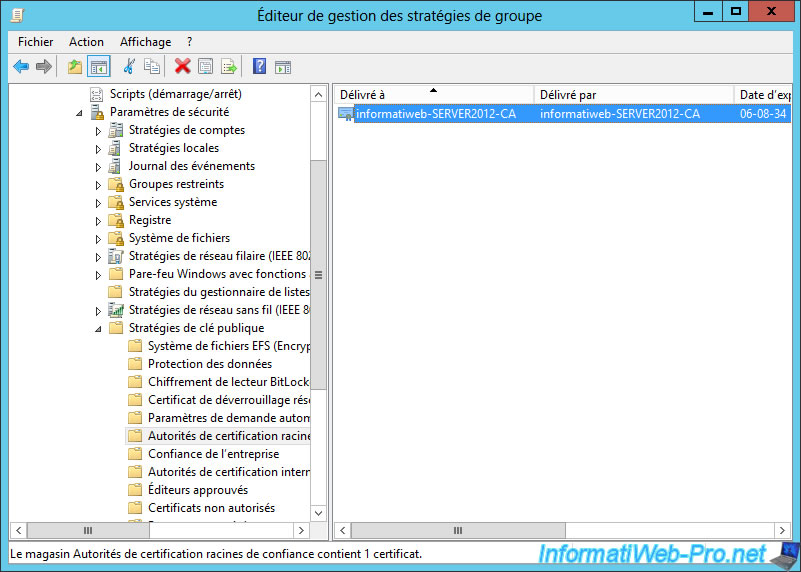
In this window, go to "Default Domain Policy Strategy [SERVER ...] -> Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies -> Trusted Root Autority Certification".
On the right side, right-click -> "Import."
The Certificate Import Wizard opens.
Select the certificate of your certification authority (we have exported at point 2).
By default, the certificate will be imported into the shop "Trusted Root CA".
A summary of the import is displayed.
If all goes well, the certificate will be imported.
Now that the certificate of our CA is imported into the list of trusted authorities of our domain, all clients of the Active Directory will receive this certificate by default.
Because we use certificates signed by this Certification Authority, our certificates are still valid (until their expiration dates).
Note :
In speaking of expiration date, remember to renew your certificate and the certificate of from your Certificate Authority because when the certificate of the authority expires, certificates signed by this authority will be considered invalid.
Remember to import the new certificate in this window so that clients of the Active Directory may receive the new certificate of the Authority (the one that has been renewed).
Restart the "gpupdate" program to update the strategy of the computer and the domain.
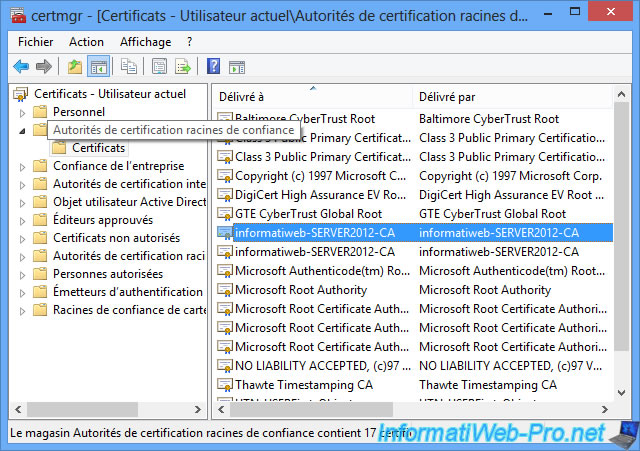
To test this configuration, we have joined a computer with Windows 8 Pro to our Active Directory and we have login with the AD user that we created at the beginning of section 6.
Then, run the "certmgr.msc" program on the client computer and go to "Trusted Root Certification Authorities -> Certificates".
If you have configured group policies properly, you will see the certificate of your certification authority.
If this is the case, try to access the website hosted on your server by typing the domain name configured on the server.
Notes :
- The certificate is only valid for this address.
- If you access the website by its IP address, the browser will display a warning because the address is different from the common name in the certificate.
- If you want to secure multiple sub-domains with a single certificate, simply enter "* .domain.extension" as the common name. This certificate will be valid for all subdomains except the domain. The solution is to redirect the main domain to the subdomain "www" to avoid warnings about the certificate.
- On Windows Server 2012 R2, this page is different. With this version of Windows, you'll have a page called "Internet Information Services" with a blue background.

Share this tutorial
To see also
-
Windows Server 1/12/2024
WS 2016 - AD CS - Create an enrollment agent
-

Windows Server 10/13/2023
WS 2016 - AD CS - Enable and use automatic certificate enrollment
-
Windows Server 12/8/2023
WS 2016 - AD CS - Install and configure a root CA and a secondary CA
-

Windows Server 9/15/2023
WS 2016 - AD CS - What is a CA and install an enterprise CA

No comment