- Windows Server
- 29 September 2023 at 11:07 UTC
-

- 1/3
When you create an enterprise CA on Windows Server, certificates can be generated through a certificate template system.
- What is a certificate template ?
- Certificate template versions
- Certificate templates available on Windows Server
- Certificate template settings
- Create a new certificate template
- Request a certificate for a web server (IIS)
1. What is a certificate template ?
Certificate templates are sets of rules and settings configured on your enterprise certificate authority on Windows Server.
Warning : the certificate templates only exist on an enterprise certification authority (which is therefore linked to an Active Directory domain) and not on a standalone certification authority (not linked to the Active Directory).
When your certificate authority receives a certificate request, it must apply a set of rules and settings to issue or renew the requested certificate so that it's valid for the intended use (for example : protecting a web server or proving the identity of a user).
This also ensures that the client will submit a valid certificate request (CSR).
The advantage of a company certificate authority is that it's linked to the Active Directory.
This means that its certificate and certification templates are also stored in your Active Directory infrastructure. Specifically, in the "Configuration" partition of your Active Directory.
This means that these certificate templates can be used by any CA in your Active Directory forest.
This also allows your company certification authority to retrieve information about the client (user, computer, etc.) who submitted a certificate request directly from your Active Directory infrastructure.
2. Certificate template versions
On Windows Server, there are 4 versions of certificate templates :
- version 1 : version compatible with all certification authorities on Windows Server since Windows 2000.
- version 2 : available from Windows Server 2003 Enterprise and Datacenter
- version 3 : available from Windows Server 2008 Enterprise and Datacenter
- version 4 : available since Windows Server 2012
Note that certificate template versioning has changed since Windows Server 2012.
Important : as you will see below, some versions of certificate templates are editable and others are not.
Nevertheless, we strongly recommend that you don't modify the pre-installed ones and create a copy of the desired template if you want to modify it.
Indeed, if you modify the pre-installed ones, you may encounter problems when you create certificate templates for third-party professional solutions where their official documentation is based on one of these pre-installed certificate templates.
2.1. Certificate template (version 1)
Certificate templates in version 1 are supported by all certification authorities on Windows Server.
These are installed automatically during your CA installation and therefore can't be changed or removed.
The certificate templates in version 1 can be :
- Automatically enroll (issue) certificates through custom scripts or through the Computer-only certificate auto-enrollment setting available in Group Policies (GPOs).
- manually enroll (issue) certificates through the Certificates snap-in (via the mmc console) or through the CA web enrollment pages
These version 1 certificate templates are available on Windows Server 2000, 2003, 2003 R2, 2008 and 2008 R2 (all editions) and later.
Important : since you can't modify a certificate template in version 1, you will have to duplicate it if you want to modify this one.
In addition, the copy of a certificate template in version 1 will become a certificate template in version 2 or 3 which can be modified.
2.2. Certificate template (version 2)
Version 2 certificate templates have been available since Windows Server 2003 and provide support for automatic certificate enrollment.
These certificate templates in version 2 can be :
- enrolled (issued) automatically using custom scripts
- enrolled (issued) automatically on Windows XP Pro, Windows Vista and their equivalents : Windows Server 2003 and 2008
- manually enrolled (issued) using the certificate enrollment wizard or CA web enrollment pages
These version 2 certificate templates are available on Windows Server 2003, 2003 R2, 2008 (Enterprise and Datacenter) and on Windows Server 2008 R2 (all editions) and later.
Important : it's technically possible to modify most of the certificate template parameters in version 2 without needing to duplicate it.
Nevertheless, as explained before, you should not modify the pre-installed ones, but rather modify a copy of them to avoid.
Indeed, it happens that some third-party solutions require a certificate template that doesn't exist. In this case, it will suffice to consult the official documentation of this solution to create the new certificate template based on one of the pre-installed certificate templates.
However, if you have modified the pre-installed one, you will not be able to correctly register the certificate you will need.
2.3. Certificate template (version 3)
Version 3 certificate templates have been available since Windows Server 2008 and provide the same features as version 2 certificate templates, as well as automatic certificate enrollment.
In addition to these features, version 3 certificate templates also provide support for Suite B cryptographic algorithms.
Which adds support for key exchange, encryption, digital signatures, and hashing.
These certificate templates in version 3 are available on Windows Server 2008 (Enterprise and Datacenter), 2008 R2 (all editions) and later.
Important : version 3 certificate templates can't be used to issue certificates via the web interface of your certification authority.
If you wanted to enroll (issue) a certificate using a certificate template in version 3, you can for example do so from the "Certificates" component that you can add in an "mmc" console.
2.4. Certificate template (version 4)
Certificate templates in version 4 are available since Windows Server 2012 and provide new options :
- ability to renew a certificate with the same key.
Which is handy when you want to renew your used keys with a Trusted Platform Module (TPM) for system partition encryption/decryption or with BitLocker. - support for CSP (Cryptographic Service Provider) and KSP (Key Storage Provider), as well as the ability to specify providers in order of preference
- allow renewal by key
- activate the issue specified by the caller
Also, since Windows Server 2012, certificate template versioning has changed.
Indeed, previously, you had to select the version of the certificate template that you want to create.
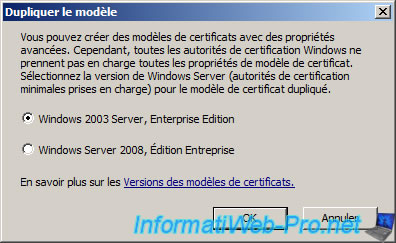
But, since Windows Server 2012, this window will no longer appear and you will have to use the settings available in the "Compatibility" tab.
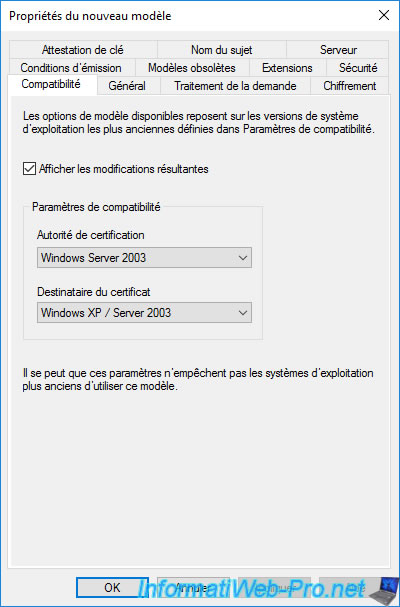
When you modify the version of the certification authority or the certificate recipient in the "Compatibility" tab of the new template being created, this influences the options that will or will not be available in the other tabs.
When you modify these values, a "Resulting changes" window will appear and tell you which options will be added or removed from the future certificate template.
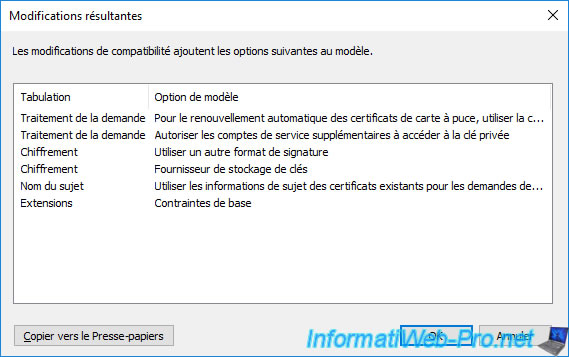
The "These settings may not prevent earlier operating systems from using this template" message means that changing these compatibility settings will not affect the version of the certificate template.
Although duplicating a version 1 certificate template will always produce a version 2 or 3 certificate template.
On the other hand, from the moment you select "Windows Server 2012" at least for these 2 compatibility settings, a version 4 certificate will be created.
Note that the version of the schema (certificate template) is chosen when the template is created and that it will therefore not change if you try to modify this new certificate template later.
Warning : version 4 certificate templates will not appear on your certification authority's Web enrollment pages.
2.5. Choosing the certificate template version
If you select "Windows Server 2012" for the "Certification Authority" and "Certificate Recipient" compatibility settings, a version 4 certificate template will be created.
On the other hand, if one of these settings is configured with a value prior to "Windows Server 2012", the version used (2 or 3) will depend on the cryptography provider selected in the "Encryption" tab :
- Key Storage Provider (KSP) : certificate template in version 2.
- cryptographic service provider (CSP) : certificate model in version 3.
This option is available as "Legacy Cryptographic Services Provider / Determined by CSP".
Sources :
- Certificate Template Concepts
- Certificate Template Versions (WS 20008)
- Certificate Template Versions (WS 2008 R2)
- Version 3 (CNG) templates won't appear in Windows Server 2008 or Windows Server 2008 R2 certificate web enrollment
- Windows Server 2012: Certificate Template Versions and Options
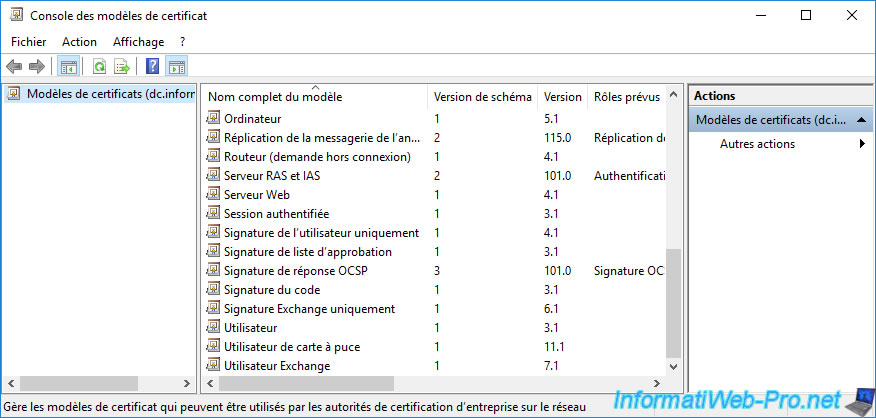
3. Certificate templates available on Windows Server
As you can see from the "Certification Authority" console, several certificate templates can be issued by default.
In other words, only these (by default) will be visible from the "Certificate Enrollment" wizard of the "mmc" console, as well as from the web interface of your certification authority (if this web interface is installed).
However, note that you will also have adequate permissions to be able to use them. Also, the web interface may not display all certificate templates (as explained previously).
To see the complete list of certificate templates available on Windows Server, right-click "Manage" on "Certificate Templates".
Note : in business, it may be interesting to remove the templates of certificates to be issued that you don't wish to use in your case.
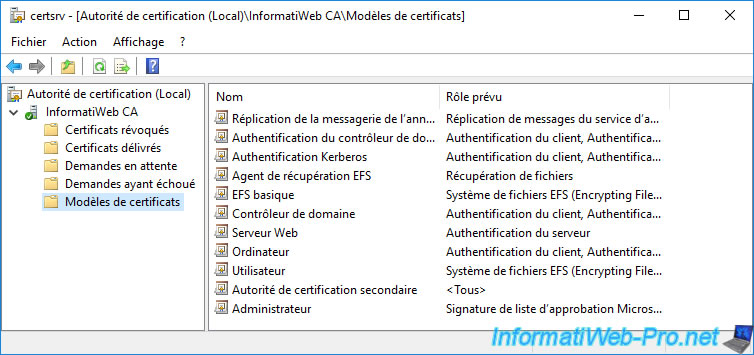
As you can see, many certificate templates (33 in the case of Windows Server 2016) are available.
Among the widely used certificate templates, you will find :
- Computer : generally used via the certificates auto-enrollment, this makes it possible to prove the identity of a client workstation (or of a server) when it connects to a server.
- Web Server : generally used to secure access to a website. But, it's also used generically when server authentication is required.
- User : typically used through certificate auto-enrollment, this helps prove a user's identity when they connect to a computer or server.
This certificate template can also allow you to encrypt confidential data via the EFS file system or secure your e-mails.
As you can see, there are several schema versions (certificate template versions).
Most are version 1 and will be at least version 2 when you duplicate them (as explained before) and others are version 2 or 3.
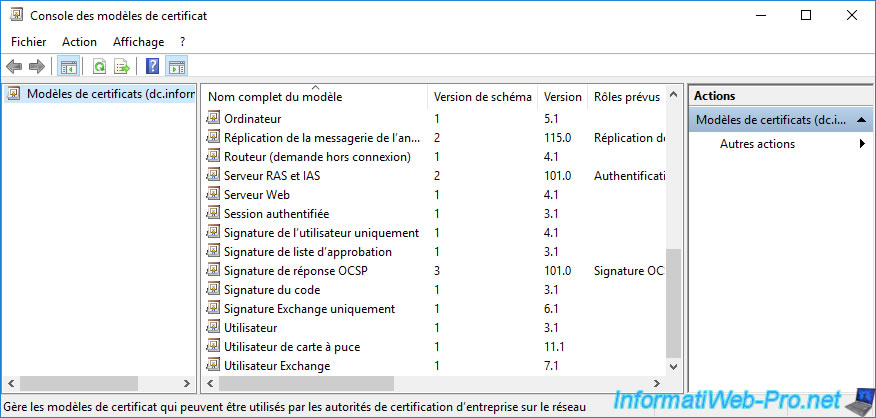
As you can see, version 1 templates are not editable (unless you duplicate them to be able to edit the copy of them).
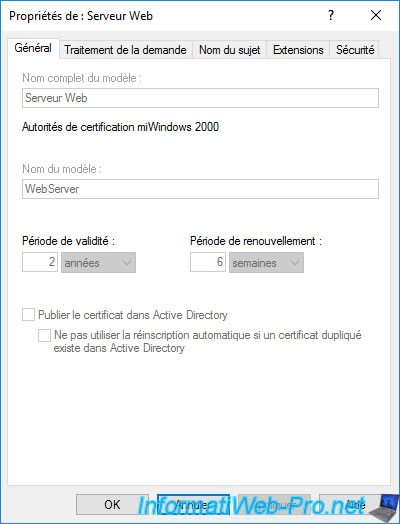
Version 2 certificate templates are editable.
Important : we recommend that you do NOT modify the pre-installed ones, but rather duplicate these if necessary to modify a copy and not the original.
Indeed, as explained previously, it happens that the manufacturer of a professional solution asks you to base yourself on an existing certificate template, then to modify specific settings on the copy of it so that the certificate is valid for this solution.
However, if you have modified the original certificate template, you may have problems in the future.
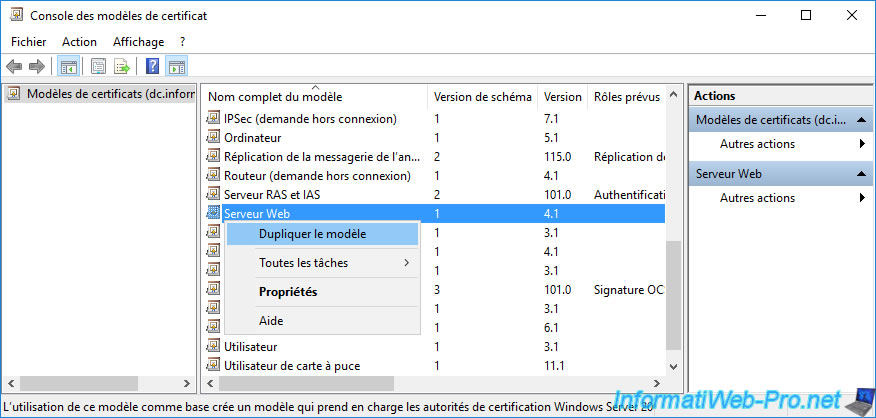
4. Certificate template settings
As you will see, certificate templates contain a lot of settings, as well as the permissions applied to them.
For the example, we duplicate the "Web Server" certificate template.
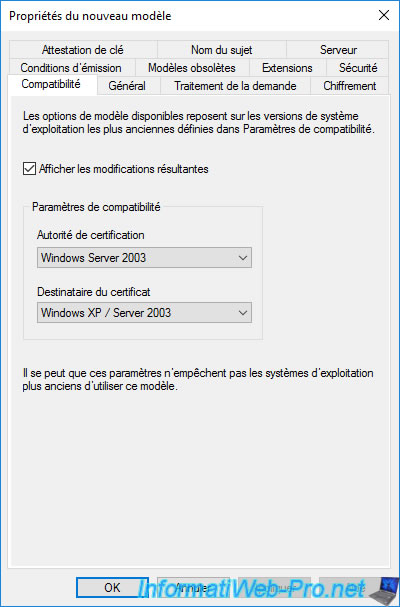
To begin with, starting with Windows Server 2012, you will have the option to choose the compatibility of this certificate.
Unlike previous versions of Windows Server where you had to select the certificate template version you wanted to create.
The "Show resulting changes" checkbox simply enables the display of a "Resulting changes" window listing the features added or removed according to the values selected for these compatibility settings.
Warning : as indicated previously, if you select at least "Windows Server 2012" for these 2 compatibility options, a version 4 certificate template will be created.
This means that it will not appear in the web interface of your certification authority (if applicable).
As a workaround, select "Windows Server 2008 R2" for the "Certification Authority" compatibility setting when creating this new certificate template.
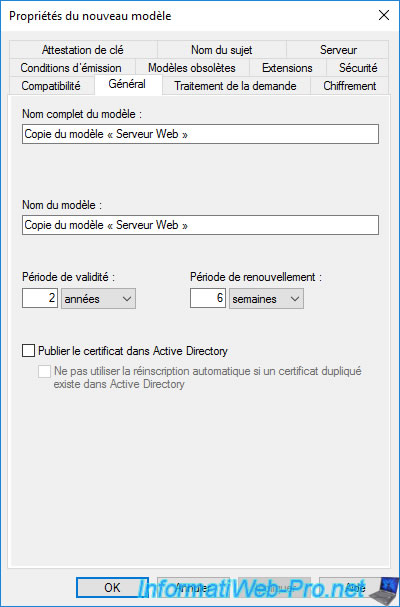
In the "General" tab, you can specify :
- the template display name : the name under which it will appear in the list of certificate templates on your certification authority, but also on the client side in the mmc console or in the web interface of your certification authority.
- the template name : the internal name (without space of preference) under which this template will be created.
- the validity period : the length of time the certificate issued (delivered) using this certificate template will be valid.
- the renewal period : indicates when the certificate must be renewed (if automatic renewal is supported by the application that uses this certificate).
- whether to publish certificate in Active Directory : useful if several users or computers must have access to the same certificate, as well as for certificate roaming.
Indeed, if a user obtains a user certificate and this user can connect to several computers and/or servers and the roaming profiles are not configured, this user would obtain as many certificates as there are computers and/or servers where he has logged on. This will quickly become a problem if it's a user certificate allowing data to be encrypted using EFS, for example.
If you publish the certificate in the Active Directory and you enable certificate roaming, this user will be able to retrieve his unique user certificate, regardless of the computer or server where he connects. - do not automatically reenroll if a duplicate certificate exists in Active Directory : simply allows not to create a new certificate if a valid certificate for the computer, server or user concerned already exists in Active Directory.
Important : for a certificate to be renewed, 80% of its validity period must have passed.
In the example below, our certificate will be valid for 2 years (= 2 x 52 weeks = 104 weeks) and it will be renewed 6 weeks before its expiry date (so at week 98).
If you calculate 80% of 104 weeks, you will see that this corresponds to : 83.2 weeks (104 / 100 x 80).
The renewal will therefore be carried out after the 80% validity of this certificate. Which respects the Microsoft recommendation : Recommended values of validity period and renewal period.
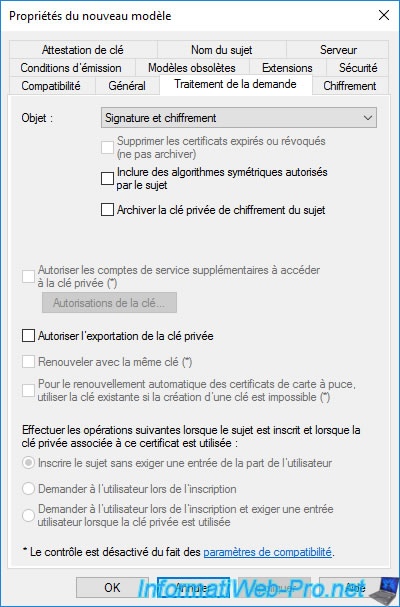
In the "Request Handling" tab, you will find several options allowing for example :
- allow private key to be exported : which is practical to be able to export the certificate in ".pfx" format from the "Personal" store of your computer or server via the mmc console, for example.
- renew with the same key : to renew the certificate using the same key, which allows you to continue signing with the same private key. Client-side verification with the same public key will therefore be possible.
Note that the greyed-out options in this case where an asterisk (*) is displayed correspond to the options that you can't modify because of the values selected for the compatibility settings present in the "General" tab.
To access it, you will need to increase these values.
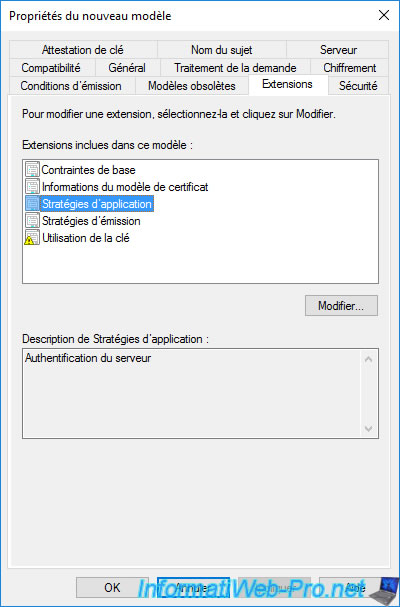
In the "Extensions" tab, you will find several advanced options that you will only change if the manufacturer of the solution you want to secure asks you to do so or you know exactly what you are doing.
However, for the "Web Server" certificate template, you will see that the application policy used is : Server authentication.
This allows the client to authenticate the server or in other words to be sure that it connects to the correct server and not that of a hacker who would try to pretend to be the desired server.
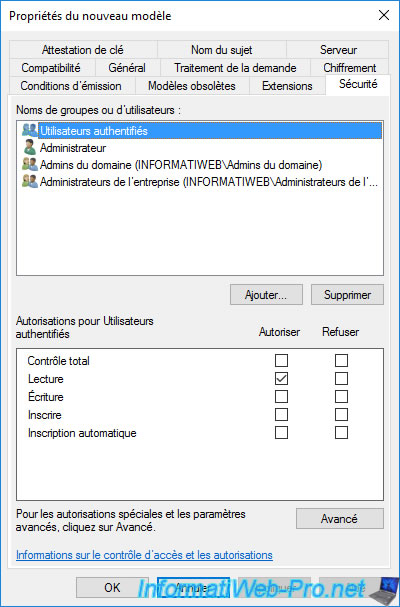
In the "Security" tab, you will see that the "Authenticated Users" group only has a "Read" right.
This is necessary so that you can see the certificate templates available through the "mmc" console's certificate enrollment wizard or in your CA's web interface.
On the other hand, users will not be able to enroll certificates, because they don't have the right to enroll (Enroll or autoenroll).
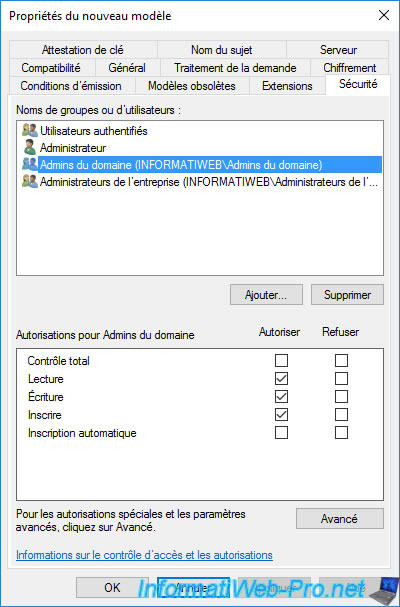
If you select the "Domain Admins" group, you will see that domain administrators can :
- Read : see this certificate template.
- Enroll : enroll certificates using this certificate template.
Warning : you can only enroll certificates from a computer or server allowed to enroll certificates.
Which means that, by default, you will be able to enroll certificates while logged in as the domain admin on your CA, but not remotely through the mmc console (for example).
If you wish to enroll a certificate using this certificate template remotely (via the "mmc" console), you will also need to grant the "Enroll" right for the computer account from which you will attempt to enroll the certificate.
Difference between "Enroll" and "Autoenroll":
- Enroll : allows you to manually enroll certificates (via the "mmc" console or via the web interface of your certification authority, if applicable).
- Autoenroll : enables certificates to be automatically enrolled through the computer or user certificate auto-enrollment setting available in group policy (GPO).
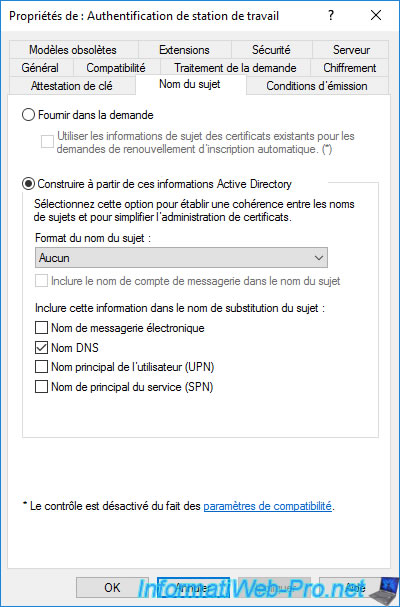
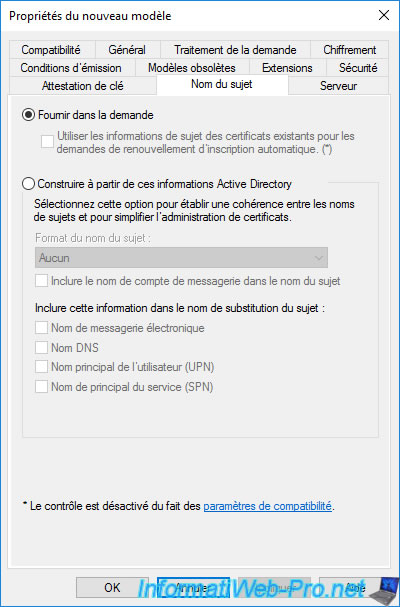
In the "Subject Name" tab, you can choose whether :
- Supply in the request : the person who wants to enroll a certificate can provide the information when requesting the certificate.
- Build from this Active Directory information : the information used must be retrieved from the Active Directory.
This implies that the request for the certificate is made by the user for whom it's intended or from the computer or server for which it is intended.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

You must be logged in to post a comment