What is a certificate authority (CA) and install enterprise CA on Windows Server 2016
- Windows Server
- 15 September 2023 at 15:39 UTC
-

- 4/5
10. Automatic distribution of your CA certificate via Active Directory
As explained and demonstrated previously, your company certification authority is referenced by default in your Active Directory infrastructure and its certificate is also there.
This will allow members (servers and computers) of your Active Directory domain to automatically receive the certificate from your certification authority.
However, as you can see, at the moment, your servers and computers have not yet received this certificate.
Which means that at the moment, these don't trust the certificates that your certificate authority issues.
Indeed, for them, these certificates emanate for the moment from a certification authority that they don't know (and which they therefore do not trust).
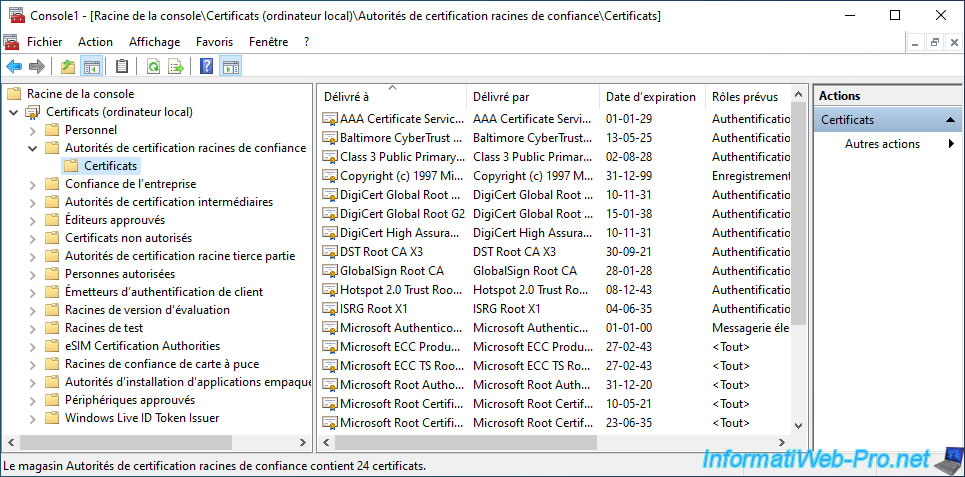
In order for your certification authority's certificate to be added to their "Trusted Root Certification Authorities" certificate store, the policy for your servers and computers must be updated.
In a test environment, you can force a policy update on a server or computer by simply running the command below to make it instant.
Batch
gpupdate /force
However, be aware that in production, you will not need to do this.
Indeed, by default, group policy is updated automatically when the server or computer starts, as well as periodically.
Source : Applying and updating Group Policy (GPO).
Once the policy (group policies) has been updated on the desired server or computer, you will see that your enterprise CA's certificate will appear in its "Trusted Root Certification Authorities" certificate store.
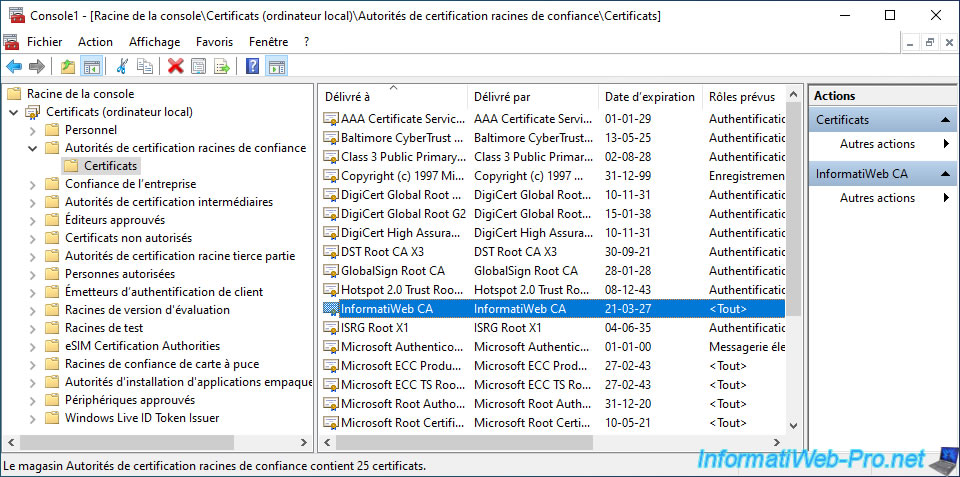
Note that the certificate automatically distributed via Active Directory is the one that does NOT contain the associated private key.
Indeed, the only key your clients need is the public key.
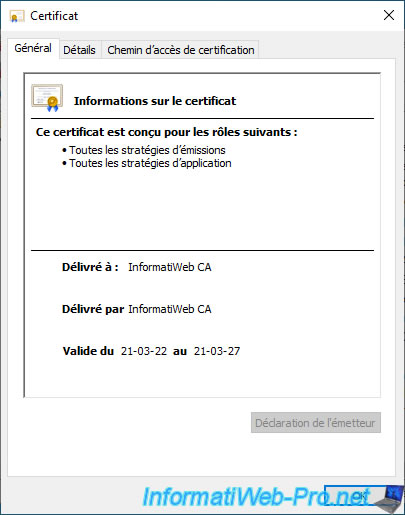
You can find it in the "Details" tab of this certificate.
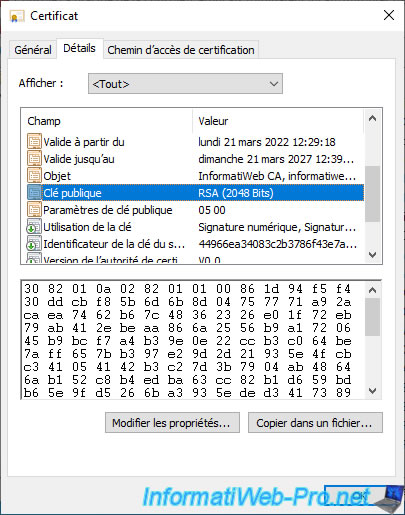
11. Request a user certificate (example)
For the example, we are going to request a user certificate for one of the users of our Active Directory domain.
11.1. Request a certificate from the mmc console
To begin, connect to one of your servers or computers with a user authorized to enroll user certificates.
That is, by default, a domain or enterprise administrator.
Of course, you can change this behavior later when you know what certificate templates are.
For this example, we will use the "Administrator" account of our Active Directory domain.
Launch the mmc console from a server or computer where you updated the policy (GPO).
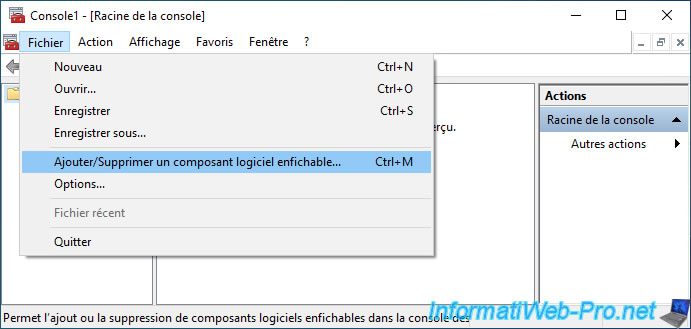
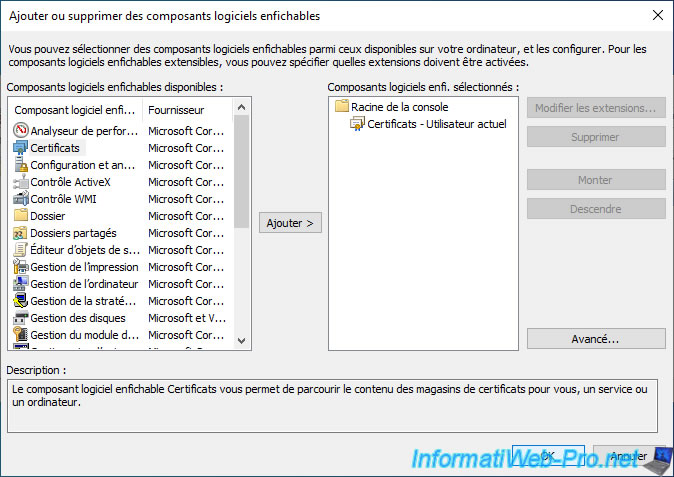
In the "mmc" console that appears, go to : File -> Add/Remove Snap-in.
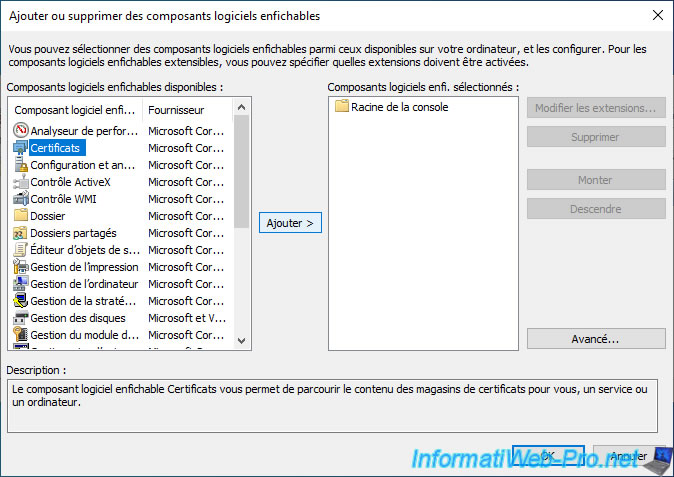
Select the "Certificates" component and click Add.
Select "My user account" (since we want to obtain a user certificate) and click Finish.
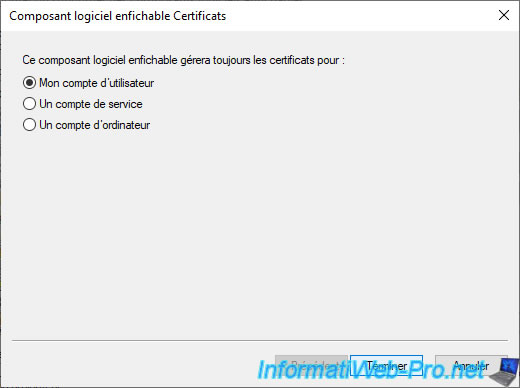
Click OK.
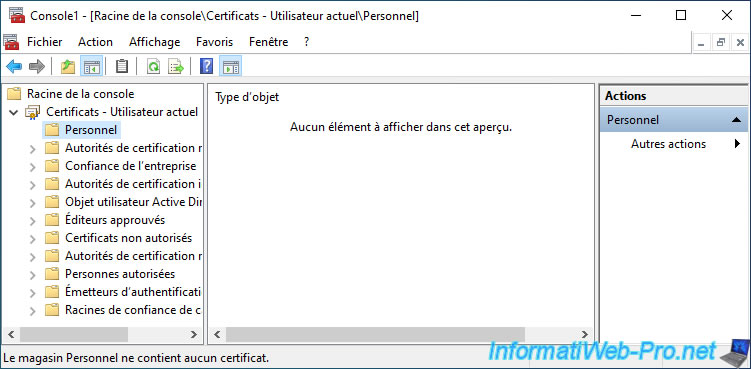
In the "Certificates - Current User" component that appears, go to the "Personal" certificate store.
As you can see, this one is currently empty.
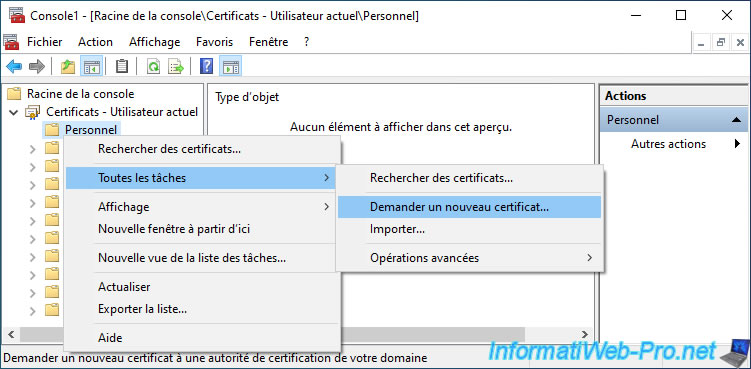
To request a user certificate, right-click on the "Personal" certificate store and click : All Tasks -> Request New Certificate.
In the "Certificate Enrollment" window that appears, click Next.
Click Next.
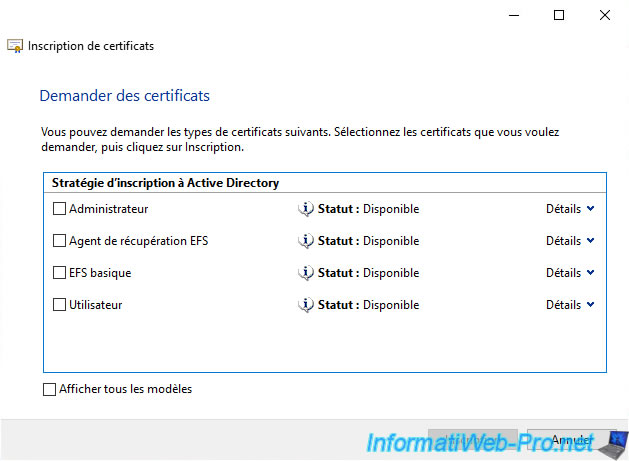
As you can see, by default, as a user, we can enroll different types of certificates.
Including the desired "User" certificate which makes it possible to prove the identity of a user when he connects to a server.
11.2. Certificate templates created by default on your certificate authority (CA)
The types of certificates visible from the certificate enrollment wizard are actually certificate templates and these are visible from the "Certification Authority" console.
When you select the "Certificate Templates" folder in this console, you only see part of the existing certificate templates.
Indeed, these are those that are part of the list of model certificates to be issued.
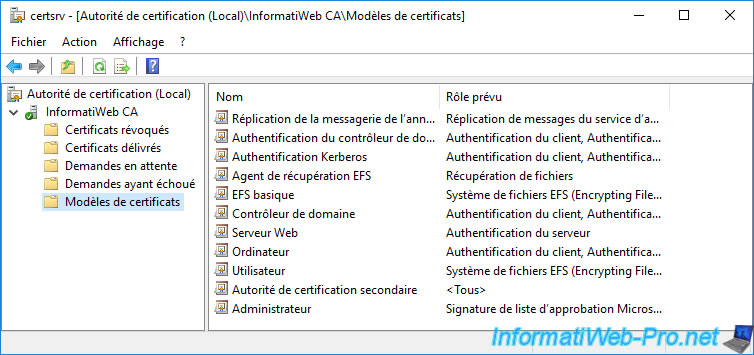
Right-click "Manage" on this "Certificate Templates" folder.
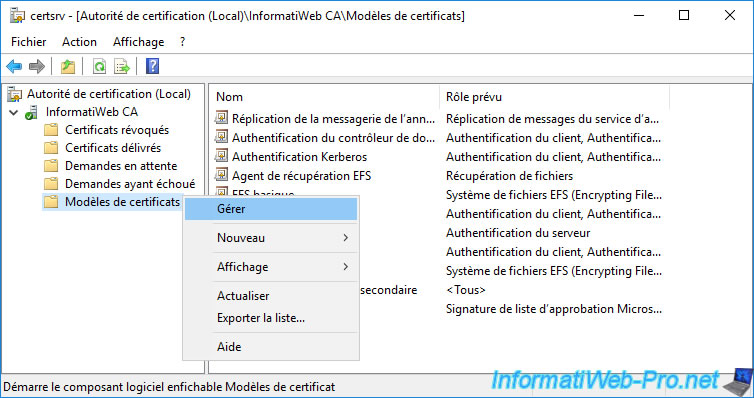
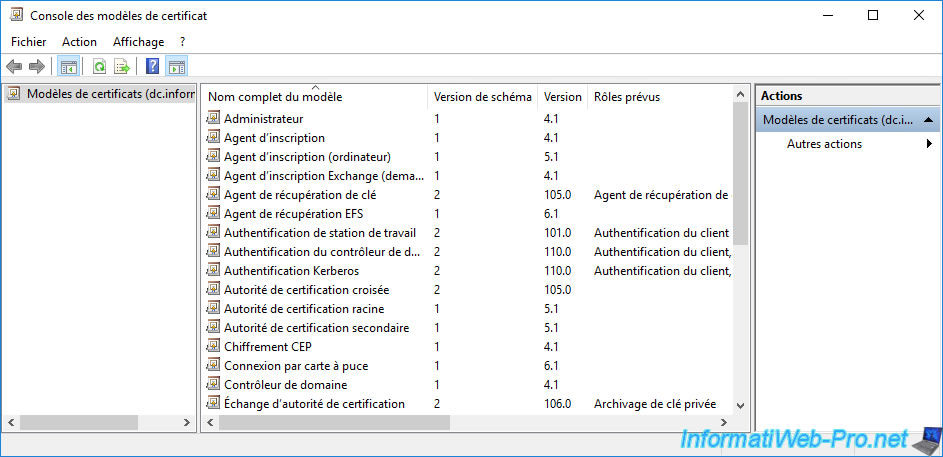
Now, you can see the full list of existing default certificate templates on your server.
On Windows Server 2016, there are currently 33. However, you can create others later (if necessary) by duplicating the existing ones.
11.3. Certificate templates stored in Active Directory
As explained previously, when you install a company certification authority, it uses the features of the Active Directory and stores certain data there.
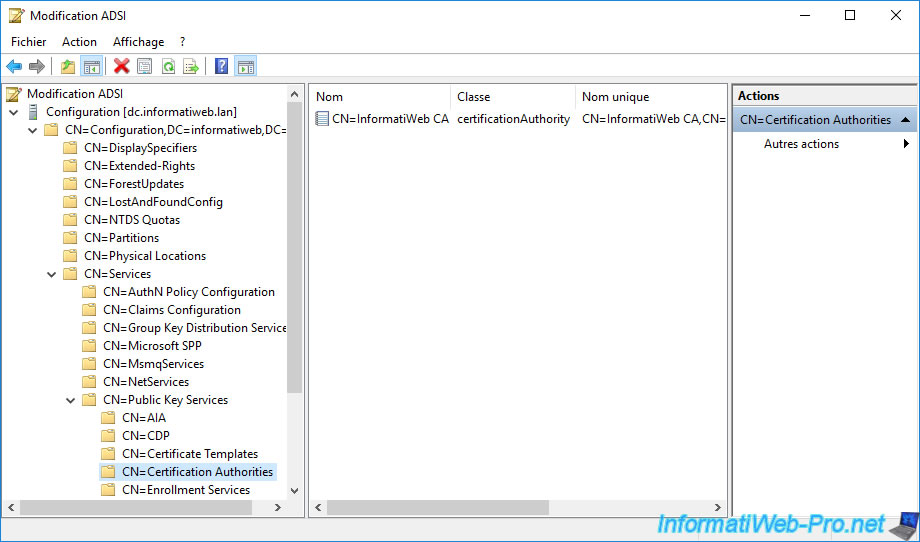
You can also see it by exploring the "Configuration" partition of your Active Directory infrastructure using the "ADSI Edit" console.
For example, you will find the LDAP object corresponding to your certification authority by going to : CN=Configuration,DC=... -> CN=Services -> CN=Public Key Services -> CN=Certification Authorities.
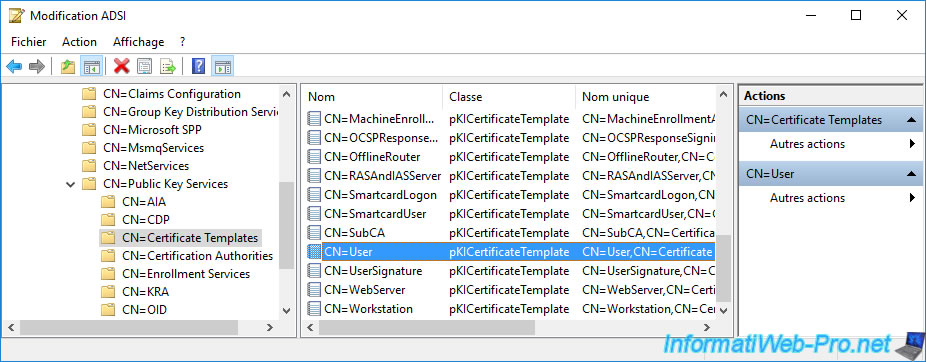
In the "CN=Certificate Templates" folder (located just above the one concerning the certification authorities), you will find the LDAP objects corresponding to the certificate templates of your certification authority.
For example, you will find the LDAP object "CN=User" which corresponds to the certificate template "Users".
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment