Create a recovery agent to recover certificates on Windows Server 2016
- Windows Server
- 05 January 2024 at 12:04 UTC
-

- 2/4
6. Request a recovery agent certificate
6.1. Request a recovery agent certificate from an mmc console
Log on to your CA with the user you want to use as recovery agent and open the "mmc" console.
In this "mmc" console, add the "Certificates" component for the current user, then right click on the "Personal" certificate store and click : All Tasks -> Request New Certificate.
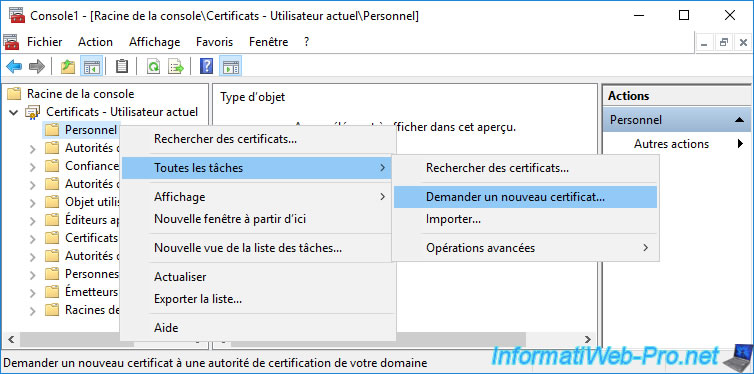
Select the "Key Recovery Agent v2" certificate template and click "Details".
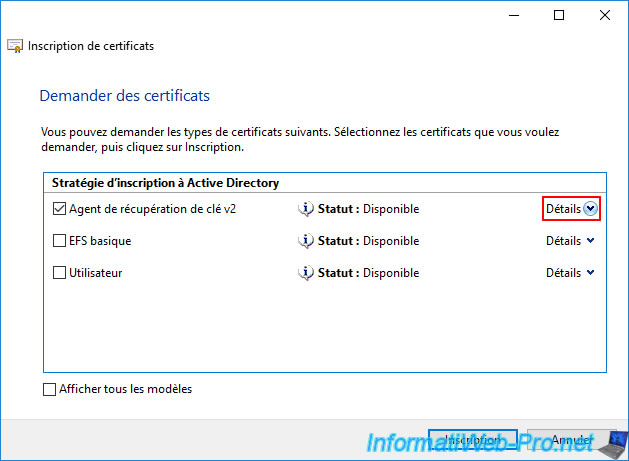
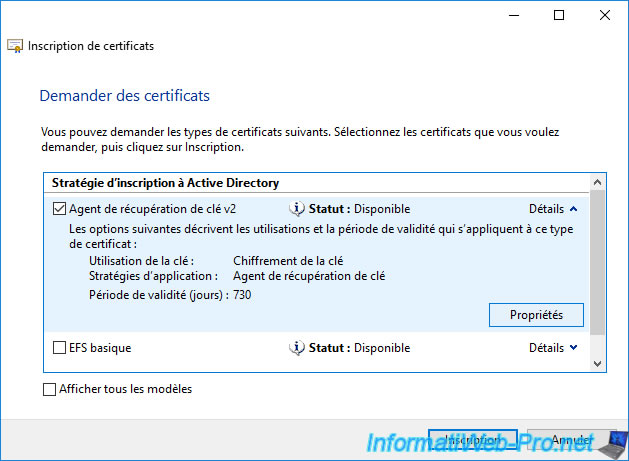
Click on the "Properties" button.
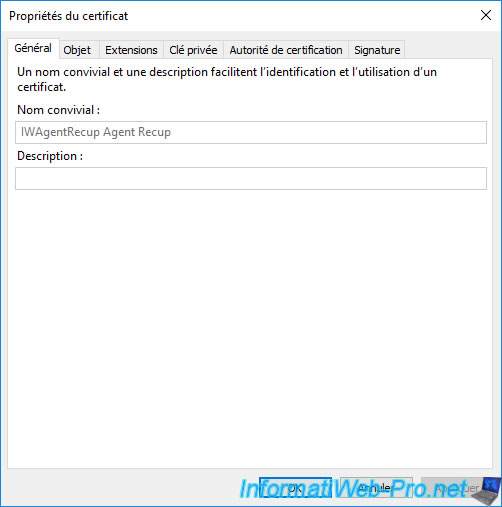
Specify "IWAgentRecup Recovery Agent" as the friendly name (for example) and click OK.
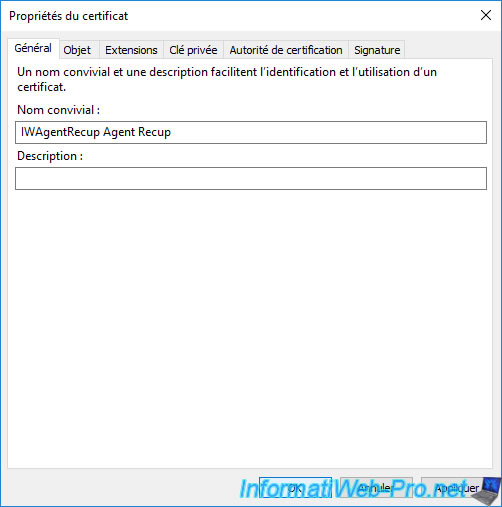
Click on Enroll.
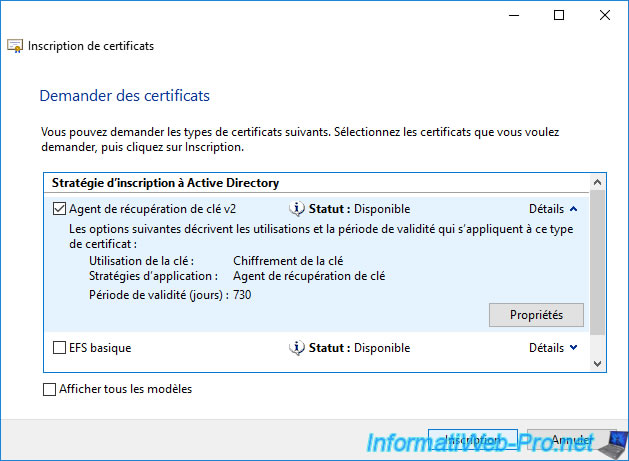
As you can see, the status is "Enrollment pending" and not "Succeeded" as it usually is.
This is due to the "CA certificate manager approval" option which is enabled by default in the "Issuance Requirements" tab of the certificate template used (Key Recovery Agent v2).
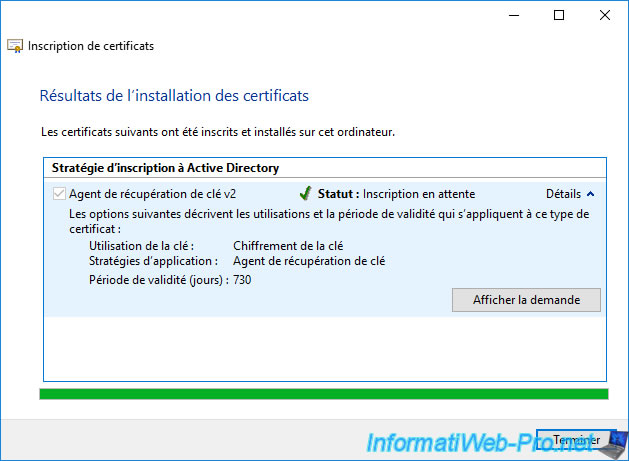
If you click on the "View request" button, you will see the "Certificate Properties" window appear.
Click Finish.
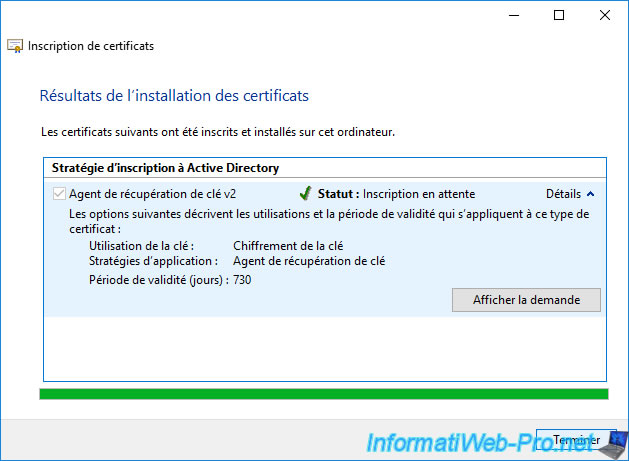
Because enrollment is pending, no certificate are added to your "Personal" certificate store.
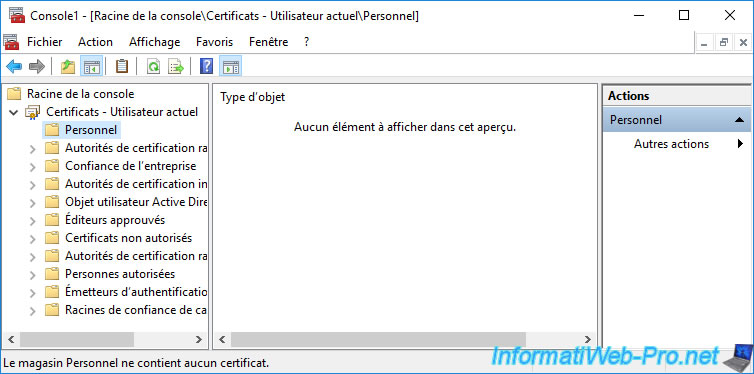
Select the "Certificates - Current User" node and click on the "Refresh" icon (framed in red in the image below).
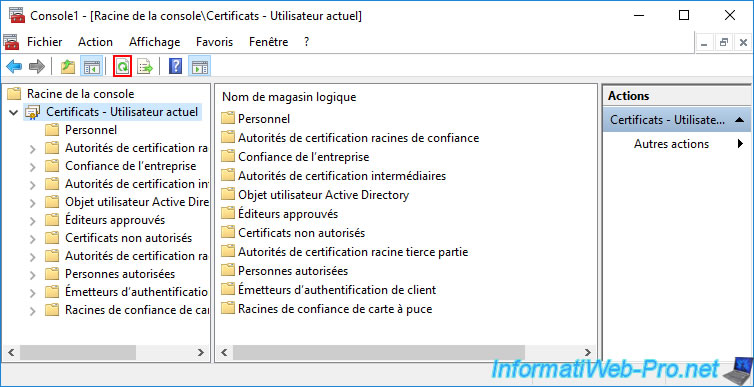
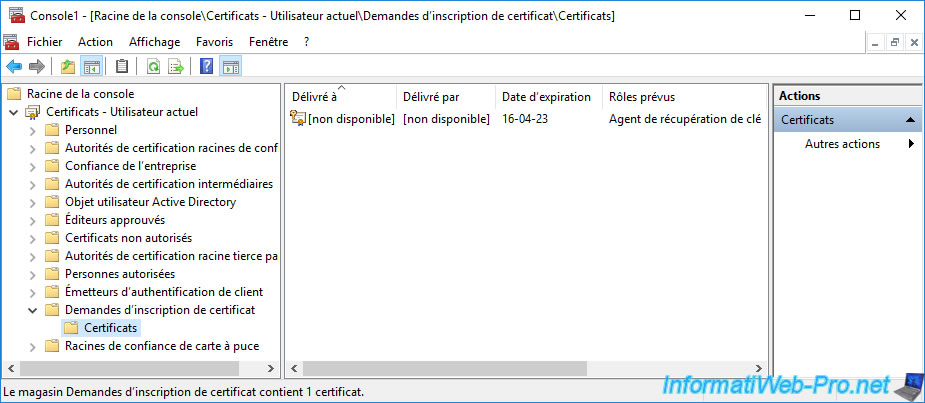
Now, you will see a new "Certificate Enrollment Requests" folder appear with a request whose intended role is "Key Recovery Agent".
Which corresponds to your certificate request which is currently pending on your certification authority.
6.2. Validate the certificate request as a recovery agent on your CA
Open the "Certification Authority" console and go to the "Pending Requests" folder.
As you can see, there is a certificate request that is currently pending.
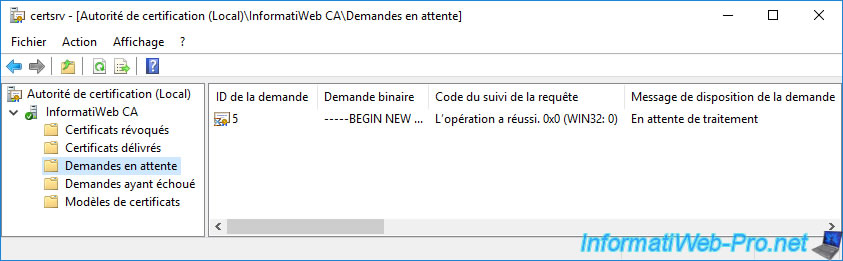
If you look at the following columns for this certificate request, you will see that it's a "Key Recovery Agent v2" certificate request made by your "IWAgentRecup" user (in our case).
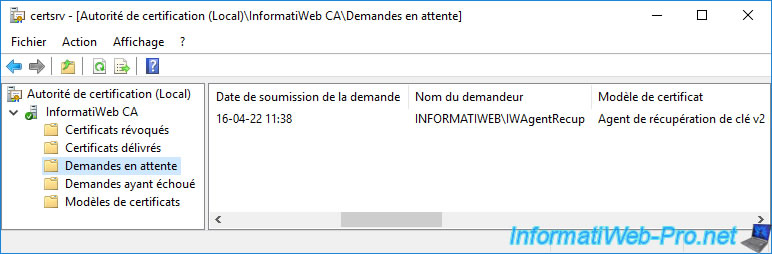
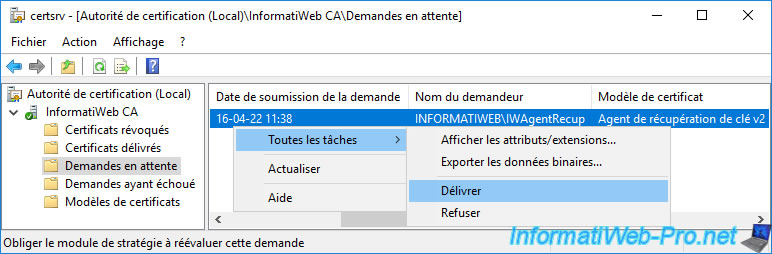
Validate its certificate request by right-clicking "All Tasks -> Issue" on it.
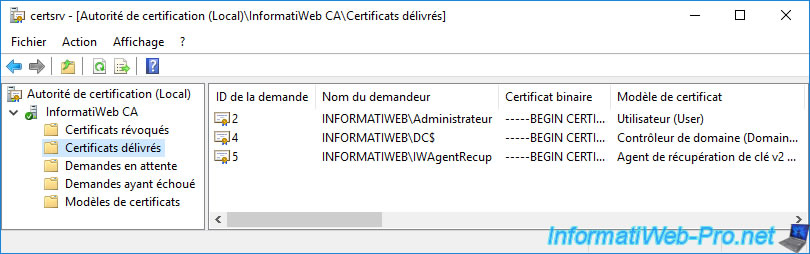
The recovery agent certificate appears in the "Issued Certificates" folder.
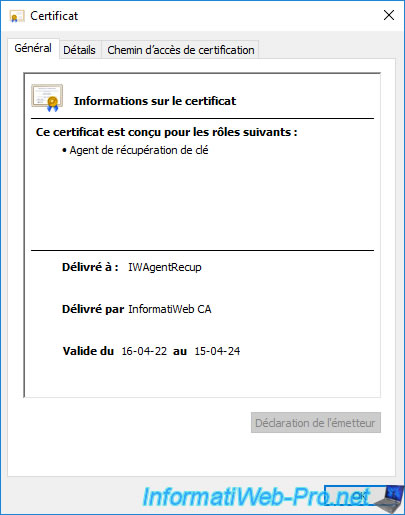
If you double-click on this issued certificate, you will see that it's designed for the role : Key Recovery Agent.
Important : since the certificate request had to be manually validated, you will need to manually import the certificate into your CA's certificate store (where you originally made the request).
6.3. Export manually issued recovery agent certificate
Since the certificate request was validated manually, the certificate is not in the "Personal" certificate store of the server from which you requested this certificate.
You will therefore first need to export it from your certification authority.
To do this, go to the "Issued Certificates" folder of the "Certification Authority" console and double-click on the issued certificate to display it.
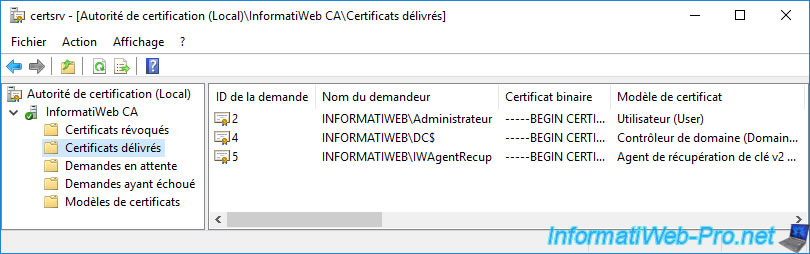
Then, go to the "Details" tab of this certificate and click on the "Copy to File" button.
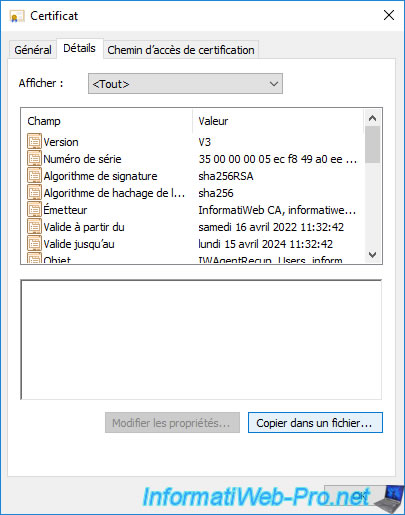
The certificate export wizard appears.
Click Next.
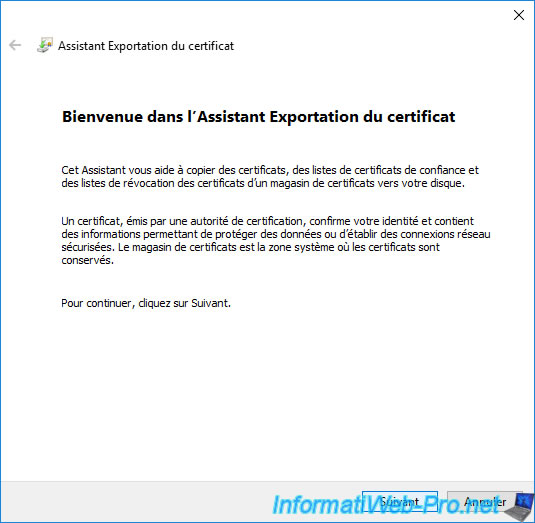
Leave the "DER encoded binary X.509 (.CER)" format selected and click Next.
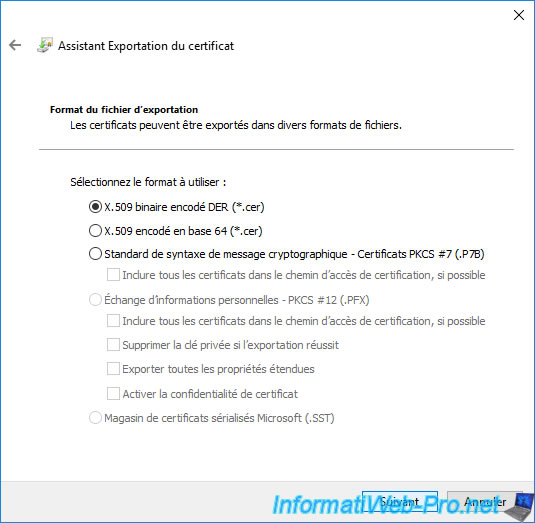
Click "Browse" to choose where and under what name you want to export this certificate.
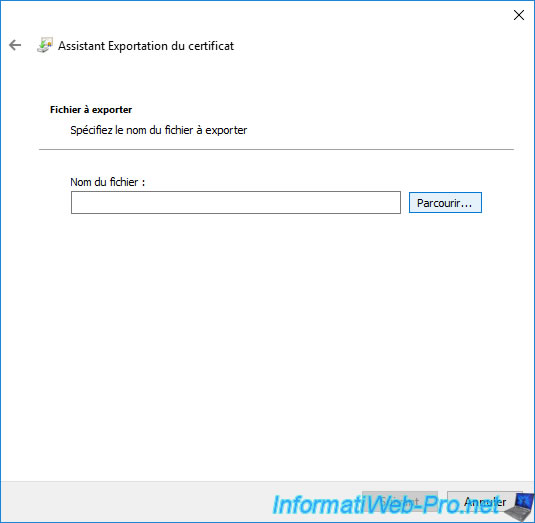
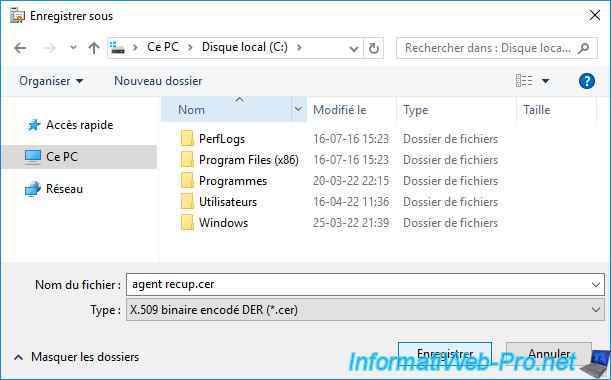
Save this certificate to the root of your CA's "C" partition so you can easily retrieve it when you reconnect with your "IWAgentRecup" user.
Click Next.
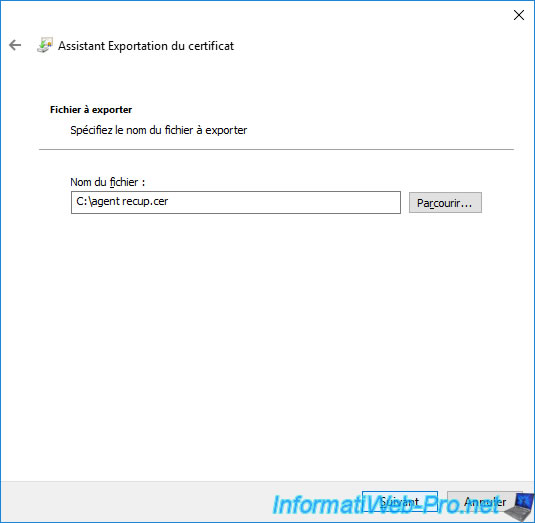
Click Finish.
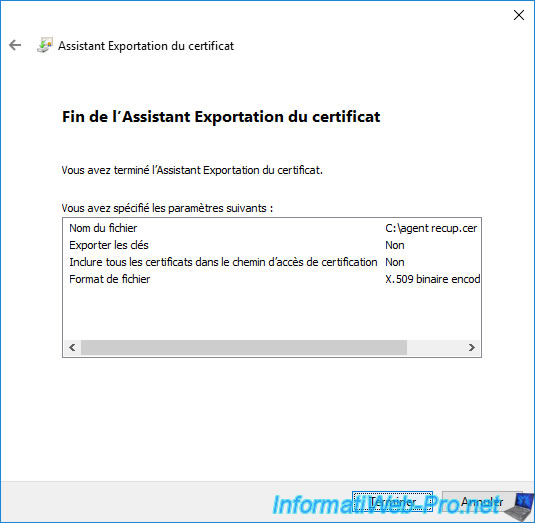
The "The export was successful" message appears.
Click OK.
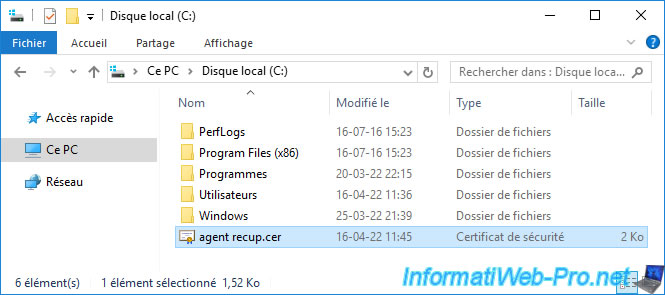
The certificate was exported under the name "agent recup.cer" (in our case).
6.4. Import recovery agent certificate into user certificate store
Now that you have retrieved your recovery agent certificate, log out and log back in with the affected user (IWAgentRecup in our case).
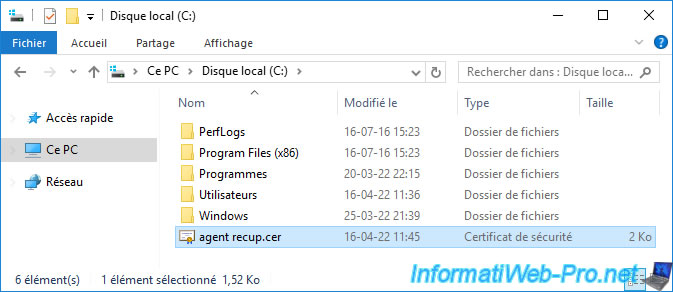
Double-click on the "agent recup.cer" certificate exported earlier.
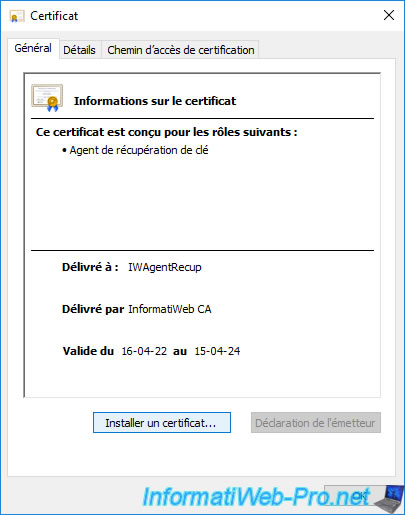
The certificate appears.
Click on : Install a certificate.
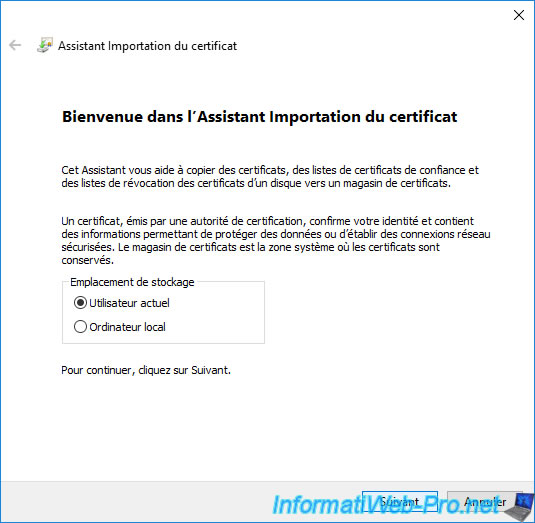
The certificate import wizard appears.
Select "Current User" for the storage location since a recovery agent is a user, then click Next.
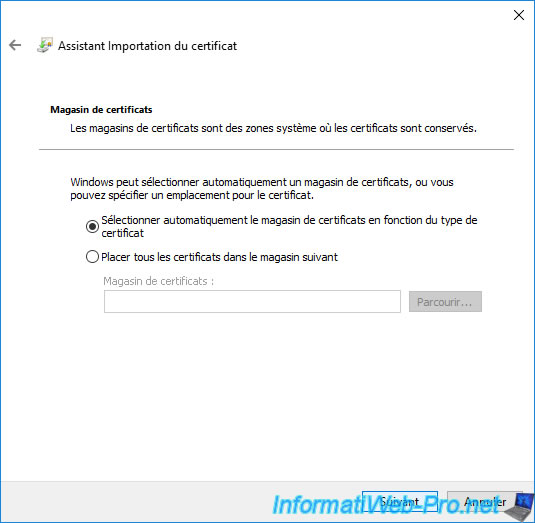
Leave the "Automatically select the certificate store ..." option selected and click Next.
Note : the certificate store that will be automatically selected in this case will be "Personal".
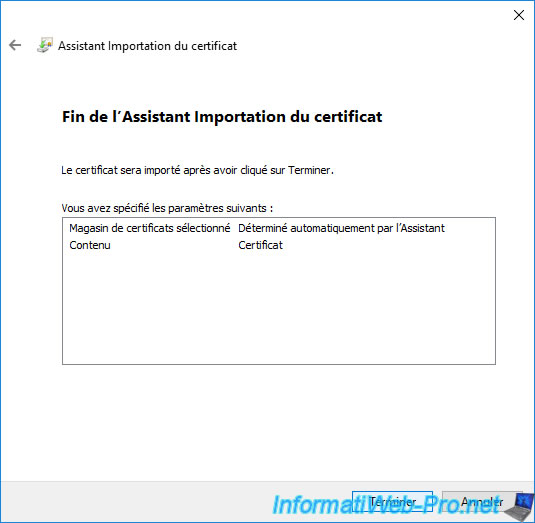
Click Finish.
The "The import was successful" message appears.
Click OK.
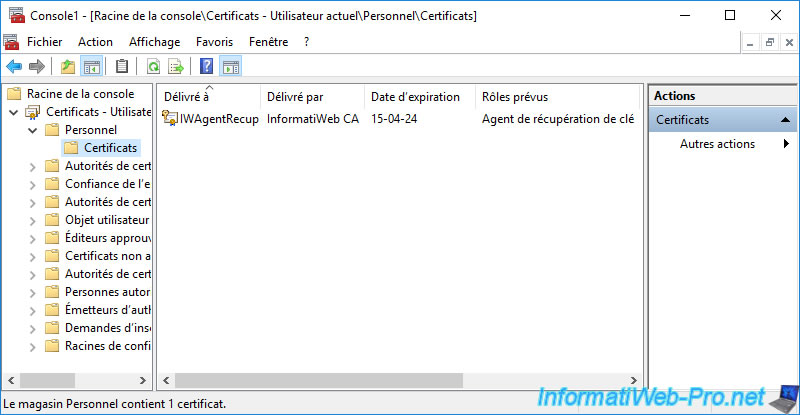
Open a "mmc" console and add the "Certificates" component for the current user.
Then, in the "Personal" certificate store, you will see that a new Key Recovery Agent certificate has appeared.
Also, if you look at the icon of this certificate, you will see that the private key associated with it is also present. Although it was not in the certificate in ".cer" format that you just imported.
Indeed, since the certificate had been requested from the same server, the associated private key could be automatically reassociated with the imported certificate since there is always an unique mathematical link between a public key and a private key.
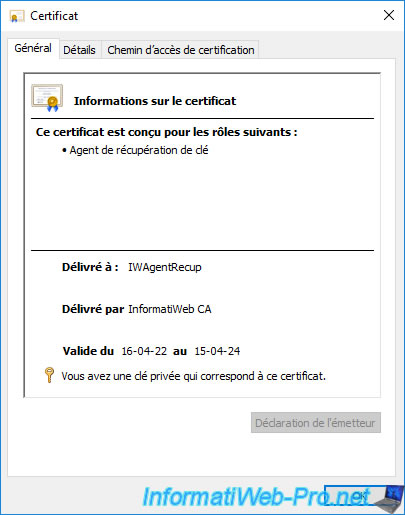
If you double click on this certificate, you will see that the private key associated with it is also present.
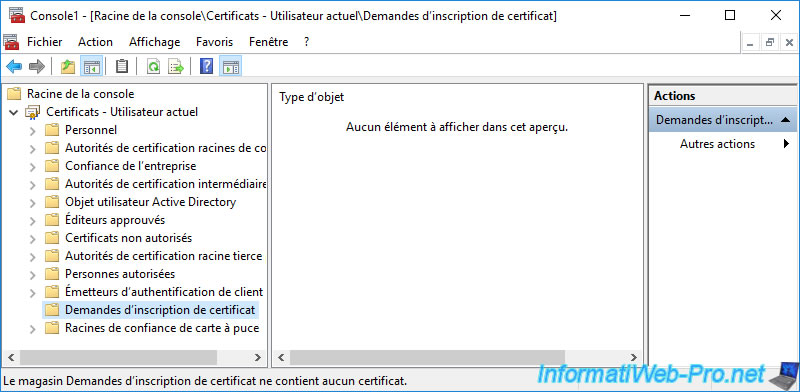
Now, if you go back to the "Certificate Enrollment Requests" folder, you will see that it's empty.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment