Create a site-to-site (S2S) VPN tunnel via PPTP/L2TP on Windows Server 2022, 2016 and 2012
7. Allow ping on your VPN servers
To test the connectivity between your VPN servers, and then the routing of packets from client PCs to the remote network, we'll use the Windows "ping" command.
However, ping is blocked by default in Windows Server.
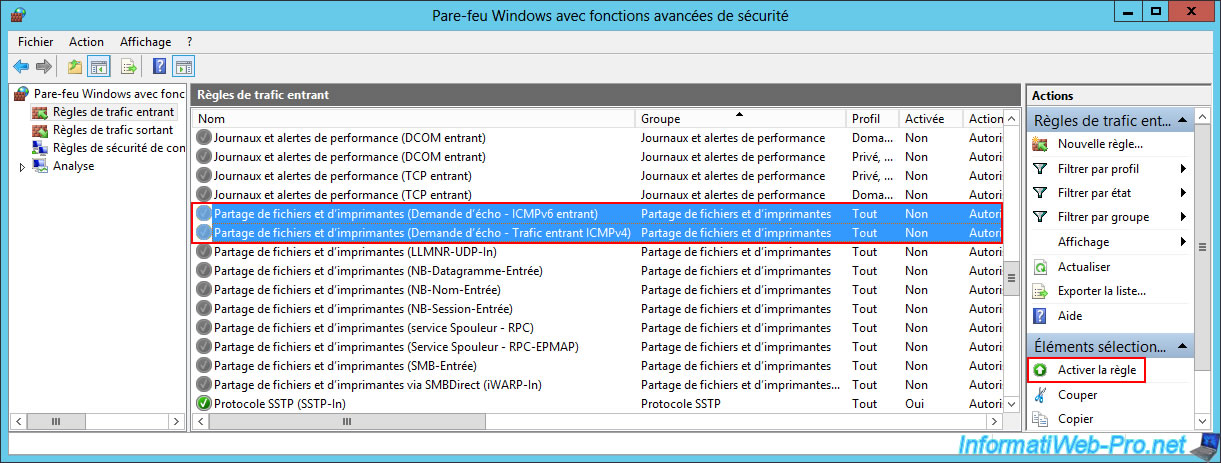
Warning : on both VPN servers, go to the advanced settings of the Windows Firewall and enable these rules:
- File and Printer Sharing (Echo Request - ICMPv4-In).
- File and Printer Sharing (Echo Request - ICMPv6-In).
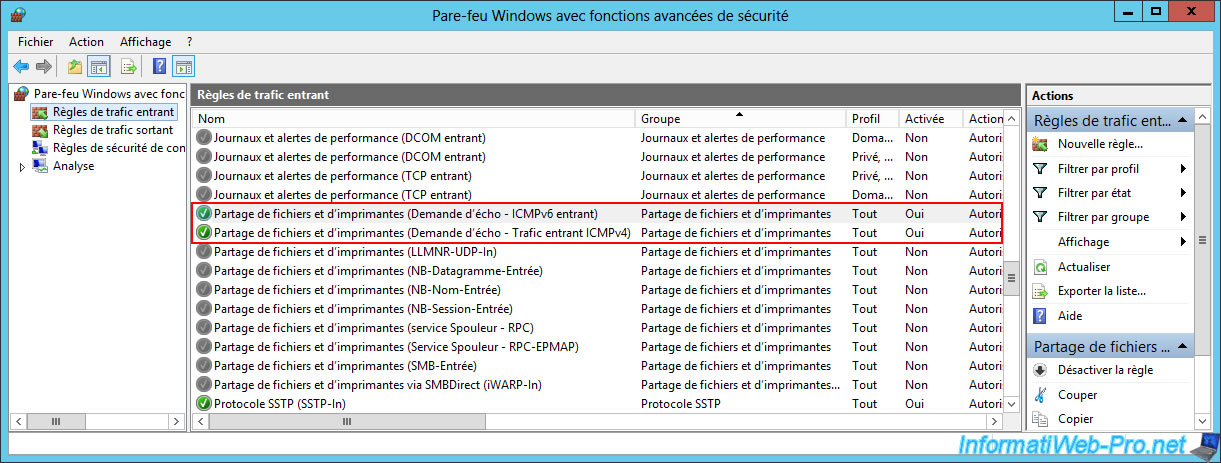
Once these rules are enabled, the icon in front of these rules will turn green.
8. Establish site-to-site VPN connections (VPN tunnels)
8.1. Connect site 1 (Brussels) to site 2 (Paris) via a site-to-site VPN tunnel
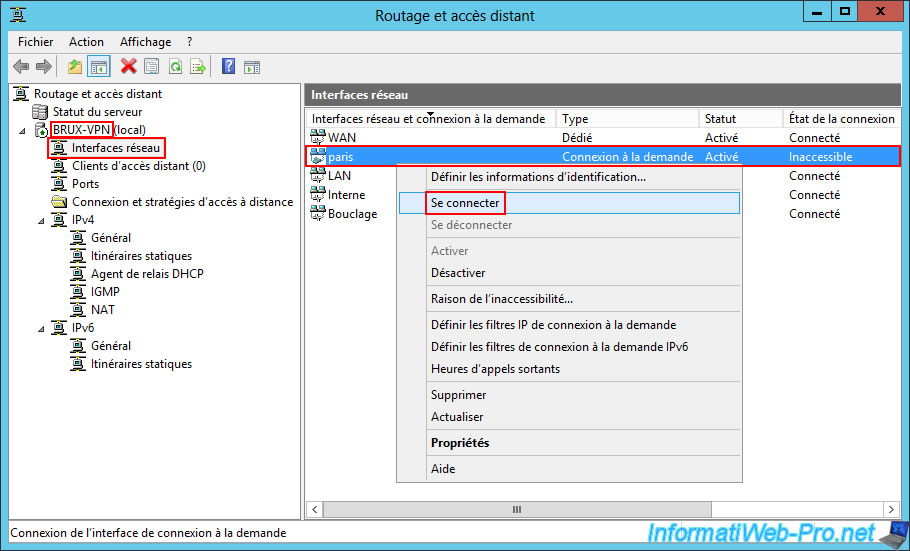
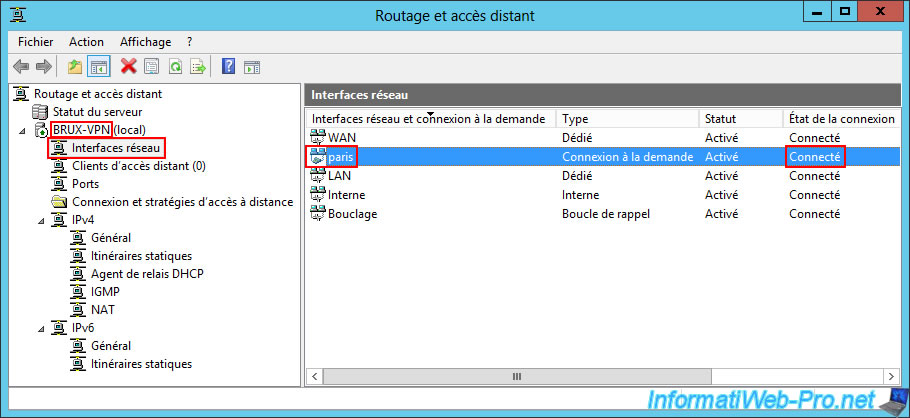
On your VPN server "BRUX-VPN" of site 1 (Brussels), go to the "Network interfaces" section and right-click "Connect" on your on-demand connection interface (in our case "paris").
Please wait a few seconds while connecting to the remote site.
If everything is configured correctly, the connection status will be "Connected".
8.2. Connect site 2 (Paris) to site 1 (Brussels) via a site-to-site VPN tunnel
Similarly, go to the "Network Interfaces" section of your VPN server "PARIS-VPN" of site 2 (Paris) and right-click "Connect" on your "brux" on-demand connection interface.
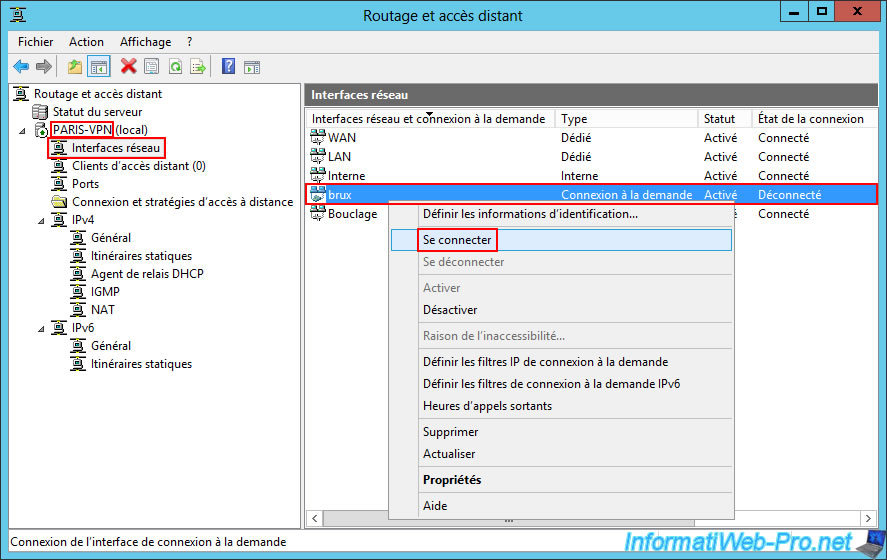
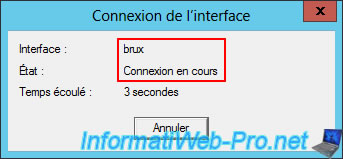
Please wait a while while the VPN connection with the remote site is established.
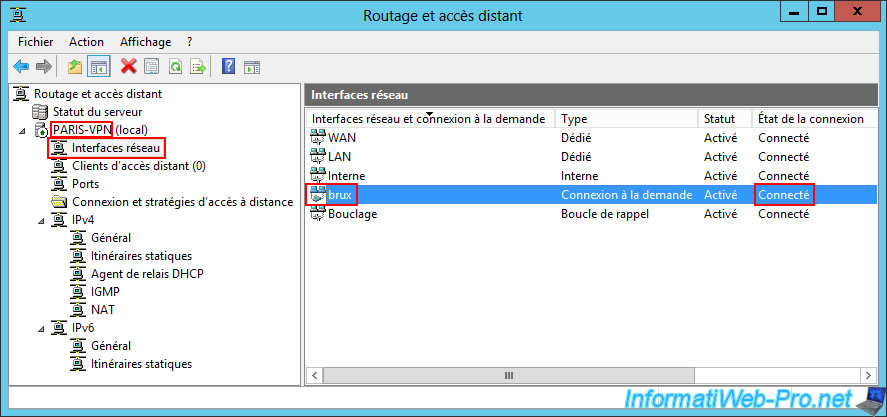
If your configuration is correct, the connection status will be "Connected".
8.3. VPN ports used for your site-to-site VPN connections
Refresh the console on your two VPN servers (using the "F5" key or the fifth icon in the console toolbar), then go to the "Remote Access Clients" section on the VPN server at Site 1 (Brussels).
In this "Remote Access Clients" section, you can see that the user "parisuser" (used by the on-demand connection from the remote site (Site 2 (Paris)) has logged in with the user account "parisuser" located on your VPN server "BRUX-VPN".
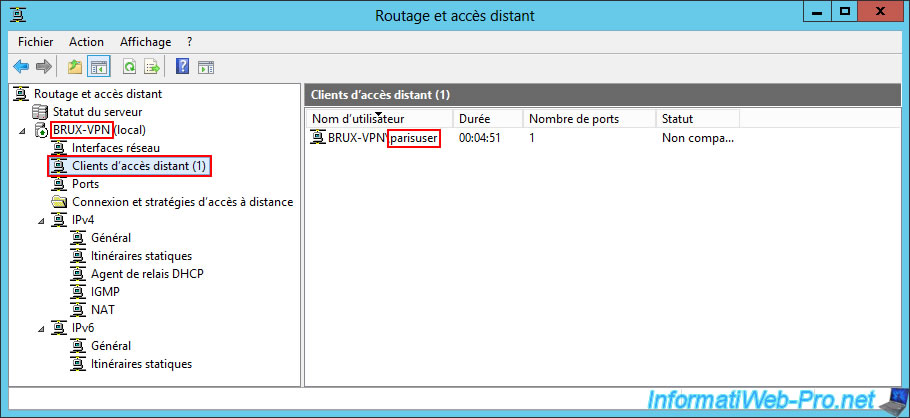
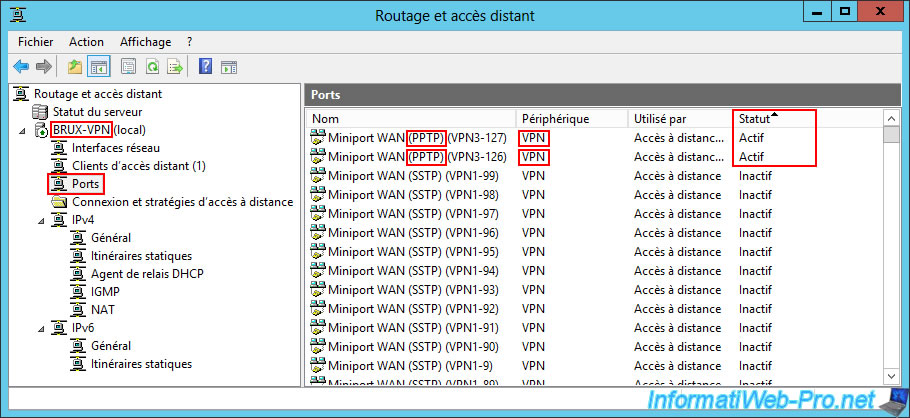
In the "Ports" section, if you sort the list by "Status", you will be able to see that the VPN protocol "PPTP" is used for the VPN tunnel established by Paris with your VPN server "BRUX-VPN" in Brussels.
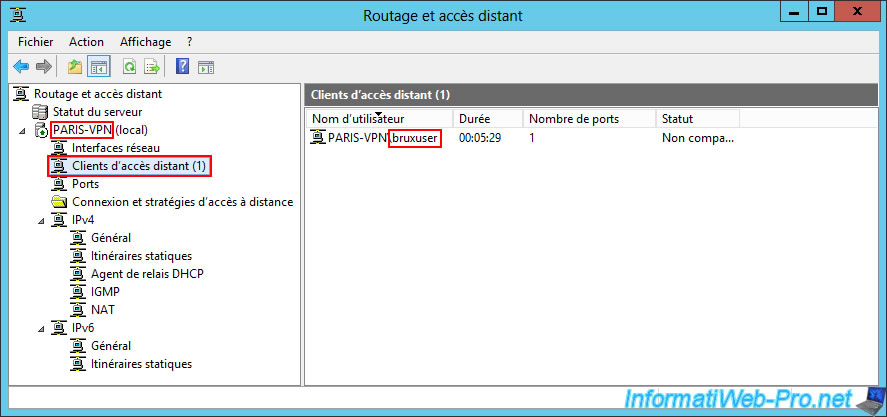
Similarly, on the remote VPN server "PARIS-VPN", you will be able to see that the Brussels site has connected to your Paris site with the user account "bruxuser" present on your VPN server "PARIS-VPN".
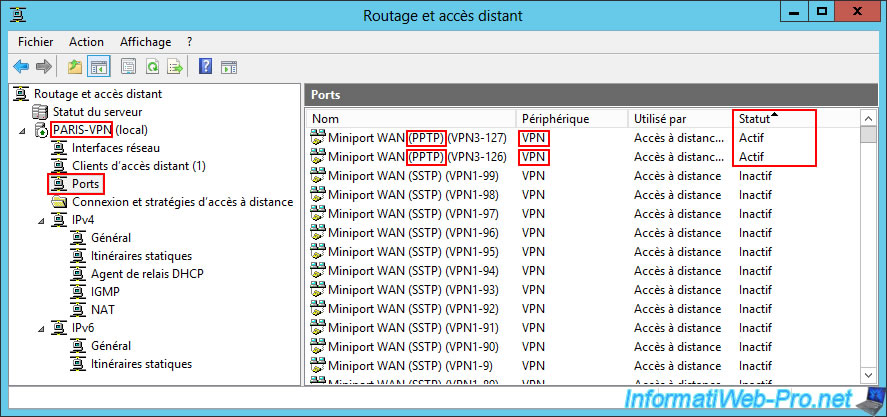
In the "Ports" section of this remote VPN server "PARIS-VPN", sort the list again by "Status" and you will be able to see that the VPN protocol used is again "PPTP".
9. Test connectivity between your physical sites (between VPN servers and from client PCs)
To verify that everything is configured correctly, whether it's the VPN tunnel or routing from machines on the local network (at the source or destination site), the best way is to test connectivity with the ping command from your VPN servers, as well as from a client PC at each physical site.
By testing connectivity from a VPN server, you are primarily testing the VPN tunnel.
Whereas, by testing connectivity between a client PC and the remote VPN server, you are also testing the network packet routing that each VPN server must perform correctly (which should be the case if you have followed our tutorial carefully).
As you can see, in our case, our Brussels VPN server "brux-vpn" can communicate without any problems with itself (10.0.1.10), but also with the remote Paris VPN server "paris-vpn" (10.0.2.10).
Batch
ping 10.0.1.10
Plain Text
Reply from 10.0.1.10: bytes=32 time<1ms TTL=128
...
Packets: Sent = 4, Received = 4, ...
Batch
ping 10.0.2.10
Plain Text
Reply from 10.0.2.10: bytes=32 time<1ms TTL=127
...
Packets: Sent = 4, Received = 4, ...
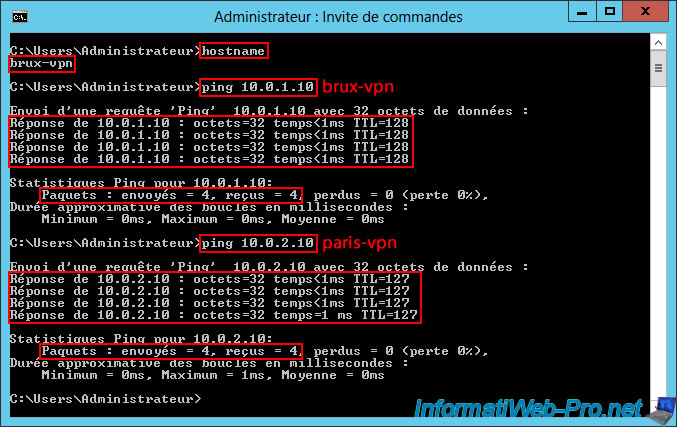
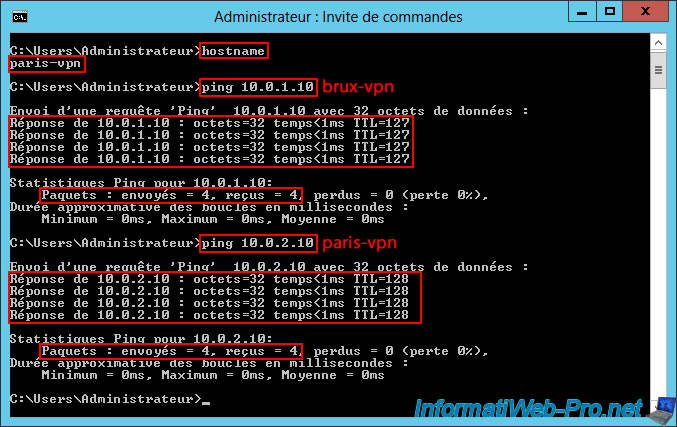
Conversely, our Paris VPN server "paris-vpn" can communicate seamlessly with the remote Brussels VPN server "brux-vpn" (10.0.1.10), as well as with itself (10.0.2.10).
This confirms that both VPN tunnels are functional between your two VPN servers.
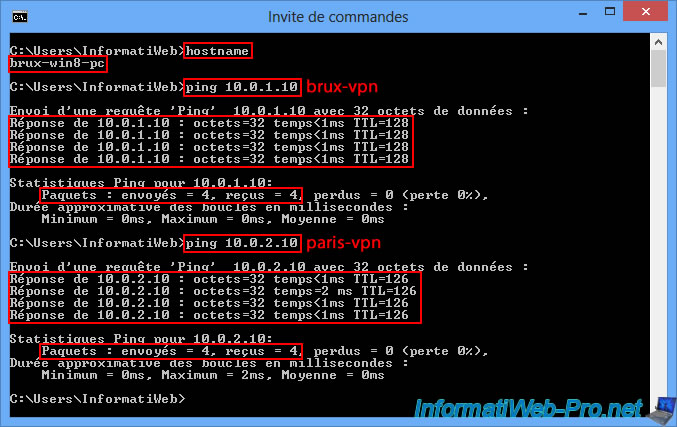
Now, test the connectivity between a client PC at Site 1 (Brussels) and your two VPN servers.
As you can see, our client PC "brux-win8-pc" at Site 1 (Brussels) can communicate without any problems with the VPN server "brux-vpn" (10.0.1.10) located at the same site, as well as with the VPN server "paris-vpn" at the remote site in Paris.
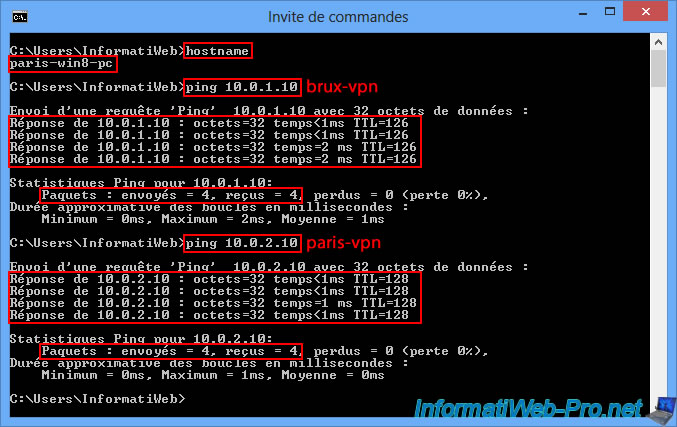
Conversely, our client PC "paris-win8-pc" at site 2 (Paris) can communicate without any problems with the remote VPN server "brux-vpn" (10.0.1.10) in Brussels, as well as with the VPN server "paris-vpn" (10.0.2.10) at the local site where it is located.
If all pings from your client PCs to your VPN servers are working, this confirms that your two VPN servers are correctly routing packets between each LAN network and the remote network (via each VPN tunnel).
Share this tutorial
To see also
-

Windows Server 4/28/2012
WS 2003 - NAT and network routing
-

Windows Server 8/8/2012
WS 2008 - NAT and network routing
-

Windows Server 4/22/2015
WS 2012 - NAT and network routing
-
Windows Server 11/23/2017
WS 2012 / 2012 R2 - Dynamic routing (RIPv2)

No comment