Create an enterprise root certification authority (Root CA PKI) on Windows Server 2012 / 2012 R2
- Windows Server
- AD CS
- 04 January 2015 at 10:57 UTC
-

- 3/4
New tutorial available for Windows Server 2016: WS 2016 - AD CS - What is a CA and install an enterprise CA.
7. Install the web interface of the certification authority
Now that your authority is working properly, we will configure the certificate revocation system. This system allows you to invalidate a certificate for one reason or another.
For now, your CA publishes revocation list, but only via LDAP protocol.
The problem is that the server is the only one able to access to Active Directory (LDAP) by this protocol. To resolve this issue, simply publish these revocation lists for the http protocol (Web).
Caution : When we will have configured the certificate revocation system, you will have to recreate your certificates. Why ? Because the links to the revocation lists are included in the certificates when signed by your certification authority.
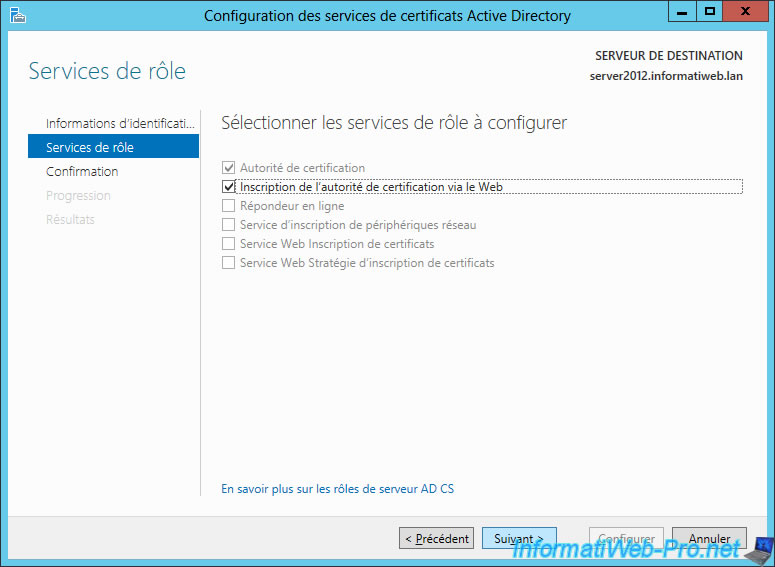
To publish the revocation lists for the HTTP protocol, we will install the feature "Certification Authority Web Enrollment" of the "Active Directory Certificate Services" role.
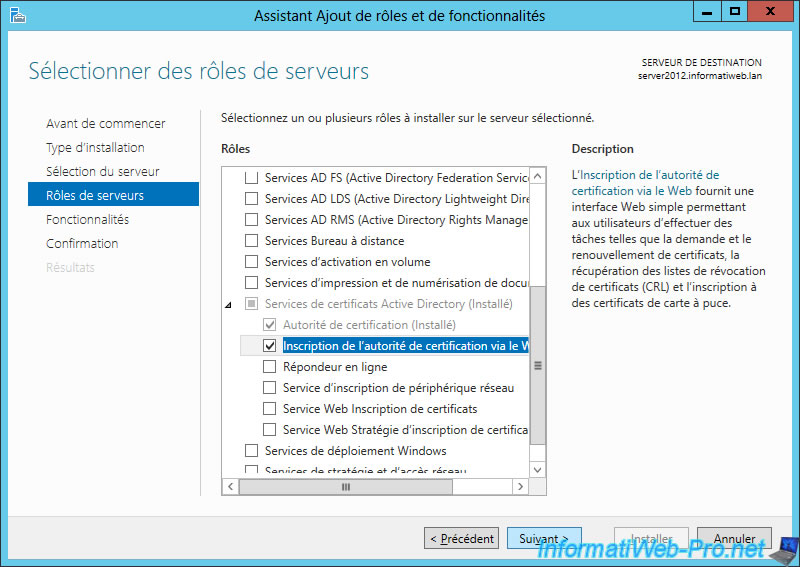
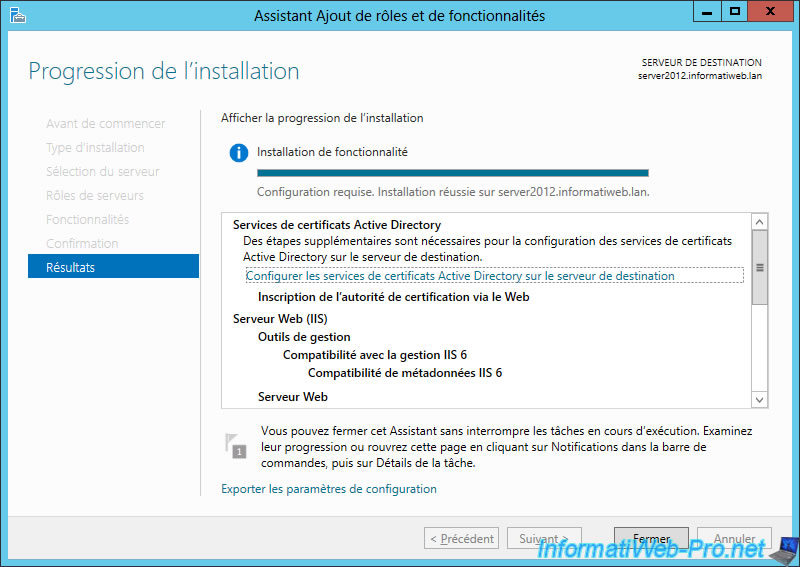
At the end of the installation, click on the "Configure Active Directory Certificate Services ...".
Click Next.
Check the "Certification Authority Web Enrollment" box.
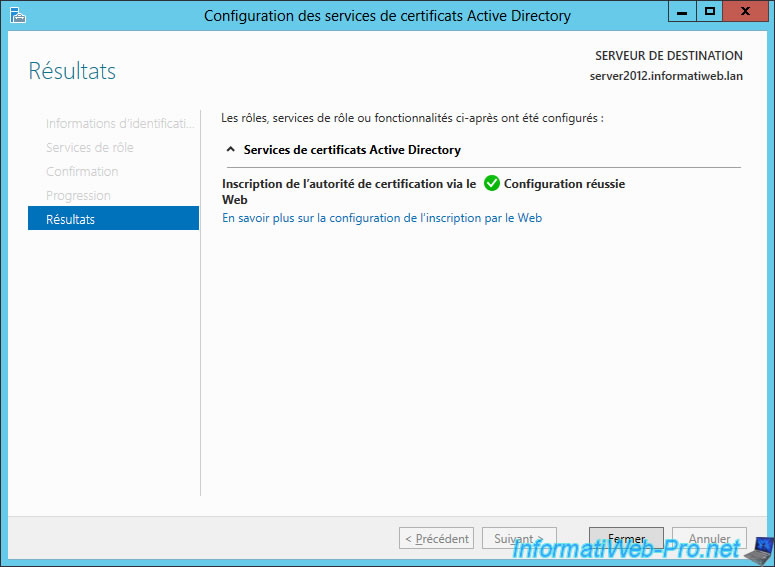
The authority web inteface is installed.
8. Overview of the certification authority web interface
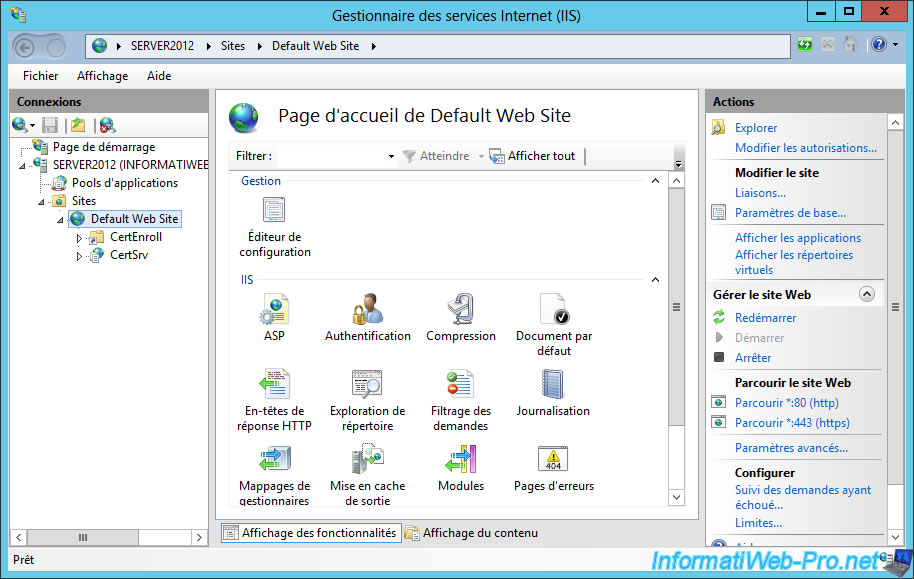
The installation of the certification authority web interface, created two folders in the default site :
- CertEnroll : Contains revocation lists (for file and http protocol)
- CertSrv : The web interface of the certification authority.
Access the web interface, by accessing the address "https: //domain.ext/CertSrv" and log in with the Administrator account.
In this web interface, you can :
- Request a certificate : For copy / paste a certificate request to be signed by the CA.
- View the status of a certificate request : Only concerns the standalone certification authority (so it doesn't concern us)
- Download a CA certificate ... : Allows you to download the certificate of your authority, the authority certificate chain (if you created a secondary authority instead of a root CA) and lists revocation (base + the delta lists).
Click on "Download a CA certificate ...".
Confirm access.
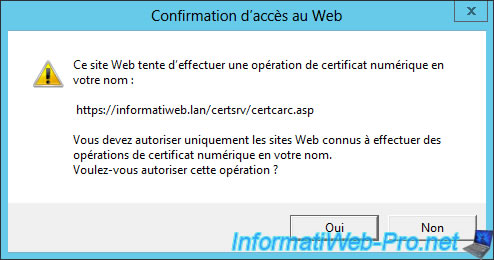
On this page, you can download the certificate of your authority to add it to the trusted authority of client computers.
For this, read this : Import a certificate (of a root certification authority) in the trusted certificates list of Windows
For the "CertEnroll" folder, select this folder on the left, then, click on "Explore" in the right column.
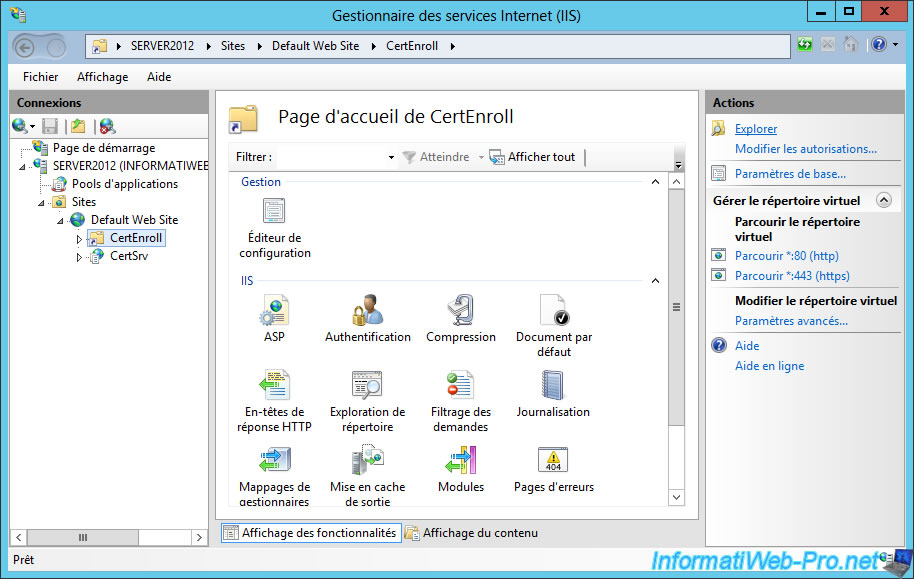
As you can see, this file contains :
- The base of revocation list (informatiweb-SERVER2012-CA.crl).
- The delta revocation lists (informatiweb-SERVER2012-CA+.crl). These are the updates to the list of revocations.
- An .asp file. This is a script created for the IIS server (ASP .Net language being used with the IIS server).
- The certificate of your certification authority (server2012.informatiweb.lan_informatiweb).
9. Configuring HTTP and File protocols for revocation lists
To configure the protocols to use for revocation lists, launch the "Certificate Authority" (or certsrv) program.
Then, right-click on the name of your authority and click on "Properties".
As you can see, by default, certificate revocation lists are only available for the "ldap" protocol.
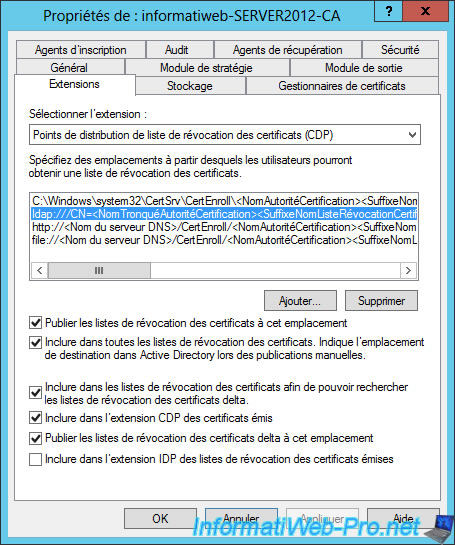
But not for the "HTTP" and "File" protocols.
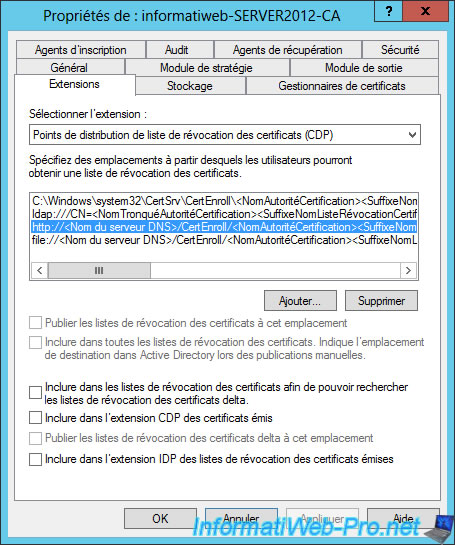
To fix this problem, check all possible boxes except the last one (because it isn't checked for the ldap protocol).
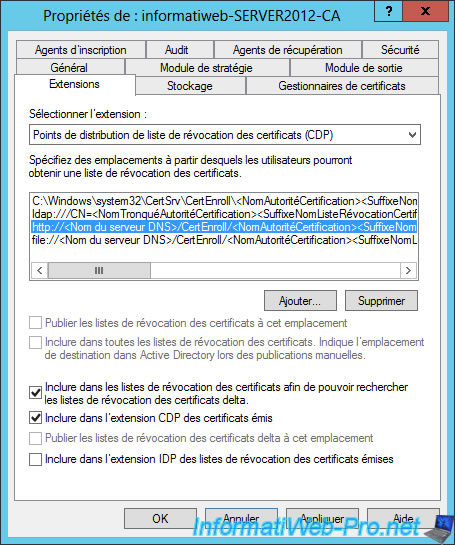
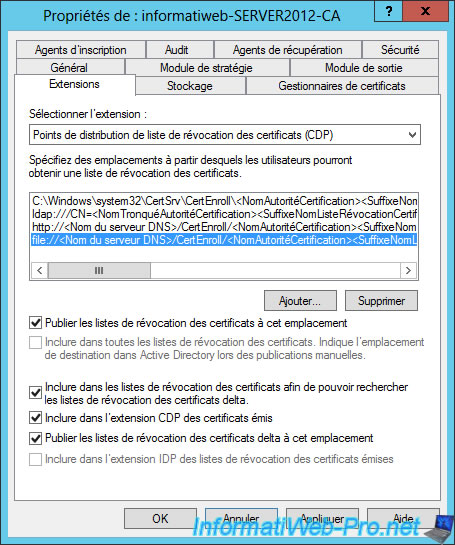
Same for the "File" protocol.
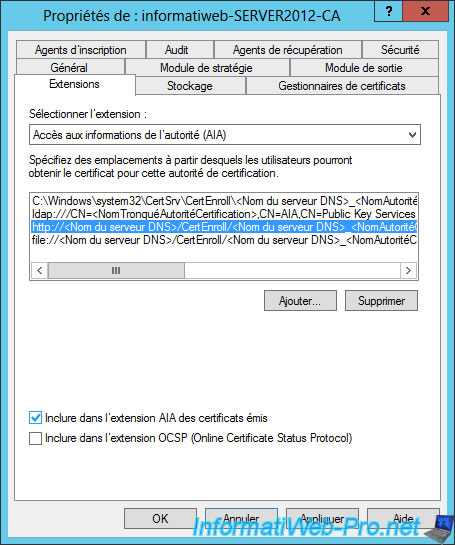
Then, select "Authority Information Access (AIA)." As you can see, the information of the CA are only available via the "ldap" protocol but not for others.
Access to this information enables customers, to know whether the authority is valid (validity dates, ...).
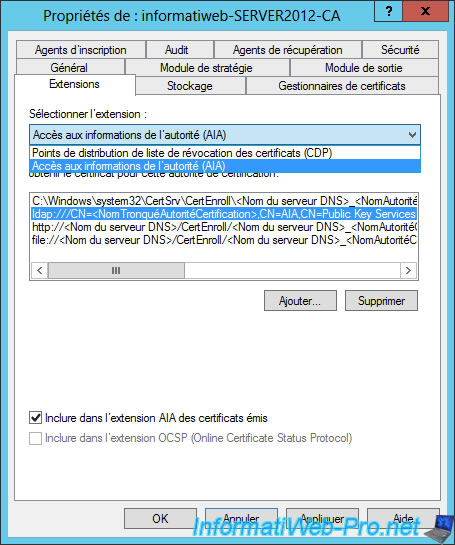
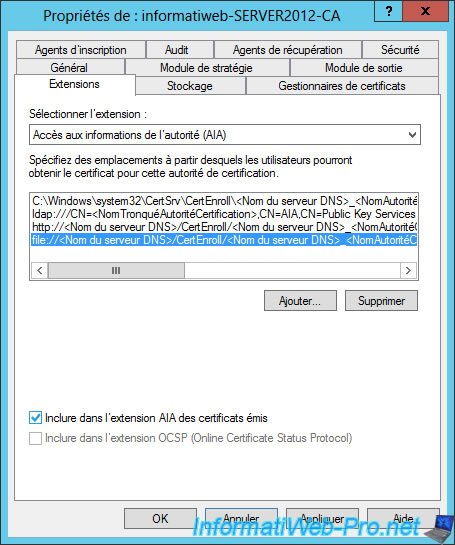
Check the "Include in the AIA extension of issued certificates" for protocols "http" and "file".
Then, click "OK".
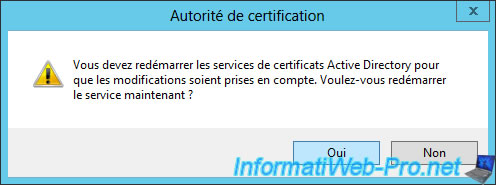
The authority must be restarted. Click Yes.
Share this tutorial
To see also
-

Windows Server 12/15/2023
WS 2016 - AD CS - Fix the issue of an expired CRL on a root CA (0x80092013)
-
Windows Server 12/8/2023
WS 2016 - AD CS - Install and configure a root CA and a secondary CA
-

Windows Server 10/20/2023
WS 2016 - AD CS - Publish CRLs accessible via the web (HTTP)
-
Windows Server 9/29/2023
WS 2016 - AD CS - What is a certificate template ?

No comment