Create an enterprise root certification authority (Root CA PKI) on Windows Server 2012 / 2012 R2
- Windows Server
- AD CS
- 04 January 2015 at 10:57 UTC
-

- 4/4
New tutorial available for Windows Server 2016: WS 2016 - AD CS - What is a CA and install an enterprise CA.
10. Revoke a certificate
To start, revoke the old certificate using the "Web Server" model.
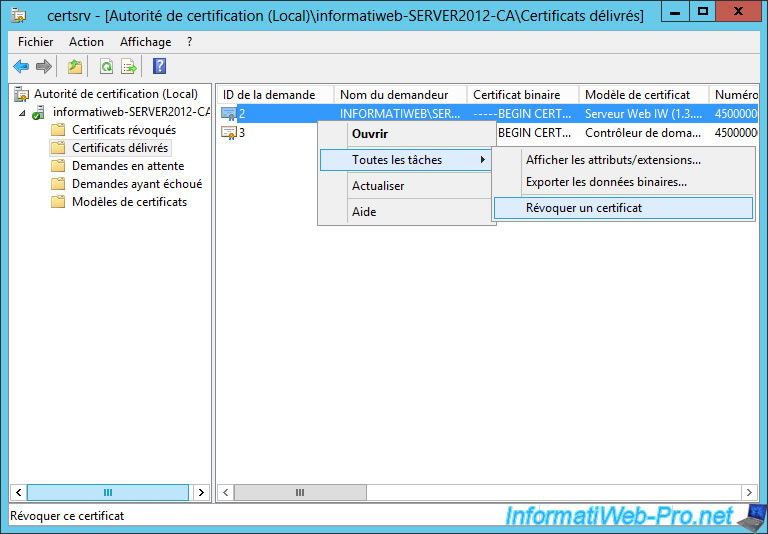
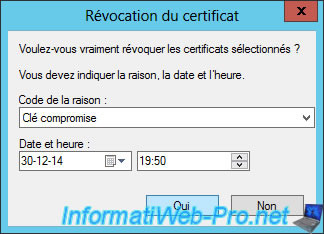
Select a reason and click "Yes".
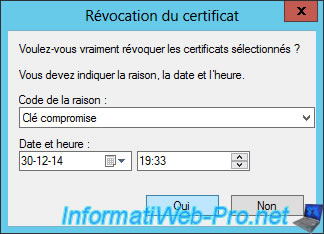
Now, the certificate is displayed in the revoked certificates list. To allow clients to know if this certificate is revoked, you must publish the list of revoked certificates.
Note : When a certificate is expired, it appears in this list.
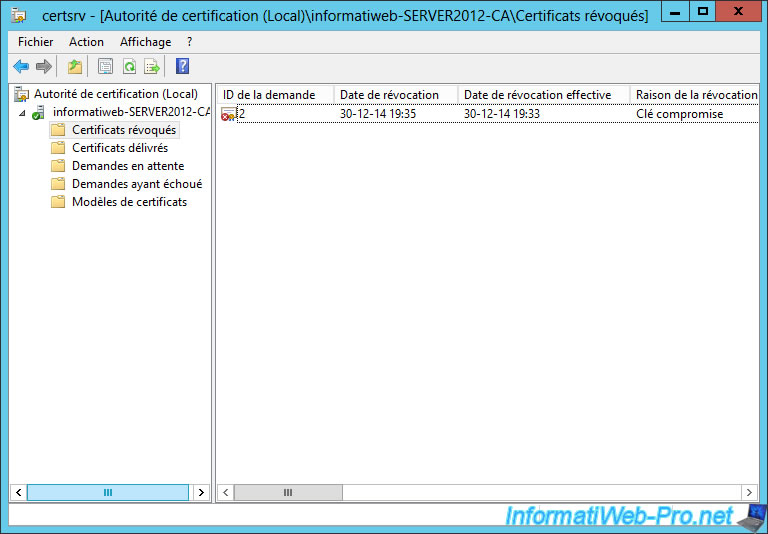
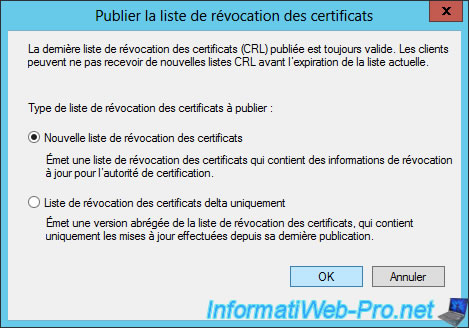
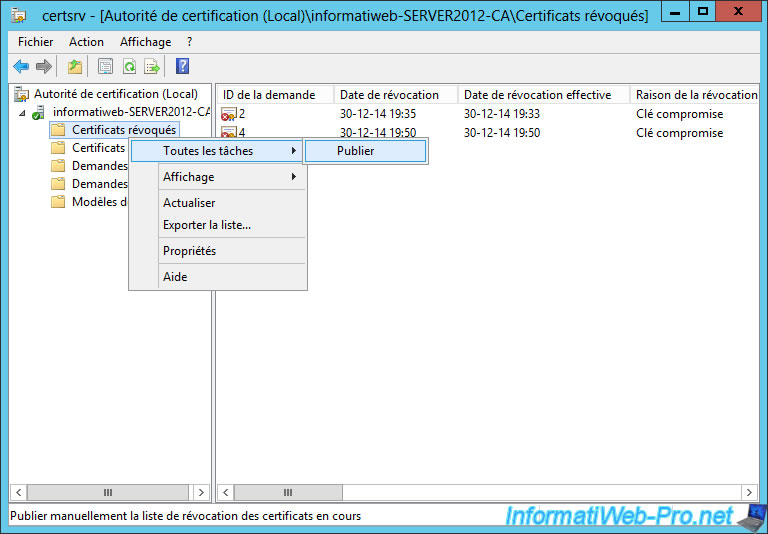
To do this, right click on "Revoked Certificates" and click "All Tasks -> Publish."
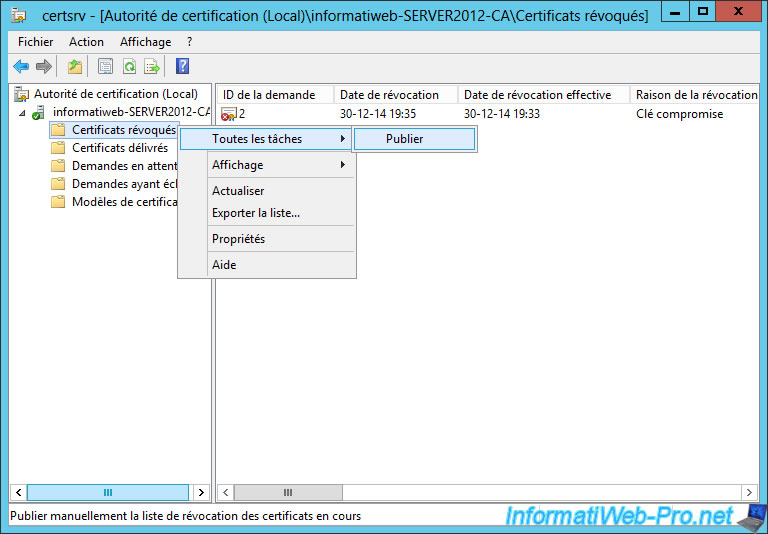
When the list of revoked certificates is small, select "New certificate revocation list".
Once you have revoked a lot of certificates, you choose "Certificate Revocation List delta only."
As mentioned at the beginning of this page, the old certificates should be recreated because the revocation lists are indicated only for the ldap protocol.
The server has access to revocation lists via this address but clients of your server will not have access to it.
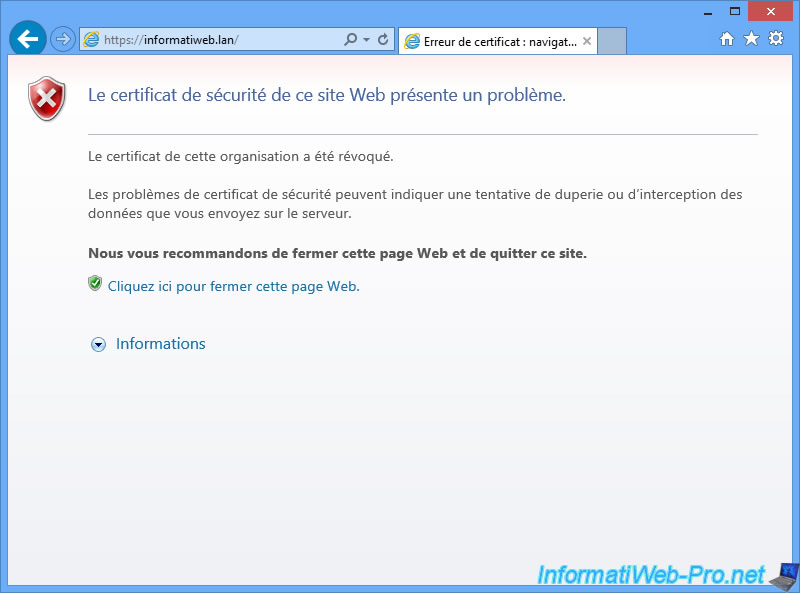
To illustrate this problem, we tried to access the site on the server and a client. The server displays the error message "This organization's certificate has been revoked".
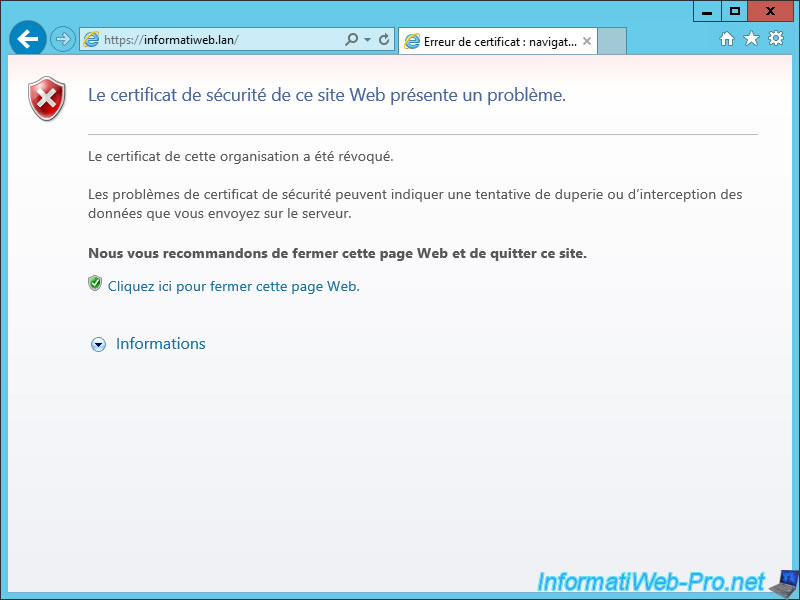
But, the client accesses the website despite that the certificate is revoked.

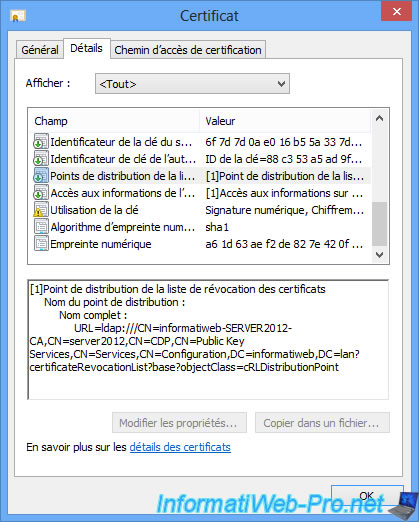
If you click on the "View Certificates" link and you go to the "Details" tab, you will see that only the ldap address is in this old certificate.
11. Request a new certificate
So that three protocols are specified in the certificate, simply redo a certificate request.
To do this, refer to the section "4. Request a certificate" of this tutorial.
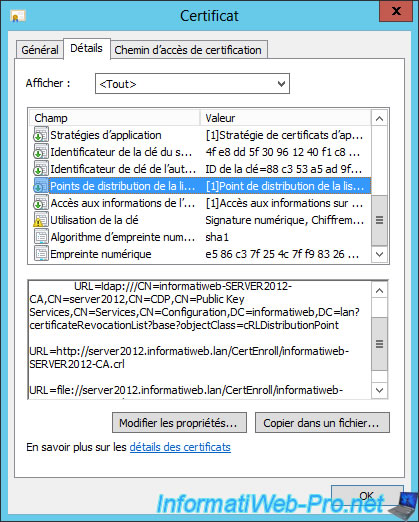
After creating the certificate, double-click on it and go to the "Details" tab. Now, certificate revocation lists (Point distribution of revocations list) are available for 3 protocols (ldap, http, and file).
Don't forget to replace the old certificate of IIS with the new certificate.
To do this, run "Internet Information Services Management" (IIS), select the default website and click on "Bindings" in the right colum.
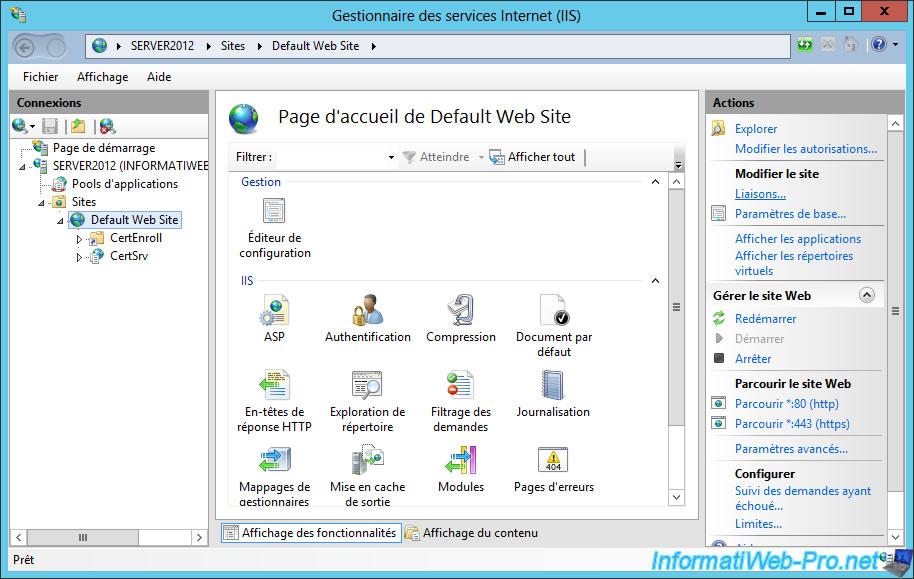
Select "https" and click "Edit".
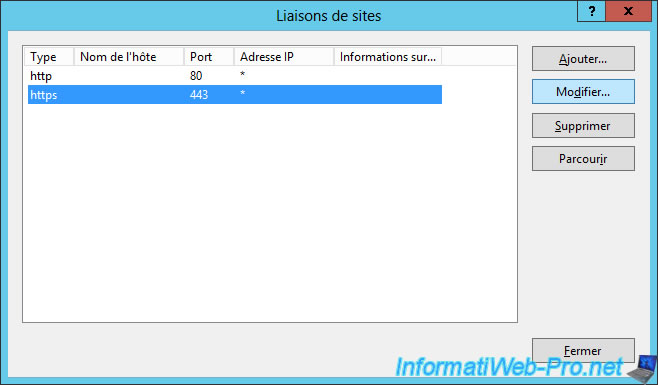
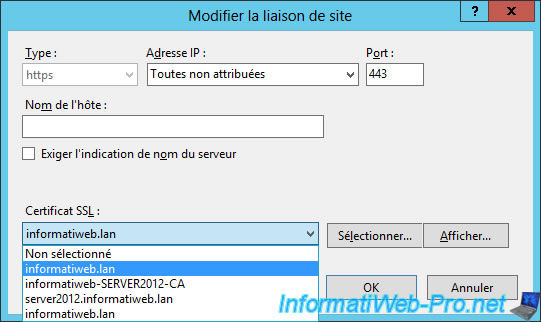
Select the new certificate in the list.
Note : don't fool you, select one certificate and click on "Show". Then, look in the "Details" tab to check that the certificate contains the 3 protocols for revocation lists.
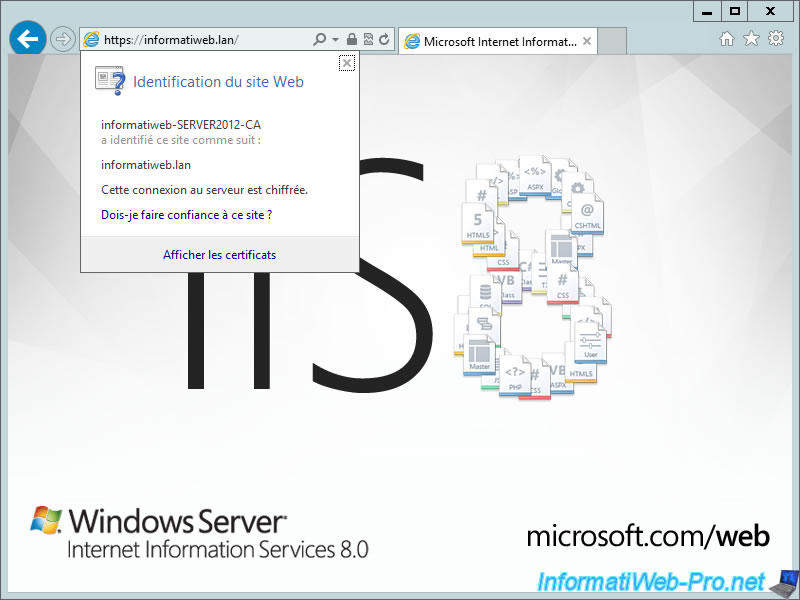
The new certificate is valid on the server and clients.
12. Revoke the new certificate
Now that we have add the "http" protocol for revocation list in our new certificate, we will try to revoke it.
Note : The revocation of the certificate will work for everyone (server and clients).
For this, select the new certificate (based on the "Web Server" model), right-click on this certificate and click "All Tasks -> Revoke Certificate".
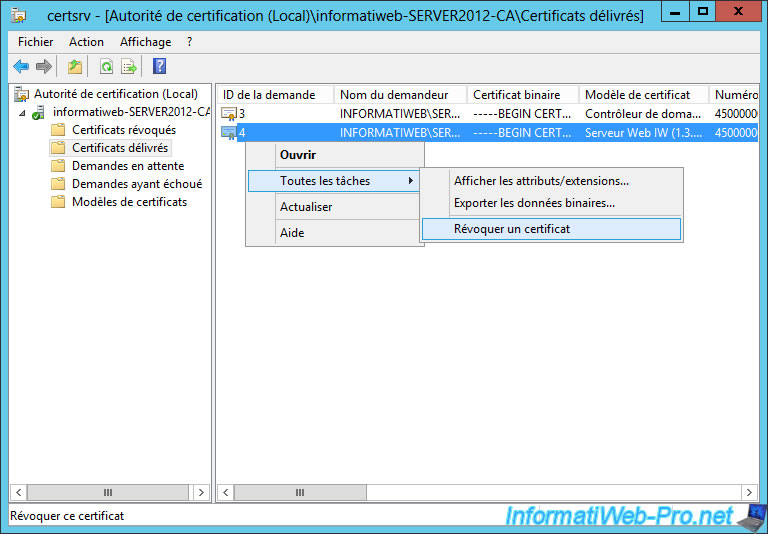
Choose a reason and click "Yes".
Publish the new list of revoked certificates.
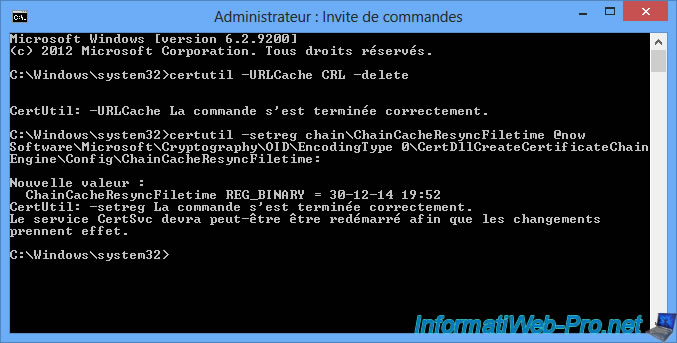
For this test to be correct, we will clear the cache of Windows revocation lists.
This will avoid you from having a revoked certificate that is not recognized as revoked.
To do this, type these two commands in a "Command Prompt" launched as administrator.
Clear the CRL (certificate revocation lists) cache of the HDD.
Batch
certutil -URLCache CRL –delete
Invalid the use of CRL cached in memory and the hard drive.
Batch
certutil –setreg chain\ChainCacheResyncFiletime @now
Source : blogs.technet.com.
Now, your web browser (on the server and clients) will display the error message "This organization's certificate has been revoked".
Note : The revocation of a certificate blocks access to websites affected by this certificate.
Share this tutorial
To see also
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them
-
Windows Server 11/24/2023
WS 2016 - AD CS - Install and configure CEP and CES servers
-

Windows Server 10/6/2023
WS 2016 - AD CS - Install the web interface of a certificate authority (CA)
-
Windows Server 9/29/2023
WS 2016 - AD CS - What is a certificate template ?

No comment