- Windows Server
- 03 November 2023 at 09:52 UTC
-

- 1/2
When issuing certificates for different services and/or users, it may be necessary to be able to revoke (invalidate) a certificate before its expiration date.
- What is revocation ?
- Issues with using revocation lists
- Valid certificate used
- Revoke a certificate
- Publish a revocation list (CRL)
- Force the update of the revocation cache of the client PC
- Publish a delta revocation list (delta CRL)
1. What is revocation ?
Revoking a certificate allows it to be invalidated before its expiration date.
Thus, if you know that a hacker has potentially been able to recover a certificate (as well as its private key) which was on a server or a computer, you have the possibility of revoking it so that it's no longer valid.
Thus, access to the service that was protected with this certificate will be completely blocked.
If it was a user certificate, the user will no longer be able to authenticate using this certificate.
When you revoke a certificate (from the "Certification Authority" console), the serial number of this certificate is added to a revocation list (CRL) or to a delta revocation list (delta CRL).
As you will see in this tutorial, revocation lists (CRLs and delta CRLs) are published periodically and you can also publish these manually if you wish.
By default, these revocation lists are published in the Active Directory and any server or computer member of your Active Directory domain can therefore access them (in the company) via the "ldap" protocol.
Note that the "Issue and Manage Certificates" permission is required to be able to revoke certificates.
2. Issues with using revocation lists
2.1. Revocation support required
To begin, an application may not function properly if revocation lists are not accessible.
Indeed, for security, the application chooses not to work to be sure that a revoked certificate can't be used (by a hacker, for example).
This is notably the case of Citrix XenApp.
2.2. Application may not support revocation
This is rather rare, but it's possible that an application doesn't support revocation.
In other words, as long as the certificate is valid for the server, computer or user concerned, it will work. And if you revoke this certificate, the certificate will continue to be "valid" in this specific case since the application will not check if it has been revoked in the meantime.
This is notably the case of the EFS file system (Encrypting File System) which doesn't support revocation during file encryption.
However, revocation is checked by EFS when you attempt to share an encrypted file with other users.
2.3. Unable to access revocation lists
If an application secured using one of your certificates can't access your certificate authority's revocation lists, it's possible that the application refuses to work in this specific case as a security measure.
Indeed, since the application is unable to verify whether or not this certificate has been revoked by your certification authority, it prefers to stop working to prevent you from connecting to a server compromised by a hacker (for example).
As explained previously, by default, these revocation lists are accessible via the "ldap" protocol (in other words : from your Active Directory infrastructure).
If you use a portable PC and leave the company with it, you will not be able to access these revocation lists via the "ldap" protocol.
To solve the problem, you will have to add the "HTTP" protocol with an address that is always accessible by your client computers for access to the revocation lists (CRL and CRL delta) of your certification authority.
2.4. Revocation list caching and latency
As you will see in this tutorial, by default, revocation lists (CRLs) are published weekly and a delta revocation list (delta CRL) is published daily.
Which means that there will always be a delay between the moment you revoke a certificate and the moment when the serial number of this certificate appears in a revocation list (CRL) or a delta revocation list (delta CRL).
In addition, when a client workstation checks the revocation of a certificate, it downloads a copy of your revocation lists (CRL and CRL delta) and it keeps these copies in cache for a certain time (delay = at the frequency of publication of these revocation lists).
This means that there may also be a delay between the moment when the serial number of the revoked certificate has been added to a revocation list (CRL or CRL delta) and the moment when the client becomes aware of this revocation.
Note that you can force the revocation check by clearing the revocation cache of the client workstation by running the command :
Batch
certutil -setreg chain\ChainCacheResyncFiletime @now
The use of the client-side cache allows you not to saturate the bandwidth of your certification authority by avoiding re-downloading your revocation lists each time your client workstation must check the revocation of one of your certificates.
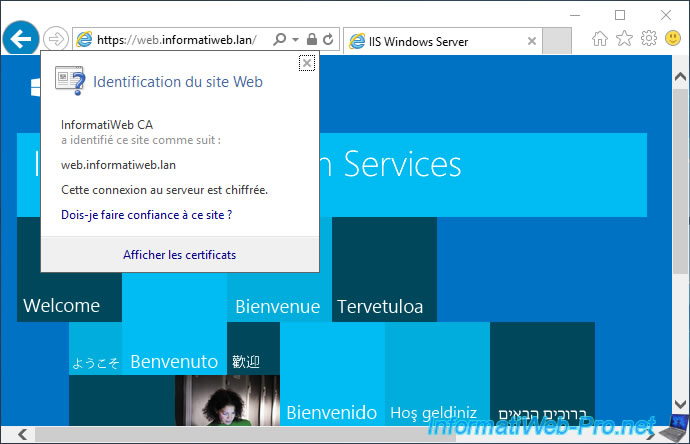
3. Valid certificate used
To start, we secured an IIS web server with a valid certificate from our certification authority.
4. Revoke a certificate
To revoke a certificate, open the "Certification Authority" console, go to the "Issued Certificates" section and locate the desired certificate.
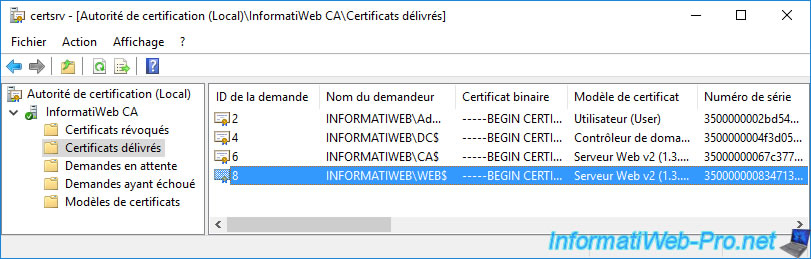
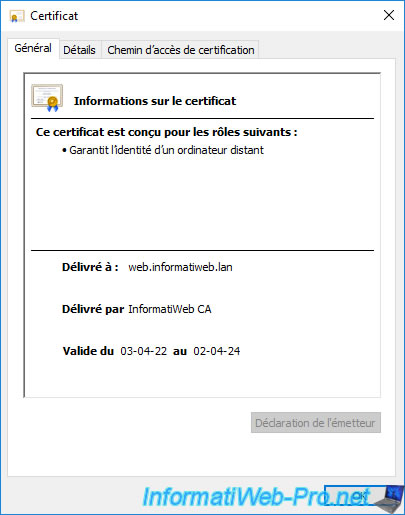
If needed, double click on it to get more information about it.
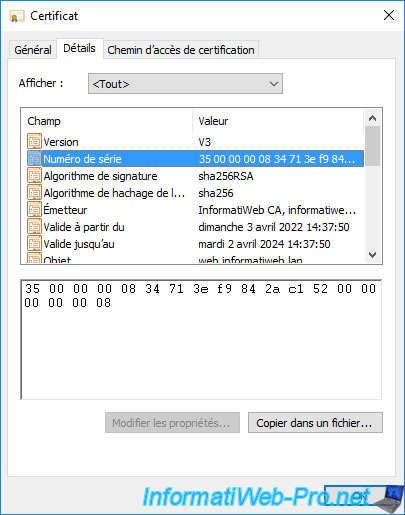
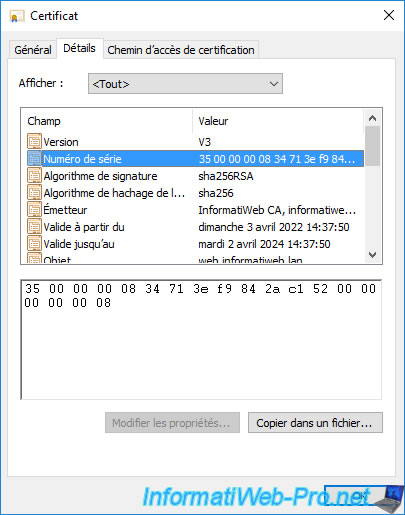
You can also check its serial number in the "Details" tab to be sure that it's the correct certificate.
Once you find the certificate you want to revoke, right click "All Tasks -> Revoke Certificate" on it.
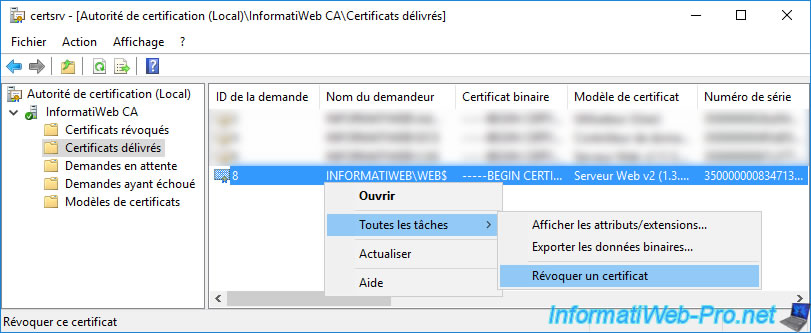
In the "Certificate Revocation" window that appears, you can select a revocation reason :
- Unspecified : in case you don't want to specify the reason.
- Key Compromise : in the event that a hacker had access to a server and potentially had access to the private key of the certificate.
- CA Compromise : in the event that the private key of the certification authority that issued this certificate has been compromised.
Note that when you revoke a certificate authority's certificate, all certificates issued from it will also be invalidated, since the chain of trust will be broken.
However, since these certificates are no longer valid, they must also be revoked on your side so that they no longer appear in the list of certificates issued. - Change of Affiliation : the certificate has changed ownership. You therefore revoke the old certificate and issue a new one to the new owner.
- Superseded : in case you have issued a new certificate (perhaps based on another template or an updated template) and therefore the old certificate will no longer be used.
- Cease of Operation : if the server, the computer or the user who possessed this certificate no longer exists, this certificate is no longer used and can therefore be revoked.
- Certificate Hold : allows you to temporarily revoke a certificate when a user is not present all the time, for example.
This reason is the only one that allows you to undo the certificate revocation later, if desired.
For this tutorial, we will choose "Key Compromise" (for example).
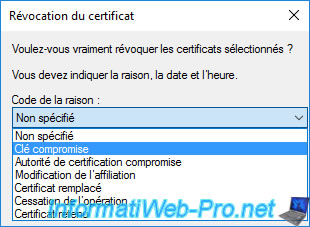
You can also choose a date from which this certificate will be revoked.
Default : now.
The revoked certificate disappears from the list of issued certificates.
The revoked certificate will appear in the list of revoked certificates.
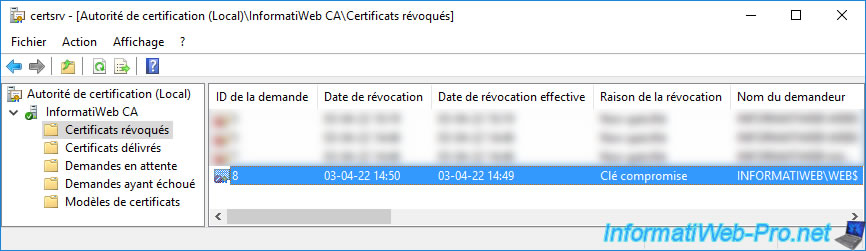
If you double click on it, you will be able to get information about it again.
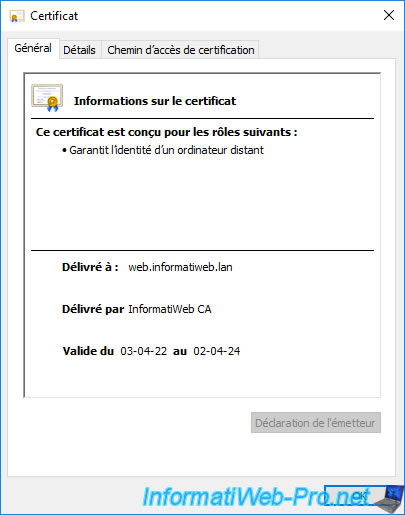
You can also double-check its serial number if you wish.
5. Publish a revocation list (CRL)
Now that this certificate has been revoked, you must add its serial number to one of your revocation lists so that your client workstations can know that it has been revoked.
To do this, right-click "All Tasks -> Publish" on the "Revoked Certificates" folder.
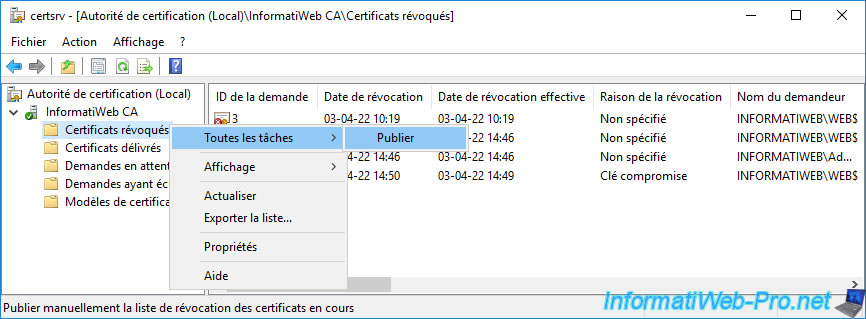
Choose "New CRL" to publish a complete "CRL".
As you can see, you have the choice between :
- New CRL : contains the complete list of serial numbers of revoked certificates on your certificate authority.
- Delta CRL only : contains only the list of serial numbers of the last certificates revoked after the creation of the complete certificate revocation list (CRL).
This type of revocation list obviously requires that a first certificate revocation list (CRL) has been published beforehand.
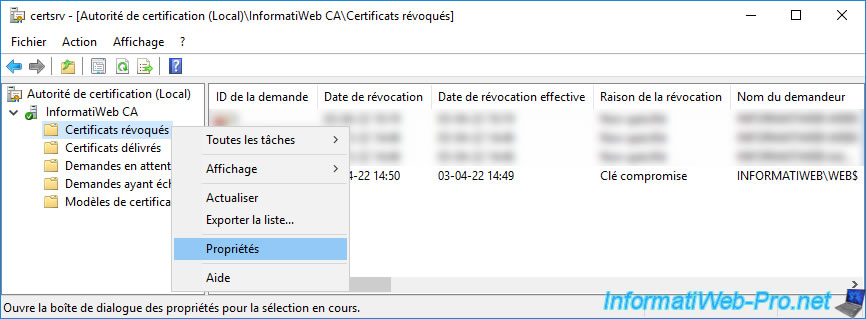
To verify that the revoked certificate has been added to the certificate revocation list (CRL), right-click "Properties" on the "Revoked Certificates" folder.
In the "View CRLs" tab, you can see that a revocation list has just been published.
To obtain information about it, click on the "View CRL" button.

In the "Certificate Revocation List" window that appears, go to the "Revocation List" tab.
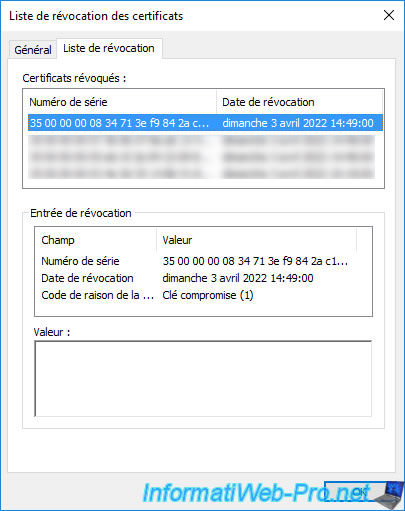
In this "Revocation List" tab, you will see the list of serial numbers of revoked certificates on your certification authority.
If you select a serial number from this list, you will be able to see when and why it was revoked.
In our case, we can see that we revoked this certificate for : Key compromised.
If you attempt to access the secure service using the certificate you have just revoked, an error will occur.
In our case, if we try to access our web server with Internet Explorer, the error "This organization's certificate has been revoked" appears and access to the desired website is completely blocked.
Indeed, as you can see, when a certificate is revoked, you can't ignore this security issue.
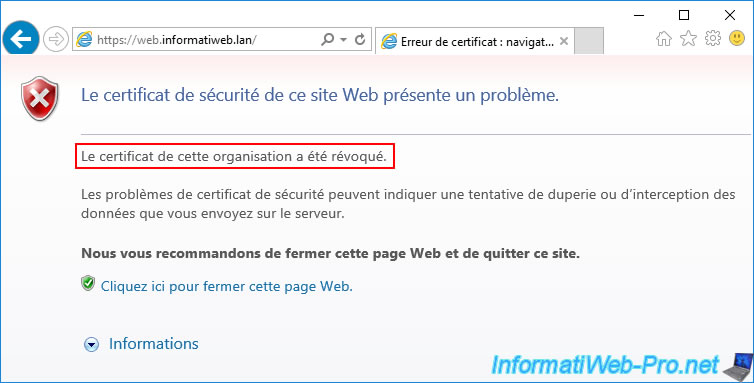
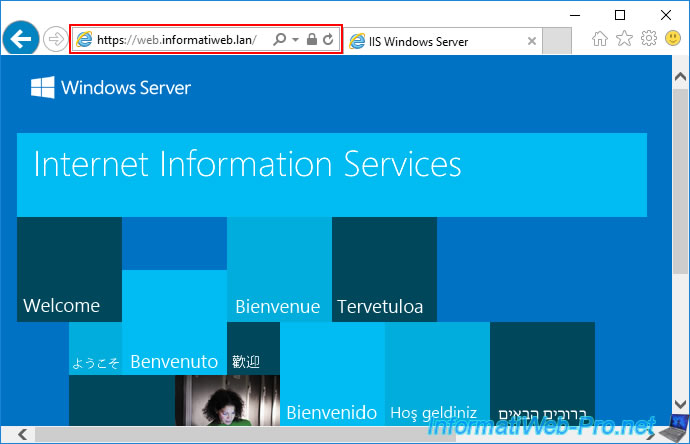
However, it's also possible that you still have access to this same service from other servers or client workstations.
Indeed, as explained above, clients keep a copy of your revocation lists in cache for a certain time (which corresponds to the frequency of publication of these).
6. Force the update of the revocation cache of the client PC
When a client checks if one of your certificates has been revoked, he downloads a copy of your revocation lists (CRLs and CRL delta) and keeps them for a certain period of time.
To find out how long these copies will be kept in the cache of your client computer, open the "Certification Authority" console (on your CA server) and right-click "Properties" on the "Revoked Certificates" folder.
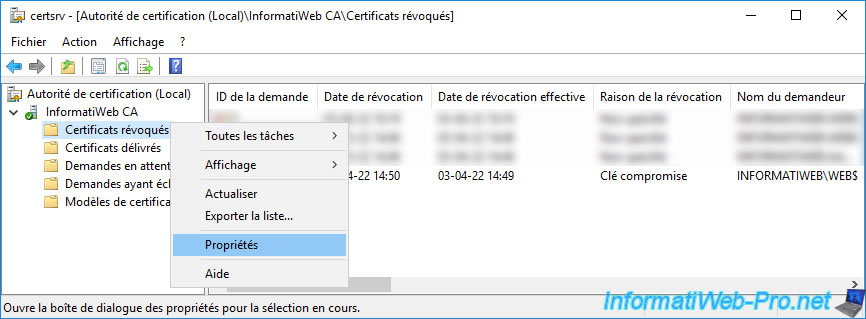
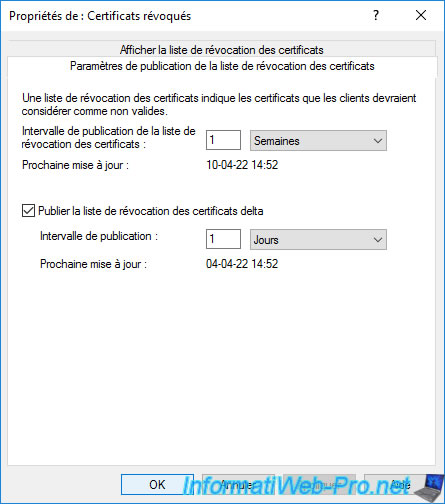
If you go to the "CRL Publishing Parameters" tab, you will be able to see how often :
- the revocation list (CRL) is published
- the delta revocation list (delta CRL) is published
On the client side, copies of these lists will be kept for the time indicated here for each of them.
To force a client-side revocation status update, clear your web browser's cache.
Erase everything.
Then, open a command prompt and force the update of the revocation cache of your computer or server by running the command :
Batch
certutil -setreg chain\ChainCacheResyncFiletime @now
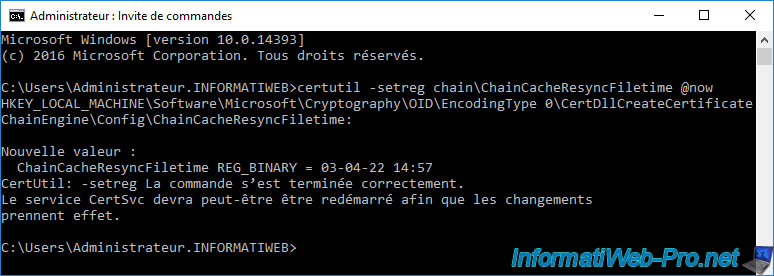
Now, if you open your web browser again and attempt to re-access the secure website with a revoked certificate, you will see the "This organization's certificate has been revoked" error.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

You must be logged in to post a comment