Implement Multi-WAN (Dual-WAN) on pfSense 2.6
- Firewall
- pfSense
- 29 August 2025 at 11:09 UTC
-

- 2/3
4. Create a WAN gateway group
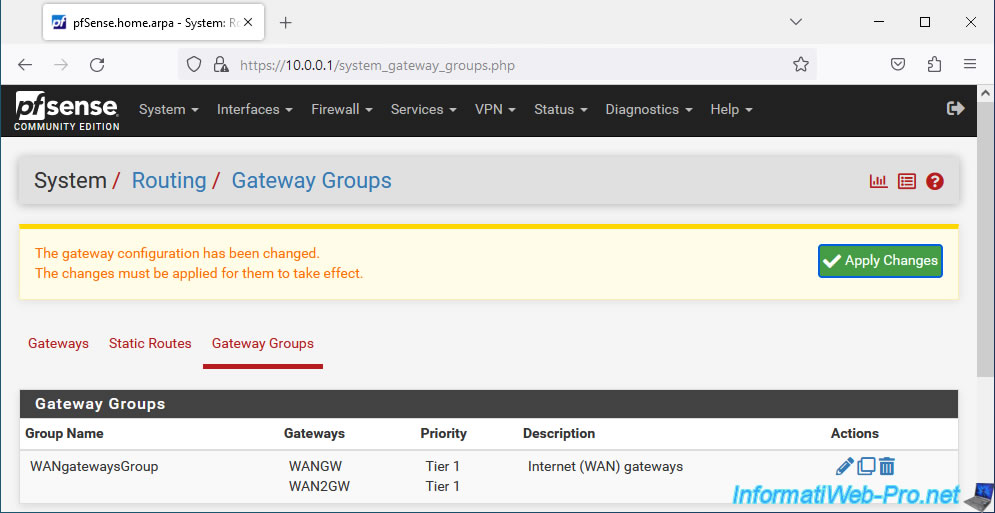
For pfSense to use your multiple WAN interfaces, you must first create a gateway group.
To do this, go to: System -> Routing.
Then, go to the "Gateway Groups" tab.
Note: for information, the parent WAN gateway added previously for the WAN2 interface appears here, in the "Gateways" tab.
In our case, this is the "WAN2GW" gateway.
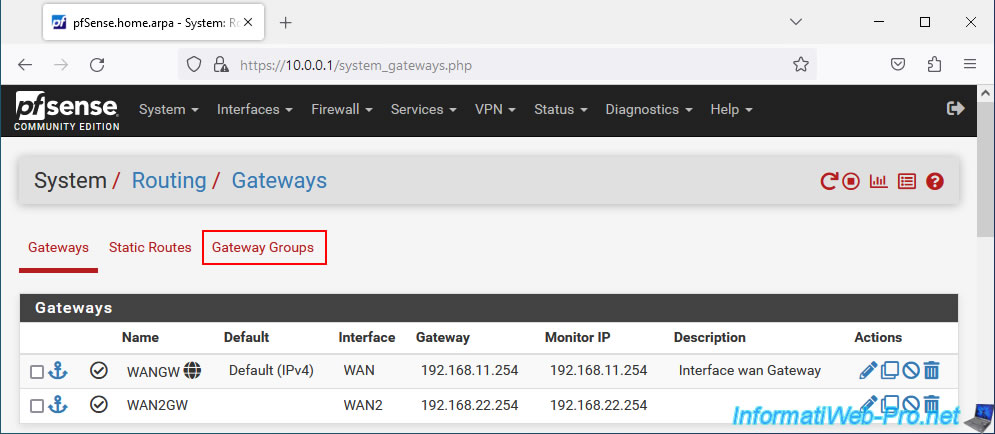
In the "Gateway Groups" tab, click Add.
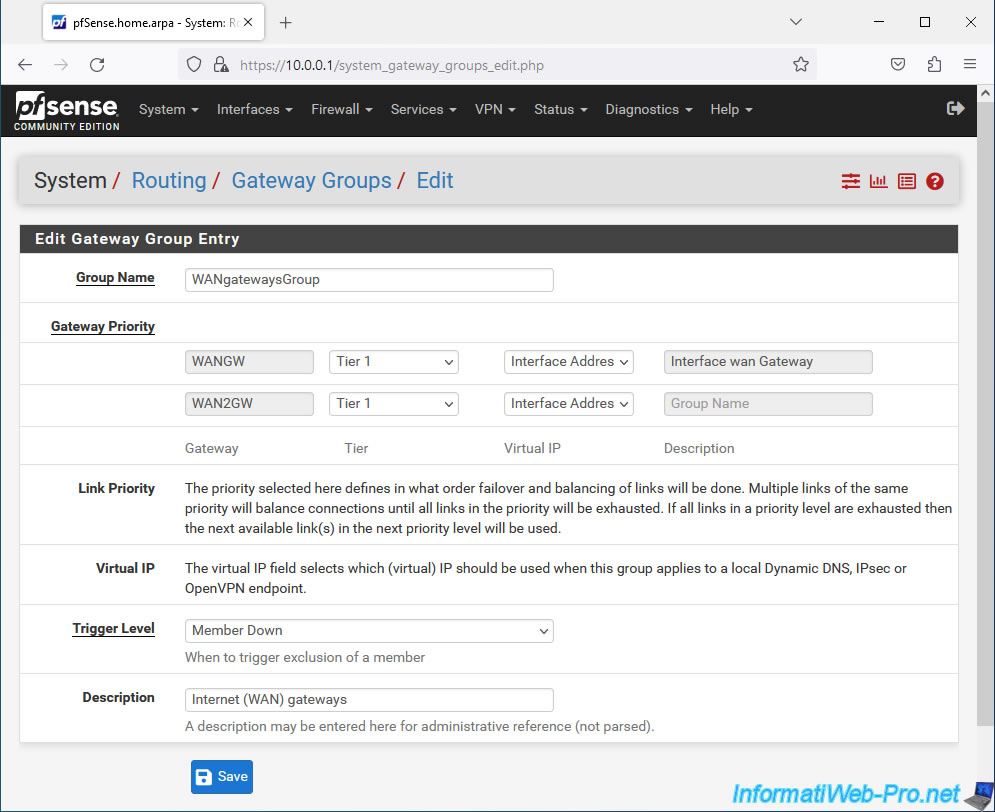
In the "Edit Gateway Group Entry" section, configure these settings:
- Group Name: name of the gateway group to create.
For example: WANgatewaysGroup.
Warning: you can't use spaces in this name. - Gateway Priority: allows you to manage the priority of the gateways located in this gateway group.
Priority is managed via the "Tier" value.- Fault Tolerance: to make one WAN interface active and the others passive (used only if the active WAN interface fails), select "Tier 1" for the gateway to be used first and "Tier 2" for "Tier 5" for others.
- Load Balancing: to distribute network load across multiple WAN interfaces, select the same priority (Tier x) for multiple WAN interfaces.
- in our case, we want to distribute the network load, so we select the same priority (Tier 1) for our 2 WAN gateways: WANGW and WAN2GW.
- Link Priority: pfSense tells you that the selected priority (via the "Tier" option above) defines how the WAN interfaces will be used for fault tolerance and/or load balancing.
- Virtual IP: in case you use virtual IP addresses for your WAN interfaces, this allows you to choose which one to use for each WAN interface for access to local dynamic DNS, IPsec (VPN tunnel) or OpenVPN (alternative to IPsec).
Again, this explanation refers to the "Virtual IP" option above. - Trigger Level: allows you to choose under what conditions a gateway will be considered "down" by pfSense.
- Member Down: pfSense will consider a gateway dead when it is completely dead.
Which means that one or two thresholds configured for the gateway are exceeded.
However, this only detects the worst possible state. So a lot of time can pass between the moment a problem occurs and the moment pfSense considers it dead. - Packet Loss: pfSense will consider a gateway dead when the number of lost packets exceeds a specific threshold.
- High Latency: similar to the previous option, but regarding latency.
- Packet Loss or High Latency: pfSense will consider a gateway dead when the packet lost threshold or latency threshold is exceeded.
- Member Down: pfSense will consider a gateway dead when it is completely dead.
- Description: provide a description for reference.
For example: Internet (WAN) gateways.
Sources :
- Load Balancing and Failover with Gateway Groups | pfSense Documentation
- Gateway Groups | pfSense Documentation
Click: Apply Changes.
Your WAN interface group has been created and configured.
5. Configure the firewall to use the WAN gateway group
For pfSense to use your WAN gateway group for Internet access from the LAN, you must modify existing rules in the pfSense firewall.
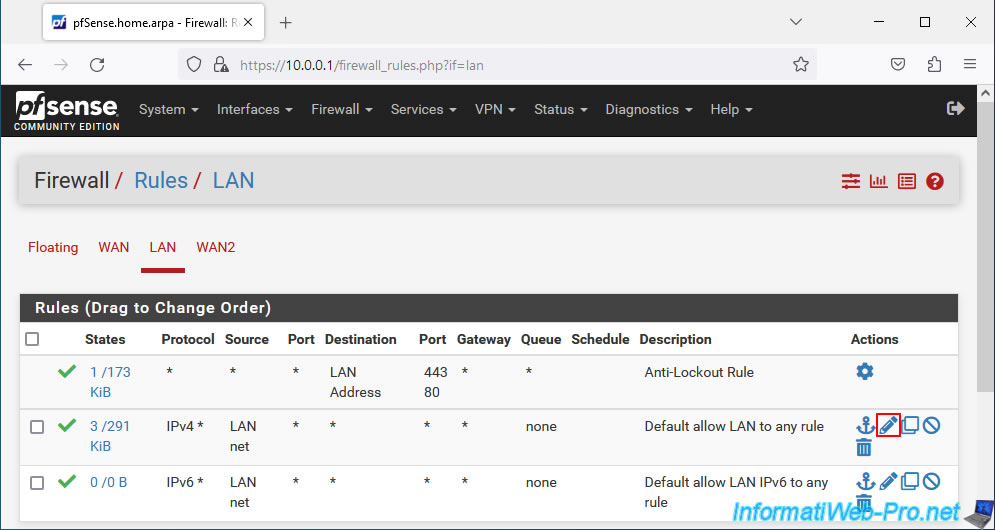
To do this, go to: Firewall -> Rules.
In our case, we modify the default IPv4 rule (Default allow LAN to any rule) which therefore concerns all IPv4 traffic on the LAN network.
The "Edit Firewall Rule" page appears.
At the bottom of the page, click on the "Display Advanced" button.
An "Advanced Options" section appears.
In this "Advanced Options" section, near the end of the page, you will find a setting called "Gateway".
Select the WAN gateway group created previously. In our case: WANgatewaysGroup.
Then, click Save.
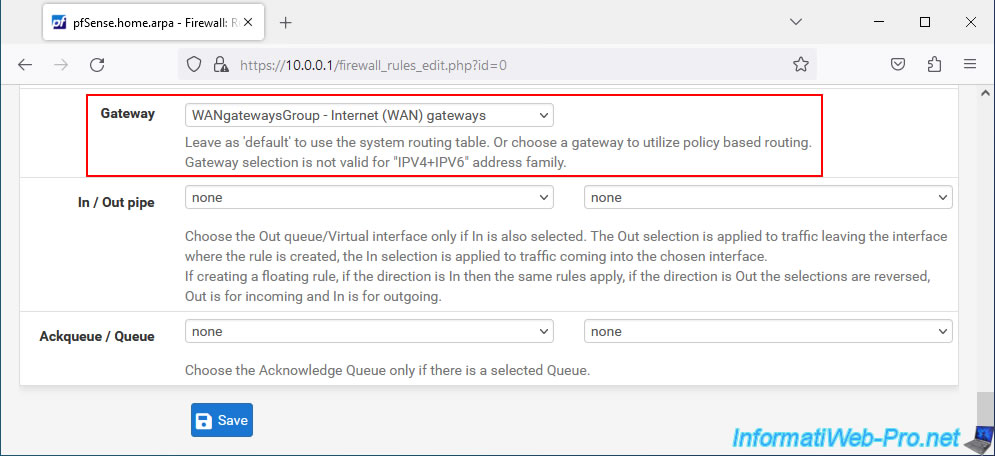
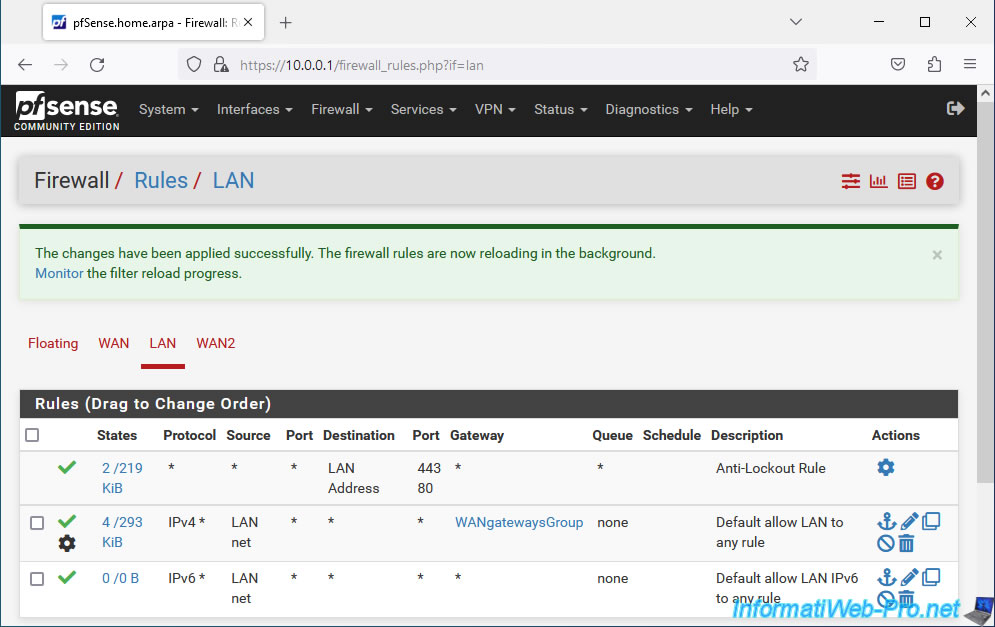
Click: Apply Changes.
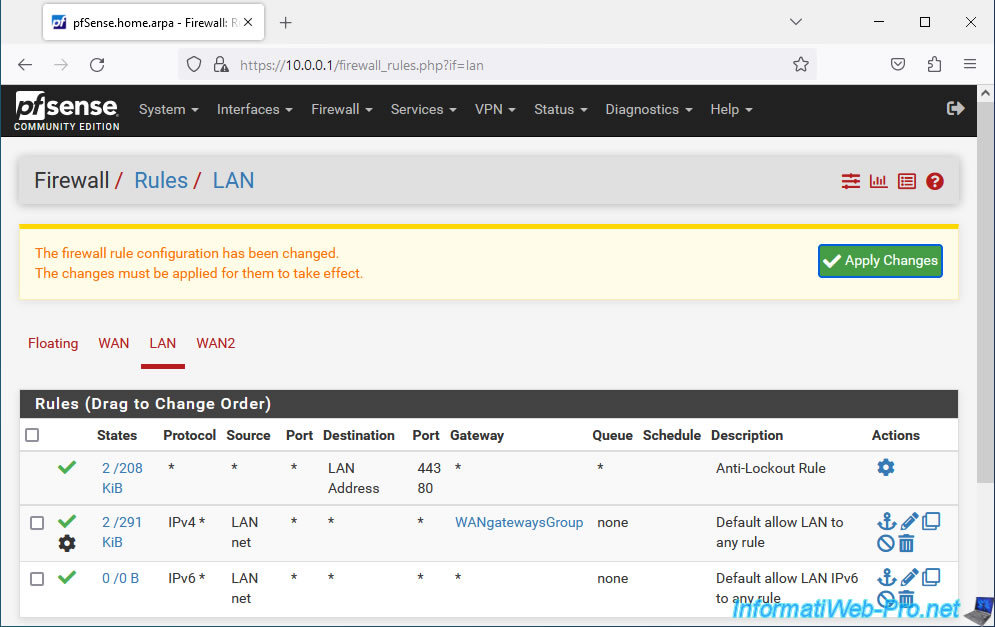
Your IPv4 rule has been modified.
Note that you will not be able to specify your gateway group for IPv6 rules if your WAN interfaces do not support IPv6.
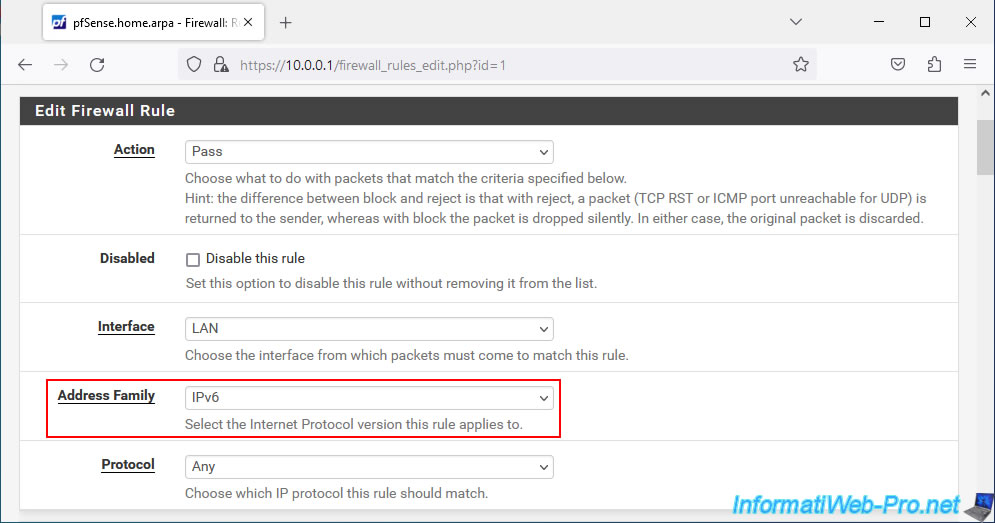
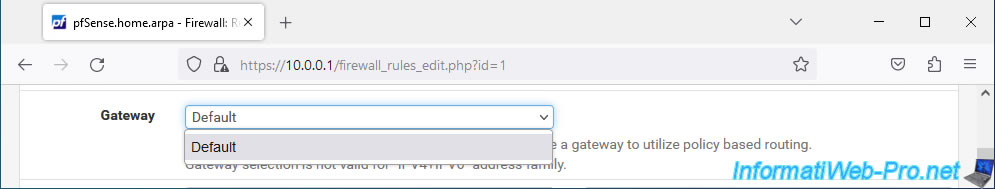
In our case, our WAN and WAN2 interfaces only use IPv4.
So if you look in the "Gateway" list, you will only see the "Default" value and not your previously created gateway group.
Share this tutorial
To see also
-

Firewall 6/25/2025
pfSense 2.6 - 1:1 NAT (IP address mapping)
-

Firewall 7/25/2025
pfSense 2.6 - Create and manage aliases
-

Firewall 8/16/2025
pfSense 2.6 - Monitoring via SNMP and Zabbix 6
-

Firewall 7/9/2025
pfSense 2.6 - Secure the web interface in HTTPS

No comment