Create a site-to-site (S2S) VPN tunnel via OpenVPN secured with SSL/TLS (L2 mode) on pfSense 2.6
- Firewall
- pfSense
- 19 September 2025 at 07:48 UTC
-

- 3/7
5.3. Create the network bridge between the LAN and the OpenVPN tunnel on site 1 (Brussels)
So that the machines on the LAN network at site 1 (Brussels) can communicate with the machines at the other physical site via the VPN tunnel, you must create a network bridge between the LAN network and the OpenVPN server interface.
To do this, go to: Interfaces -> Assignments.
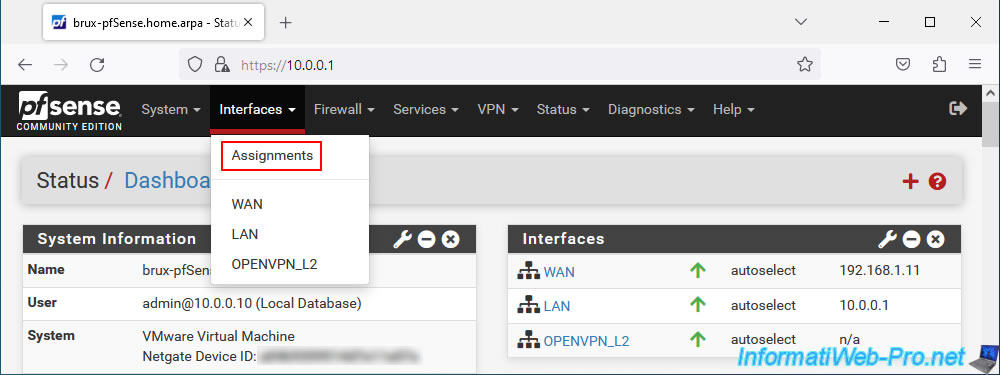
In the "Bridges" tab, click: Add.
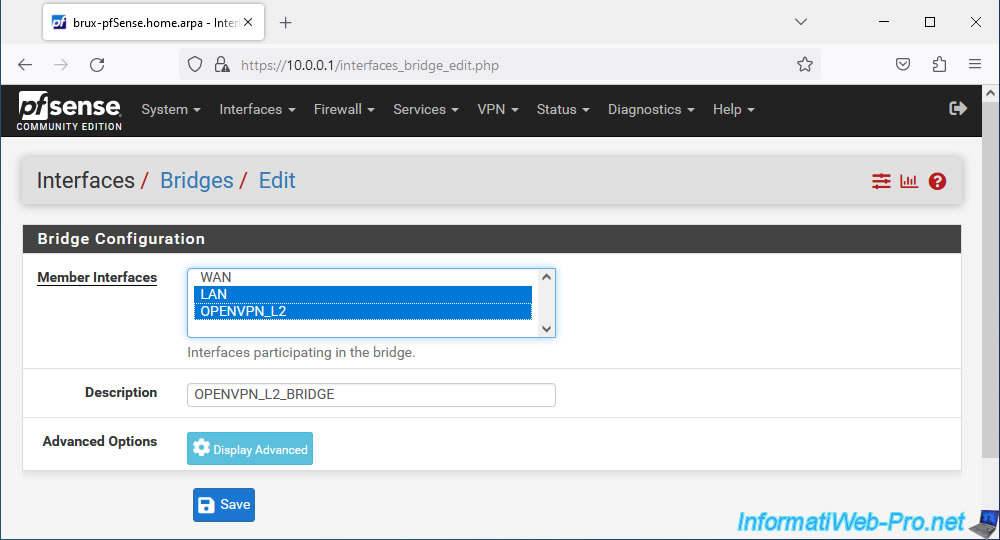
Select the network interfaces "LAN" and "OPENVPN_L2" for the "Member Interfaces" parameter and specify "OPENVPN_L2_BRIDGE" as the description (for example).
Then click Save.
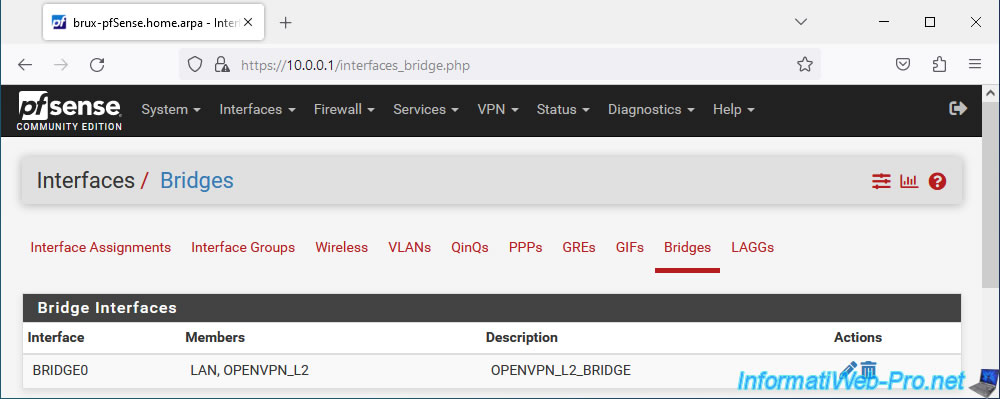
Your network bridge has been created.
5.4. Authorize access to the OpenVPN server on site 1 (Brussels)
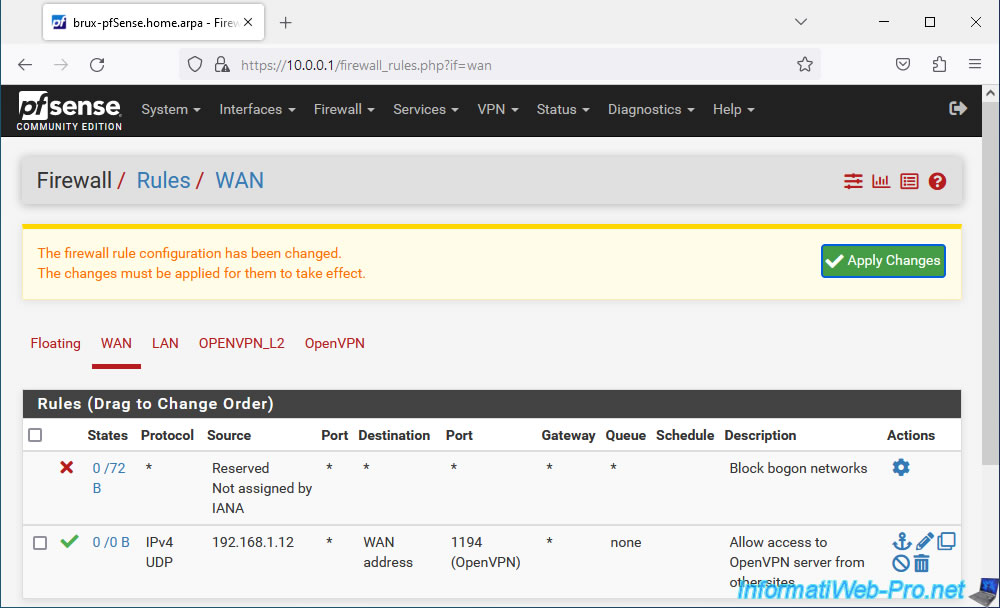
So that the future OpenVPN client can connect to your OpenVPN server, you need to add a rule in the firewall.
To do this, go to: Firewall -> Rules.
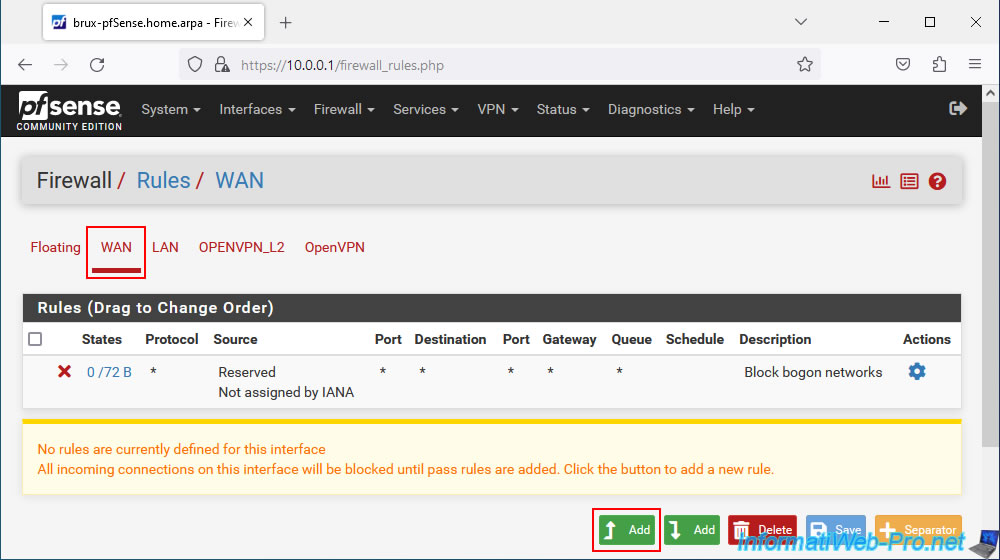
In the "WAN" tab, click Add.
Warning : if you see the "RFC 1918 networks" rule appear in the "WAN" tab and pfSense uses a private (local) IP address for its WAN interface, you will first need to deactivate the "Block private networks and loopback addresses" at the bottom of the "Interfaces -> WAN" page.
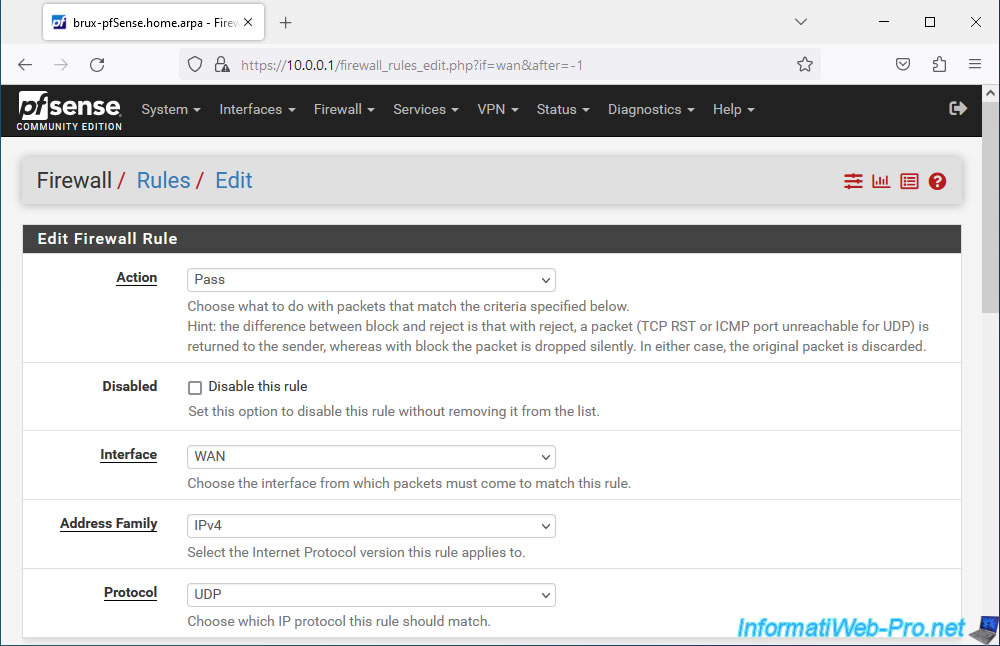
Configure this firewall rule like this:
- Actions: Pass.
- Interface: WAN. The OpenVPN server must be accessible from the Internet.
- Address Family: IPv4.
- Protocol: UDP. The OpenVPN server listens on UDP port 1194.
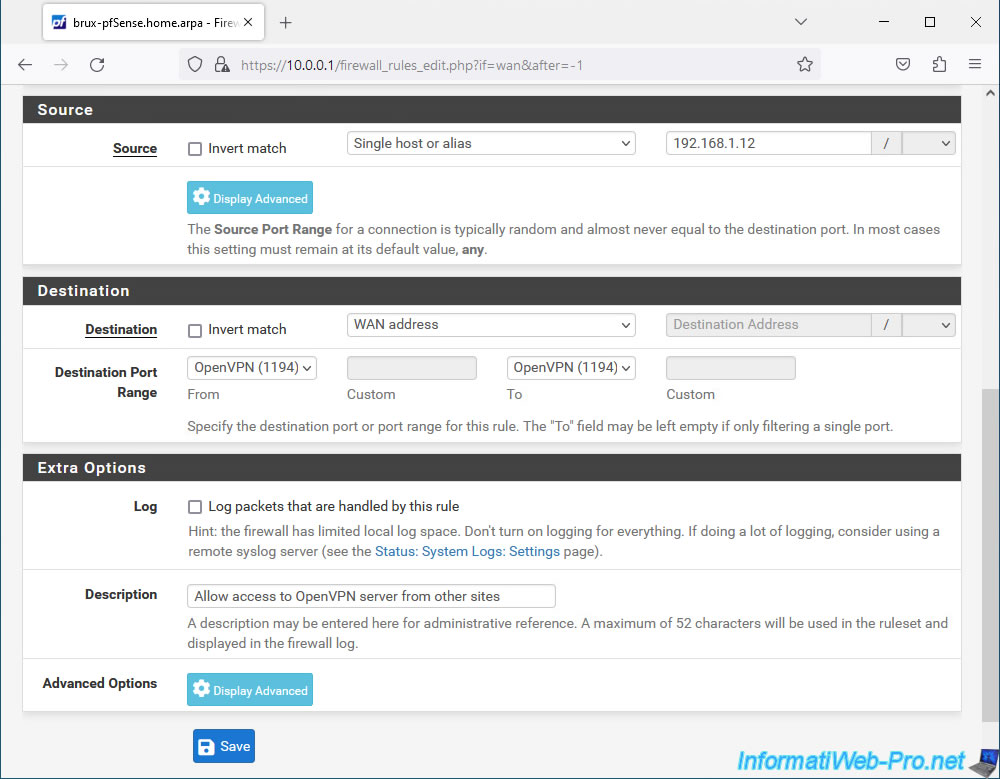
- Source: if the remote site has a fixed public IP (WAN) address, select "Single host or alias" and indicate the public IP address of the remote site (in our case: the IP address of site 2 (Paris)).
Otherwise, select "Any" to allow all IP addresses to attempt to connect to your OpenVPN server. - Destination: WAN address. The WAN IP address of pfSense where the OpenVPN server is located.
- Destination Port Range: OpenVPN (1194). Port used by default by OpenVPN.
- Description: Allow access to OpenVPN server from other sites.
Then, click Save.
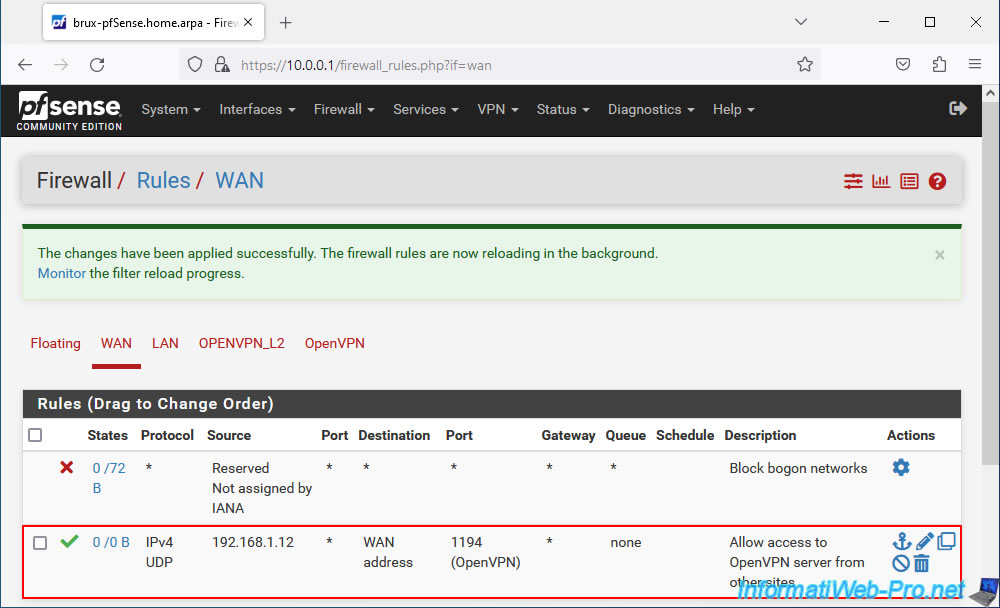
Click: Apply Changes.
External access to your OpenVPN server is allowed in the pfSense firewall.
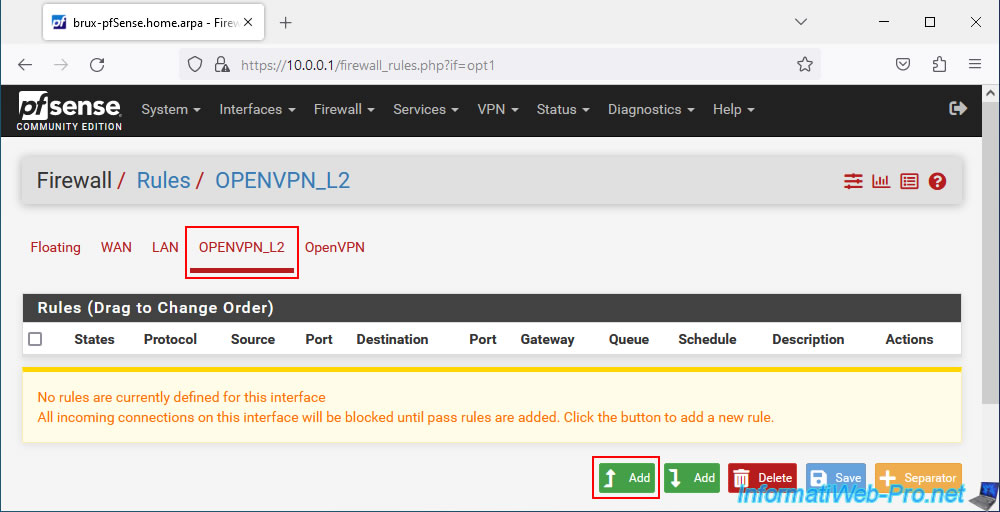
5.5. Allow network traffic in the OpenVPN tunnel on site 1 (Brussels)
For network traffic to pass through the OpenVPN tunnel, you need to go to the "OPENVPN_L2" tab (which corresponds to the "OPTx" logical interface previously created for the OpenVPN server's "ovpns1" virtual interface) and click :Add.
Allow all protocols for the "OPENVPN L2" interface.
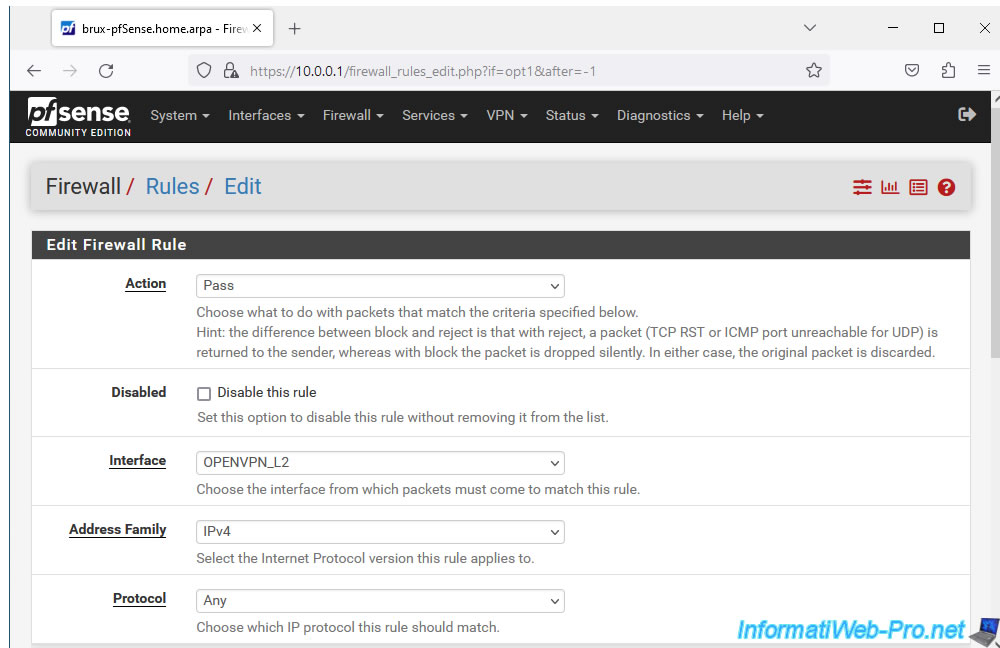
The source and destination don't matter, as it only concerns what passes through the OpenVPN tunnel.
For the description, indicate "Allow all traffic through the OpenVPN L2 tunnel".
Then click Save.
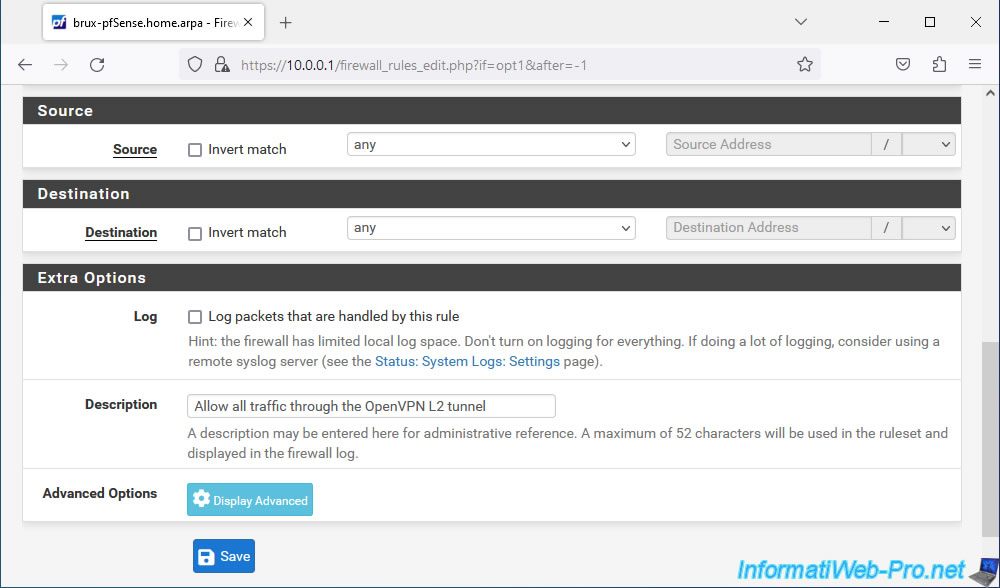
Click: Apply Changes.
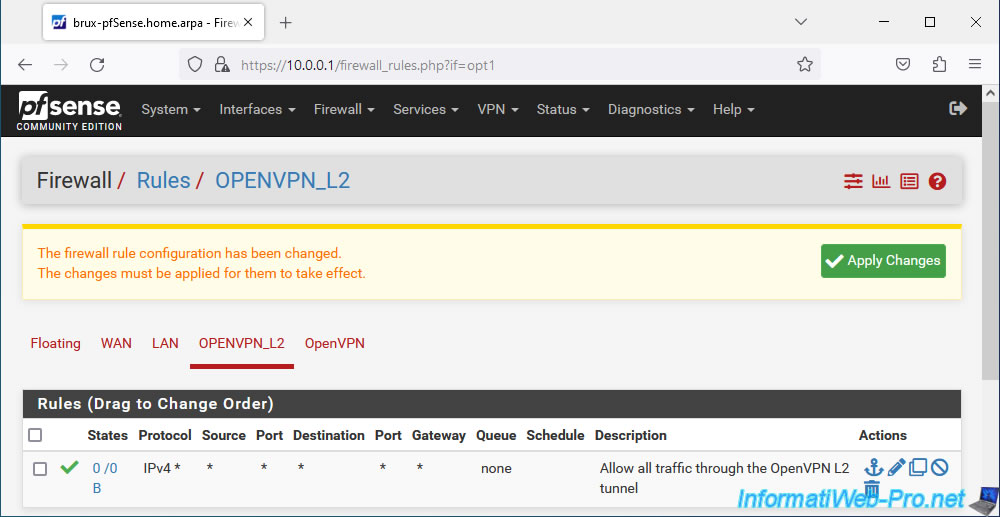
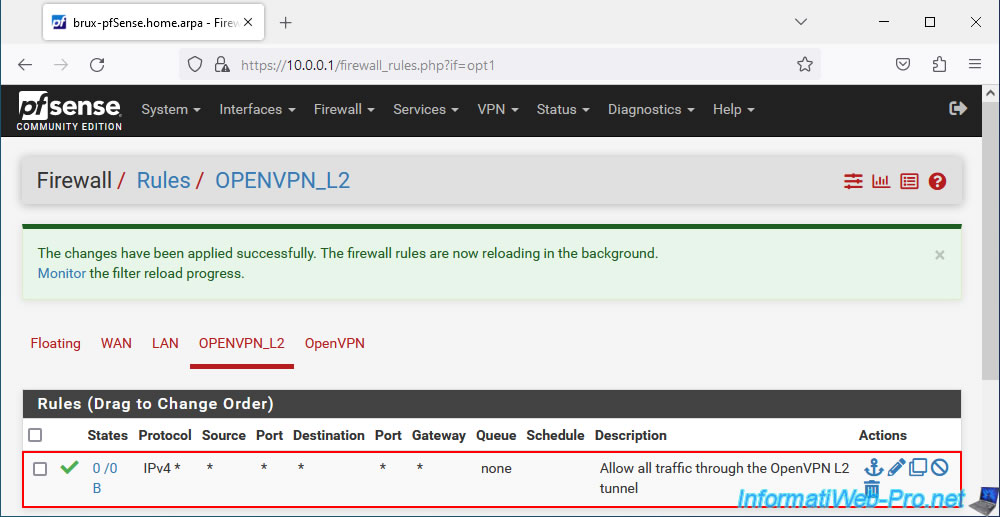
All network traffic is allowed in the OpenVPN tunnel for your OpenVPN server configured in "tap" mode (layer 2).
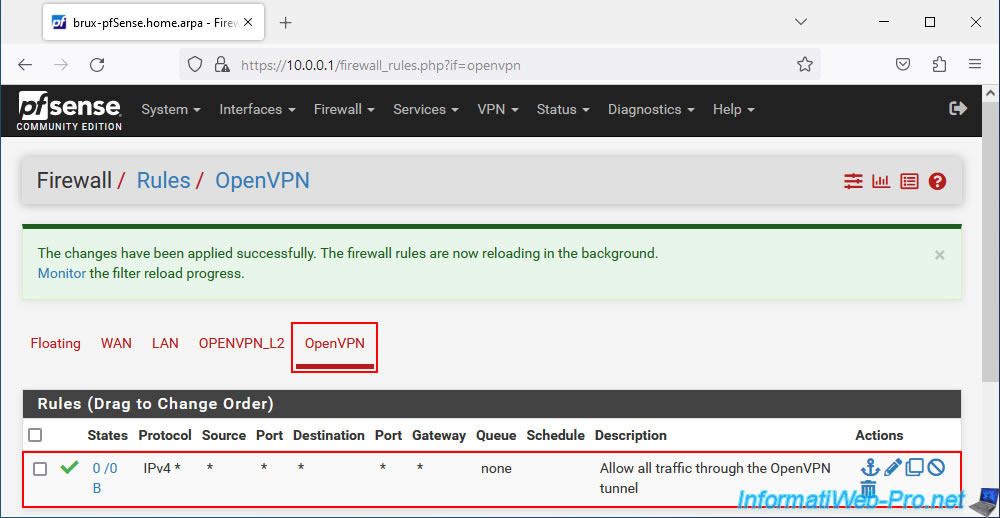
Also allow all network traffic for all OpenVPN tunnels (globally) by creating the same rule in the "OpenVPN" tab of the firewall.
This time, the description is "Allow all traffic through the OpenVPN tunnel".
Share this tutorial
To see also
-
Firewall 8/6/2025
pfSense 2.6 - Create a network bridge
-

Firewall 8/29/2025
pfSense 2.6 - Implement Multi-WAN (Dual-WAN)
-
Firewall 5/23/2025
pfSense 2.6 - Network interfaces
-

Firewall 8/1/2025
pfSense 2.6 - Update pfSense

No comment