- VMware
- 30 October 2024 at 08:20 UTC
-

- 1/3
By default, web access to your VMware vCenter Server (VCSA) is protected with an SSL certificate that is issued by a "VMCA" certification authority that is not recognized by your computer.
To find out more, refer to our previous tutorial: VMware vSphere 6.7 - Secure access to VMware vCenter Server (VCSA) over HTTPS.
- Invalid SSL certificate used by default by VMware vCenter Server (VCSA)
- Create a certificate template for the VMware vCenter Server machine certificate
- Enable SSH
- Create the certificate request for the VMware vCenter Server (VCSA) machine certificate via SSH
- Request a certificate from your certification authority on Windows Server
- Replace VMware vCenter Server machine SSL certificate
- VMware ESXi host SSL certificates considered invalid
- Trust SSL certificates issued by the VMCA certificate authority
- VMware ESXi host certificates considered valid
1. Invalid SSL certificate used by default by VMware vCenter Server (VCSA)
By default, when you access the web interface of your VMware vCenter Server (VCSA), a warning is displayed because the issuer of the certificate used is unknown.
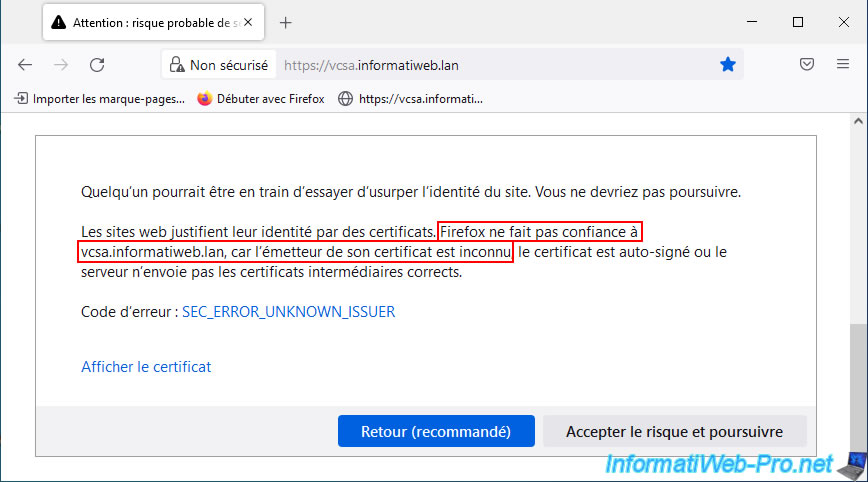
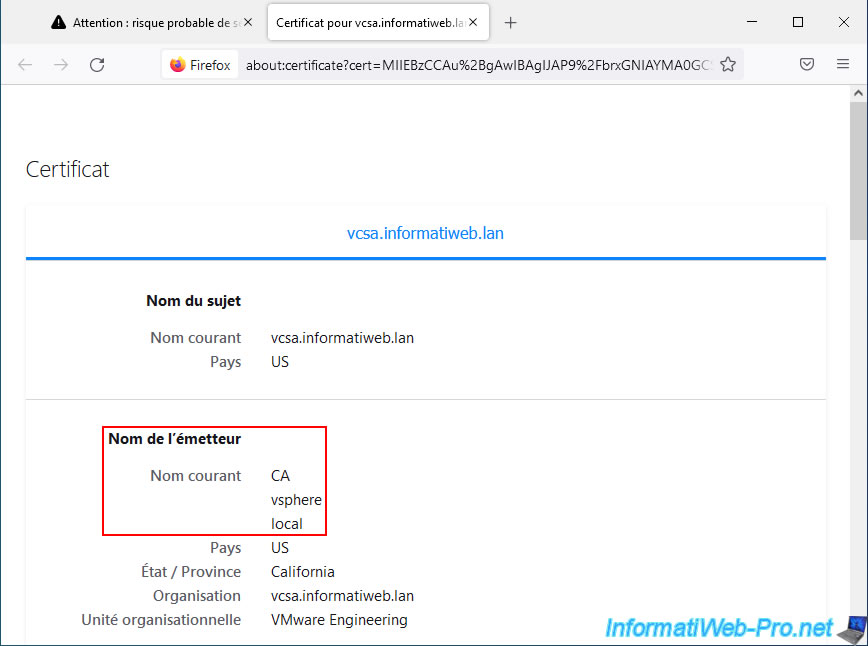
If you click on "Show certificate", you will see that this certificate was issued by: CA vsphere local.
Which corresponds to the VMCA certificate authority automatically created on your VMware vCenter Server (VCSA) during the installation of your server.
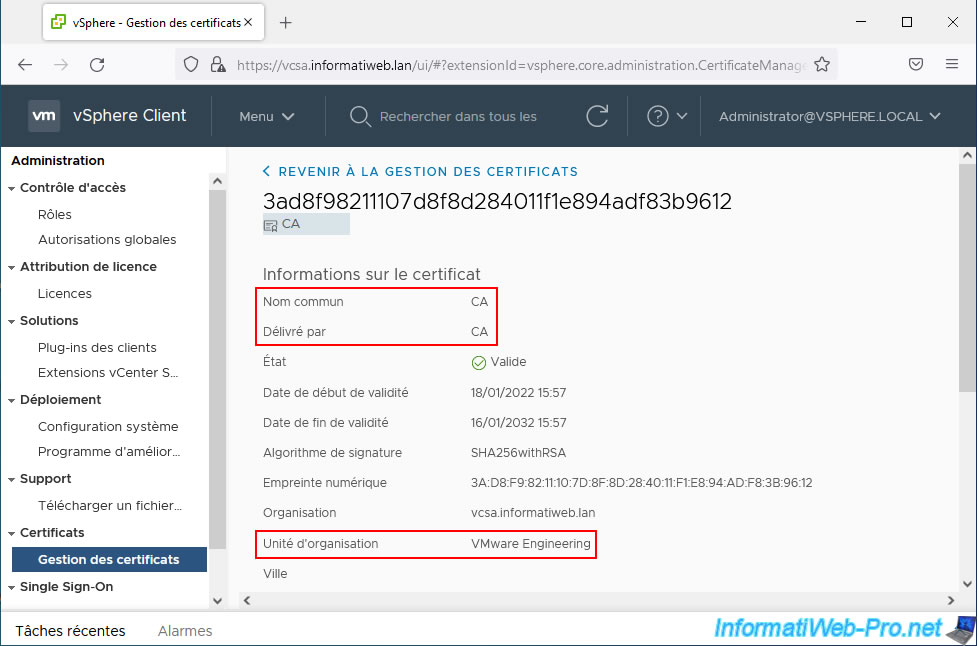
You can also check this by going to the VMware vSphere Client menu, then in: Administration -> Certificates -> Certificate Management -> Trusted Root Certificates.
As you can see, the only certificate in this section is that of VMCA whose name is "CA" and which corresponds to the issuer of the certificate used by VMware vSphere Client by default.
2. Create a certificate template for the VMware vCenter Server machine certificate
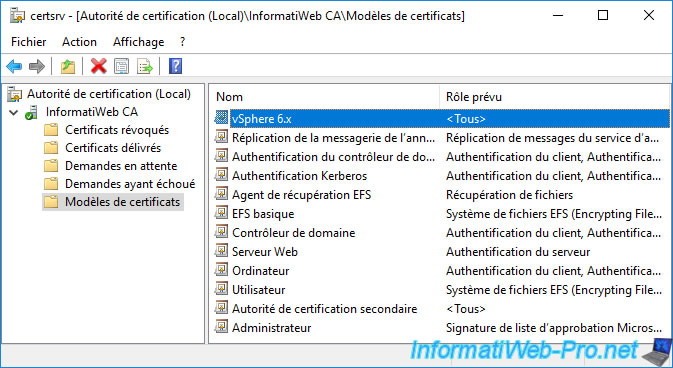
To generate a certificate that will be valid for your VMware vCenter Server, you must create a new certificate template on your certificate authority on Windows Server.
To do this, refer to step "3. Create a certificate template for the VMware vCenter Server machine certificate" our previous tutorial.
Once this template has been created and added to the certificate templates to be issued, you will see this new "vSphere 6.x" template appear in the list of certificate templates for your certification authority.
3. Enable SSH
To be able to secure your VMware vCenter Server (VCSA) using the command line, it is obvious that SSH must be enabled on your VCSA server.
To do this, access the "Appliance Management" page by accessing the address: https://[domain name of your VCSA server]:5480/ui/.
Which gives in our case: https://vcsa.informatiweb.lan:5480/ui/.
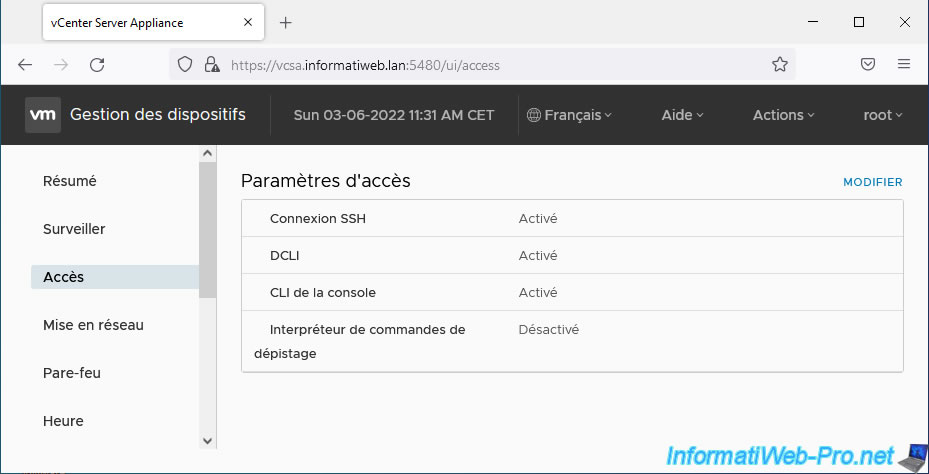
On the "Appliance Management" page that appears, log in as root, then go to the "Access" section.
The "SSH" access setting must be enabled. If not, click Edit.
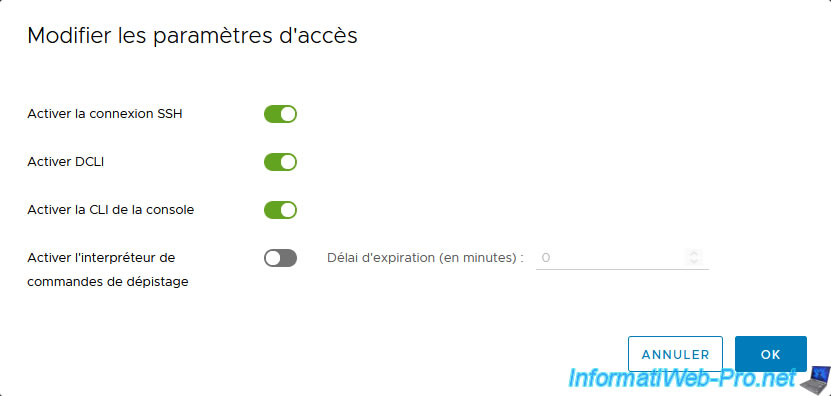
Enable the "Enable SSH Login" setting and click OK.
4. Create the certificate request for the VMware vCenter Server (VCSA) machine certificate via SSH
To get started, SSH into your VMware vCenter Server (VCSA).
On Windows you can use PuTTY (for example).
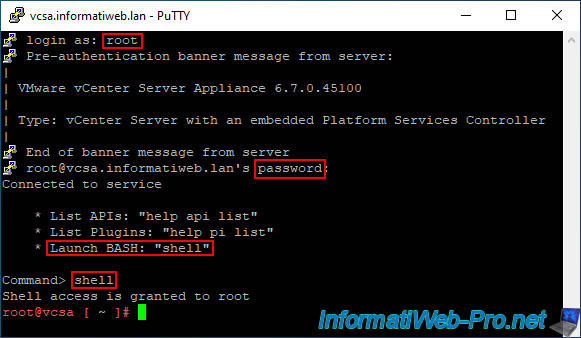
Log in as "root" and use the "shell" command to access the BASH (Linux) shell of your VMware vCenter Server Appliance (VCSA) server.
Indeed, by default, you are in the shell of the VCSA appliance and not that of Linux.
Bash
shell
To get started, create a "certs" folder in the root of your VCSA server where you can later store the certificate request (CSR), associated private key, and necessary certificates.
Bash
mkdir /certs
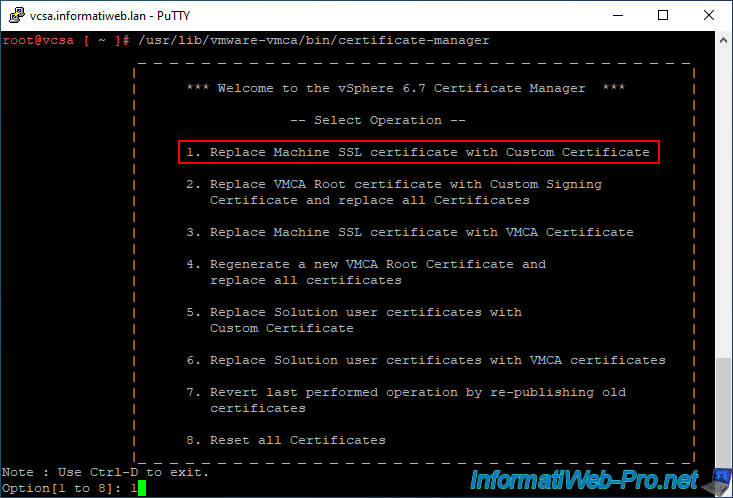
Next, launch the VCSA (VMware vCenter Server Appliance) certificate manager and choose option 1 (Replace Machine SSL certificate with Custom Certificate).
This will allow you to replace only the certificate protecting the web client (VMware vSphere Client) of your VMware vCenter Server (VCSA).
Bash
/usr/lib/vmware-vmca/bin/certificate-manager
Plain Text
*** Welcome to the vSphere 6.7 Certificate Manager ***
-- Select Operation --
1. Replace Machine SSL certificate with Custom Certificate
...
Option[1 to 8]: 1
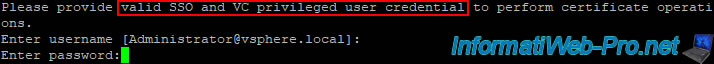
Specify the credentials of a vCenter account in your vSphere SSO domain that is authorized to perform certificate operations.
For example: the "administrator@vsphere.local" account created by default during the installation of VMware vCenter Server (VCSA).
Plain Text
Please provide valid SSO and VC privileged user credential to perform certificate operations. Enter username [Administrator@vsphere.local]: Enter password:
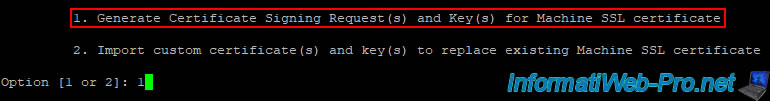
Select option 1 to generate a certificate request for the machine SSL certificate.
Plain Text
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate.
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate.
Option [1 or 2]: 1
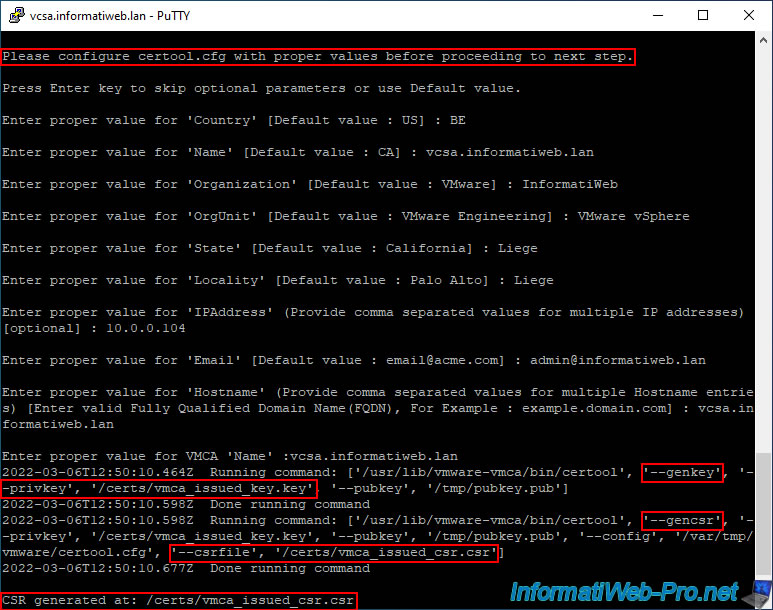
Indicate the path to the "certs" folder created previously.
As instructed by the wizard, the Certificate Request (CSR) and associated private key will be created in this folder.
Plain Text
Please provide a directory location to write the CSR(s) and PrivateKey(s) to: Output directory path: /certs
![]()
To create the certificate request, you will need to provide the following information:
- Country: the code of the country where you are located.
In our case: BE. - Name: the domain name of your VCSA server.
In our case: vcsa.informatiweb.lan. - Organization: the name of your company.
In our case: InformatiWeb. - OrgUnit: the desired organization unit.
For example: VMware vSphere. - State: the state in which your business is located.
- Locality: the city in which your business is located.
In our case: Liege. - IPAddress: the IP address of your VCSA server.
This allows the certificate to also be valid if you attempt to access your VCSA server by specifying its IP address in the address bar instead of its domain name.
Which can be useful in the event of a temporary DNS problem, for example. - Email: the email address of the person managing the certificate for this server. So, in the event of a problem, the user can easily notify this person.
- Hostname: the domain name of your VCSA server.
This value is very important, because it is the one that will be checked by your web browser. - VMCA Name: the domain name of your VCSA server.
Once all this information has been entered, you will see that 2 commands will be executed:
- certool --genkey ... : generates the private key you will need later.
- certool --gencsr ... : generates the certificate request (CSR) that you will need to submit to your certification authority to obtain a valid certificate from it.
As you can see, the generated private key and certificate request (CSR) were created in your folder: /certs.
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

You must be logged in to post a comment