Secure access to VMware vCenter Server (VCSA) over HTTPS (via SSH) on VMware vSphere 6.7
- VMware
- 30 October 2024 at 08:20 UTC
-

- 3/3
6. Replace VMware vCenter Server machine SSL certificate
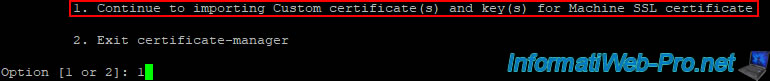
In your preferred SSH client (for example: PuTTY), continue the Machine SSL certificate replacement process by selecting option 1.
Plain Text
1. Continue to importing Custom certificate(s) and Key(s) for Machine SSL certificate
2. Exit certificate-manager
Option [1 or 2]: 1
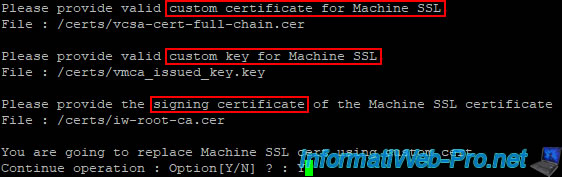
Indicate the path of the requested files:
- the personalized Machine SSL certificate: /certs/vcsa-cert-full-chain.cer
- the associated private key (previously generated during the certificate request (CSR)): /certs/vmca_issued_key.key
- the certificate of the certification authority that issued the certificate of your VCSA server (indicated previously): /certs/iw-root-ca.cer
Plain Text
Please provide valid custom certificate for Machine SSL File : /certs/vcsa-cert-full-chain.cer Please provide valid custom key for Machine SSL File : /certs/vmca_issued_key.key Please provide the signing certificate of the Machine SSL certificate File : /certs/iw-root-ca.cer
Then validate by answering "Y".
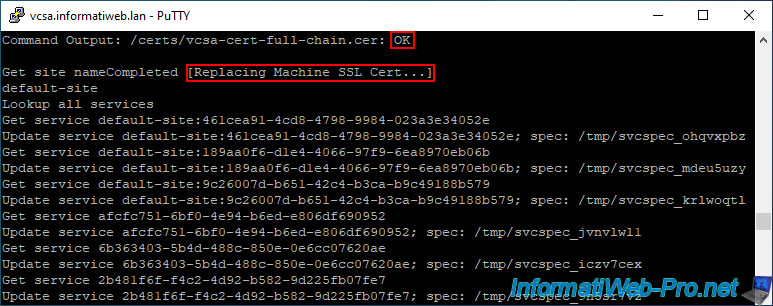
If the certificate specified as the Machine SSL certificate is valid, the keyword "OK" will be displayed after its name.
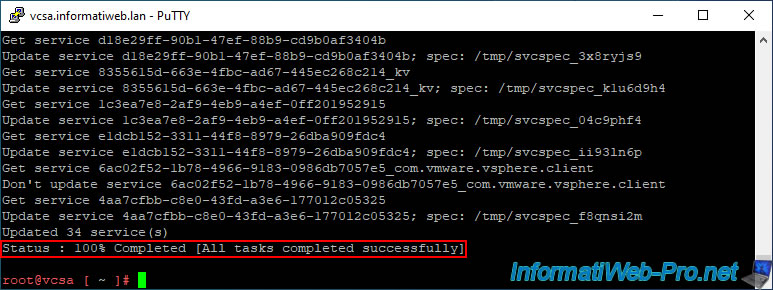
Then, the message "Replacing Machine SSL Cert" will be displayed.
Approximately 34 VCSA services will be updated automatically.
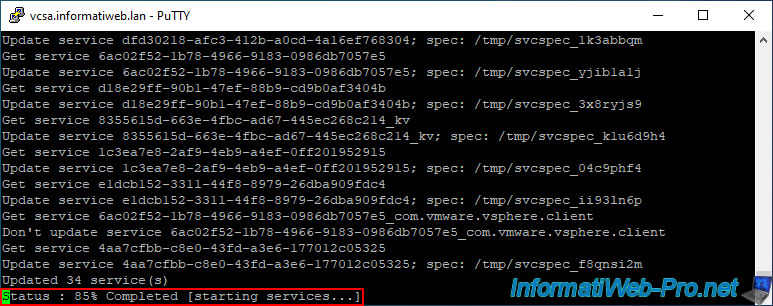
Once the necessary services are updated, they will be restarted.
This may take a little time.
Plain Text
Updated 34 service(s). Status : 85% Completed [starting services...]
Once the services restart, the process will be completed.
Plain Text
Status : 100% Completed [All tasks completed successfully]
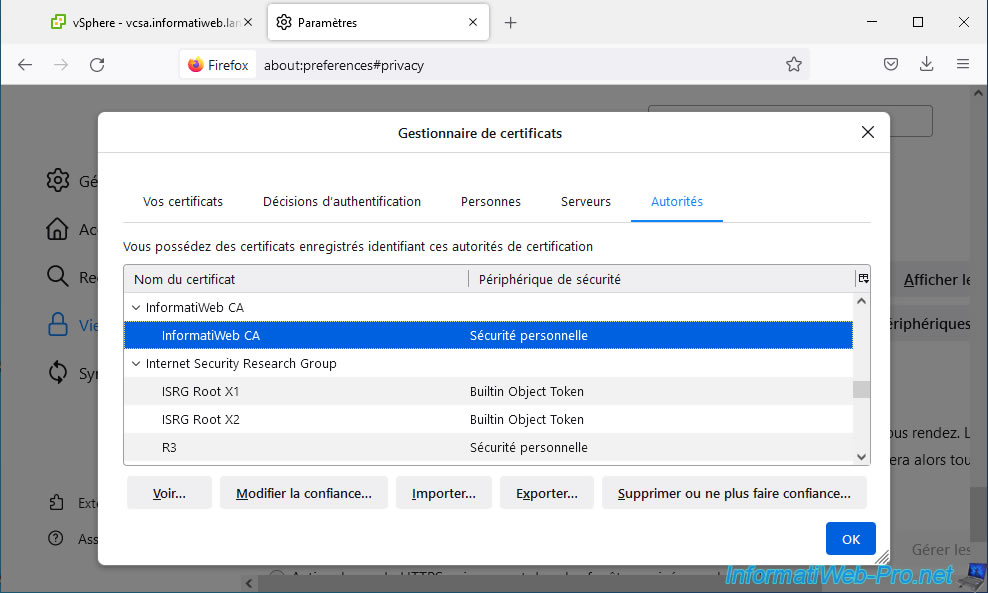
Important : for the certificate from your certificate authority to be considered valid by your computer, it is important that your certificate authority's certificate is part of your computer's certificate store.
This is already the case if your computer is linked to the same Active Directory domain as the enterprise certification authority from which the SSL certificate used comes.
Warning : if you use "Mozilla Firefox, you will also need to import it into its certificate store.
This is because Mozilla Firefox uses its own certificate store and not that of your computer.
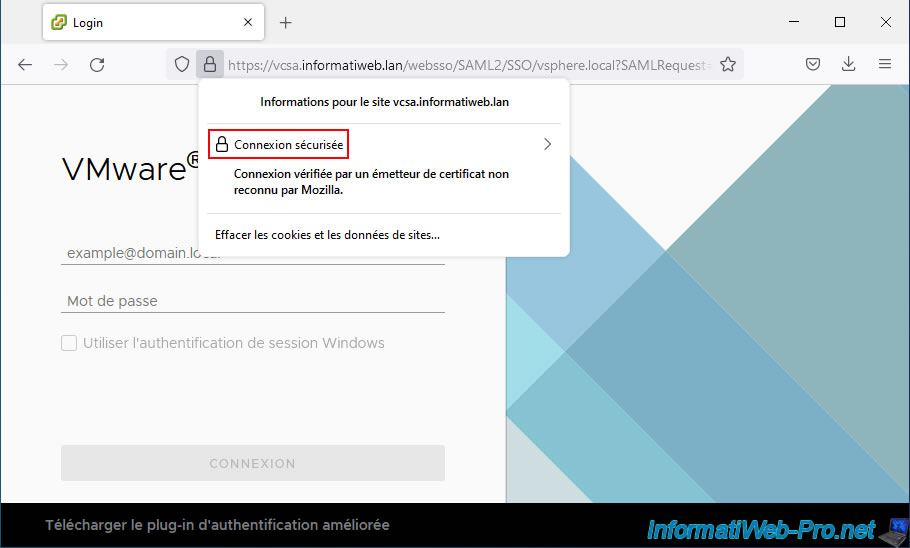
Once your computer and web browser trust the certificates from your certificate authority, you will be able to access the web interface of your VMware vCenter Server (VCSA).
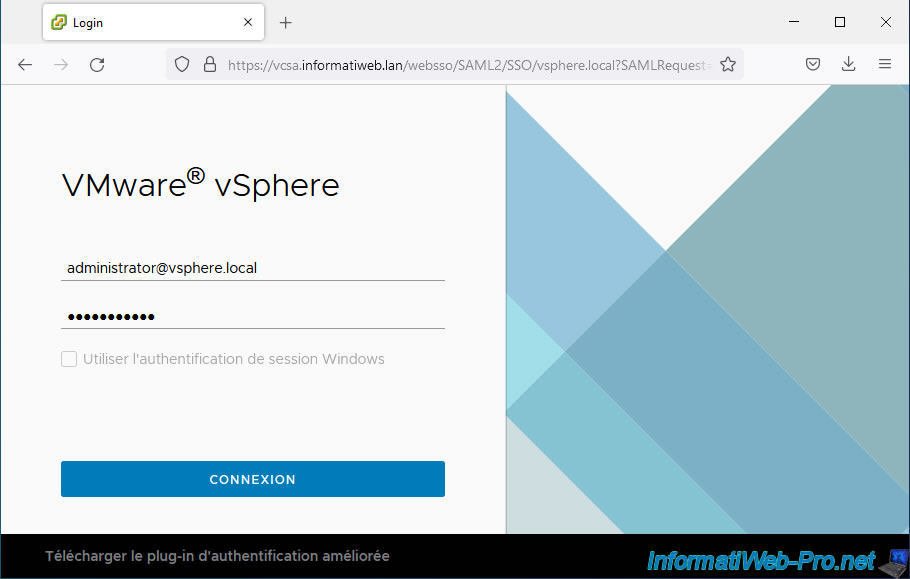
As you can see, the warning has disappeared and your web browser says: Secure connection.
If you click on this "Secure Connection" status, you will see that the certificate has been verified by your own certificate authority.
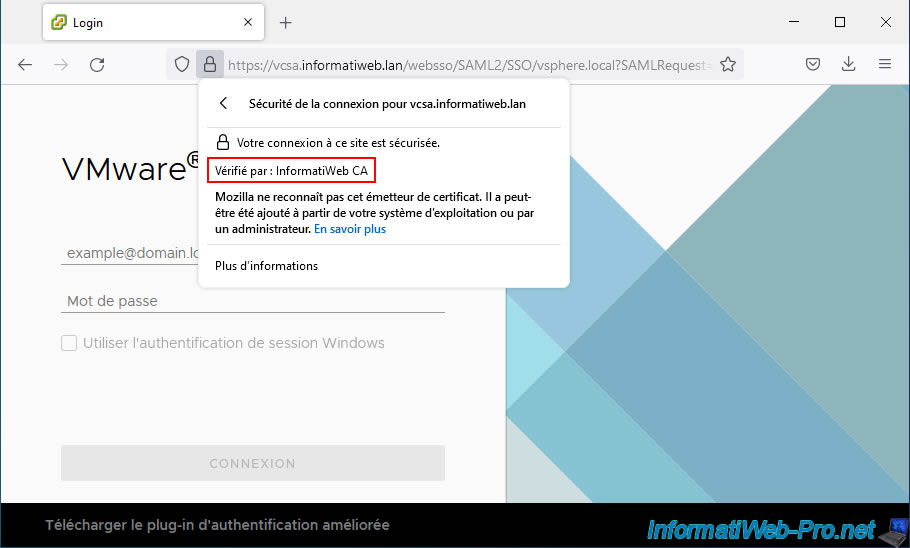
If you click on "More information", you will see this window appear.
Click the button: View Certificate.
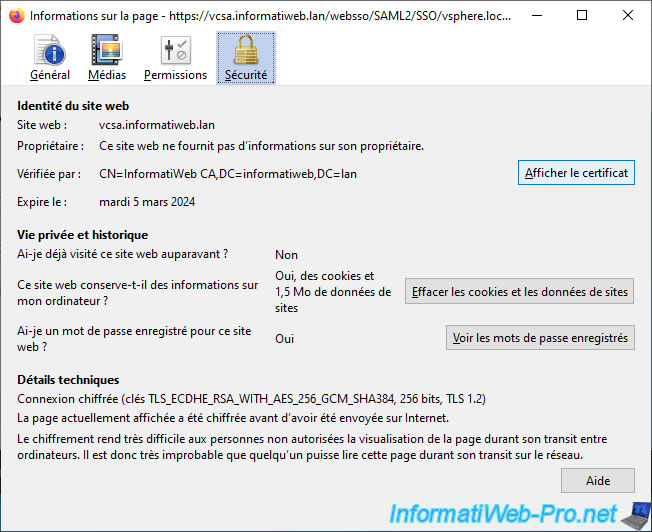
As you can see, the certificate used by VMware vSphere Client:
- is valid for the domain name of your VCSA server
- was issued by your certification authority
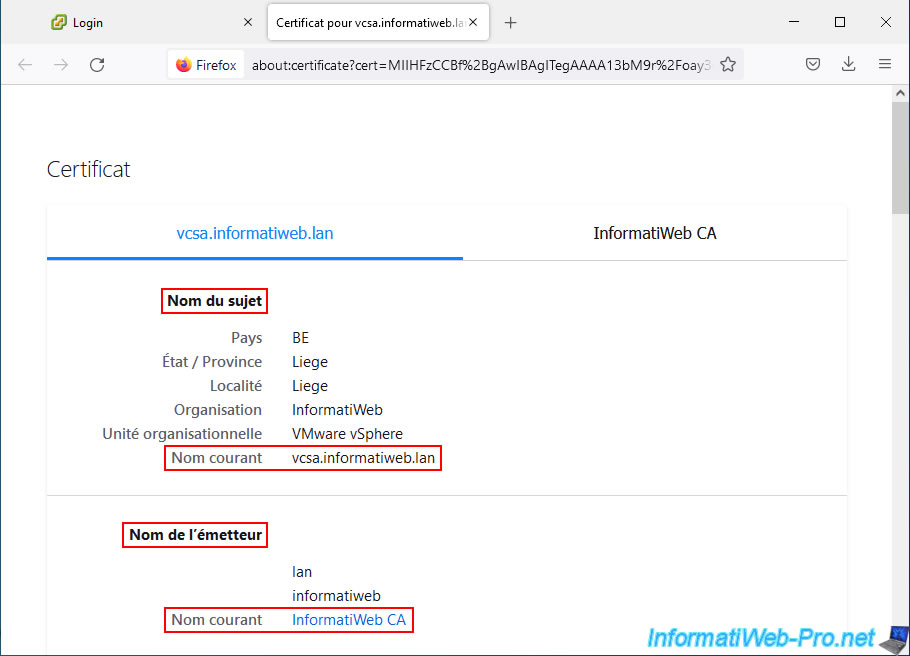
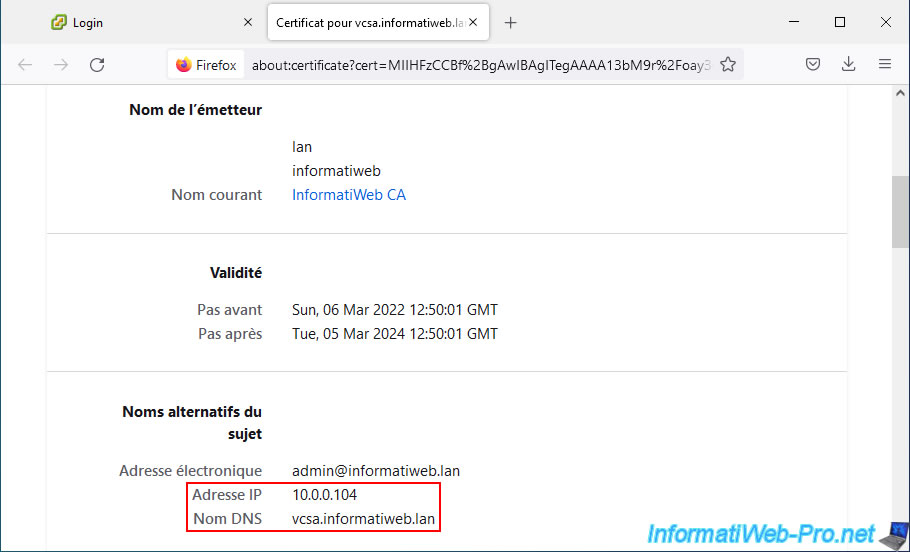
In the "Subject Alt Names" section, you will see the IP address and domain name of your VCSA server appear.
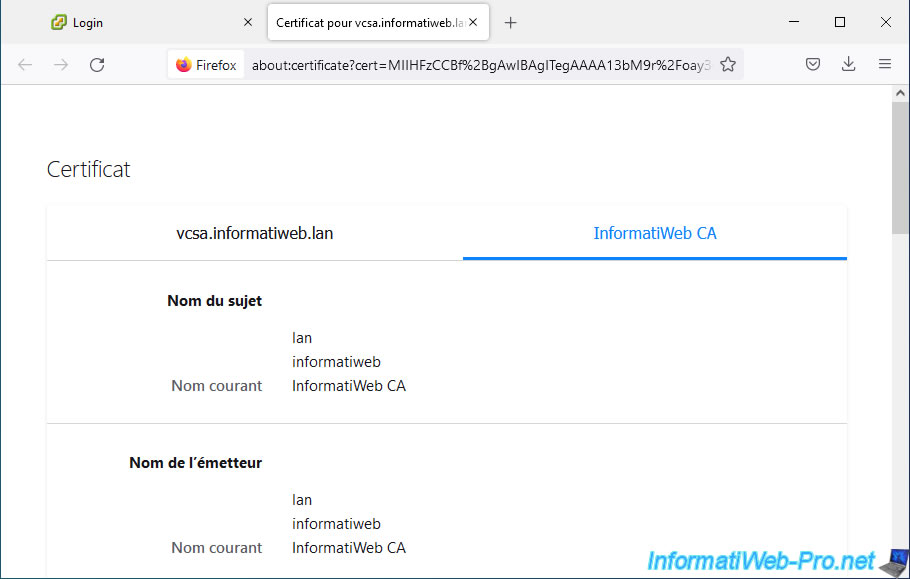
If you click on the 2nd tab, you will see the information about your root certificate authority certificate.
You can now log in as administrator@vsphere.local and be sure that you are connecting to the correct server and not a pirate server.
Note that this will also work correctly with Google Chrome and Microsoft Edge.
7. VMware ESXi host SSL certificates considered invalid
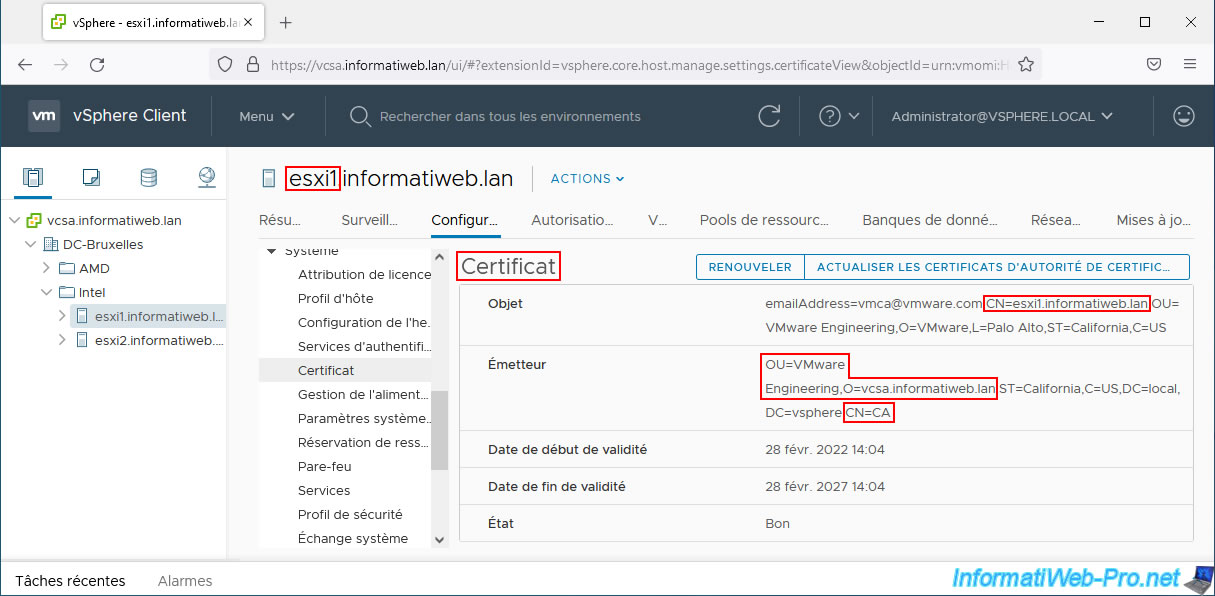
In your VMware vCenter Server (VCSA) inventory, select a VMware ESXi host and go to: Configure -> System -> Certificate.
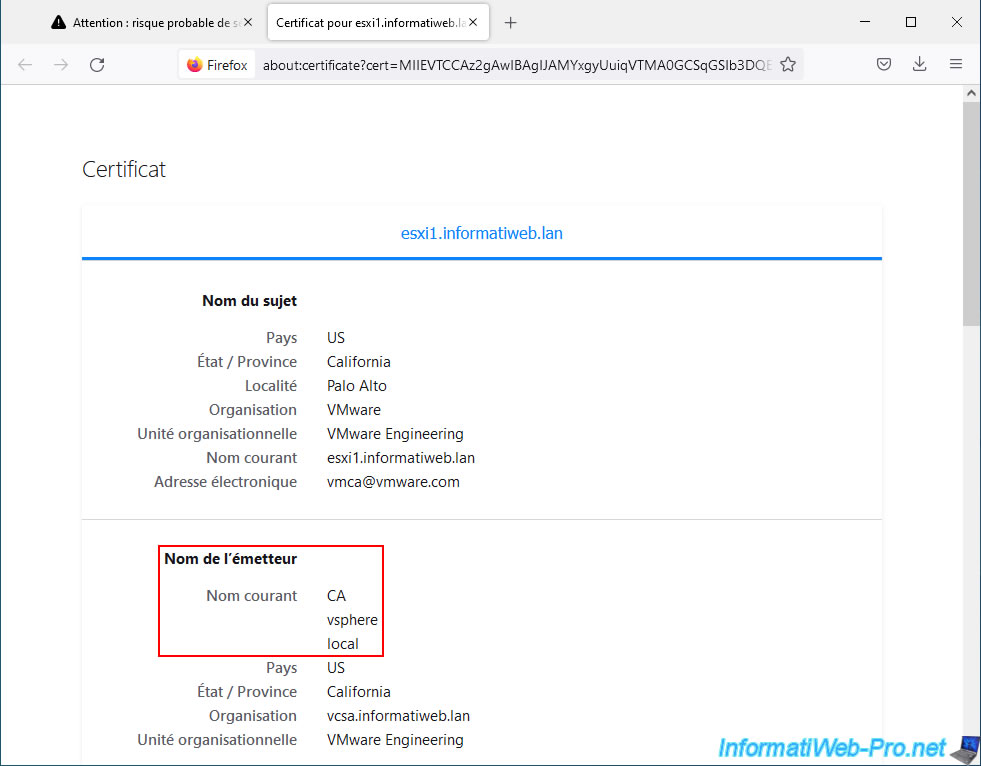
As you can see, when you bind a VMware ESXi host to a VMware vCenter Server (VCSA), the certificate that is generated for that VMware host:
- is valid for its domain name: CN=esxi1.informatiweb.lan.
- is issued by the VMCA certification authority present on your VMware vCenter Server (VCSA) and which you can easily identify thanks to the common name "CA" (CN=CA) and its organizational unit "VMware Engineering".
Indeed, when you link a VMware ESXi host to your VMware vCenter Server (VCSA), your server generates a new certificate via its "VMCA" certification authority used internally and therefore replaces the current certificate of your VMware ESXi host with this new certificate.
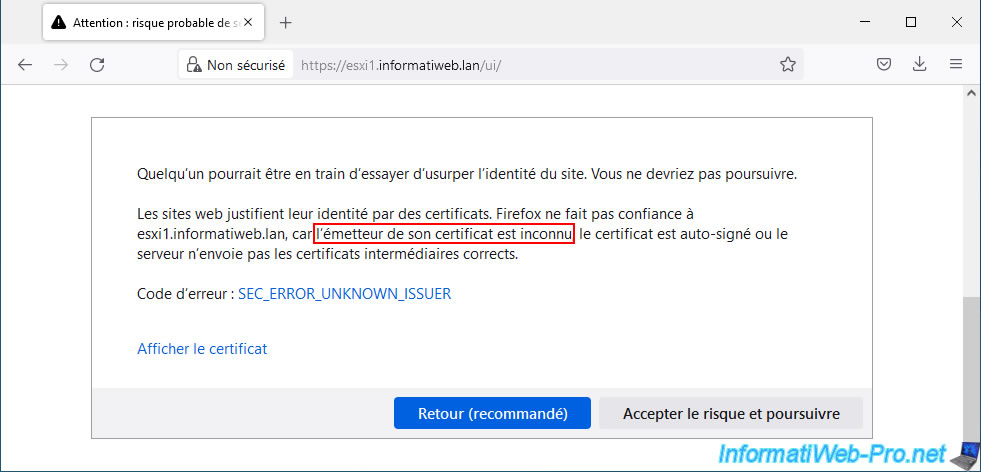
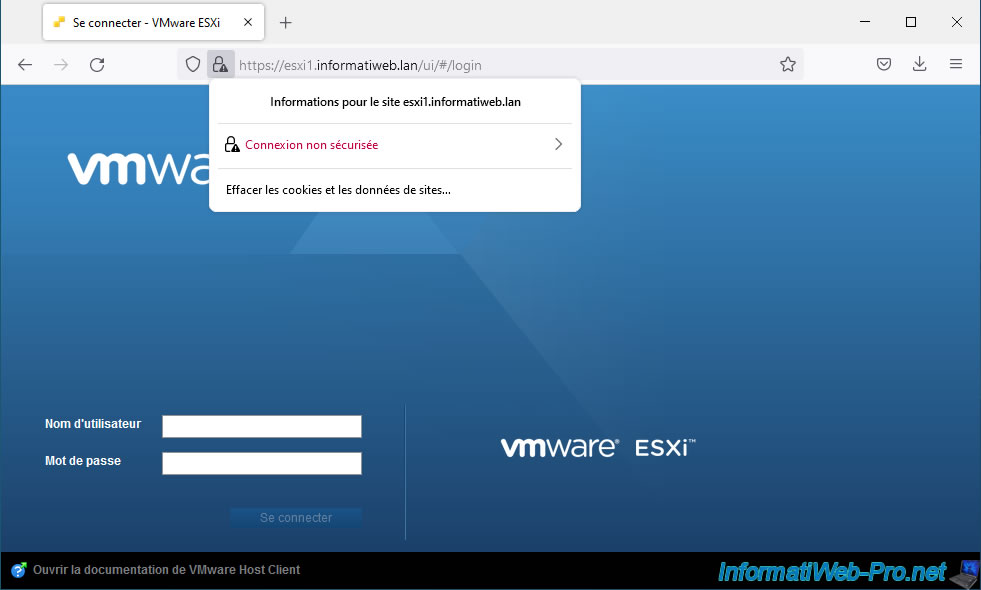
However, if you try to directly access one of the VMware ESXi hosts linked to your VMware vCenter Server (VCSA), you will find that it will not work.
In fact, a security warning will appear telling you that the issuer of the certificate is unknown.
The error code is: SEC_ERROR_UNKNOWN_ISSUER.
This warning is due to the fact that VMCA (whose common name is: CA vsphere local) is used internally by your VMware vCenter Server (VCSA) and that by default your computer does not trust this certificate authority (which he does not know).
If you ignore this warning, you will be able to access the web interface of your VMware ESXi host, but your web browser will consider the connection to be insecure.
8. Trust SSL certificates issued by the VMCA certificate authority
If you want, you can easily trust the certificates issued by this VMCA certificate authority.
To do this, download the certificates from the certification authorities recognized by your VMware vCenter Server (VCSA) by accessing the address: https://vcsa.informatiweb.lan/certs/download.zip.
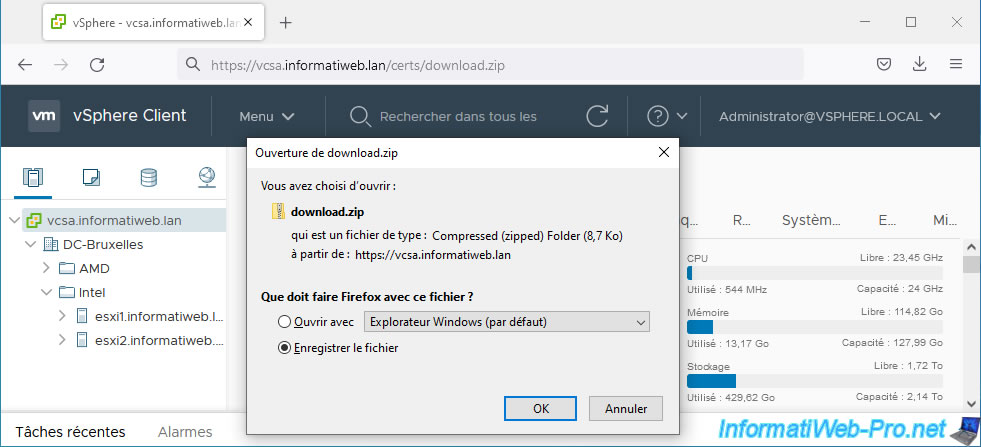
Unzip the downloaded "download.zip" file and go to the folder: download/certs/win.
In this folder you will find 2 SSL certificates in ".crt" format and a certificate revocation list (which you will not need).
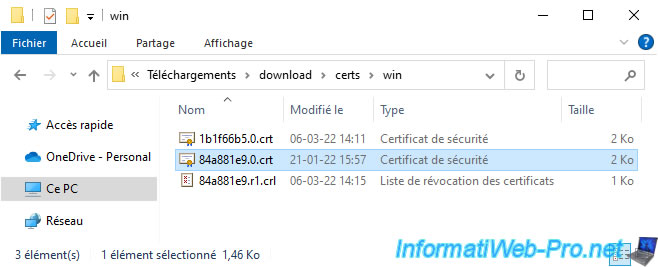
Open the ".crt" files to find the VMCA CA certificate.
You can easily spot it thanks to the name "CA" which will appear for the "Issued to" and "Issued by" lines, as well as the warning concerning trust in this certificate.
To trust certificates issued by this authority only on this computer, click "Install Certificate" and place this certificate in the "Trusted Root Certification Authorities" certificate store on your Windows computer.
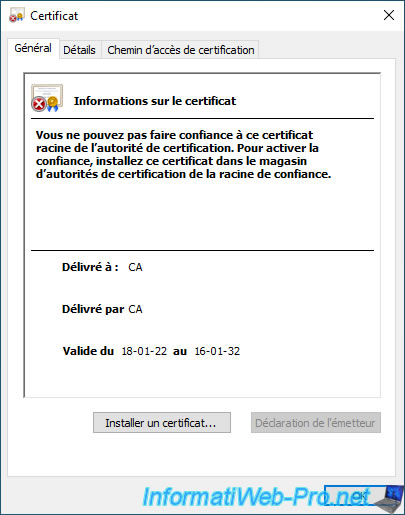
If you want all your computers and/or servers to trust the certificates issued by your VMware vCenter Server's "VMCA" certificate authority (VCSA), use group policies as explained in the "Distribute the certificate to the Active Directory clients" step of our tutorial "WS 2012 / 2012 R2 - Create an enterprise root CA".
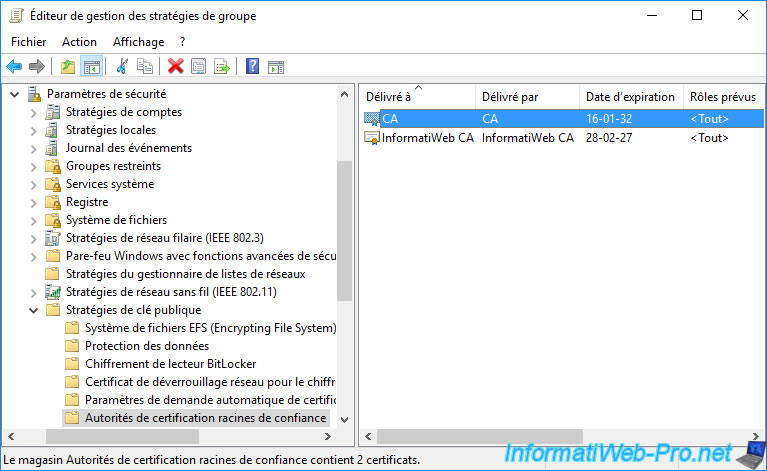
Warning : if you use Mozilla Firefox, you will also need to import it into its certificate store.
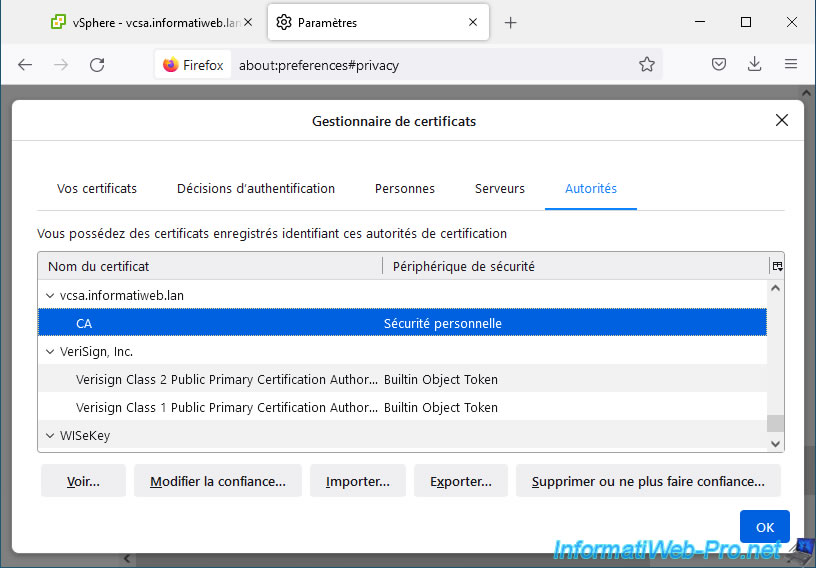
9. VMware ESXi host certificates considered valid
Now that your computer and web browser trust the certificates issued by your VMware vCenter Server (VCSA) "VMCA" certificate authority, the connection will be considered secure.
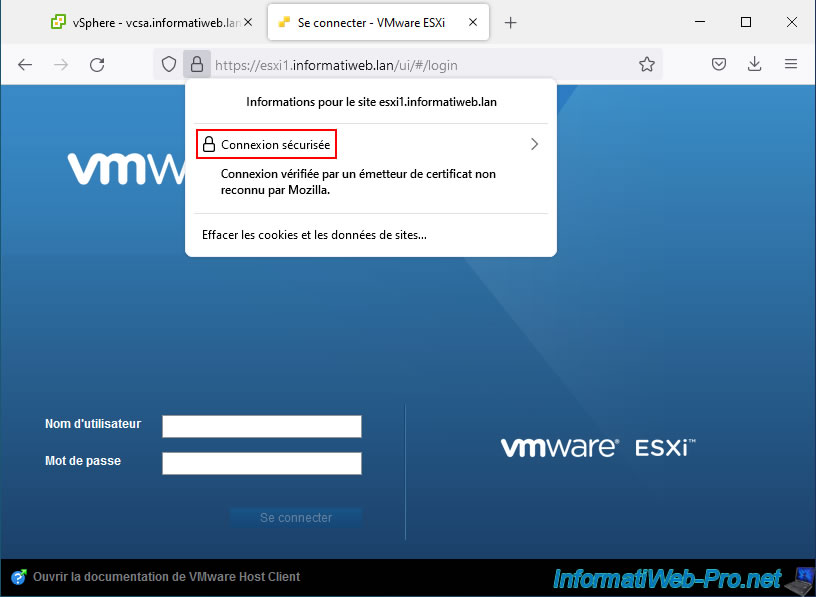
As you can see, the certificate used has been verified by your VCSA server.
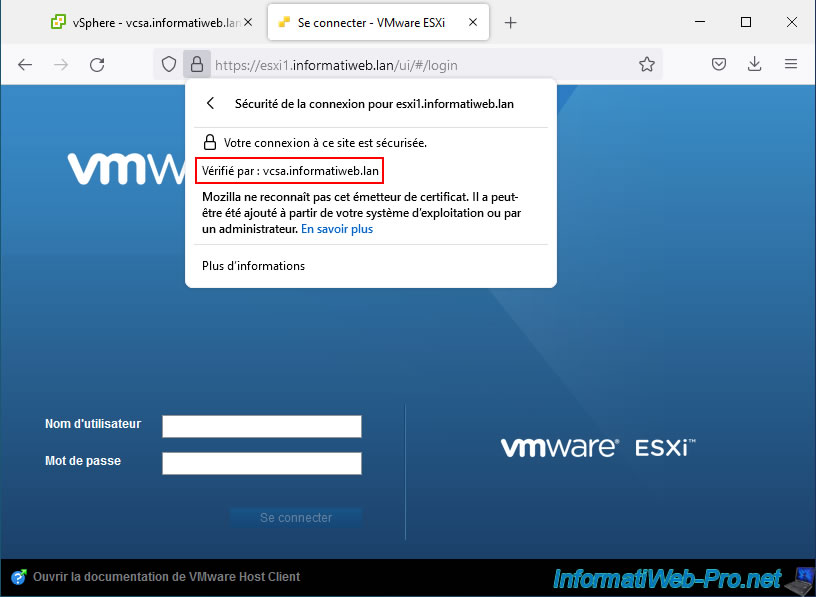
If you click on "More information", then on "View certificate", you will be able to see that this certificate:
- is valid for the domain name of your VMware ESXi host: common name - esxi1.informatiweb.lan
- was issued by the "VMCA" certification authority of your VCSA server: common name - CA vsphere local
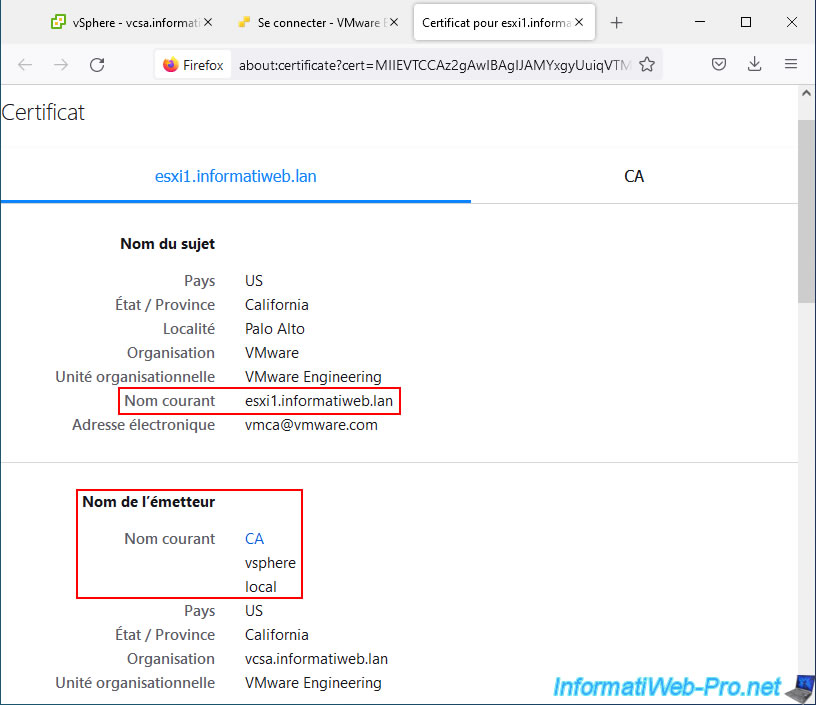
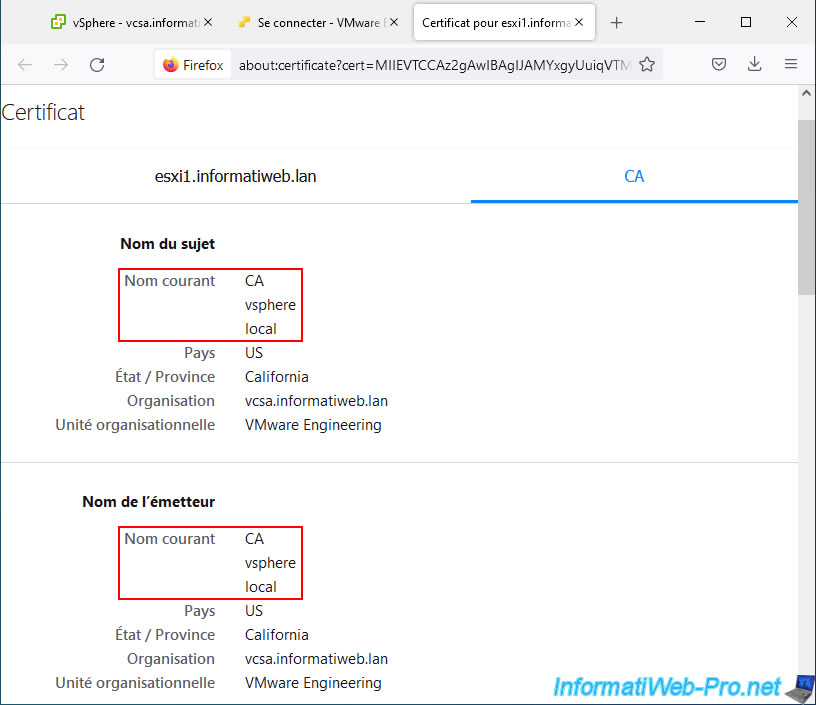
If you click on the "CA" tab, you will see the information about the "VMCA" certificate authority certificate.
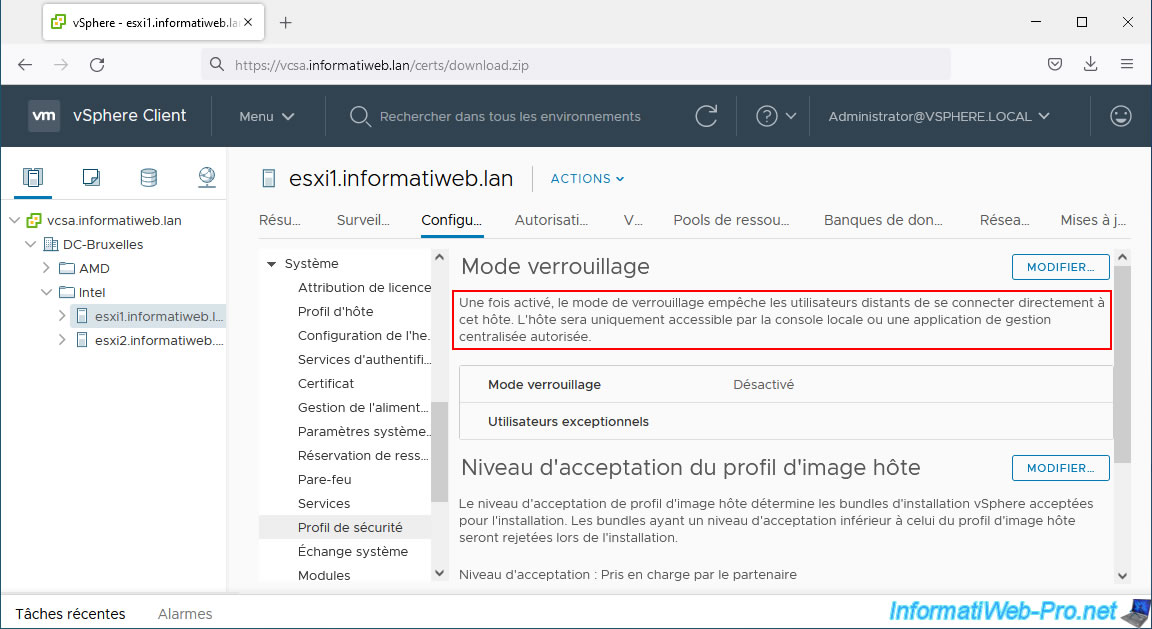
Note that in business, when you link VMware ESXi hosts to a VMware vCenter Server (VCSA), it is common to block direct access to the VMware ESXi hosts so that they are managed only from the VMware vCenter Server (VCSA) concerned.
This way, you only manage permissions on your VMware vCenter Server (VCSA) and your computers do not need to trust the certificates issued by VMCA.
Indeed, the only server that will communicate with your VMware ESXi hosts is your VMware vCenter Server (VCSA) and it already trusts the certificates issued by VMCA.
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

No comment