Monitor network traffic on a vDS switch using NetFlow on VMware vSphere 6.7
- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 29 January 2025 at 16:05 UTC
-

- 2/3
3. Enable NetFlow on your Virtual Distributed Switch (vDS)
In the case of NetFlow analysis of your virtual distributed switch (vDS), you must configure the settings on your VCSA server and not through the ManageEngine NetFlow Analyzer web client.
If you view the ManageEngine NetFlow Analyzer dashboard, you will see that no data is available at the moment.
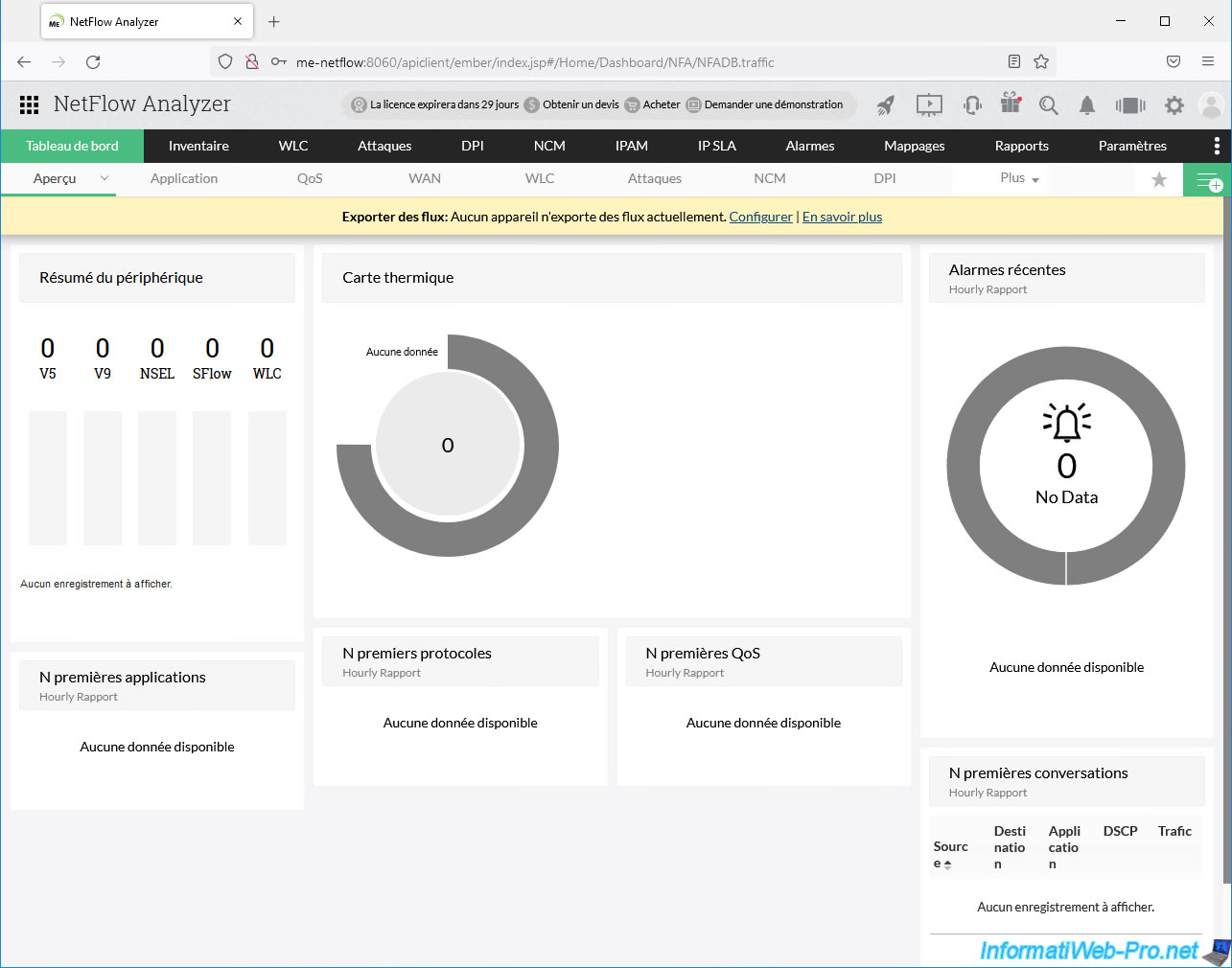
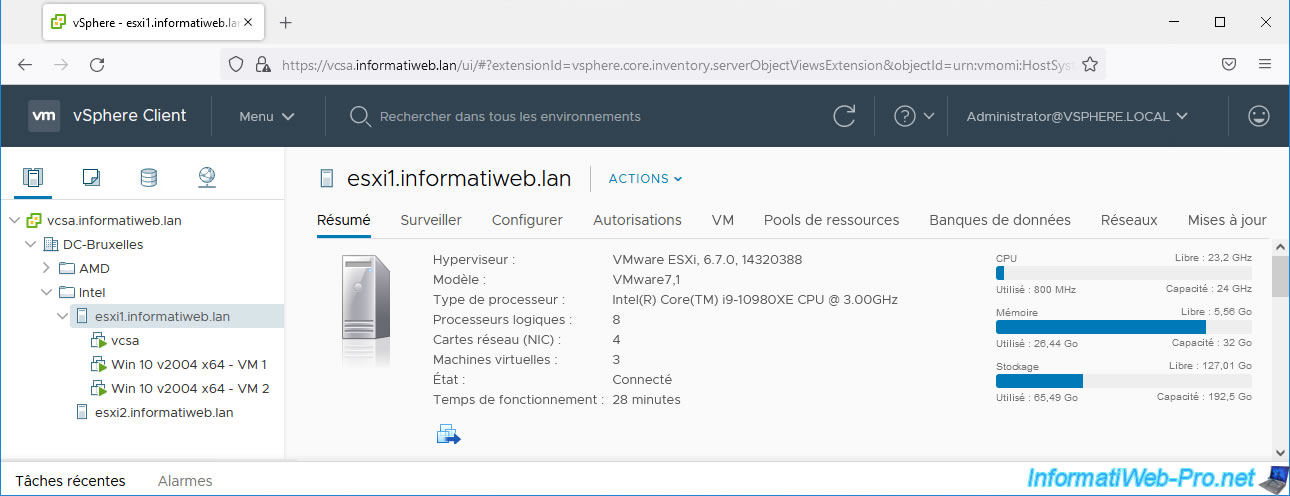
As you can see, in our case we have 2 VMware ESXi hosts.
The 1st VMware ESXi host has 3 virtual machines and the 2nd host has none.
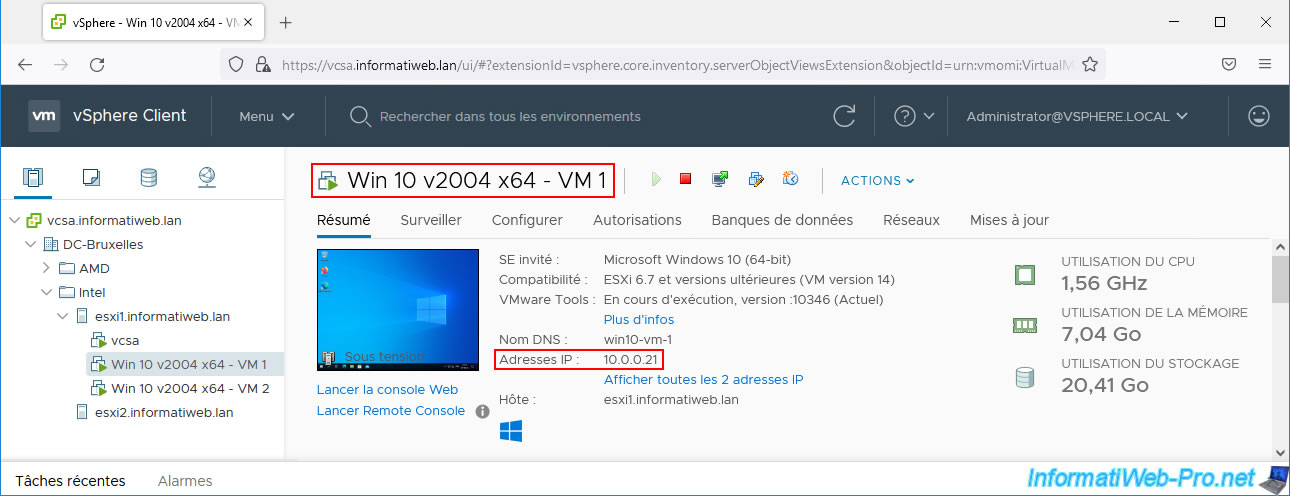
As you can see, your virtual machine "Win 10 v2004 x64 - VM 1" has the IP address "10.0.0.21".
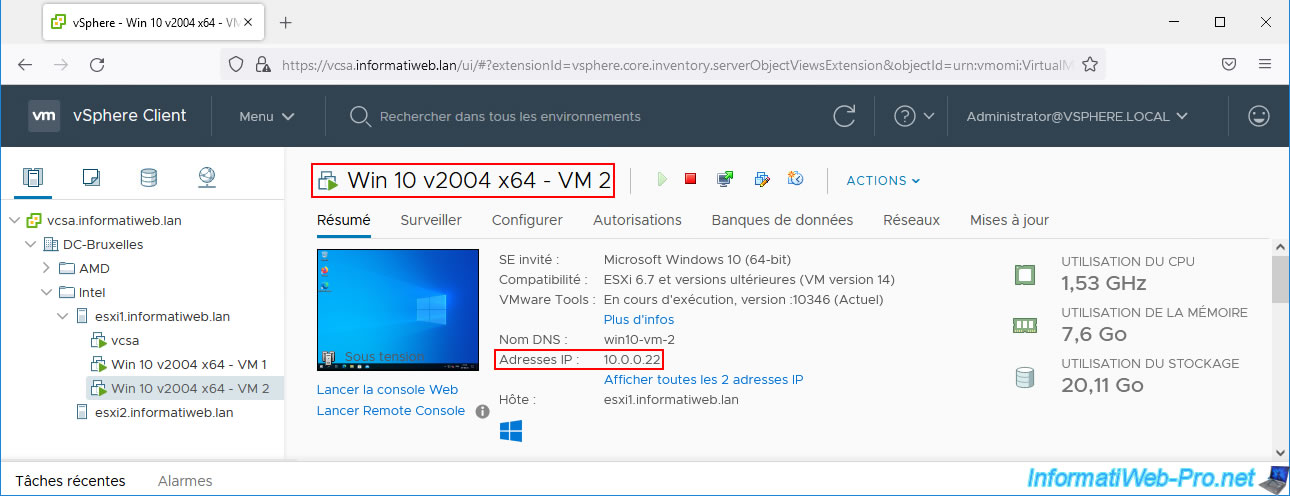
The 2nd virtual machine on Windows 10 has the IP address "10.0.0.22".
This information will help you better understand the data collected through NetFlow later in this tutorial.
In our case, we have a distributed virtual switch "MyDSwitch" with 3 distributed port groups.
All our virtual machines are connected to the “DPortGroup_VMs” port group.
As you can see in the "Features" section of this virtual distributed switch (vDS), NetFlow is supported.
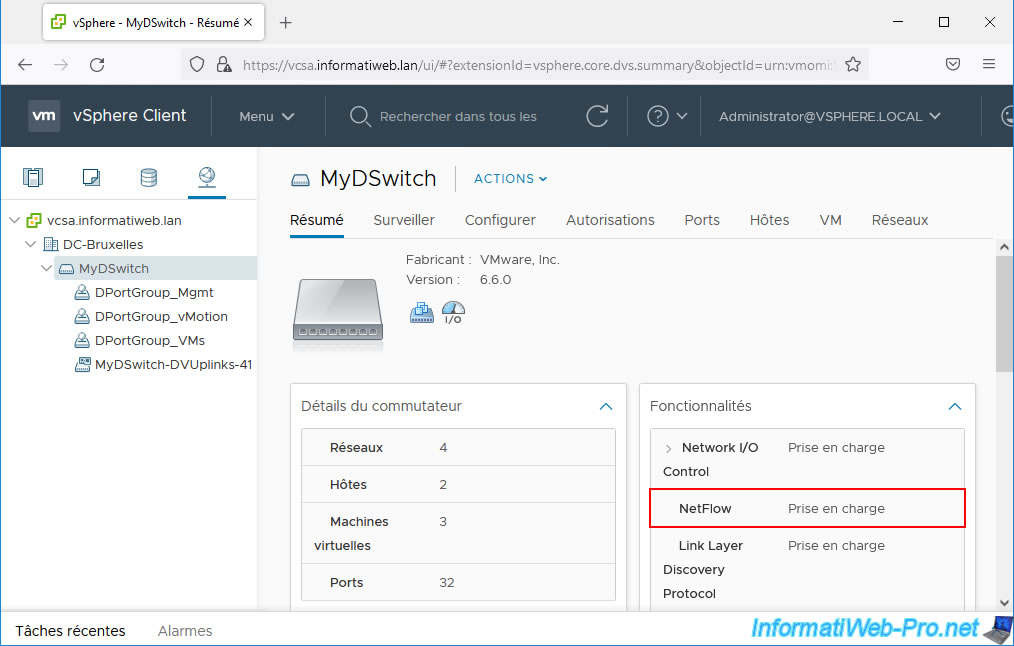
To monitor the network traffic of your virtual distributed switch (vDS) via NetFlow, you need to select it (on the left), then go to "Configure -> Settings -> NetFlow" and click Edit.
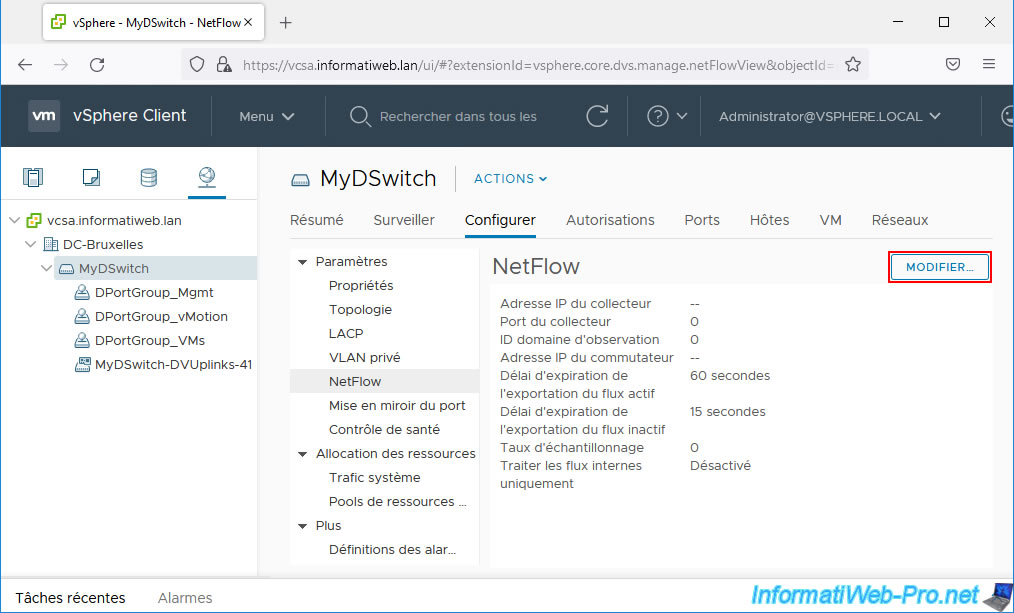
In the "Edit NetFlow Settings - MyDSwitch" window that appears, configure the settings:
- Collector IP address: the IP address of your NetFlow collector.
In our case, the server where "ManageEngine NetFlow Analyzer" is installed has the IP address "10.0.0.15". - Collector port: in the case of ManageEngine NetFlow Analyzer, the port used by default (visible when installing this NetFlow collector) is: 9996.
- Observation Domain ID: identifies information about the switch. 0 by default.
- Switch IP address: a dummy IP address that will allow this distributed virtual switch's network traffic to be displayed as coming from a single switch (MyDSwitch) and not from multiple switches (one per host).
In our case, we indicated the IP address "10.0.0.13" (which does not exist and therefore does not point anywhere). - Active flow export timeout (Seconds): how long to wait before sending information after the flow is initialized.
- Idle flow export timeout (Seconds): same, but for the inactive flow.
- Sampling rate: indicates whether to collect all packets or only 1 packet out of X (defined here).
If you leave the default value "0", all packets will be collected.
On the other hand, if you indicate "1", one packet will be collected, the next one will be canceled, ... - Process internal flows only: if "enabled", this allows only network traffic internal to this distributed virtual switch to be analyzed.
This is useful if the physical switch is already configured to analyze network traffic from the physical network via NetFlow.
In most cases, you will therefore leave this setting disabled to analyze all network traffic (internal to the virtual switch and what is exchanged with the physical network) via NetFlow.
Source : Configure the NetFlow Settings of a vSphere Distributed Switch - VMware Docs.
As you can see by clicking on the little "i" next to the "Switch IP Address" setting, you will see that assigning an IP address to this virtual distributed switch (vDS) will display it as a single device on your NetFlow collector instead of multiple devices (one per ESXi host = each host proxy switch).
Note that this setting is ignored in IPv6 environments.

NetFlow has been configured on your distributed virtual switch.
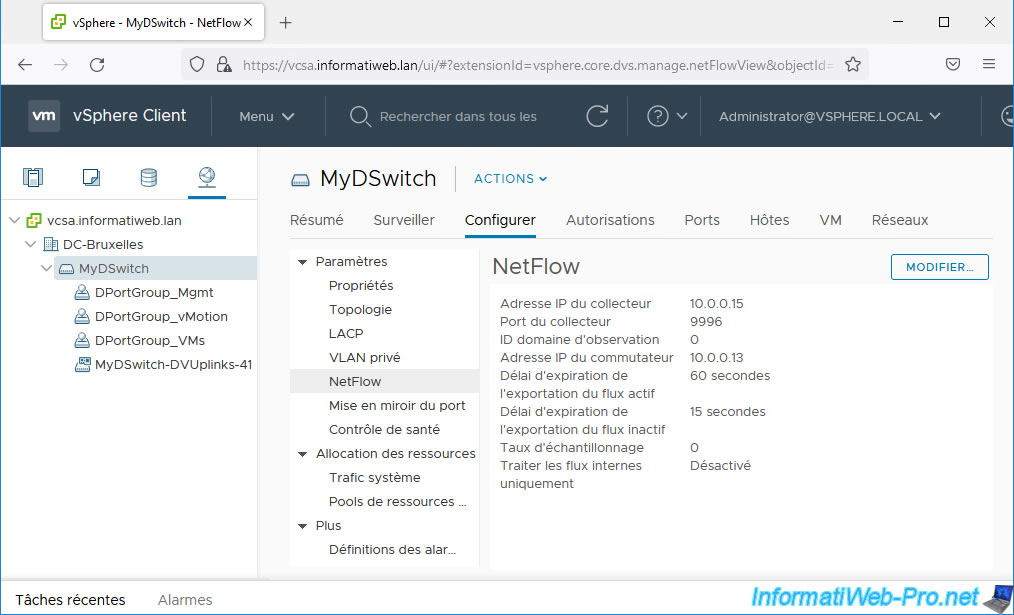
4. Enable NetFlow on your distributed port groups
Once NetFlow settings are configured on your virtual distributed switch (vDS), you must enable NetFlow monitoring on the desired distributed port groups of it.
To do this, select your virtual distributed switch (vDS) and click: Actions -> Distributed Port Group -> Manage Distributed Port Groups.
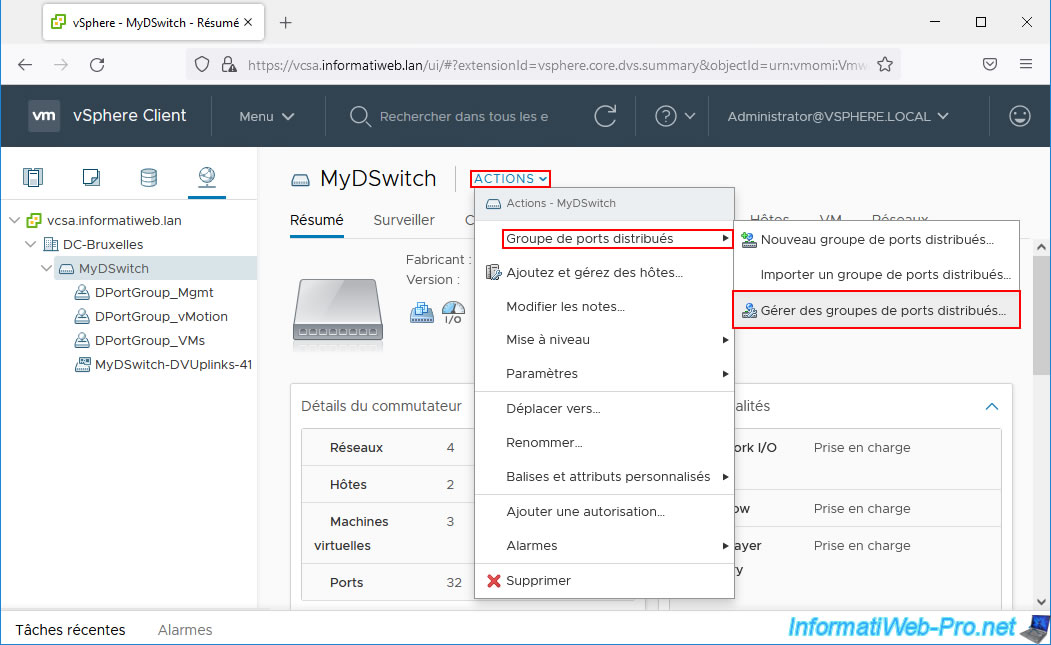
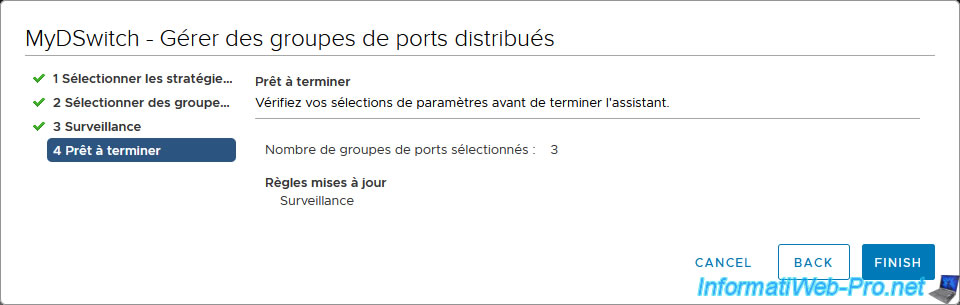
In the "[vDS name] - Manage Distributed Port Groups" wizard that appears, check the "Monitoring" box and click Next.
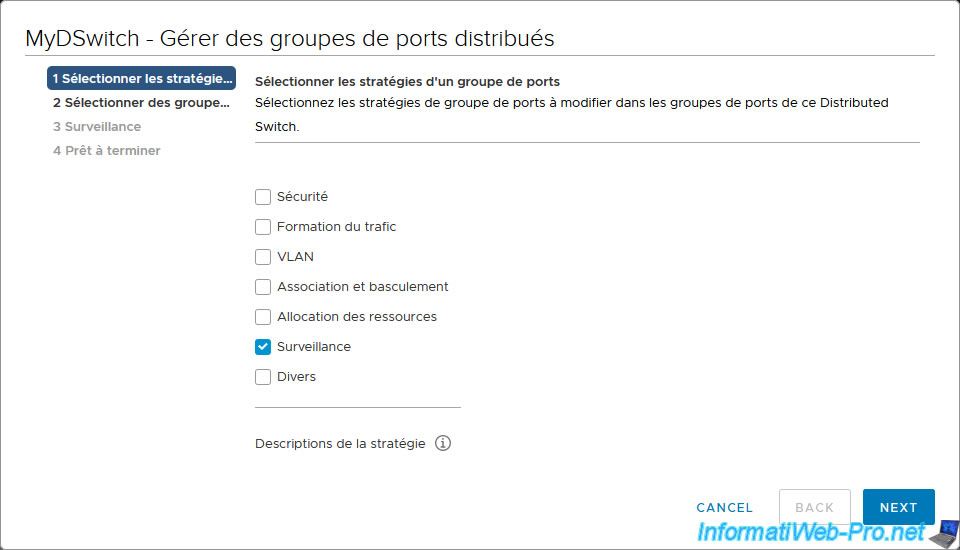
Select the distributed port groups where you want to enable NetFlow.
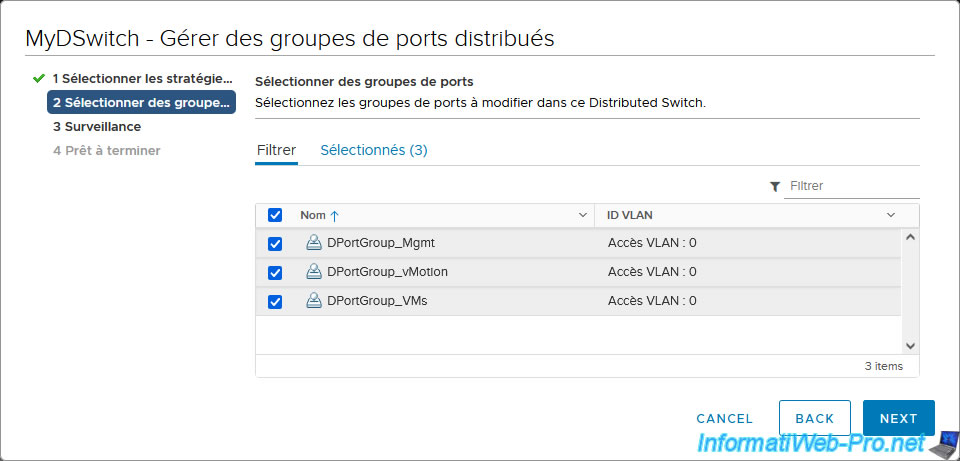
Enable the “NetFlow” setting.
A summary appears.
Click Finish.
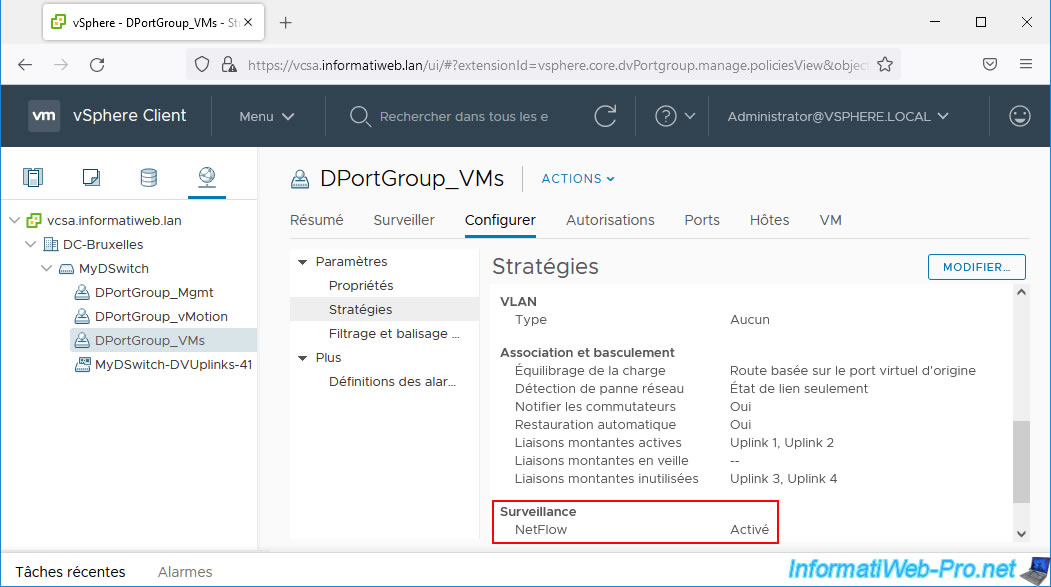
Select a distributed port group where you just enabled NetFlow and go to: Configure -> Policies.
As you can see in the "Monitoring" section, NetFlow is enabled.
Share this tutorial
To see also
-

VMware 12/9/2022
VMware ESXi 6.7 - Manage the virtual hard disks of your VMs from the VMRC console
-

VMware 7/29/2022
VMware ESXi 7.0 / 6.7 - Create a NFS datastore
-

VMware 5/24/2024
VMware vSphere 6.7 - Export and import VMs with VMware Workstation Pro
-

VMware 6/28/2024
VMware vSphere 6.7 - Tasks and events

No comment