Monitor network traffic on a vDS switch using NetFlow on VMware vSphere 6.7
- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 29 January 2025 at 16:05 UTC
-

- 3/3
5. NetFlow information collected
At the bottom right, a notification may appear regarding SNMP.
However, it is not possible to enable SNMP on the Virtual Distributed Switch (vDS).
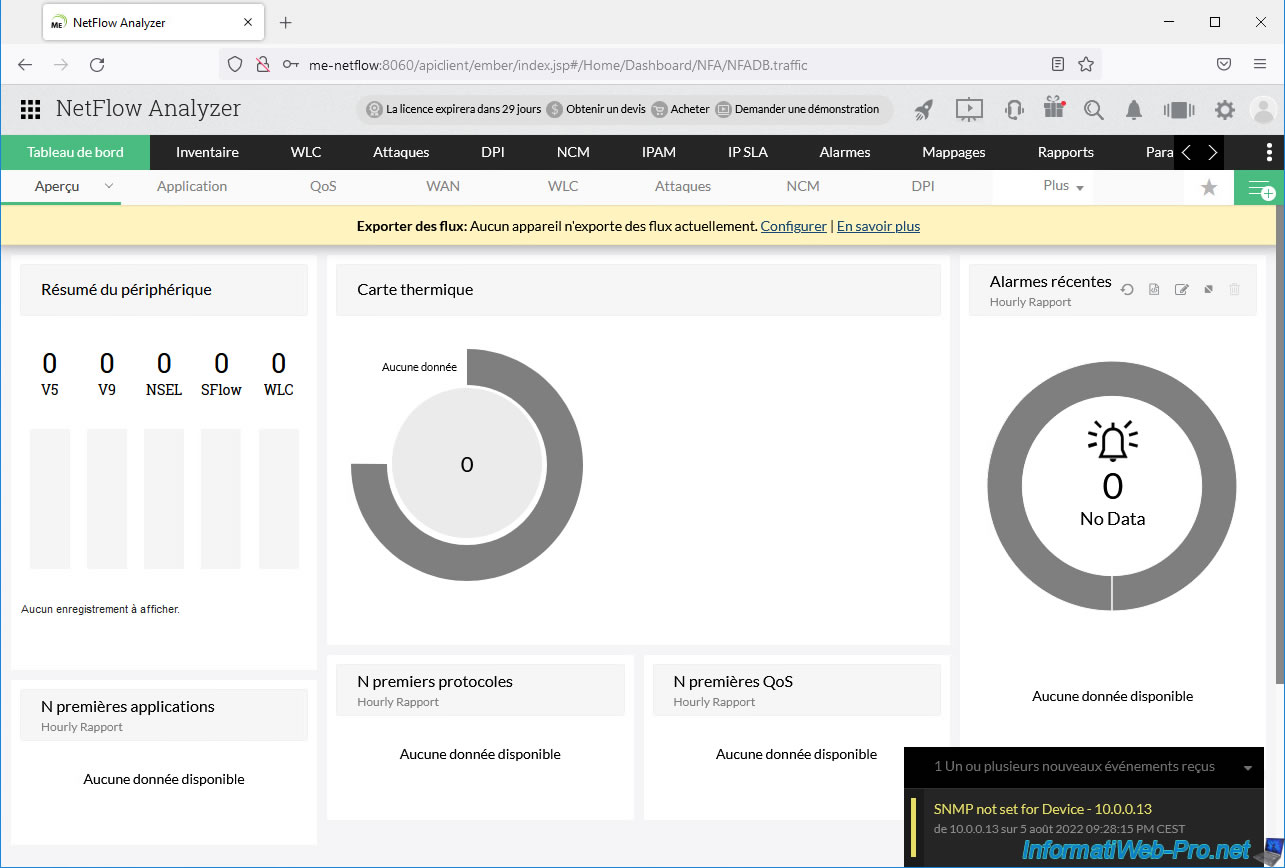
That said, data collection via NetFlow will still work.
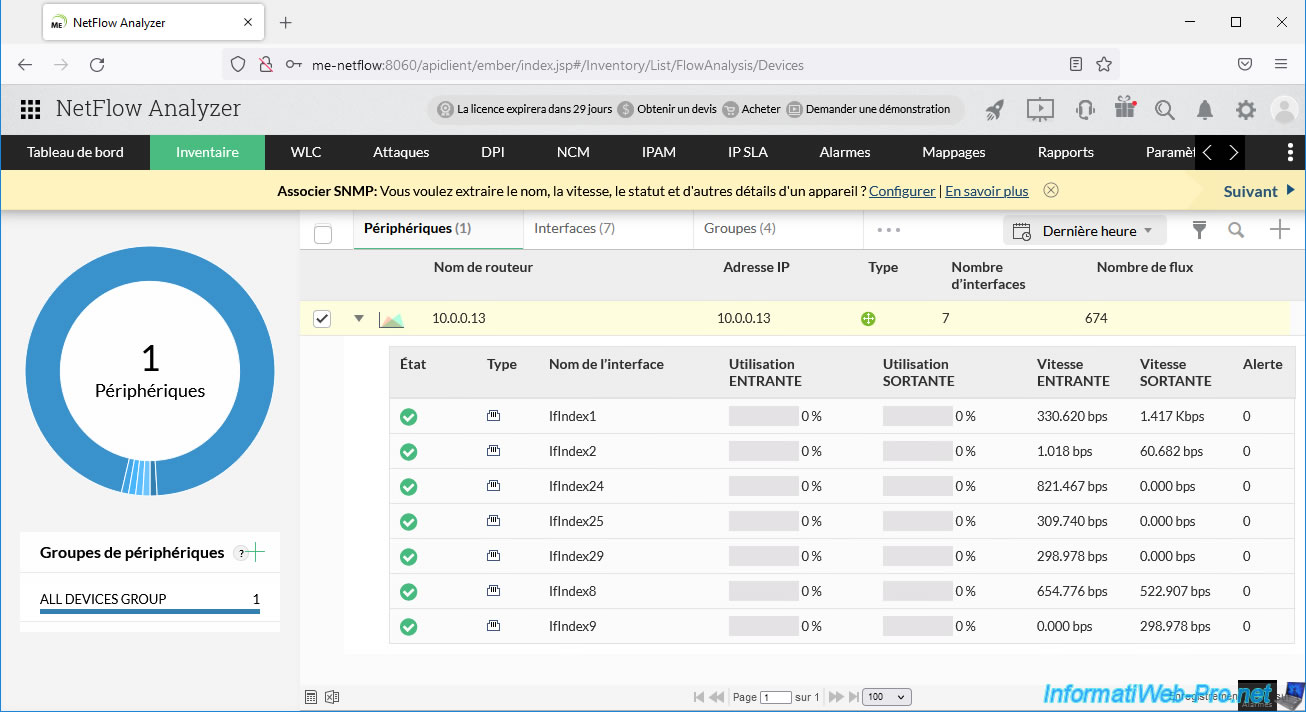
In the "NetFlow Analyzer" web client, go to "Inventory" you will see a device appear (the virtual distributed switch (vDS) whose name corresponds to the IP address of the switch previously configured on vCenter Server).
If you deploy this device, you will see that several interfaces will appear: virtual machines, ...
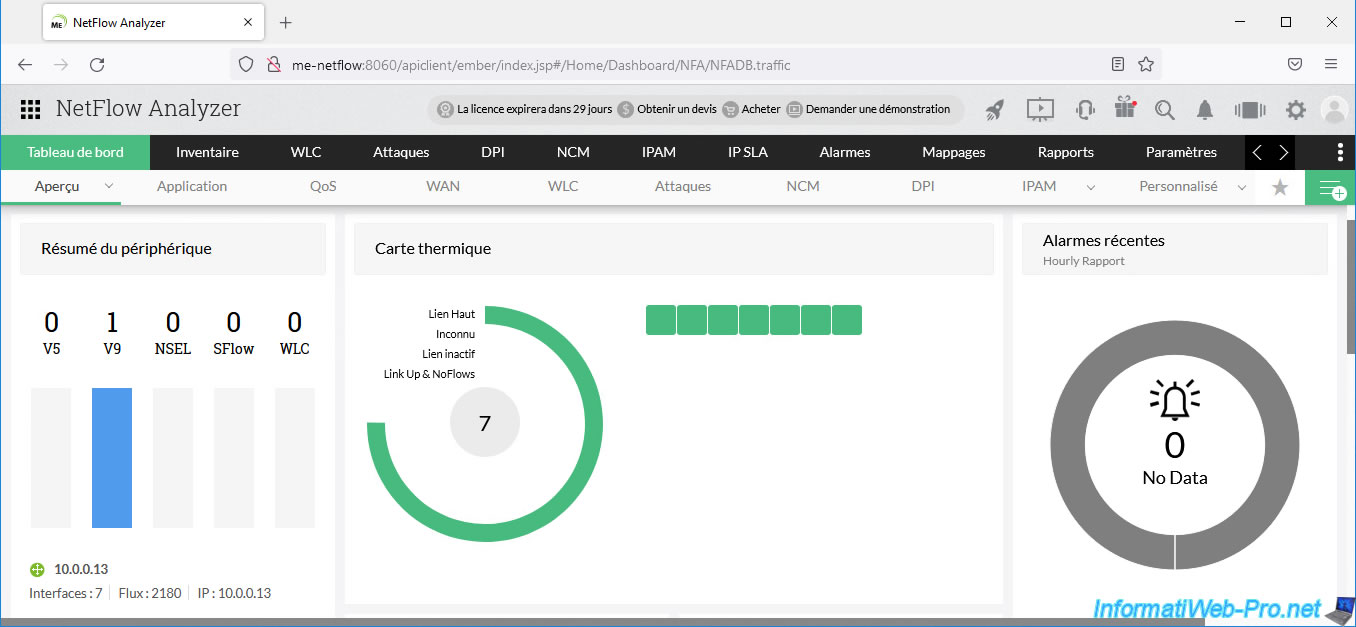
In the "Dashboard -> Overview" section, you will see that there is a NetFlow V9 traffic flow and there are several top links.
Top links correspond to interfaces that are currently in use on your distributed virtual switch and therefore currently have network traffic.
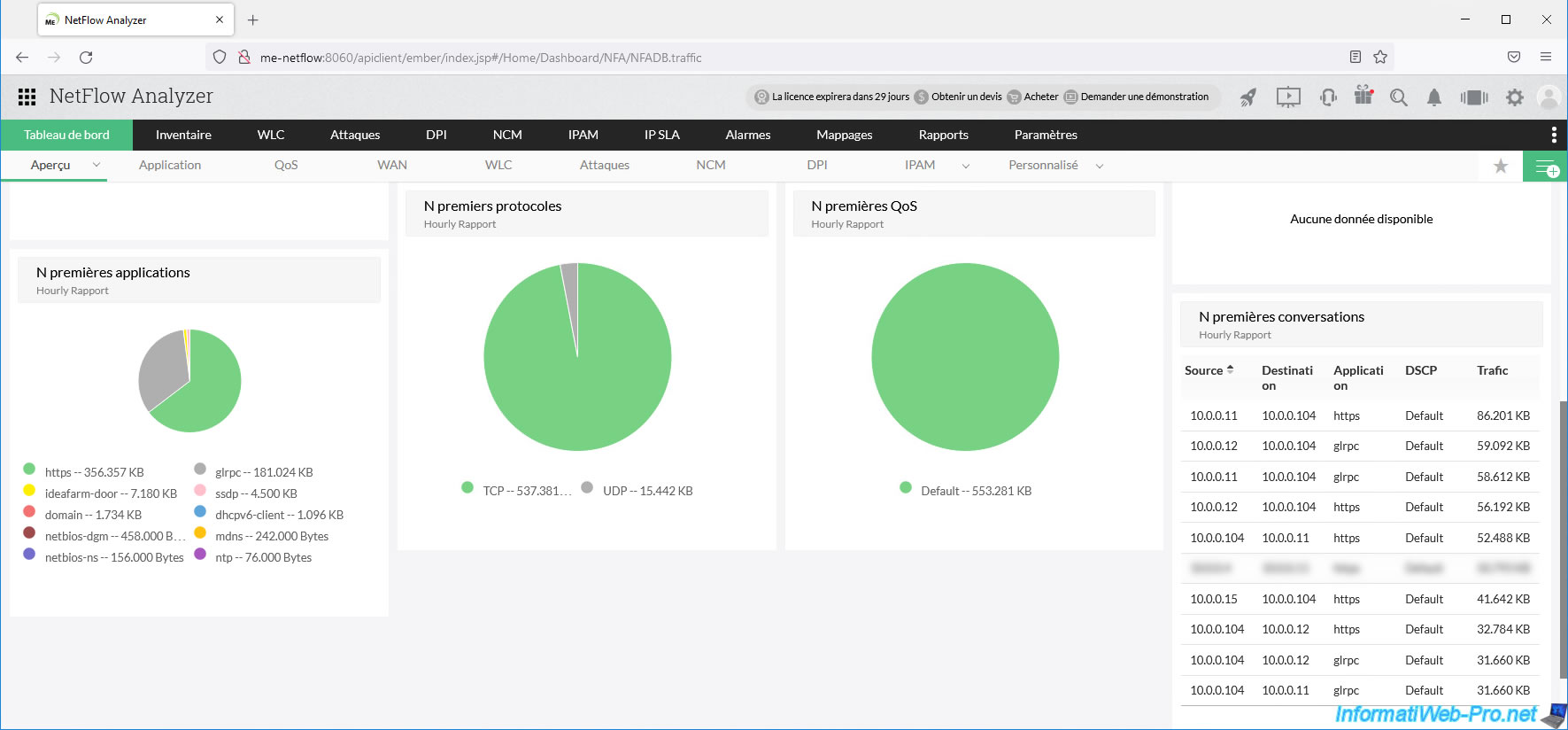
A little further down, you will find information and graphics regarding:
- the most used applications (protocols) on your network: https (mainly for access to secure websites)
- netbios-dgm and netbios-ns: for the NETBIOS protocol used by default on Windows.
- domain: for Active Directory (AD) domain services.
- ntp: for clock synchronization from a time server via the NTP protocol.
- and more
- the most used protocols on your network: TCP / UDP.
- QoS (quality of service).
- conversations: network traffic between 2 machines (clients or servers).
6. Spotting a high download on your network
Although you should rather manage your bandwidth correctly by managing its allocation via NIOC (for example), you can also use NetFlow to spot downloads prohibited in your company.
For this, we downloaded a known live repair CD which is around 3 GB. The goal being only to download a large file from a virtual machine connected to our distributed virtual switch to locate this download via NetFlow.
Indeed, if someone downloads for too long, it risks blocking access to other services hosted on your VMware ESXi hosts since it saturates your bandwidth.
This download can obviously be legitimate in some cases, but not always.
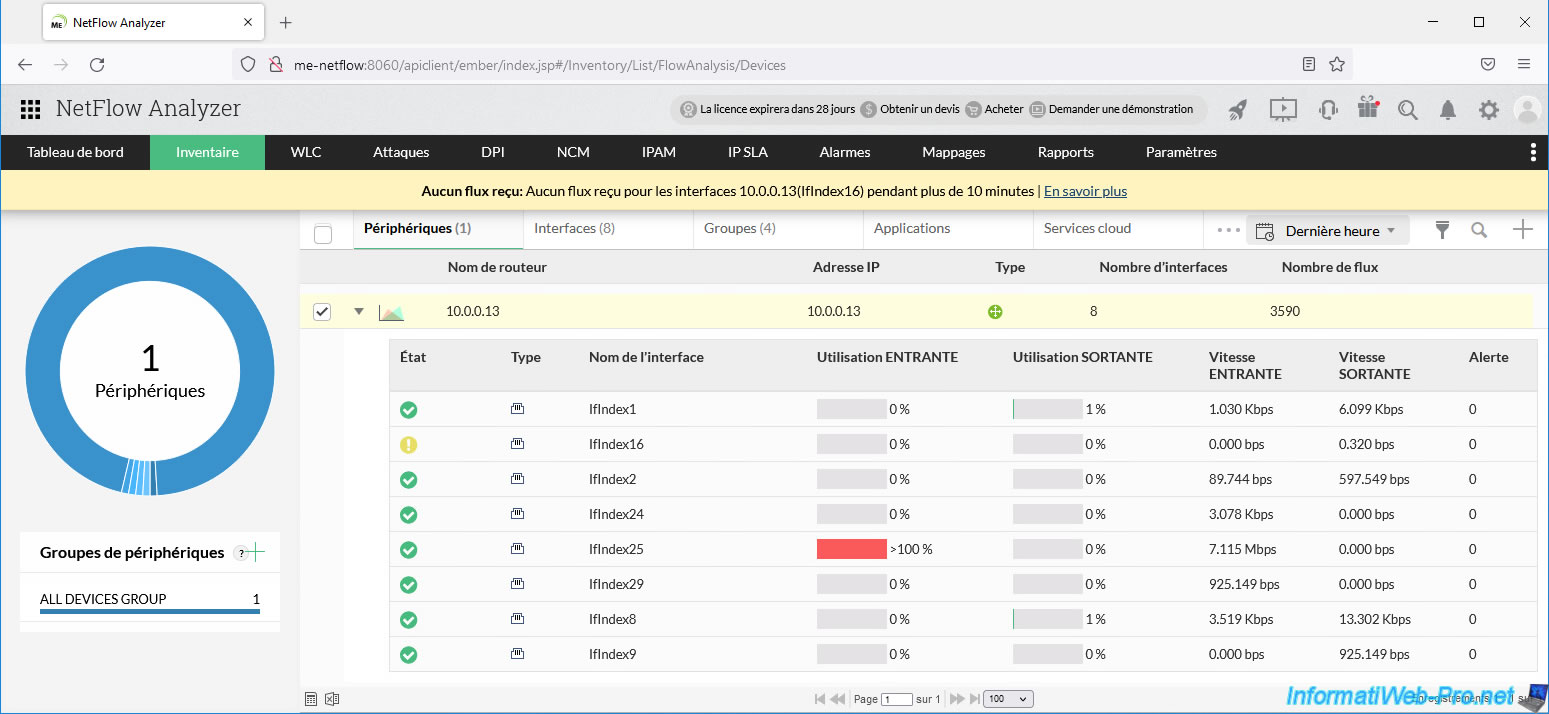
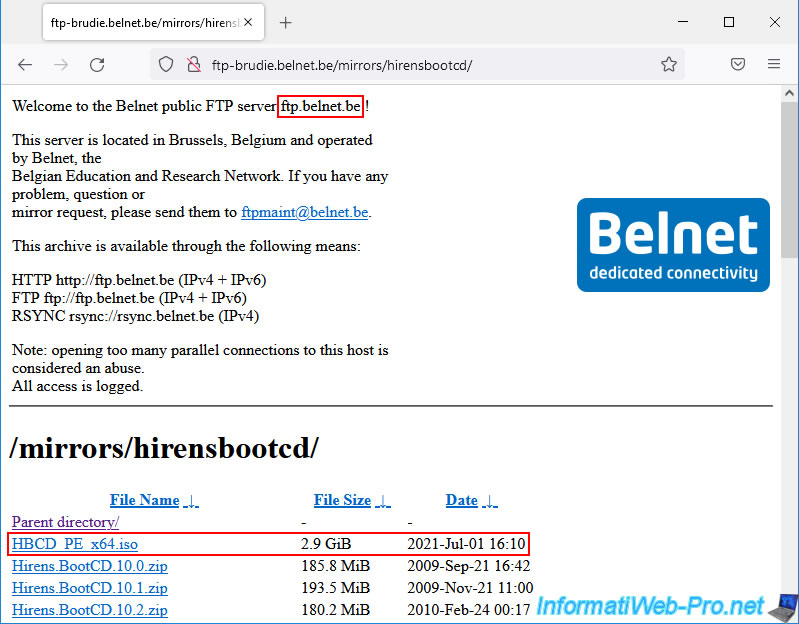
In the ManageEngine NetFlow Analyzer Inventory section, you will see that an interface is currently heavily used.
In our case, we can see that the "IfIndex25" interface of our distributed virtual switch (10.0.0.13) is 100% utilized and the incoming throughput is around 7 Mbps.
Since the virtual machine downloads data from the Internet, traffic therefore enters this VM through this interface.
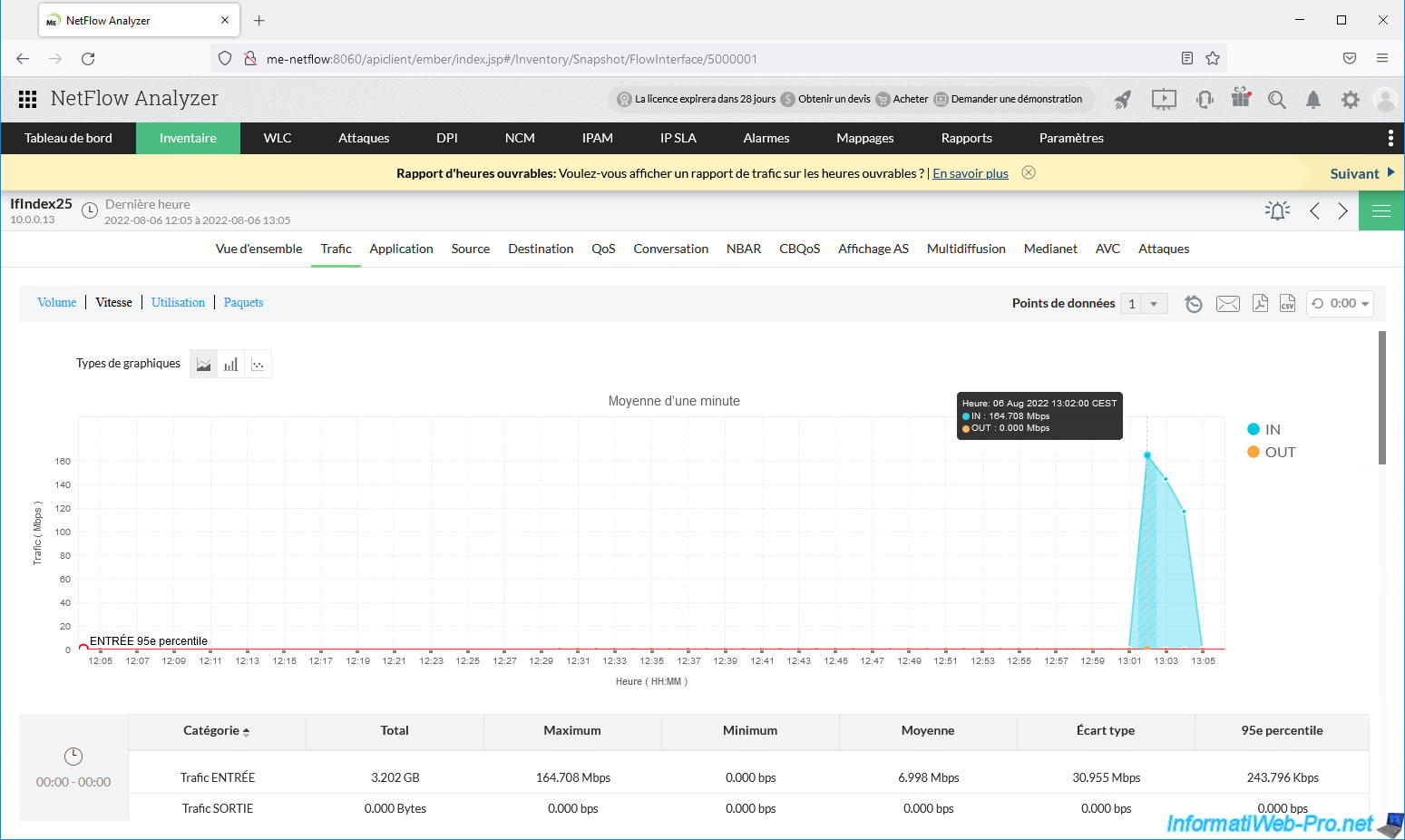
If we click on this interface and go to the "Traffic" tab, we can see that there is mainly incoming traffic (IN) and that there was 3.2 GB of data that passed into the network.
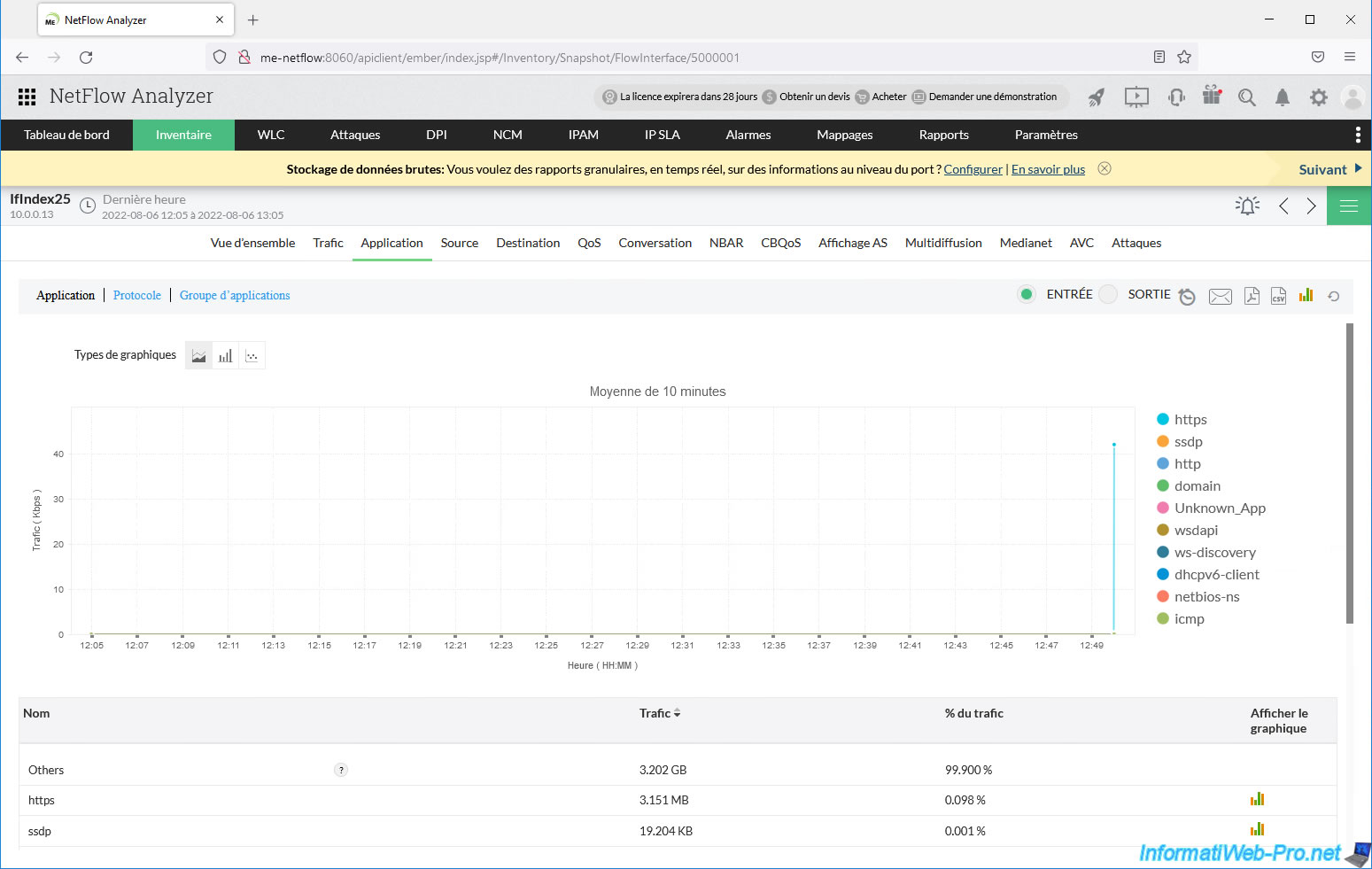
In the "Application" tab, we can see that the protocol used is mainly "https".
Which means the download is done from a secure website.
At the moment, in the "Source" tab we can see that the source of the 3 GB of data downloaded is: Others.
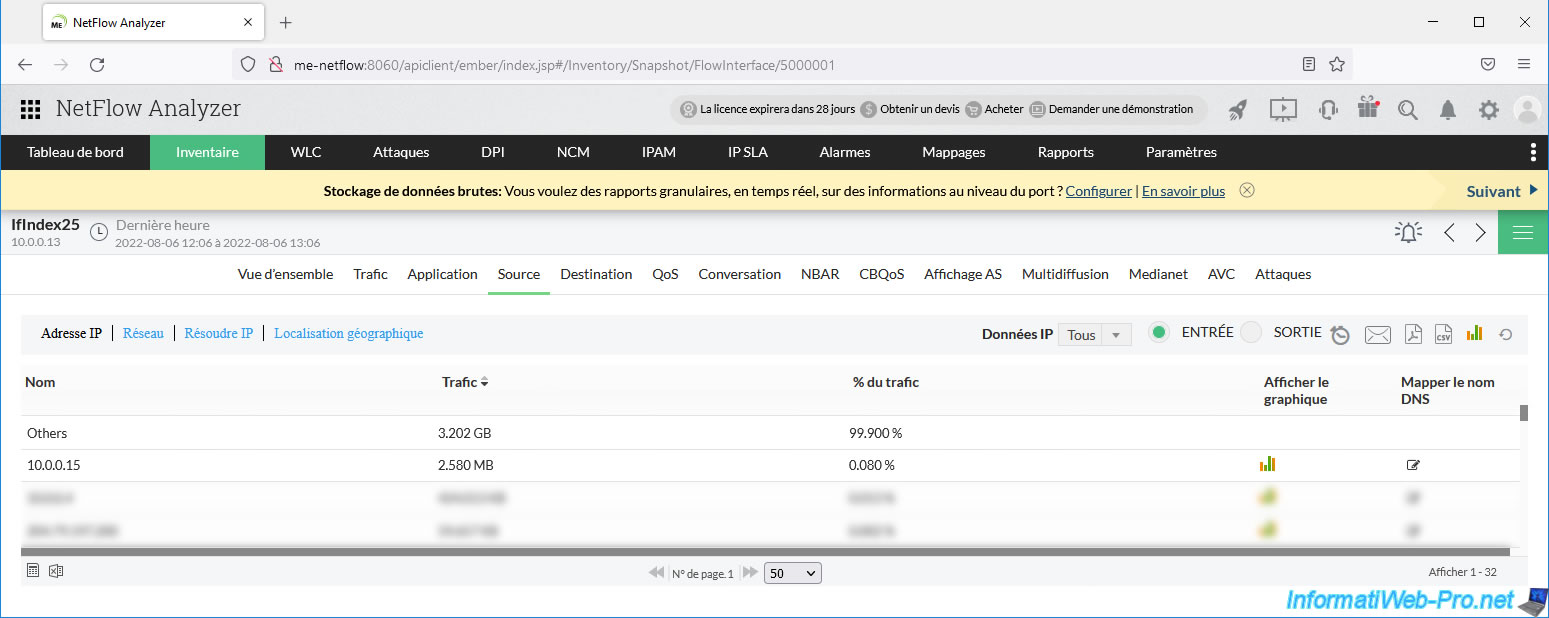
Same in the “Destination” tab.
You can see the name "Others" again instead of the destination IP address.
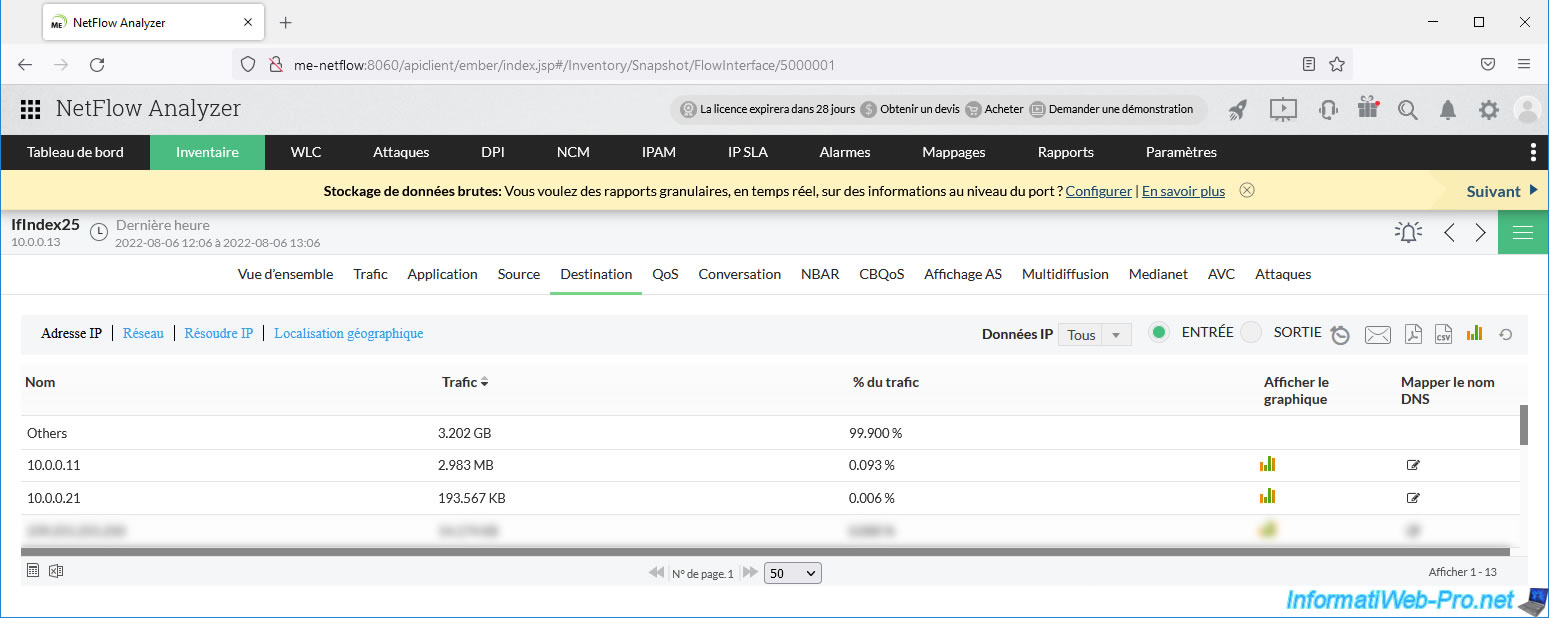
As you can see, in our case the large file was downloaded from the domain "belnet.be".
Indeed, the site has partners who allow you to download their live CD from a server that is physically closer to you.
Given that we are in Belgium, the download was therefore carried out from a server hosted in this country.
Later, you will see that the source and destination IP addresses have appeared in the NetFlow data.
Indeed, you have to wait for your virtual distributed switch (vDS) to send the new NetFlow data for you to see it on your NetFlow collector.
In our case we can see that the source IP address is: 193.190.198.27.
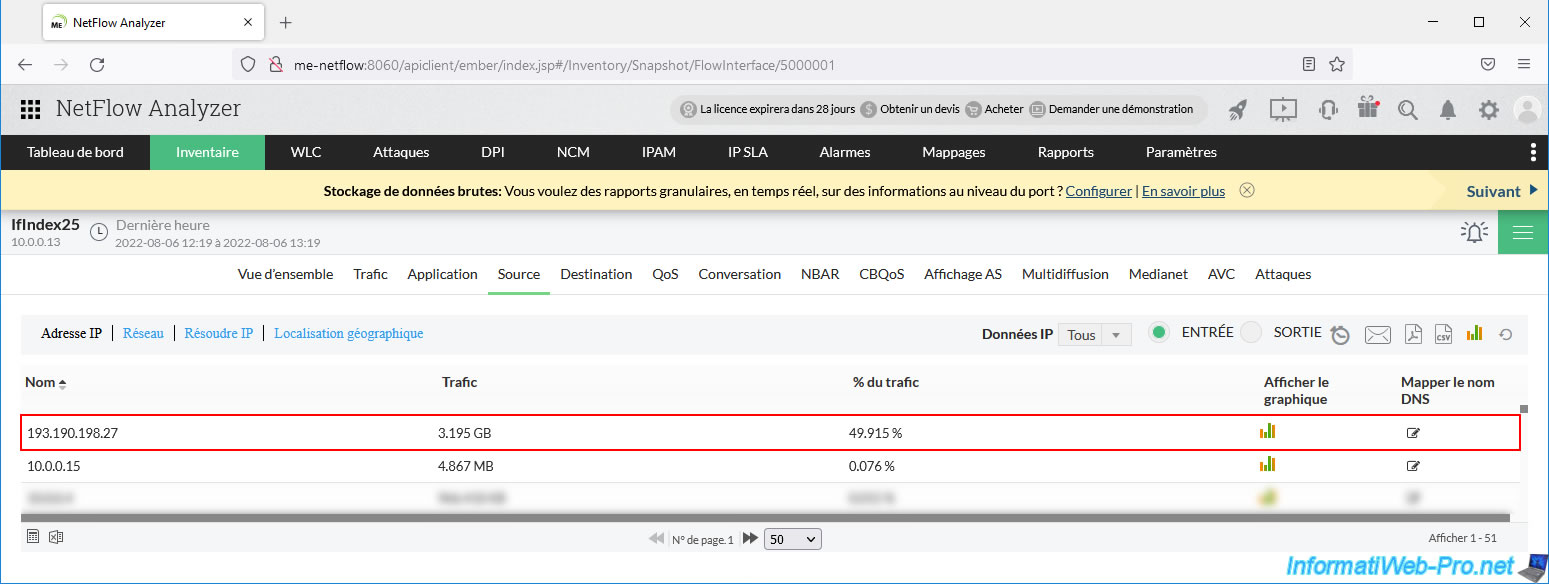
For the destination IP address, we can see that it is IP address "10.0.0.21".
We can therefore know that it is the user of our virtual machine "Win 10 v2004 x64 - VM 1" who downloaded so much data. (Note that this could also be the reverse, in the case where you sent data to this VM from a computer located outside your company).
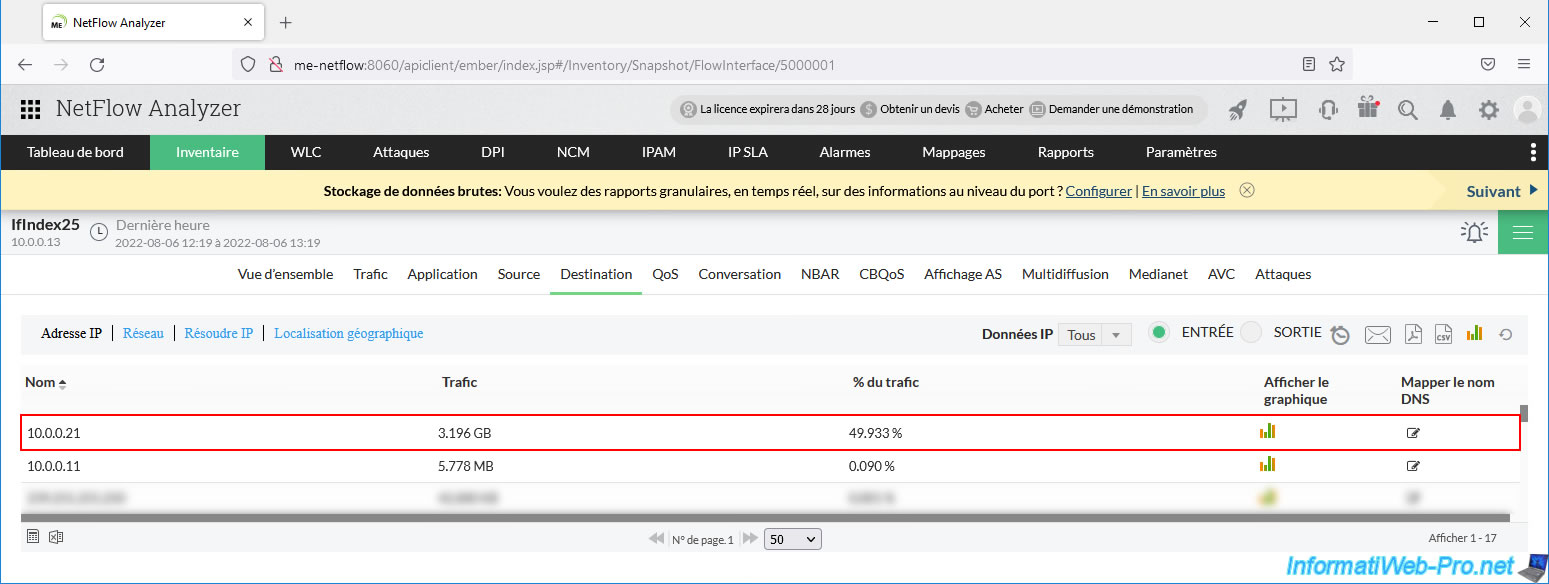
To find out the domain name associated with an IP address, you can try to use the "nslookup" command available on Windows and Windows Server by simply specifying the IP address as a parameter.
If reverse DNS is correctly defined on the DNS server concerned, the associated domain name will appear.
In our case, we can see that it is the server: ftp-brudie.belnet.be.
Which corresponds to the domain name "belnet.be" which was displayed when downloading the large file from our VM.
Important : this is not always this simple given that certain large files are sometimes hosted on third-party servers (such as: Amazon Web Services) or on CDNs.
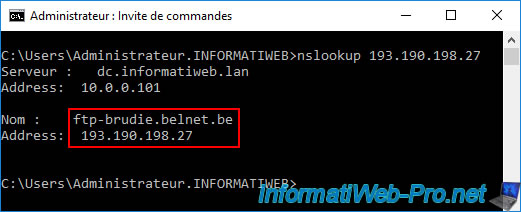
Another way to find out what an IP address is is to look for it on the RIPE website (which is the official manager of IP addresses).
As expected, we see again that the company concerned by this IP address is "BELNET" and that the contact address again refers to the domain "belnet.be".
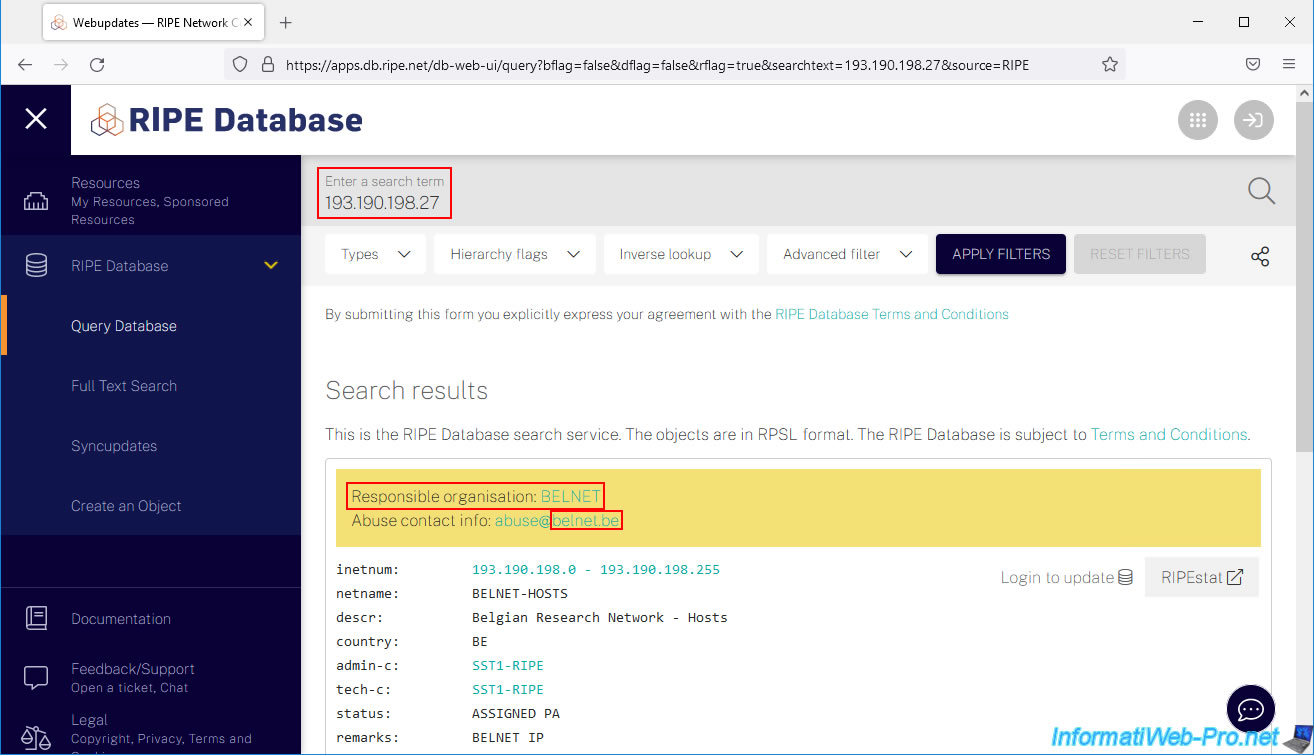
Note that you can also use other third-party sites, such as "DomainTools" to obtain this same information.
On this site, we can also see the reverse DNS of this IP address: ftp-brudie.belnet.be.
If we type in the domain "ftp-brudie.belnet.be", we can see that it is an alias of the domain "ftp.belnet.be".
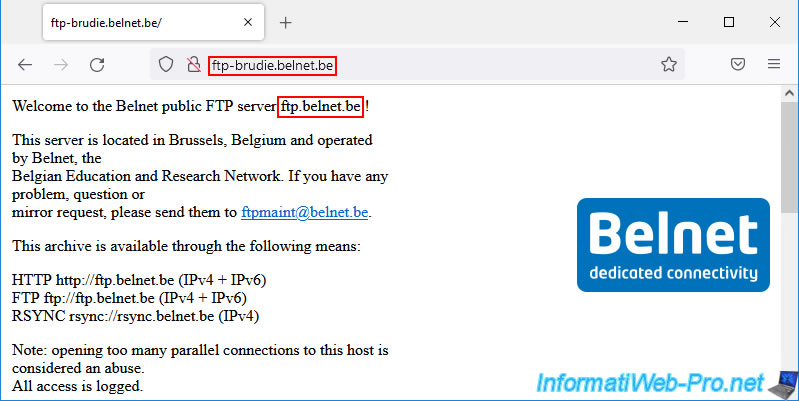
By searching a little in the folders of this server, we realize that there is indeed the file which had been downloaded previously.
In short, as you will have understood, this download was legitimate.
But if someone is spending time downloading data from an IP address (which corresponds to a server or website that you do not allow on your network), this will allow you to stop these prohibited downloads).
Warning : the same IP address can be used by several websites. This is very often the case because of shared web hosting allowing users to host their websites at a lower cost.
Share this tutorial
To see also
-

VMware 3/24/2023
VMware ESXi 6.7 - Enable Jumbo frame support
-

VMware 9/7/2022
VMware ESXi 7.0 / 6.7 - Export and import VMs with VMware Workstation Pro
-
VMware 2/12/2025
VMware vSphere 6.7 - Create a datastores cluster and enable SDRS
-
VMware 6/19/2024
VMware vSphere 6.7 - Manage VCSA files via WinSCP

No comment