- VMware
- 31 July 2024 at 15:23 UTC
-

By default, you can connect to the vSphere Client using a local account (localos) or from an account in the SSO domain "vsphere.local" created during the deployment of VMware vCenter Server (or VCSA).
To avoid multiplying the places where you will have to manage different user accounts, you can use the user accounts present on your Active Directory infrastructure by adding your Active Directory domain as an identity source.
- Add Active Directory identity source
- Set a default identity source
- View Active Directory users from vCenter Server
- Add an Active Directory user to a vCenter group
- Log in to vCenter Server with a user from your Active Directory domain
1. Add Active Directory identity source
To get started, log in as "administrator@vsphere.local" to the vSphere Client: https://vcsa.informatiweb.lan/ui/
Then, go to: Menu -> Administration.
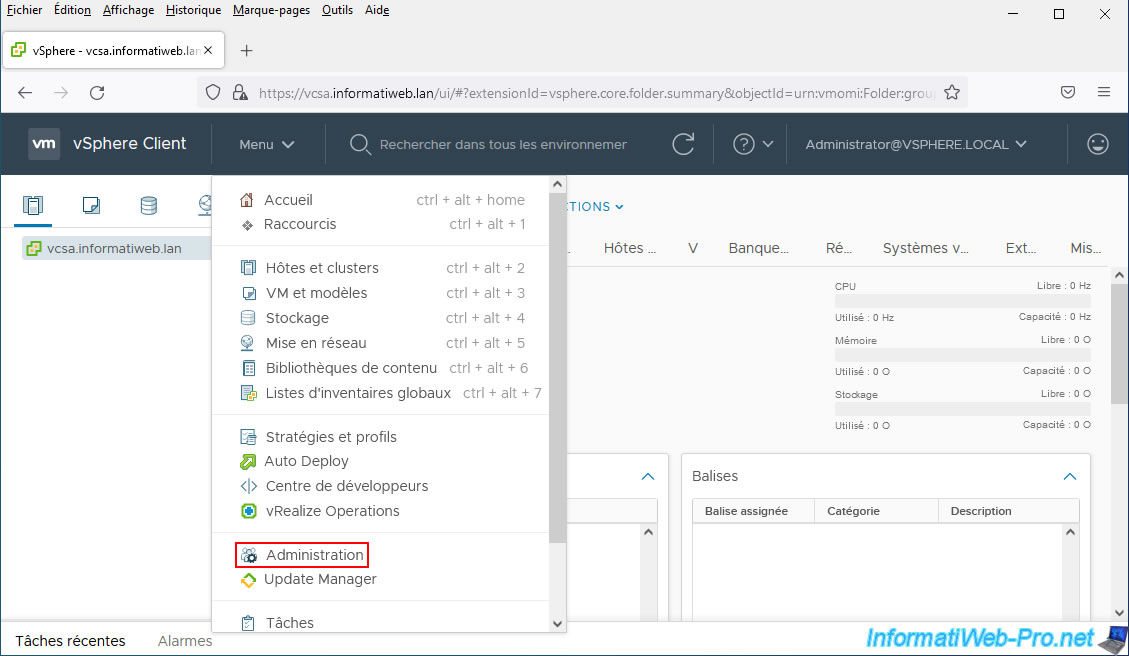
In the left menu, go to "Single Sign-On -> Configuration".
In the "Identity Sources" tab, click "Add identity source".
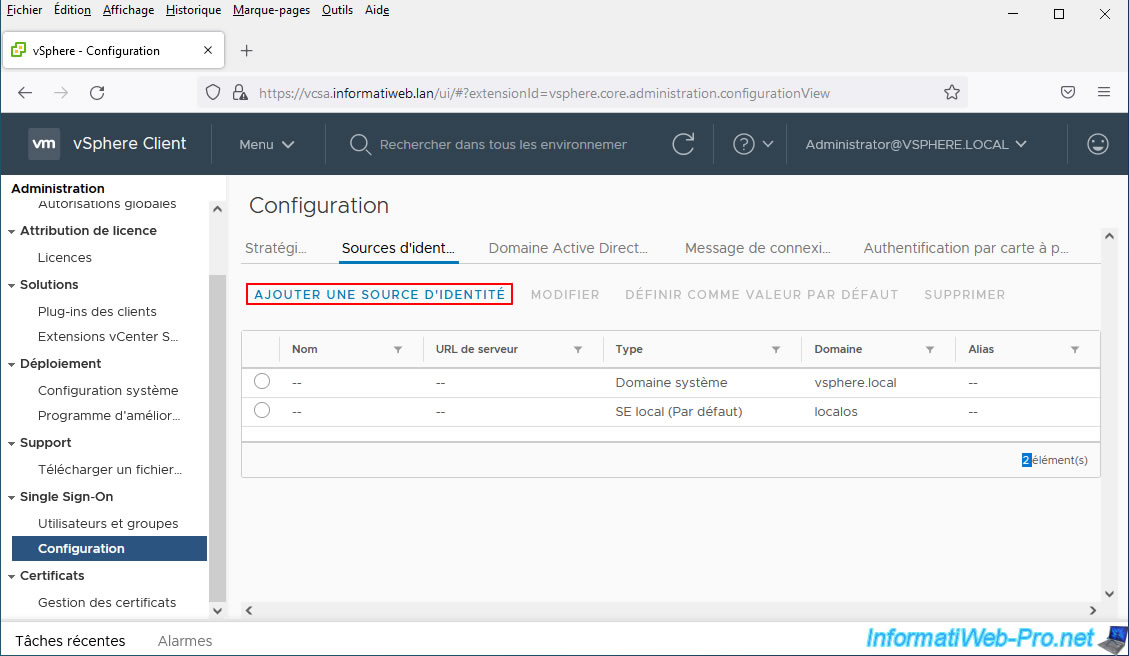
By default, the selected identity source type is "Active Directory (Windows Integrated Authentication)".
However, this type of identity source requires that the vCenter Server is already linked to an Active Directory domain.
If you are on Windows, you have probably already linked it to an Active Directory domain, so you could use it without any problem by referring to step "2. Add an identity source" of our tutorial on joining VMware vCenter Server (VCSA) to an Active Directory domain.
Otherwise, select "Active Directory over LDAP".
A form will appear with many settings to configure.
To get started, you'll need the LDAP path of where you want user lookups to be performed later by your VMware vCenter Server (or VCSA).
Or in other words, you can limit the search for AD users from vCenter Server to a particular container (CN) or organizational unit (OU) or not.
In our case, we will authorize vCenter Server to search for users in the "Users" folder present by default on your Active Directory infrastructure.
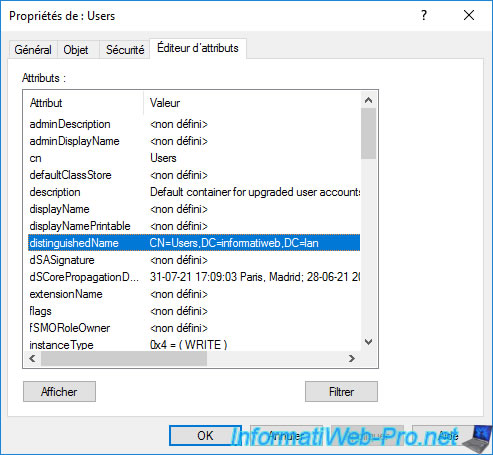
If you want to know the LDAP path of a particular AD object, use the "Active Directory Users and Computers" console and enable advanced features.
Then, in the "Attribute Editor" tab of the desired container (CN) or organizational unit (OU), you will be able to find the distinguishedName (which corresponds to the LDAP path of this Active Directory object).
In our case, this LDAP path is therefore: CN=Users,DC=informatiweb,DC=lan.
For the example, we created an organizational unit "Groups" at the root of our Active Directory domain.
In our case, its LDAP path is: OU=Groups,DC=informatiweb,DC=lan.
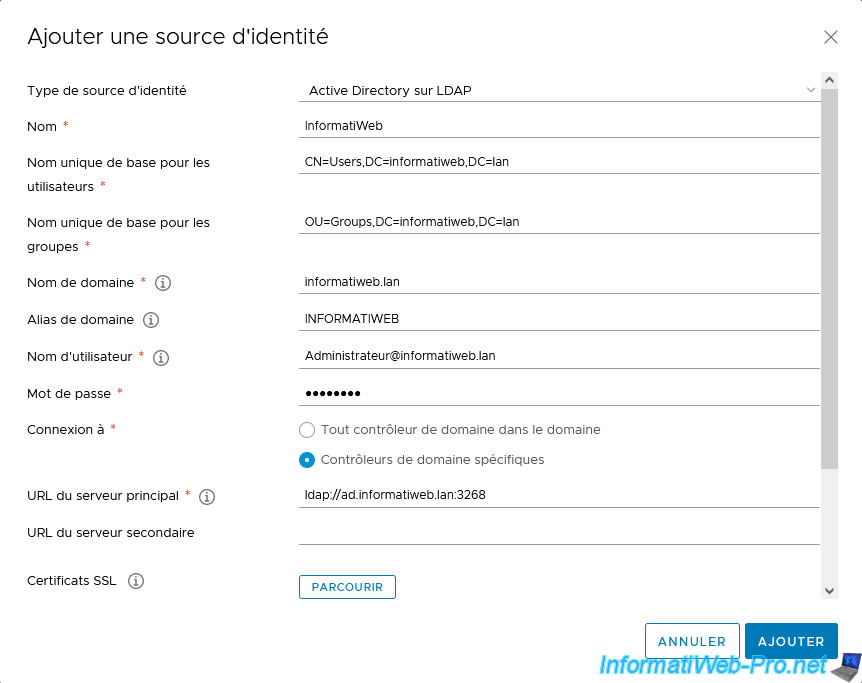
In the large form that appeared by selecting "Identity source type: Active Directory over LDAP", specify this:
- Name: the name under which this identity source will appear in vCenter Server.
In other words, you can indicate whatever you want. - Base distinguished name for users: LDAP path to tell vCenter Server where it should perform user searches.
In our case, we indicated the LDAP path of the "Users" folder present by default in Active Directory infrastructures.
Namely: CN=Users,DC=informatiweb,DC=lan.
vCenter Server will therefore be able to search this "Users" folder and its subfolders (if applicable).
If you want to allow vCenter Server to search for users in your entire Active Directory domain, specify the root of your domain (e.g. domain.lan): DC=domain,DC=lan. - Base distinguished name for groups: same as the previous line, but for searching for groups.
In our case, the organizational unit (or "folder") "Groups" that we created at the root of our domain "informatiweb.lan".
Namely: OU=Groups,DC=informatiweb,DC=lan. - Domain name: name of your Active Directory domain.
In our case: informatiweb.lan. - Domain alias: as indicated by the small "i" next to this option, for Active Directory, you must provide the NETBIOS name associated with this Active Directory domain name.
By default, this is the 1st part of the Active Directory domain name. But this could have been modified during the creation of the Active Directory domain.
In our case, the NETBIOS domain name is: INFORMATIWEB. - Username: the name of a user in the format [user name]@[name of the AD domain where it is located] who has the necessary permissions for vCenter Server to join your Active Directory domain.
In our case, we will use the "Administrator" account of our Active Directory domain "informatiweb.lan".
Namely: Administrator@informatiweb.lan. - Password: his password
- Connect To: if you only have one Active Directory domain controller (which is not recommended by default), you can select "Any domain controller in domain".
Otherwise, select "Specific Domain Controllers" and provide the address of the domain controller(s) to use in the "Primary Server URL" and "Secondary Server URL" boxes.
Note that in production, it is recommended to have at least 2 domain controllers per Active Directory domain, so that the second domain controller can take over in case one of them fails. - SSL Certificates: allows you to specify a certificate for connecting to your domain controller if it is configured to be used securely via LDAPS.
For more information on configuring these settings, refer to the "Active Directory LDAP Server and OpenLDAP Server Identity Source Settings" page of the official VMware documentation.
To learn more about the ports used by Active Directory, refer to the "How to configure a firewall for Active Directory domains and trusts" page of the official Microsoft documentation.
The new "Active Directory" identity source appears.
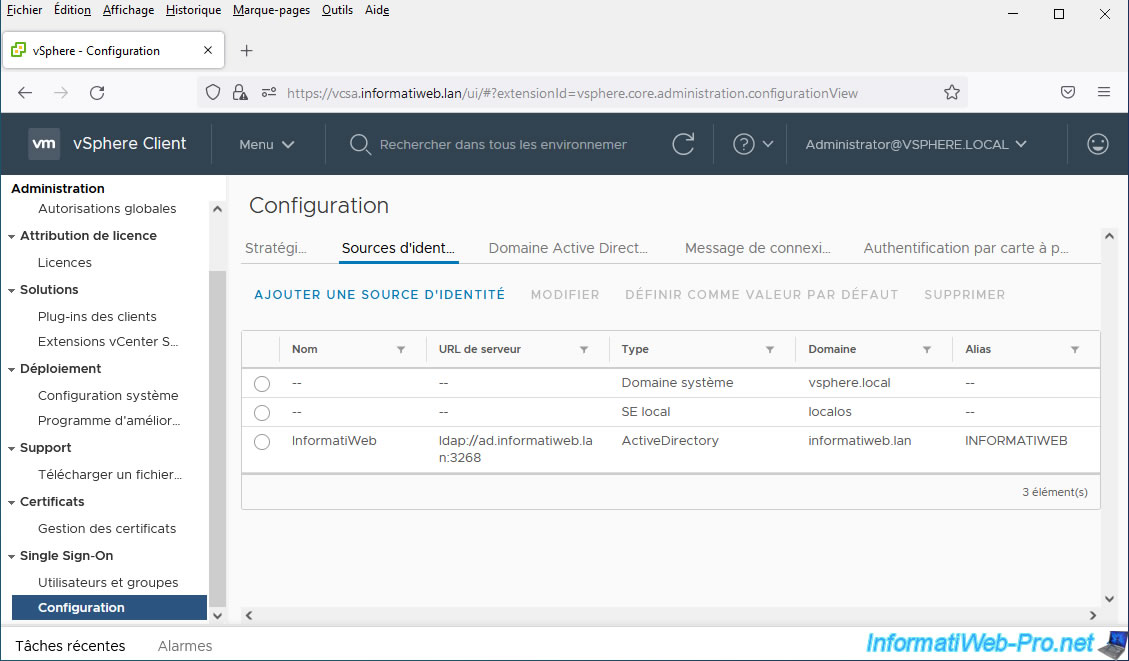
2. Set a default identity source
Currently, users in your Active Directory domain must specify their username, as well as the domain name they are a part of.
In our case, to connect with the Administrator account of our Active Directory domain, we should therefore also specify our Active Directory domain name "informatiweb.lan" when connecting to this vSphere Client.
To make this optional, simply set your Active Directory identity source as the default.
So, when a user tries to connect without specifying a domain name, vCenter Server will attempt to authenticate them using the Active Directory domain name defined here by default.
In short, select your data source "Active Directory" and click "Set as default".
Source : Set the Default Domain for vCenter Single Sign-On.
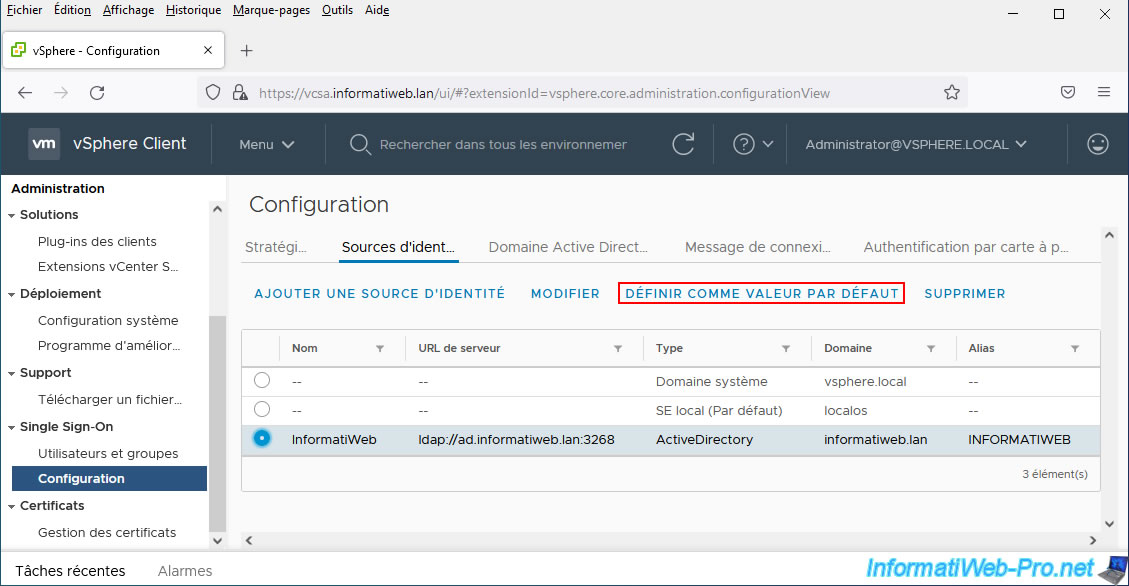
Confirm by clicking OK.
Your Active Directory identity source has been set as "default".
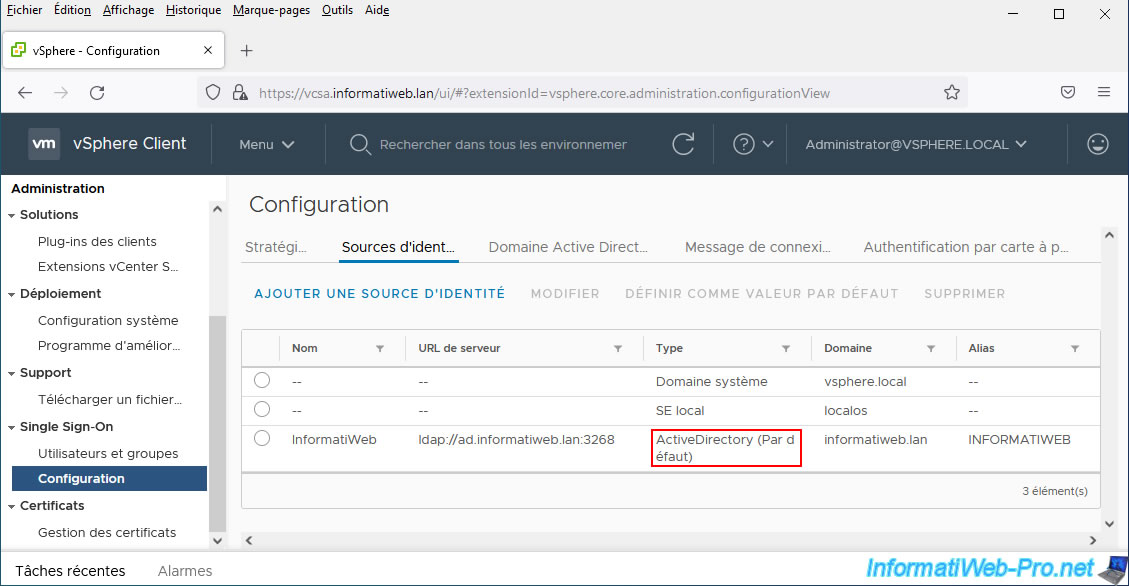
3. View Active Directory users from vCenter Server
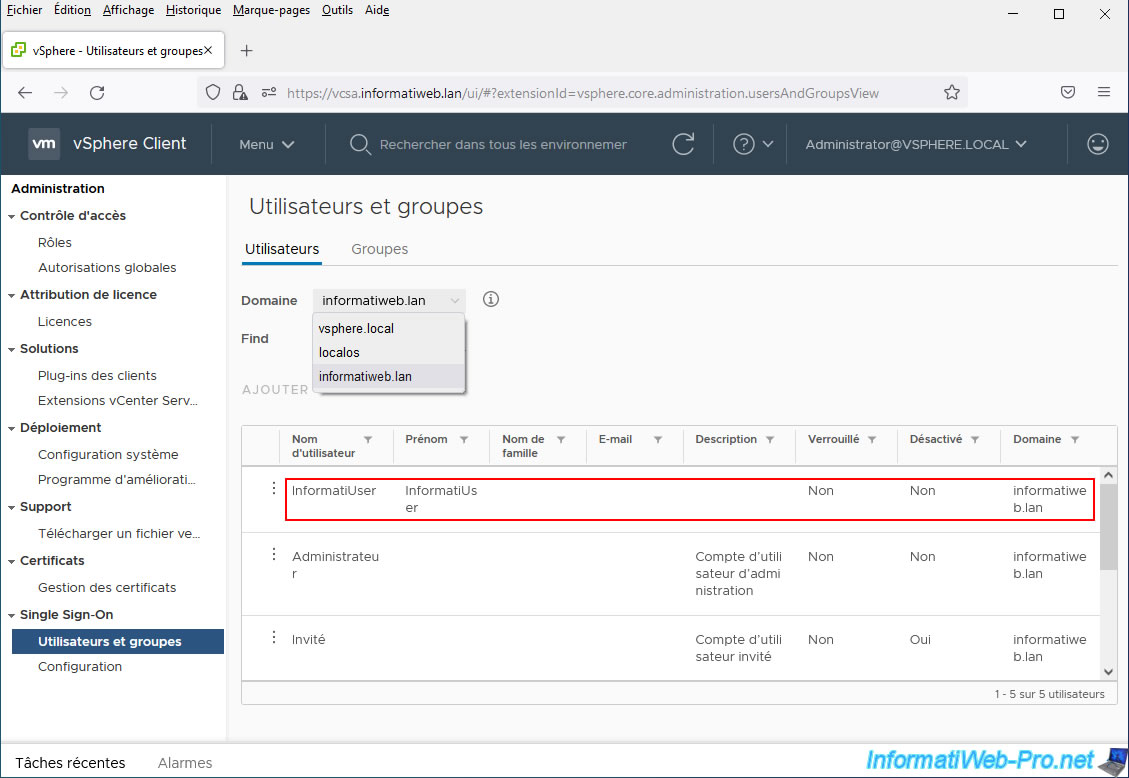
For the example, we have created a new user "InformatiUser" in the "Users" folder of our Active Directory domain "informatiweb.lan".
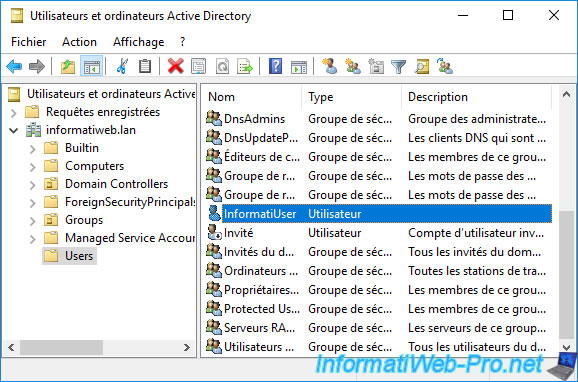
Go to: Single Sign On -> Users and Groups.
By default, the list of local vCenter Server users appears.
As you can see, these are part of the "localos" domain.
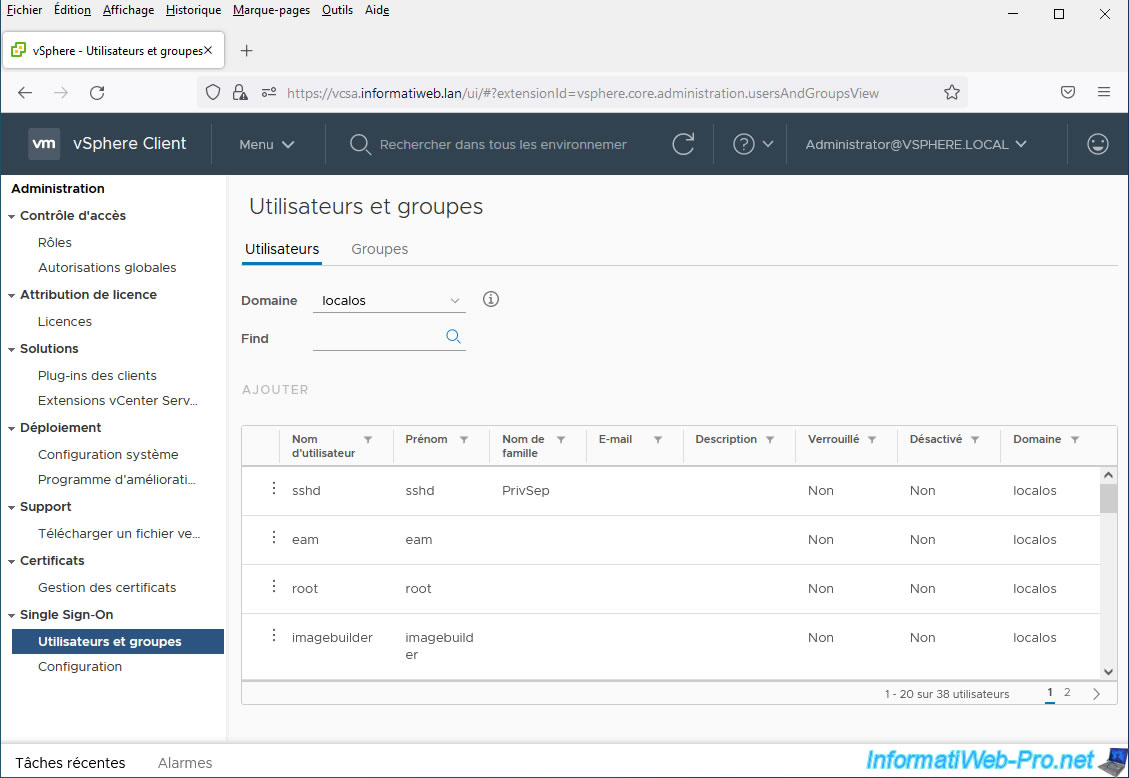
On the other hand, if you select your Active Directory domain in this "Domain" list, you will see your Active Directory users appear.
In our case, we see in particular our new Active Directory user "InformatiUser".
4. Add an Active Directory user to a vCenter group
By default, vCenter Server offers several groups.
To see the list of these groups, go to "Single Sign On -> Users and Groups -> Groups".
In this list, you will find in particular the "Administrators" group to which all rights are granted.
This group contains the "administrator@vsphere.local" account that you are probably logged in with at the moment.
Click on the name of this group "Administrators".
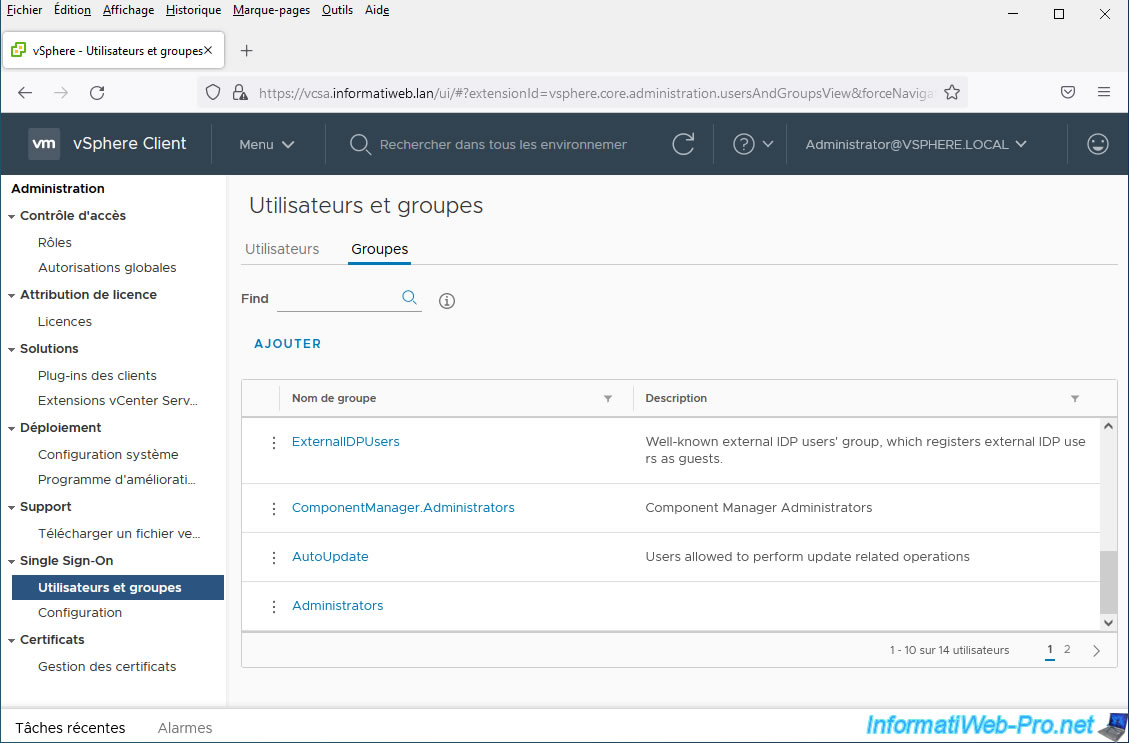
Then, click: Add members.
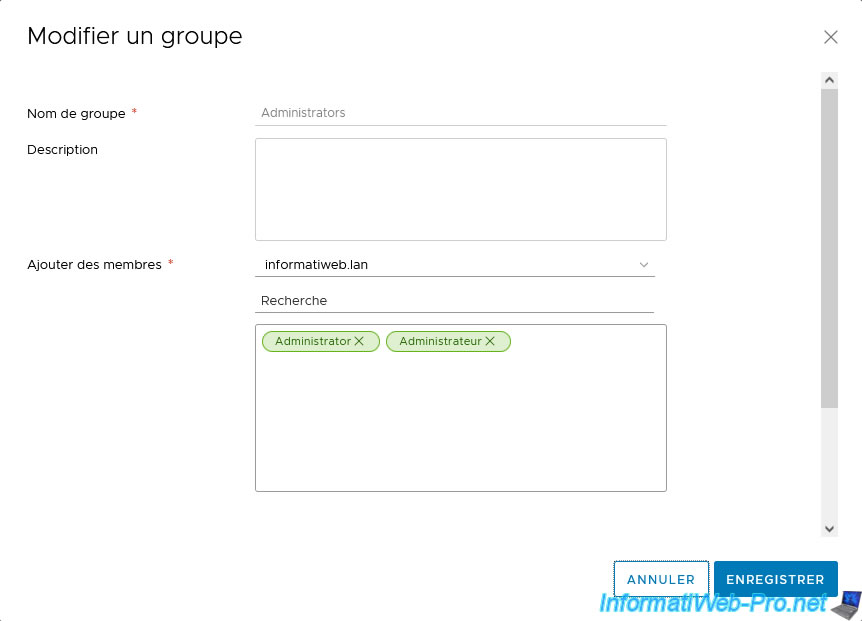
In the "Edit Group" box that appears, select your Active Directory domain in the "Add Members" line and type the name of a user you want to add there.
In our case, the "Administrator" user account of our domain.
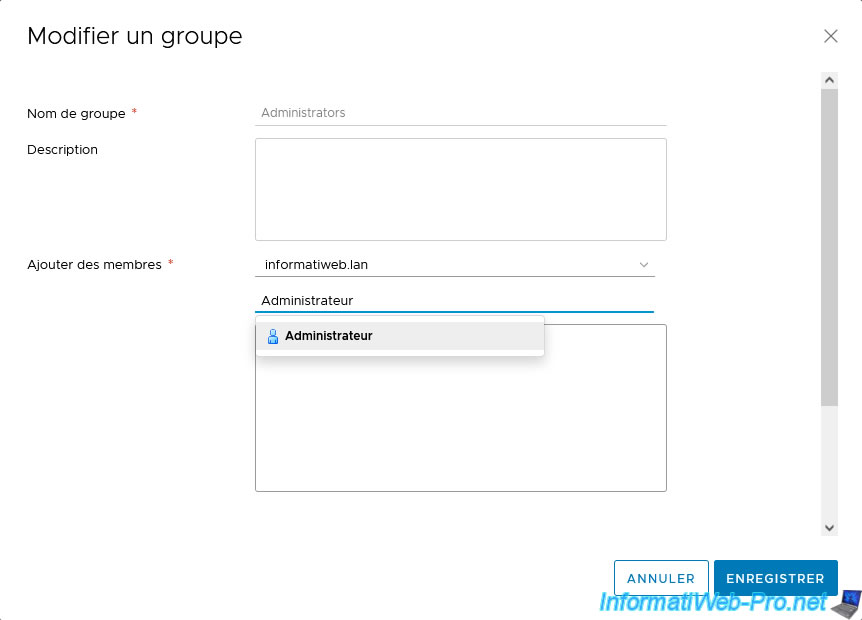
The desired user appears in green.
Click Save.
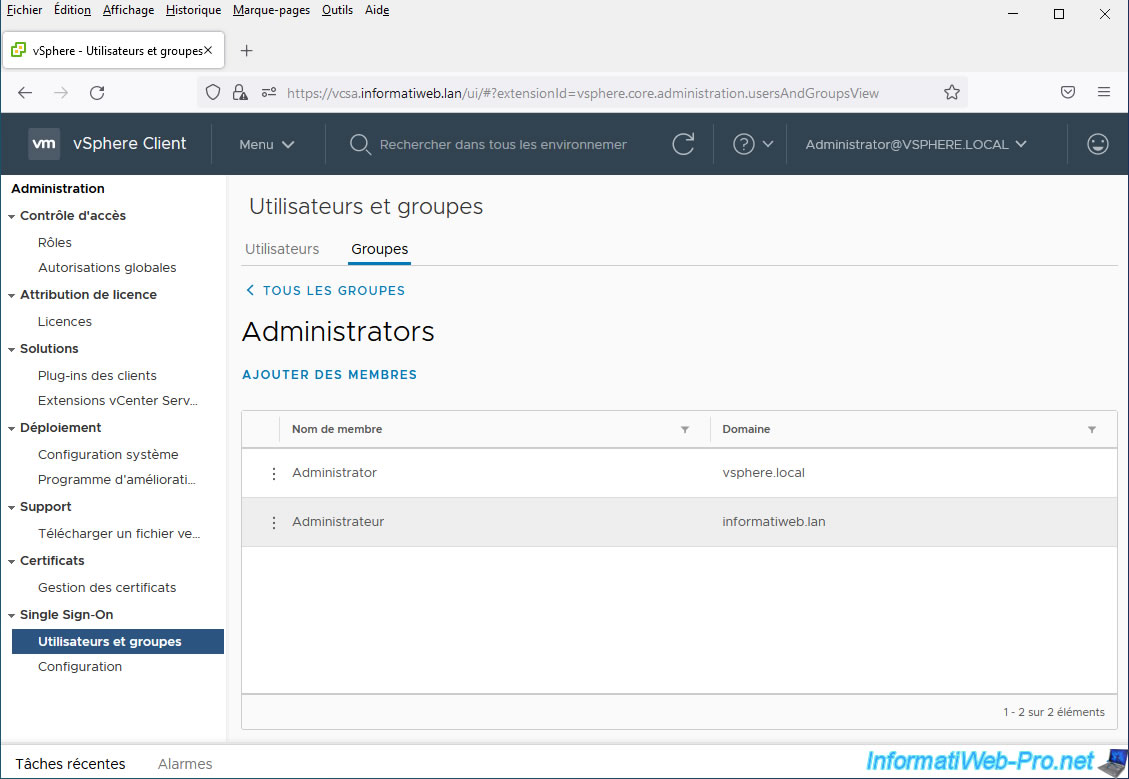
The desired user appears in the list of members of this "Administrators" group.
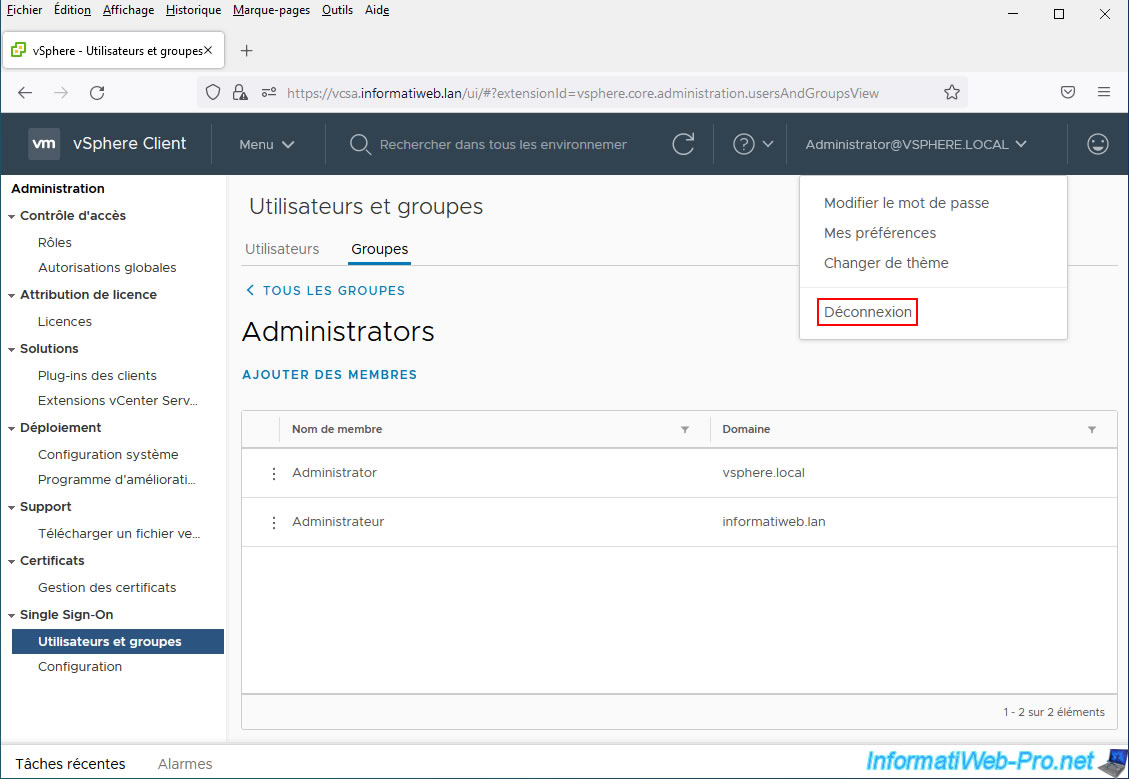
Log out of the vSphere Client to test the connection with an account in your Active Directory domain.
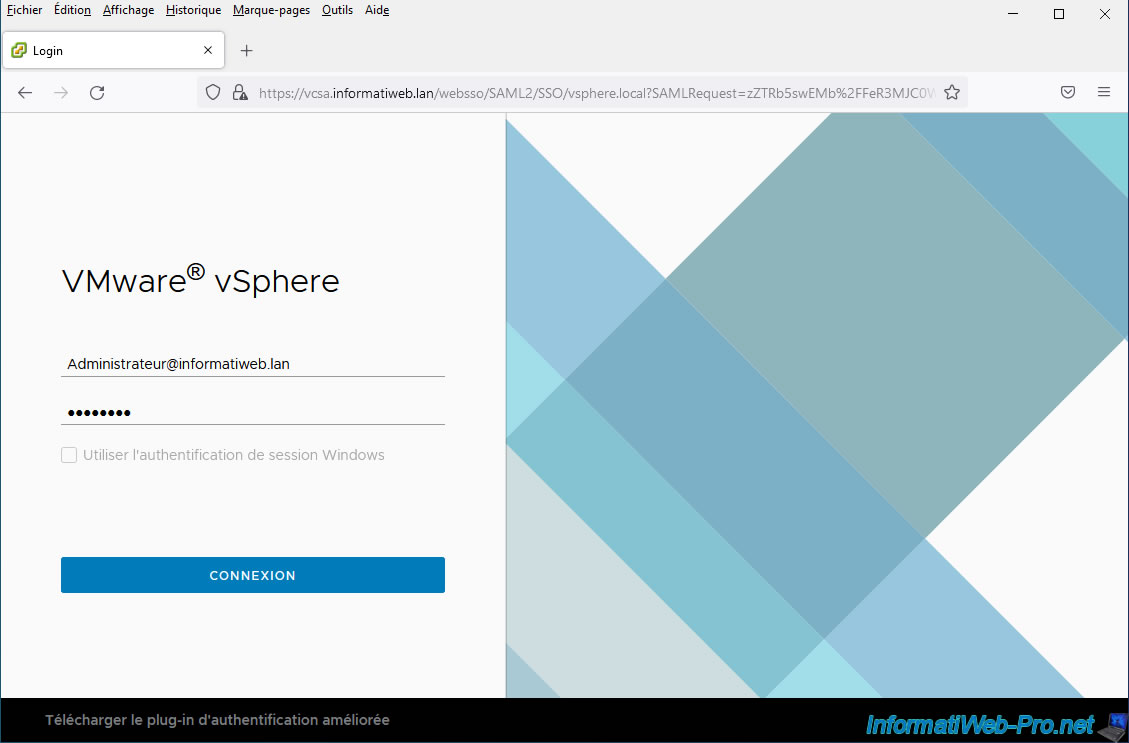
5. Log in to vCenter Server with a user from your Active Directory domain
On the "VMware vSphere" login page that appears, log in with the Active Directory user account you just added in the "Administrators" group.
In our case, the user "Administrateur@informatiweb.lan".
Note that since we had set our "informatiweb.lan" identity source as default, we could also simply specify "Administrator" to log in with the same Active Directory account.
As expected, we are well connected to the vSphere Client with our "Administrator" user account from our "informatiweb.lan" domain.
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console
-

VMware 7/19/2024
VMware vSphere 6.7 - Configure your virtual machines settings

You must be logged in to post a comment