- Windows Server
- 20 August 2021 at 13:46 UTC
-

- 1/3
If you've ever managed an Active Directory domain controller, you're probably familiar with this long-standing, easy-to-use "Active Directory Users and Computers" console.
Here is a full presentation of it.
- Available folders
- Create new objects in your Active Directory domain
- Advanced features
- Filter options
- Actions
1. Available folders
By default, only the main folders are displayed :
- Builtin
- Computers
- Domain Controllers
- ForeignSecurityPrincipals
- Managed Service Accounts
- Users
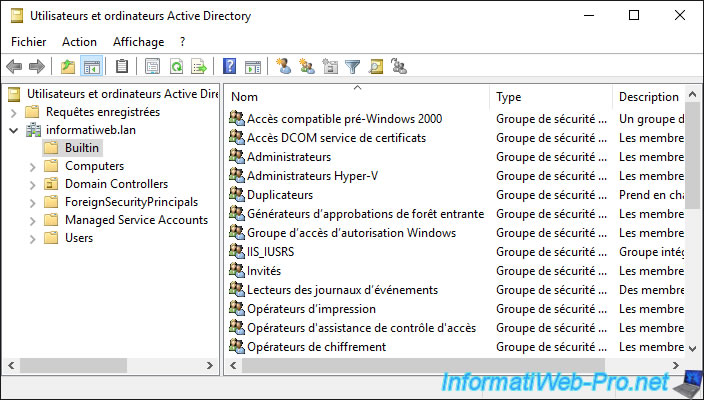
1.1. Builtin folder
In the "Builtin" folder, you will find the groups created by default by Windows Server and Active Directory.
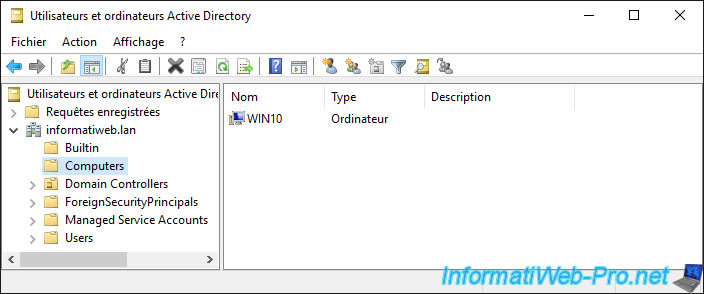
1.2. Computers folder
In the "Computers" folder, you will find the "computer" type objects corresponding to the client computers that you have joined to your Active Directory domain.
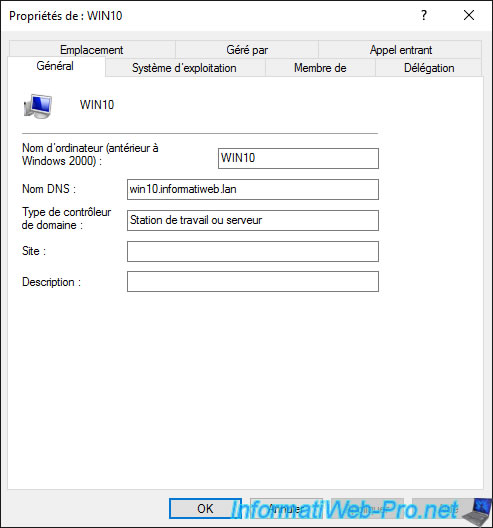
If you display the properties of a computer type object, you will find, for example :
- the NETBIOS name of the affected computer
- its full DNS name
- the type of computer or domain controller. In this case, it indicates that it's a workstation. In other words, a client computer with a client version of Windows (ex : Win 10).
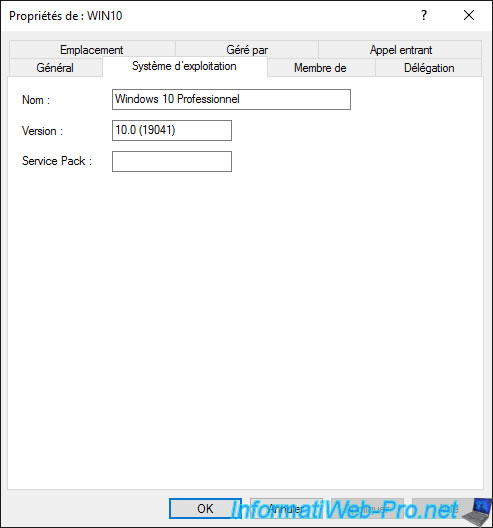
In the "Operating System" tab, you will find information about the operating system installed on it :
- the name of the operating system : in our case, Windows 10 Professional
- its version : 10.0 (19041)
- the service pack installed (if applicable)
In the "Member of" tab, you can choose in which group you want to add this computer.
By default, computer objects are members of the "Domain Computers" group.
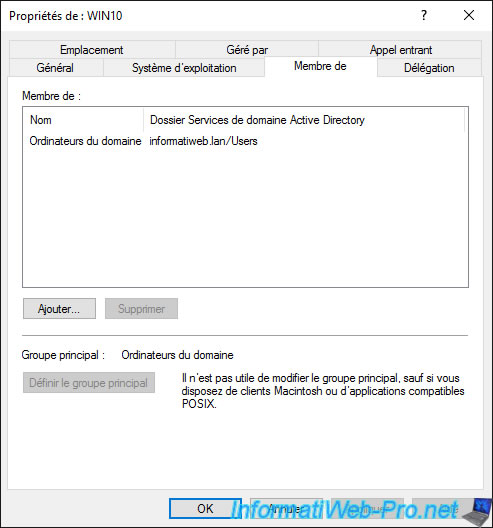
In the "Delegation" tab, you can approve or not this computer for Kerberos or for specific services.
This tab is particularly useful when you implement dynamic migration with several Hyper-V servers.
In the "Location" tab, you can choose its location.
You can delegate management of a computer to a user in your Active Directory domain.
Although this "Managed By" tab is mostly useful for domain controllers.
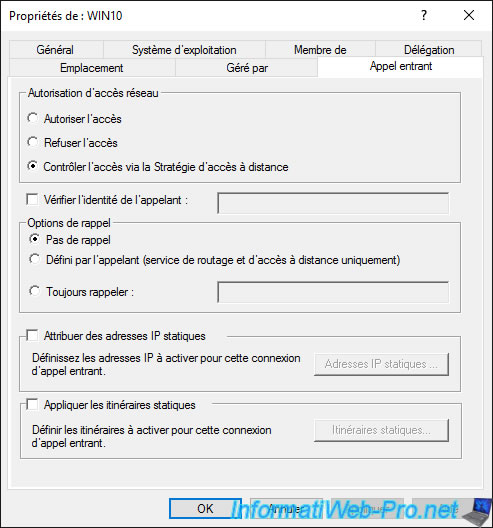
Finally, in the "Dial-In" tab, you can :
- choose whether this computer can access the network or not, or if this setting is managed by the "NPS Network policy"
- assign static IP addresses to this computer
- apply static routes if necessary
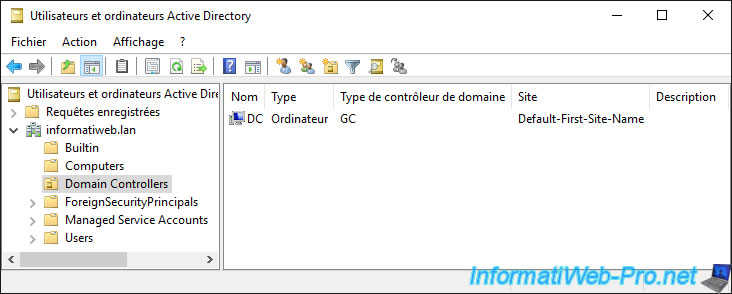
1.3. Domain Controllers folder
In the "Domain Controllers" folder, you will find the list of domain controllers joined to this Active Directory domain.
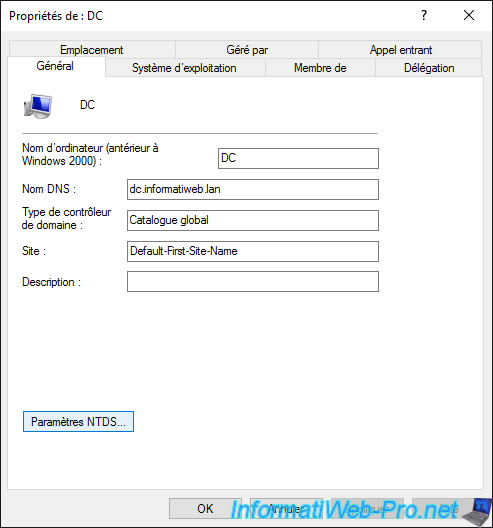
If you display the properties of the computer object of a domain controller, you may find out :
- his NETBIOS name
- his DNS name
- what type is this domain controller : global catalog, ...
- in which Active Directory site it's located
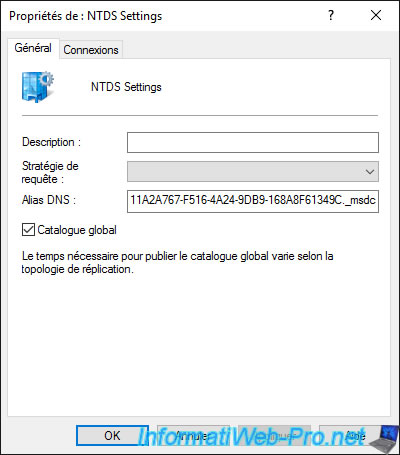
In the case of a domain controller, a "NTDS Settings" button is present in the properties of the computer object.
In these NTDS Settings, you can choose whether or not this domain controller should act as a "Global Catalog".
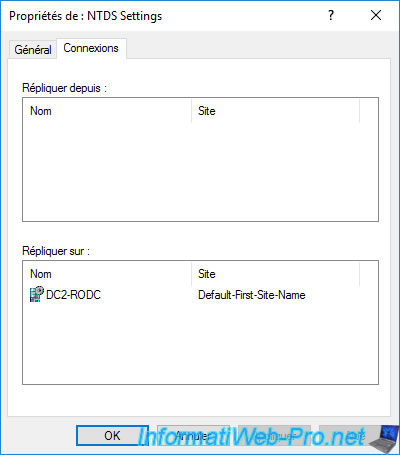
In the "Connections" tab, you will find the list of domain controllers from or to which the data of your Active Directory domain are replicated.
For example, assuming that we add a new domain controller to our Active Directory domain, and that we choose our domain controller "DC" as the source, we would see a "DC2-RODC - Default-First-Site-Name" appear in the "Replicate To" list.
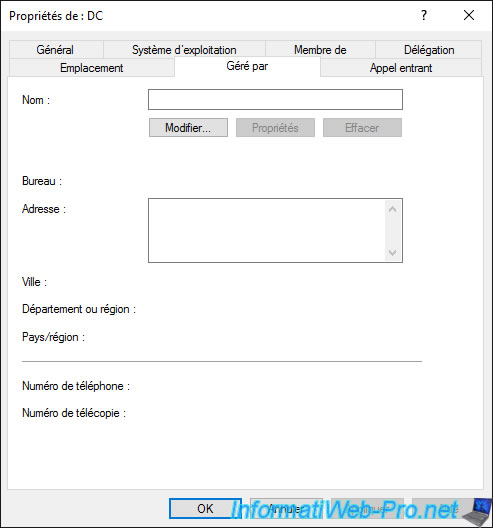
The "Managed By" tab is blank by default for writable domain controllers.
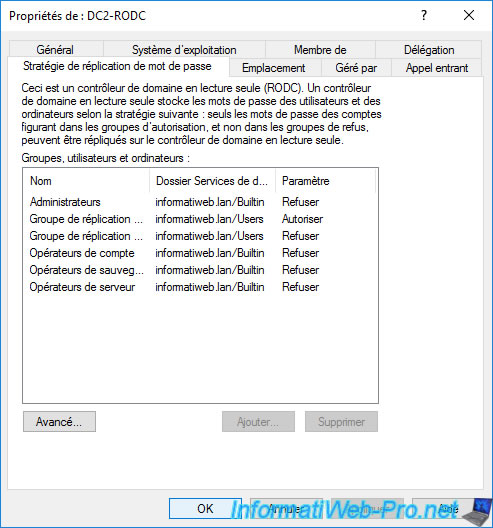
In the case of read-only domain controllers (RODCs), an additional "Password Replication Policy" tab will be displayed.
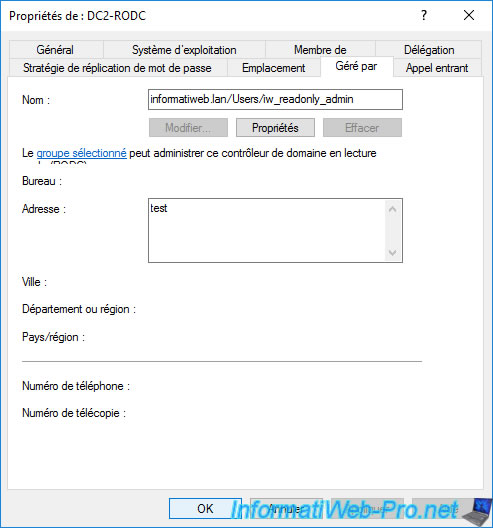
Still in the case of a read-only domain controller (RODC), you will be able to find the name of its delegated administrator if you defined one when you deployed this read-only domain controller (RODC).
1.4. ForeignSecurityPrincipals folder
This "ForeignSecurityPrincipals" folder looks empty by default, but actually contains several special security-related identities.
To learn all about this somewhat special folder, refer to the Microsoft site : Active Directory: Foreign Security Principals and Special Identities
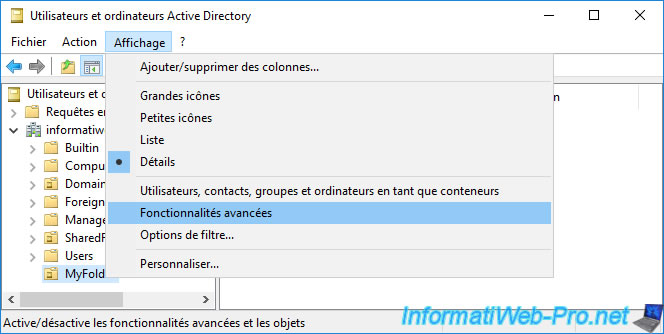
To display the contents of this "ForeignSecurityPrincipals" folder, you must go to the "View" menu and click "Advanced Features".
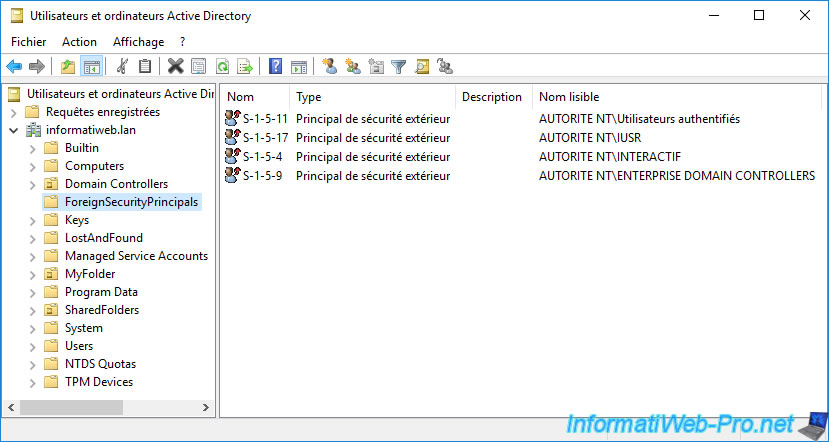
Now, as you can see, several security identities appear, include one which is for example linked to the "NT AUTHORITY\Authenticated Users" group.
1.5. Managed Service Accounts folder
Managed Service Accounts are domain accounts whose password is automatically managed by the domain controller.
These managed service accounts are used to run specific services (the services that you find on Windows), scheduled tasks or for application pools on Microsoft IIS web servers.
Sources : Running Assessments with Managed Service Accounts
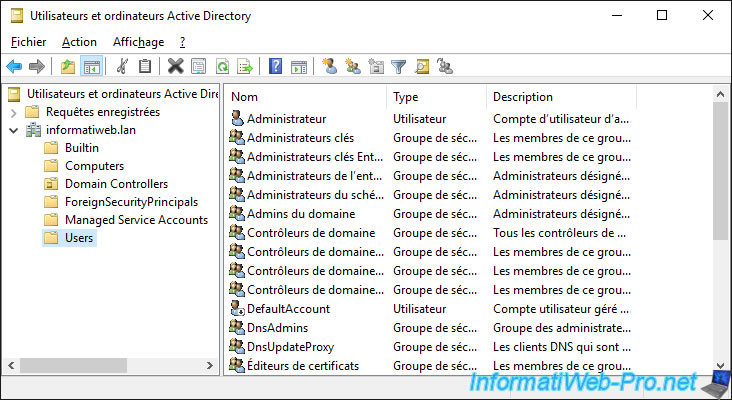
1.6. Users folder
In the "Users" folder, you will find by default, a list of users and groups created during the installation of Windows Server or created later during the installation of specific roles (including AD DS).
Among these users and groups, you will obviously find :
- the "Administrator" account of the server which also becomes the administrator of the domain when you promote your server as a domain controller
- the "Domain Admins" group
- and more
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment