- VMware
- VMware ESXi, VMware vSphere
- 22 June 2022 at 14:53 UTC
-

When you install the VMware ESXi 6.7 hypervisor, by default, an SSL certificate is used to secure the connection between your computer and this server via the HTTPS protocol.
However, by default, VMware ESXi uses a self-signed certificate. This will cause a security warning to appear when you try to access its web interface.
Warning : this only concerns VMware ESXi hypervisors that are not linked to a VMware vCenter Server (VCSA) server.
Indeed, if it's linked to a VMware vCenter Server (VCSA), its certificate is no longer a self-signed certificate, but a certificate signed by the internal certification authority "VMCA" present on the VMware Server (VCSA) server concerned.
- Prerequisites
- Security warning displayed by default
- Define a domain name for your VMware ESXi hypervisor
- Create a DNS record for your VMware ESXi hypervisor
- Replace VMware ESXi certificate with a valid SSL certificate
1. Prerequisites
To secure your VMware ESXi hypervisor with a valid certificate, you will need :
- an internal DNS server or an Active Directory domain controller (on which a DNS server will be automatically installed)
- a certification authority on Windows Server (in our case) or on Linux
In our case, we will use a server on Windows Server 2016 which will act as an Active Directory domain controller and as a certification authority.
2. Security warning displayed by default
As you can see, by default, when you access the web interface of your VMware ESXi hypervisor, a warning is displayed.
With Mozilla Firefox, you will see the warning "Warning: Potential Security Risk Ahead" appear.
Click on : Advanced.
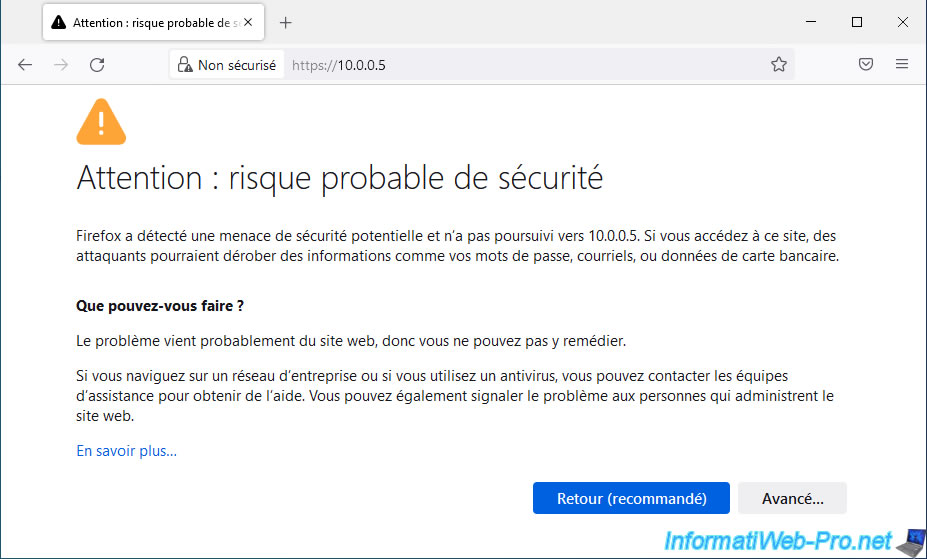
As you can see, Firefox doesn't trust your VMware ESXi server, because its certificate issuer is unknown.
In other words, the SSL certificate used by default has not been signed by a certification authority recognized by default by Firefox (or by your computer for other web browsers).
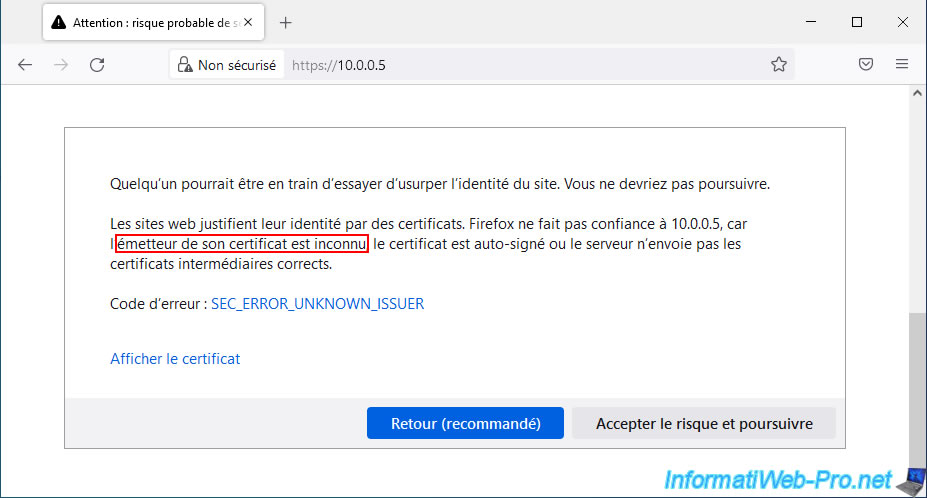
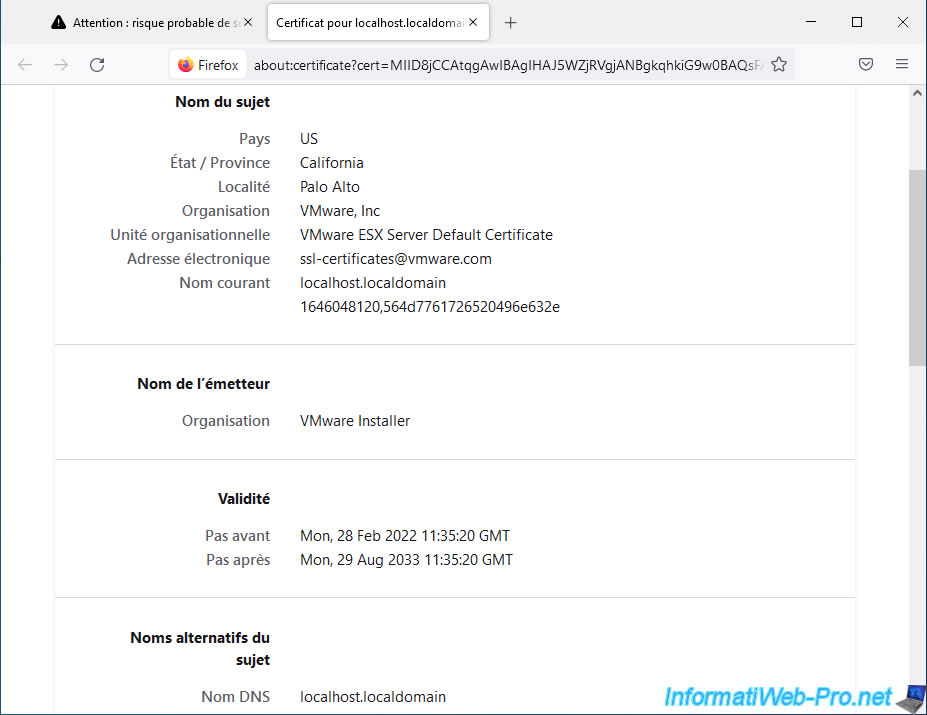
If you click on the "View Certificate" link, you will see that the issuer is "VMware Installer" (which is a fictitious name).
3. Define a domain name for your VMware ESXi hypervisor
To generate a valid SSL certificate for your hypervisor, you will need to define a domain name for it.
Then, this domain name must be indicated as a common name (CN) in the SSL certificate issued.
To begin, log in as "root" on your VMware ESXi hypervisor.
Information about your VMware ESXi hypervisor appears.
Go to the "Networking" section, then to the "TCP/IP stacks" tab.
Then, click on the "Default TCP/IP stack" link.
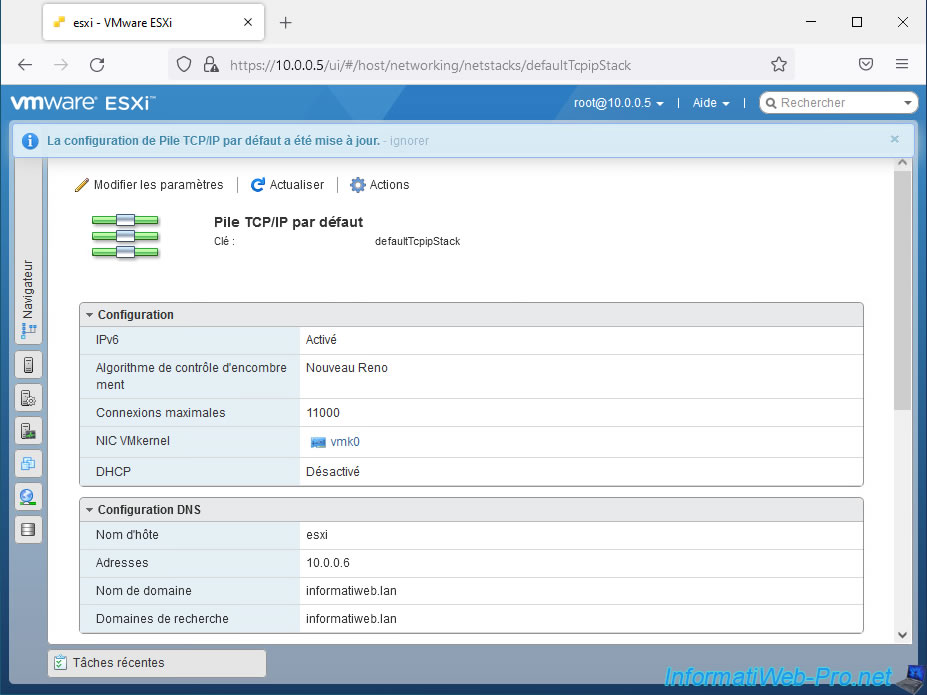
On the "Default TCP/IP stack" page that appears, click on the "Edit settings" link.
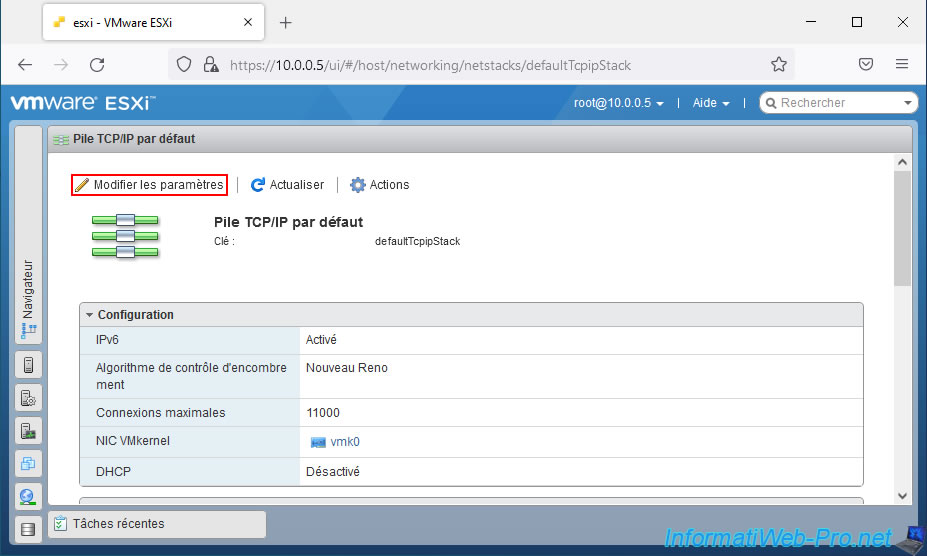
In the "Edit TCP/IP configuration - Default TCP/IP stack" window that appears, select "Manually configure the settings of this TCP/IP stack", then specify :
- Host name : the name that will be used as a subdomain for your VMware ESXi hypervisor.
In our case : esxi. - Domain name : your Active Directory domain name or your root internal domain name.
In our case : informatiweb.lan. - Primary DNS server : the IP address of your internal DNS server.
In an Active Directory infrastructure, you will specify the IP address of a domain controller located on the same network as your VMware ESXi hypervisor.
In our case, the IP address of our Active Directory domain controller is : 10.0.0.6. - Secondary DNS server : the IP address of a secondary internal DNS server (if applicable) allowing the domain name indicated above to be resolved.
- Search domains : same as the domain name. This allows your VMware ESXi hypervisor to resolve short names to IP addresses using your internal DNS server.
In our case : informatiweb.lan.
Example : if your VMware ESXi hypervisor wishes to know the IP address of the "ad" server, it will attempt to obtain the IP address of the "ad.informatiweb.lan" server from one of the DNS servers previously entered.
Once the above informations are filled in, click Save.
The "Successfully updated configuration for Default TCP/IP stack" message appears.
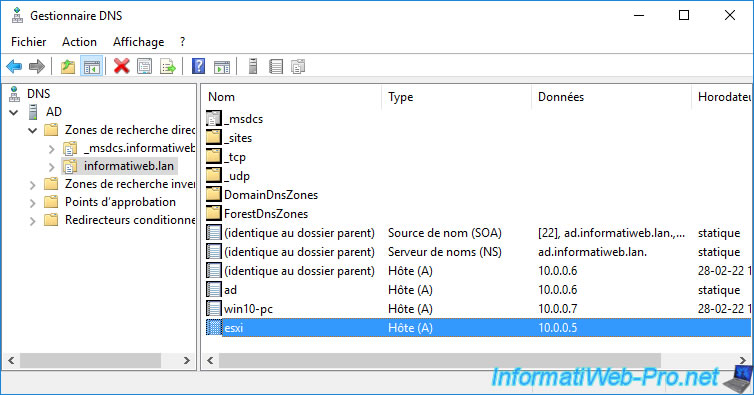
4. Create a DNS record for your VMware ESXi hypervisor
To be able to access your VMware ESXi hypervisor using its domain name (indicated previously), you must create the corresponding DNS record on your internal DNS server.
To do this, open the "DNS Manager" of your internal DNS server.
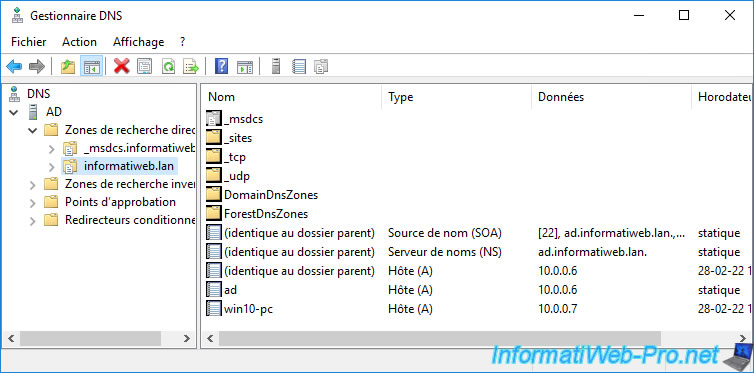
Then, right-click "New Host (A or AAAA)" on your internal domain name in "Forward Lookup Zones".
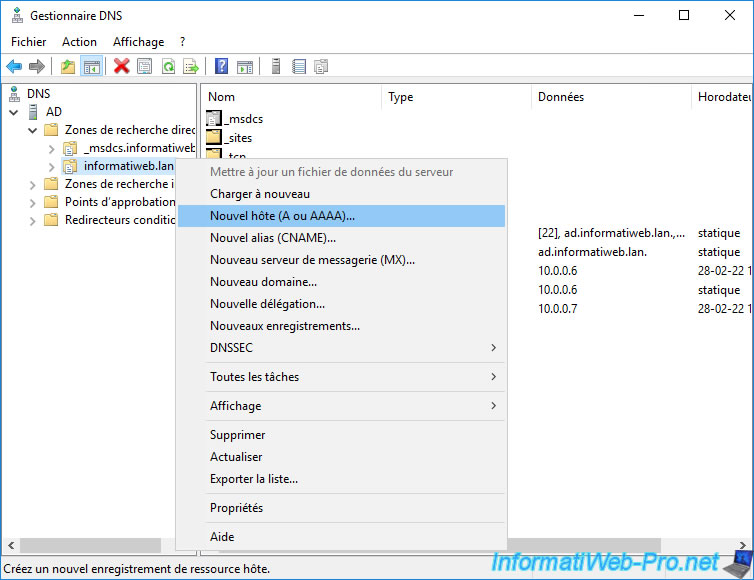
Provide the short name (in our case : esxi) and the IP address of your VMware ESXi hypervisor, then click Add host.
Note that creation of the associated PTR record pointer is only possible if the corresponding reverse lookup zone is created on your internal DNS server.
If you only have one VMware ESXi server, this is not required. However, if you are in a VMware vSphere infrastructure with at least one VMware vCenter server, you will need to create this reverse lookup zone to avoid various problems.
To create a reverse lookup zone on your internal DNS server, refer to step "4. Create a reverse lookup zone (IP address -> domain)" of our tutorial on creating a DNS server.
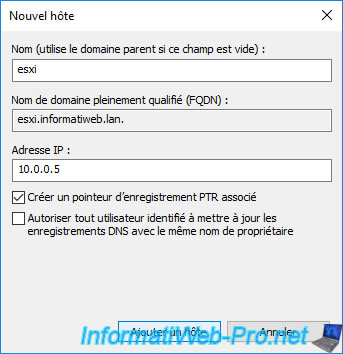
The DNS record for your VMware ESXi hypervisor has been created.
5. Replace VMware ESXi certificate with a valid SSL certificate
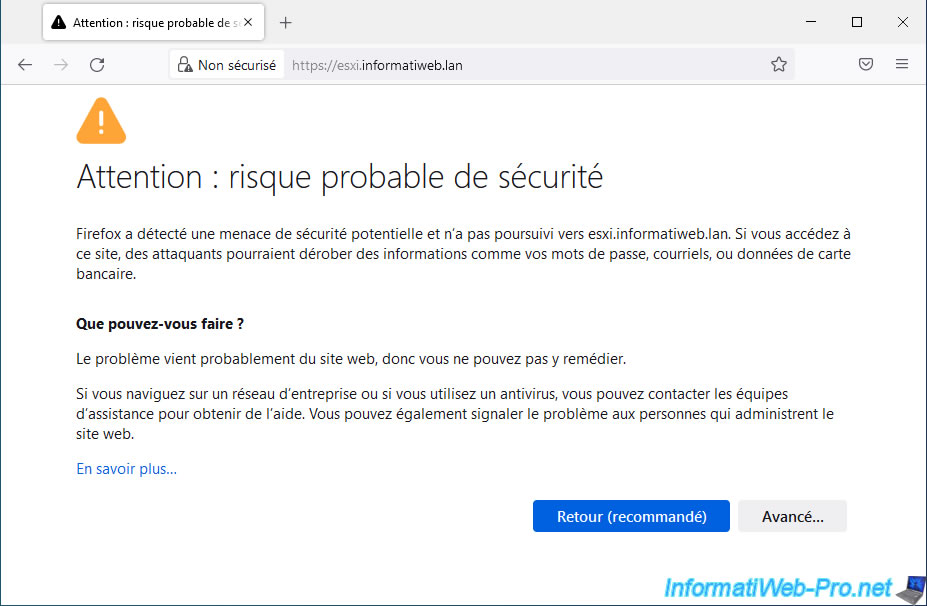
To get started, access your VMware ESXi hypervisor using the domain name created earlier to test your DNS configuration.
If the security warning appears, you are probably connected to your VMware ESXi hypervisor.
Ignore this warning for now.
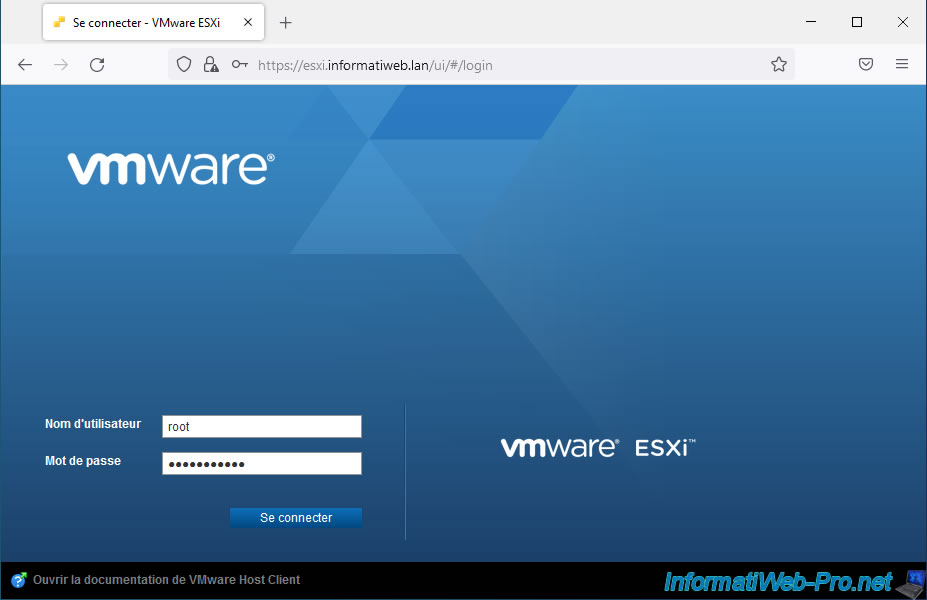
Log in as "root".
As you can see, the name of your VMware ESXi hypervisor has changed.
In our case, we see our domain "esxi.informatiweb.lan" appear in the page, as well as in the name of the tab.
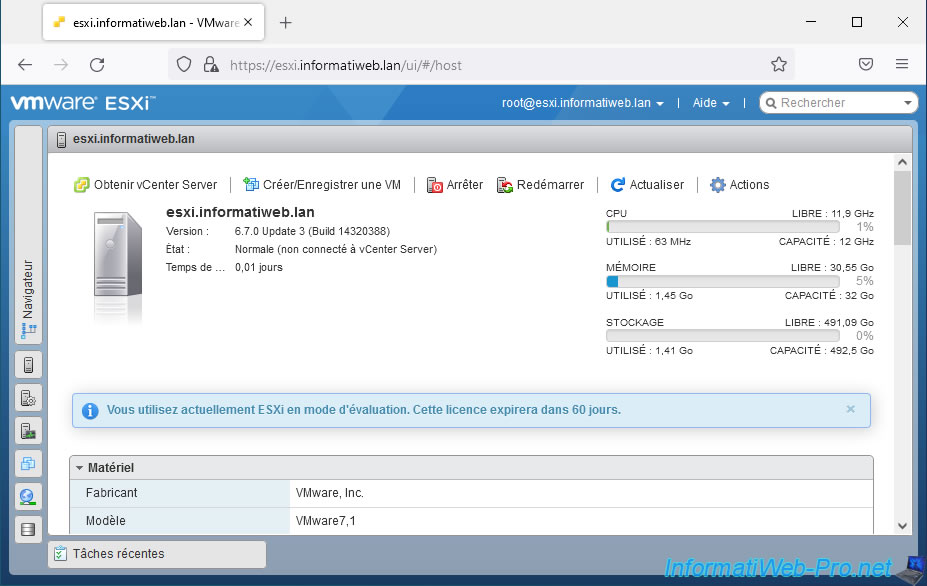
Go to : Host -> Manage -> Security & users -> Certificates.
Note : as you can see, currently the certificate used is the default one issued by "VMware Installer" and valid for the "localhost.localdomain" domain.
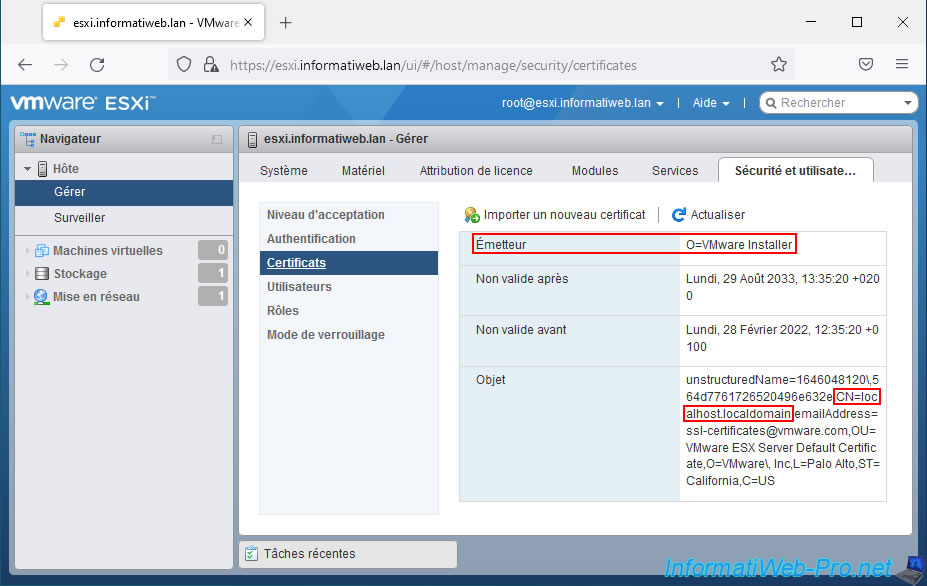
Click on "Generate FQDN signing request" to be able to request a certificate that will be valid for the FQDN (ex : esxi.informatiweb.lan) of your VMware ESXi hypervisor.
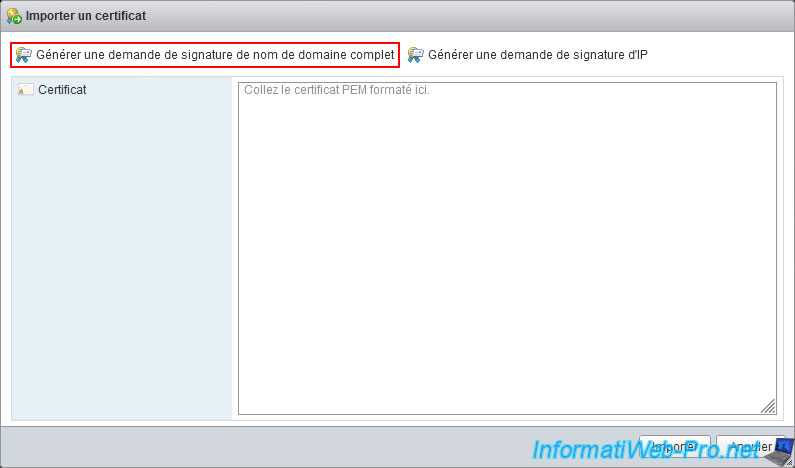
The result of the certificate signing request appears.
Copy the text including the start line (-----BEGIN CERTIFICATE REQUEST-----) and the end line (-----END CERTIFICATE REQUEST-----).
Connect to the web interface of your certification authority on Windows Server by connecting to the "https://ad.informatiweb.lan/CertSrv" address.
If your web browser asks you to identify yourself to your certificate authority (as is the case in the image below), log in as an administrator (or a user authorized to issue certificates based on the "Web Server" certificate template).
On the "Microsoft Active Directory Certificate Services -- [your certification authority name]" page that appears, click the "Request a certificate" link.
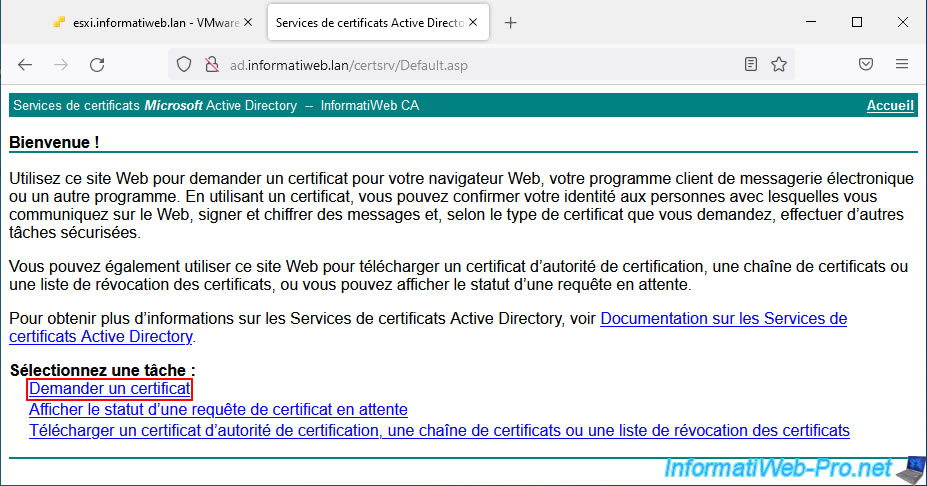
Then, click on the "advanced certificate request" link.
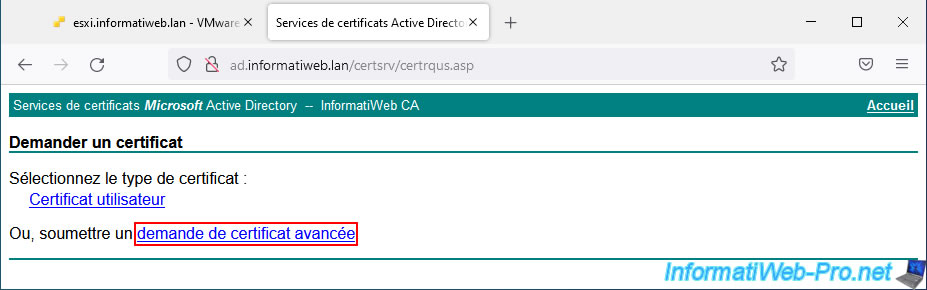
On the "Submit a Certificate Request or Renewal Request" page that appears, paste the previously copied certificate signing request into the "Base-64-encoded certificate request (CMC or PKCS #10 or PKCS #7)" box".
Then, select the "Web Server" certificate template and click "Submit".
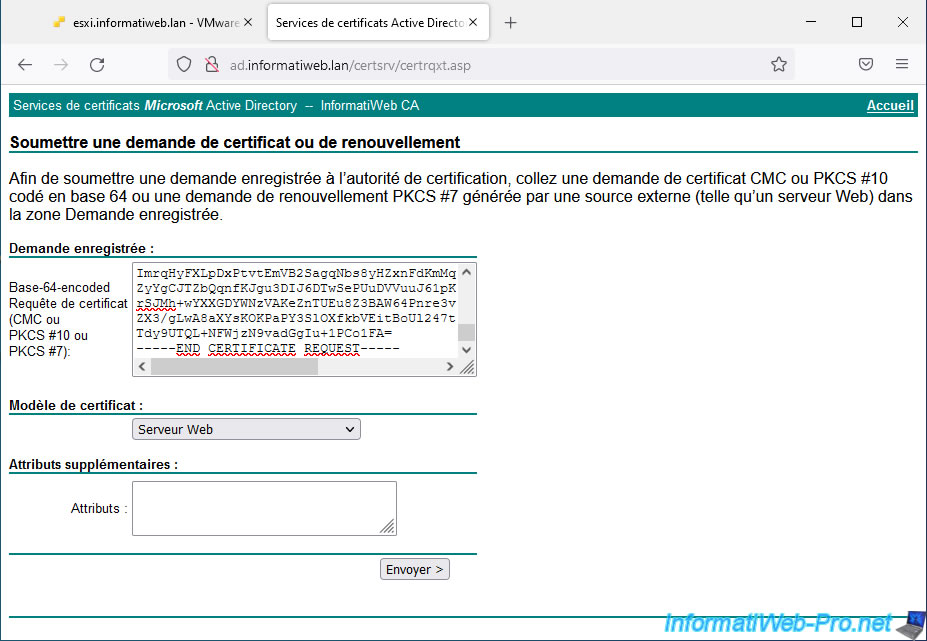
On the "Certificate issued" page that appears, select "Base 64 encoded" to obtain your certificate in PEM format (which is a text format usually used on Linux) and click on : Download certificate.
Your certification authority offers you to download a "certnew.cer" file.
Open this "certnew.cer" file with notepad and you will see that it looks like this :
Plain Text
-----BEGIN CERTIFICATE----- xxxxxxxxxxxxxxxxxxxxxxxxxxxx... -----END CERTIFICATE-----
Note : if this is not the case for you, you forgot to select "Base 64 encoded" before downloading your certificate.
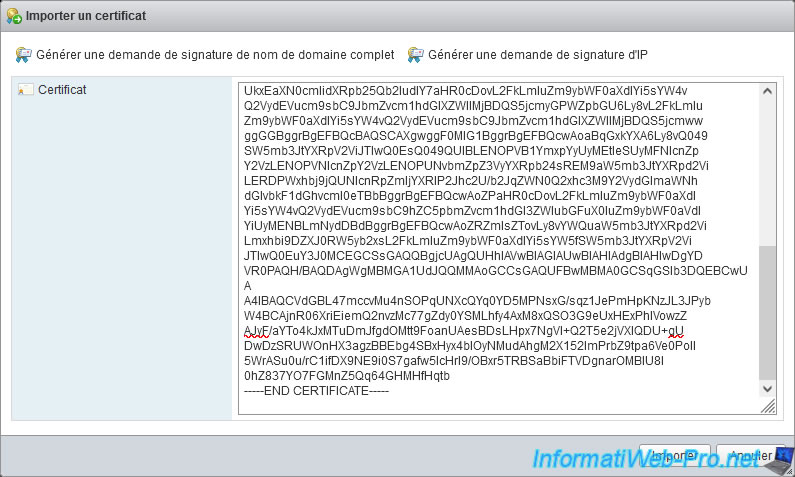
Copy the contents of the previously downloaded "certnew.cer" file into the large "Certificate" box of VMware ESXi.
Then, click Import.
The message "The certificate has been updated. Refresh your browser." appears.
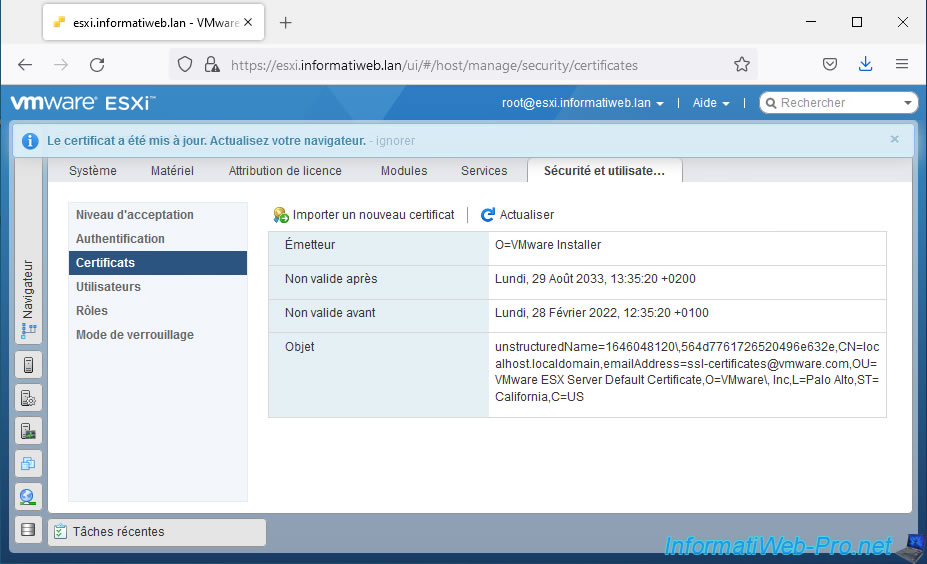
Refresh the page and you will see that the certificate used has been updated.
Indeed, now, the issuer displayed corresponds to the name of your certification authority and this certificate is valid for the domain name of your VMware ESXi hypervisor (CN=esxi.informatiweb.lan).
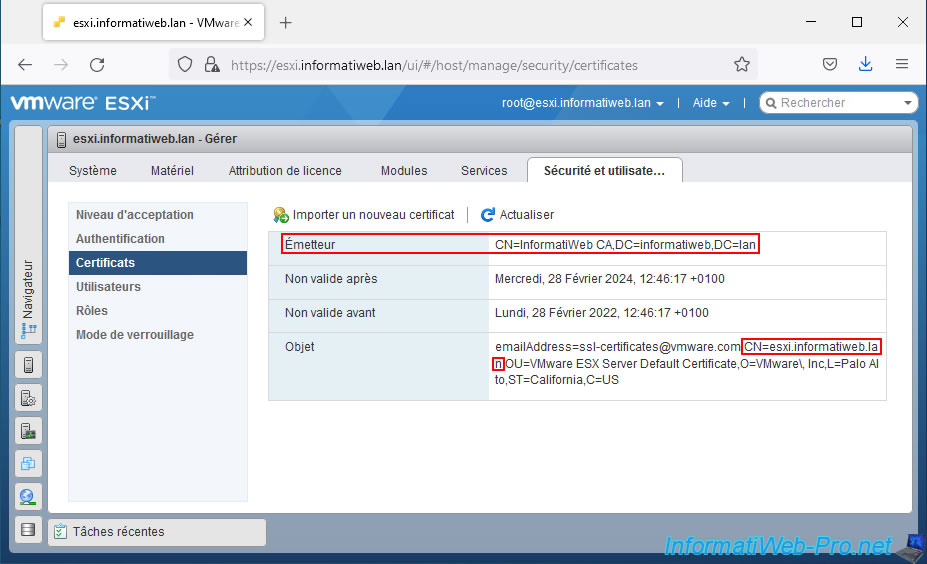
Although your hypervisor's SSL certificate has been updated, you will see that Firefox still considers the connection as insecure.
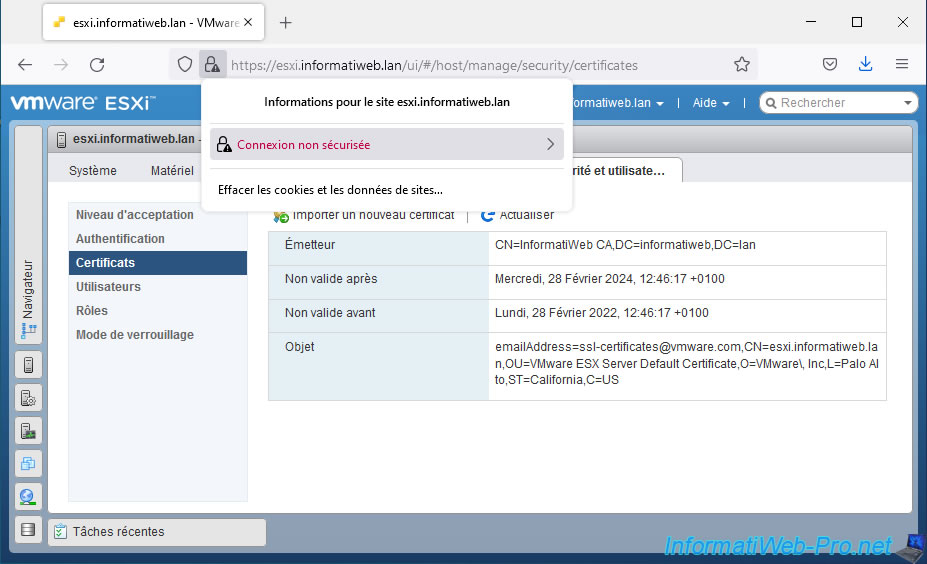
To fix this problem, you just need to remove the exception that was created earlier because of the self-signed SSL certificate.
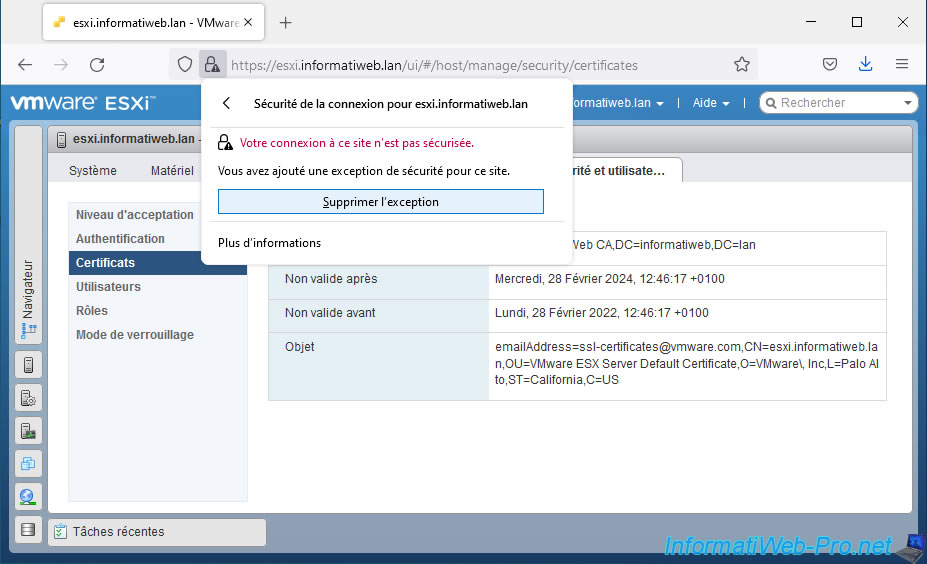
Once this exception has been removed from your web browser, the connection will be considered secure given that the certificate is valid (domain name, validity dates, ...) and that it comes from a certification authority recognized by your computer.
Important : if you are using the "Mozilla Firefox" web browser, you must also ensure that your certificate authority's certificate is in the certificate store of this web browser.
Indeed, unlike other web browsers that use your computer's certificate store on Windows, Mozilla Firefox uses its own certificate store.
To import your CA certificate into Mozilla Firefox's certificate store, go to the "Tools -> Settings" menu, then go to "Privacy & Security" and click the "View Certificates" button at the bottom of the page.
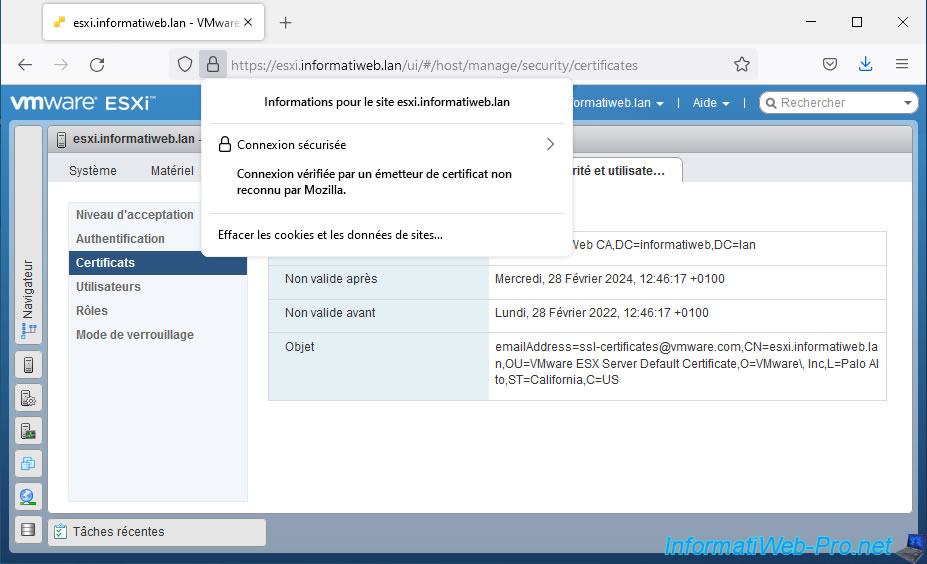
If you click on the "Secure connection" status, you will see that the connection to this site is secure and that the certificate has been verified by your certification authority.
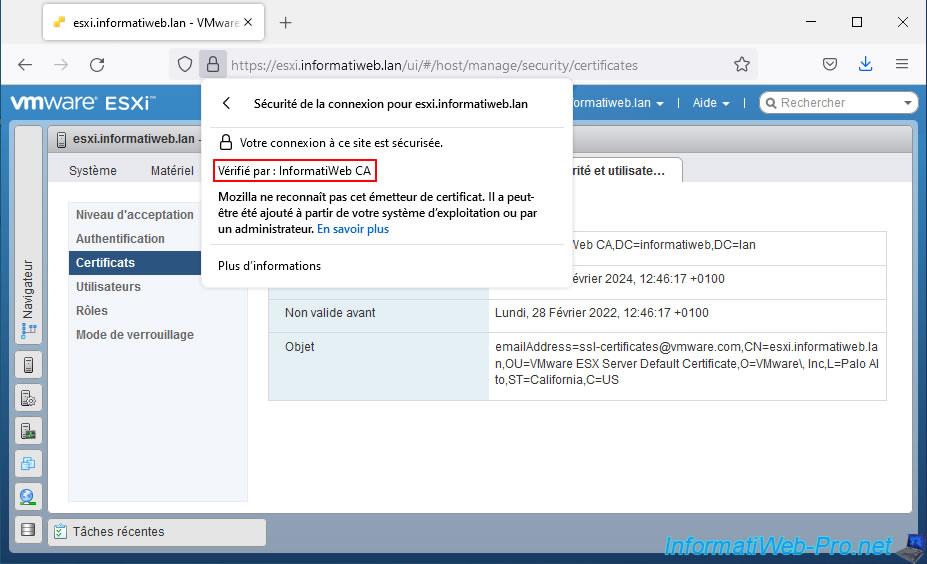
If you click on "More information", you can view information about the SSL certificate used by your VMware ESXi hypervisor by clicking on : View Certificate.
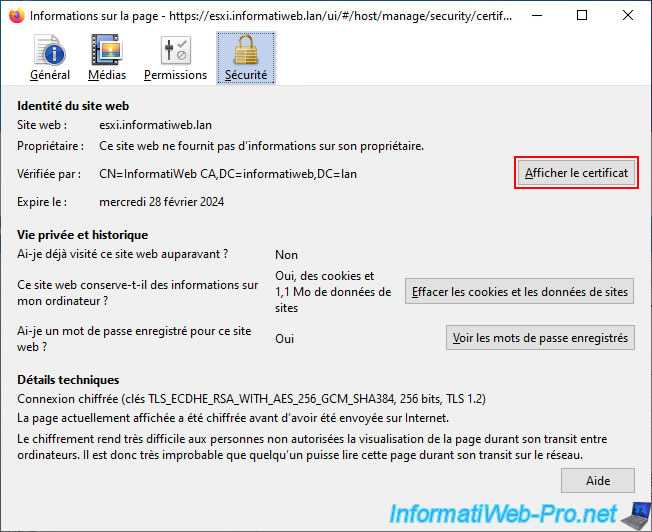
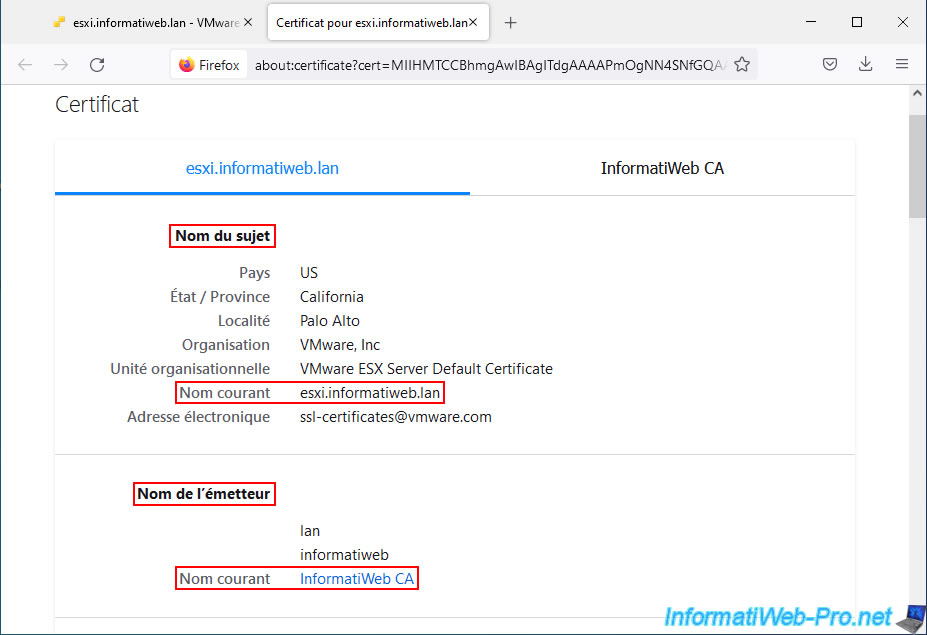
As you can see, the SSL certificate used :
- is valid for the domain name of your VMWare ESXi hypervisor.
In our case : esxi.informatiweb.lan. - comes from your certification authority.
In our case : InformatiWeb CA.
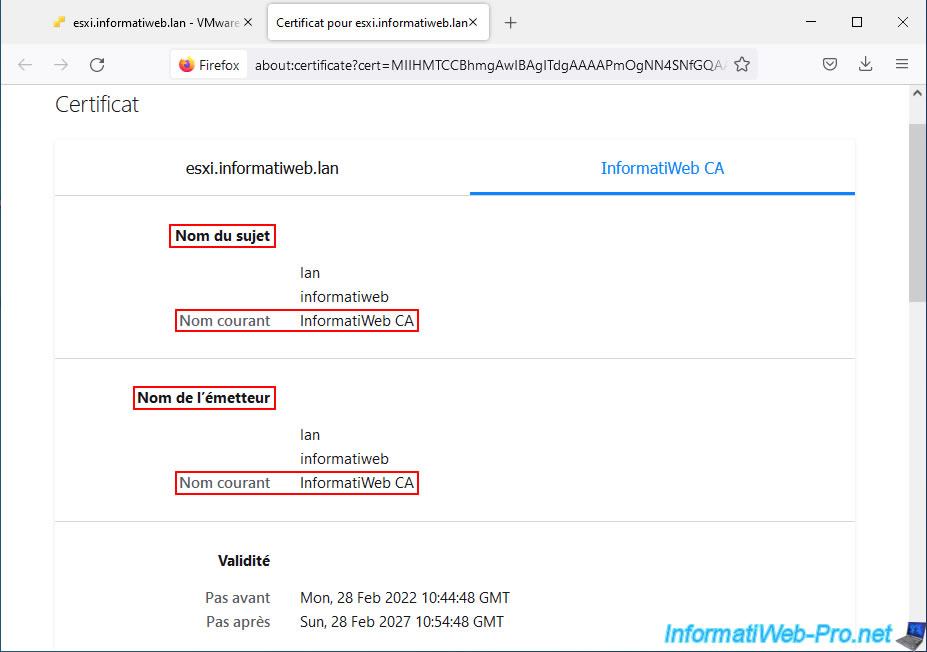
If you click on the 2nd tab, you will be able to see the information regarding the certificate of the certification authority that issued this certificate.
Share this tutorial
To see also
-
VMware 11/15/2024
VMware vSphere 6.7 - Migrate VMs via vMotion (rename VM files)
-
VMware 9/25/2024
VMware vSphere 6.7 - Shared storage (FC, iSCSI, NAS and SAS)
-
VMware 12/25/2024
VMware vSphere 6.7 - Virtual Distributed Switches (vDS)
-

VMware 10/16/2024
VMware vSphere 6.7 - Virtualize a physical computer (P2V)


You must be logged in to post a comment