- Windows Server
- 23 July 2021 at 18:55 UTC
-

- 1/2
When a computer doesn't apply a group policy, the first thing is of course to force the update of the policies on it, but you can then use various tools which allow you to obtain all the necessary information to try to find the cause of your problem.
Here's how to generate this information, also known as : Resultant Set of Policy (RSoP).
- Update the client computer policy
- GPResult
- rsop.msc (Resultant Set of Policy)
- "Resultant Set of Policy" component from the mmc console
1. Update the client computer policy
To get started, update the policy on the client computer or server using the command :
Batch
gpupdate /force
Which will give :
Plain Text
Updating policy ... Computer Policy update has completed successfully. User Policy update has completed successfully.
2. GPResult
GPResult is a command line program that generates the Resultant Set of Policy (RSoP) for :
- current computer and user
- a remote system (computer / server) using the "/S" parameter. The identifiers of an account authorized to access the remote system must be specified using the "/U" and "/P" parameters.
- another user with the "/USER" parameter
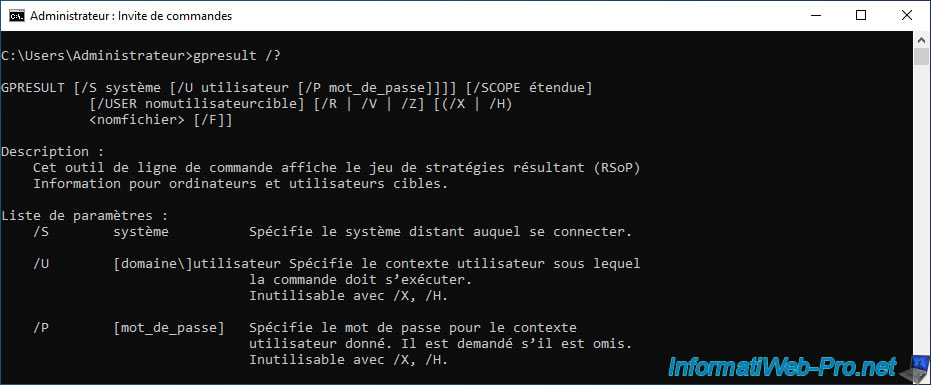
For more informations about the parameters of this "GPResult" command, see : Microsoft Docs.
2.1. Generate Resultant Set of Policy (RSoP) in HTML format
To generate a Resultant Set of Policy (RSoP) in HTML format for the computer and the current user, you must use the "/H" (for the HTML version) or "/X" (for the XHTML version) parameter.
Batch
gpresult /H c:\GPReport.html
Once the command is executed, the file specified in parameter will be created at the desired location.
Note that the "/U", "/P", "/R", "/V" and "/Z" options cannot be specified with "/X" and "/H".
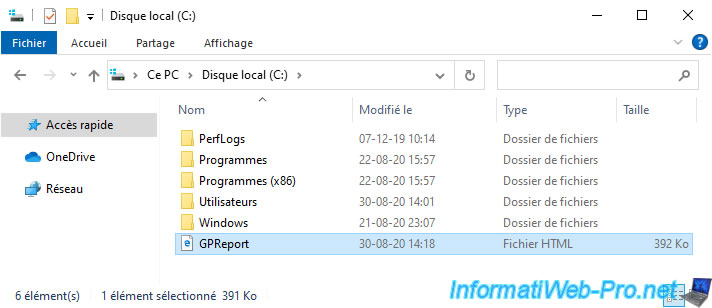
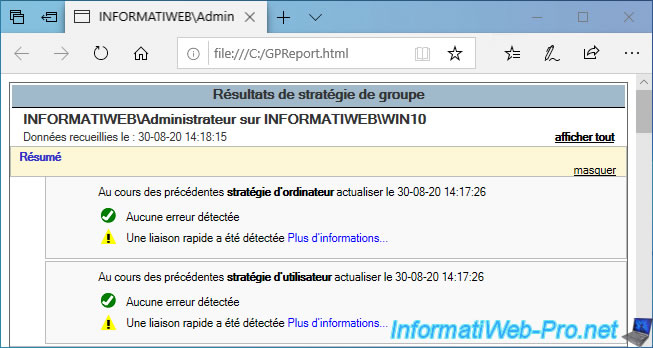
If you open this report, you will first see which user it concerns and for which computer it was generated.
In addition, you will find several sections :
- summary
- computer details
- user details
In the "Summary" section, you can quickly find out (for computer and user policies) :
- if an error occurred while retrieving the updated policy for this computer / user
- whether fast or slow link has been detected.
Note that if a slow link was detected, this may be the source of your problem.
Indeed, when a slow link is detected, it influences the policies that will be applied on this computer.
However, this will never influence security policies and administrative models.
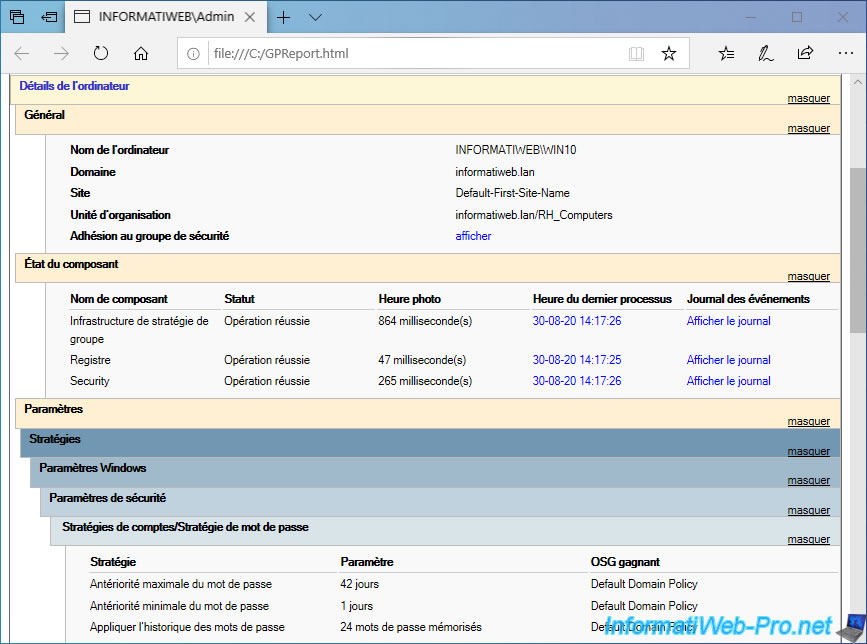
In the "Computer Details" section, you will find :
- the name of the computer concerned by this report
- the Active Directory domain in which it's located
- the Active Directory site of which it's part
- the organizational unit in which the associated computer object is located
- its membership in the security group
- the status of various components : group policy infrastructure, registry and security
- and finally, the most important : the list of policy settings received by this computer. These are therefore the parameters it's supposed to apply.
Note that for each policy setting received, you will have :
- its location in the group policy tree
- his name
- his value
- the name of the winning Group Policy Object (GPO)
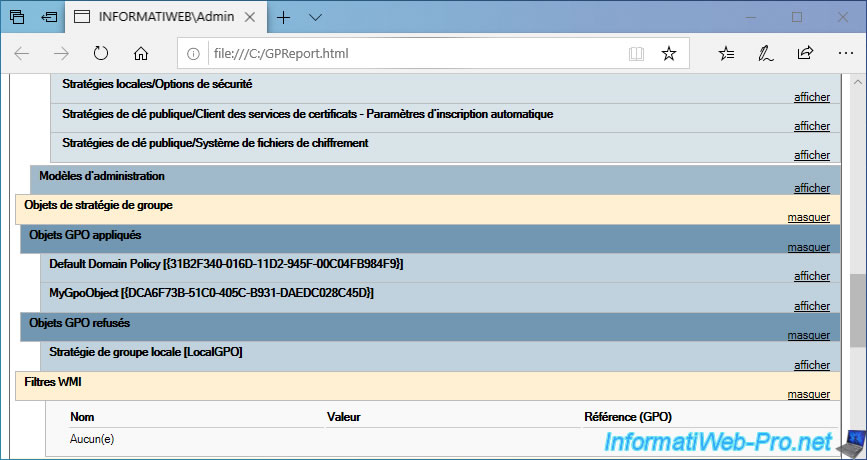
Towards the end of the computer details, you will find a "Group Policy Objects" section that will let you know :
- which GPOs have been applied : with their names and unique identifiers
- which GPOs have been denied : with their names and unique identifiers
Finally, you will find a "WMI Filters" section with the WMI filters that you have created on your domain controller if these WMI filters are affected by this client computer.
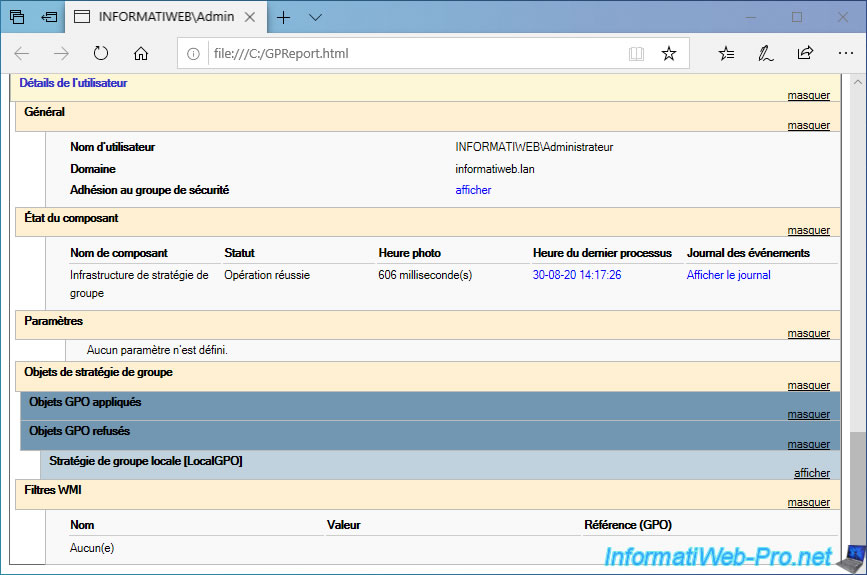
Then, you will find a "User Details" section in which you will find :
- the name of the user for whom this report was generated
- the Active Directory domain in which it's located
- its membership in the security group
- component status : Group Policy Infrastructure
- the list of parameters applied on the user side. In our case, there is none.
- Group Policy Objects (GPOs) applied or denied for user configuration of Group Policies
- the associated WMI filters if there are any
2.2. Generate Resultant Set of Policy (RSoP) in text format
Unlike the report that you generate in HTML format, the one in text format can be longer or shorter (and therefore more or less complete) depending on your needs.
To do this, all you have to do is specify the desired level of detail using one of these parameters :
- /R : show RSoP summary data
- /V : specifies that detailed information should be displayed
- /Z : specifies that extremely detailed information should be displayed
Note that by default, the report is displayed in the console, as you can see below.
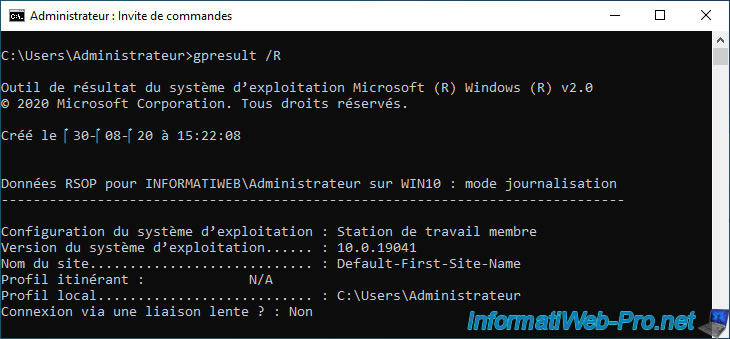
However, you can very easily export the result to a text file thanks to the output redirection supported by the Windows command prompt :
Batch
gpresult /R >> c:\GPReport.txt
Once the report is generated, it will be automatically saved in the "GPReport.txt" file at the root of the "C" partition (in our case).
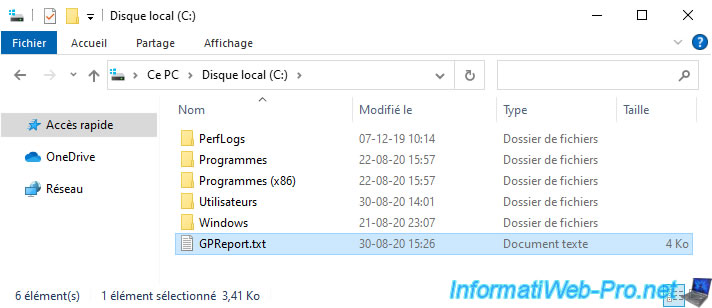
Then, you just have to open it with Notepad.
At the beginning of the report, you can know :
- the domain and name of the user for which this report was generated
- same for the computer name
- information about the operating system installed, including its version
- the name of the Active Directory site in which it's located
- whether roaming profiles are used or not
- whether a connection via a slow link was detected or not
You will then find a "Computer settings" section with :
- the absolute name (distinguishedName) of the associated computer object
- the last Group Policy update time and from which domain controller this update was performed
- the threshold used to detect whether a connection is slow or not. Default : 500 kbps
- the domain name of the computer
- the type of domain used
- the list of applied GPOs
- the list of policies applied on this computer
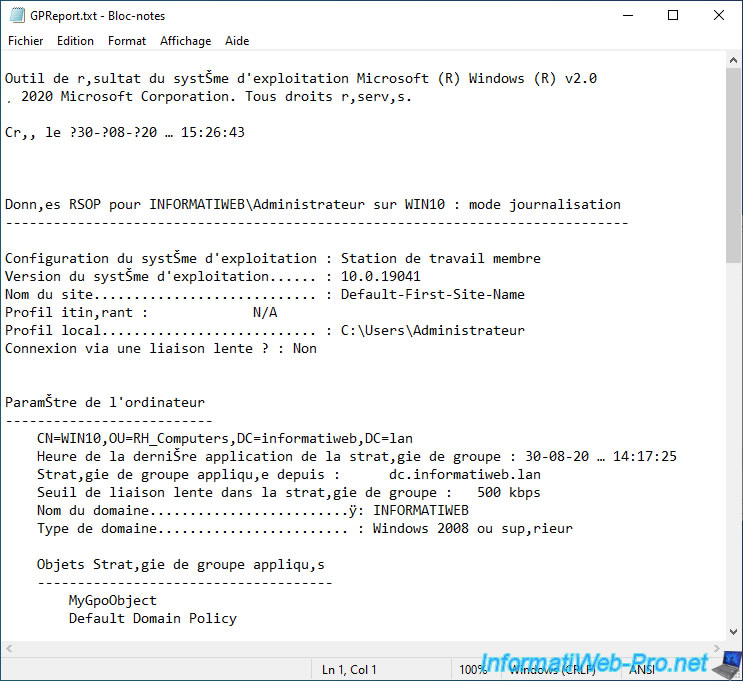
Further down, you will find a "User settings" section with, for example :
- the absolute name of the associated user object
- the list of applied GPOs
- the list of group policies that have been applied on the user side
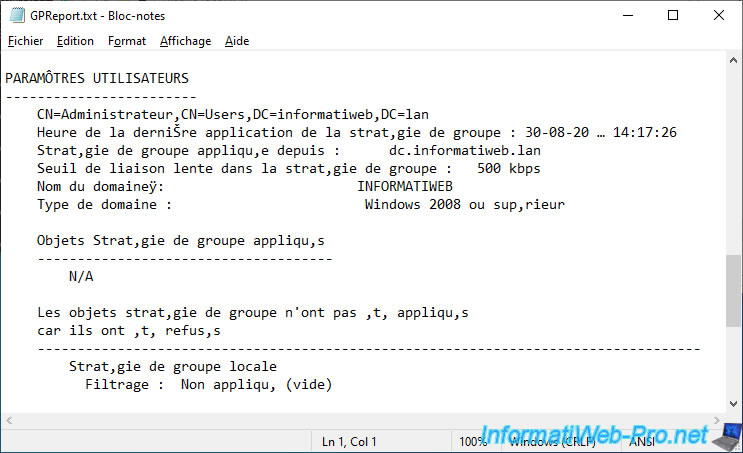
If you are a little observant, you may have noticed that some characters were not the right ones.
This is because the notepad only supports ANSI, Unicode, and UTF-8. However, the command prompt uses another encoding which is the OEM 850.
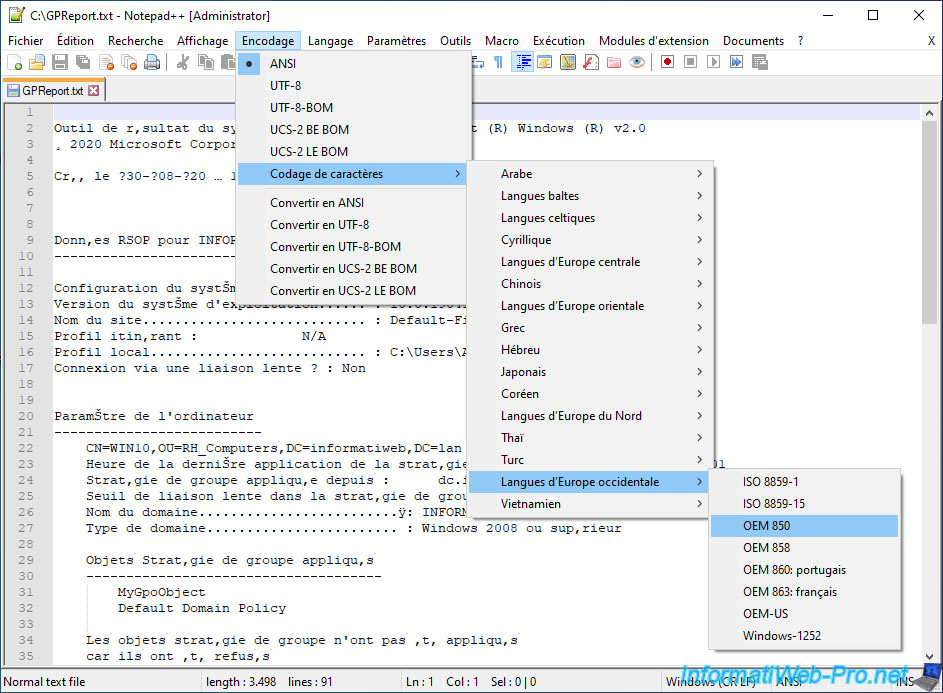
If you want to see the correct characters :
- use another free text editor like Notepad++
- open the "GPReport.txt" file
- go to the "Encoding -> Character sets -> Western European -> OEM 850" menu
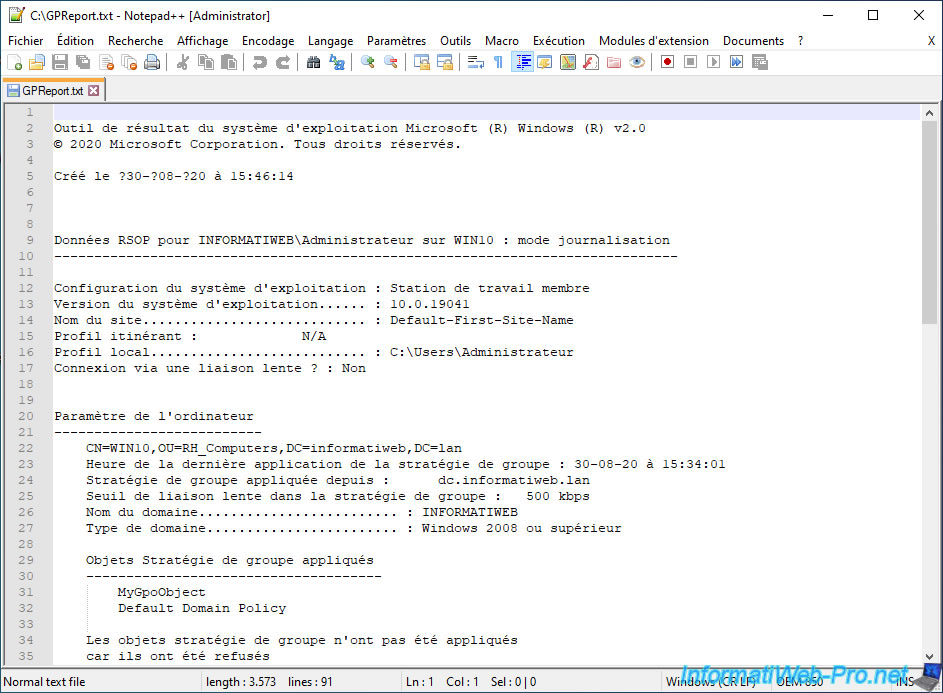
Now, all characters are displayed correctly.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment