- Windows Server
- 20 October 2023 at 08:19 UTC
-

- 1/3
By default, full certificate revocation lists (CRLs) and delta certificate revocation lists (delta CRLs) are accessible only through the LDAP protocol.
In other words, by default, only computers and servers that are members of your Active Directory domain can check the revocation of certificates used in your company.
However, you will see that it's also possible to access these revocation lists (CRL and CRL delta) via the HTTP protocol if you wish.
- Install your certificate authority's web interface
- Installed CA web interface
- Certificate revocation lists accessible via the web
- Add HTTP access to revocation lists (CDP) and certificate authority information (AIA)
- CDP and AIA extensions of old certificates not modified
- CDP and AIA extensions of the new certificates
- Test the validity of the paths present in the CDP and AIA extensions of the certificates (via certutil)
- Test the validity of the paths present in the CDP and AIA extensions of the certificates (via the PKI Enterprise component)
1. Install your certificate authority's web interface
For your clients to be able to access the revocation lists using the HTTP protocol, you obviously need a web server (IIS in the case of Windows Server).
However, you can also install the web interface of your certification authority as explained in our "Install the web interface of a certificate authority (CA) on Windows Server 2016" tutorial.
Indeed, when you install this role service, the IIS web server will be installed and configured automatically to allow access to revocation lists in HTTP.
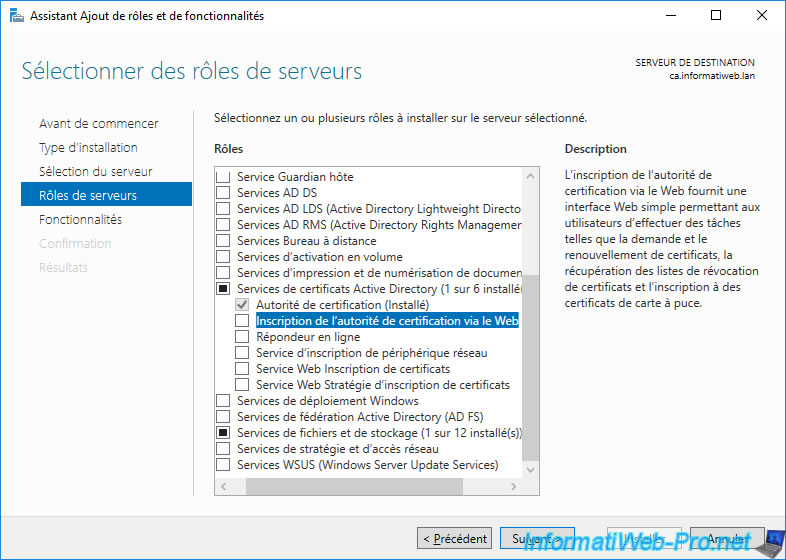
Adding the "Certification Authority Web Enrollment" role service will also add the "Web Server (IIS)" role for HTTP protocol support.
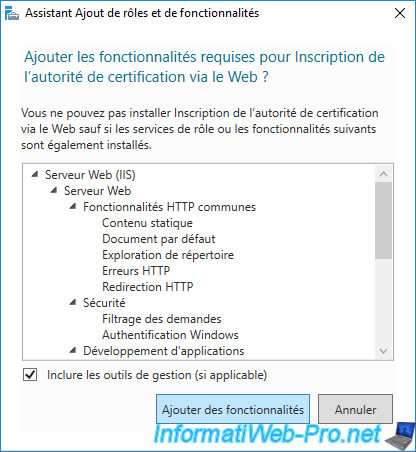
2. Installed CA web interface
Once the "Certification Authority Web Enrollment" role service of your CA is installed and configured, open IIS Manager which was automatically installed.
In this IIS manager, expand the "Default Web Site" node and you will see that 2 folders are present for this site :
- CertEnroll : contains the public certificate of your authority, as well as the complete (CRL) and delta (delta CRL) certificate revocation lists.
- CertSrv : provides access to your CA's web interface to request certificates from any computer or server authorized to do so or download your CA's certificate.
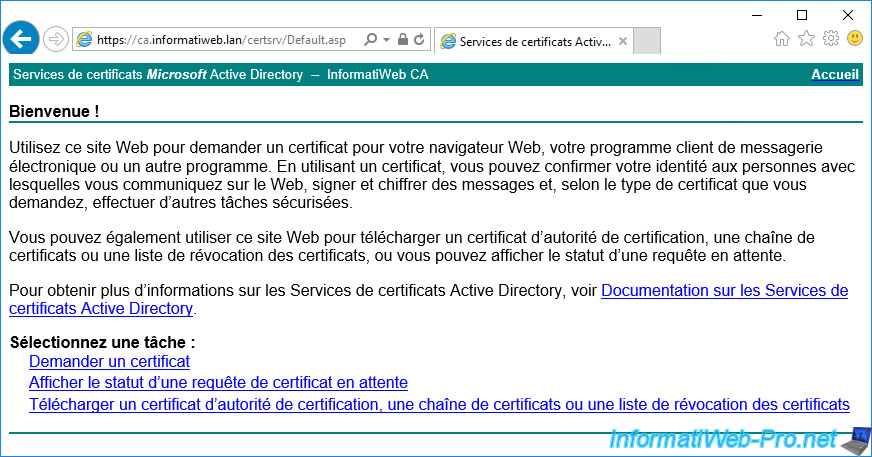
As you can see, if you access the "certsrv" folder of this web server via a web browser, you will arrive on the web interface of your certification authority.
3. Certificate revocation lists accessible via the web
As explained previously, when you install the web interface of your certification authority, a virtual folder named "CertEnroll" is also configured by default on the Default Web Site.
To see its contents, select this "CertEnroll" folder and click on the "Explore" link (in the right column).
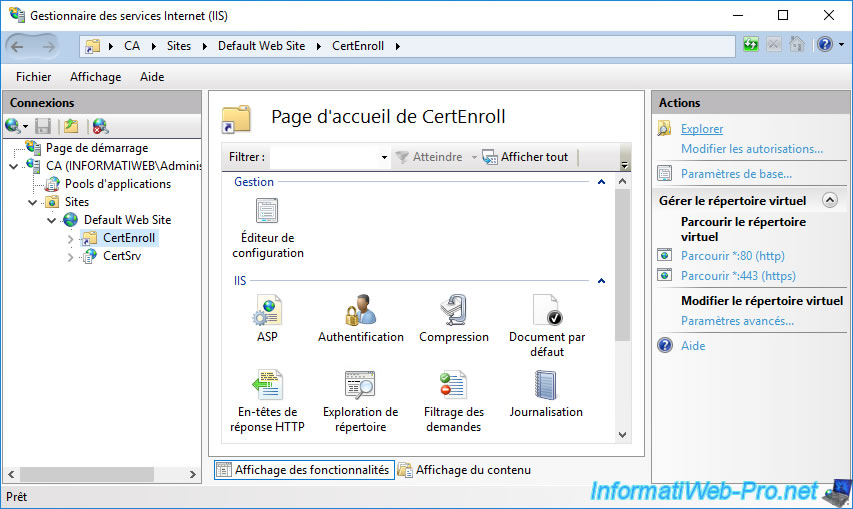
As you can see, this "CertEnroll" virtual folder present on IIS points to the physical folder "C:\Windows\system32\CertSrv\CertEnroll".
In this folder, you will find :
- a "[DNS name of the certification authority]_[common name of the certification authority].crt" certificate : corresponds to the public certificate of your certification authority.
- a "[certification authority name].crl" file: the complete certificate revocation list (CRL)
- a "[certification authority name]+.crl" file : the delta certificate revocation list (delta CRL)
- nsrev_[certification authority name].asp : a script used by IIS.
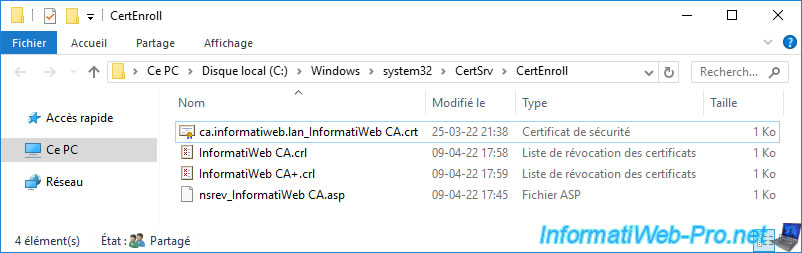
If you open the ".crt" certificate present, you will see that it's indeed the certificate of your certification authority.
This is referenced in your certificates thanks to the AIA extension included in your certificates.
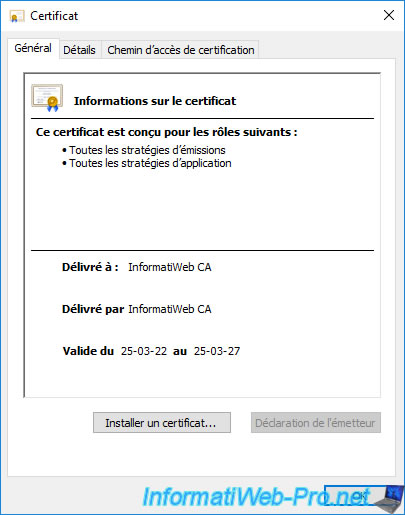
If you go to the "Details" tab of this certificate and select the "Basic Constraints" field, you will see that it's a CA certificate.
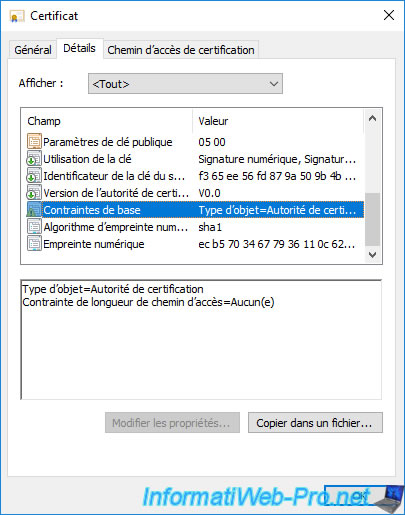
If you double-click on the "[certification authority name].crl" file, you will see that it's the full certificate revocation list (CRL) of your certification authority.
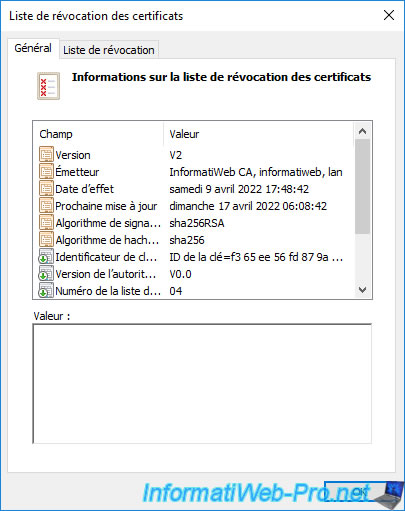
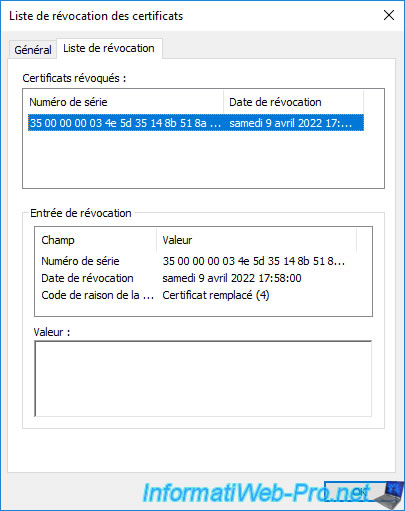
If you go to the "Revocation List" tab of this certificate revocation list, you will see the list of serial numbers of certificates that have been revoked on your certification authority.
If you double click on the file with a "+" at the end ([certification authority name].crl), you will see that it's the delta certificate revocation list (delta CRL) from your certificate authority.
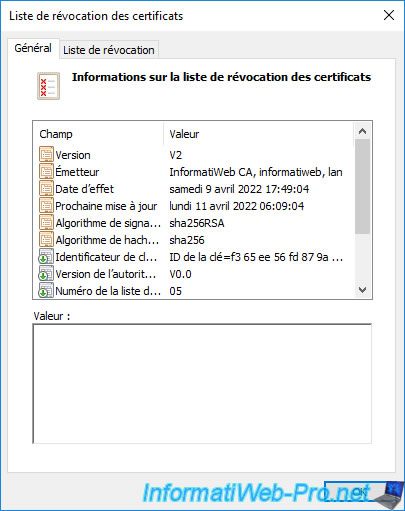
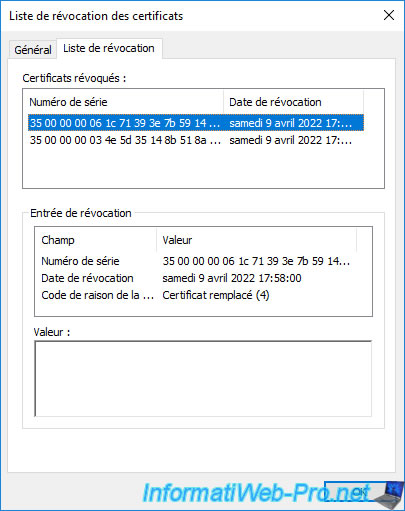
If you go to the "Revocation List" tab of this delta certificate revocation list (delta CRL), you will be able to see the list of certificates that were revoked after the complete certificate revocation list (CRL) was published.
As you can see, the ASP script present in this folder is used for certificate revocation checking.
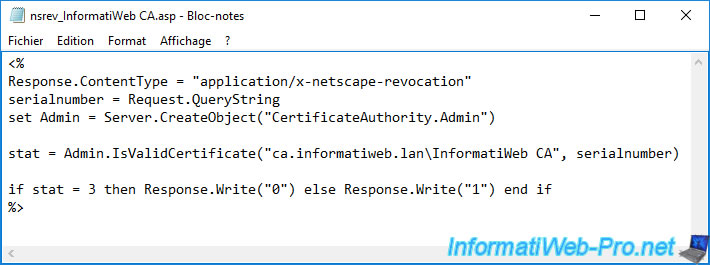
Note that for the delta revocation lists to also be accessible via this "CertEnroll" virtual folder, a specific configuration setting must be correctly configured.
This is the case by default if you have installed the web interface of your certification authority.
However, if you have manually created this virtual folder on an existing IIS web server, it's necessary to check its configuration.
To do this, select your "CertEnroll" virtual folder and go to the configuration editor.
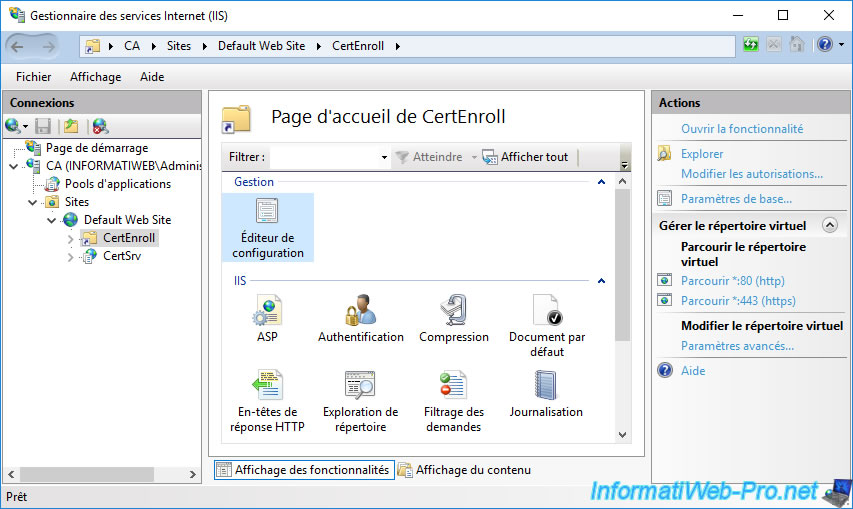
In the configuration editor that appears, go to the "system.webServer\security\requestFiltering" section.
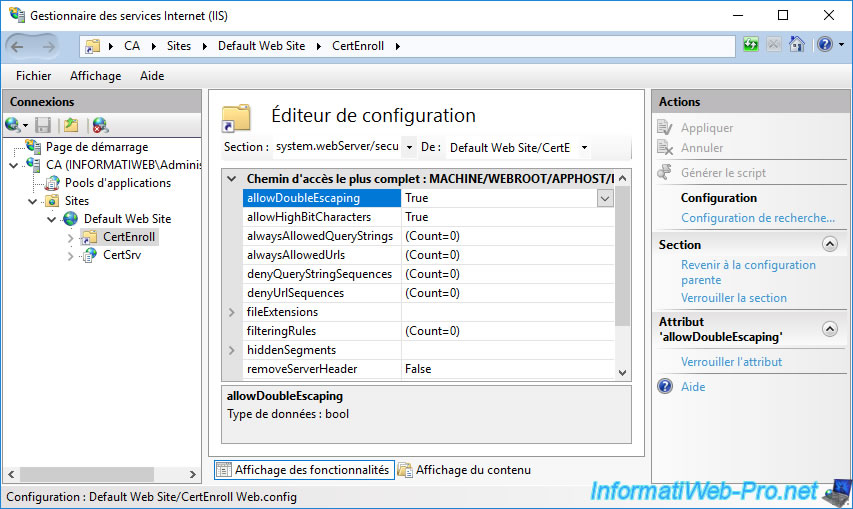
In the table that appears, make sure that the value of the "allowDoubleEscaping" setting is "True".
This authorizes access to files containing special characters in their name (including the certificate revocation list beyond whose file name ends with a "+").
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them


You must be logged in to post a comment