Publish CRLs accessible via the web (HTTP) on an authority on Windows Server 2016
- Windows Server
- 20 October 2023 at 08:19 UTC
-

- 2/3
4. AIA and CDP extensions present in your certificates
By default, your servers and computers can access revocation information and your CA information through data stored in your Active Directory.
To verify this, open one of the certificates issued by your certification authority.
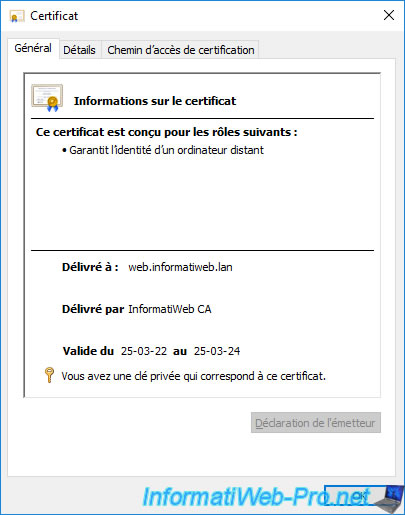
Then, go to the "Details" tab of it.
As you can see, the "CRL Distribution Points" field contains the "ldap://" path (Active Directory) so that your server or computer knows where to find the certificate revocation lists in your Active Directory infrastructure.
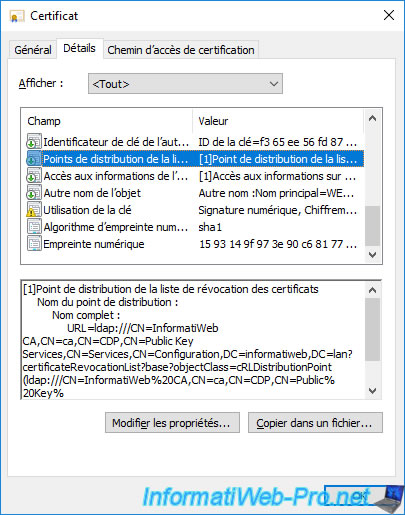
If you select the "Authority Information Access" field, you will see that it contains the path "ldap://" (Active Directory) so that your server or computer knows where to find information about your certification authority in your Active Directory infrastructure.
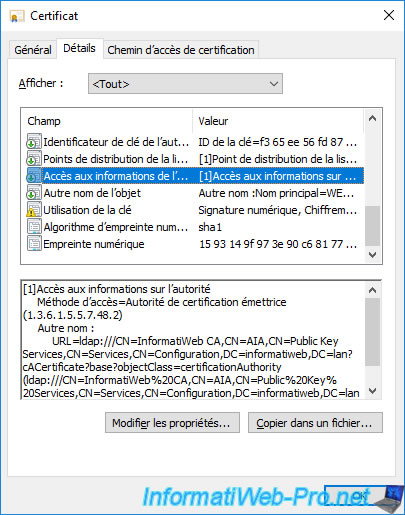
As you will have understood, by default, your servers and computers can access your certification authority's revocation lists, as well as its information, only via the "ldap://" protocol.
Which means that if your server or computer doesn't have access to Active Directory, it will not be able to access this data.
5. Add HTTP access to revocation lists (CDP) and certificate authority information (AIA)
For redundancy purposes or to provide access to revocation lists (CRLs) and CA information from a server or computer that is not a member of your Active Directory infrastructure, you can add HTTP access to these informations.
To do this, open the "Certification Authority" console and right-click "Properties" on the name of your certification authority.
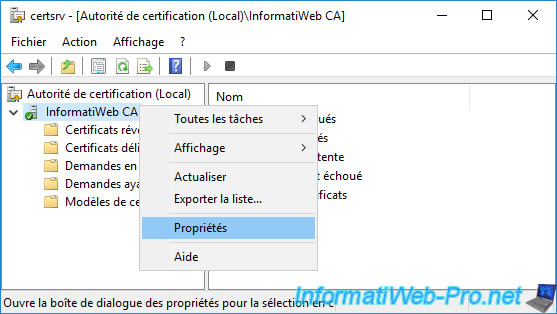
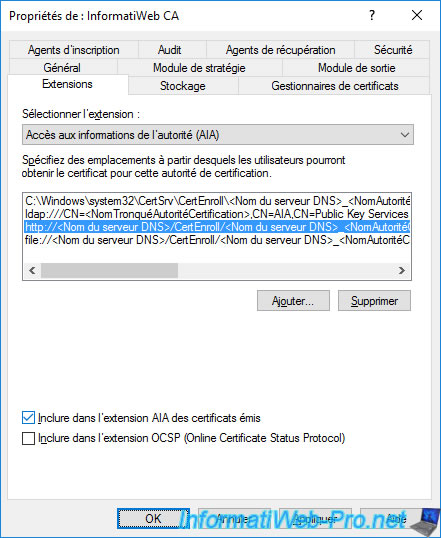
In the properties window of your certificate authority that appears, go to the "Extensions" tab.
As you can see, by default, the "CRL Distribution Point (CDP)" option is displayed.
This shows you the different locations where your certification authority's certificate revocation lists (CRLs) are published (stored).
To begin, you can see that the local path "C:\Windows\system32\CertSrv\CertEnroll\..." is selected by default and the following boxes are checked as soon as your CA is installed :
- Publish CRLs to this location : specifies that complete certificate revocation lists (CRLs) will be published (stored) to this location.
- Publish Delta CRLs to this location : same, but for publishing (storing) delta certificate revocation lists (delta CRLs).
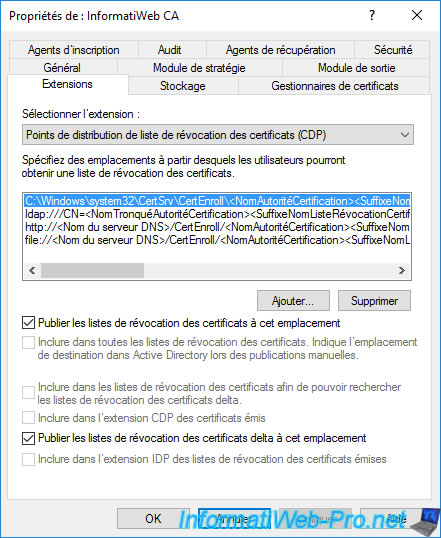
If you select the "ldap://CN=..." path, you will see that most of the boxes are checked :
- Publish CRLs to this location : specifies that complete Certificate Revocation Lists (CRLs) will be published (stored) here in your Active Directory infrastructure.
- Include in all CRLs. Specifies where to publish in Active Directory when publishing manually : indicates that the storage location of the certificate revocation lists in the Active Directory will be indicated in the CDP extension of your certificates for manual publications of revocation lists.
- Include in CRLs. Clients use this to find Delta CRLs locations : indicates that the search location for delta certificate revocation lists (delta CRLs) will be indicated in the "CDP" extension of your certificates.
- Include in CDP extension of issued certificates : specifies that the search location for complete Certificate Revocation Lists (CRLs) will be listed in the "CDP" extension of your certificates.
- Publish Delta CRLs to this location : specifies that delta certificate revocation lists (delta CRLs) will be published (stored) here in your Active Directory infrastructure.
- Include in the IDP extension of issued CRLs : this box is unchecked by default, because this IDP (Issuing Distribution Point) extension is only used by non-Microsoft clients to check the revocation of certificates issued by your certification authority.
In summary :
- the "Publish CRLs..." options indicate that CRLs will be published (stored) in the desired location.
- the "Include in..." options indicate that paths to certificate revocation lists (CRLs or delta CRLs) will be specified in the "CRL Distribution Points (CDP)" extension of future certificates issued by your certificate authority.
As you can see, by default, a copy of your CA's revocation lists are published (stored) in the Active Directory and their paths are included in certificates issued by your CA.
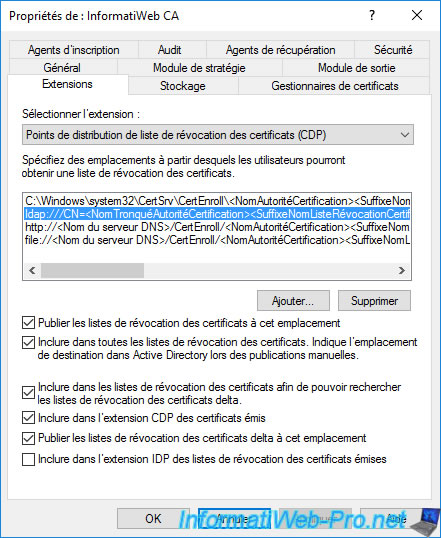
As you can see, by default, HTTP access is configured for accessing your CA's revocation lists via the web, but this is not used by default.
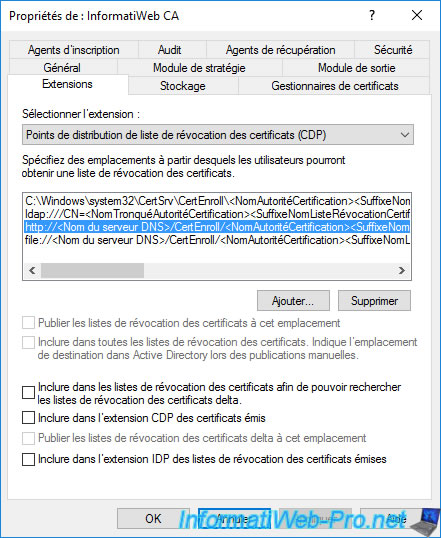
If you have installed your CA's web interface (via the "Certificate Authority Web Enrollment" role service) on the same server as your CA, you can very easily add this access by HTTP by checking the boxes :
- Include in CRLs. Clients use this to find Delta CRL locations : allows you to indicate the HTTP link to the delta certificate revocation lists (delta CRLs) in the "CDP" extension of future certificates issued.
- Include in the CDP extension of issued certificates : ditto, but for access to complete certificate revocation lists (CRLs).
Note : there is no need to check the "Include in the IDP extension ..." box if you only use Windows Server servers and Windows clients, because these will never use this IDP extension.
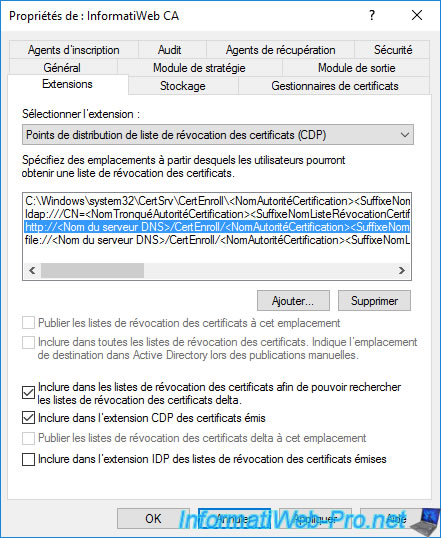
Finally, you can also publish and provide access to certificate revocation lists (CRLs and delta CRLs) via a network share if you wish, using the "file://" protocol.
However, this is never used in business.
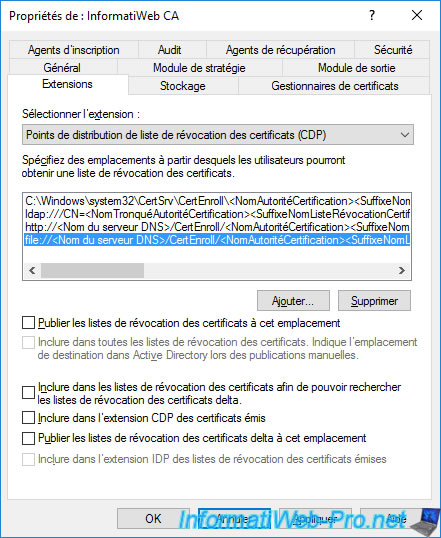
In this "Extensions" tab, you can also configure access to information from your certification authority by selecting the "Authority Information Access (AIA)" option.
The 1st path selected by default is again the "C:\Windows\system32\CertSrv\CertEnroll\..." folder.
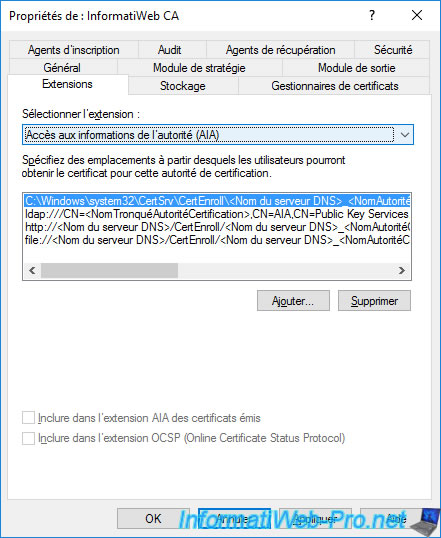
If you select the "ldap://CN=..." path, you will see that by default, your servers and clients will be able to access your CA information via Active Directory.
Having the "Include in AIA Extension of Issued Certificates" box checked indicates that the path to your specified CA information will be included in the "Authority Information Access (AIA)" extension of the issued certificates.
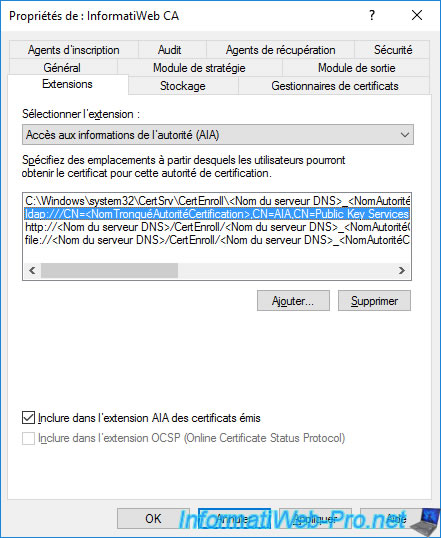
Again, you can see that an "HTTP" access is configured by default, but its path is not included by default in your issued certificates.
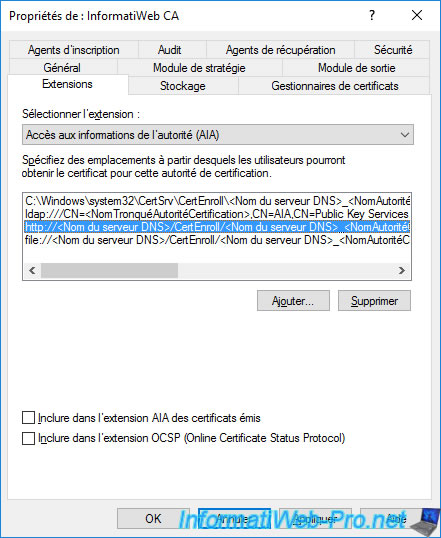
Again, if you installed your CA's web interface on the same server as your CA, you can simply check the "Include in the AIA extension of issued certificates" box.
This will ensure that the HTTP path to your CA information will be included in the "Authority Information Access (AIA)" extension of your future certificates.
Finally, you will see that you also have the option of using the "file://" protocol to access information from your certification authority.
Nevertheless, this is again not used in business.
Click OK to save changes.
Note : the option concerning the OCSP extension requires the installation of an online responder (OCSP) and allows clients to check the revocation of a certificate by sending an OCSP request to the previously configured responder rather than downloading all the revocation lists from your certificate authority.
A warning will appear telling you that Active Directory Certificate Services needs to be restarted.
Click Yes.
Wait while Active Directory Certificate Services stops and then starts.
6. CDP and AIA extensions of old certificates not modified
If you open one of your old certificates, you will notice that the new paths (HTTP) that you have just enabled are not present on your old certificates.
Indeed, the paths added for the "CDP" and "AIA" extensions of your certificates will only be included in your future certificates.
It's therefore important that these extensions are configured from the beginning.
If you want these new HTTP paths to be included in these certificates, you will need to regenerate them.
7. CDP and AIA extensions of the new certificates
For this tutorial, we issued a new certificate to our web server using the "mmc" console on it.
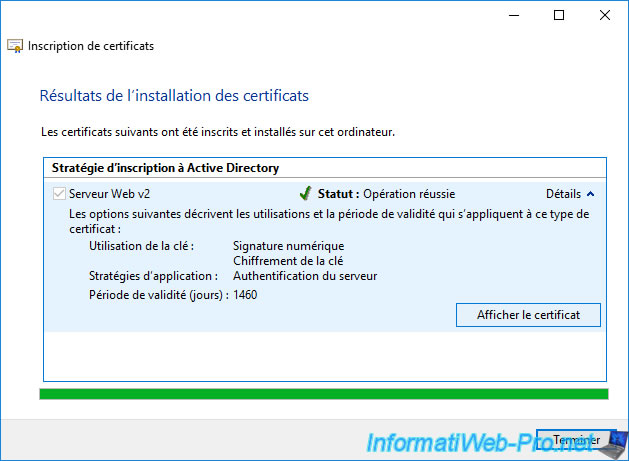
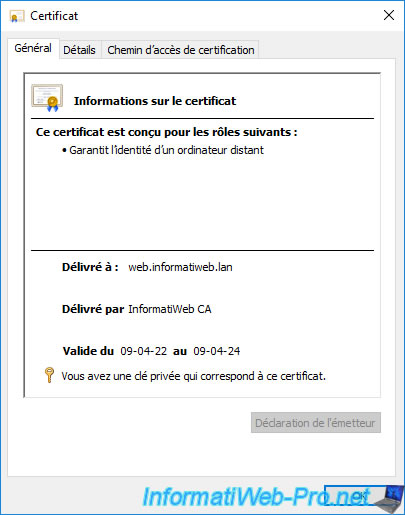
We open the certificate that we have just enrolled.
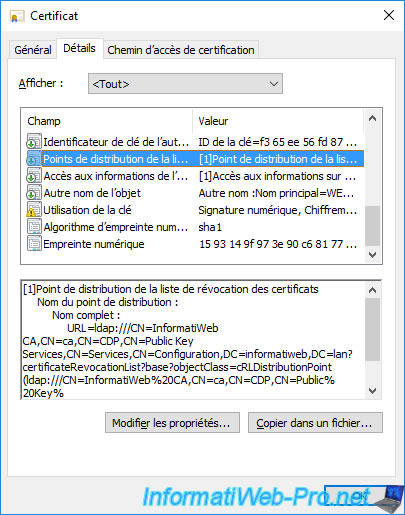
Go to the "Details" tab of this new certificate and select the "CRL Distribution Points" (CDP) field.
As you can see, the search path for revocation lists (CRLs) is still there.
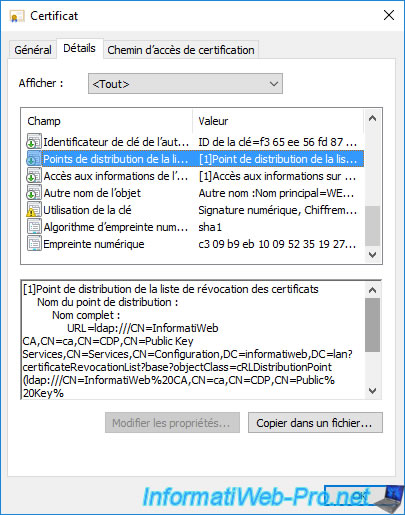
But, if you look at the bottom of this field, you will see that the HTTP path to the revocation lists of your authority has also been added there.
If you copy-paste the HTTP link present in this extension "CRL Distribution Points" (CDP) in a web browser, you will see that a "[your CA name].crl" file will be offered for download.
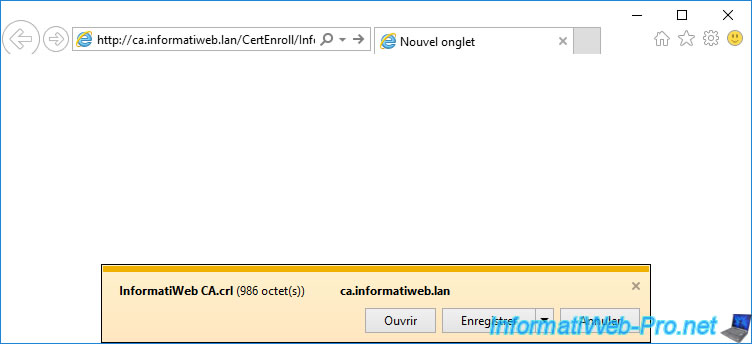
If you open it, you will see that it's indeed the certificate revocation list published by your certificate authority.
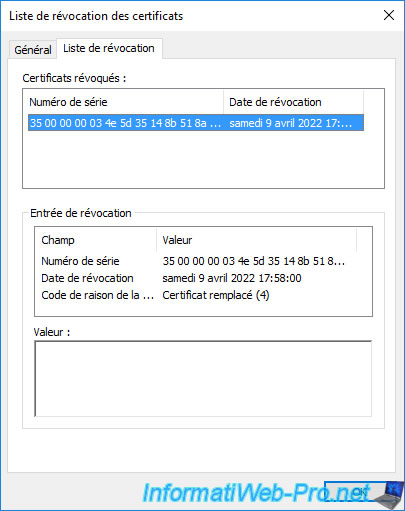
To see the revoked certificates there, go to the "Revocation List" tab.
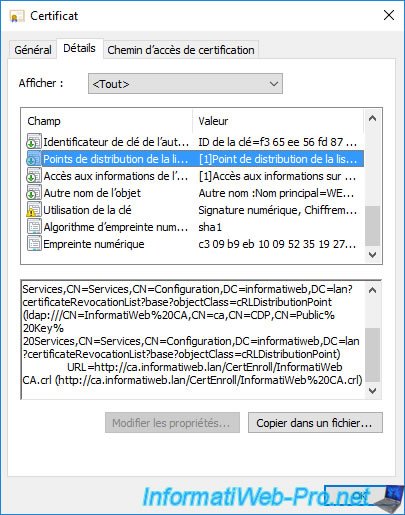
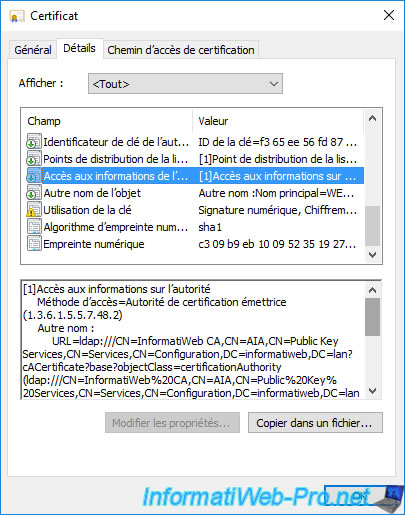
If you select the "Authority Information Access" (AIA) field, you will see that the path to your CA information via the "ldap://" protocol (Active Directory) is still present.
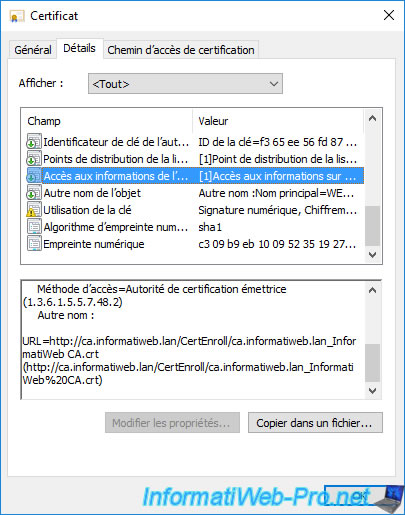
But, if you look at the bottom of this field, you will see that the HTTP path to your authority information has also been added there.
In this case, the link indicated points to the certificate of your authority present in the "C:\Windows\system32\CertSrv\CertEnroll" folder of your certification authority.
If you copy-paste the HTTP link present in this "Authority Information Access" (AIA) extension into a web browser, you will see that a "[your CA's DNS name]_[your CA's name].cer" file will be offered for download.
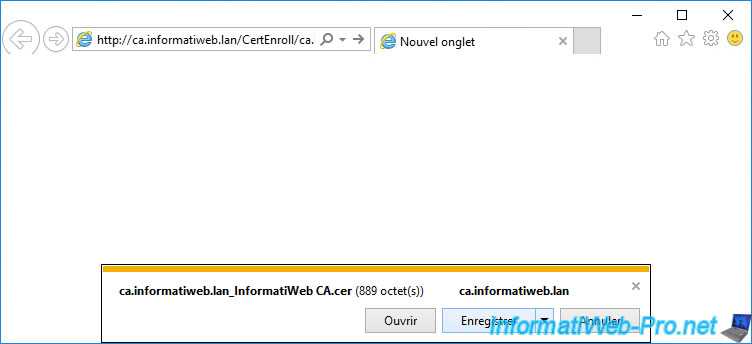
Once this file is downloaded, open it.
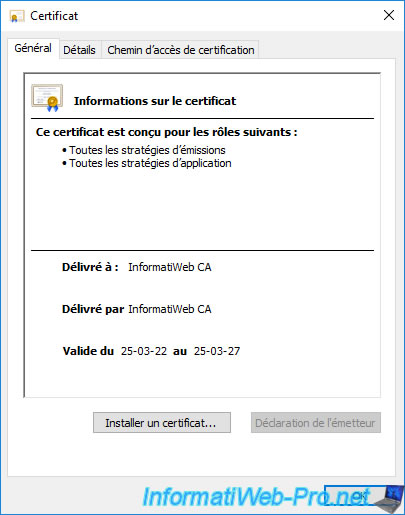
As you can see, this is your CA's public certificate.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment