Manage EFS certificates in enterprise on Windows Server 2016
- Windows Server
- 02 December 2023 at 09:55 UTC
-

- 3/3
6.2. Copy of the public certificate stored in the Active Directory (visible from the mmc console)
When you use the "mmc" console on your computer or server to see your personal certificates (for the current user), you can see that these also have an associated private key (thanks to the key displayed on the icon of the certificate).
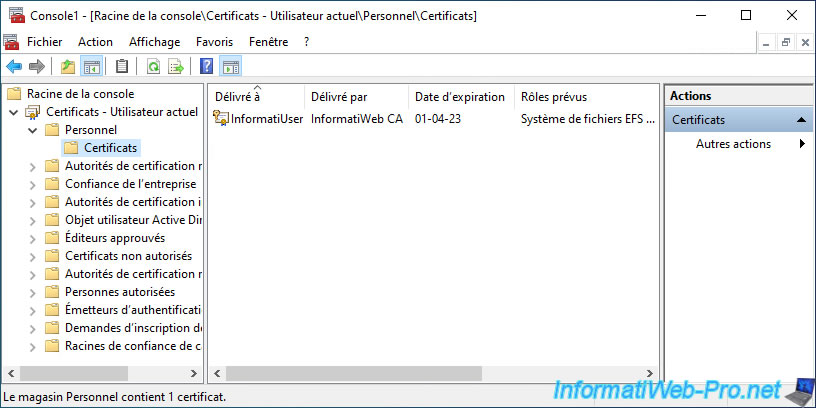
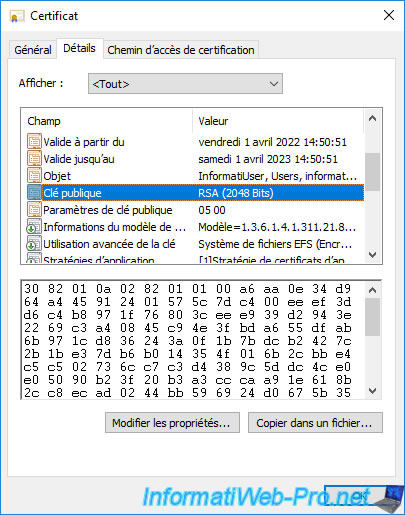
If you double-click on this personal certificate, you will see the line "You have a private key that corresponds to this certificate" appear.
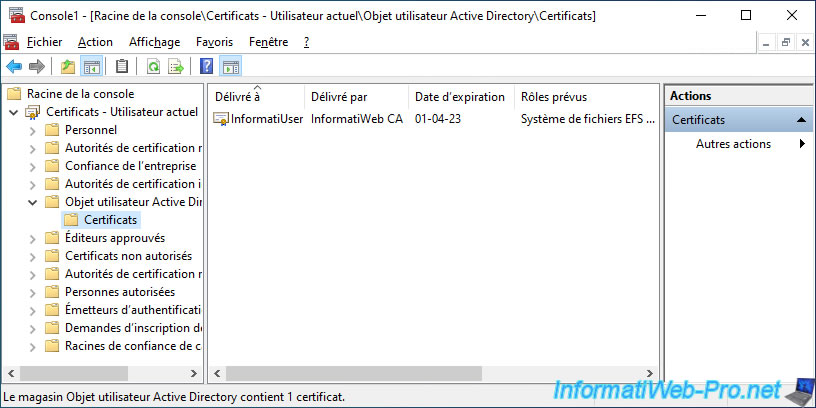
If you go to the "Active Directory User Object" folder of this same "mmc" console, you will see that your user certificate is also present.
However, the icon is slightly different, as this one doesn't contain a private key.
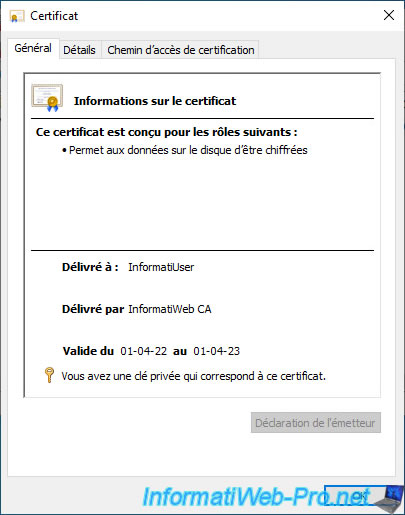
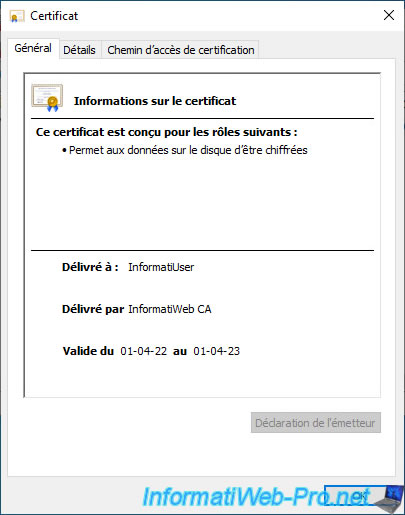
If you double-click on it, you will find that the line "You have a private key that corresponds to this certificate" doesn't appear this time.
Which indicates that the private key corresponding to this certificate is not present.
6.3. Copy of the public certificate stored in the Active Directory (visible from the domain controller)
As explained previously, if the "Publish certificate in Active Directory" option was checked in the settings of the certificate template used when enrolling the certificate, a copy of this certificate was stored in the Active Directory.
To see this copy, open the "Active Directory Users and Computers" console on your Active Directory domain controller and go to : View -> Advanced Features.
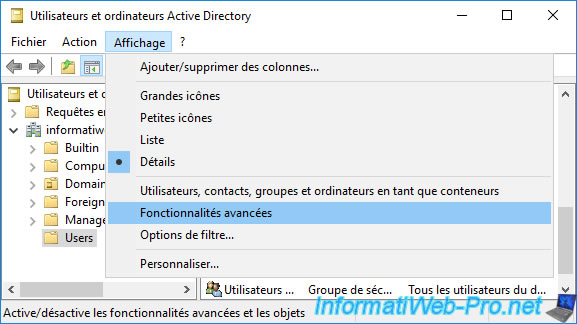
Now that the advanced features of this console are enabled, double-click a user account that has already received a certificate for EFS through auto-enrollment.
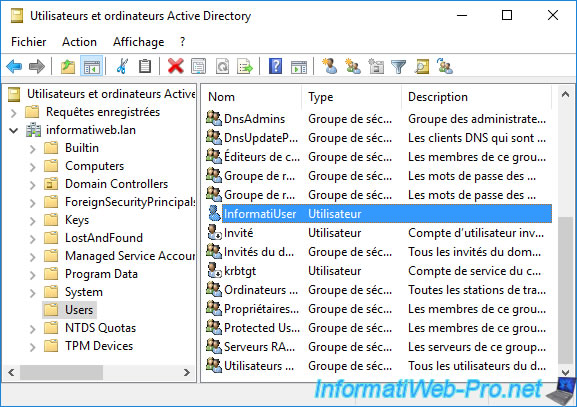
If you go to the "Published Certificates" tab, you will see that this user's certificate will appear.
To see the details of this certificate, select it and click : View Certificate.
Note : this tab is only visible if the advanced features of this "Active Directory Users and Computers" console have been enabled.
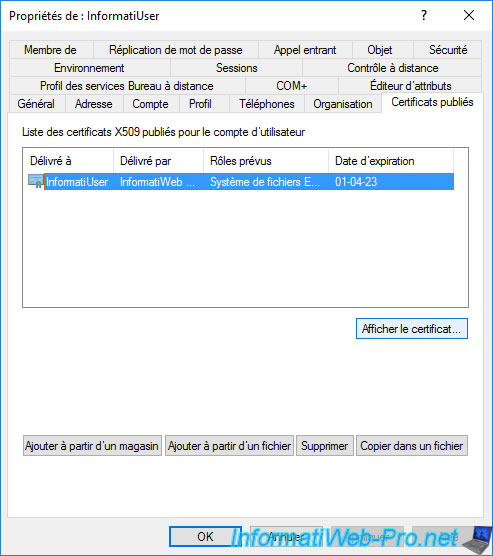
As you can see, it's again the same user certificate, but the associated private key is not present (as it's not indicated at the bottom of the window).
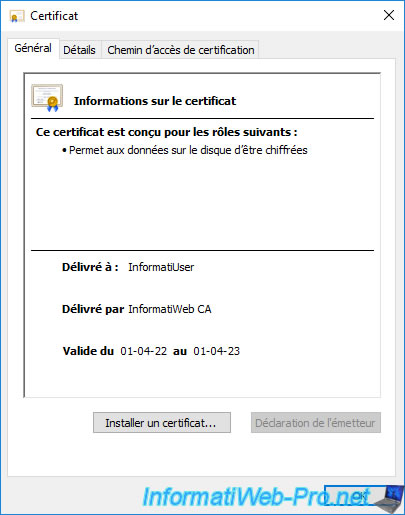
6.4. Issued certificate visible from CA
A copy of the enrolled (issued) certificate is also visible from your certification authority.
To do this, open the "Certification Authority" console and go to the "Issued Certificates" folder.
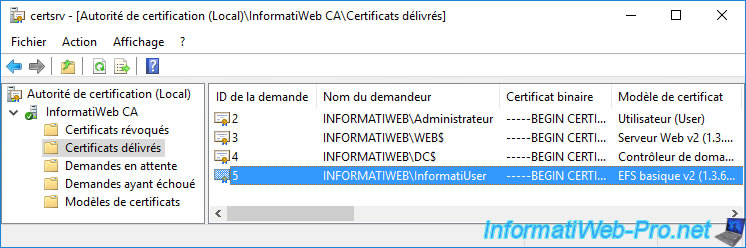
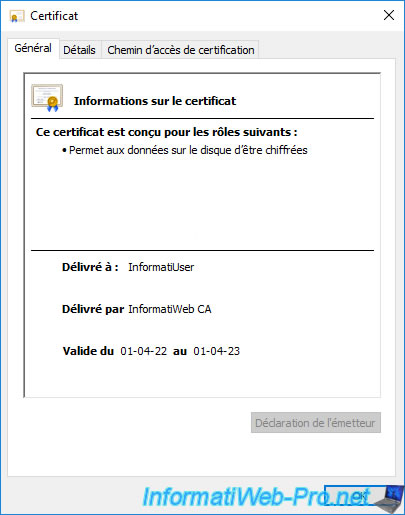
If you double click on it, you will see the same certificate again.
But, again, this is the public copy of it.
The private key is therefore not available here.
In summary, this user's public certificate is visible from several places, but the private key is only available in the user's "Personal" certificate store on the computer or server where the user received it. .
7. Encrypt data using the EFS file system
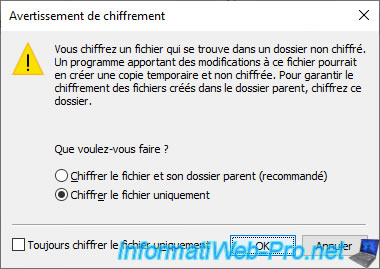
To encrypt data using the EFS file system, create a "test.txt" file (for example).
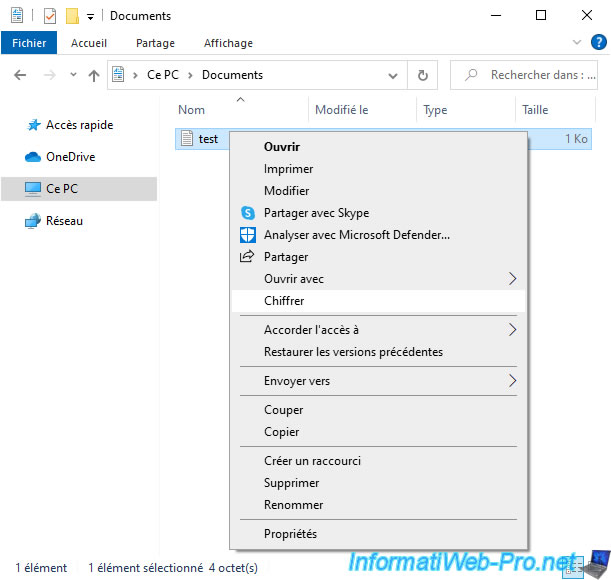
Then, right click "Encrypt" on it.
Note : this option is available thanks to the data that we have added to the registry thanks to group policies (GPO).
Choose "Encrypt the file only" and click OK.
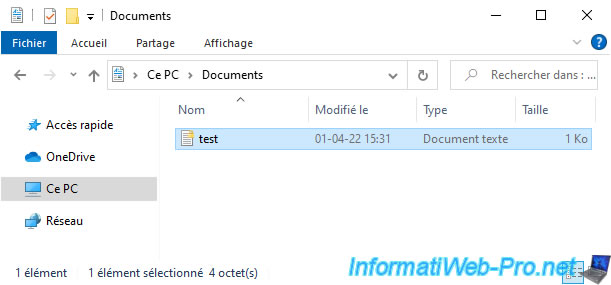
Once the file is encrypted, a yellow icon will appear on it.
Note : on previous versions of Windows, the file name will be displayed in green.
8. Enable certificate roaming
Currently, a user can only obtain a certificate on one computer or server.
If he connects to another computer or server, he will not receive an additional certificate (based on the same template) automatically.
Indeed, when creating the new "Basic EFS v2" certificate template, we checked the "Do not automatically reenroll if a duplicate certificate exists in Active Directory" box.
This avoids issuing several different certificates (serial number and different public/private keys) to the same user.
Nevertheless, so that he can encrypt data from a computer or a server and decrypt them from another computer or server (if he wishes), it's important that the latter can retrieve a copy of his certificate and his associated private key.
To do this, you will need to enable certificate roaming.
Note that certificate roaming is recommended whether or not roaming profiles are enabled.
If roaming profiles are enabled, certificates are already roaming from computer to computer.
To enable certificate roaming, edit your Active Directory domain group policies again and go to : User Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies.
Then, double-click the setting : Certificate Services Client - Credential Roaming.
Enable this setting and click OK.
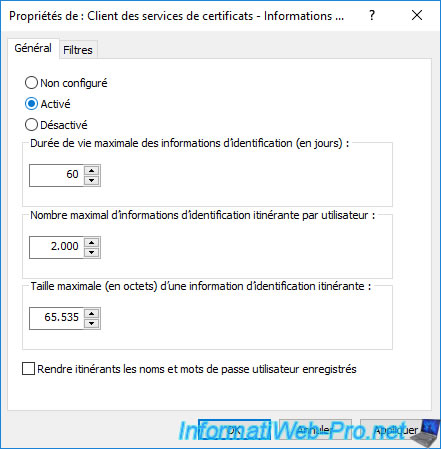
To avoid conflicts, you can choose to exclude certificates from roaming profiles.
Whether or not roaming profiles are enabled in your case, we recommend that you click "OK" to exclude certificates from roaming profiles.
So, if you later decide to use roaming profiles, this exclusion will already be set up.
9. Certificate roaming test
To begin, log on to the computer from which you have already received your user certificate.
Important : in order for the certificate issued, as well as its associated private key to be stored in the Active Directory, it's important that certificate roaming has been configured before the user receives his certificate.
Otherwise, the user will have to reconnect, then disconnect at least once on the computer or server where he had received his certificate, so that this user can automatically retrieve his certificate and his private key from any another computer or member server of the same Active Directory domain.
Since we reconnected on the same computer as before, our personal certificate is still present, as well as its associated private key.
Now, we log off from this computer so that a copy of this certificate and its associated private key is stored in the Active Directory.
We connect to one of our servers with this same user.
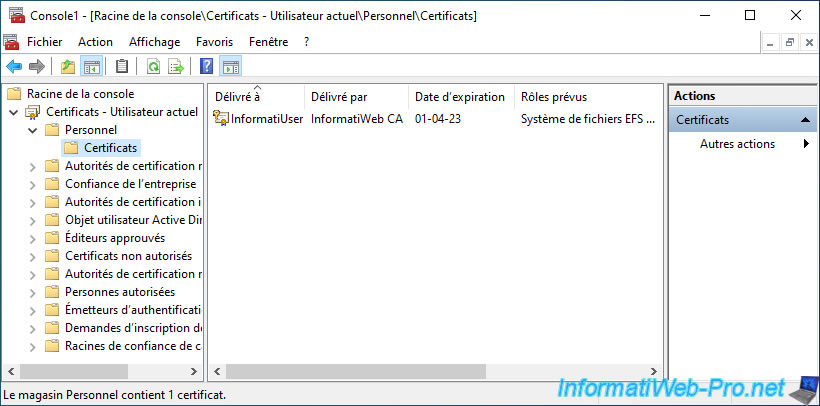
We use the "mmc" console to see our user certificates and we can see that our personal certificate and its associated private key are present.
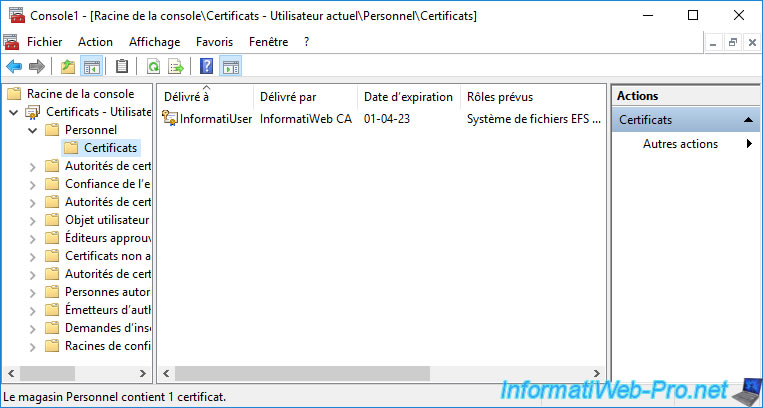
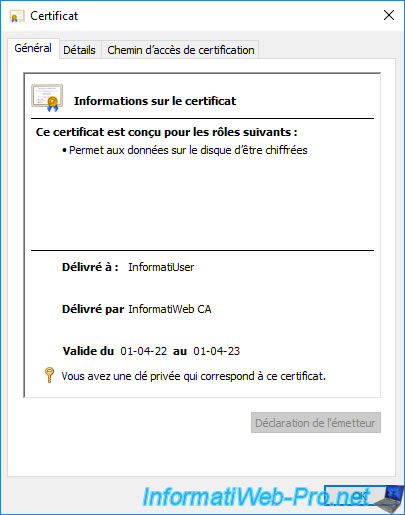
If you double click on this certificate, you will see at the bottom of the window that the private key corresponding to this certificate is present.
Unlike the copy of the certificate visible from the domain controller or from your certification authority.
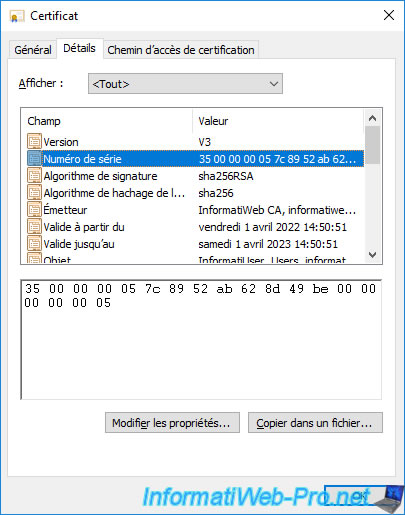
If you go to the "Details" tab, you will see that the serial number of this certificate is the same as the one you received previously from another computer in your company.
It's therefore the same certificate.
If you check the public key of this certificate, you will see that it's also the same.
Which means that this user can easily encrypt a file from one computer and decrypt it from another computer (given that the "public key / private key" pair is identical for him).
Important : in business, we therefore advise you to configure automatic enrollment and roaming of certificates before creating your user accounts.
Thus, when your users have their user account, they will automatically receive a certificate at the first logon and a copy of the certificate and the associated private key will be automatically transferred to your Active Directory when they close their session.
Remember that user policy is automatically updated at logon, as well as periodically.
Warning : deleting a certificate locally (via the mmc console, for example) will also delete the copy of the certificate and the associated private key that had been synchronized to the Active Directory (if applicable).
To find out how certificate roaming works via Active Directory, refer to the official Microsoft documentation : Understanding credential roaming.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment