Install and configure a root certificate authority (CA) and a secondary CA on Windows Server 2016
- Windows Server
- 08 December 2023 at 12:04 UTC
-

- 2/5
5. Store standalone root certification authority (CA) information in Active Directory
When you create an enterprise certificate authority (CA), its information (CA certificate and revocation lists) are automatically stored in Active Directory.
This then allows servers and computers in your Active Directory domain to know that a certification authority is present in your company.
This also allows them to check the revocation of your certificates by accessing the revocation lists which are automatically published there.
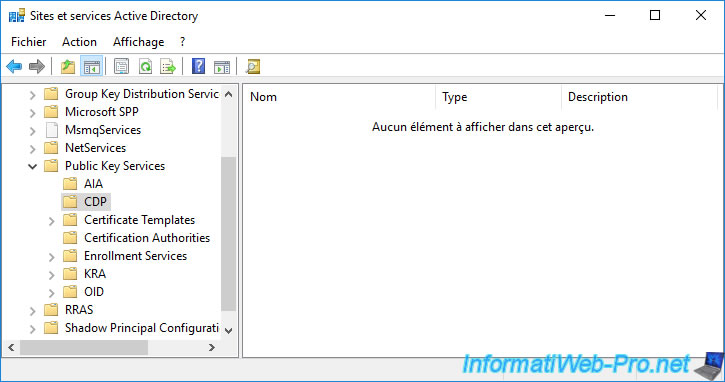
On your domain controller, open the "Active Directory Sites and Services" console and go to the menu : View -> Show Services Node.
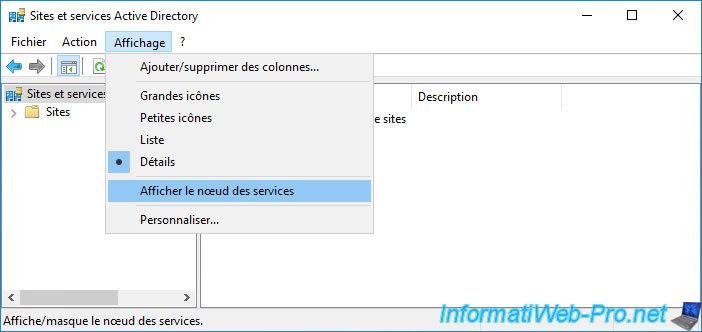
The "Services" folder appears in this console.
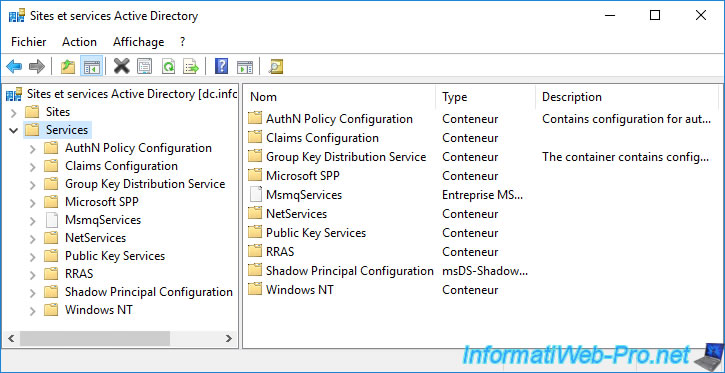
In the "Services" folder, you will find a "Public Key Services" folder.
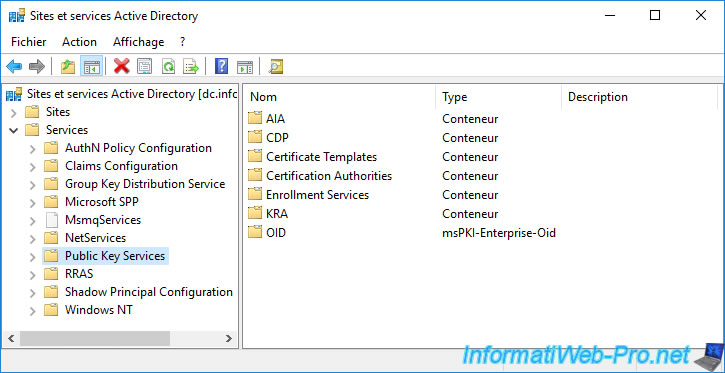
In this "Public Key Services" folder, you will find several folders :
- AIA : provides access to information of your certification authority
- CDP : allows access to the certificate revocation lists of your certificate authority
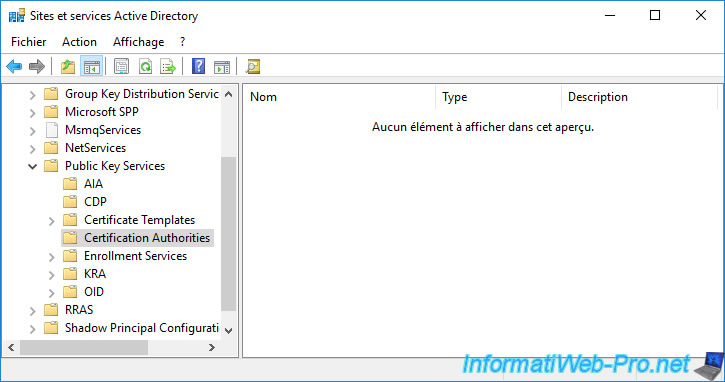
- Certification Authorities : allows your servers and client workstations to know that one or more certification authorities are present in your company
As you will understand, this information is stored in the Active Directory.
However, in the case of a standalone certification authority, this information is not created in the Active Directory automatically.
Indeed, a standalone certification authority is always installed on a server located in a workgroup and not in an Active Directory domain.
Since your "root-ca" server has no knowledge of your Active Directory, so your standalone root CA information is not present here.
Specifically, the information presented above is located in the "Configuration" partition of your Active Directory infrastructure.
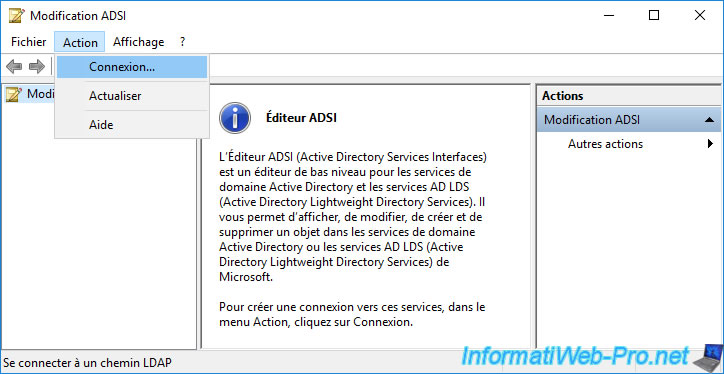
To verify this, you can use the "ADSI Edit" console of your Active Directory domain controller.
In this console, go to the menu : Action -> Connect to.
In the "Connection Settings" window that appears, select the option "Select a well known Naming Context: Configuration" to explore the "Configuration" partition of your Active Directory infrastructure and click OK.
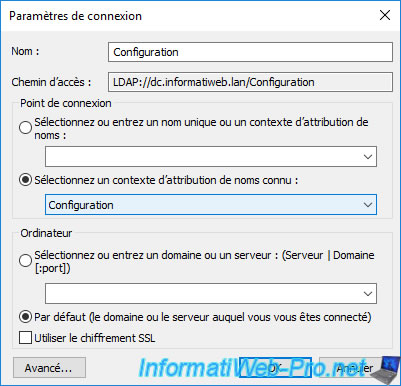
In the "Configuration" partition that is displayed, go to : CN=Configuration,DC=informatiweb,DC=lan\CN=Services\CN=Public Key Services.
As you can see, you will find the same folders (AIA, CDP, Certification Authorities, ...).
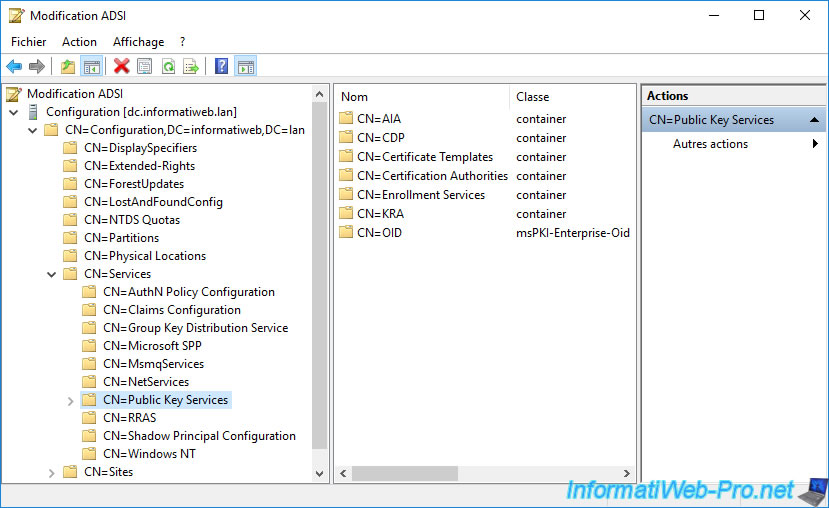
To get the LDAP path of your "Configuration" partition, you can right-click "Properties" on it, then view its "distinguishedName" attribute.
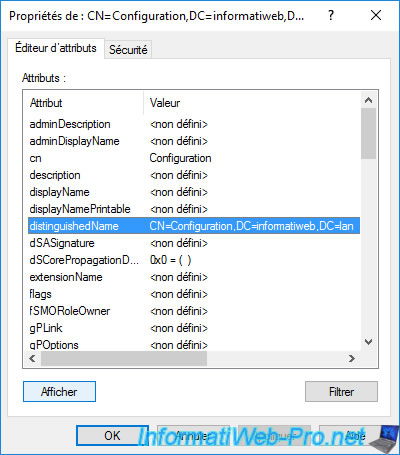
In the small window that appears, you will be able to select the displayed value to copy it.
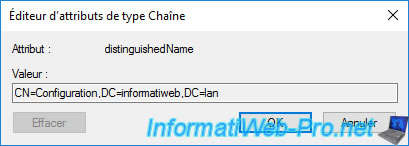
In order for your servers and clients to be aware of this standalone root CA, as well as these revocation lists, you must manually publish its information to your Active Directory infrastructure.
To do this, on your standalone root CA (root-ca), open a command prompt and run this command :
Batch
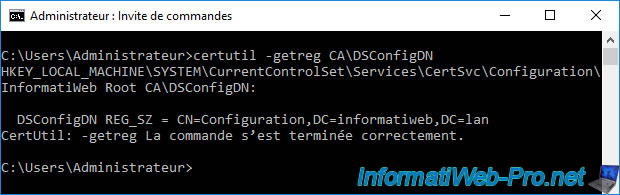
certutil -setreg CA\DSConfigDN CN=Configuration,DC=informatiweb,DC=lan
This command will let your CA know where to post their information.
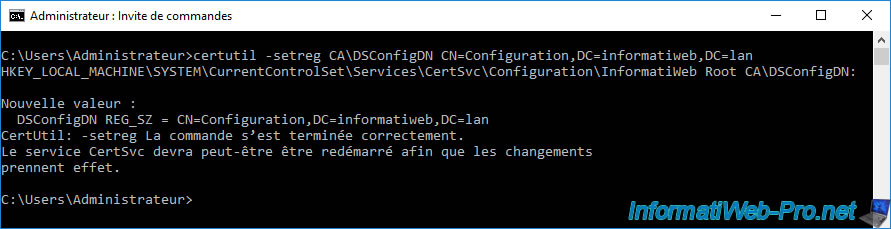
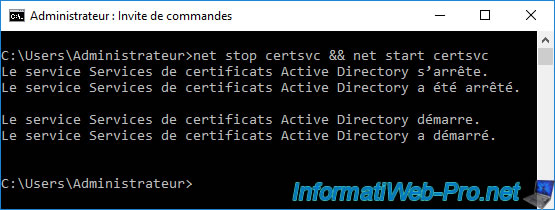
As indicated by the command run earlier, restarting the "CertSvc" service may be required.
To restart it, use the command :
Batch
net stop certsvc && net start certsvc
Once the "CertSvc" service has restarted, check that the modification has been taken into account by running this command :
Batch
certutil -getreg CA\DSConfigDN
6. Change the AIA and CDP publishing location of your standalone root CA
In the "Certification Authority" console of your standalone root CA, right-click "Properties" on its name.
Note : you will notice that certificate templates don't exist when you install a standalone CA.
Hence the fact that the "Certificate Templates" folder is not present here.
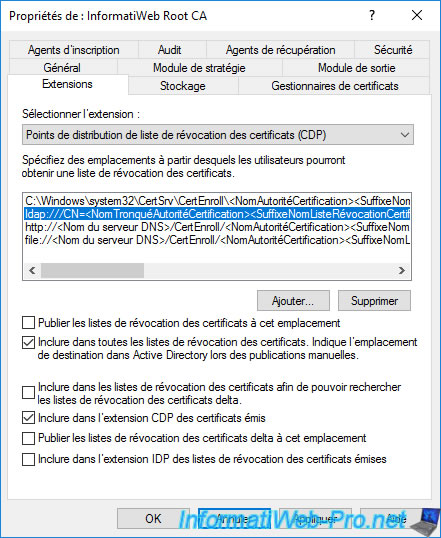
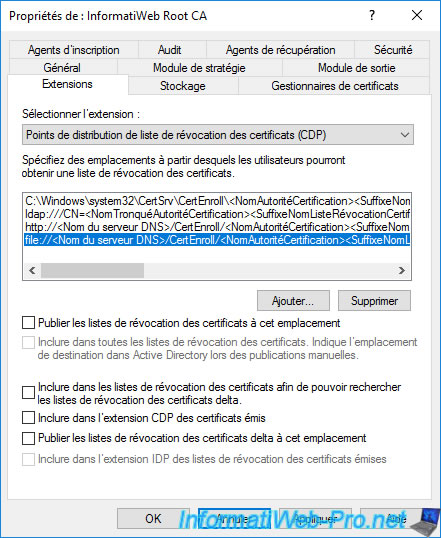
To get started, go to the "Extensions" tab and select the "CRL Distribution Point (CDP)" extension (if you haven't already).
Then, select the path "ldap://..." and check the boxes :
- Include in all CRLs. Specifies where to publish in the Active Directory when publishing manually.
- Include in the CDP extension of issued certificates.
This tells clients that this CA's revocation lists are available at this location in your Active Directory infrastructure.
Then, select the local path "file://..." and uncheck all the boxes.
Indeed, since a standalone root CA must be taken offline once your PKI infrastructure is installed correctly, this path will never be accessible.
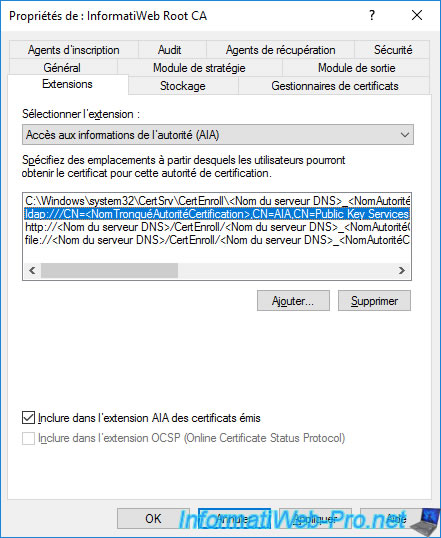
Now, select the "Authority Information Access (AIA)" extension and select the path "ldap://...".
Check the "Include in the AIA extension of issued certificates" box to indicate to your clients that your CA information resides here in your Active Directory infrastructure.
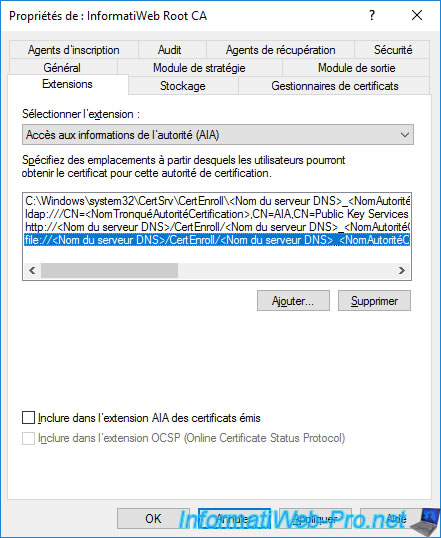
Then, select the "file://" path and uncheck "Include in the AIA extension of issued certificates" for the same reason as before (the standalone CA must be taken offline, so this path will not be never available).
Click OK to save changes.
Click Yes to restart Active Directory Certificate Services.
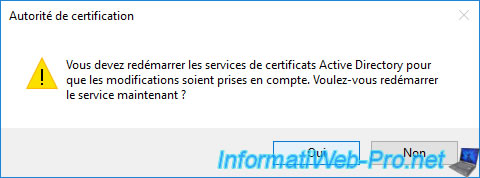
Your standalone root CA has been restarted.
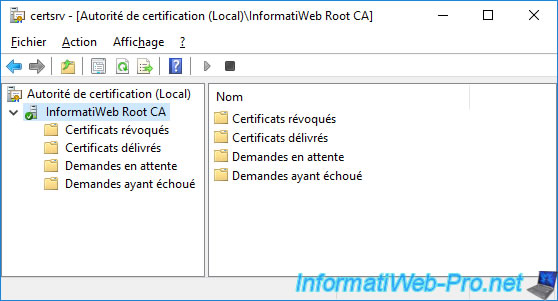
To start, publish a 1st revocation list by right-clicking "All Tasks -> Publish" on the "Revoked Certificates" folder.
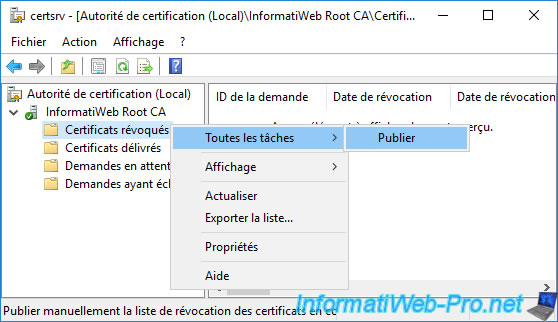
In the "Publish CRL" window that appears, select "New CRL".
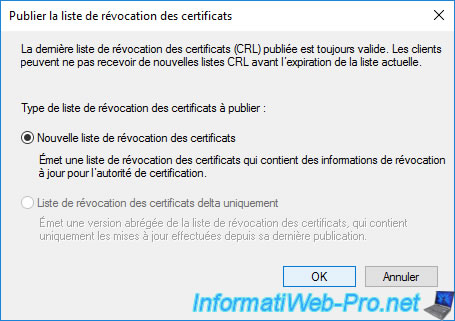
As you can see, by default, when you install a standalone root CA, only full revocation lists (CRLs) are published automatically.
Indeed, again, since a standalone root CA is expected to be taken offline for security reasons, there is no need to configure regular publication of delta revocation lists (delta CRLs).
Warning : the publication interval indicated here also corresponds to the frequency at which you will have to restart this standalone certification authority to publish its new revocation list in the Active Directory.
Indeed, once this period has elapsed, the revocation list downloaded by your clients will have expired. This means that your secondary CAs will also stop working.
Note : for this tutorial, we have left the default value. But, in enterprise, we recommend that you specify a longer publishing interval for this standalone root CA.
For example : 6 months or 1 year.
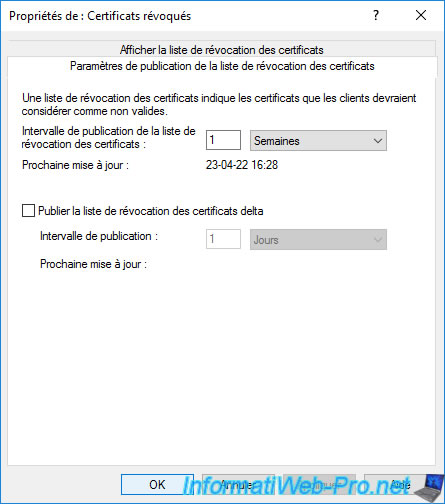
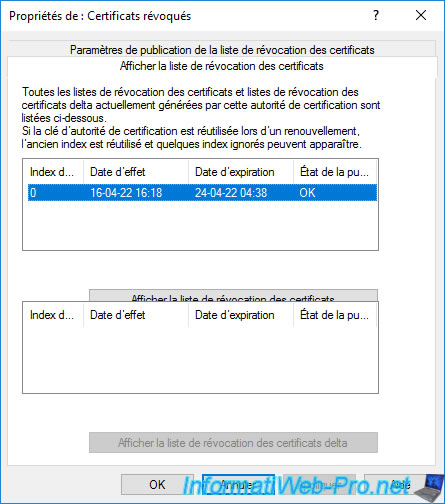
If you go to the "View CRL" tab, you will see that a revocation list has already been published.
This is obviously the one you just published manually. Although this revocation list is currently empty.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment