Create a DMZ and configure the pfSense 2.6 firewall
- Firewall
- pfSense
- 11 June 2025 at 07:59 UTC
-

- 2/2
4. Install a web server in the DMZ zone
For the example, we will install a web server and connect it to our DMZ zone.
For this, we installed a virtual machine on Windows Server 2016.
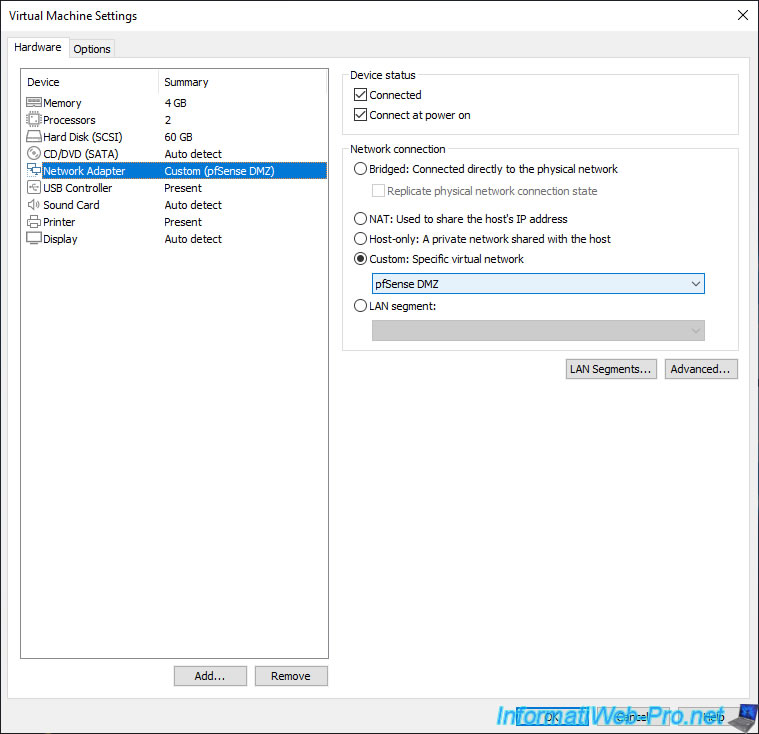
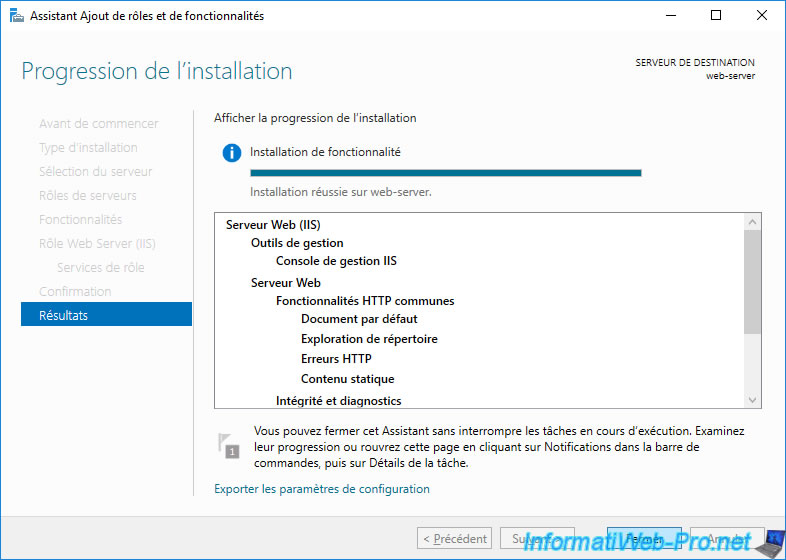
Open the Add Roles and Features Wizard from Server Manager and select: Role-based or feature-based installation.
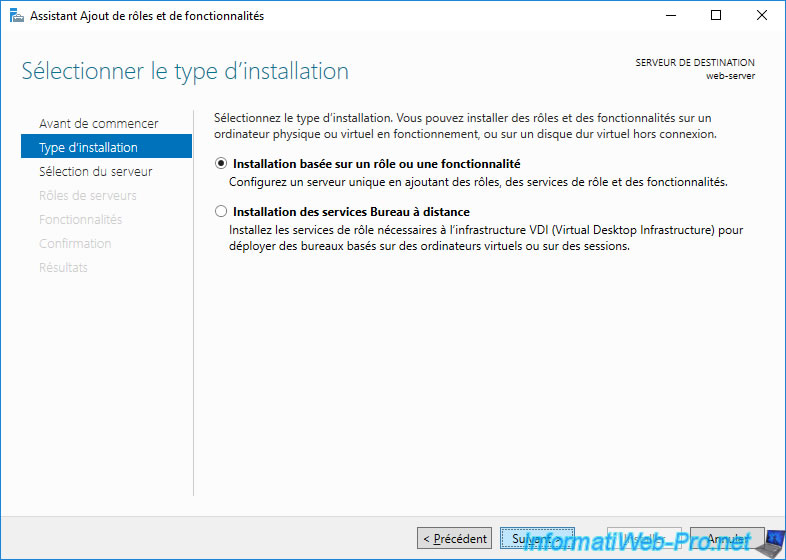
Check the "Web Server (IIS)" box and click Next.
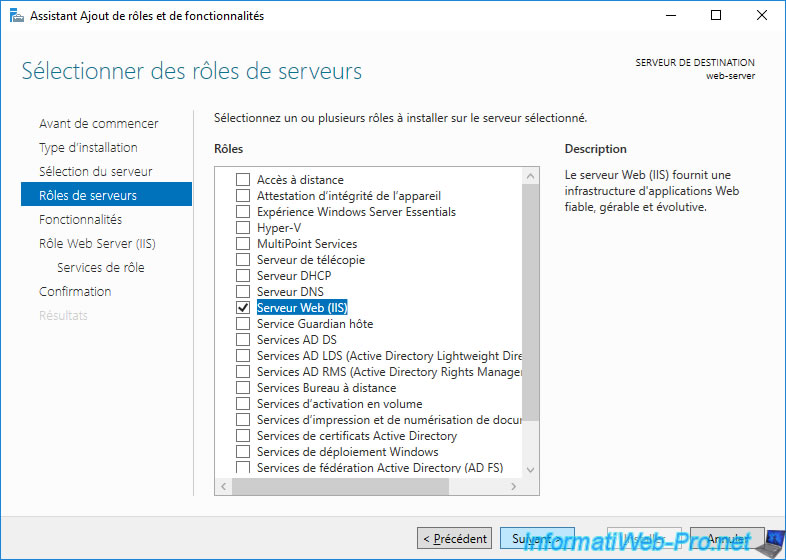
Click Install.
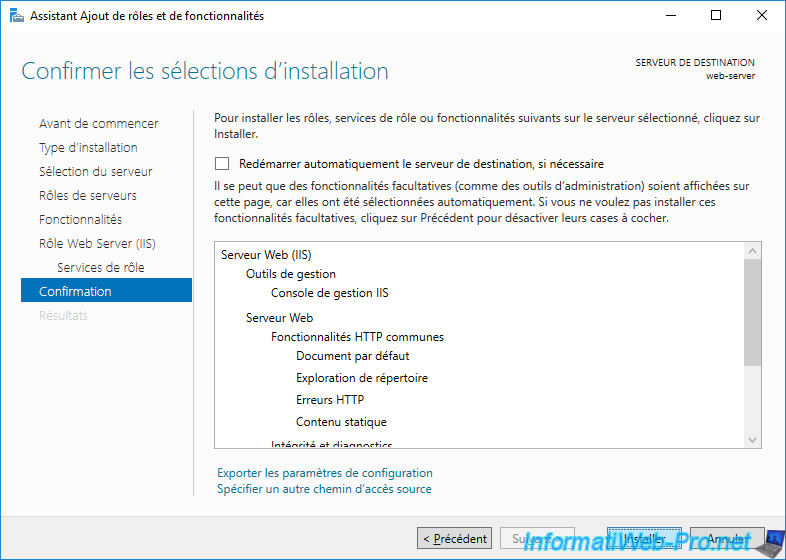
Once the web server is installed, click Close.
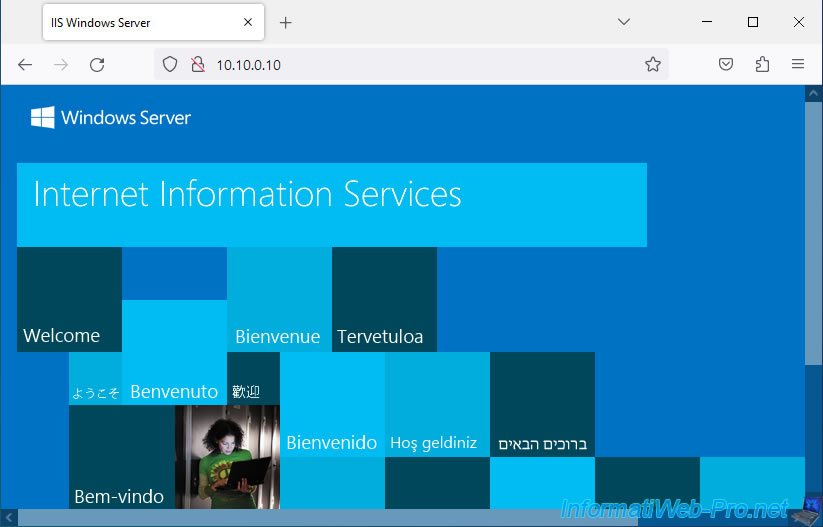
5. Testing access to the DMZ zone
From a client PC connected to the LAN network, you can easily access your web server present in the DMZ zone.
On the other hand, if you try to ping from a PC on the LAN network to your server in the DMZ zone, you will see that the ping does not work.
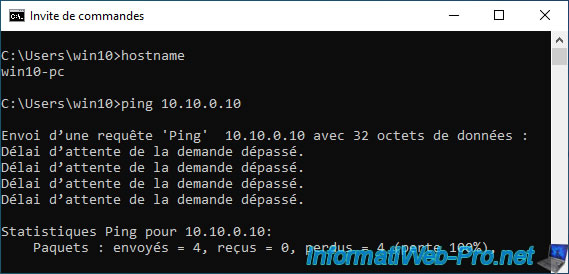
This is not caused by the DMZ, but by the Windows Server Firewall which blocks ping by default.
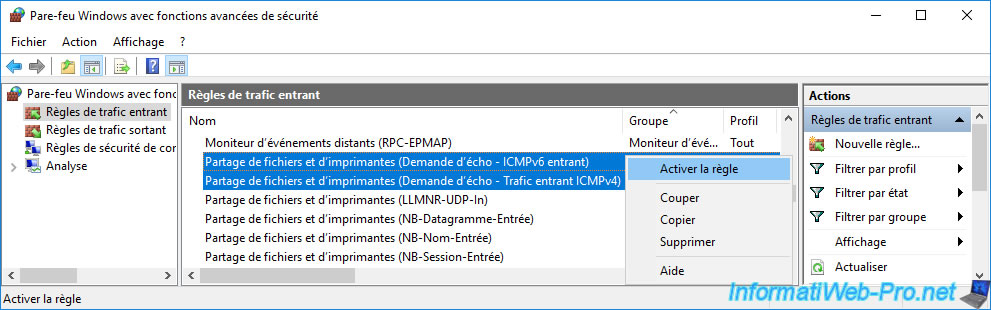
To authorize it, simply open the control panel and go to: System and security -> Windows Firewall -> Advanced settings.
Then, in the "Inbound Rules" section, allow these rules:
- File and Printer Sharing (Echo Request - ICMPv6-In)
- File and Printer Sharing (Echo Request - ICMPv4-In)
Then, you will see that your PC connected to the pfSense LAN network will be able to ping your DMZ server without any problem.
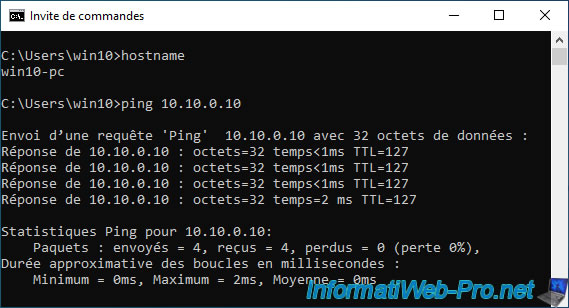
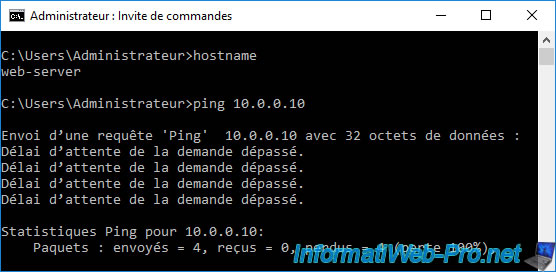
On the other hand, the reverse will not be possible.
6. Create a rule in the firewall to allow ping to the LAN network
So that your server located in the DMZ zone can ping a PC connected to the LAN network, you will need to create a new rule in the pfSense firewall.
To do this, go to: Firewall -> Rules.
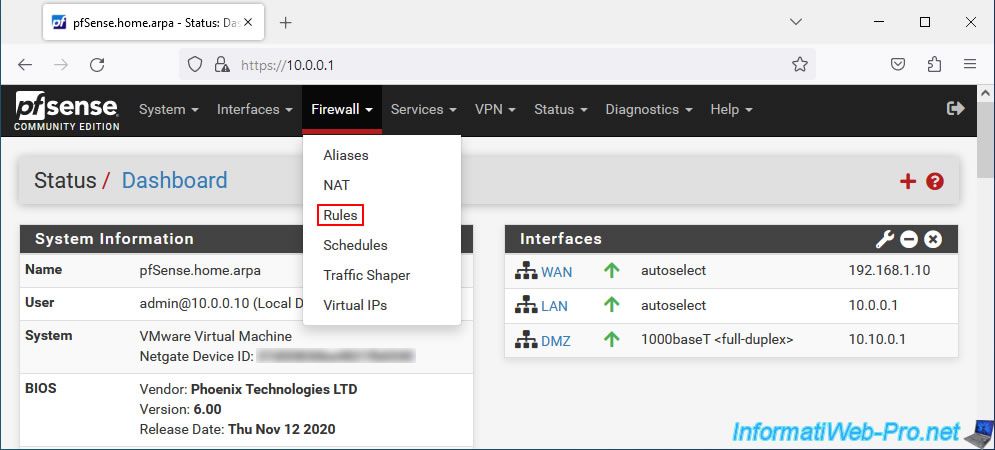
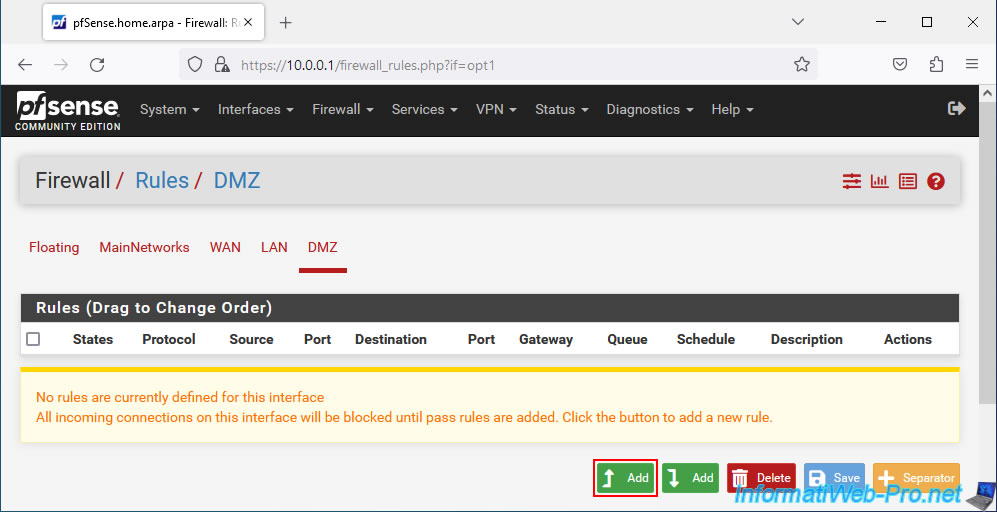
Next, go to the "DMZ" tab and click "Add".
Important : as you can see, by default, no rules are defined for this default "DMZ" interface.
Which means that all incoming connections are blocked until any rules allow incoming traffic on this interface.
On the "Edit Firewall Rule" page that appears, you will see that the "DMZ" interface is selected by default (since you are coming from the "DMZ" tab of the "Firewall" page).
To authorize IPv4 ping on this "DMZ" interface, select these options:
- Address Family : IPv4.
- Protocol : ICMP.
Using this "Edit Firewall Rule" form, you will be able to:
- Action: allows you to allow (Pass), block the packet without notifying the client or reject the packet by sending a packet back to the client indicating that it has been rejected.
- Disable: checking the "Disable this rule" box allows, as its name indicates, to deactivate this rule.
Which is useful in the event of a problem to test whether this or that firewall rule is causing the problem without deleting it. - Interface: pfSense network interface affected by this rule.
Example: WAN, LAN, OPT, DMZ or a group of interfaces previously defined via the "Interfaces -> Assignments -> Interface Groups" menu. - Address Family: allows you to create a rule for the IPv4, IPv6 protocol or both (IPv4+IPv6).
- Protocol: allows you to choose the protocol for which to authorize or block network traffic.
Examples:- TCP: for web servers (80/443), file servers (21), ...)
- UDP (for distribution of IP addresses via DHCP (67), TFTP servers (69), ...)
- TCP/UDP (for DNS domain name resolution (53), ...)
- ICMP (for ping), ...
- and much more: ESP, IGMP, ...
- ICMP Subtypes: if you have selected the "ICMP" protocol, you will see this option appear.
By default, all ping types are allowed (any). But you can also choose to only allow or block specific types of ping requests/responses.
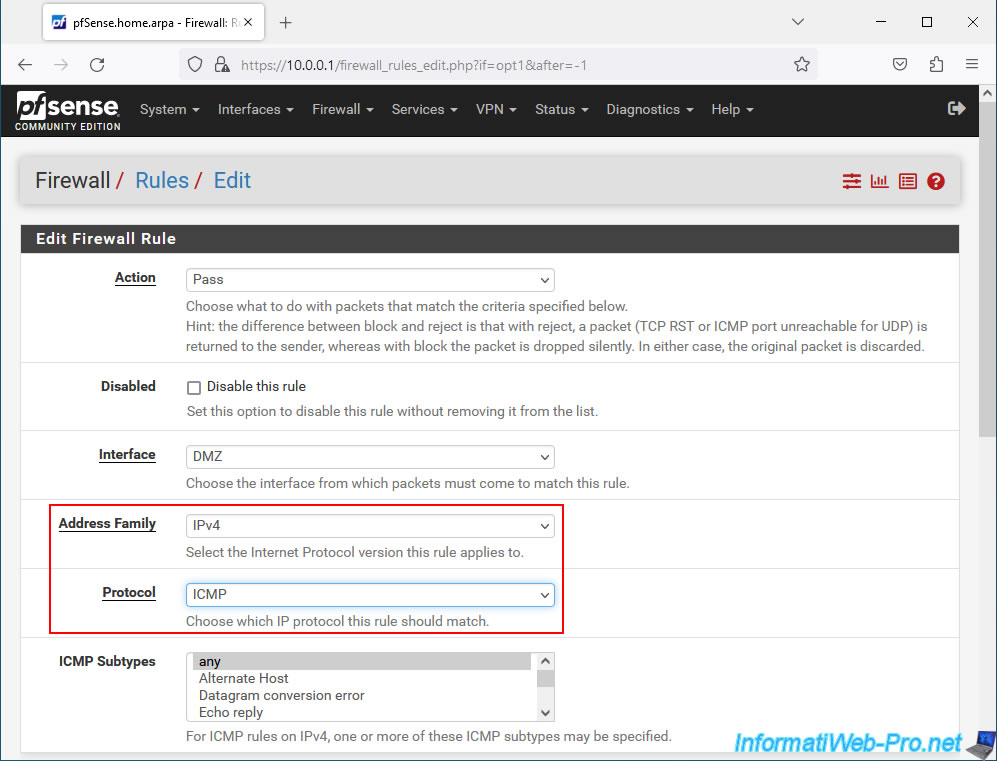
To authorize ping from a server in the "DMZ" zone to a PC connected to the "LAN" network, select:
- Source : DMZ net.
- Destination : LAN net.
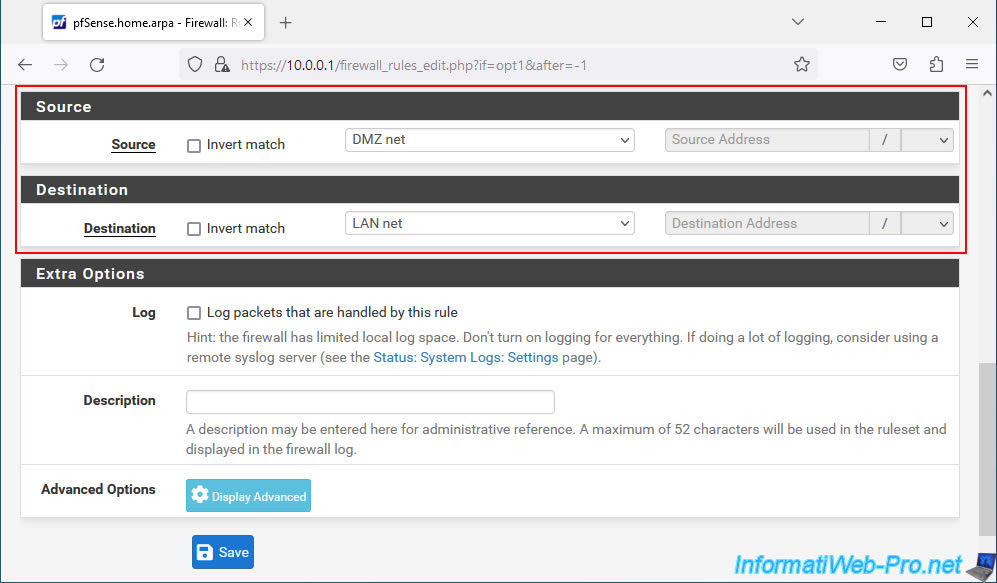
Here is what these options are for:
- Source: allows you to specify a host, a specific network, or the IP address of a pfSense network interface as the source for this firewall rule.
- any: anyone as a source.
- Single host or alias: allows you to target a specific host using its IP address.
- Network: allows you to target a subnet by specifying an IP address and the associated subnet mask.
- PPPoE clients: indicates that the source must correspond to PPPoE clients.
- L2TP clients: same, but for clients connected via the L2TP protocol.
- WAN net: allows you to target devices on the WAN network, as well as alias virtual IP addresses that would be different from the subnet used on the WAN network.
- WAN address: allows you to indicate that the source must be the IP address of the pfSense WAN interface.
- LAN net: same as "WAN net", but for the LAN network.
- LAN address: same as "WAN address", but for the LAN network.
- DMZ net: same as "WAN net", but for the LAN network.
- DMZ address: same as "WAN address", but for the LAN network.
- Destination: allows you to specify a host, a specific network, or the IP address of a pfSense network interface as the destination for this firewall rule.
Note: the options available are the same as for the source.- The "Invert match" box allows you to invert the match with the selected option.
That is, this will target anything that does not match the selected option in the list.
- The "Invert match" box allows you to invert the match with the selected option.
- Extra Options:
- Log: allows you to log all traffic matching this rule.
This can help to understand why certain packets are blocked or not in certain cases. - Description: allows you to indicate a purely indicative description which will be displayed for this rule in the pfSense web interface.
- Advanced Options: allows you to specify many additional options such as: the source operating system, the maximum number of connections per host (TCP only), specify specific TCP flags, ...
To learn more about these advanced options, see the official pfSense documentation cited below.
- Log: allows you to log all traffic matching this rule.
Click "Save" to save this new firewall rule.
Source : Configuring firewall rules | pfSense Documentation.
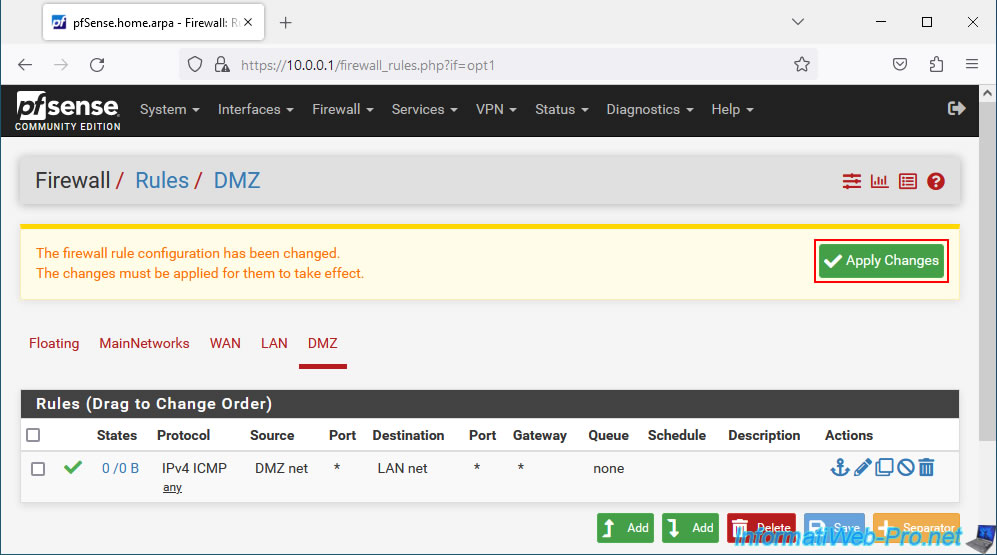
When you create or modify a firewall rule, a warning will appear telling you that the configuration has been modified and that you need to apply the changes.
Click: Apply Changes.
Plain Text
The firewall rule configuration has been changed. The changes must be applied for them to take effect.
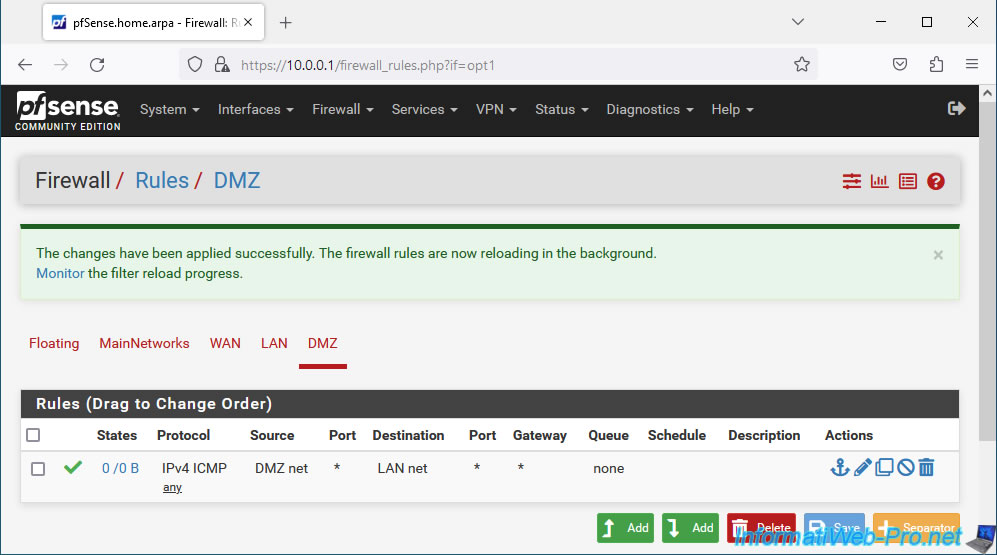
The changes have been applied. However, note that there may be a slight delay between the application of the changes and the use of these new rules as indicated by the message which appears in green.
This is because the new rules are being reloaded in the background.
Plain Text
The changes have been applied successfully. The firewall rules are now reloading in the background. Monitor the filter reload progress.
If you try to ping a PC on the LAN network from your server located in the "DMZ" zone, you will see that the ping does not work at the moment.
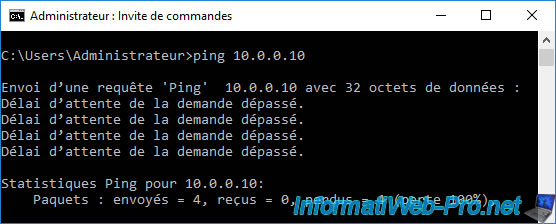
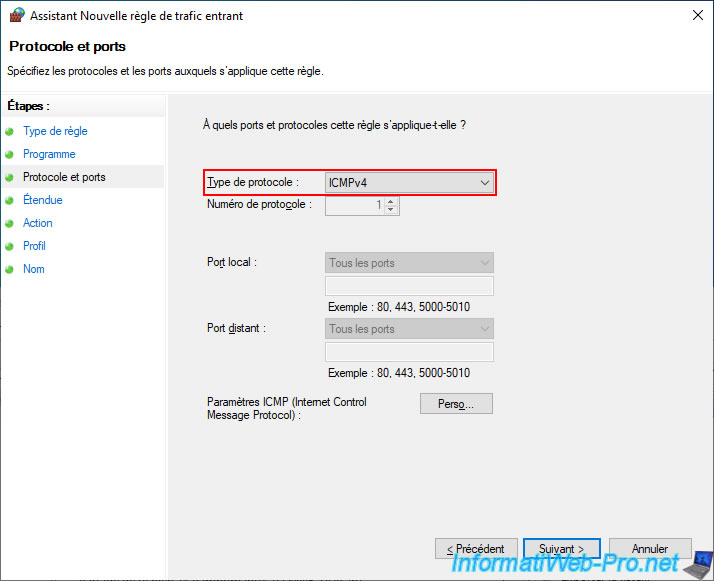
To do this, on your LAN PC, create a new incoming traffic rule in the Windows firewall and authorize the "ICMPv4" protocol (to authorize ping via an IPv4 network).
If necessary, refer to our tutorial: Configure the firewall of your computer.
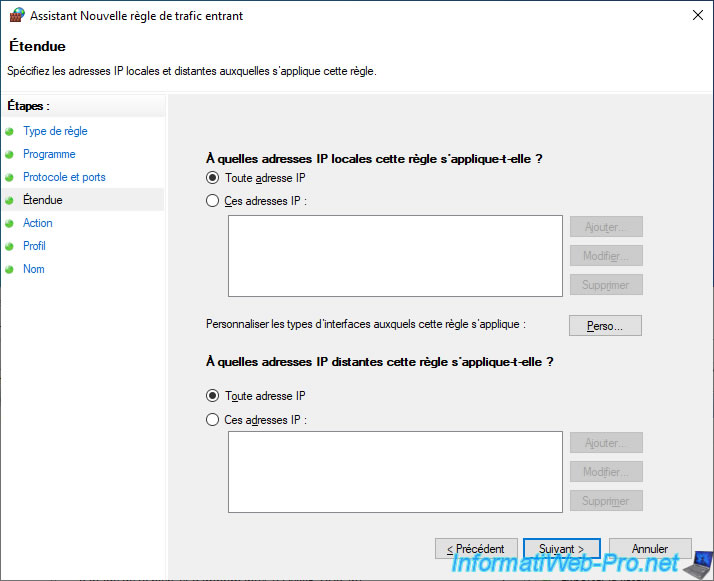
For source and remote IP addresses, leave the "Any IP address" option selected.
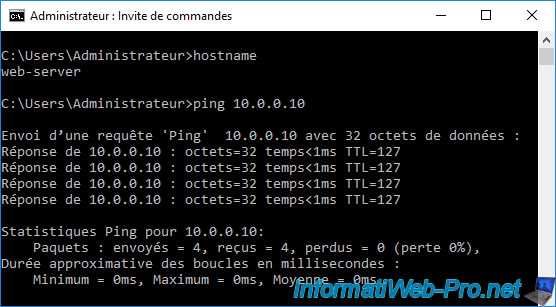
Now, ping from a server in the DMZ to your PC connected to the LAN network works.
Share this tutorial
To see also
-

Firewall 5/28/2025
pfSense 2.6 - Create and use VLANs
-

Firewall 6/6/2025
pfSense 2.6 - DDNS (dynamic DNS)
-

Firewall 5/17/2025
pfSense 2.6 - Enable SSH protocol
-

Firewall 8/29/2025
pfSense 2.6 - Implement Multi-WAN (Dual-WAN)

No comment