Secure access to VMware vCenter Server (VCSA) over HTTPS on VMware vSphere 6.7
- VMware
- 25 October 2024 at 11:03 UTC
-

- 7/7
15. Trust SSL certificates issued by the VMCA certificate authority
If you want your client computers and/or servers to be able to trust certificates issued by your VMCA certificate authority, you will need that certificate authority's certificate.
To do this, simply access the address: https://vcsa.informatiweb.lan/certs/download.zip.
A "download.zip" file will be offered for download.
Unzip the "download.zip" file downloaded from your VCSA server and go to the folder: download/certs/win.
In this folder you will find:
- several security certificates in ".crt" format
- a certificate revocation list in ".crl" format
The exported certificates correspond to the certificate authorities that your VCSA server trusts.
These certificates correspond to those found in the "Trusted Root Certificates" section of the "Certificate Management" page of your VCSA server.
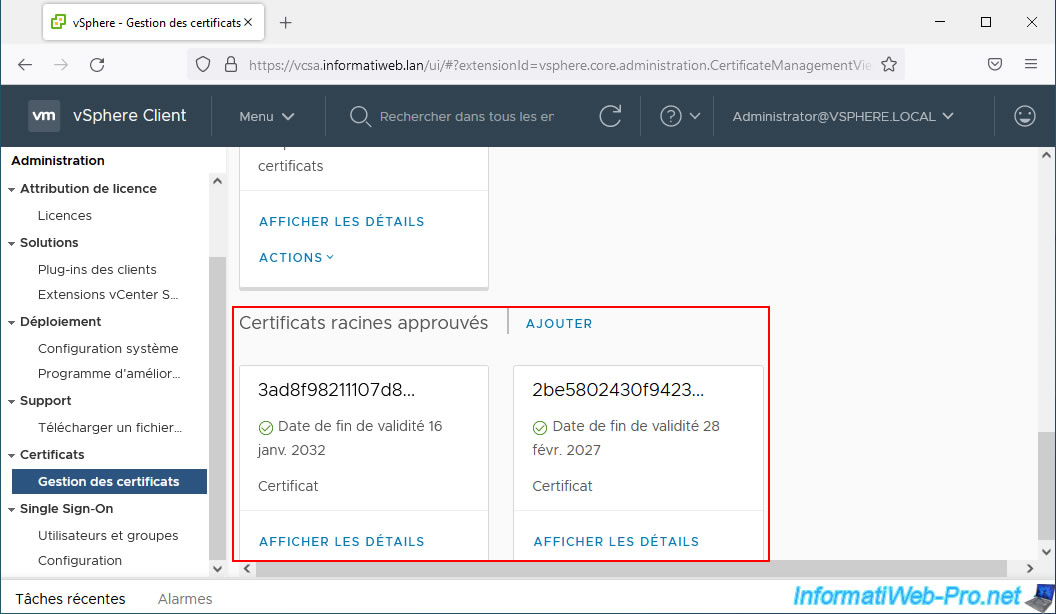
In our case, we find the certificate of our root certification authority "InformatiWeb CA" which our computer already trusts.
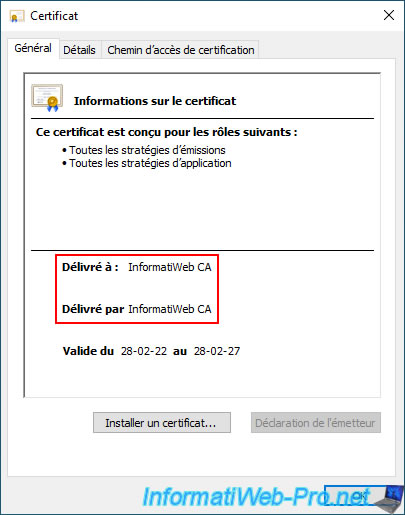
You will also find the certificate of your VMCA certification authority so the name displayed is "CA" and which your computer does not trust by default.
Hence the error that appears for this one.
Plain Text
This CA Root certificate is not trusted. To enable trust, install this certificate in the Trusted Root Certification Authorities store.
To have only this computer trust certificates issued by this VMCA certificate authority, click: Install Certificate
Otherwise, for several computers and/or servers to trust the certificates issued by this VMCA certification authority, use group policies as explained later in this tutorial.
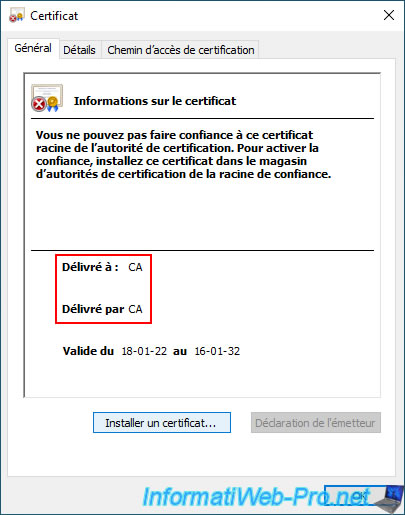
If you clicked on "Install Certificate", the Certificate Import Wizard will appear.
Click Next.
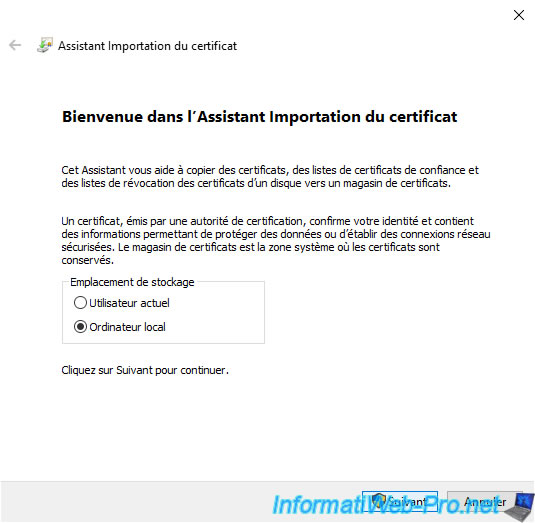
Make sure this certificate will be placed in the certificate store: Trusted Root Certification Authorities.
Otherwise, click "Browse" and select it.
Then click Next.
To finish, click Finish.
The message "The import was successful" appears.
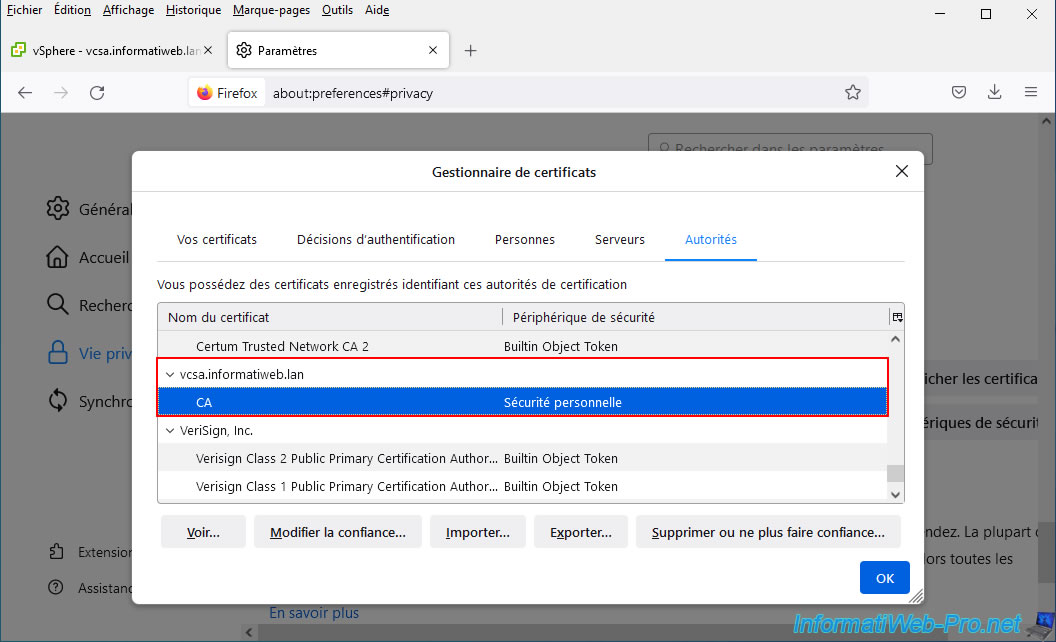
Important : if you use the "Mozilla Firefox" web browser, you will also need to import this certificate into its certificate manager.
Indeed, as explained previously, this web browser uses its own certificate store. Unlike Google Chrome, Microsoft Edge and Internet Explorer which uses that of Windows.
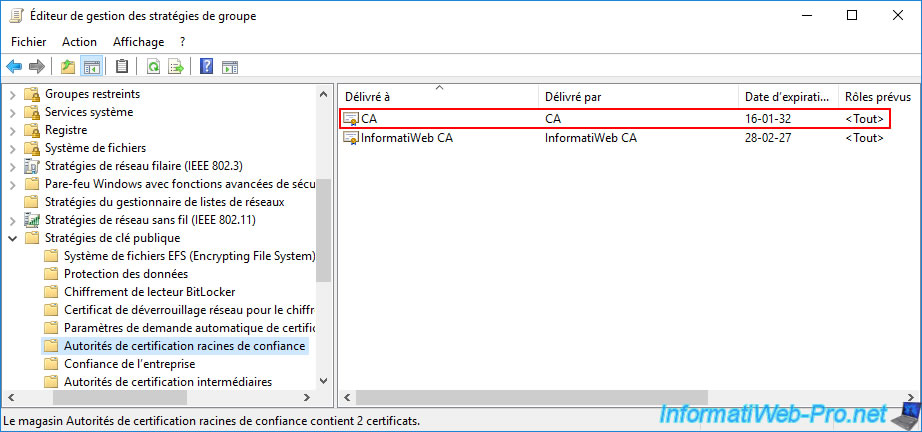
If you want all your computers and/or servers to be able to trust the certificates issued by this VMCA certification authority, you will need to add it to their "Trusted Root Certification Authority" certificate store using group policies. (GPOs).
To do this, refer to the step "Distribute the certificate to the Active Directory clients" of our tutorial "WS 2012 / 2012 R2 - Create an enterprise root CA".
As you can see, the VMCA certificate authority certificate will appear under the name "CA".
16. VMware ESXi host certificates considered valid
Once the VMCA certificate authority certificate has been imported into the certificate store of your computer and Mozilla Firefox (if applicable), relaunch your favorite web browser and attempt to access one of your VMware ESXi hosts linked to your VCSA server.
As you can see, no warnings will be displayed and the connection will be considered secure.
Important : if you have chosen to distribute the VMCA certificate using group policies, you will first need to force the group policies to be updated (via a "gpupdate /force") on your computer for the certificate to be added to the certificate store on your computer or server.
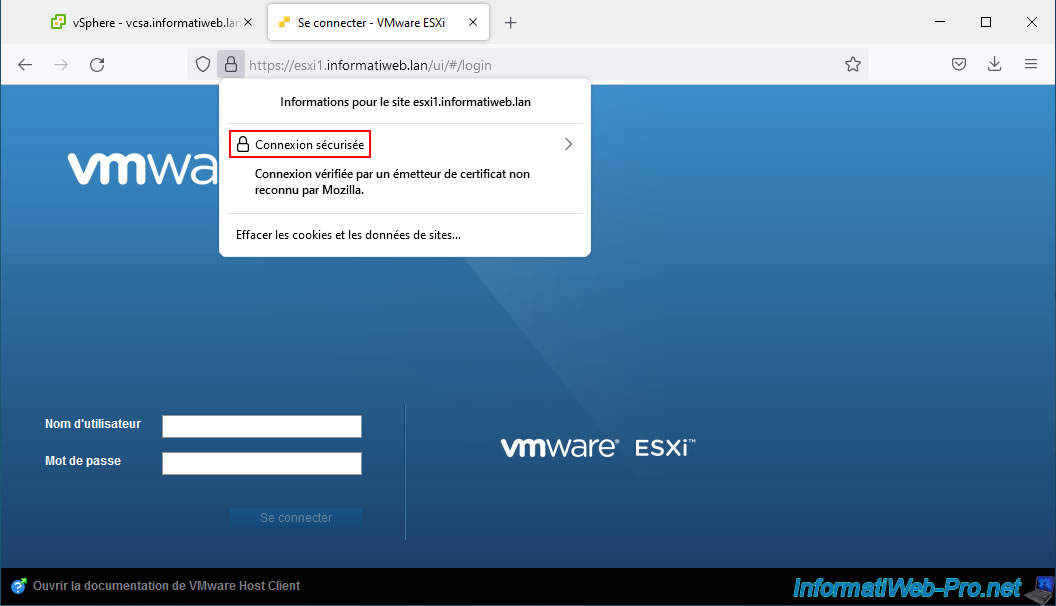
As you can see, the certificate used on the desired VMware ESXi host has been verified by your VCSA server (in our case: vcsa.informatiweb.lan).
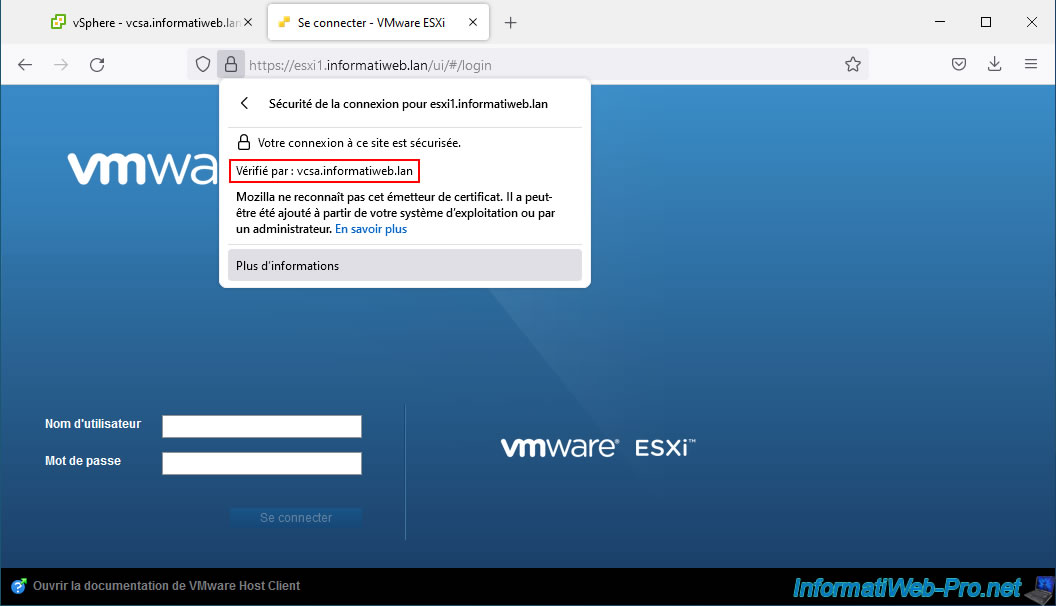
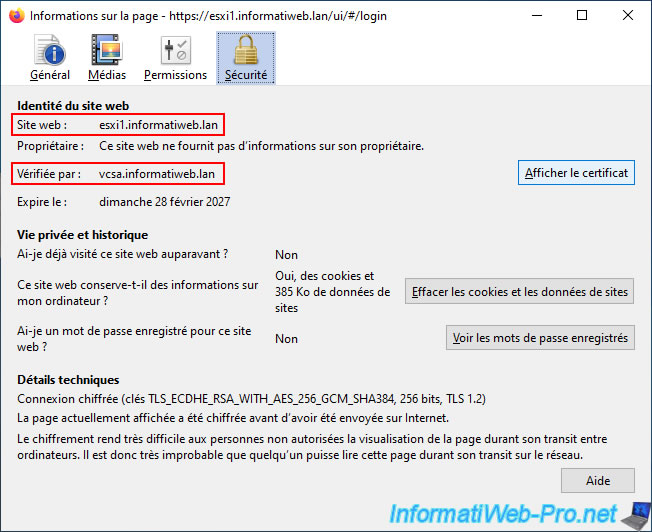
If you click on "More information" (on Mozilla Firefox), you will see that the website identity is "esxi1.informatiweb.lan" (in our case) and that it has been verified by "vcsa.informatiweb.lan".
Click "View Certificate" for more information.
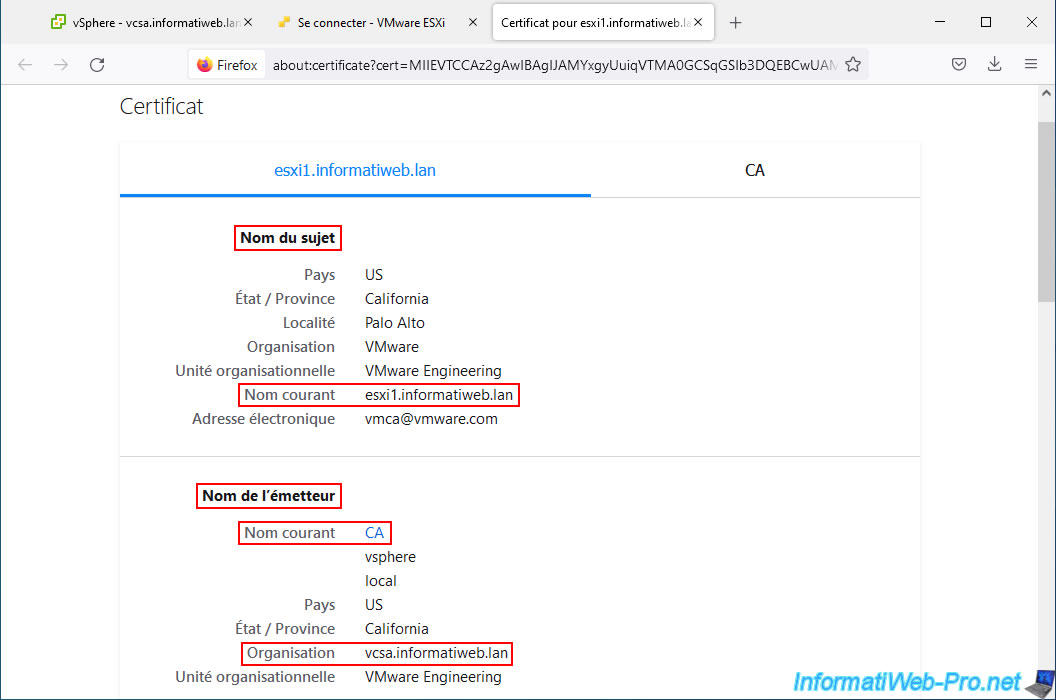
As you can see, the certificate for your VMware ESXi host was issued by the VMCA certificate authority (vsphere local CA).
Note that in business, it is very rare to directly access a VMware ESXi host when you have a VMware vSphere virtual infrastructure. In fact, you manage these centrally via the VMware vSphere Client of your VMware vCenter Server (VCSA).
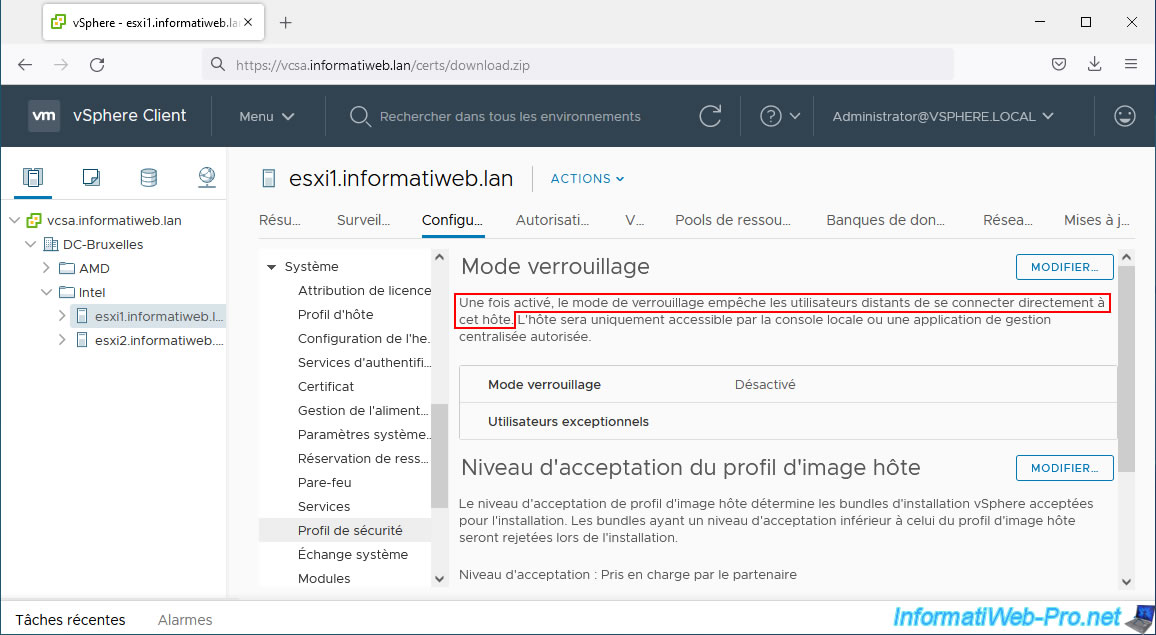
This is why VMware created a locking mode that allows you to block direct access to a VMware ESXi host from its web interface, as well as from its DCUI (Direct Console User Interface) console. if you wish it.
Rather than configuring your computers and servers to trust the VMCA certification authority used by your VMware vSphere virtual infrastructure, you should therefore configure the locking mode in normal or even strict mode (depending on the security policy of your business).
So, since access from the web interface of your VMware ESXi hosts will be blocked, there will be no point in adding this trust to this VMCA authority.
From the VMware vSphere Client, you can configure this locking mode on a VMware ESXi host by selecting the desired host, then going to: Configure -> System -> Security Profile.
Next, click the "Edit" button to the right of "Lockdown Mode".
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

No comment