Secure access to VMware vCenter Server (VCSA) over HTTPS (in a multi-site infrastructure) on VMware vSphere 6.7
- VMware
- 06 November 2024 at 14:42 UTC
-

- 4/4
12. VMware ESXi host SSL certificates considered invalid
If you select one of your VMware ESXi hosts and go to "Configure -> System -> Certificate", you will see that its certificate comes from a certificate authority "CA" belonging to the domain "vsphere.local" (the domain SSO used on your VMware vCenter infrastructure).
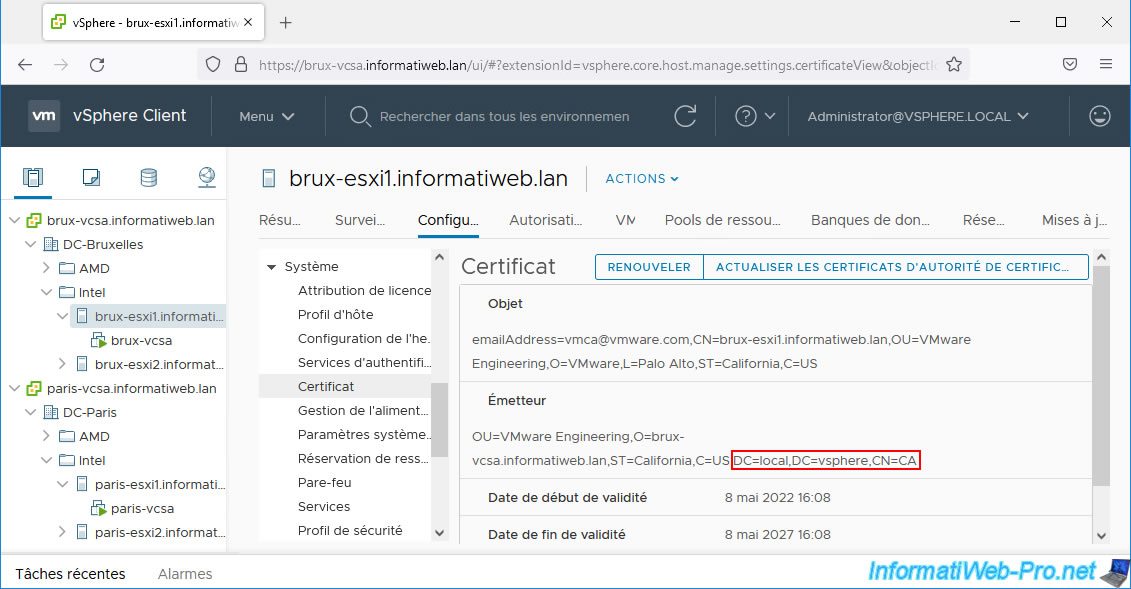
If you attempt to directly access one of your VMware ESXi hosts, you will notice that your web browser displays a warning because the issuer of its certificate is unknown.
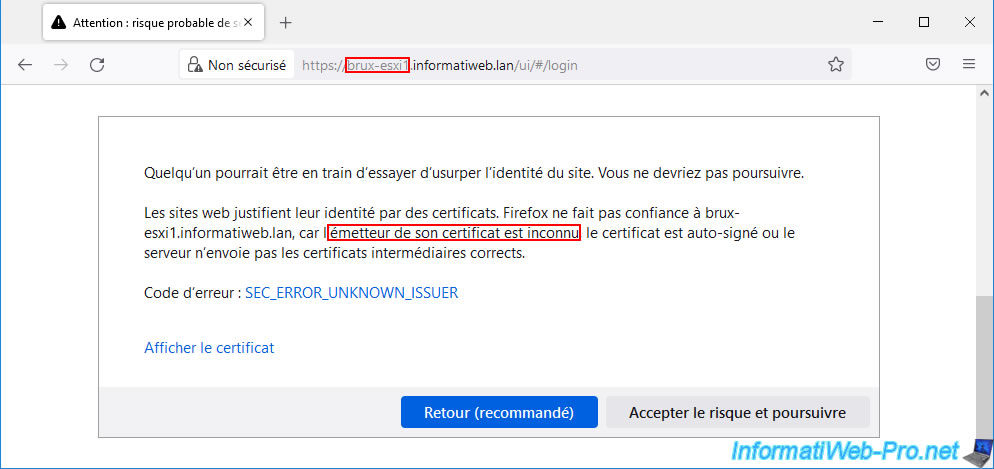
If you view the certificate used, you can see that it has been issued to your VMware ESXi host (in our case: brux-esxi1.informatiweb.lan).
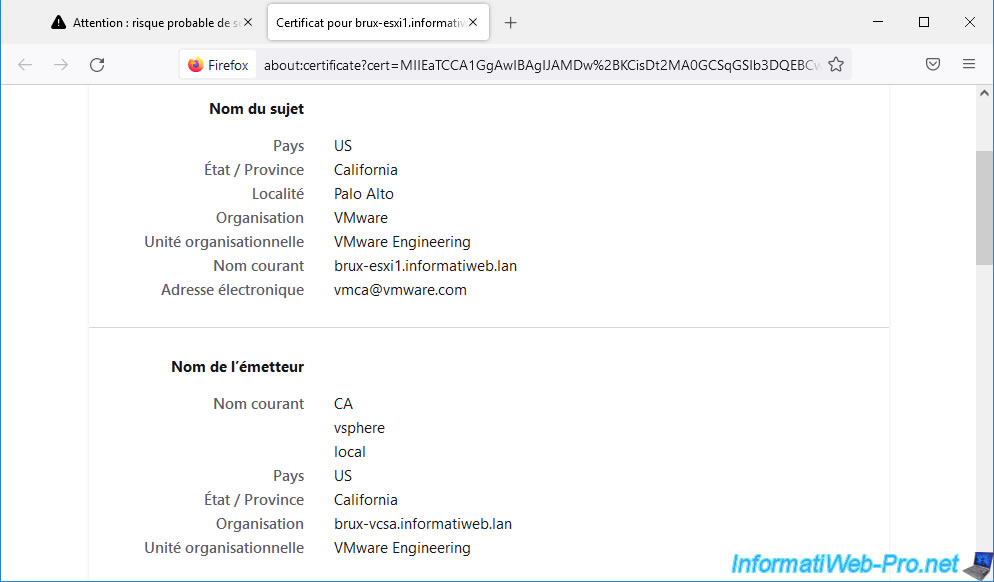
If you look at the email address listed in the subject, you can see that it refers to the VMCA certificate authority used by VMware vCenter Server (VCSA).
For the issuer, you can see that it is the "CA" certificate authority which is part of the "vsphere.local" domain (in other words: the SSO domain used by VMware vCenter Server (VCSA) and that The organization corresponds to the domain of your VMware vCenter Server (VCSA).
For your web browser, the certificate used therefore does not come from a valid certification authority (which in this case is the VMCA certification authority used internally by your VMware vCenter Server (VCSA)) given that it does not trust this certificate authority by default.
However, because this VMCA CA certificate is one of the certificates trusted by your VMware vCenter Server (VCSA), your VMware vCenter Server (VCSA) trusts this certificate when communicating with your VMware host ESXi.
13. Trust SSL certificates issued by the VMCA certificate authority
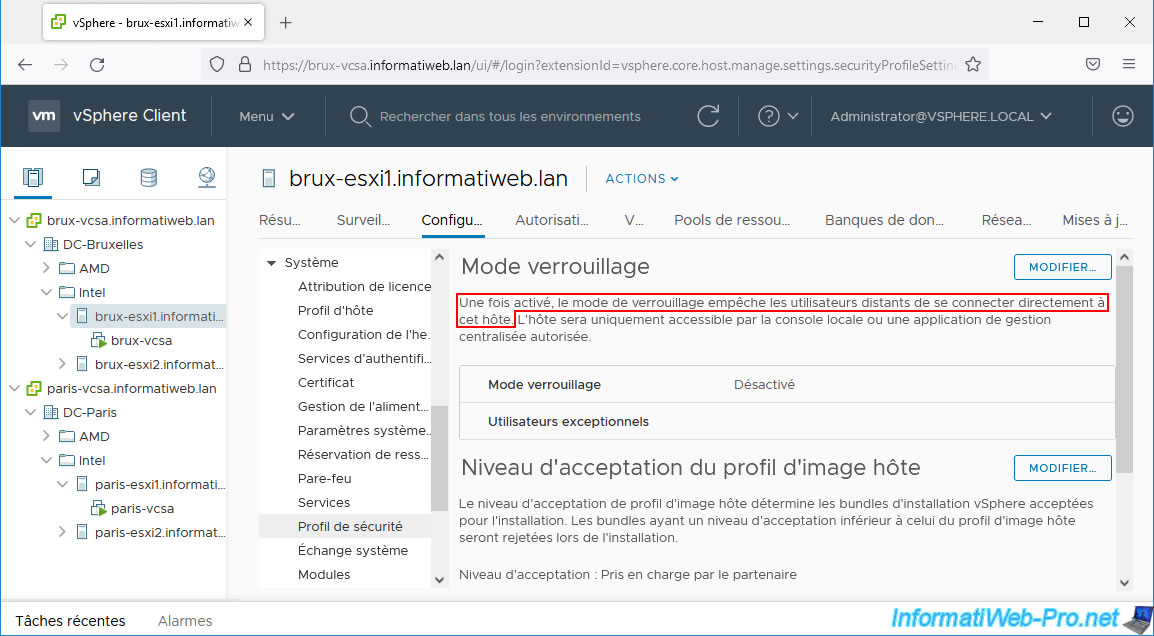
In business, it is very rare that you directly access a VMware ESXi host if it is linked to a VMware vCenter Server (VCSA).
Especially since direct access to a VMware ESXi host can very well be blocked thanks to the locking mode available on it.
However, if you want to be able to directly access your VMware ESXi hosts without this security warning, you can download your VMware vCenter Server's VMCA Certificate Authority (VCSA) certificate by navigating to "https: //[domain name of your vCenter server]/certs/download.zip".
Then, simply add the VMCA certificate to the trusted certification authorities of your computer or server, as well as to the Mozilla Firefox certificate store (if you use this web browser).
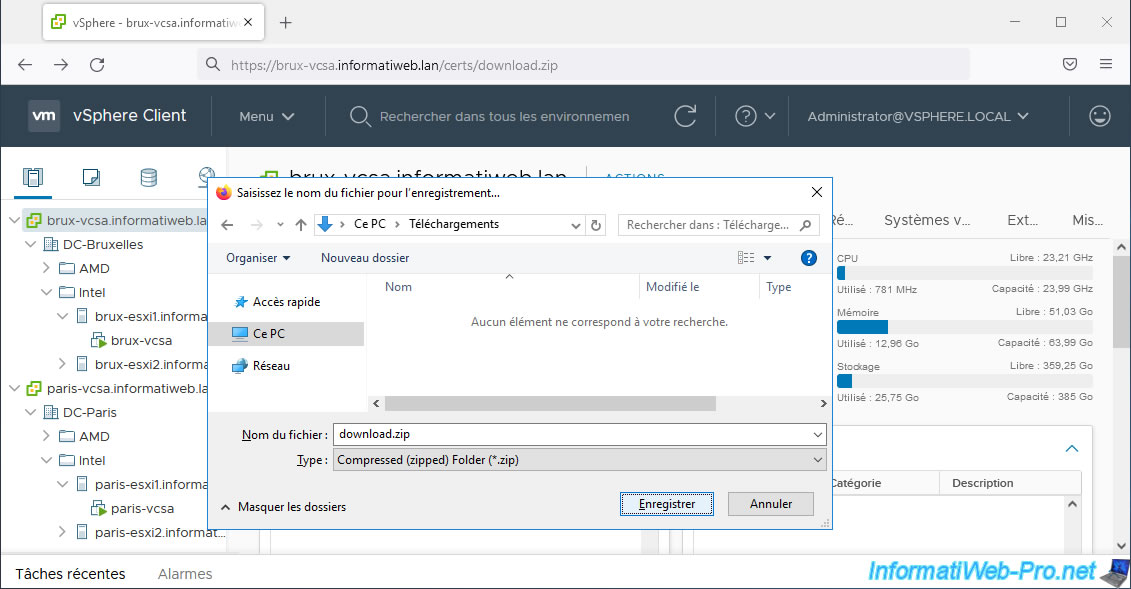
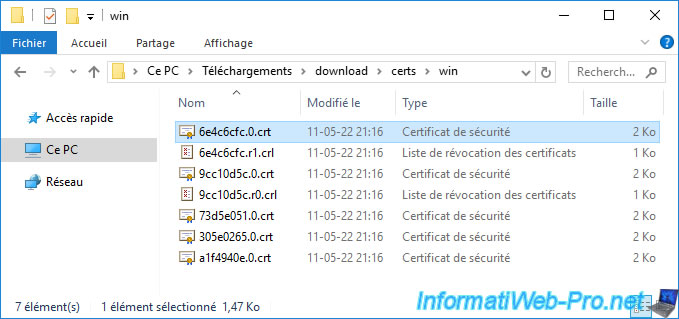
Unzip the downloaded “download.zip” file and go to the folder: download/certs/win.
In this folder, you will find:
- 2 certificates (.crt) with their corresponding revocation lists (.crl).
These are the certificates of the VMCA certification authorities of your different VMware vCenter Servers (VCSA) linked together using ELM mode. - certificates (.crt) from your own certification authorities (your root CA and its secondary CAs).
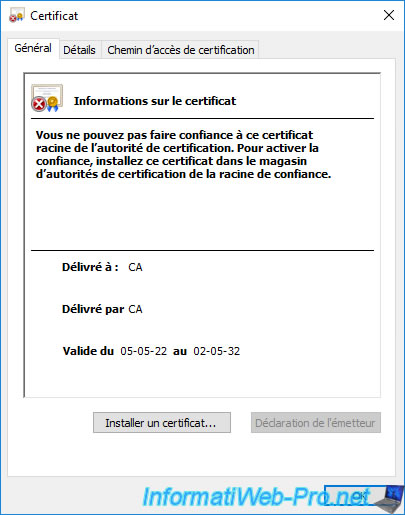
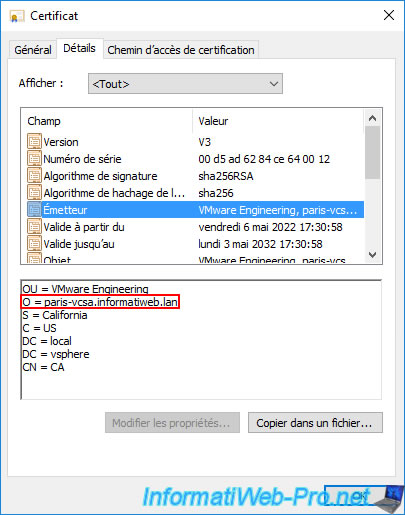
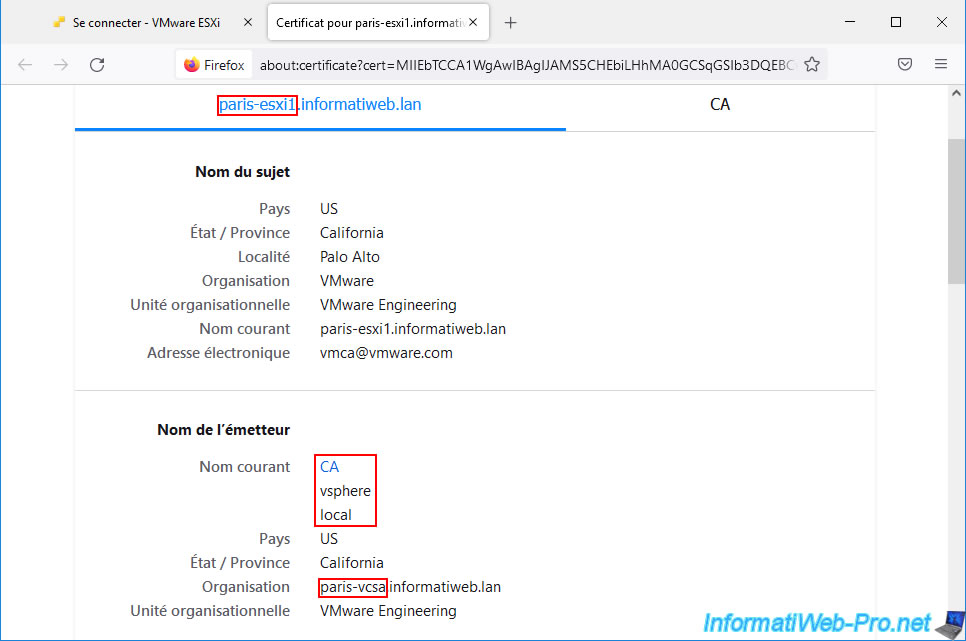
If you opened the certificate from one of your VMCA CAs, you will see that the certificate was issued to and by "CA".
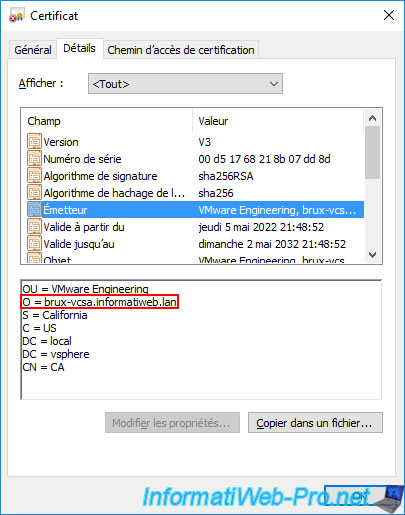
If you go to the "Details" tab and select the "Issuer" field, you will be able to find out which VMware vCenter Server (VCSA) server it corresponds to.
In our case, this first "CA" certificate corresponds to the "VMCA" certification authority of our "brux-vcsa" server.
If we open the 2nd certificate, we can see that it was also issued to and by "CA".
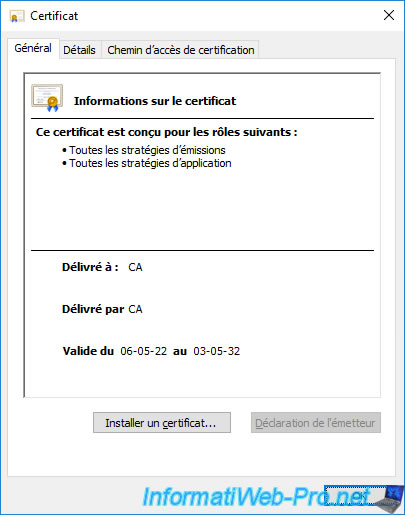
But if we look at its issuer, we can see that its issuer is our 2nd VMware vCenter Server (VCSA).
In this case: paris-vcsa.
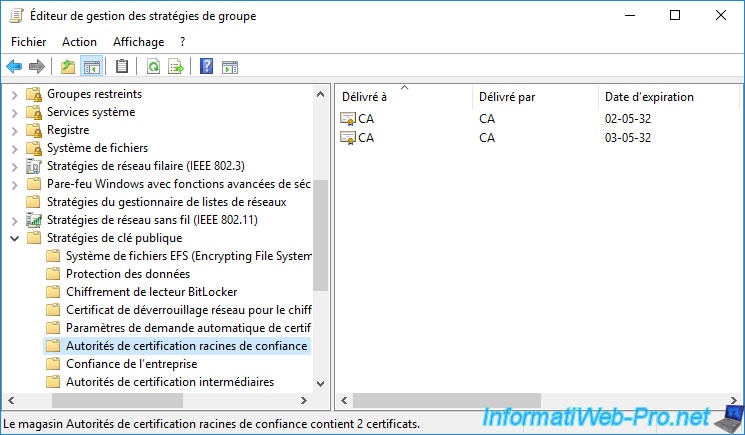
To trust your different VMCA certification authorities, you can manually install them in the "Trusted Root Certification Authorities" certificate store of your computer or server and opening the desired certificate, then clicking on the "Install" button a certificate".
However, you can also distribute it automatically to the various computers and/or servers in your company using group policies (GPOs) by following this: Distribute the certificate to the Active Directory clients.
14. VMware ESXi host certificates considered valid
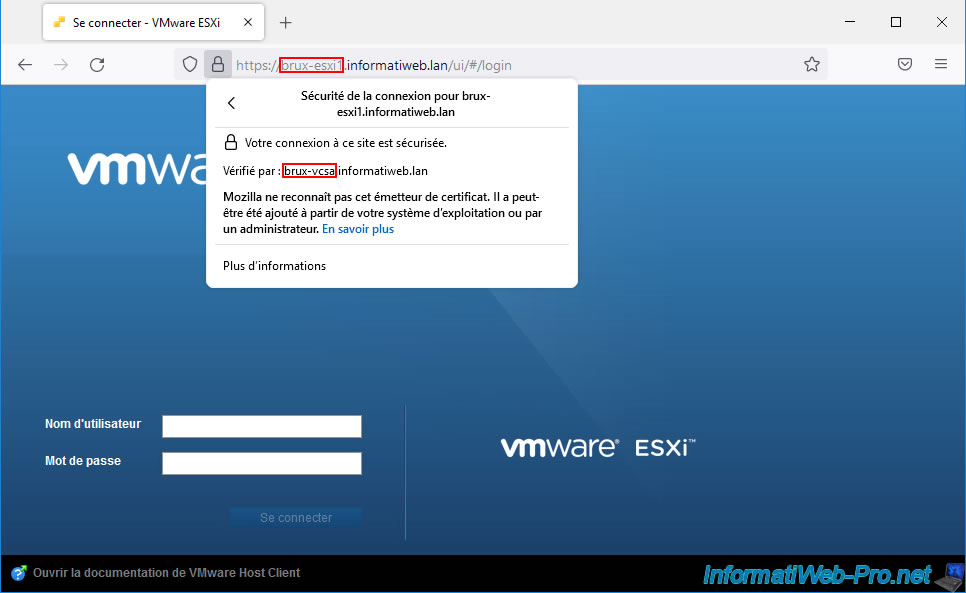
Once your VMCA CA certificate is part of your computer or server's trusted authorities (and Mozilla Firefox's certificate store, if applicable), navigate to your VMware ESXi host and you will notice that no security warning will not appear.
Additionally, if you click the padlock icon in the address bar, you will see that it has been verified by the VCSA server it is linked to.
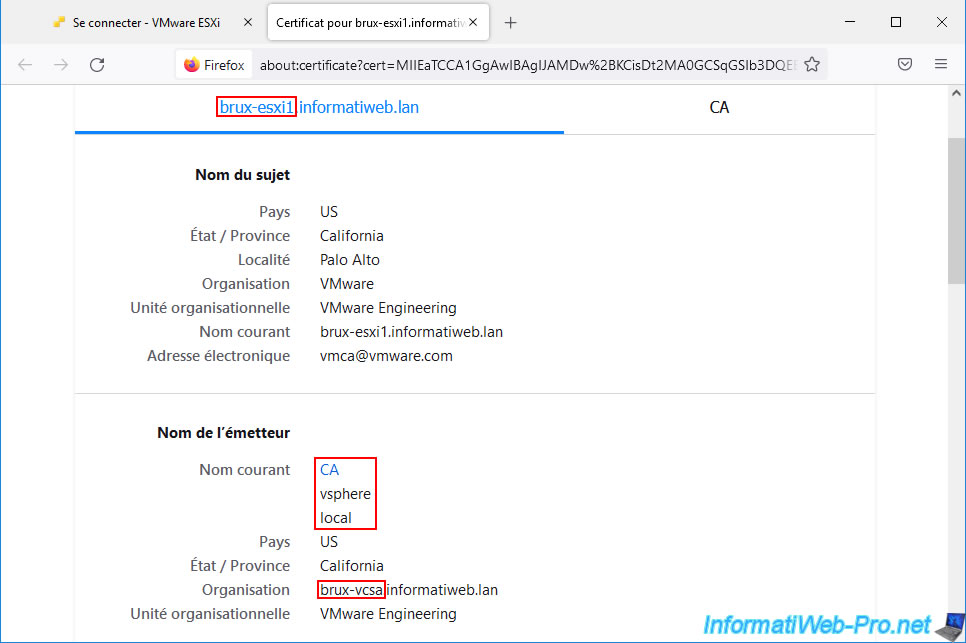
If you display the certificate used, you will see that it comes from the "local vsphere CA" certification authority (in other words: VMCA) and that it belongs to your VMware vCenter Server (VCSA).
In our case, the certificate of our host "brux-esxi1" was issued by the VMCA certification authority located on our server "brux-vcsa".
If you go to a VMware ESXi host on the remote site (in our case: that of Paris), you will see that its certificate has been verified by the remote VCSA server.
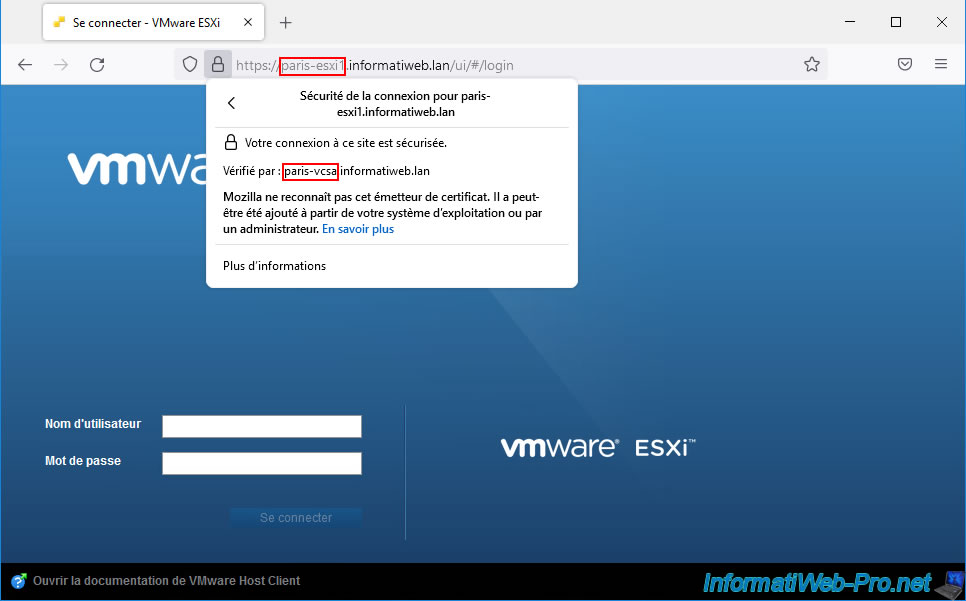
Once again the certificate comes from the "local vsphere CA" (VMCA) certification authority, but this time, it is that of your remote VCSA server (in our case: paris-vcsa).
However, as indicated previously, in business, it is very possible that you have activated the locking mode and that direct access to your VMware ESXi hosts is therefore no longer possible.
Share this tutorial
To see also
-

VMware 3/13/2024
VMware ESXi 6.7 - Synchronize the clock of ESXi hosts from a time server (NTP)
-

VMware 3/8/2024
VMware ESXi 6.7 - Synchronize the clock of VCSA from a time server (NTP)
-
VMware 7/31/2024
VMware vSphere 6.7 - Add an Active Directory identity source
-
VMware 5/22/2024
VMware vSphere 6.7 - Change default console

No comment