Install and configure an OCSP responder to manage certificate revocation on Windows Server 2016
- Windows Server
- 10 November 2023 at 12:13 UTC
-

- 4/4
7. Regenerate certificate : Certificate Authority Exchange (CAExchange)
If an error occurs accessing the OCSP location, the problem may simply be with the "Certificate Authority Exchange (CAExchange)" certificate that was enrolled (issued) automatically transparently.
Source : OCSP Responder - Error in pkiview.msc - Microsoft TechCenter.
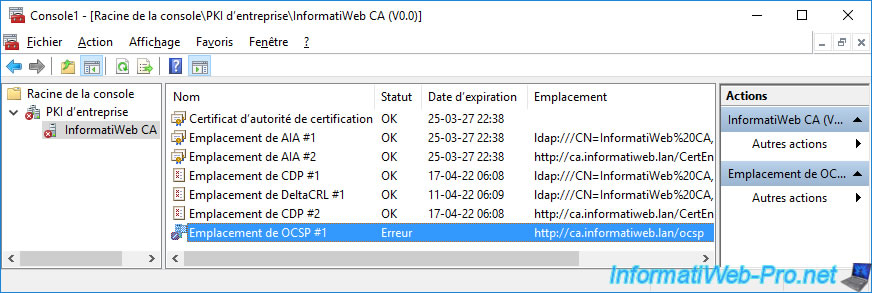
Indeed, if you open the "Certification Authority" console, you will see that a "Certificate Authority Exchange (CAExchange)" certificate has been issued.
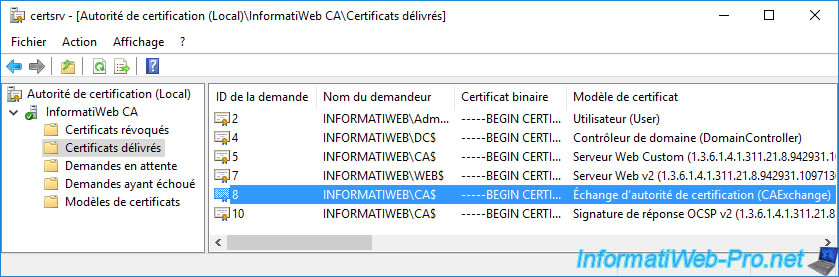
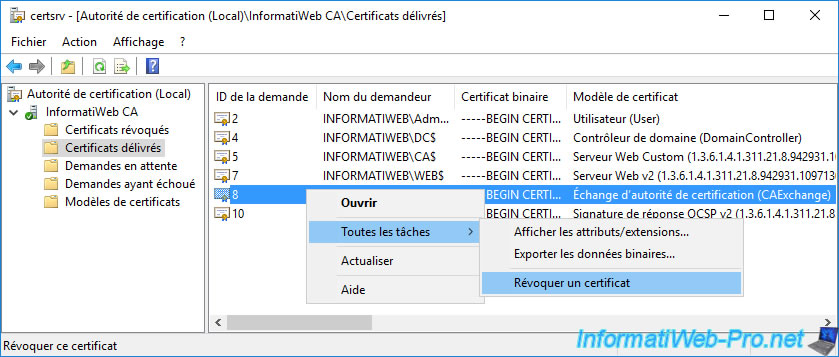
To solve the problem, simply revoke the existing one by right-clicking "All Tasks -> Revoke Certificate" on it.
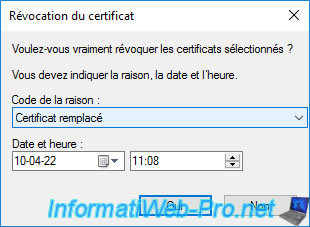
Select "Replaced certificate" as the revocation code (for example).
Then, generate a new Certificate Authority Exchange (CAExchange) certificate by running the following command :
Batch
certutil -cainfo xchg
Which will display this :
Plain Text
CA exchange cert[0]: -----BEGIN CERTIFICATE----- xxxxxxxxxxxxxxxxxxxxxxxxxxxx... -----END CERTIFICATE----- ...
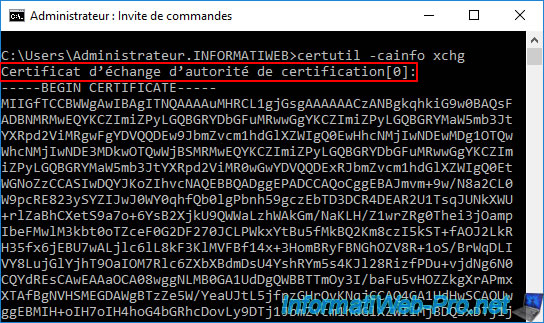
If you refresh the list of certificates issued on your certification authority, you will see that a new "Certificate Authority Exchange (CAExchange)" certificate has been issued.
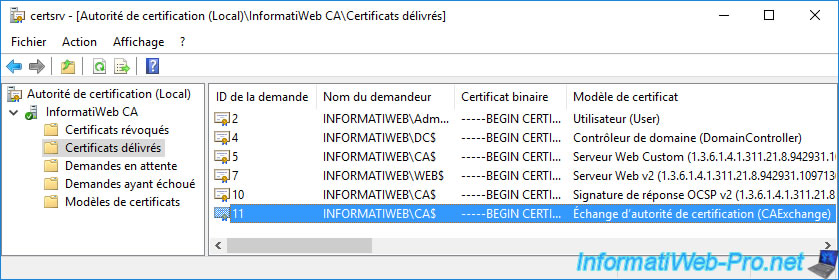
If you double-click on this certificate and select the "Authority Info Access" field, you will see that the information concerning the "OCSP" protocol has been added to it.
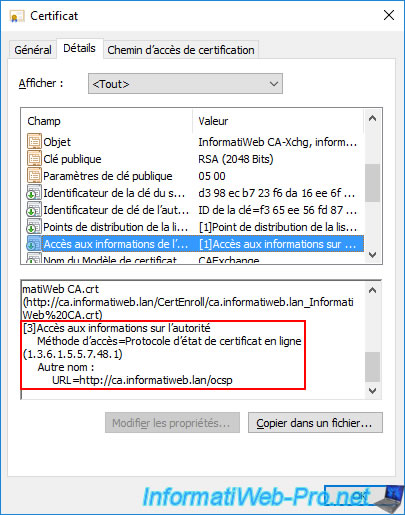
Which was not the case previously.
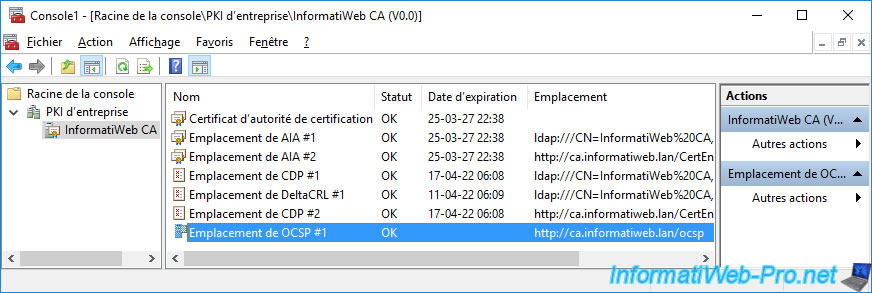
Now, if you retest access to the "OCSP" location through the "Enterprise PKI" component, the test should pass.
8. Request a new certificate (which will include OCSP support)
Now that your online responder and certification authority are properly configured to support certificate revocation checking via OCSP, it's necessary to renew certificates already generated (if any) if you want the OCSP protocol to be usable for these certificates.
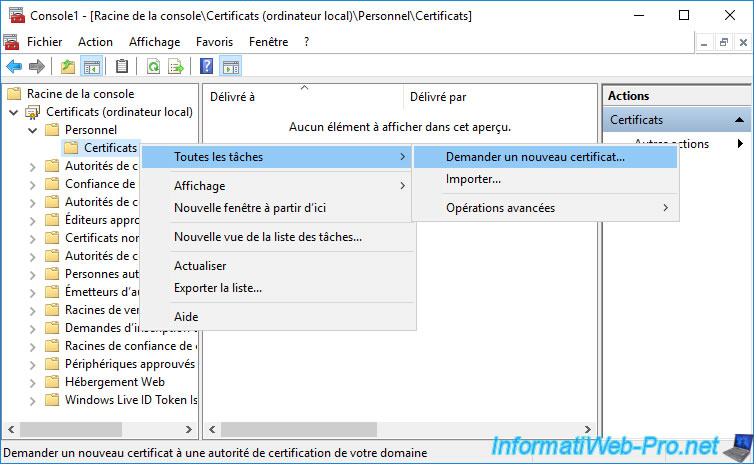
For this tutorial, we will request a new certificate for our web server (used for testing only).
For this, we will use the "mmc" console (for example).
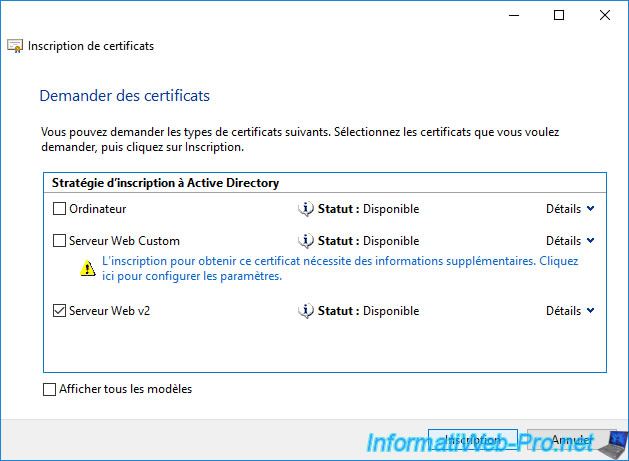
We choose our "Web Server v2" certificate template created in our "Securing an IIS web server on Windows Server 2016" tutorial.
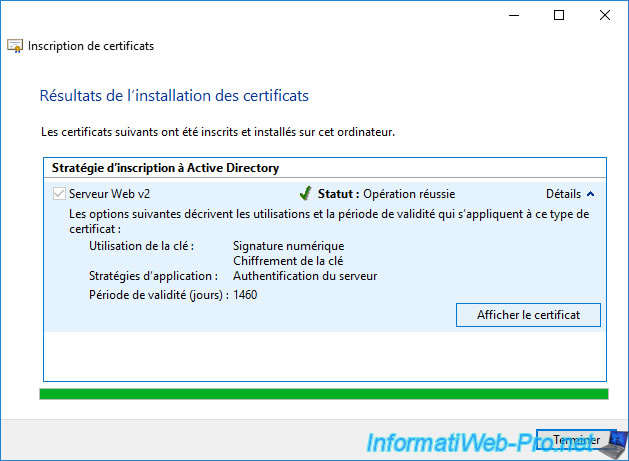
Once this new certificate is enrolled, click on "Details", then on the button : View Certificate.
Note : the enrolled certificate is also available in your "Personal" certificate store.
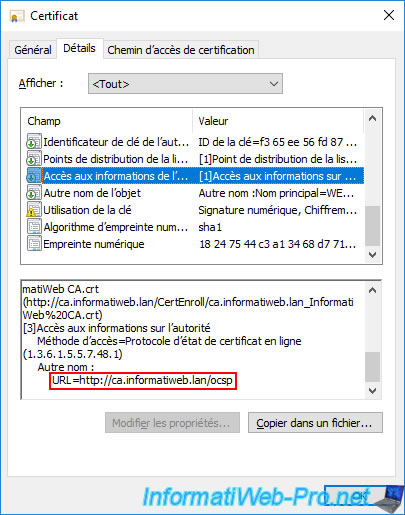
Go to the "Details" tab of the certificate that appears and select the "Authority Information Access" field.
If you look at the end of this field, you will see that a new section has been added there :
Plain Text
[3]Authority Information Access
Access Method=On-line Certificate Status Protocol (1.3.6.1.5.5.7.48.1)
Alternative Name:
URL=http://ca.informatiweb.lan/ocsp
9. Test access to OCSP address (via certutil tool)
To test access to the OCSP address from any server or computer, you can use the "certutil" tool.
However, for this, you will need a recent certificate (= including the address of your OCSP online responder).
In our case, we are going to export the requested certificate for our web server via the "mmc" console.
Export this certificate without the private key to obtain a certificate in ".cer" format.
Leave the ".cer" format selected by default.
The desired certificate has been exported in ".cer" format.
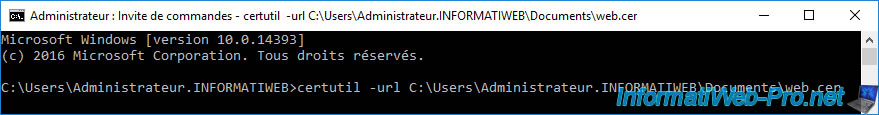
Now, to test access to the OCSP address found there, use the "certutil" tool, indicating the path to the desired certificate for the "-url" parameter :
Batch
certutil -url certificate_name.cer
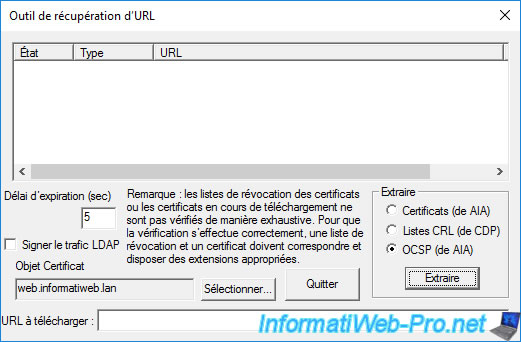
Although this is a command line tool normally, you will see that the "-url" parameter of certutil will bring up a "URL Retrieval Tool" window.
To detect and test the OCSP path found in your certificate, select the "OCSP (from AIA)" option and click on the "Extract" button.
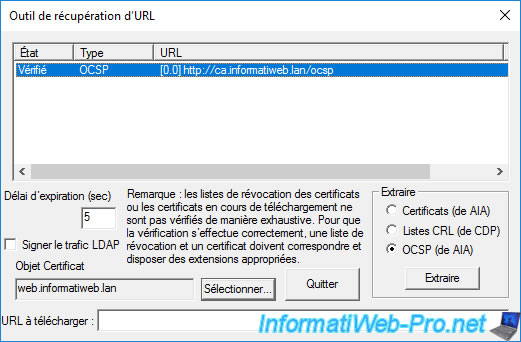
The OCSP address detected in this certificate appears and the status will be "Verified" if certutil can access this OCSP address.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment