Install and configure a root certificate authority (CA) and a secondary CA on Windows Server 2016
- Windows Server
- 08 December 2023 at 12:04 UTC
-

- 5/5
13. Certificate and revocation lists of your certification authorities
Since the informations (authority certificate and revocation lists) of your certification authorities are published in Active Directory, your servers and client computers were able to automatically retrieve these informations.
To verify this, open a "mmc" console on a server or computer linked to your Active Directory domain and add the "Certificates" component (for the current user or the local computer, depending on your rights).
In the "Trusted Root Certification Authorities" certificate store, you will find the certificate for your standalone root CA.
In our case : InformatiWeb Root CA.
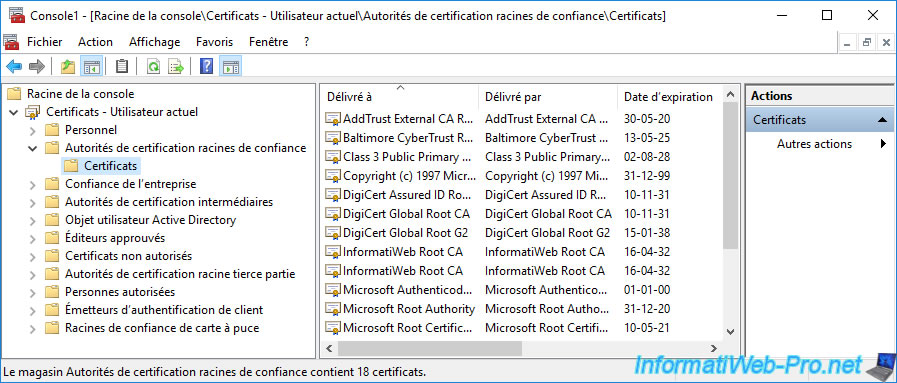
In the "Intermediate Certification Authorities -> Certificates" certificate store, you will find the certificates of all your certification authorities.
In our case :
- InformatiWeb Root CA : the certificate of our standalone root certification authority.
- InformatiWeb Sub CA : the certificate of our enterprise sub-CA.
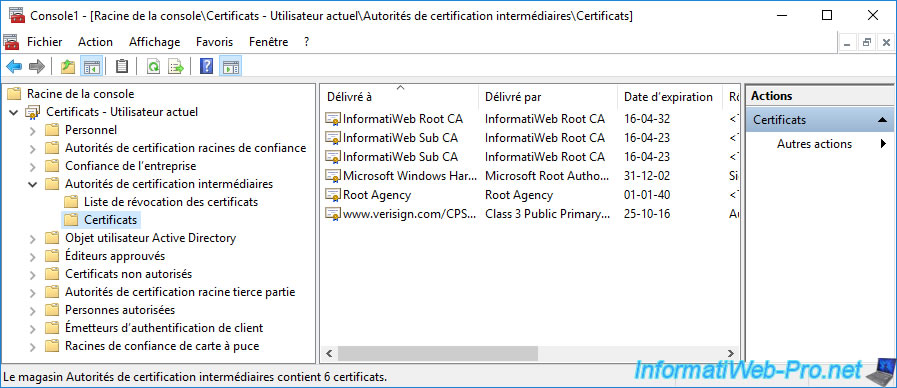
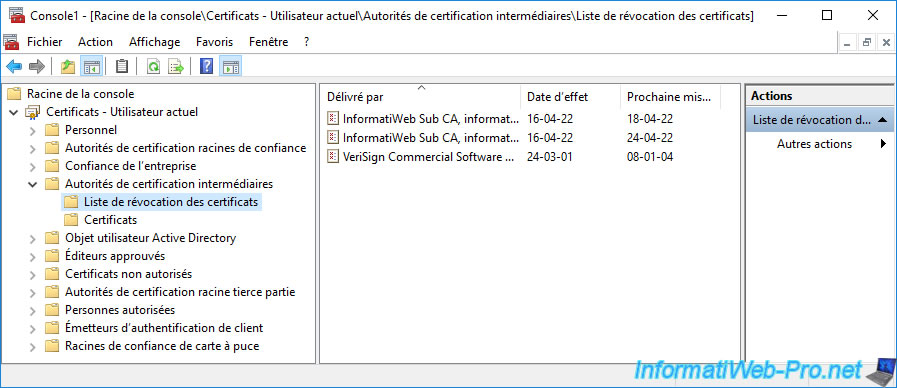
In the "Certificate Revocation List" folder of the "Intermediate Certification Authorities" certificate store, you will find the revocation lists of your subordinate CA.
In our case, it's therefore the revocation lists of our secondary certification authority "InformatiWeb Sub CA".
14. Distribute your CA certificate via group policies (GPO)
In this case, since your standalone root CA certificate and your enterprise subordinate CA certificate are in the Active Directory, your clients have already retrieved those automatically through the Active Directory.
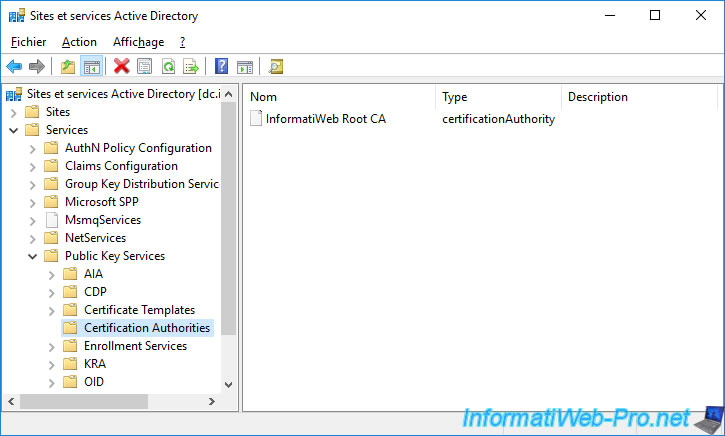
However, if you need to import the certificate of a root certification authority on servers or computers that are members of an Active Directory domain, be aware that it's possible to do it very quickly thanks to group policies (GPO).
To do this, export the public certificate of the desired root certification authority from the "Trusted Root Certification Authorities" folder of any server or computer that already knows your certification authority.
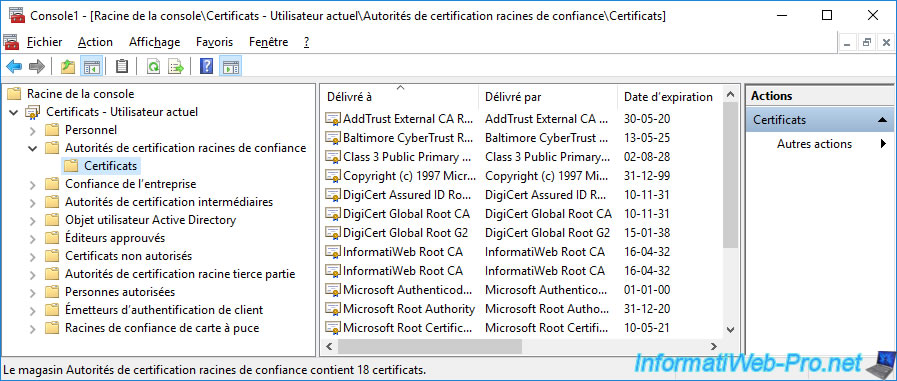
You can also export this same certificate from your root CA's "Personal" certificate store.
To do this, right-click "All Tasks -> Export" on your root CA certificate.
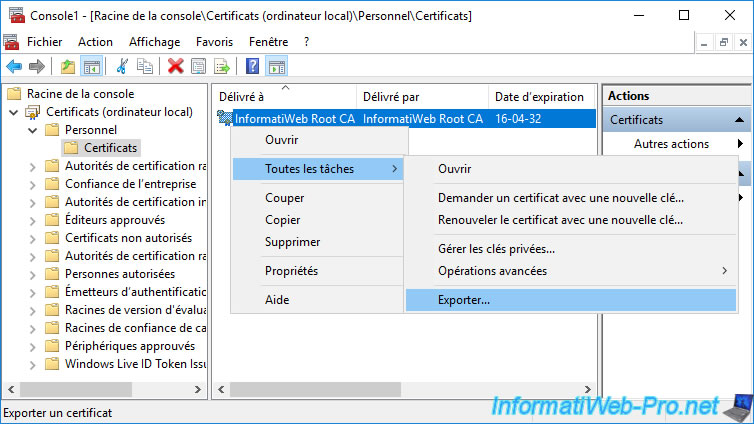
Important : select "No, do not export the private key" and click Next.
Indeed, the private key must remain secret and your clients only need the public key of your certification authority to be able to check the validity of the certificates that it issues.
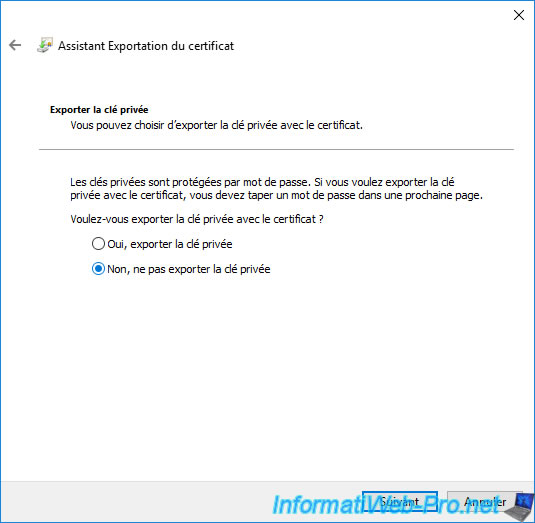
Select the "DER encoded binary X.509 (.CER)" format and click Next.
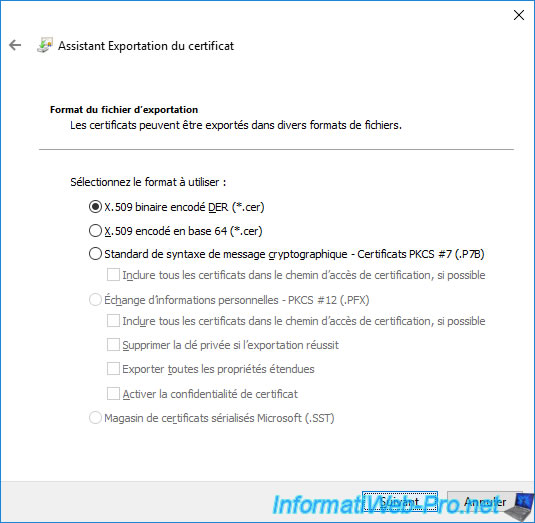
Click "Browse" and select where and under what name you want to export your CA's public certificate.
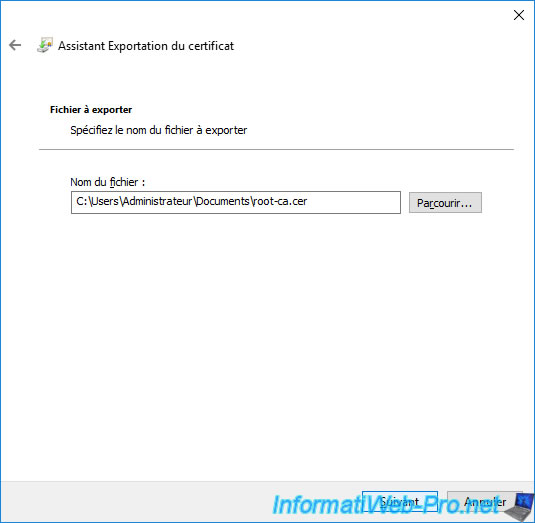
As stated here, the keys (or in other words : the private key) will not be exported.
Click Finish.
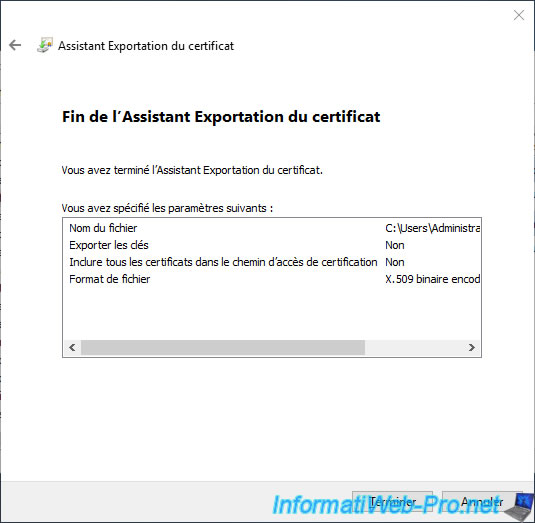
The "The export was successful" message appears.
Your root CA certificate has been exported.
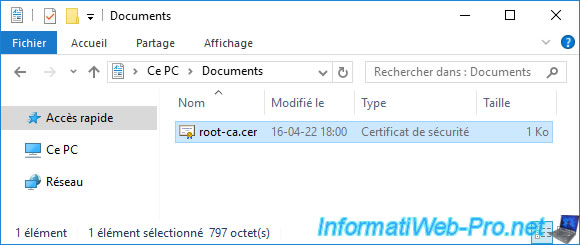
Transfer your root CA certificate to your domain controller.
For example : at the root of the "C" partition.
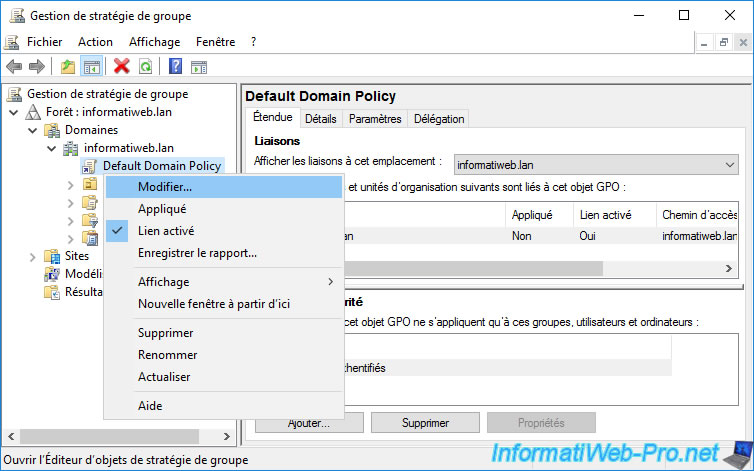
On your domain controller, open the "Group Policy Management" console and edit the "Default Domain Policy" GPO.
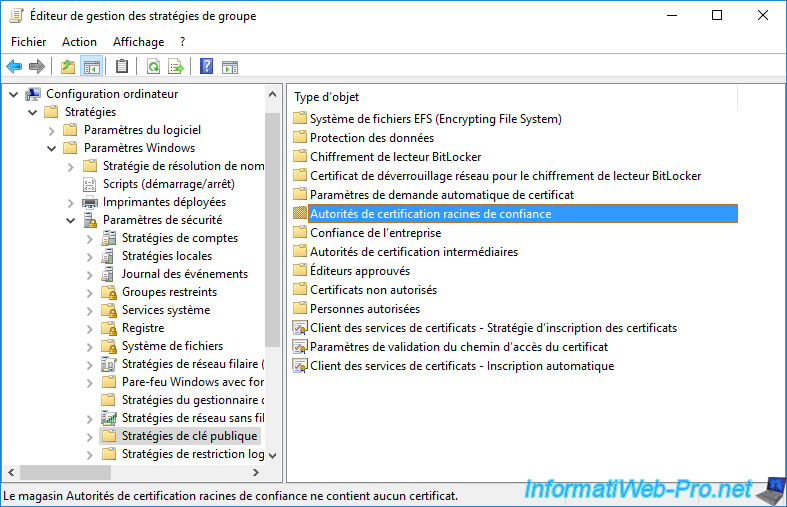
In the Group Policy Management Editor that appears, go to : Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies -> Trusted Root Certification Authorities.
In the right part, right click "Import".
The "Certificate Import" wizard appears.
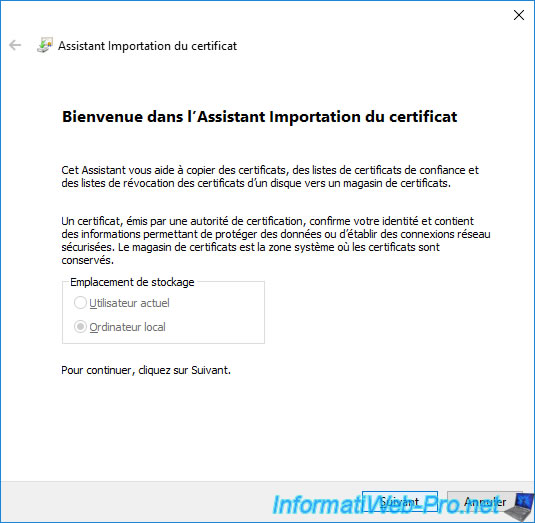
Click "Browse" and select your root CA certificate exported earlier in ".cer" format.
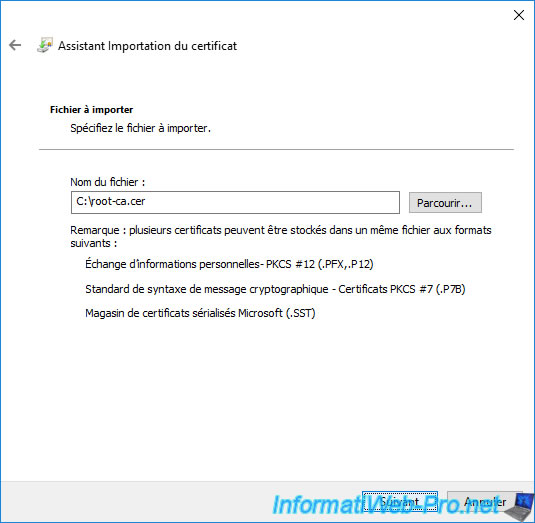
The certificate will automatically be in the "Trusted Root Certification Authorities" certificate store (which corresponds to the folder chosen previously in the GPO Management Editor).
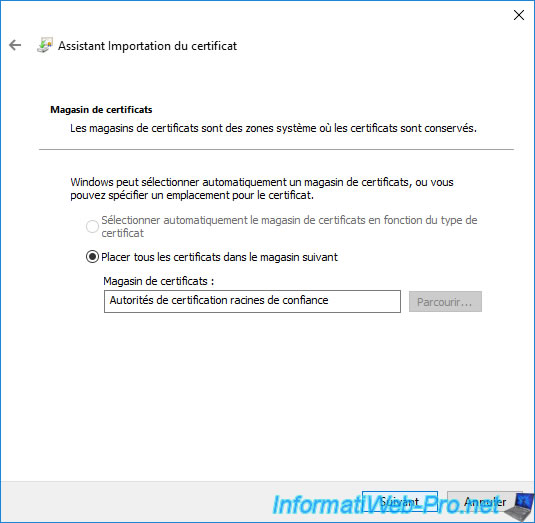
A summary is displayed telling you that the desired certificate will be imported into the "Trusted Root Certification Authorities" certificate store.
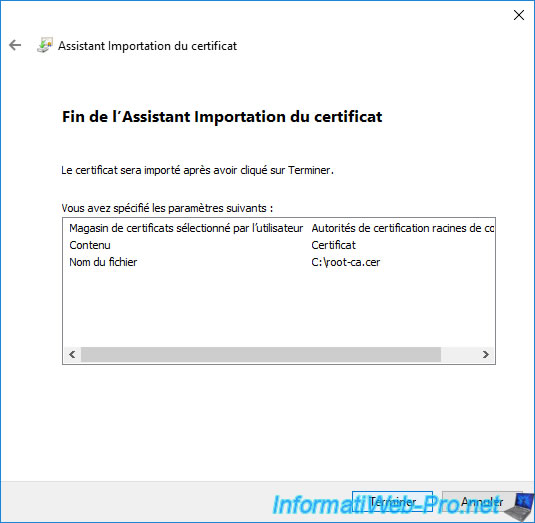
The "The import was successful" message appears.
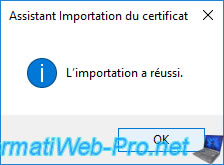
The imported certificate appears in the list.
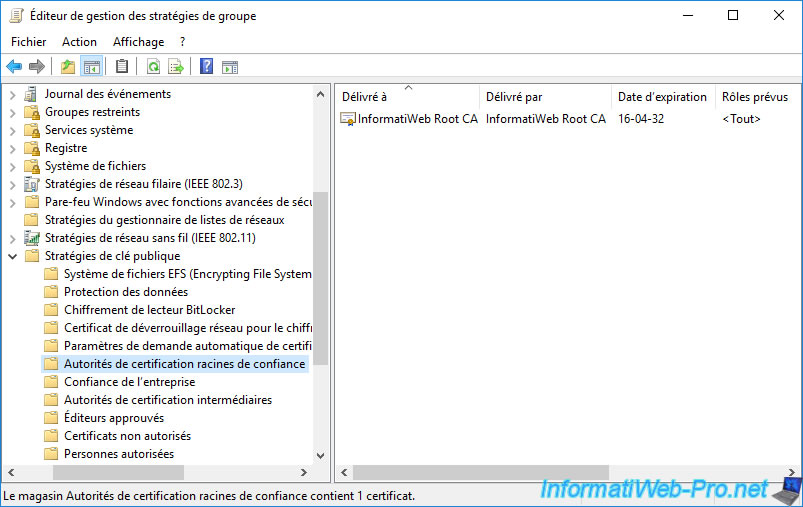
To test that this Group Policy is working, remove your root CA certificate(s) from the "Trusted Root Certification Authorities" certificate store on a server or member computer in your Active Directory domain.
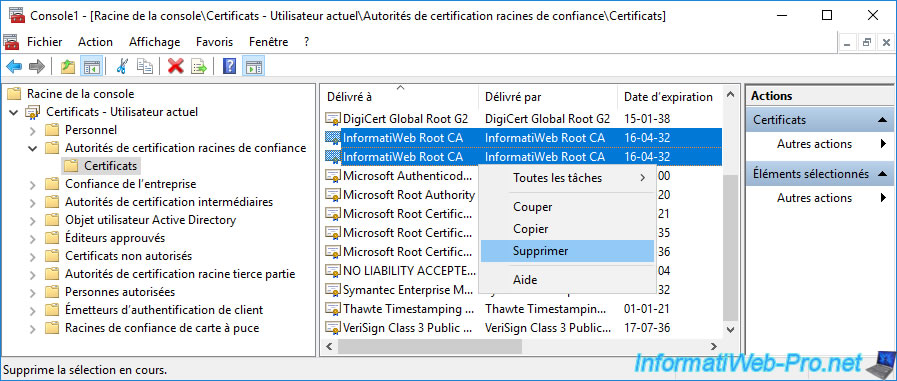
Confirm deletion of this root certificate.
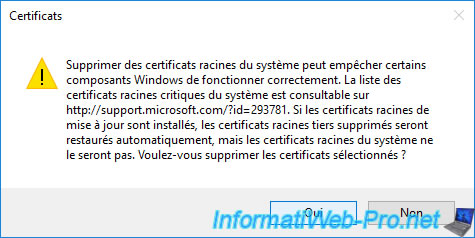
Your root CA's certificate is no longer part of your server's or computer's trusted root certification authorities.
To make your root CA certificate part of your server or computer's trusted root CAs again, force update its policy.
Batch
gpupdate /force
Click on the "Refresh" icon of the "mmc" console.
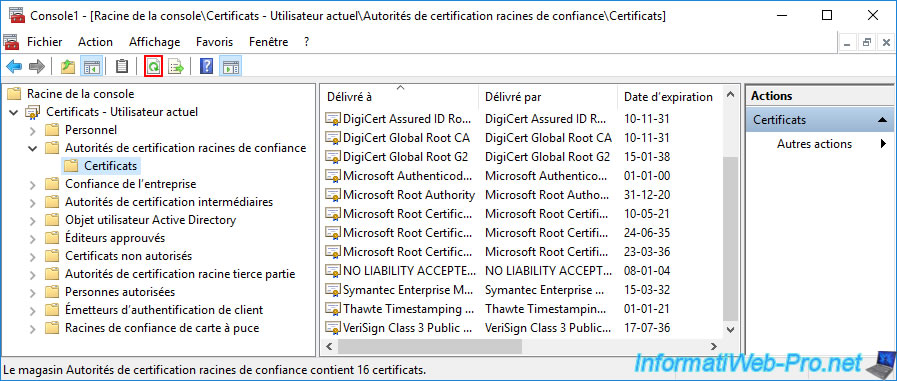
As expected, your root CA certificate is once again part of your server or computer's trusted root CAs.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-

Windows Server 1/19/2024
WS 2016 - AD CS - Buy smart cards and log in via them

No comment