Buy smart cards and log in via them on Windows 10 and Windows Server 2016
- Windows Server
- 19 January 2024 at 12:51 UTC
-

- 5/6
10. Group policies (GPOs) available for using smart cards
When you implement smart cards in your company, you can make their use mandatory and define the behavior to adopt when the smart card is removed.
To do this, open the "Group Policy Management" console and use the GPO you want.
In our case, we will modify the one that exists by default (Default Domain Policy), nevertheless this means that it will apply to all the servers and computers of the company.
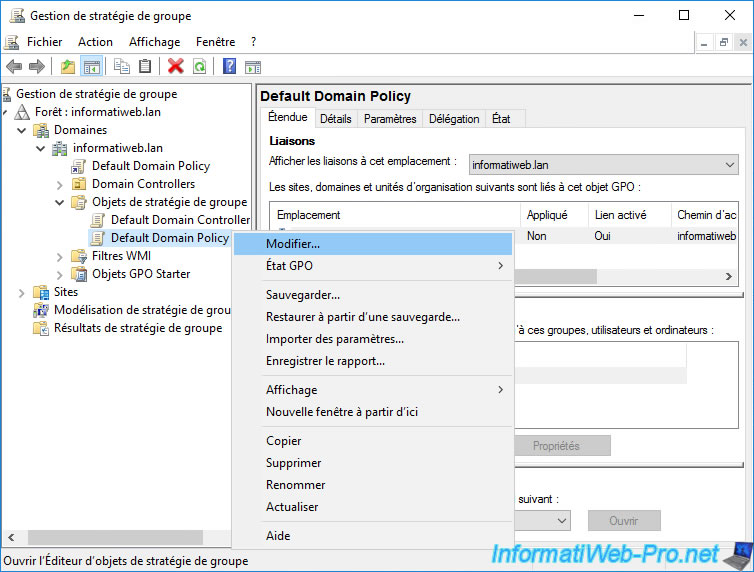
In the Group Policy Management Editor that appears, go to : Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options.
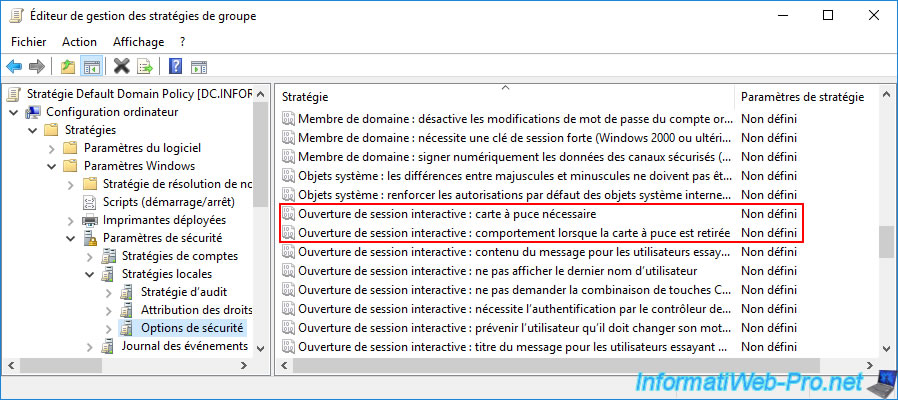
The 1st policy is called "Interactive logon: Require smart card" and allows you to define whether the smart card logon is mandatory or not.
Warning : if the Administrator account of your domain doesn't have a smart card and you enable this group policy (GPO) on all the servers and computers of your company, you will find yourself blocked.
Indeed, you will no longer be able to log in as an administrator with his password to remove this group policy (GPO).
As indicated in the "Explain" tab :
- Enabled : means that your users will only be able to log on with a smart card.
- Disabled : default behavior. Allows your users to log on with a smart card or with their usual credentials (username / password).
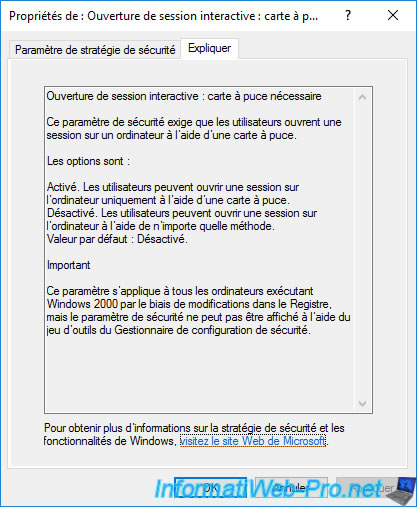
The 2nd policy is called "Interactive logon: Smart card removal behavior" and allows you to define the behavior to adopt when the smart card is removed from your card reader.
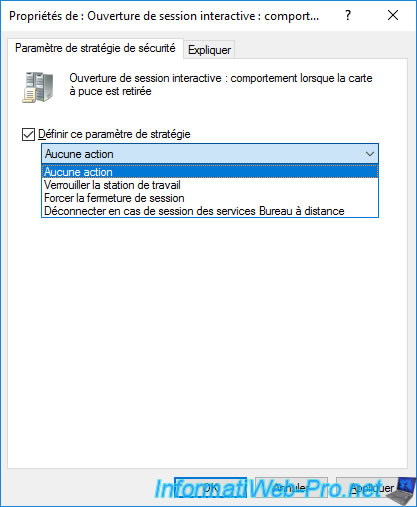
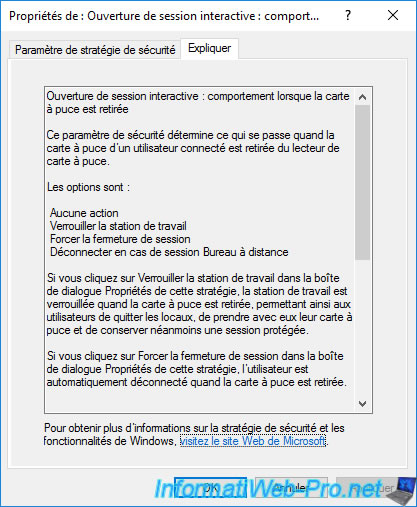
As indicated in the "Explain" tab :
- No Action : default behavior. Nothing happens when removing the smart card from the reader.
Indeed, by default, the smart card is only required during the session opening. - Lock Workstation : for security reasons, your session will be locked (NOT closed) when removing the smart card.
Thus, you can leave your workstation with your smart card (for security reasons) and keep your session open, but locked. - Force Logoff : for security reasons, your session will be closed when removing the smart card.
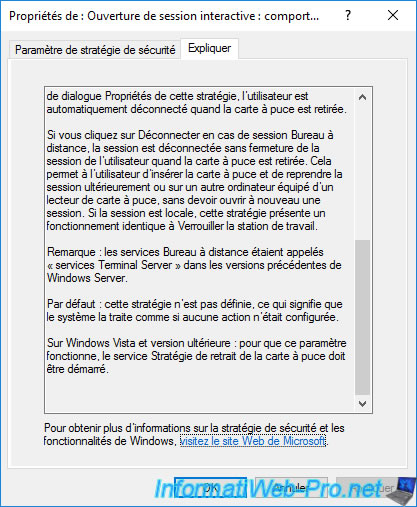
- Disconnect if a remote Remote Desktop Services session : if the user is connected via a Remote Desktop connection (RDS), the user will be disconnected when the smart card is removed.
The session will therefore remain open, but locked on the server or the remote computer and the user can reconnect to this session later by reusing his smart card.
If the user is logged on locally, the behavior adopted will be the same as the "Lock Workstation" option.
In our case, we didn't enable any of these policies in our test environment.
These policies are to be used only according to the needs of your company.
Finally, be aware that it's also possible to make smart card login mandatory for a specific user if you wish.
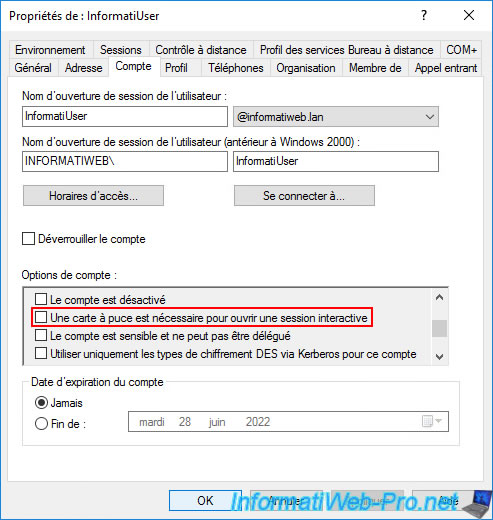
To do this, simply modify the desired user on your domain controller and go to the "Account" tab.
In the list of account options available to each user, you will find the "Smart card is required for interactive logon" option.
Important : if you check this box for this user, this user will only be able to log in using their smart card.
This means that this user will only be able to connect to servers and/or computers with a compatible smart card reader.
Otherwise, that user will not be able to log in as they will no longer be able to use their "username/password" combination.
11. Update the certificate used by your domain controller
For you to be able to connect with a smart card to a server or a computer in your company, they must be able to trust your Active Directory domain controller.
For this to be possible, you must update the certificate that your Active Directory domain controller has.
Otherwise, you will surely receive this error on the client PC.
Plain Text
The system could not log you on. You cannot use a smart card to log on because smart card is not supported for your user account. Contact your system administrator to ensure that smart card logon is configured for your organization.
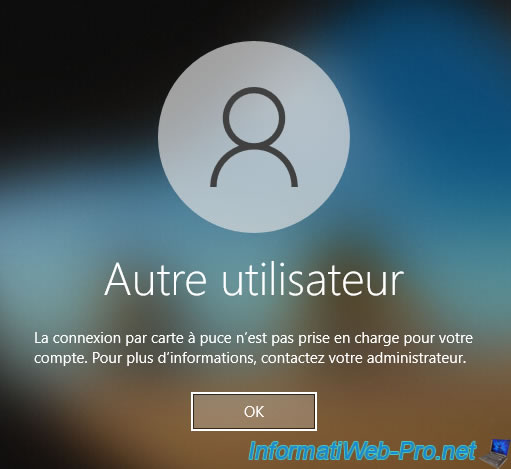
Indeed, by default, your domain controller uses a certificate based on the "Domain Controller" certificate template.
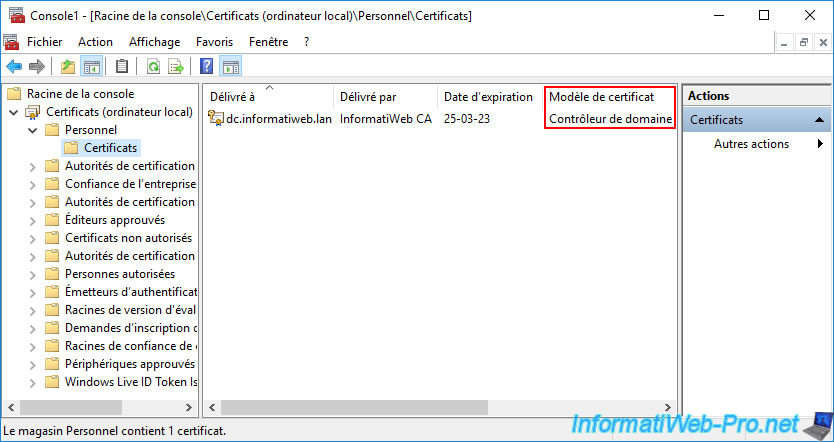
However, this type of certificate is only designed for 2 roles :
- Proves your identity to a remote computer : which corresponds to the "Client Authentication" application policy.
- Ensures the identity of a remote computer : which corresponds to the "Server Authentication" application policy.
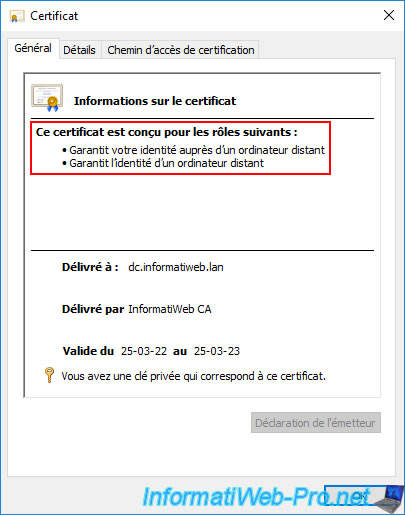
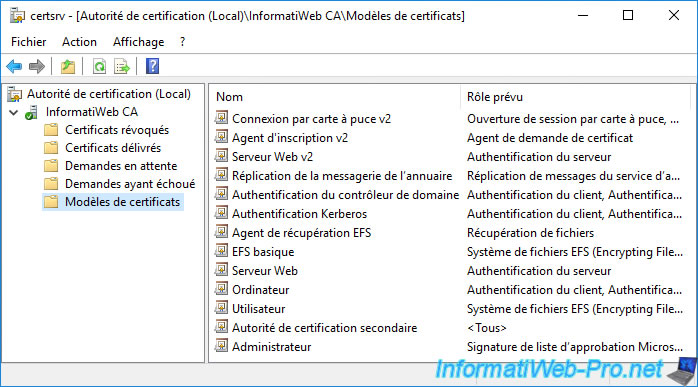
If you look at the certificate templates that your certificate authority can issue by default, you will see that domain controllers can obtain different certificate templates :
- Domain controller : the certificate template used by default by your domain controllers.
As you just saw, this type of certificate is only designed for client and server authentication. - Directory Email Replication : a certificate template that can be obtained by a domain controller if you have enabled automatic certificate enrollment (computer side) for your domain controllers.
- Domain Controller Authentication : has the same enforcement policies as the "Domain Controller" certificate template it replaces.
But, this certificate template is also designed for smart card logon. - Kerberos Authentication : newer certificate template that has the same application policies as the previous one (Domain Controller Authentication).
But, this model has an additional 4th application policy allowing KDC (Key Distribution Center) authentication.
For the connection using a smart card to work correctly on your servers and computers (which are members of your Active Directory domain), you will therefore need to use a certificate based on the "Domain Controller Authentication" or "Kerberos Authentication".
Source : Validate and Configure Public Key Infrastructure - Certificate Trust Model - Microsoft Docs.
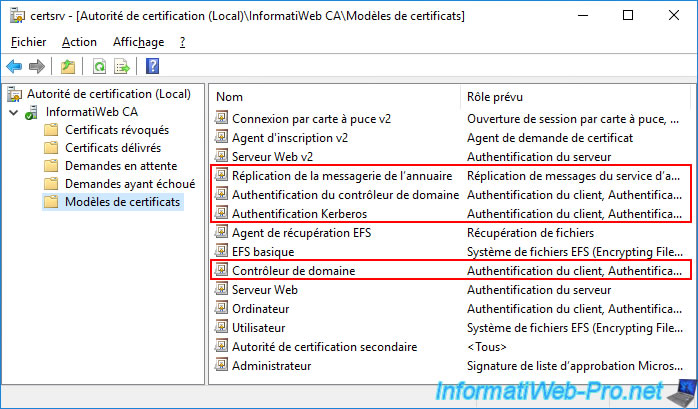
To check what we have just explained to you, you can right-click "Manage" on "Certificate Templates".
Then, double click on "Domain Controller Authentication".
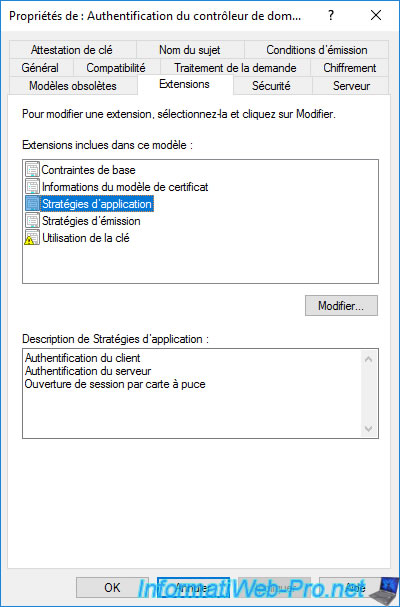
As you can see in the "Extensions" tab of this "Domain Controller Authentication" certificate template, the application policies are :
- Client Authentication
- Server Authentication
- Smart Card Logon
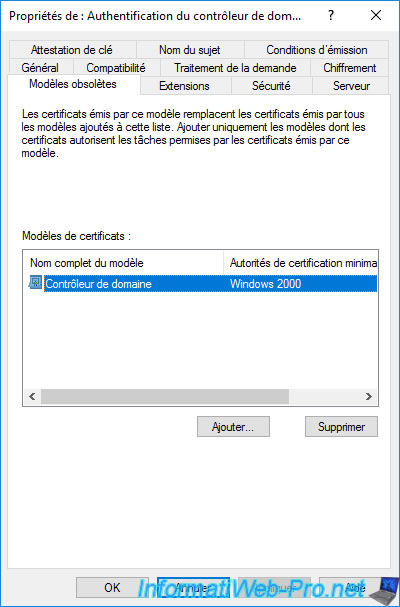
If you go to the "Superseded Templates" tab of this certificate template, you will see that it makes the "Domain Controller" certificate template obsolete.
Indeed, this "Domain Controller Authentication" certificate template is more recent than its predecessor (Domain Controller).
This also means that by enabling automatic certificate enrollment, enrolling a certificate based on the "Domain Controller Authentication" certificate template will make the old certificate based on the "Domain Controller" template disappear.
The other possibility is to use a certificate based on the "Kerberos Authentication" template.
Double click on this template.
As you can see, the 3 policies mentioned above are also present.
But, an additional application policy has appeared (if you have a recent version of Windows Server) : KDC Authentication.
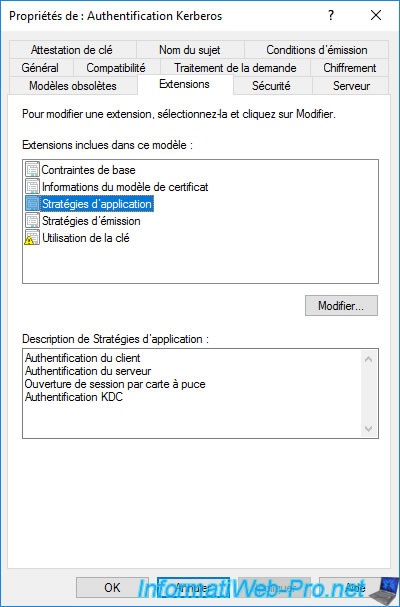
However, this certificate template doesn't make the "Domain Controller" certificate template obsolete.
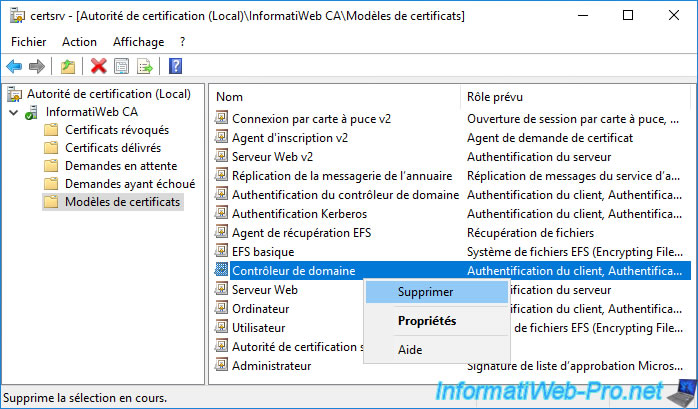
To update your domain controller's certificate, remove the "Domain Controller" certificate template from the list of certificate templates that your certification authority can issue.
Note that this doesn't remove the affected certificate template, it only prevents your CA from issuing this type of certificate.
Confirm disabling this certificate template by clicking Yes.
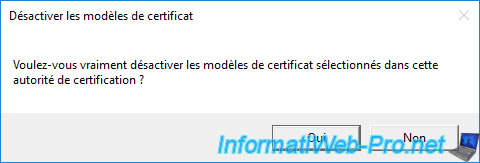
The "Domain controller" certificate template disappears from the list.
To have your domain controller's current certificate replaced with a newer certificate template (through the management of superseded certificate templates you saw earlier), you will need to enable automatic certificate enrollment for your domain controllers.
To do this, on your domain controller, open the "Group Policy Management" console and modify the "Default Domain Controllers Policy" GPO object which exists by default and which concerns all your domain controllers.
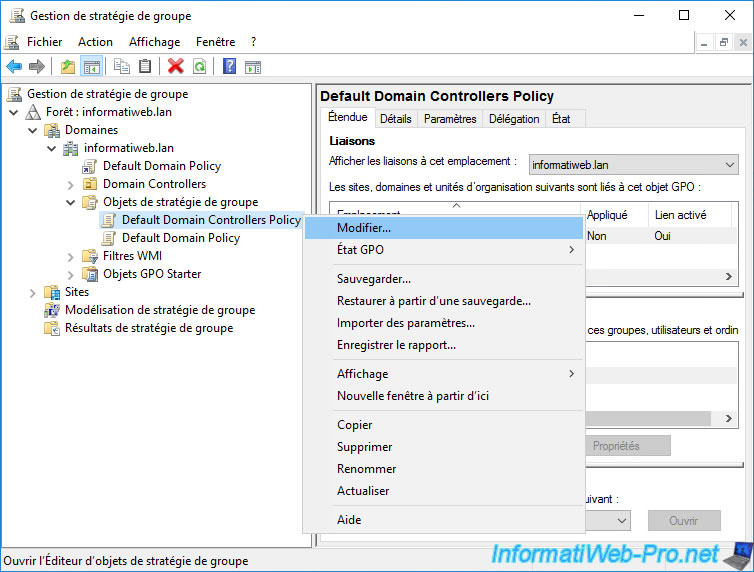
In the Group Policy Management Editor that appears, go to "Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies" and double-click the "Certificate Services Client - Certificate Enrollment Policy".
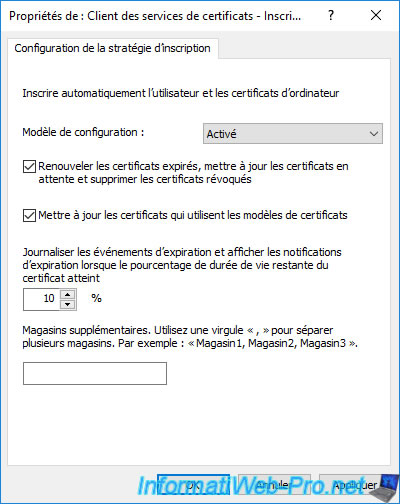
Enable this policy and check the 2 boxes to enable automatic renewal of certificates that your domain controller can automatically enroll and updating old certificates using new certificate templates that replace them (if any).
Then, click OK.
On your domain controller, force the Group Policy update by running the command.
This will also cause auto-enrollment of certificates, if needed.
Batch
gpupdate /force
If necessary, you can force the automatic enrollment of certificates by running the command :
Batch
certreq -autoenroll -q
If you go to your domain controller's "Personal" certificate store, you will notice that your certificates have changed.
This is because your certificate based on the "Domain Controller" certificate template (as it's obsoleted by the "Domain Controller Authentication" certificate template that was detected during automatic certificate enrollment).
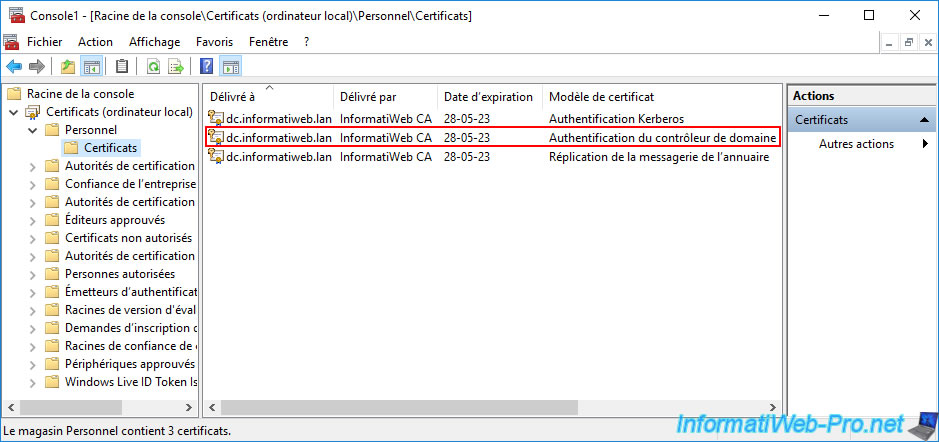
Now, your domain controller normally has 3 certificates :
- 1 certificate based on the "Kerberos Authentication" certificate template.
- 1 certificate based on the "Domain Controller Authentication" certificate template.
- 1 certificate based on the "Directory Email Replication" certificate template.
Important : the only certificate really necessary for the proper functioning of the smart card connection is the one based on the "Domain controller authentication" certificate template.
As explained before, if your domain controller has at least one certificate based on the "Domain Controller Authentication" or "Kerberos Authentication" certificate template, it will work fine since these 2 templates are designed for smart card logon.
Note : in your case, the certificate template is displayed on the far right of the list.
But, for this tutorial, I deliberately moved it to the left to make it more readable.
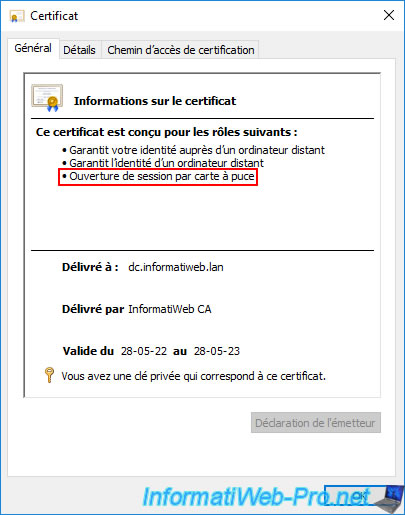
If you double-click on the certificate based on the "Domain Controller Authentication" certificate template, you will see that this certificate is designed especially for smart card logon.
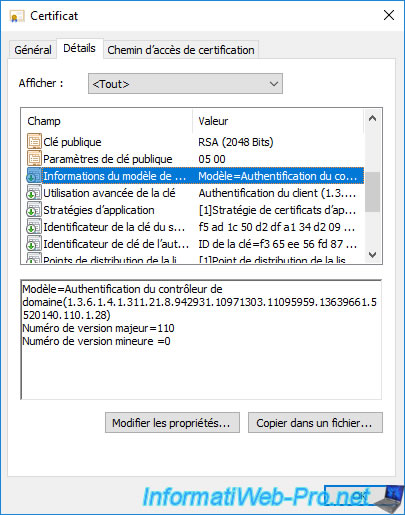
In the "Details" tab, if you select the "Certificate Template Information" field, you will see that the template used is : Domain Controller Authentication.
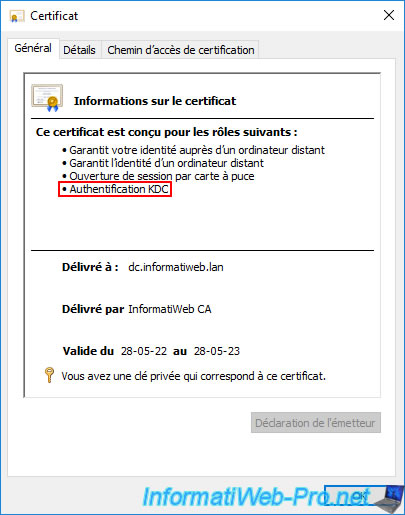
Double-click the certificate based on the "Kerberos Authentication" certificate template.
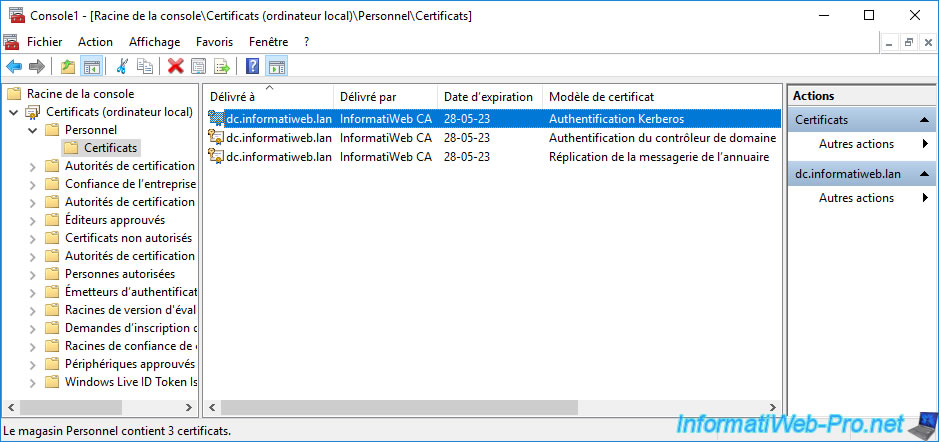
As you can see, the certificate based on the "Kerberos Authentication" certificate template is also designed for smart card logon, but also for KDC Authentication.
In our case, this is not required, but just be aware that this certificate template is newer than the "Domain Controller Authentication" template.
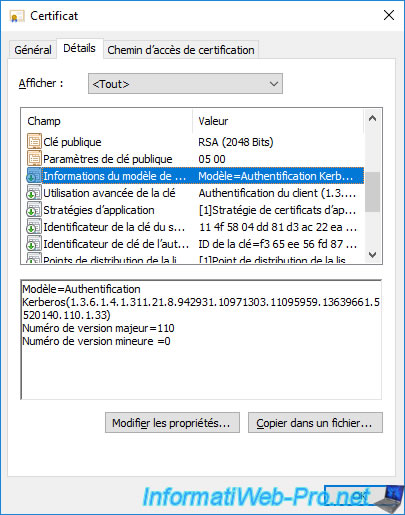
In the "Details" tab, if you select the "Certificate Template Information" field, you will see that the template used is : Kerberos Authentication.
Share this tutorial
To see also
-

Articles 1/26/2024
SafeNet Authentication Client (SAC) - Installation and overview
-

Articles 9/8/2023
What is encryption and how does it work ?
-

Windows Server 12/29/2023
WS 2016 - AD CS - Backup and restore a certificate authority (CA)
-
Windows Server 1/5/2024
WS 2016 - AD CS - Create a recovery agent to recover certificates

No comment