The physical, virtual and logical network interfaces of pfSense 2.6
- Firewall
- pfSense
- 23 May 2025 at 11:24 UTC
-

- 2/2
6. Other types of interfaces
On pfSense, you can also create other types of interfaces:
- VLANs: allows you to create subnets on the same physical network whose packets will be tagged with a VLAN ID.
- QinQ: allows you to group several VLANs using an external tag where the packets will already be tagged with the correct VLAN IDs.
- PPPs: allows you to create interfaces connected directly to the Internet (PPP for telephones and modems), PPPoE for DSL connections, and PPTP or L2TP for ISPs that require this type of protocol for connection to the Internet.
- GREs: allows you to tunnel network traffic between 2 endpoints, but without encryption. IPv4 and IPv6 can be tunneled, including at the same time.
The Generic Routing Encapsulation (GRE) protocol was originally developed by Cisco and is the default tunneling mode on most of their devices. - GIFs: generic tunneling interface similar to GRE which also allows transporting IPv4 and IPv6, but which can also be used to transport IPv6 over an IPv4 network.
- Bridges: allows you to easily connect multiple ports together.
- LAGGs: allows network links to be aggregated into a logical interface to benefit from better bandwidth and/or for fault tolerance.
Sources :
- Virtual LANs (VLANs) | pfSense Documentation
- QinQ Configuration | pfSense Documentation
- PPPs | pfSense Documentation
- GRE (Generic Routing Encapsulation) | pfSense Documentation
- GIF (Generic tunnel InterFace) | pfSense Documentation
- Creating a Bridge | pfSense Documentation
- LAGG (Link Aggregation) | pfSense Documentation
7. Configure the WAN interface (connected to the Internet)
To configure the pfSense WAN interface, go to the menu: Interfaces -> WAN.
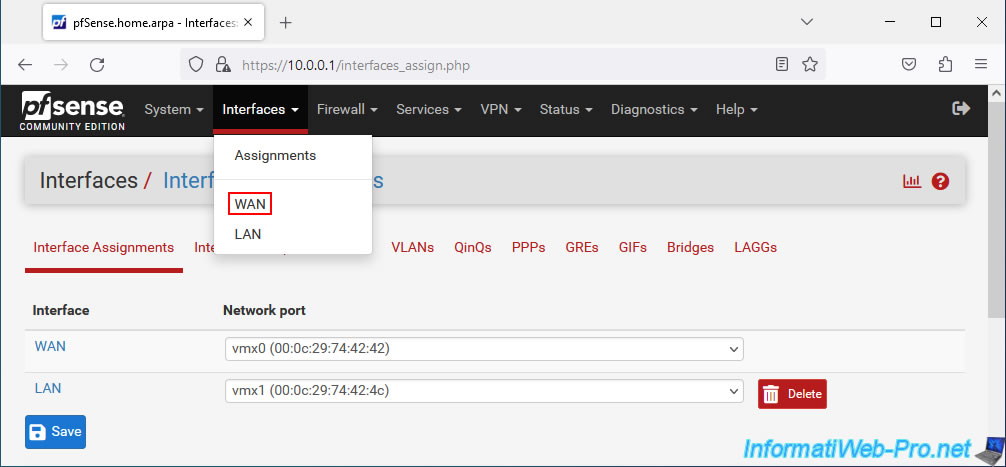
On the "Interfaces / WAN" page that appears, you will first find a "General Configuration" section to configure the settings:
- Enable: check the "Enable interface" box to enable this WAN interface.
- Description: the description of this interface. Defaults to "WAN" in this case.
- IPv4 Configuration Type: allows you to choose the type of IPv4 configuration to use for the WAN interface.
- None: do not assign an IPv4 address to the WAN interface.
- Static IPv4: allows you to define a static IPv4 address for the WAN interface.
- DHCP: automatically obtains an IP address for the WAN interface from the parent network's DHCP server.
- PPP: allows you to directly connect the WAN interface to the Internet via a USB modem (for mobile Internet) or a traditional modem.
- PPPoE: same, but for DSL Internet connections.
- PPTP: same, but for ISPs that require authentication via the PPTP protocol.
Warning: CANNOT be used to connect to a VPN server. - L2TP: same, but for ISPs that require the L2TP protocol.
Warning: CAN'T be used to connect to a VPN server.
- IPv6 Configuration Type: allows you to choose the type of IPv6 configuration to use for the WAN interface.
- None: do not assign an IPv6 address to the WAN interface.
- Static IPv6: allows you to define a static IPv6 address for this interface.
- DHCP6: automatically obtains an IPv6 address for the WAN interface from the parent network's DHCPv6 server (if applicable).
- SLAAC: automatic configuration of an IPv6 address using router advertisements (RA) which includes the prefix and associated information.
- 6rd Tunnel: supports IPv6 using 6RD data provided by your ISP to pass IPv6 traffic into IPv4 packets.
- 6to4 Tunnel: an alternative method of passing IPv6 traffic through an IPv4 network.
The main difference being that no settings can be configured for this alternative method and 6 to4 uses constant prefixes and relays. - Track Interface: allows you to assign IPv6 addresses delegated by the ISP through DHCPv6 prefix delegation.
- MAC Address: allows you to modify the MAC address used by the pfSense WAN interface.
By default, the MAC address used will be the one physically defined on the network card associated with this WAN interface. - MTU: allows you to modify the MTU which is by default 1500 in most cases.
Note that if the WAN interface is configured as PPPoE, the default value will be 1492 bytes.
If you want to enable Jumbo frame support, you will need to specify an MTU of 9000 bytes. - MSS: similar to MTU, but only concerns the "data" part of TCP packets. So header size is not included.
- Speed and Duplex: allows you to manually define the speed and duplex mode that this network interface should use.
By default, these values will be detected automatically from the physical network card assigned to this WAN interface.
Sources :
- IPv4 Configuration Types | pfSense Documentation
- PPPs | pfSense Documentation
- IPv6 Configuration Types | pfSense Documentation
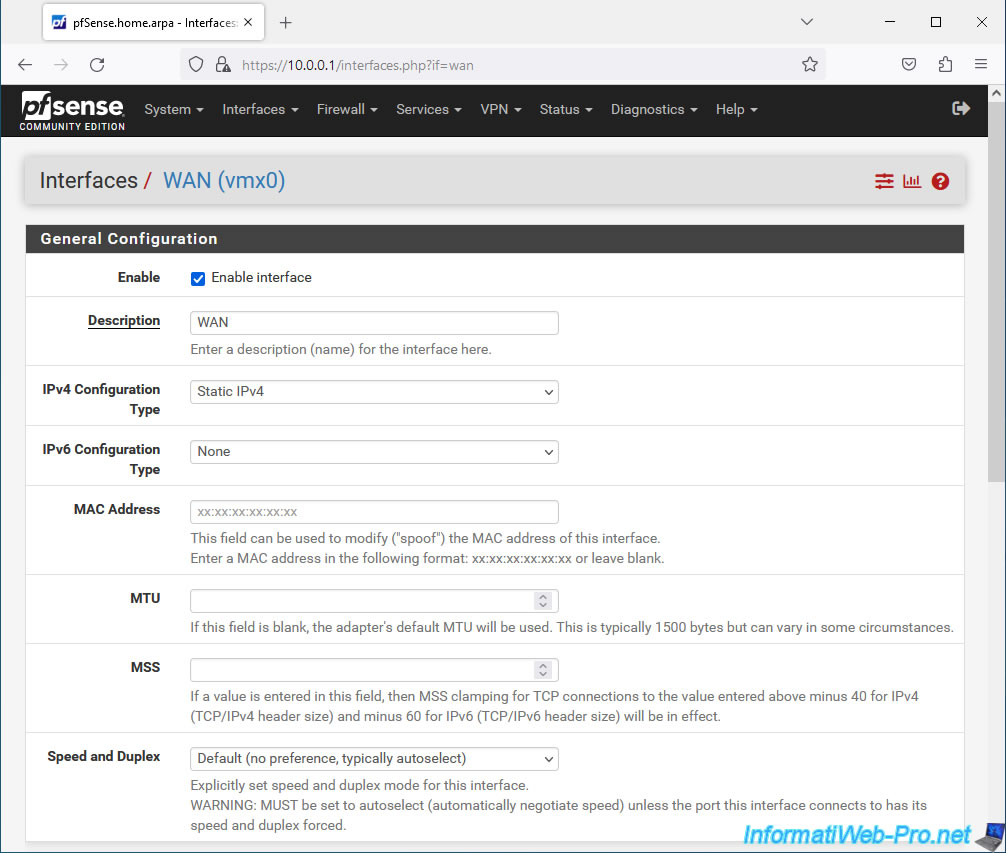
If you chose "IPv4 Configuration Type: Static IPv4", a "Static IPv4 Configuration" section will appear to allow you to configure the following settings:
- IPv4 Address: the static IPv4 address to assign to the WAN interface.
- IPv4 Upstream gateway: the IPv4 address of the parent router (for example: your Box).
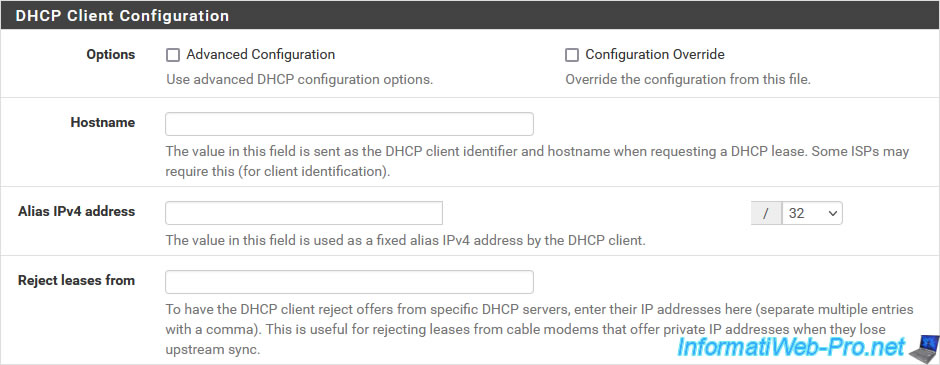
If you chose "IPv4 Configuration Type: DHCP", a "DHCP Client Configuration" section will appear to allow you to configure advanced DHCP settings.
However, usually nothing is necessary. Unless your ISP provides you with some required DHCP settings.
Indeed, the goal of the DHCP client is to automatically retrieve an IP address, as well as associated information (gateway IP address, DNS servers, ...).
If you chose "PPP", "PPPoE", "PPTP" or "L2TP" for the "IPv4 Configuration Type" setting, an additional section "PPP Configuration", "PPPoE Configuration" or "PPTP/L2TP Configuration" where you will need to specify your Internet access settings provided by your ISP.

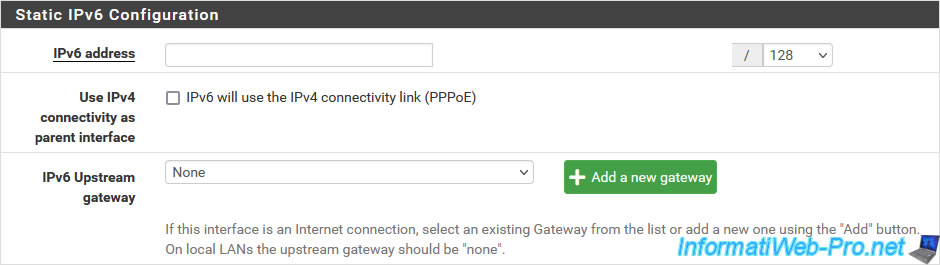
For the "IPv6 Configuration Type" parameter, if you have selected the "Static IPv6" type, a "Static IPv6 Configuration" section will appear and allow you to configure the following settings:
- IPv6 address: allows you to define an IPv6 address for this WAN interface.
- Use IPv4 connectivity as parent interface: allows you to send the DHCPv6 request via IPv4.
However, this configuration is only useful if the ISP requests it. - IPv6 Upstream gateway: the IPv6 address of the parent router (for example: your Box).
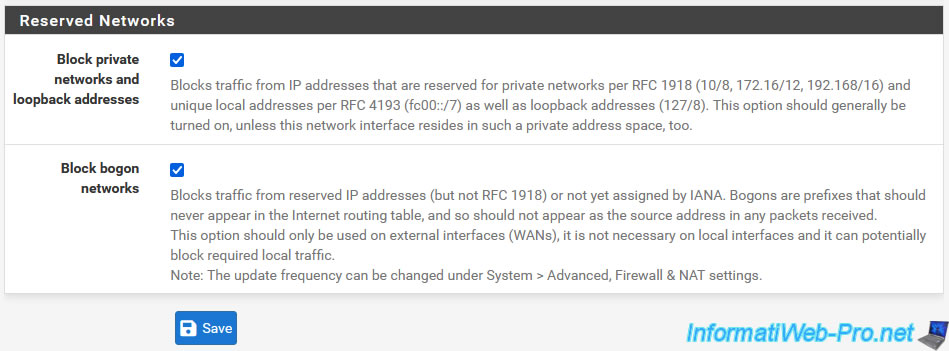
At the bottom of the page, you will find a "Reserved Networks" section with 2 settings:
- Block private networks and loopback addresses: enabling this option blocks traffic coming from private IP addresses (which should therefore only be on a local network and not on the Internet) and going to the pfSense WAN interface.
However, if the pfSense WAN interface is connected to an intermediate router and not directly to the Internet, you should disable this setting to avoid future problems. - Block bogon networks: by default, this option is enabled. This blocks traffic from networks that should not exist on the Internet. This includes reserved and unallocated IP address spaces.
Bogon network blocking is only useful on the pfSense WAN interface.
Source : Rule Methodology - Block Bogon Networks | pfSense Documentation.
8. Configure the LAN interface (connected to the local network)
To configure the pfSense LAN interface, go to the menu: Interfaces -> LAN.
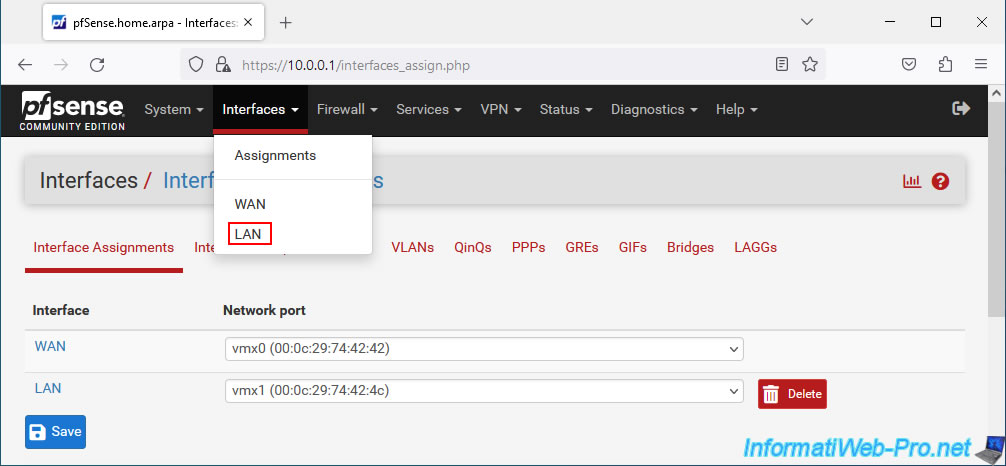
For configuring the LAN interface, you will again find a "General Configuration" section with the same settings as for the WAN interface.
So, refer to the information from the previous step of this tutorial for these settings.
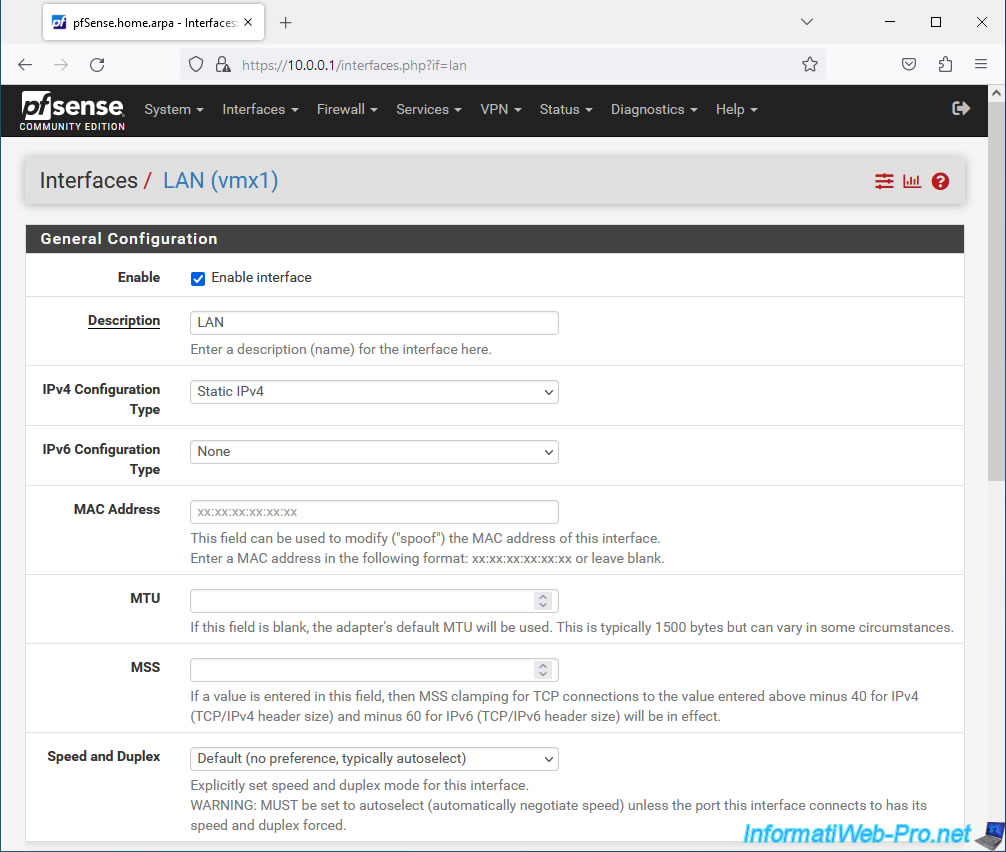
Again, if you select "IPv4 Configuration Type: Static IPv4", a "Static IPv4 Configuration" section will appear to allow you to configure:
- IPv4 Address: the static IPv4 address to assign to the LAN interface.
- IPv4 Upstream gateway: in the case of a LAN interface, there is no gateway. So always select "None".
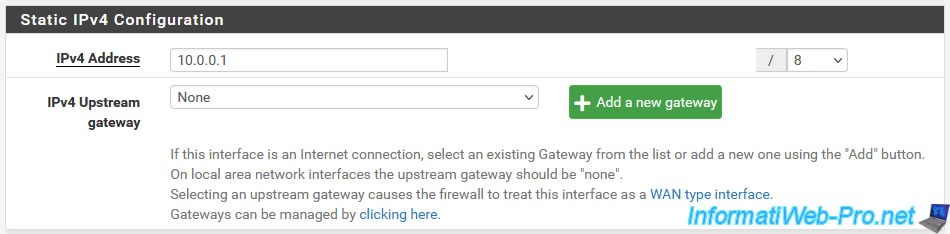
Finally, at the bottom of the page, you will find the same settings regarding reserved networks.
However, in the case of the LAN interface, it is normal to authorize traffic coming from private IP addresses, network loopback IP addresses (eg: 127.0.0.1).
Additionally, blocking bogon networks is only useful for the WAN interface (as noted in the pfSense comment) and enabling it could even block necessary local traffic.
So, in the case of the LAN interface, always disable these 2 settings:
- Block private networks and loopback addresses
- Block bogon networks
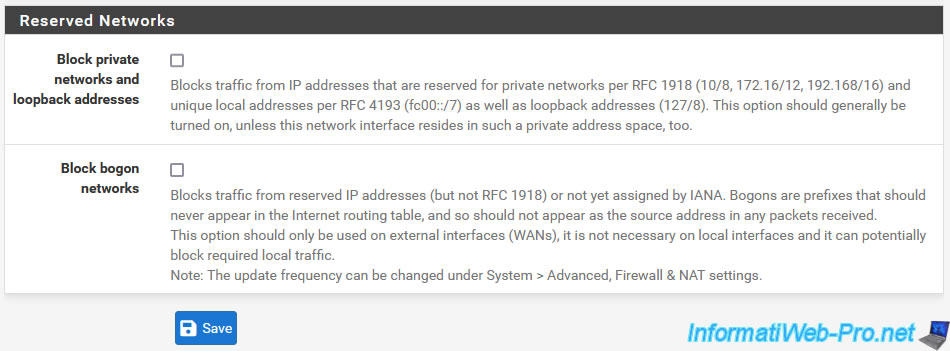
9. Switches
Finally, if you purchase one of the physical appliances sold by Netgate (where pfSense is pre-installed), an "Interfaces -> Switches" menu may appear.
Note: this is not the case for all models.
For more information, refer to the page : Configuring the Switch Ports | Netgate Documentation.
Share this tutorial
To see also
-

Firewall 6/25/2025
pfSense 2.6 - 1:1 NAT (IP address mapping)
-

Firewall 9/19/2025
pfSense 2.6 - Create a site-to-site (S2S) VPN tunnel via OpenVPN secured with SSL/TLS (L2 mode)
-

Firewall 5/9/2025
pfSense 2.6 - Download and installation on VMware Workstation
-

Firewall 6/18/2025
pfSense 2.6 - Manage quality of service (QoS)

No comment