- Firewall
- pfSense
- 04 June 2025 at 13:09 UTC
-

On pfSense, DNS resolution is managed using 2 components: the DNS resolver and the DNS forwarder.
1. DNS Resolver
The DNS resolver allows domain names to be resolved into IP addresses while caching the responses.
It supports DNS over TLS, DNSSEC (signed DNS zone), as well as many options.
This way, client machines will be able to resolve domain names by indicating the pfSense IP address as the primary DNS server.
Which is the case by default when using the pfSense DHCP server.
To configure the DNS Resolver, go to: Services -> DNS Resolver.
Source : DNS Resolver | pfSense Documentation.
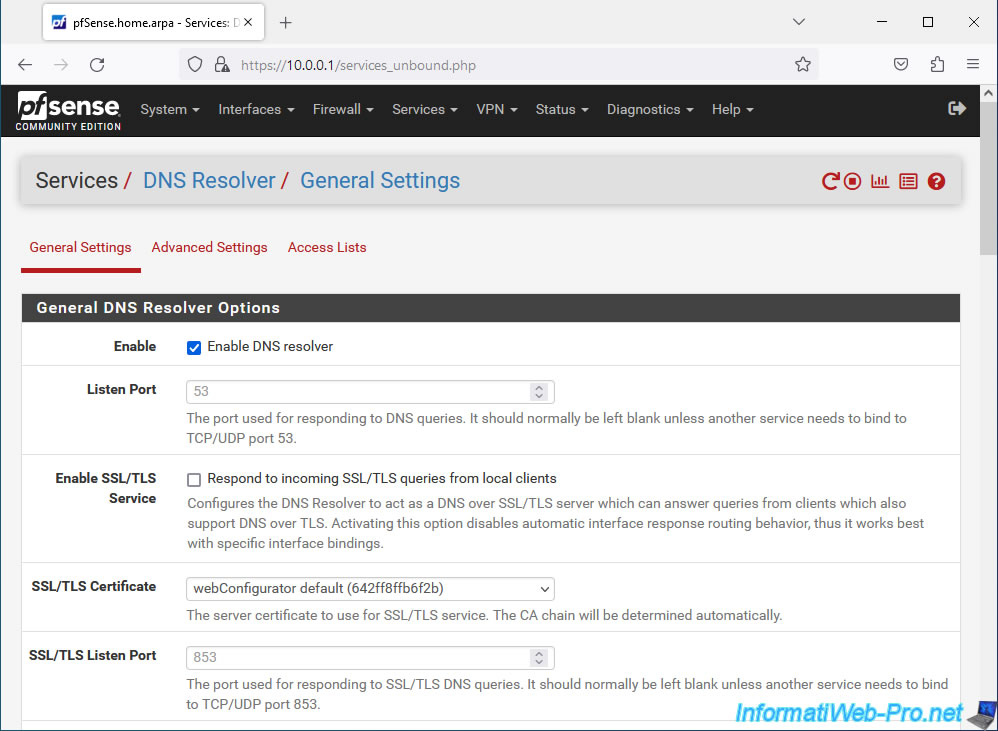
For the DNS Resolver, you can configure the settings:
- Enable: by default, the "Enable DNS resolver" box is checked. The DNS resolver is therefore enabled by default.
- Listen Port: the port on which the DNS server should listen. Defaults to port 53.
- Enable SSL/TLS Service: allows the DNS resolver to act as a DNS over TLS server which can therefore respond to DNS over TLS queries from client machines.
- SSL/TLS Certificate: the server certificate to use when the DNS resolver acts as a DNS server over TLS (see previous setting).
- SSL/TLS Listen Port: port on which the DNS over TLS server should listen to receive DNS over TLS requests from clients.
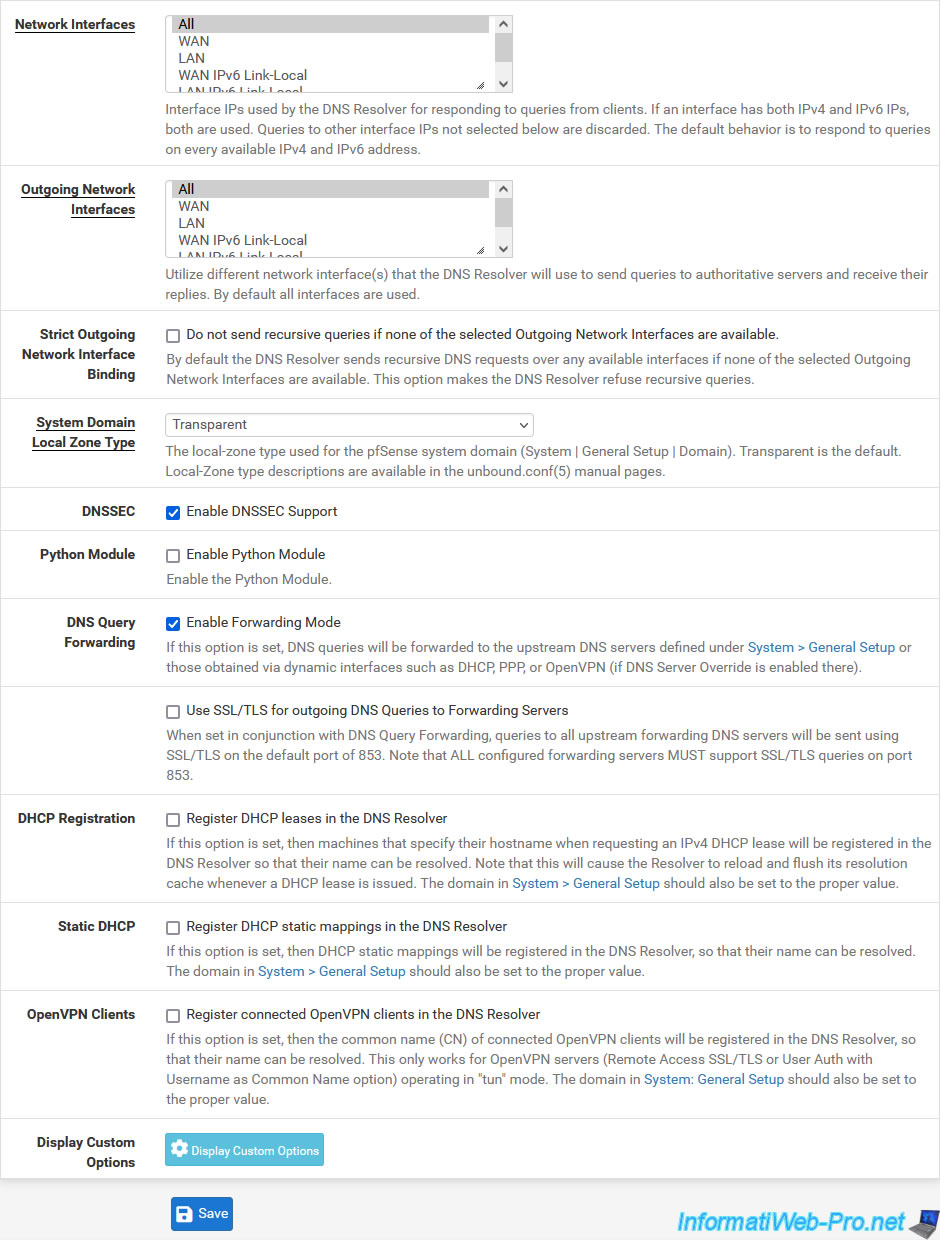
Default: port 853. - Network Interfaces: the interfaces for which the DNS resolver will listen to receive DNS requests from client machines.
By default, the DNS resolver will listen on all interfaces, but this is most useful for the LAN interface and for interfaces connected to other local networks (if applicable). - Outgoing Network Interfaces: the interfaces that the DNS resolver can use to send DNS queries to the DNS servers concerned by the domain name to be resolved.
By default, the DNS resolver will be able to use all interfaces, but to resolve existing domain names on the Internet, it will use the WAN interface. - Strict Outgoing Network Interface Binding: by default, the DNS resolver will send DNS queries on all available interfaces if the interfaces selected in the list are not available.
To avoid this behavior and force the DNS resolver to refuse the DNS query in this specific case, check the box "Do not send recursive queries if none of the selected Outgoing Network Interfaces are available". - System Domain Local Zone Type: allows you to choose which type of local zone will be used in "unbound" (= the DNS resolver).
If there is a match in the local data (host replacement, DHCP hosts, ...), a normal response will always be returned to the client.
But in case there is no match in the local data, the type selected here will define the behavior to be adopted in this case.- Deny: delete the client's DNS query and do not respond to it.
- Refused: responds to the client with a REFUSED rcode. In this case, the client clearly knows that its DNS request was refused. This was not the case with "Deny" where the client receives no response.
- Static: return a NODATA or NXDOMAIN response to the client.
- Transparent: default behavior. If the DNS query concerns a locally existing name, it will be resolved normally. But, if there is a match and the data type does not match, then a NOERROR or NODATA response will be sent to the client.
- Type Transparent: similar to "Transparent", but the DNS resolver will also use queries where the name exists, but the type does not match. This allows the request to be transmitted instead of returning a negative response.
- Redirect: manage query from local data to control queries for all subdomains of a specific domain.
- Inform: respond normally to the client, but also record the client's DNS request in the logs.
- Inform Deny: refuse the request and also record the client's DNS request in the logs.
- No Default: disable the default content of the DNS zone without altering DNS queries.
- DNSSEC: enables DNSSEC support (DNS zone signing) so clients can trust the origin and content of DNS responses. To do this, check the "Enable DNSSEC Support" box.
However, this requires the use of root DNS servers or forwarding servers that also support DNSSEC. - Python Module: allows you to activate the DNS resolver Python module to be able to act on DNS queries or their results.
To enable this Python module, check the "Enable Python Module" box. - DNS Query Forwarding: if the "Enable Forwarding Mode" box is checked, the DNS resolver will redirect DNS queries using the pfSense DNS Forwarder to the DNS servers configured via the "System -> General Setup" menu or those whose IP addresses were dynamically received on interfaces via DHCP, PPP or OpenVPN (if "DNS Server Override" is enabled there).
- Use SSL/TLS for outgoing DNS Queries to Forwarding Servers: if checked, DNS queries sent through the DNS forwarder will be sent on port 853 of remote DNS servers using SSL/TLS.
This option requires that the "DNS Query Forwarding" option is enabled and that remote DNS servers support DNS queries via SSL/TLS on port 853. - DHCP Registration: check the box "Register DHCP leases in the DNS Resolver" if you want to register the name of DHCP clients in the DNS resolver.
The root domain name that will be used is that defined in "System -> General Setup". - Static DHCP: check the box "Register DHCP static mappings in the DNS Resolver" if you want to register the names of DHCP clients with static mappings in the DNS resolver.
Again, the root domain that will be used will be that defined in "System -> General Setup". - OpenVPN Clients: same, but for VPN clients. To enable this option, check the "Register connected OpenVPN client in the DNS Resolver" box.
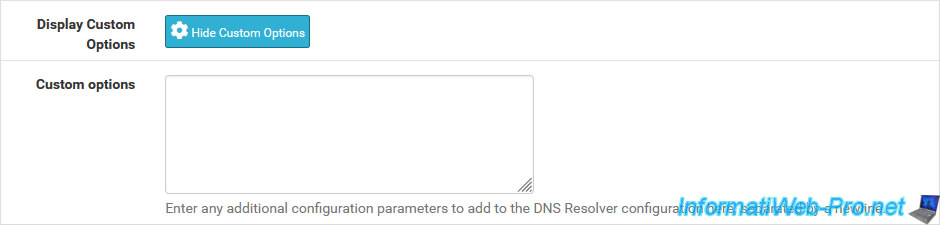
- Display Custom Options: allows you to add additional options for "unbound" (which DNS Resolver is based on) that are not available in the form below.
If necessary, add "server:" to the beginning of the 1st line if "unbound" stops working from the moment you enter something here.
Source : DNS Resolver Configuration | pfSense Documentation.
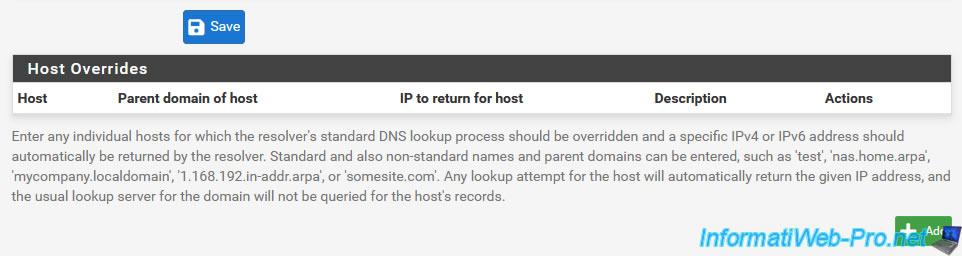
At the bottom of the page, you will find a "Host Overrides" section that will allow you to change the DNS response for a specific domain name (or subdomain).
Which can be useful for blocking access to specific websites, even if the user can always bypass this protection by directly typing the IP address of the desired site or by modifying their "hosts" file (if he has the necessary right to modify it).
Source : Host Overrides | pfSense Documentation.
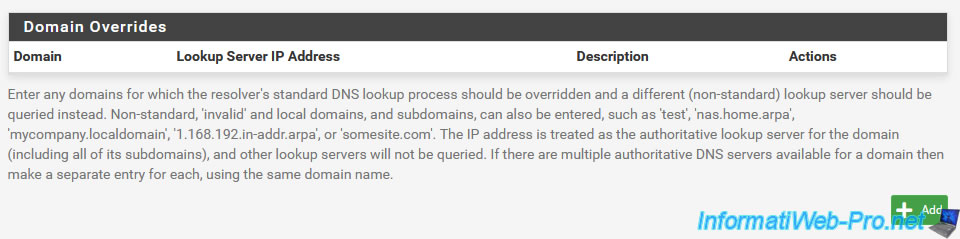
Just below you will also find a "Domain Overrides" section.
This time, it will allow you to resolve specific domains using specific DNS servers.
Which can be used to resolve the domain names of an Active Directory infrastructure using the relevant Active Directory domain controller, for example.
This is primarily used to resolve internal domain names from remote sites (via a VPN tunnel).
This allows configuration of DNS zones to be managed only at the company headquarters, while allowing each site (geographic location) to cache responses to speed up access to commonly requested DNS data.
Source : Domain Overrides | pfSense Documentation.
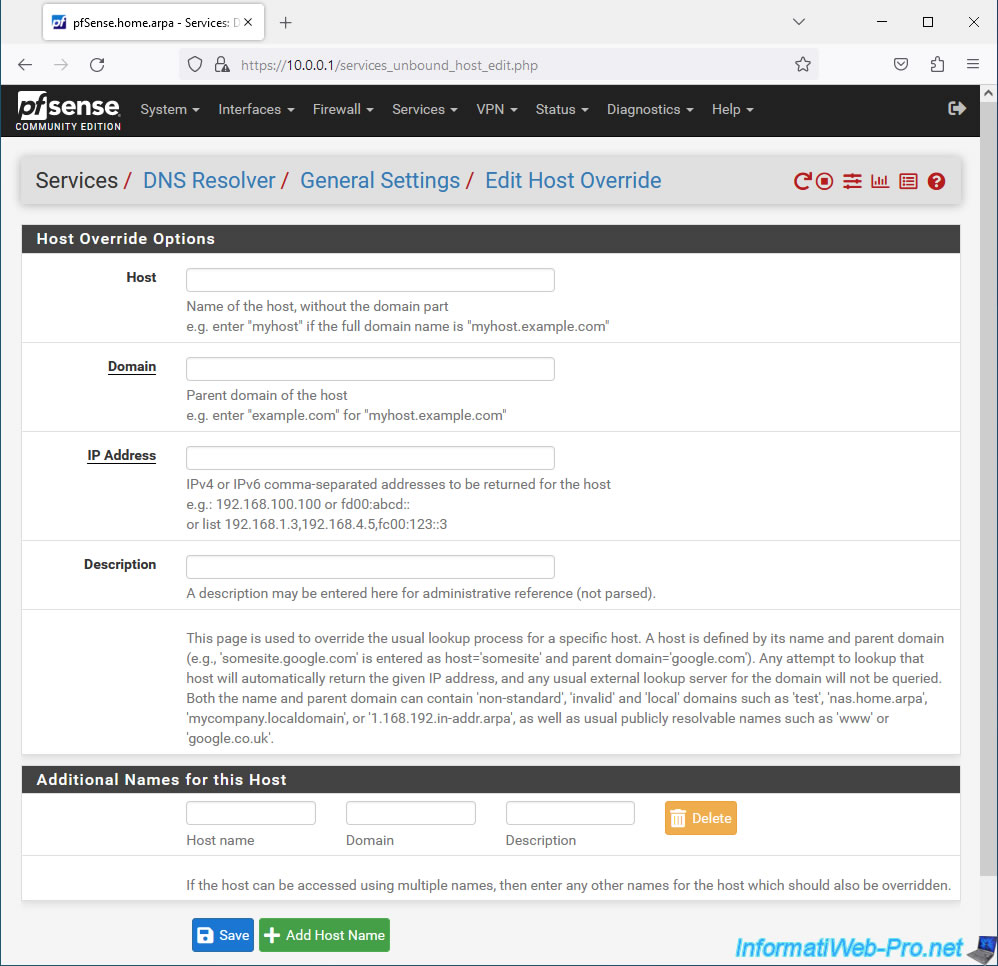
When you want to add a Host Override, a "Host Override Options" form will appear where you can specify the settings:
- Host: the host name or in other words, the subdomain for which you want to modify the DNS response.
Ex: www. - Domain: the relevant root domain name for which you want to change the DNS response.
Ex: test-domain.com. - IP Address: the IPv4 and/or IPv6 address(es) that pfSense must return for the DNS response.
You can specify one or more addresses by separating them with commas. - Description: a description that pfSense will display for this host replacement.
This will be purely indicative. - Additional Names for this Host: if a host is accessible through multiple domain names, you can add these additional host names, as well as the domain for each of these host names to the same host replacement rule.
Thus, all host names of the same host will be redirected to the same IP address without having to create several rules for it. - Add Host Name: this button simply allows you to add "Host name / Domain / Description" lines in the "Additional Names for this Host" section.
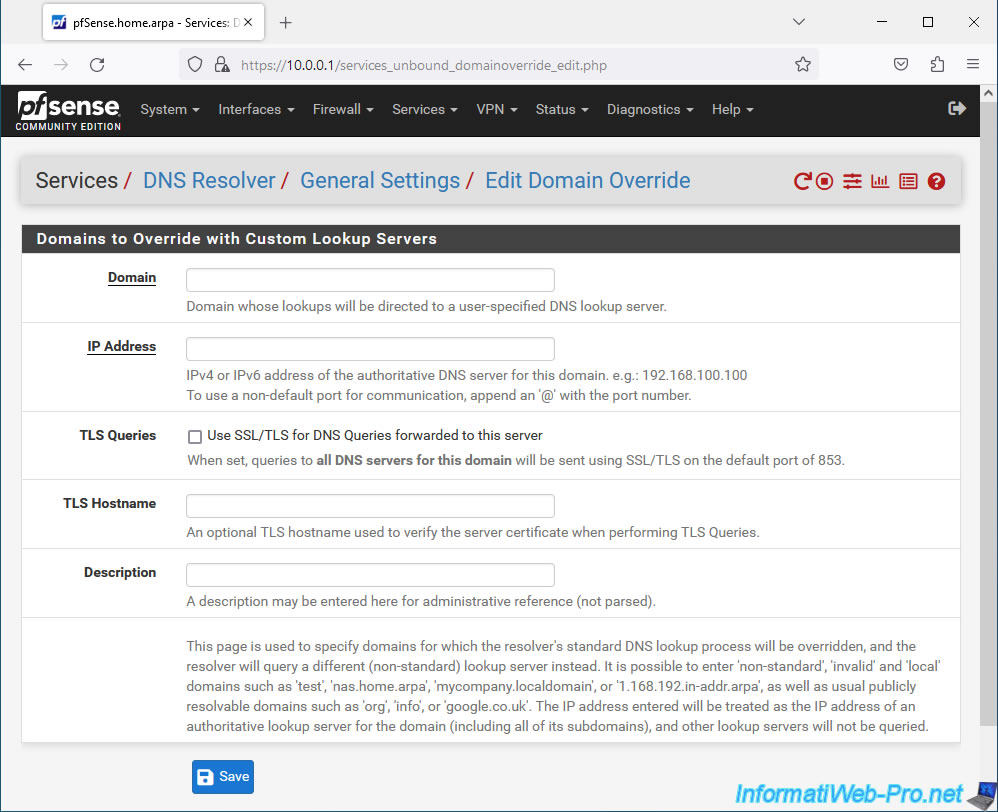
When you want to add a Domain Override, a "Domains to Override with Custom Lookup Servers" form will appear where you can specify the settings :
- Domain: the domain for which pfSense will use a different DNS server to respond to DNS queries from client machines.
- IP Address: the IPv4 or IP6 address of an authoritative DNS server for this domain.
For example: the address of an Active Directory domain controller to allow client machines to resolve your company's Active Directory domain name. - TLS Queries: send DNS queries using SSL/TLS to all DNS servers for this domain.
To do this, check the "Use SSL/TLS for DNS Queries forwarded to this server" box.
However, this requires that the DNS servers concerned support the use of SSL/TLS and that port 853 of these is therefore reachable. - TLS Hostname: an optional hostname to validate the SSL/TLS server certificate.
- Description: a purely indicative description which only appears under pfSense.
2. DNS Forwarder
To resolve existing domain names on the Internet, pfSense can redirect DNS queries to other DNS servers using its DNS Forwarder using the dnsmasq daemon.
Note that this DNS forwarder only forwards DNS queries to other DNS servers (those specified in "System -> General Setup and those obtained dynamically on the WAN interface via DHCP, PPPoe, ...).
The DNS forwarder also caches received responses to speed up responses for future clients making the same DNS requests.
To configure this DNS forwarder, go to: Services -> DNS Forwarder.
Source : DNS Forwarder | pfSense Documentation.
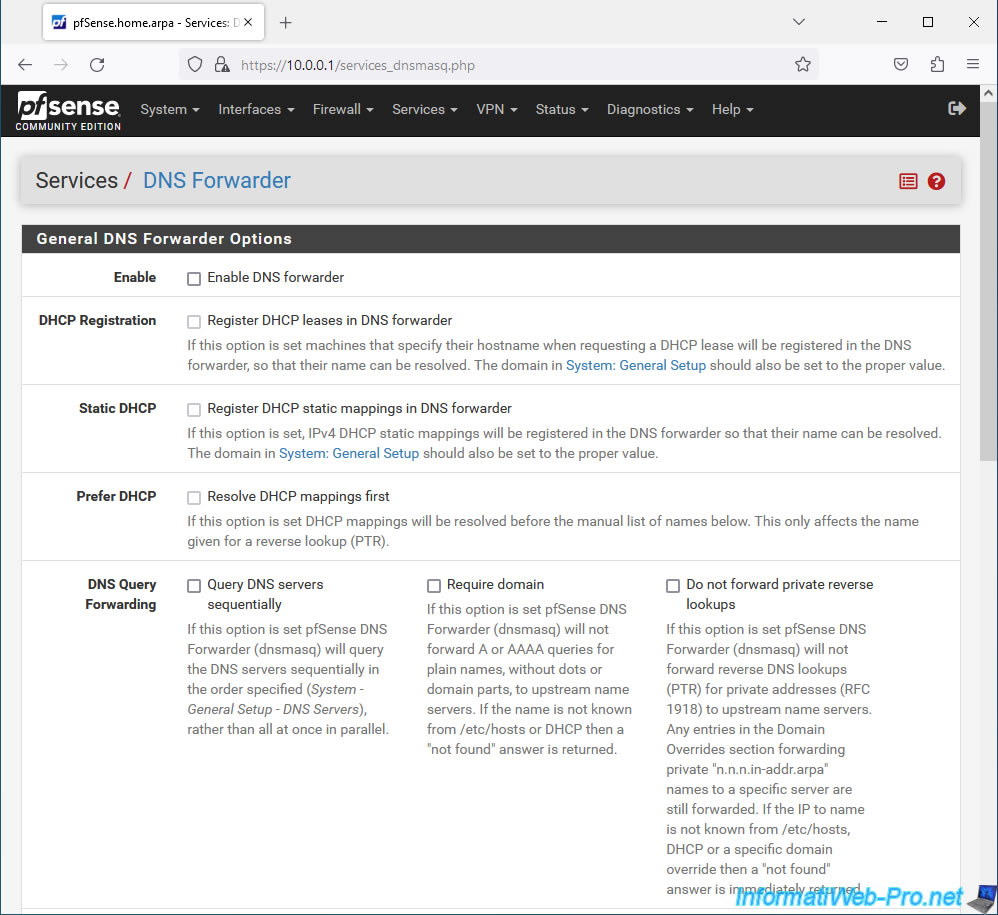
On the "DNS Forwarder" page which will appear with a "General DNS Forwarder Options" section, you can configure the settings:
- Enable: check the "Enable DNS forwarder" box to enable this DNS forwarder.
- DHCP Registration: allows you to register the host name of DHCP clients in the DNS forwarder.
The root domain used will be that indicated in "System -> General Setup".
To do this, check the "Register DHCP leases in DNS Forwarder" box. - Static DHCP: Similar to the previous option, but for DHCP clients with static IPv4 mappings.
- Prefer DHCP: check the "Resolve DHCP mappings first" box to use the DNS records of DHCP clients as a priority.
This only impacts reverse DNS lookups (getting the hostname matching an IP address).
Indeed, if an IP address corresponds to several host names, the reverse DNS lookup may return a name other than that used by the DHCP client. This option therefore resolves the problem. - DNS Query Forwarding:
- Query DNS servers sequentially: allows you to query DNS servers sequentially in the order in which they are specified in "System -> General Setup" rather than sending the DNS query to all DNS servers at the same time.
- Require domain: specifies whether the DNS forwarder requires a domain name for the host names to be forwarded to the DNS servers specified in "System -> General Setup".
- Do not forward private reverse lookups: specifies whether the DNS forwarder can perform reverse DNS lookups for private IP addresses (RFC1918) using the DNS servers specified in "System -> General Setup".
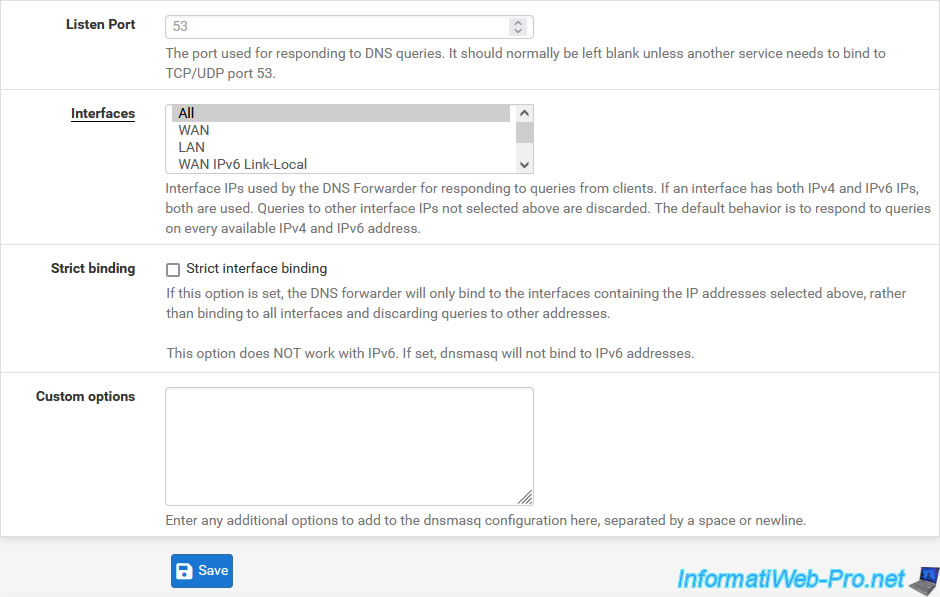
- Listen Port: the port to listen on. Defaults to port 53.
- Interfaces: interfaces on which the DNS forwarder should listen, accept, and respond to DNS queries.
- Strict binding: if you check the "Strict interface binding" box, the dnsmasq daemon will only bind to the interfaces selected above.
Please note: this option is not compatible with IPv6. The dnsmasq daemon will therefore not bind to the IPv6 addresses of the interfaces selected above - Custom options: allows you to add additional configuration options to the dnsmasq daemon that would not be available above.
Note that this DNS forwarder will only be used by the pfSense DNS Resolver if the "DNS Query Forwarding" option is enabled in the DNS Resolver configuration.
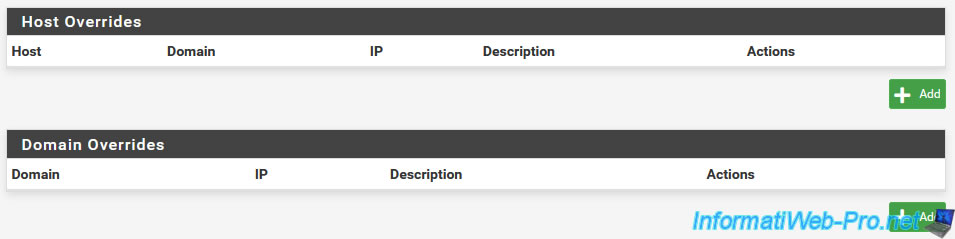
Once again, you will find the "Host Overrides" and "Domain Overrides" sections also available for the DNS resolver and whose principle is therefore the same.
For more information on these 2 sections, refer to the explanations given previously for the DNS resolver.
Share this tutorial
To see also
-

Firewall 6/25/2025
pfSense 2.6 - 1:1 NAT (IP address mapping)
-

Firewall 8/8/2025
pfSense 2.6 - Configure a LACP link (LAGG)
-

Firewall 6/6/2025
pfSense 2.6 - DDNS (dynamic DNS)
-

Firewall 5/9/2025
pfSense 2.6 - Download and installation on VMware Workstation


You must be logged in to post a comment