- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 03 January 2025 at 12:40 UTC
-

When you use a virtual distributed switch (vDS), you have the ability to block traffic through traffic filtering and marking. This allows you to secure your virtual machines and/or services at the virtual network level rather than using third-party software on your virtual machines or virtual servers.
- Enable traffic filtering and marking
- Testing the ping between our virtual machines
- Block network traffic
1. Enable traffic filtering and marking
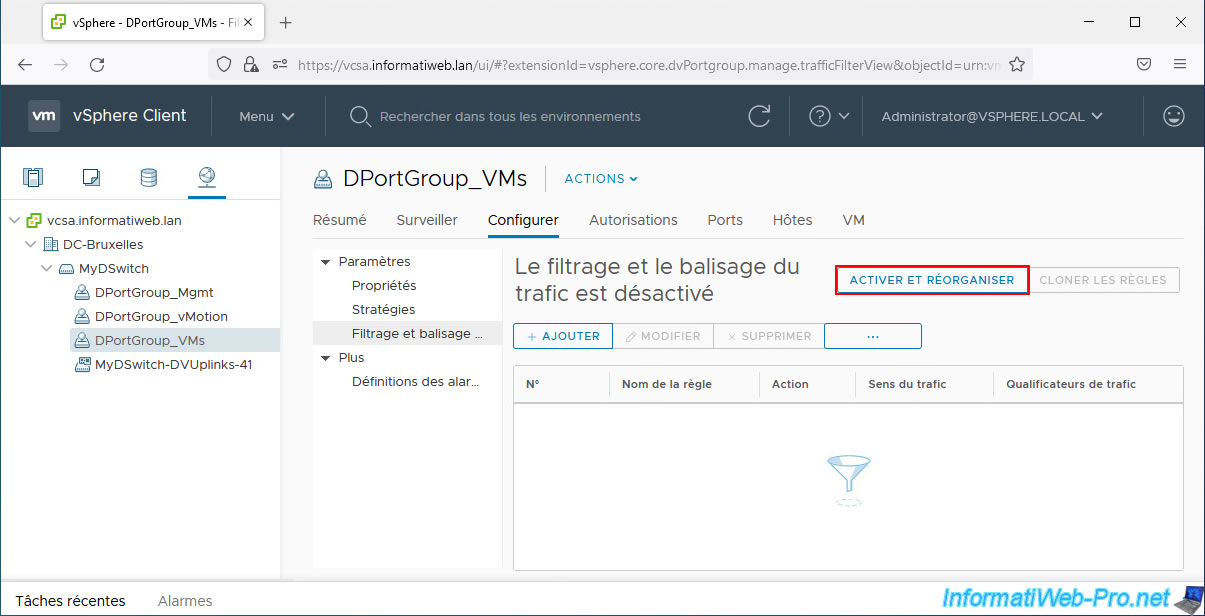
To enable traffic filtering and marking on VMware vCenter Server (VCSA) 6.7, select the desired port group (distributed or uplink) and go to: Configure -> Settings -> Traffic filtering and marking.
As you can see, by default, traffic filtering and marking is turned off.
To activate it, first click on the button: Enable and reorder.
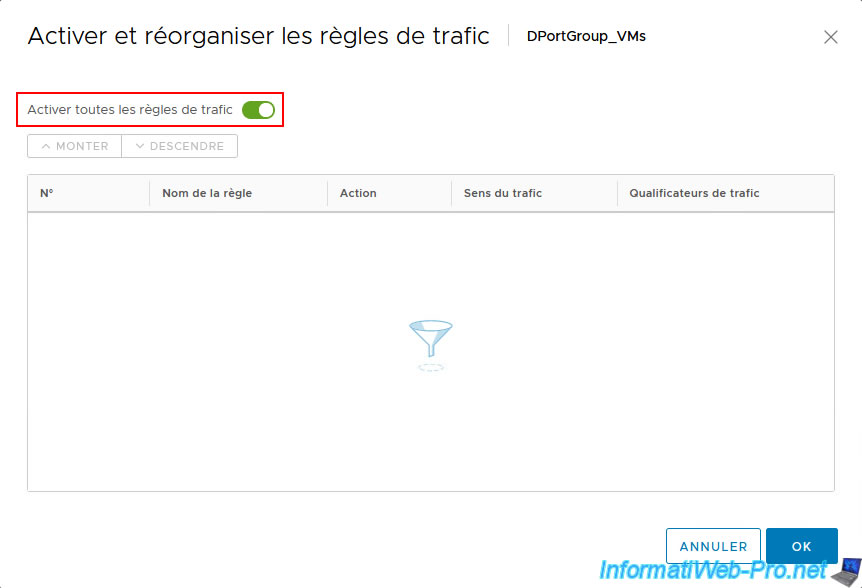
In the “Enable and Reorder Traffic Rules” window that appears, click on the “Enable all traffic rules” switch so that it appears green.
Then click OK.
Note that you can change the order of the traffic rules later if you wish by using the "Move Up" and "Go Down" buttons which are grayed out at the moment.
2. Testing the ping between our virtual machines
For this tutorial, we will create a traffic rule to block ping (whose associated protocol is: ICMP).
As you can see, in our case we have a distributed virtual switch "MyDSwitch" with a distributed port group "DPortGroup_VMs" where we have just enabled traffic filtering and marking and to which our virtual machines are connected under Windows 10.
However, at the moment there are no defined traffic rules. So everything is allowed.
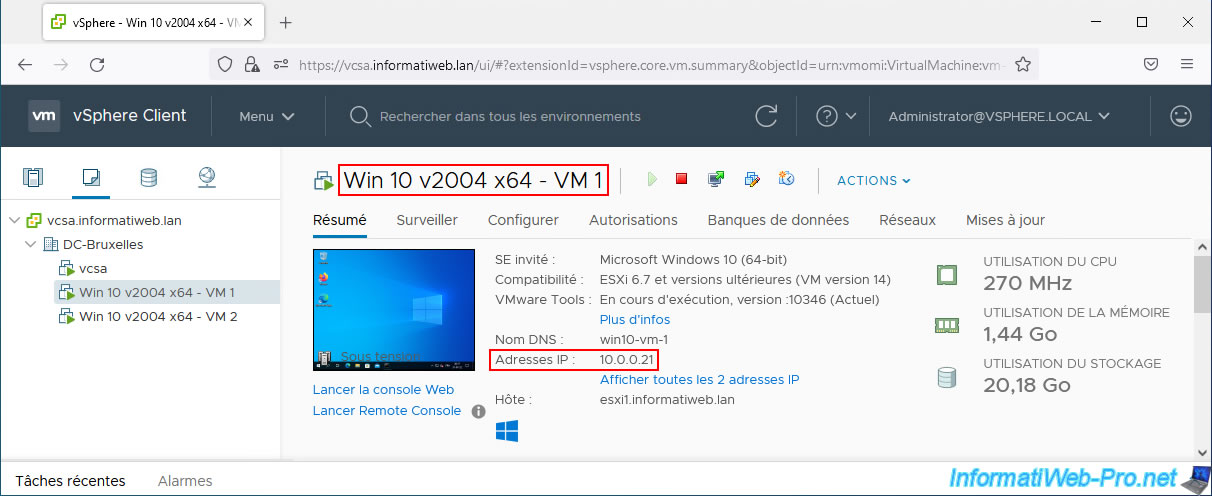
The 1st virtual machine on Windows 10 has the IP address: 10.0.0.21.
The 2nd virtual machine on Windows 10 has the IP address: 10.0.0.22.
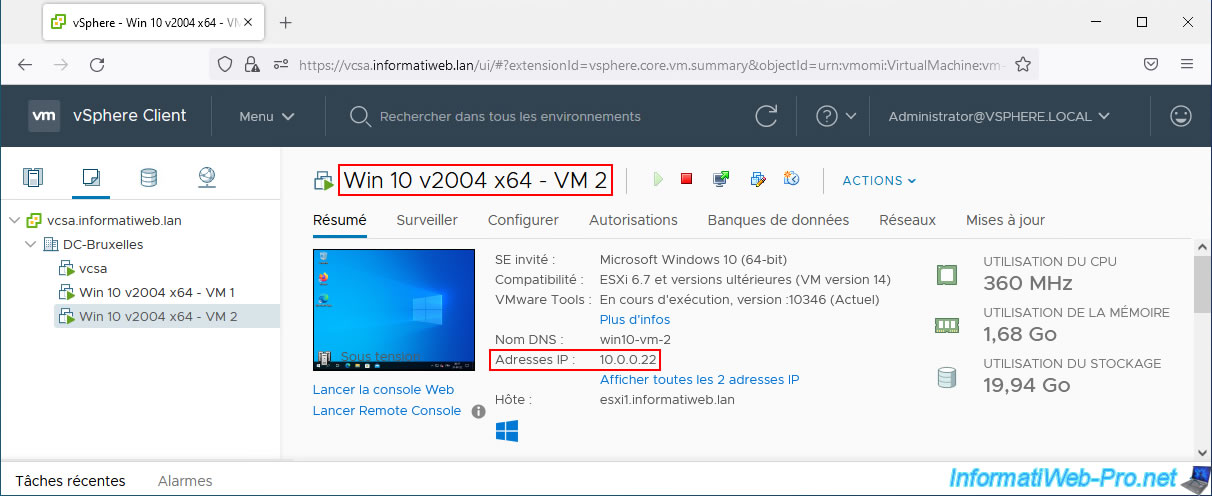
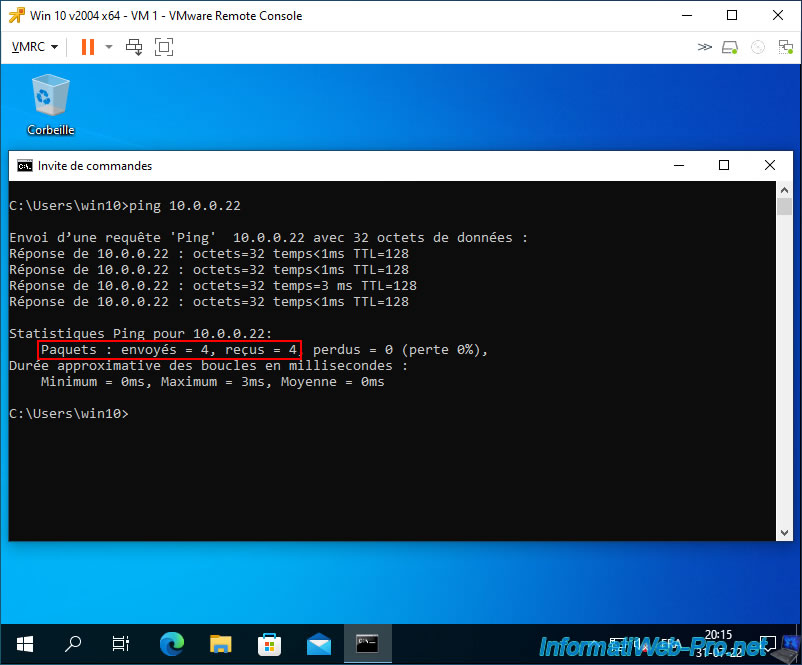
As you can see, for the moment, ping works between our 2 virtual machines on Windows 10.
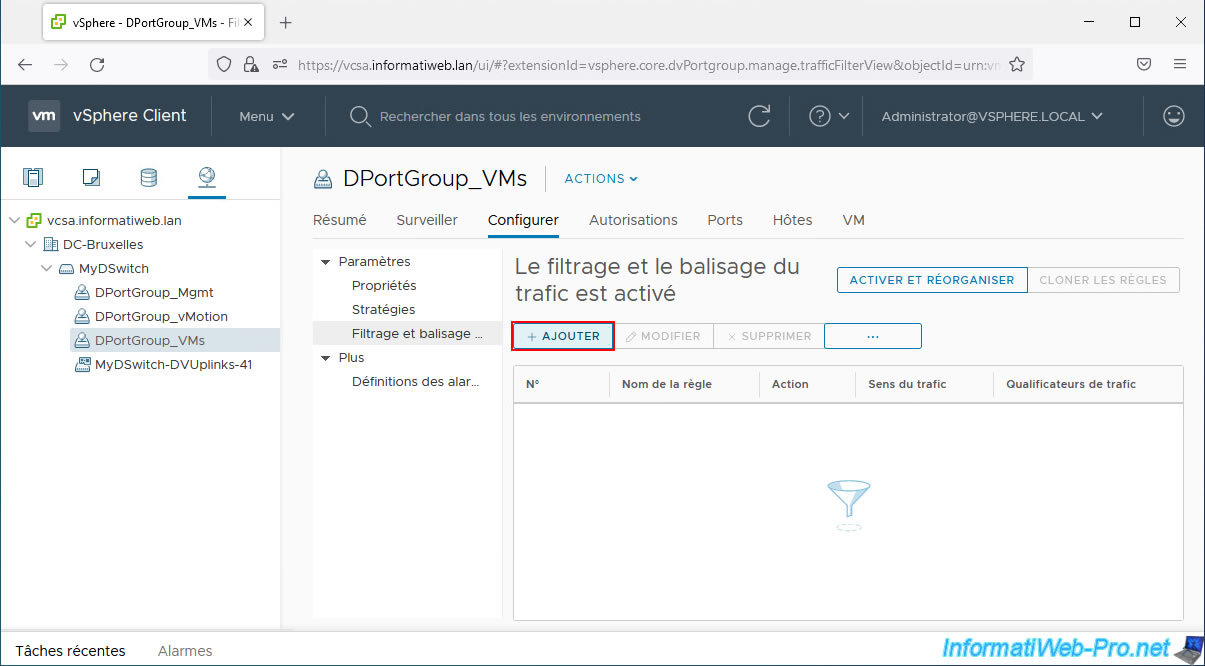
3. Block network traffic
To block some network traffic, select the desired port group and return to: Configure -> Settings -> Traffic filtering and marking.
As you can see, the message “Traffic filtering and marking is Turned ON” appears.
Click: Add.
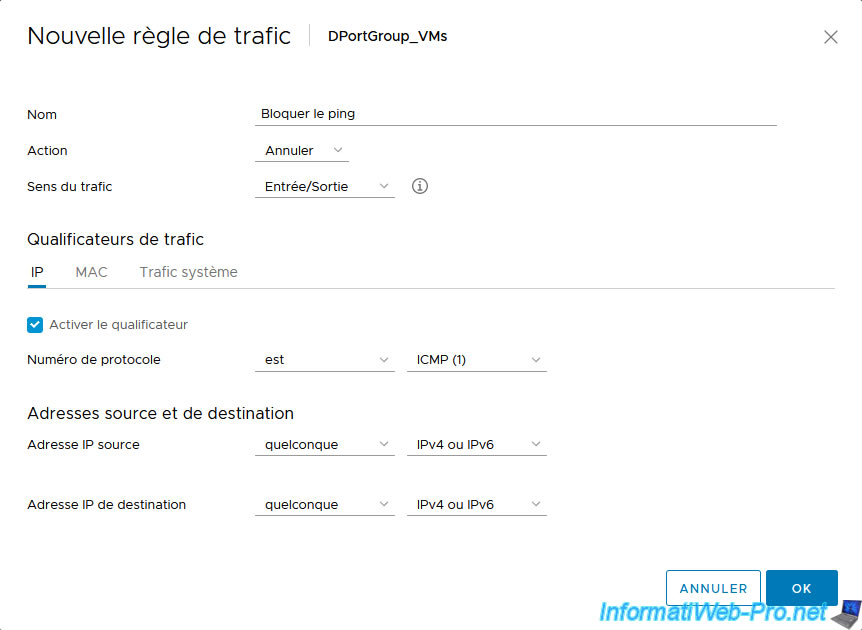
In the “New Traffic Rule” window that appears, you can specify:
- Name: the name under which this traffic rule will appear in the list.
- Action :
- Allow: allow the desired network traffic.
- Drop: block the desired network traffic.
- Tag: allows you to tag the desired network traffic to create QoS (quality of service) rules using CoS (layer 2) or DSCP (layer 3) tags.
- Traffic direction :
- Ingress/Egress : blocks incoming and outgoing virtual distributed switch (vDS) traffic.
- Egress : only blocks outbound virtual distributed switch (vDS) traffic.
- Ingress : only blocks traffic entering the virtual distributed switch (vDS).
- Traffic Qualifiers :
- IP : allows you to specify a condition based on:
- a protocol: ICMP, IPv6-ICMP, TCP or UDP.
If you select TCP or UDP, you will be able to specify a source and/or destination port number.
Which can allow you to block access to a website (by blocking TCP ports 80 and 443), to an FTP server (by blocking TCP port 21), ... - a source IPv4 or IPv6 address.
- a destination IPv4 or IPv6 address.
- a protocol: ICMP, IPv6-ICMP, TCP or UDP.
- MAC : allows you to specify a condition based on:
- a type of network traffic: IPv4, IPv6 or ARP.
- a VLAN ID
- a source MAC address.
- a destination MAC address.
- System traffic: allows you to specify a condition based on the type of system traffic detected (management, vMotion, ...).
Note that this corresponds to inbound traffic on distributed port groups and outbound traffic on uplink port groups.
- IP : allows you to specify a condition based on:
To block ping, configure the traffic rule like this:
- Name: Block ping.
- Action: Drop.
- Direction of traffic: Ingress/Egress.
- In the "IP" section, check the "Enable qualifier" box and configure these options:
- Protocol number is ICMP (1).
- Source IP address: any / IPv4 or IPv6.
- Destination IP address: any / IPv4 or IPv6.
Then click OK.
The created traffic rule appears.
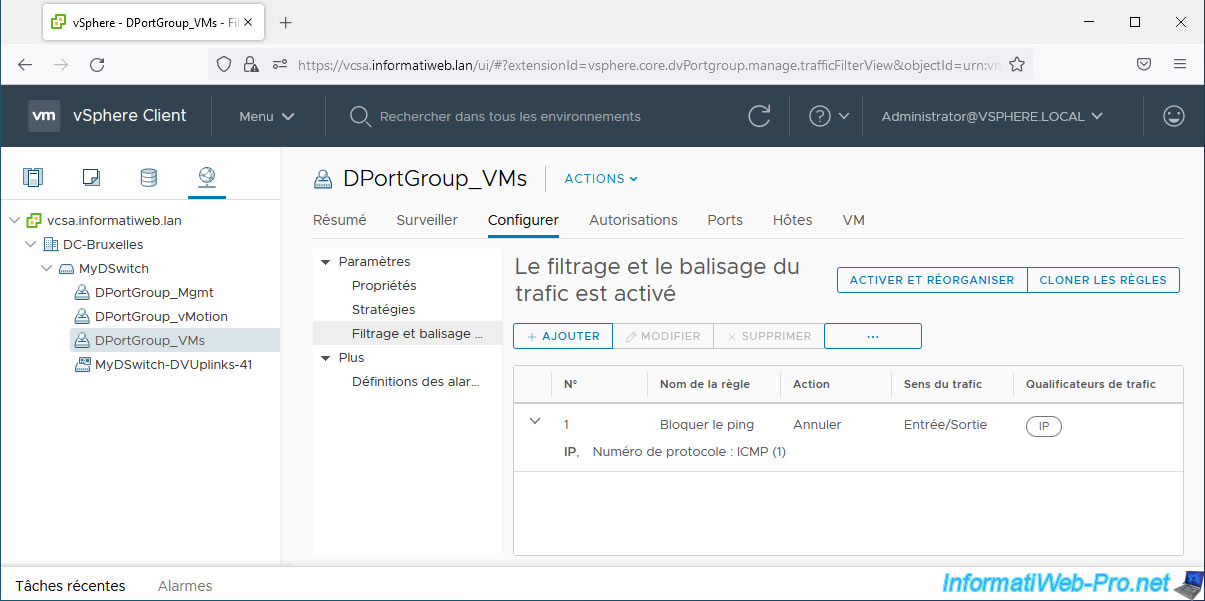
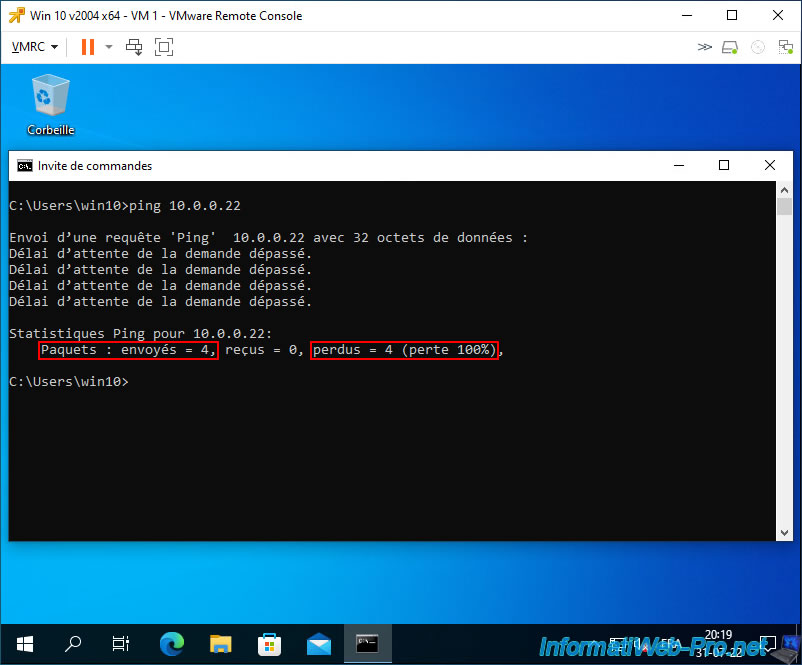
As you can see, ping no longer works between our 2 virtual machines on Windows 10.
As the ping command tells you, the 4 packets sent were lost.
Share this tutorial
To see also
-
VMware 4/7/2023
VMware ESXi 6.7 - How memory (RAM) management works
-

VMware 12/2/2022
VMware ESXi 6.7 - Install and use the VMRC console on Linux
-
VMware 1/24/2025
VMware vSphere 6.7 - Create a network protocol profile
-
VMware 10/2/2024
VMware vSphere 6.7 - Improve the performance by using a physical HDD


You must be logged in to post a comment