Create private VLANs (PVLANs) on a vDS switch on VMware vSphere 6.7
- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 17 January 2025 at 12:34 UTC
-

- 2/2
5. Connect virtual machines on private VLANs (PVLANs)
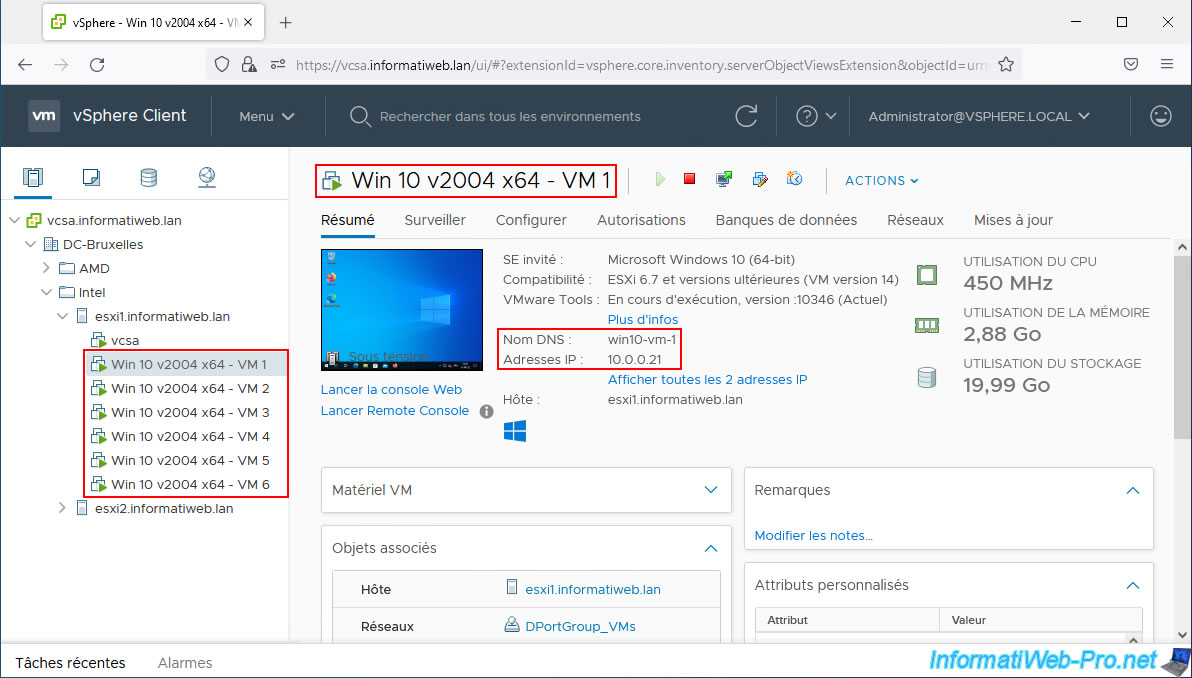
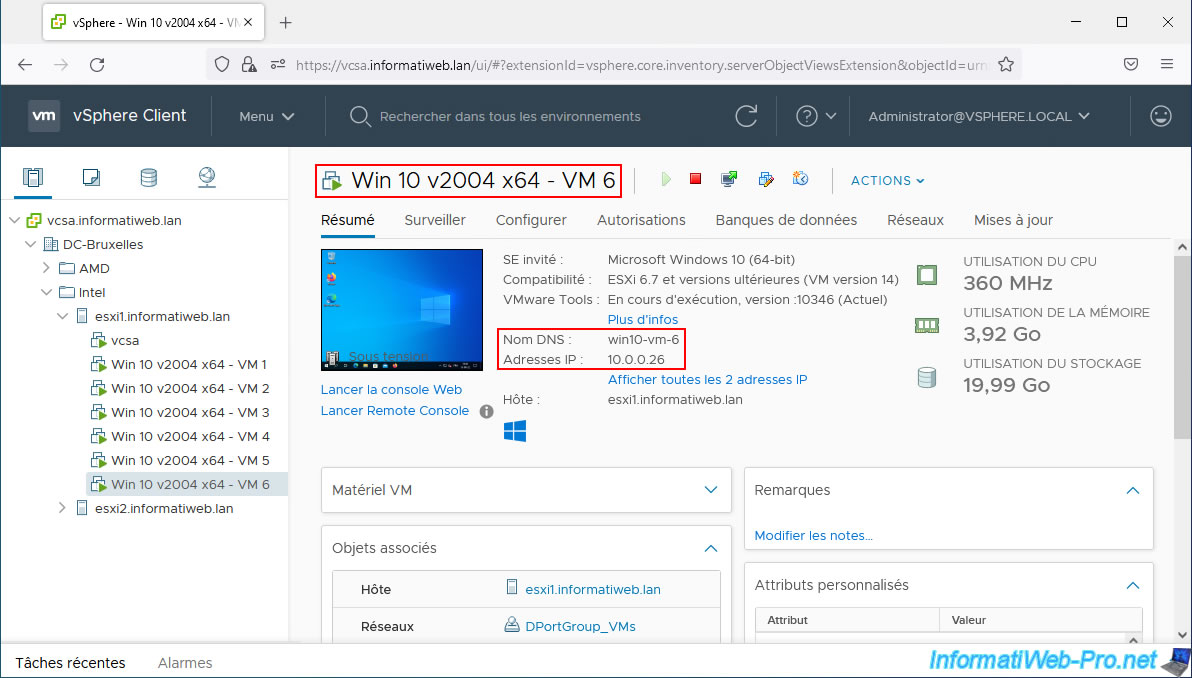
For this tutorial, we used 6 virtual machines running Windows 10 that we placed on the same host.
These 6 virtual machines use an IP address "10.0.0.2x" and a name "win10-vm-x" where "x" corresponds to the number of the VM concerned.
Important : It is important that these virtual machines are on the same host for private VLANs (PVLANs) to work as expected (regardless of your physical hardware).
Indeed, this allows you to use only the virtual network available on your host (and more precisely the "Host proxy switch" implemented from the configuration of your vDS).
Otherwise, you will need a switch that supports private VLANs (PVLANs).
For example, the "Cisco Catalyst 3750" switch: Catalyst 3750 Switch Software Configuration Guide, 12.2(25)SEE - Chapter: Configuring Private VLANs.
To test network connectivity within each private VLAN (PVLAN) and between private VLANs (PVLANs), place at least 2 virtual machines per private VLAN.
In our case, we will connect:
- VMs 1 and 2 on the private VLAN (PVLAN) in “Promiscuous” mode.
- VMs 3 and 4 on the private VLAN (PVLAN) in “Isolated” mode.
- VMs 5 and 6 on the private VLAN (PVLAN) in “Community” mode.
To begin, modify the settings of the 1st VM.
Click on the port group to which its network adapter is connected and click: Browse.
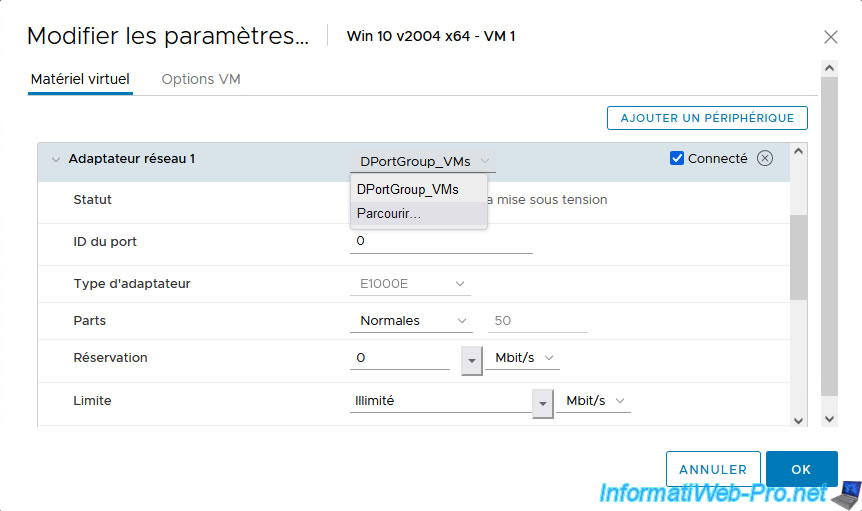
In the "Select Network" list that appears, you will see the existing port groups on your virtual distributed switch(es) (vDS). Including, the new port groups "vDS_PVLAN_xxx_..." that you have just created to use your new private VLANs.
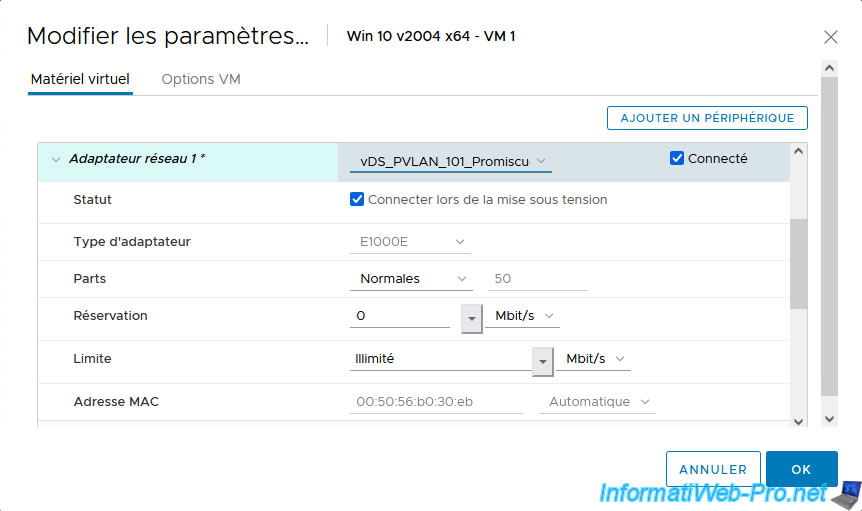
For VM 1 and 2, select the "vDS_PVLAN_101_Promiscuous" port group so that they are connected to your private VLAN in "Promiscuous" mode (VLAN ID: 101), then click OK.
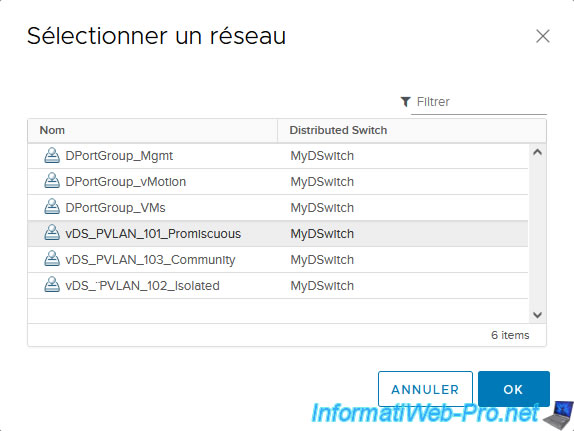
Then click: OK.
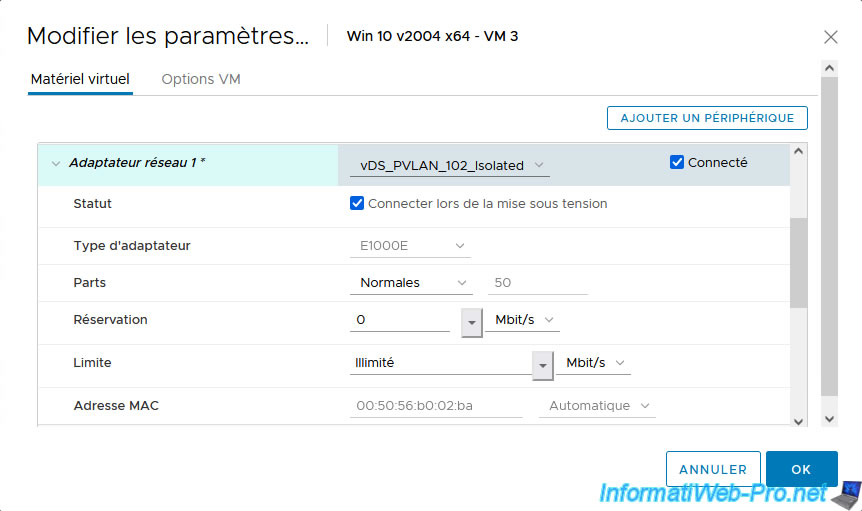
For VMs 3 and 4, select "vDS_PVLAN_102_Isolated".
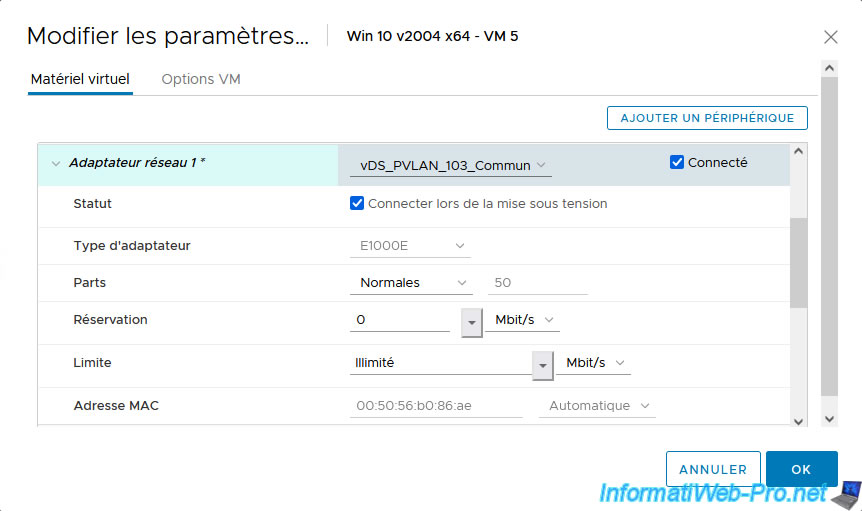
For VMs 5 and 6, select "vDS_PVLAN_103_Community".
Once your virtual machines are configured, select each distributed port group and go to the “VM” tab.
You should get this.
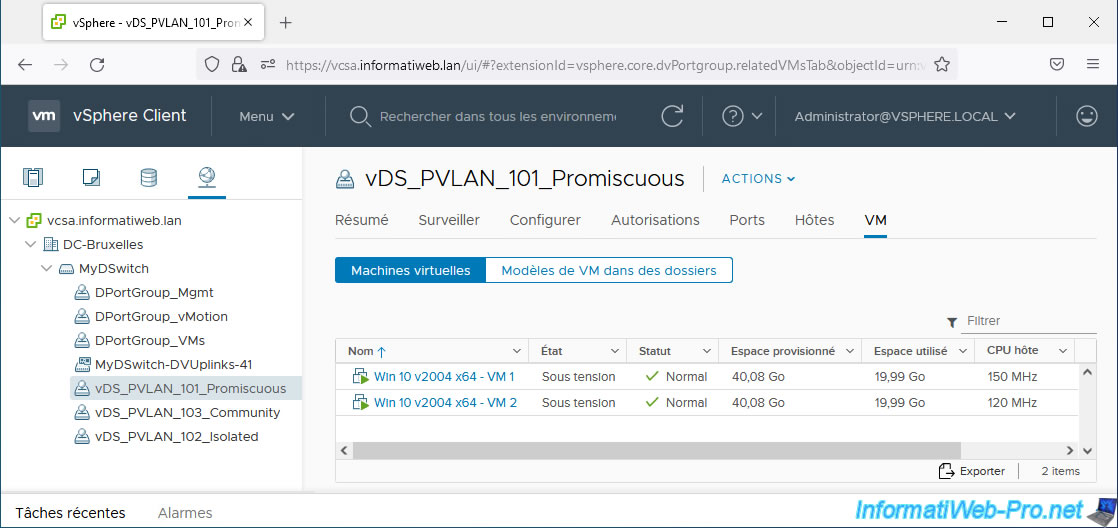
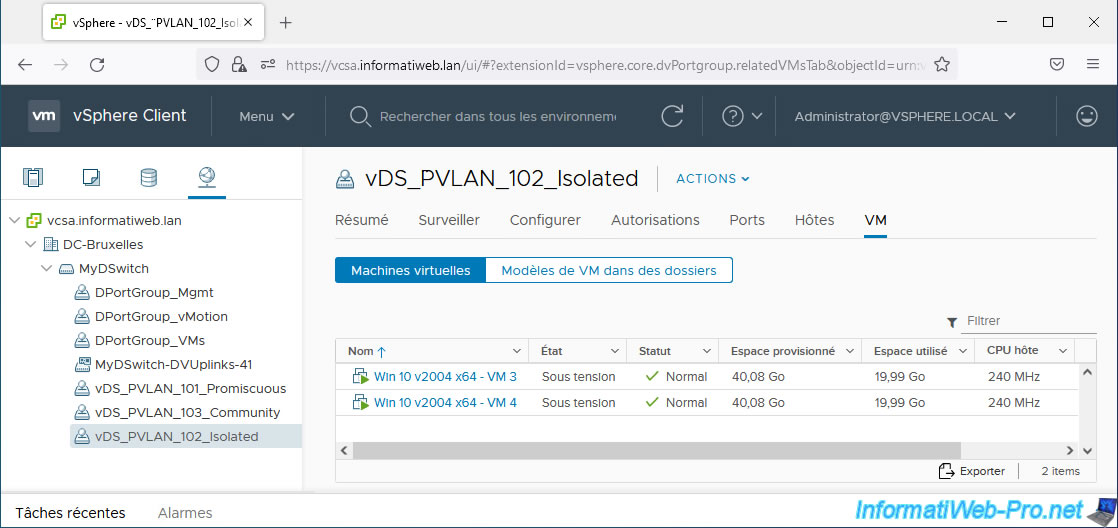
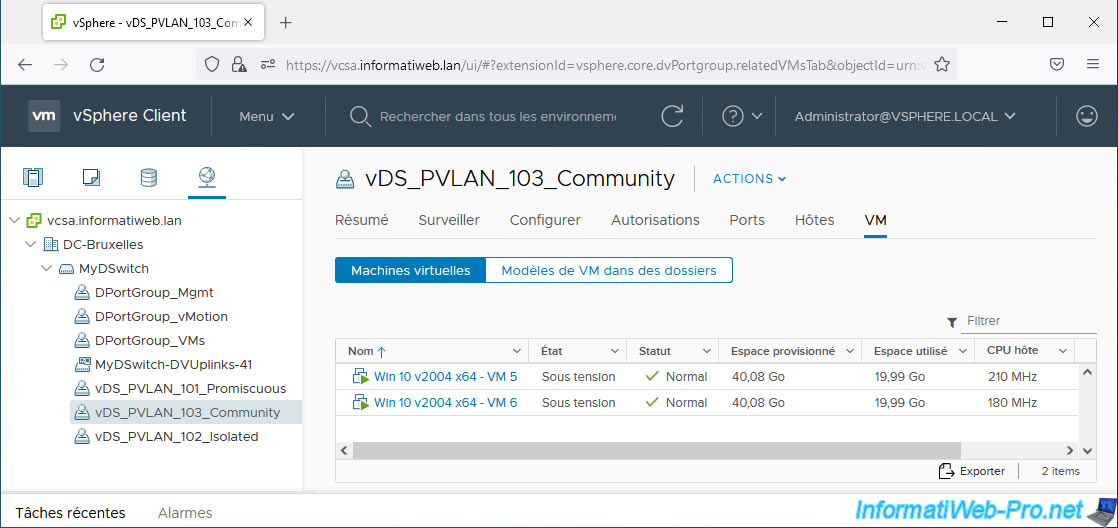
6. Testing network connectivity within and between private VLANs
To demonstrate how the different modes of private VLANs (PVLANs) work, we will attempt to ping the virtual machine present in the same private VLAN as the source virtual machine, as well as virtual machines connected to other types of private VLANs.
6.1. Testing network connectivity with a private VLAN (PVLAN) in mode: Promiscuous
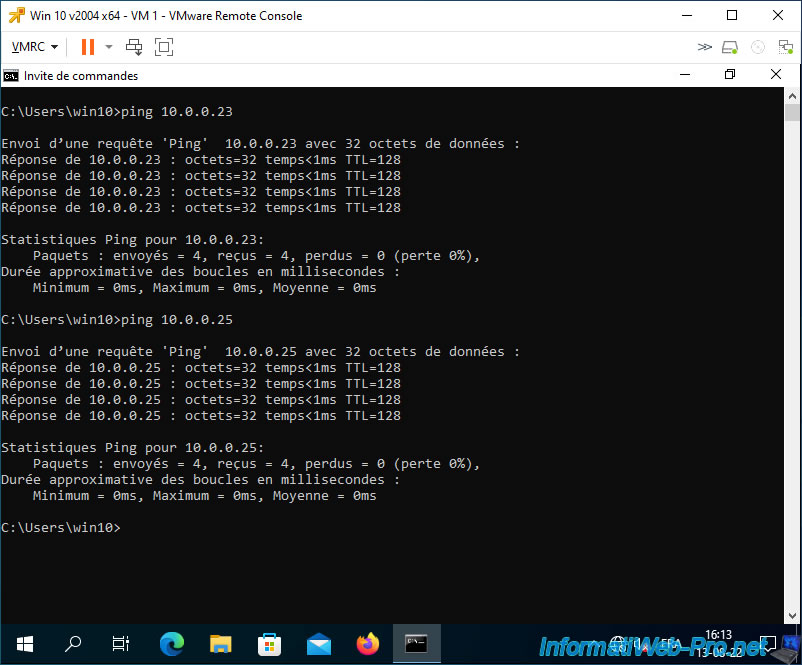
To begin with, you can see that VM 1 (IP: 10.0.0.21) can communicate with VM 2 (IP: 10.0.0.22) which is in the same private VLAN in "Promiscuous" mode.
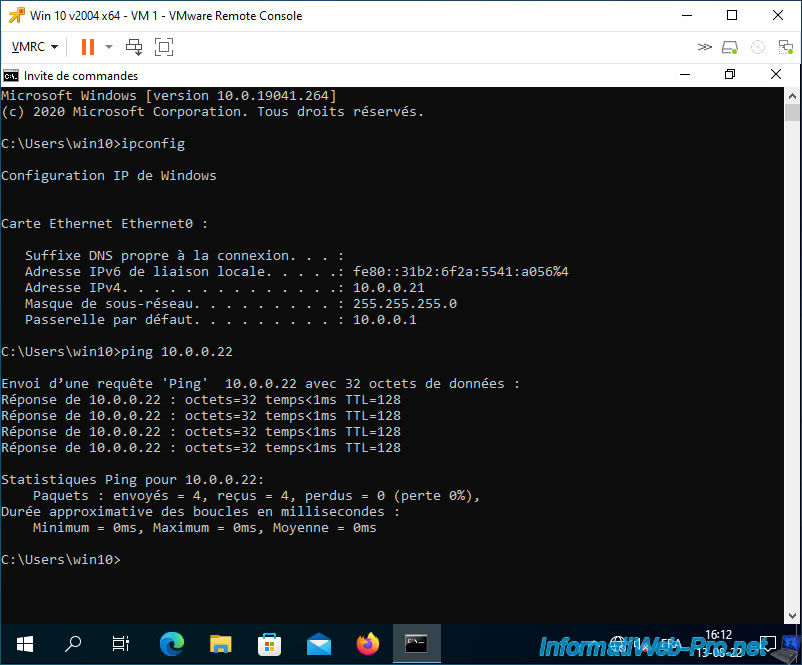
Since the virtual machine is in a private VLAN in "Promiscuous" mode, it can also communicate with other virtual machines that are in other private VLANs.
In this case, it can communicate with VMs 3 and 4 which are in the private VLAN in "Isolated" mode and it can also communicate with VMs 5 and 6 which are in the private VLAN in "Community" mode.
6.2. Testing network connectivity with a private VLAN in mode: Isolated
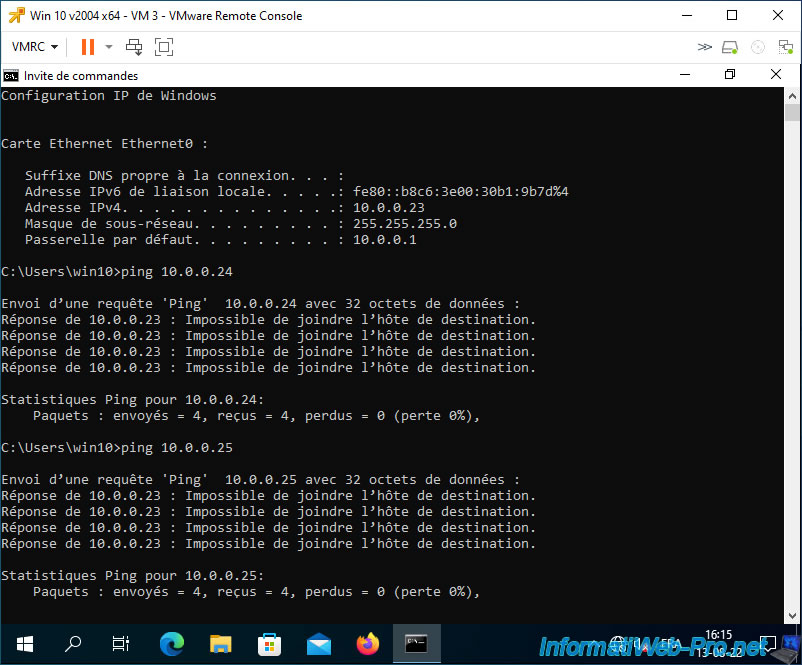
As expected, VM 3 which is in a private VLAN in "Isolated" mode cannot communicate with virtual machine 4 despite being in the same private VLAN in "Isolated" mode.
This VM 3 also cannot communicate with virtual machines 5 and 6 located in a private VLAN in "Community" mode.
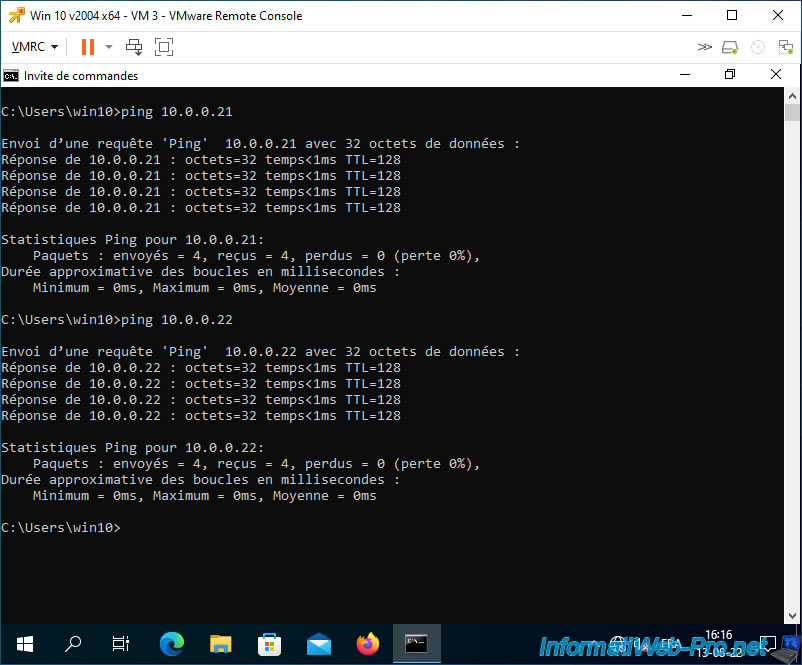
On the other hand, VM 3 can communicate with virtual machines located in a private VLAN in “Promiscuous” mode.
Indeed, all virtual machines in a private VLAN in "Promiscuous" mode can communicate with all virtual machines in your private VLANs.
6.3. Testing network connectivity with a private VLAN in mode: Community
As expected, VM 5 can communicate with VM 6 which is in the same private VLAN in "Community" mode.
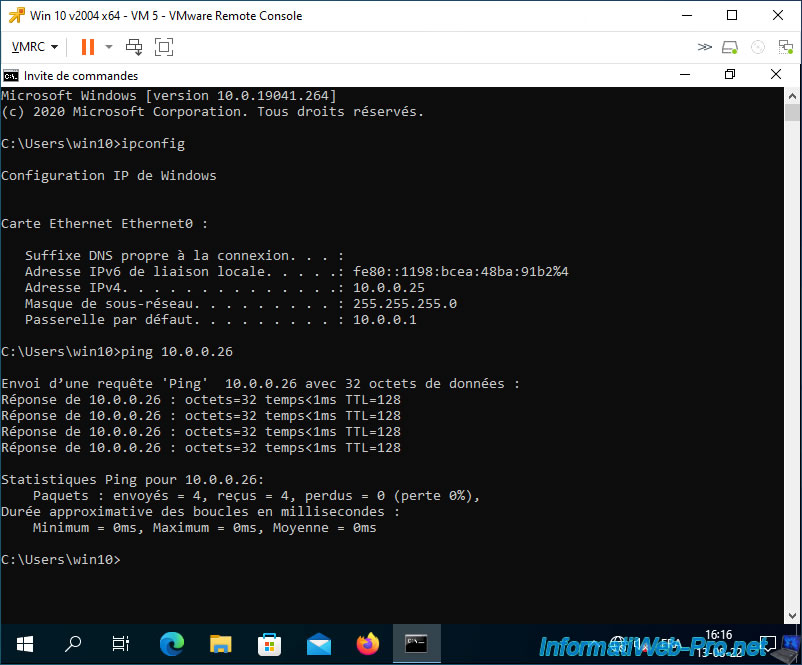
It can also communicate with virtual machines located in a private VLAN in "Promiscuous" mode.
As explained previously, virtual machines connected to a private VLAN in "Promiscuous" mode can communicate with any virtual machine connected to one of your private VLANs (regardless of the private VLAN mode used).
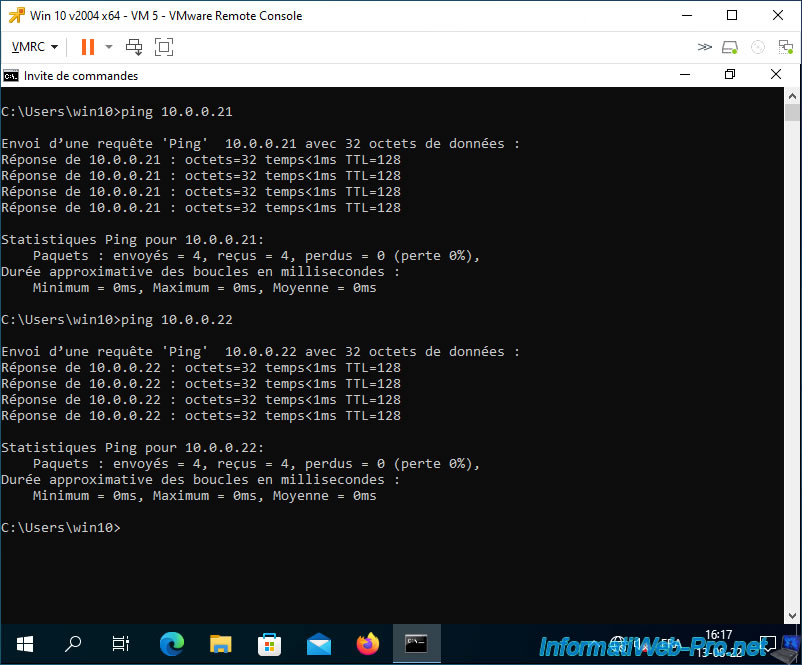
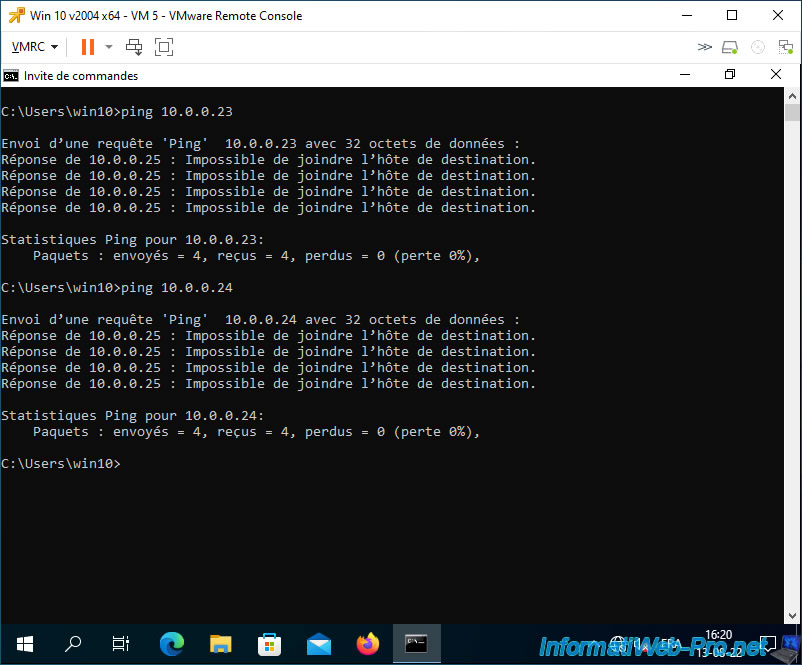
On the other hand, VM 5 and VM 6 cannot communicate with virtual machines located in a private VLAN in "Isolated" mode.
Indeed, virtual machines connected to a VLAN in "Isolated" mode are only accessible from virtual machines connected to a private VLAN in "Promiscuous" mode.
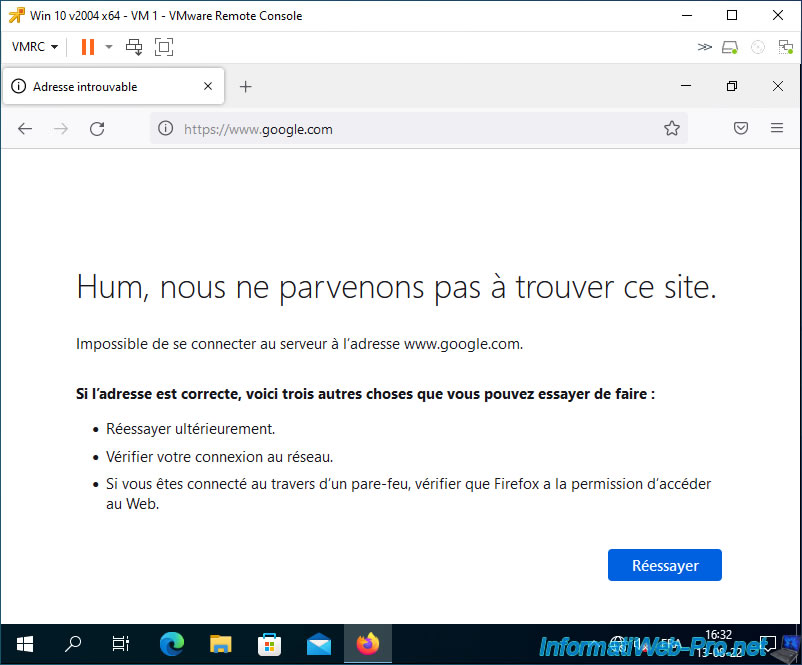
7. Internet inaccessible
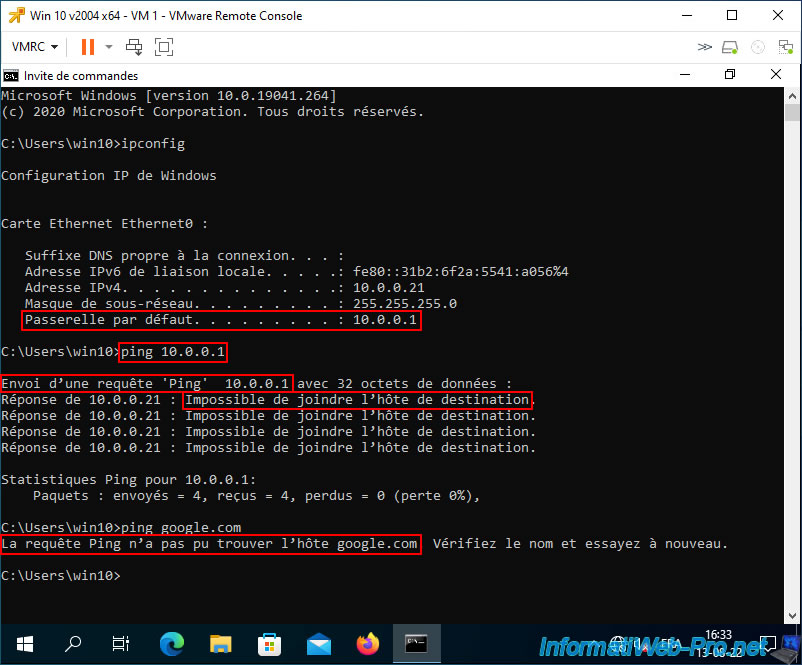
Finally, be aware that by default, without configuring the physical switch where your VMware ESXi host is connected, none of the virtual machines connected to private VLANs will have access to the physical network and the Internet.
Indeed, even your physical switch (default gateway) will not be reachable by your virtual machine.
Share this tutorial
To see also
-

VMware 3/31/2023
VMware ESXi 6.7 - How CPU management works
-

VMware 7/19/2024
VMware vSphere 6.7 - Configure your virtual machines settings
-
VMware 2/14/2025
VMware vSphere 6.7 - Create a cluster
-
VMware 1/22/2025
VMware vSphere 6.7 - Export vDS switch configuration

No comment