- Windows Server
- 03 July 2021 at 11:20 UTC
-

As explained in our "The basics of Active Directory" article, there are 5 FSMO roles in an Active Directory infrastructure.
For each role, you can only have one operation master per forest for the "Schema master" and "Domain naming master" roles, and one operation master per domain for the 3 other FSMO roles : RID master, PDC emulator and infrastructure master.
Here is how to know which controller is designated as master for each of these roles and how to properly transfer an FSMO role (via the graphical interface or from the command line) from one domain controller to another.
- Show operations masters (FSMO roles)
- Properly transfer a FSMO role via the GUI
- Connect an Active Directory console to another domain controller
- Properly transfer a FSMO role from the command line (ntdsutil)
- Transfer the "RID master" FSMO role from the command line (ntdsutil)
- Transfer the "PDC emulator" FSMO role from the command line (ntdsutil)
- Transfer the "Infrastructure master" FSMO role from the command line (ntdsutil)
- Transfer the "Domain naming master" FSMO role from the command line (ntdsutil)
- Transfer the "Schema master" FSMO role from the command line (ntdsutil)
- Quit ntdsutil
- Check that FSMO roles have been transferred
1. Show operations masters (FSMO roles)
To display the operations masters uniques by domain, open the "Active Directory Users and Computers" console and right-click "Operations masters" on your Active Directory domain name.
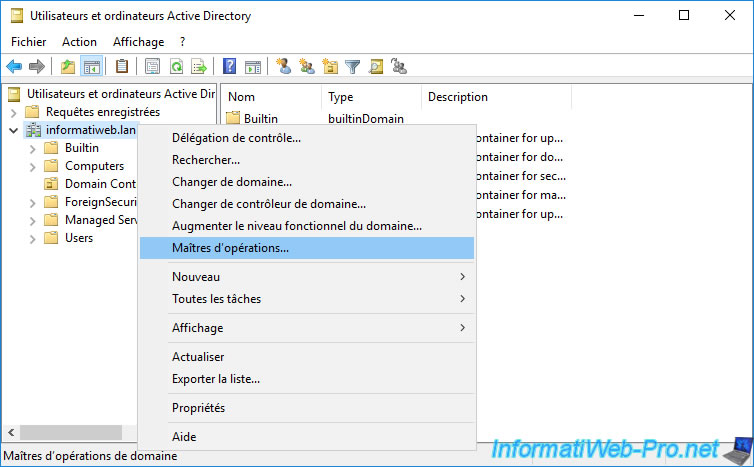
In the "Operations master" window that appears, you will be able to find out which domain controller is designated as "RID master" in the "RID" tab.
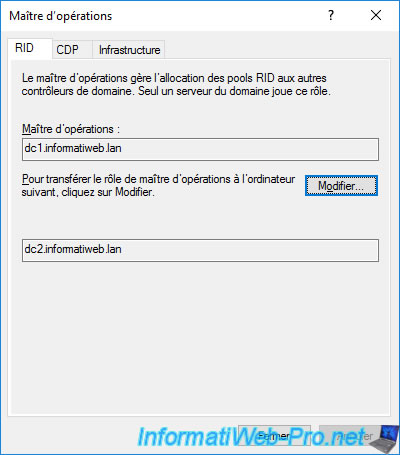
The PDC emulator in the "CDP" tab.
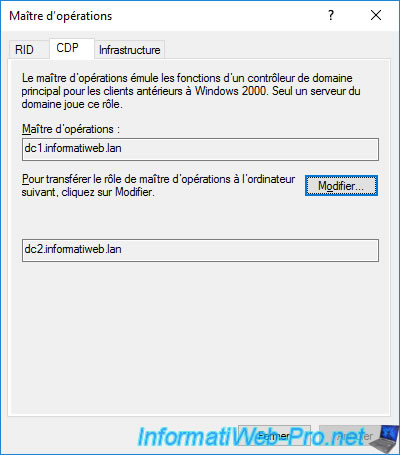
And the infrastructure master in the "Infrastructure" tab.
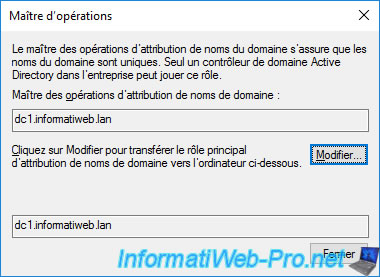
To find out the domain naming master in your Active Directory forest, open the "Active Directory Domains and Trusts" console and right-click "Operations Masters" on the root node.
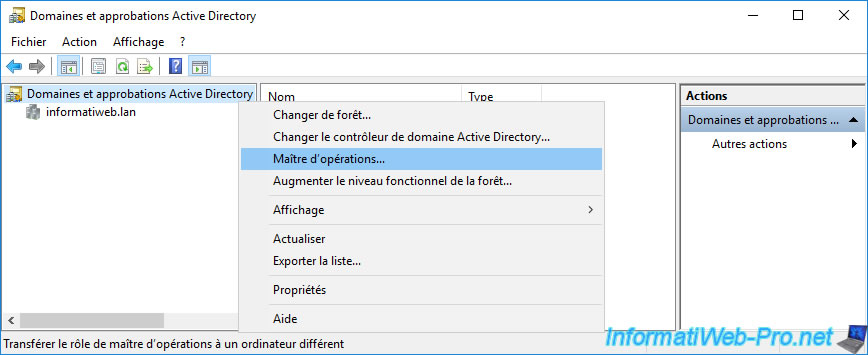
The domain naming master for your Active Directory forest is displayed.
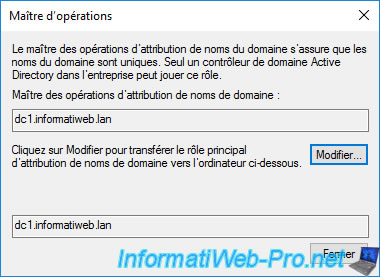
Finally, to know which domain controller is designated as "Schema master", you will have to enable the "Active Directory Schema" console which is not enabled by default for security reasons.
To do this, open a command prompt as administrator and type this :
Batch
regsvr32.exe schmmgmt.dll
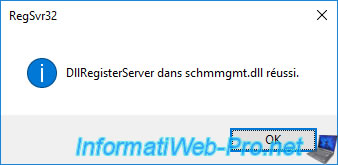
Once this console is enabled, launch the "mmc" program and go to : File -> Add/Remove Snap-in.
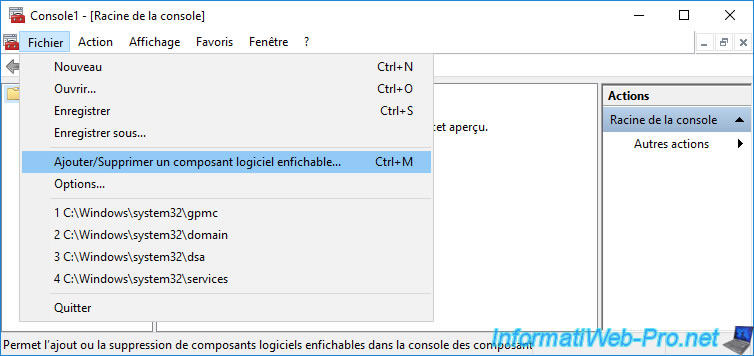
Select the "Active Directory Schema" component and click Add.
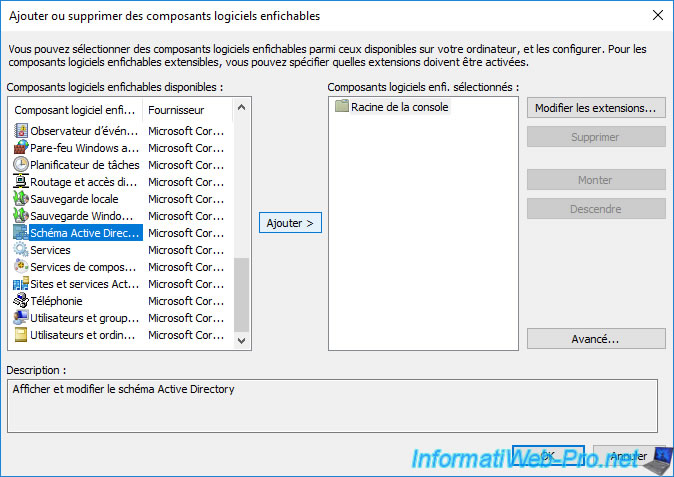
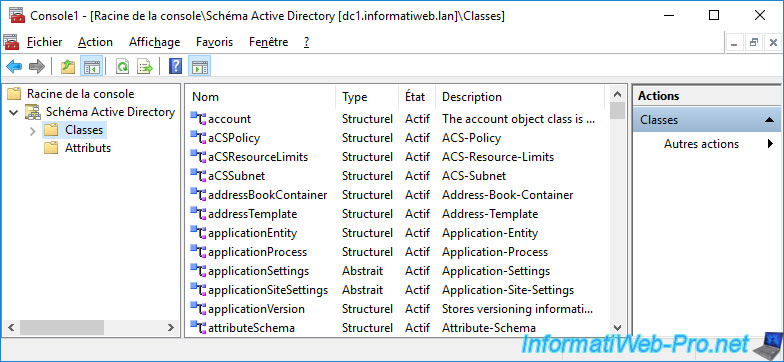
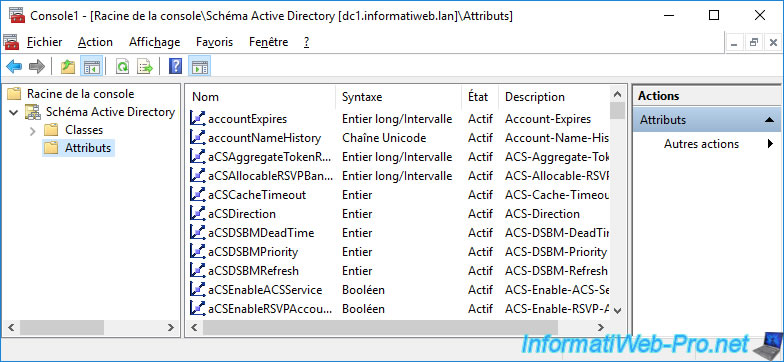
Thanks to this "Active Directory Schema" console, you will be able to find out the list of classes and attributes available in your Active Directory schema.
When you install some professional programs, some classes or attributes are sometimes added to your Active Directory schema.
However, don't edit it yourself, as this could permanently corrupt your Active Directory infrastructure. It's for this reason that this console is not enabled by default.
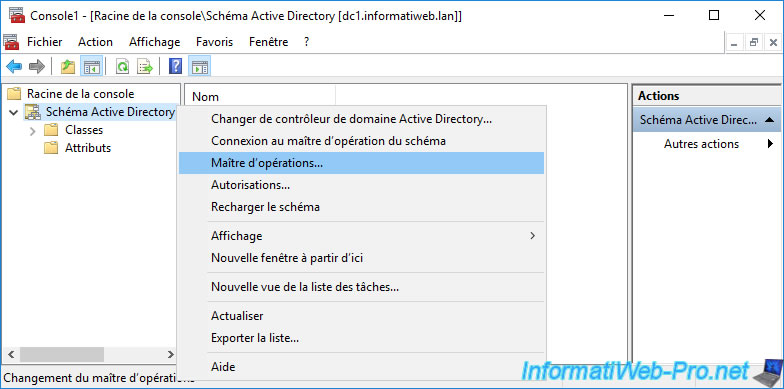
Now that you have access to this console, you can know the schema master by right-clicking "Operation masters" on "Active Directory Schema".
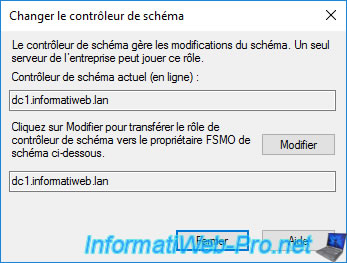
2. Properly transfer a FSMO role via the GUI
To properly transfer a FSMO role from one domain controller to another, the source domain controller and the destination domain controller must be available.
Then, to transfer a FSMO role, you must connect to the destination domain controller (therefore the one who will become the new master for the desired role).
Note that you can also use the "Change Active Directory domain controller" option available in various Active Directory consoles, as explained in the next step.
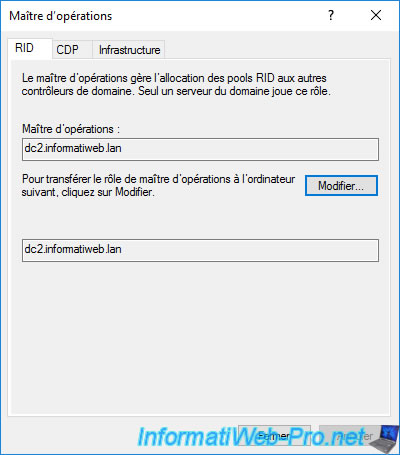
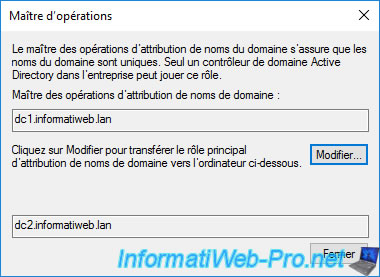
As you can see, in our case, the RID master is currently DC1 and we are currently connected to DC2.
We can therefore transfer the RID master from DC1 to DC2 by clicking on the "Change" button.
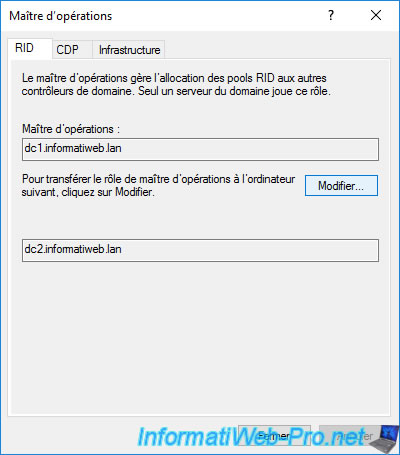
Answer "Yes" to the "Are you sure you want to transfer the operations master role?" question.
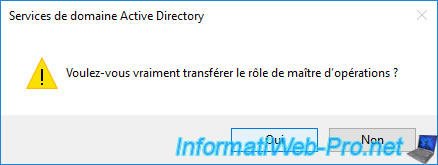
The "The operations master role was successfully transferred" message appears.
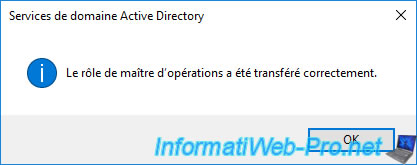
Now, the current RID master is DC2 instead of DC1.
Warning : note that the transfer of one or more roles necessarily generates data replication via the network.
3. Connect an Active Directory console to another domain controller
As mentioned earlier, to transfer a FSMO role, you must be logged in to the destination server.
For this example, we connected to the DC1 which is the current master for the role that we want to transfer.
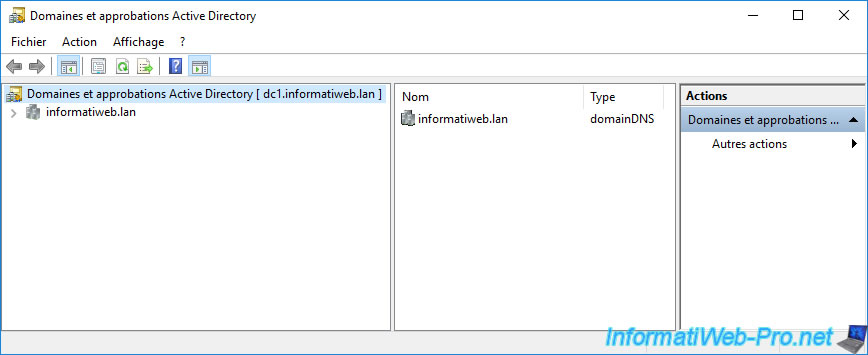
The transfer of this role is therefore not possible at the moment.
As you can see, our "Active Directory Domains and Trusts" console is currently connected to the "DC1" domain controller.
Rather than opening a new Windows session directly on the destination server, you can also use the "Change Active Directory Domain Controller" option to connect this console to the desired domain controller.
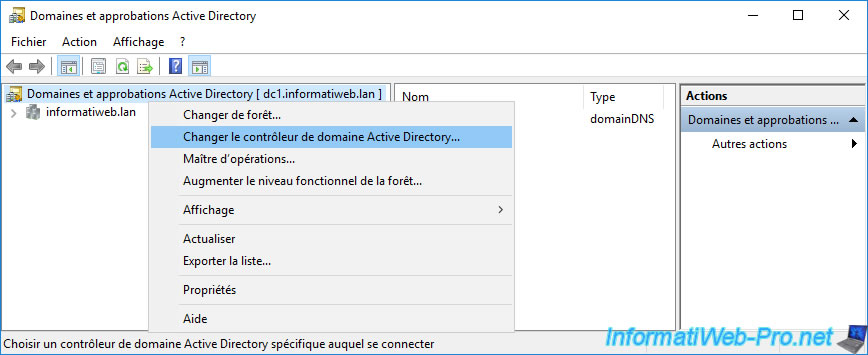
Select the domain controller to which you want to transfer this FSMO role.
In our case, the DC2 domain controller.
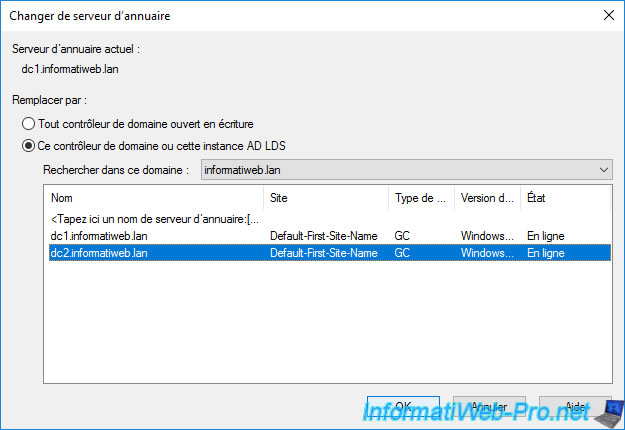
As you can see, our "Active Directory Domains and Trusts" console is now connected to the DC2 domain controller.
Right-click "Operations Master" again.
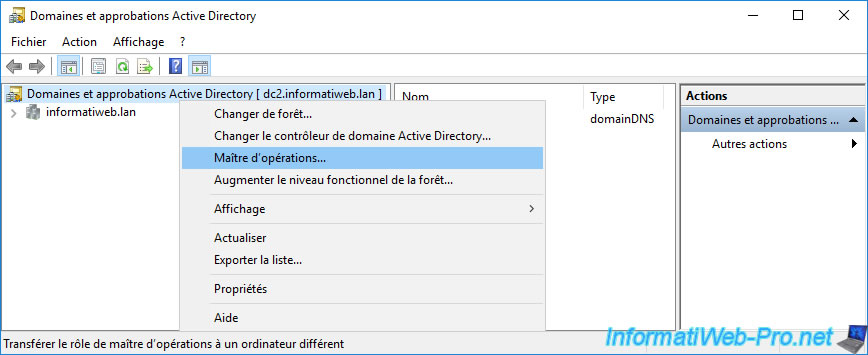
Now, we can transfer the desired FSMO role from DC1 to DC2 by clicking on the "Change" button.
4. Properly transfer a FSMO role from the command line (ntdsutil)
If you want to transfer a FSMO role cleanly from the command line, you can use the "ntdsutil" program present on all domain controllers.
To begin, you can know the commands available with ntdsutil by typing :
Batch
ntdsutil ?
Among the options available, you will find the line :
Plain Text
Roles - Manage NTDS role owner tokens
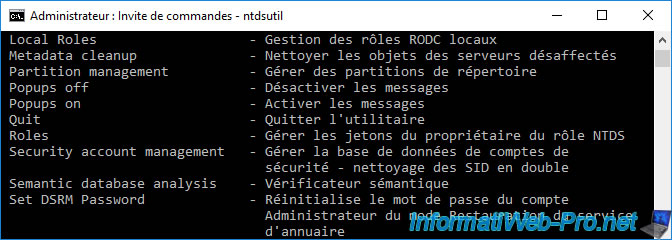
To access the "fsmo maintenance" mode, type :
Batch
ntdsutil roles
The line "fsmo maintenance" is displayed. Type "?" to display the list of commands available for this fsmo maintenance mode.
Batch
?
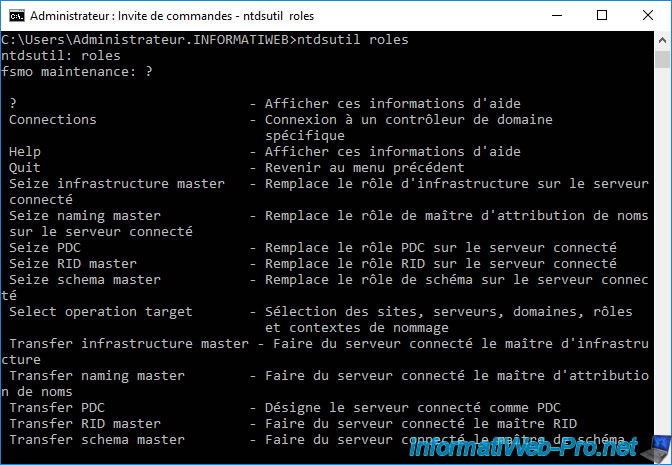
As you can see, there are mainly 2 types of commands :
- Seize [FSMO role name] : used to acquire a FSMO role when the source domain controller is down. Warning : once the FSMO role is obtained, make sure that you never put the source domain controller back on the network. Otherwise, you risk corrupting your AD infrastructure.
- Transfer [FSMO role name] : allows you to cleanly transfer a FSMO role from one domain controller to another.
Unlike the consoles available in the Windows Server GUI which automatically connect by default to the server to which you are logged on to Windows, this is not the case with the "ntdsutil" program.
So you will need to tell ntdsutil which domain controller you want to connect to. So, the domain controller to which you want to transfer an FSMO role.
To do this, in FSMO maintenance mode, type :
Batch
connections connect to server dc2
Which give :
Plain Text
Binding to dc2 ... Connected to dc2 using credentials of locally logged on user. server connections:
Once connected to the destination controller, return to FSMO maintenance mode by typing :
Batch
q
This line is displayed :
Batch
fsmo maintenance
To transfer the desired role(s), use one or more of the following commands.
4.1. Transfer the "RID master" FSMO role from the command line (ntdsutil)
To transfer the "RID master" FSMO role, type :
Batch
transfer RID master
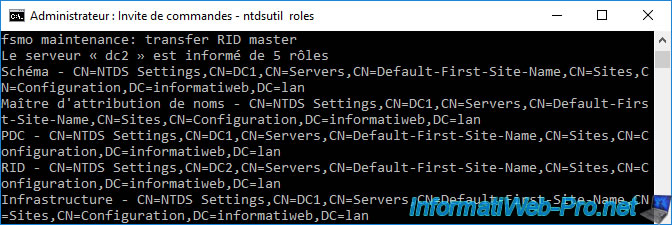
When you transfer a role (whatever it is), ntdsutil shows you each time the domain controller which is designated as operations master for each role.
Plain Text
Server « dc2 » knows about 5 roles Schema - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan Naming Master - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan PDC - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan RID - CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan Infrastructure - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan
4.2. Transfer the "PDC emulator" FSMO role from the command line (ntdsutil)
To transfer the "PDC emulator" FSMO role, type :
Batch
transfer pdc
4.3. Transfer the "Infrastructure master" FSMO role from the command line (ntdsutil)
To transfer the "Infrastructure master" FSMO role, type :
Batch
transfer infrastructure master
4.4. Transfer the "Domain naming master" FSMO role from the command line (ntdsutil)
To transfer the "Domain naming master" FSMO role, type :
Batch
transfer domain naming master
If the above command doesn't work, then use this one :
Batch
transfer naming master
4.5. Transfer the "Schema master" FSMO role from the command line (ntdsutil)
To transfer the "Schema master" FSMO role, type :
Batch
transfer schema master
4.6. Quit ntdsutil
Finally, to properly quit ntdsutil, type "q" twice :
Batch
fsmo maintenance: q ntdsutil: q
4.7. Check that FSMO roles have been transferred
To verify that the desired FSMO roles have been transferred, you can use the command :
Batch
NETDOM QUERY /Domain:informatiweb.lan FSMO
As you can see, in our case we have transferred all FSMO roles to DC2.
Plain Text
Schema master dc2.informatiweb.lan Domain naming master dc2.informatiweb.lan PDC dc2.informatiweb.lan RID pool master dc2.informatiweb.lan Infrastructure master dc2.informatiweb.lan The command completed successfully.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment