- Windows Server
- 09 July 2021 at 08:12 UTC
-

When you want to designate a new master for a FSMO role, it's strongly recommended that you transfer the desired FSMO role when the source and destination domain controllers are accessible.
However, in case of failure of the server which was master for one or more FSMO roles, you will have to obtain the concerned FSMO roles by force.
IMPORTANT : when you designate a new master for one or more FSMO roles, you must ensure that the old server which was the master of these roles will never be reintegrated into your network at the risk of corrupting your Active Directory infrastructure.
- Impossible to force the transfer of a FSMO role through the GUI
- Force the transfer of a FSMO role via the command line (ntdsutil)
- Force the transfer of the "RID master" FSMO role from the command line (ntdsutil)
- Force the transfer of the "PDC emulator" FSMO role from the command line (ntdsutil)
- Force the transfer of the "Infrastructure master" FSMO role from the command line (ntdsutil)
- Force the transfer of the "Domain naming master" FSMO role from the command line (ntdsutil)
- Force the transfer of the "Schema master" FSMO role from the command line (ntdsutil)
- Quit ntdsutil
- Check that FSMO roles have been obtained
1. Impossible to force the transfer of a FSMO role through the GUI
When a domain controller that was designated as master for one or more FSMO roles fails, it's impossible to transfer the affected role from the Windows Server GUI.
If you are trying to display the current master of the desired FSMO role :
- the name of the master will be : Error
- and this message will appear : The current operations master is offline. The role cannot be transferred.
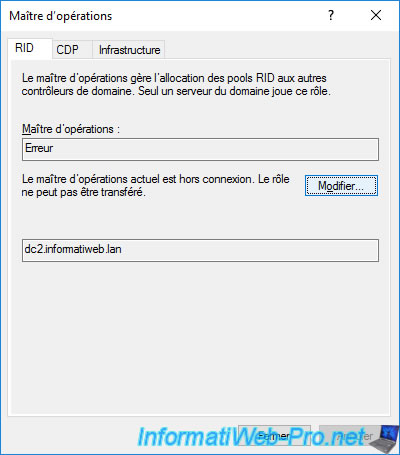
If you try to click on the "Change" button, the normal warning will be displayed.
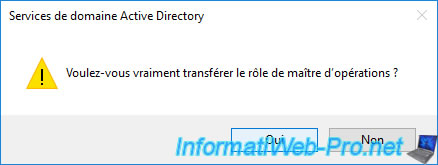
But when you confirm the role transfer by clicking Yes, this warning will be displayed :
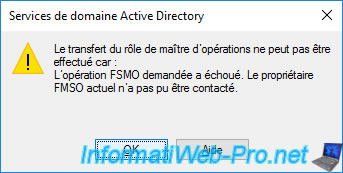
Plain Text
The transfer of the operations master role cannot be performed because: The requested FSMO operation failed. The current FSMO holder could not be contacted.
2. Force the transfer of a FSMO role via the command line (ntdsutil)
To begin, launch a command prompt as administrator and type :
Batch
ntdsutil
Then, enter FSMO maintenance mode by typing :
Batch
roles
To display the list of commands available in this mode, type :
Batch
?
Among the list of commands displayed by ntdsutil, you will find several commands that start with "Seize".
These commands are used to obtain an FSMO role even when the source domain controller is down.
Warning : once again, make sure you never reconnect the old domain controller to your network after using any of these commands, otherwise you risk to permanently crashing your Active Directory infrastructure.
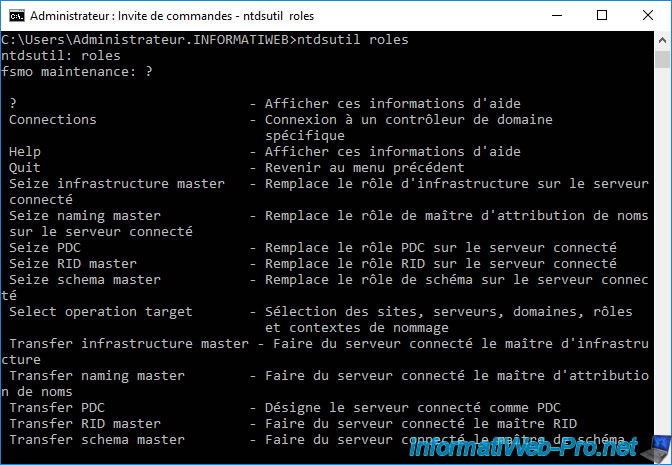
Connect ntdsutil to the destination domain controller that will need to be designated for the roles you want to transfer by typing :
Batch
connections connect to server dc2
Which give :
Plain Text
Binding to dc2 ... Connected to dc2 using credentials of locally logged on user. server connections:
Once connected to the desired domain controller, return to FSMO maintenance mode by typing :
Batch
q
Which give :
Batch
fsmo maintenance:
2.1. Force the transfer of the "RID master" FSMO role from the command line (ntdsutil)
To get the "RID master" role when the source domain controller is down, use the command :
Batch
seize RID master
Answer "Yes" for the confirmation of role seizure and this is displayed in the console :
Plain Text
Attempting safe transfer of RID FSMO before seizure. ... Transfer of RID FSMO failed, proceeding with seizure ... Searching for the highest rid pool in domain Server "dc2" knows about 5 roles Schema - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan Naming Master - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan PDC - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan RID - CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan Infrastructure - CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=informatiweb,DC=lan
2.2. Force the transfer of the "PDC emulator" FSMO role from the command line (ntdsutil)
To get the "PDC emulator" role when the source domain controller is down, use the command :
Batch
seize PDC
Answer "Yes" for the confirmation of role seizure and this is displayed in the console :
Plain Text
Attempting safe transfer of PDC FSMO before seizure. ... Transfer of PDC FSMO failed, proceeding with seizure ...
2.3. Force the transfer of the "Infrastructure master" FSMO role from the command line (ntdsutil)
To get the "Infrastructure master" role when the source domain controller is down, use the command :
Batch
seize infrastructure master
Answer "Yes" for the confirmation of role seizure and this is displayed in the console :
Plain Text
Attempting safe transfer of infrastructure FSMO before seizure. ... Transfer of infrastructure FSMO failed, proceeding with seizure ...
2.4. Force the transfer of the "Domain naming master" FSMO role from the command line (ntdsutil)
To get the "Domain naming master" role when the source domain controller is down, use the command :
Batch
seize naming master
Answer "Yes" for the confirmation of role seizure.
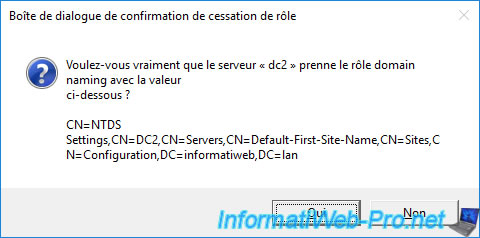
Then, this is displayed in the console :
Plain Text
Transfer of FSMO domain naming failed, proceeding with seizure ...
2.5. Force the transfer of the "Schema master" FSMO role from the command line (ntdsutil)
To get the "Schema master" role when the source domain controller is down, use the command :
Batch
seize schema master
Answer "Yes" for the confirmation of role seizure and this is displayed in the console :
Plain Text
Attempting safe transfer of schema FSMO before seizure. ... Transfer of schema FSMO failed, proceeding with seizure ...
2.6. Quit ntdsutil
Finally, to properly quit ntdsutil, type "q" twice :
Batch
fsmo maintenance: q ntdsutil: q
2.7. Check that FSMO roles have been obtained
To check that you have retrieved the desired FSMO roles, use the command :
Batch
NETDOM QUERY /Domain:informatiweb.lan FSMO
In our case, we have recovered all the FSMO roles on our 2nd domain controller :
Plain Text
Schema master dc2.informatiweb.lan Domain naming master dc2.informatiweb.lan PDC dc2.informatiweb.lan RID pool master dc2.informatiweb.lan Infrastructure master dc2.informatiweb.lan The command completed successfully.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment