- Windows Server
- 17 September 2021 at 11:31 UTC
-

By default, when you link several GPOs to an Active Directory site, an organizational unit, ... the policies are merged and applied if the security filtering and/or WMI filtering allow it.
In this tutorial, we are going to tell you about a somewhat special policy that concerns the application of group policies.
To begin, we have an organizational unit with a linked GPO.
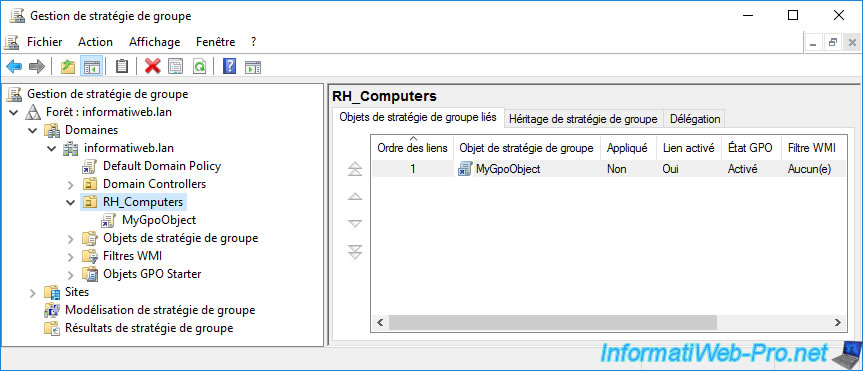
In this GPO, we have policies that apply to the computer and others to the user.
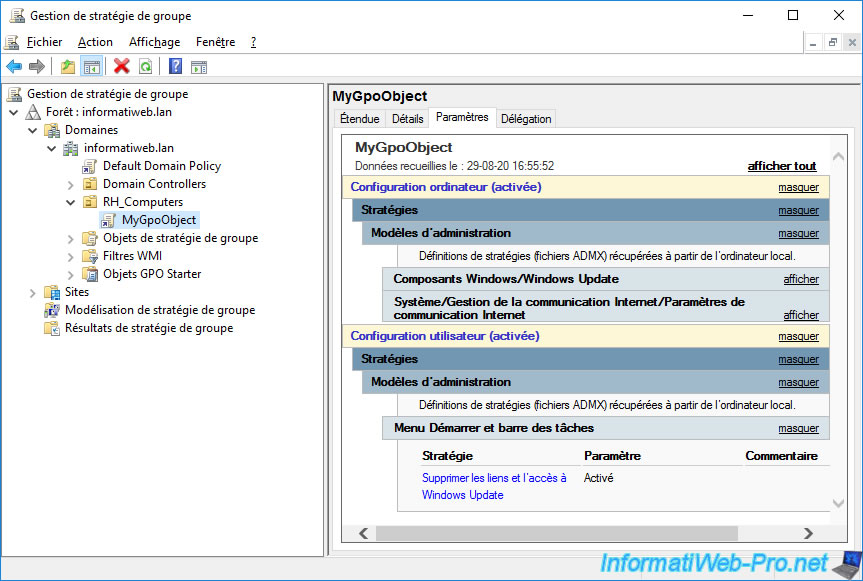
Now, we create a new GPO which we will name, for example, "LoopbackGpo".
In "Computer Configuration -> Policies -> Administrative Templates -> System", you will find a "Group Policy" folder.
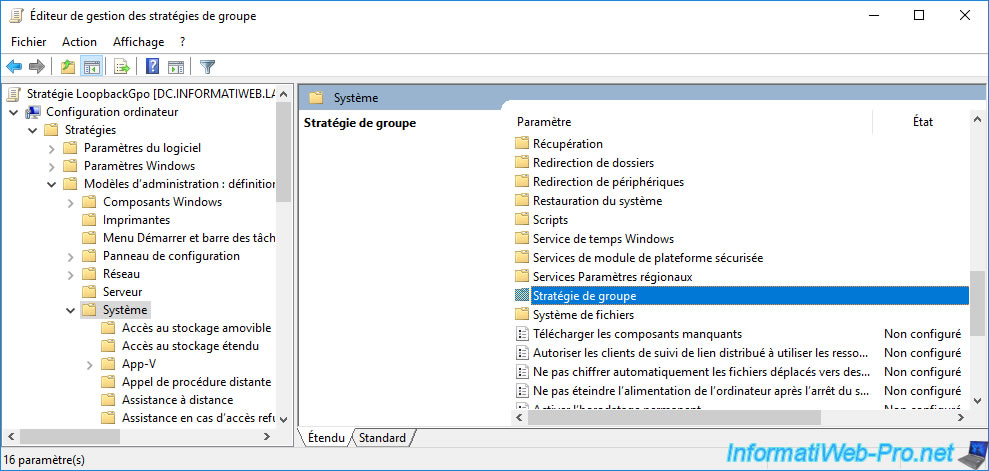
In this "Group Policy" folder, you will find a policy named : Configure user Group Policy loopback processing mode.
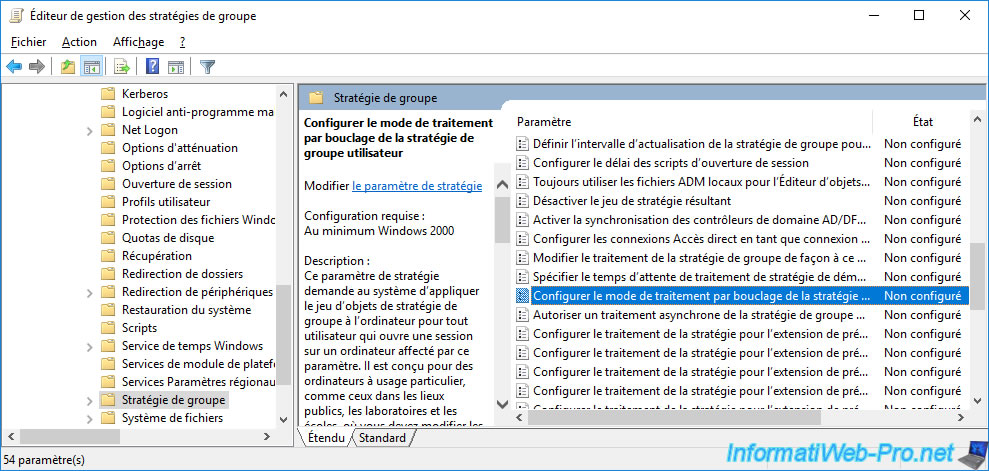
As indicated in the description of this policy, enabling this policy indicates that the group policies located in this GPO must be applied to the computer, regardless of the user who will log on to the computer affected by this GPO.
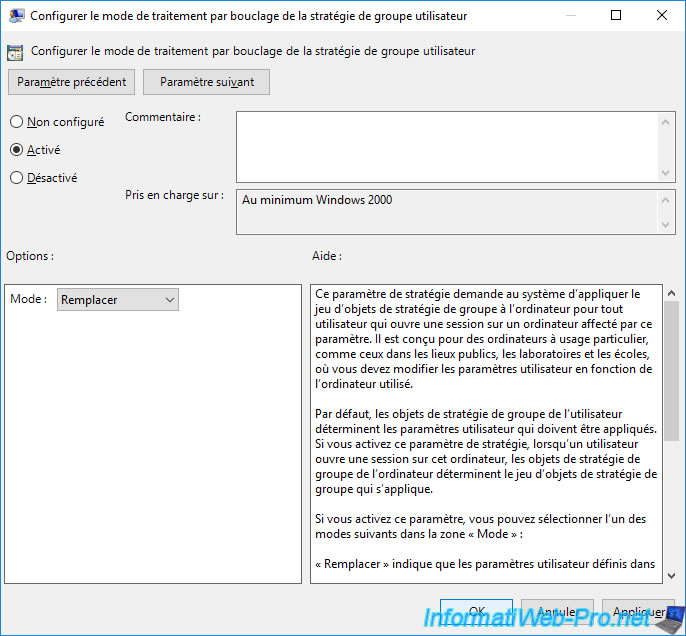
As explained in the description of this policy, there are 2 modes for this policy :
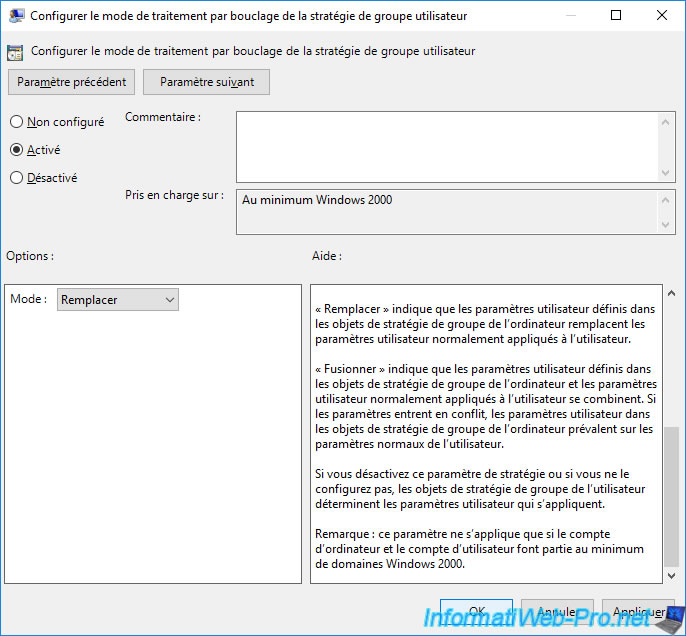
- Replace : if you choose the "Replace" mode, the user policies of this GPO will replace the user policies that would have potentially been applied by other GPOs. In summary, the only user policies that will be kept and enforced on the client computer will be those defined in this GPO.
- Merge : if you choose the "Merge" mode, the user policies of this GPO will be merged with the user policies that would have potentially been applied by other GPOs. In summary, the user policies of this GPO, as well as those of other GPOs that you would potentially have linked to the same AD location will be enforced on the client computer. However, the GPO will take priority in the event of a conflict for user policies to be applied on the client computer.
Small example : if by default, a user policy gives you the right to access a particular resource, but this right is not present in the current GPO and you select the "Replace" mode for the policy below below, you will lose your particular right on the targeted computer (due to this policy below).
For the example, we have configured some user policies in this same GPO to hide these desktop icons : This PC, Documents and Recycle Bin.
![]()
We link this new GPO to our organizational unit.
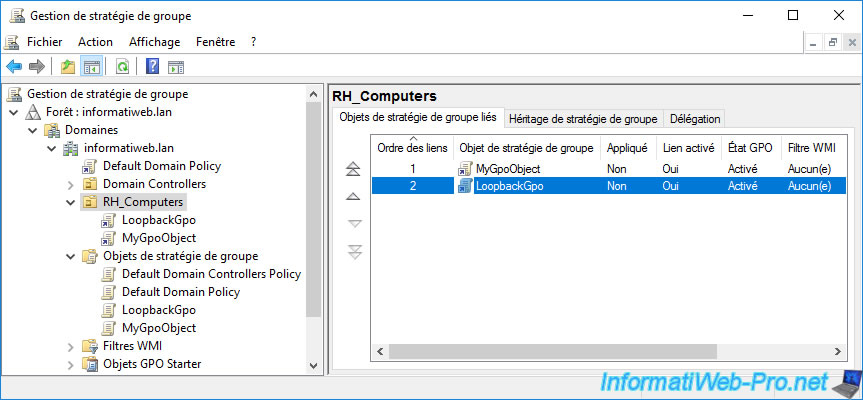
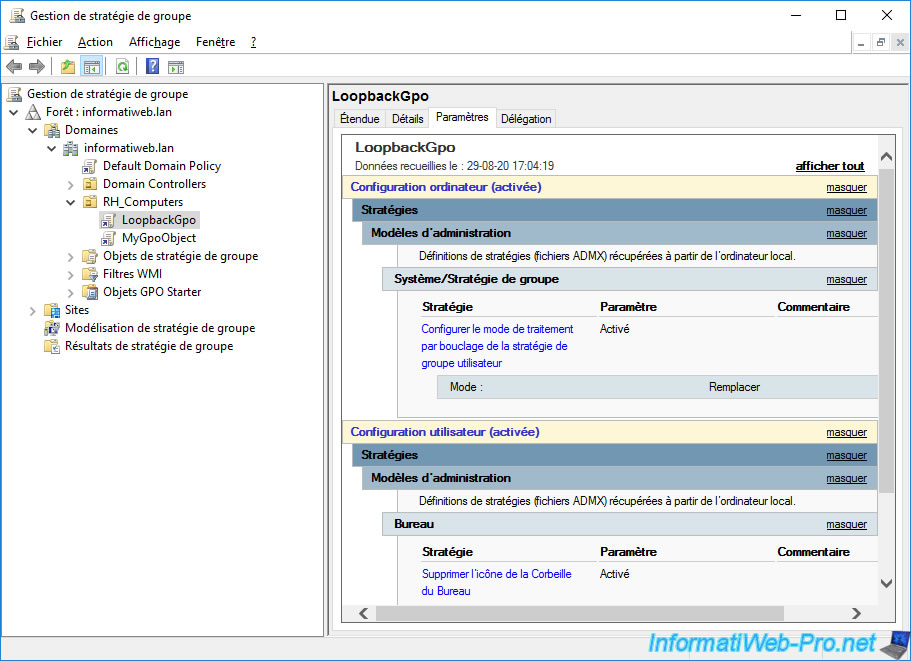
If you display your GPO settings, you will see :
- that the "Configure user Group Policy loopback processing mode" policy configuration of the computer is enabled and the mode used is : Replace
- that there are user policies including those concerning the removal of some system icons from the desktop
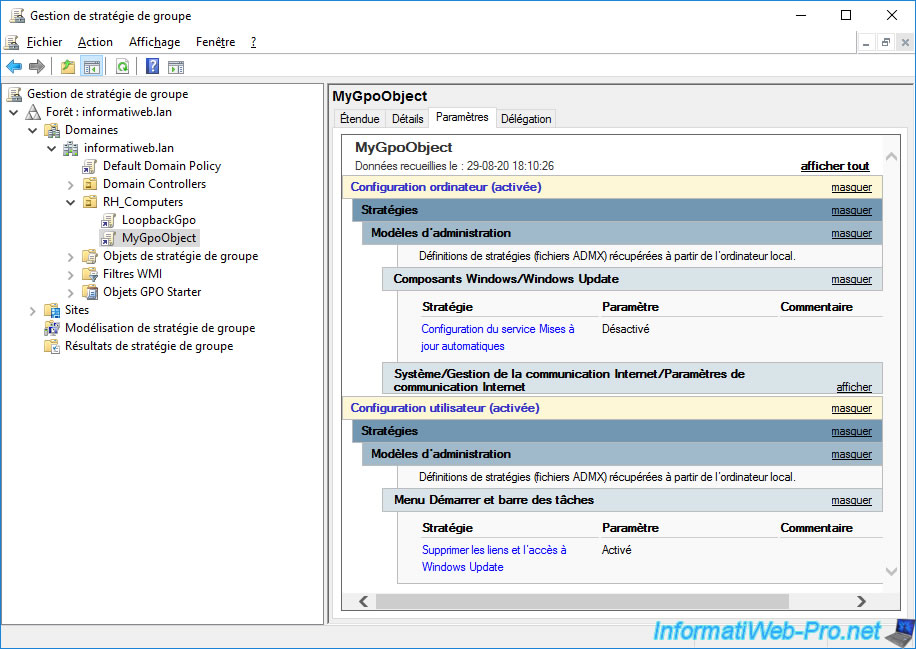
Since our 2 objects "MyGpoObject" and "LoopbackGpo" are linked to the same AD location and they are both applied to the same computers and users, the user policies defined here in the "LoopbackGpo" object will be the only group policies on user-side that will be applied on the affected client computers.
In our case, the 3 desktop icons (mentioned above) will therefore be deleted on the client PC, regardless of the user who logs on to it.
The user policies of our "MyGpoObject" GPO will therefore not be applied since the user configuration will be replaced by that of our "LoopbackGpo" GPO.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment