- Windows Server
- 03 September 2021 at 11:38 UTC
-

- 1/2
In our "Group Policy (GPO) management" tutorial, we explained to you what group policies are used for and how to configure them an apply them on your client PCs.
However, this tutorial was not complete and only presented the basics to understand how to manage the configuration and security of your IT equipment centrally.
In this new tutorial, we are going to explain the different advanced features that you can use to link policy objects to multiple locations, force the application of these policies, ...
- Link a single GPO to multiple locations
- Link enabled
- Block inheritance from parent group policies
- Bypass inheritance blocking by applying GPO
- Security filtering
- WMI filtering
1. Link a single GPO to multiple locations
In our previous tutorial, we created a GPO object that we then linked to a single organizational unit (RH_Computers).
However, if you wish, you can link a GPO object to several locations (organizational units, Active Directory sites, ...).
For the example, we have created a new "Commercial_Computers" organizational unit on our "informatiweb.lan" Active Directory domain.
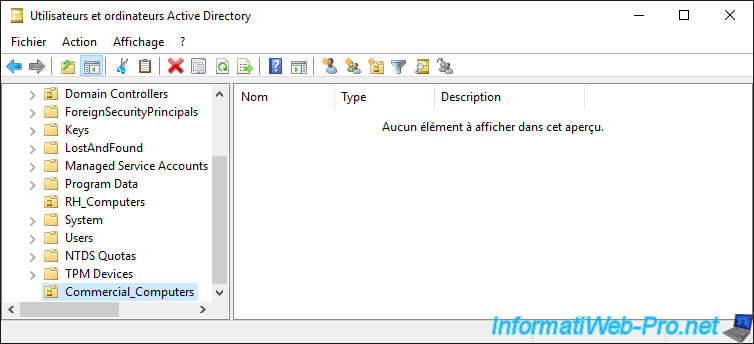
Open the "Group Policy Management" console on your domain controller and right click "Link an Existing GPO" on the new "Commercial_Computers" organizational unit.
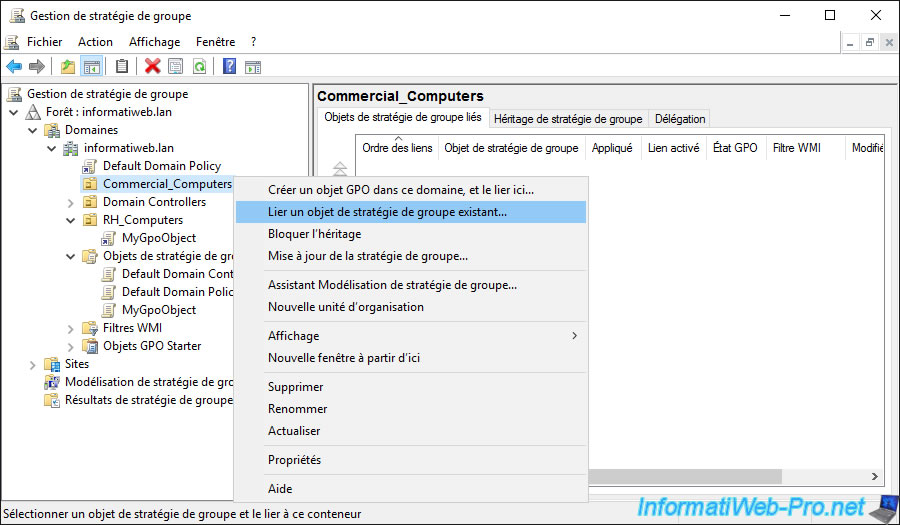
Select the GPO object that you had previously linked to another location.
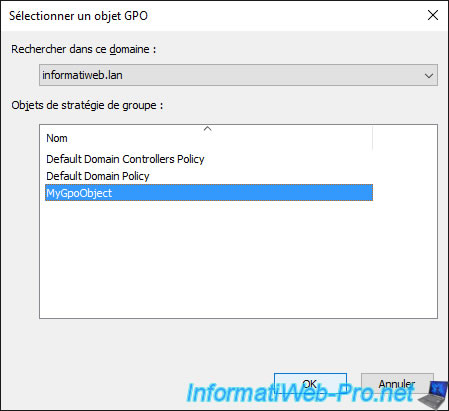
As you can see, by selecting our "Commercial_Computers" organizational unit, we see that our object has been successfully linked to it.
And if we deploy the "RH_Computers" node, we see that there is also a link to the same GPO object.
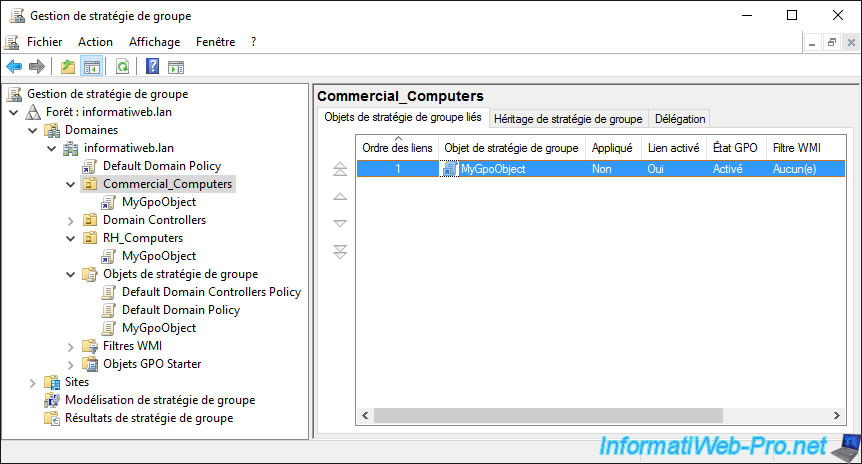
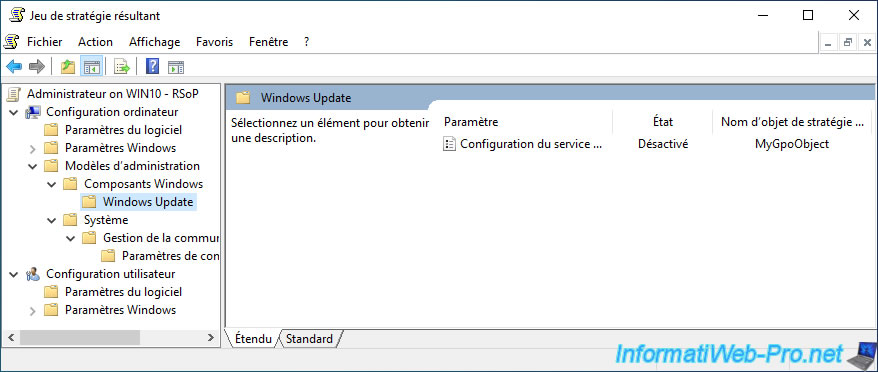
Moreover, you can see the list of current links of this GPO by selecting it on the left and going to the "Scope" tab.
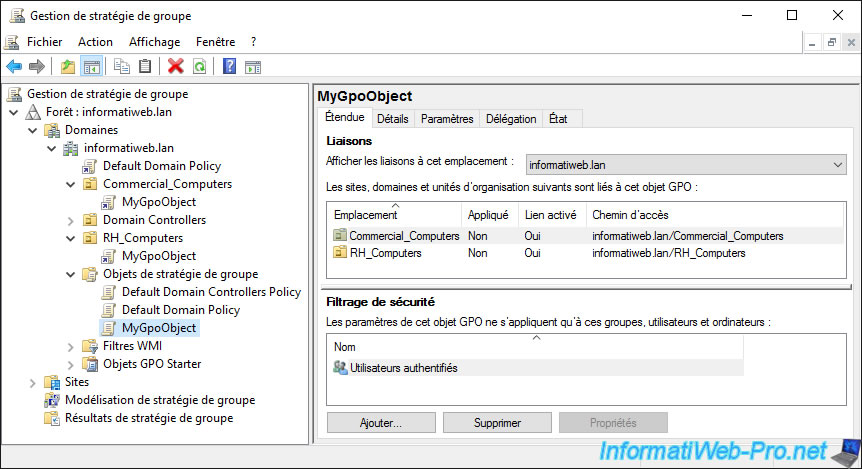
If you select the link to a GPO object and right click "Delete" on it, only the link with that GPO will be deleted.
The source GPO will not be deleted from the domain controller.
Note : if you look at the icon of this link, you will see that it has an arrow like the shortcuts on Windows. It's therefore a link to the desired GPO object and not the GPO itself.
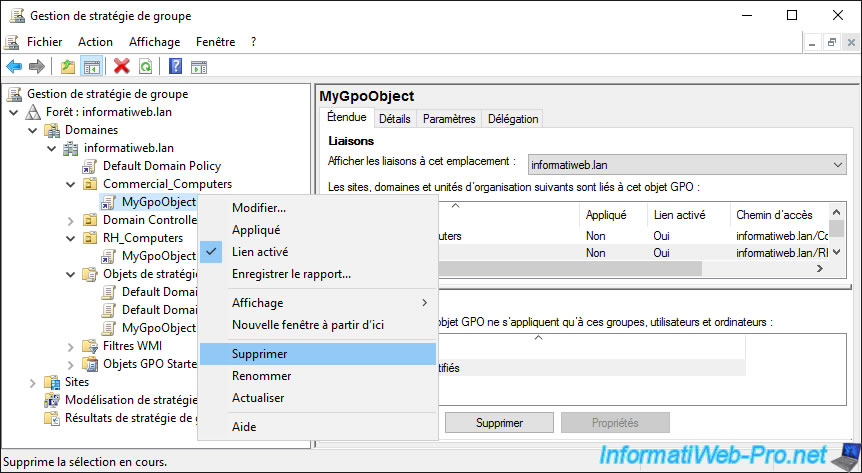
Confirm the removal of the link.
As stated in this message, this will not delete the GPO itself.
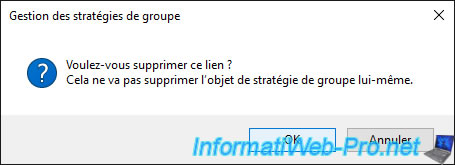
The link has been removed, but the GPO still exists and the link to the other OU still exists.
2. Link enabled
By default, when you link a Group Policy Object (GPO) to an Active Directory site, an organizational unit, ... the link is automatically enabled.
This means that the policies defined in the GPO will be applied to the computers and users affected by the location to which it is linked.
To check this, you can for example use the "rsop.msc" program on a client PC linked to your Active Directory.
A "Resultant Set of Policy is being processed" window appears.
Wait while the policies to be applied are loaded from your domain controller.
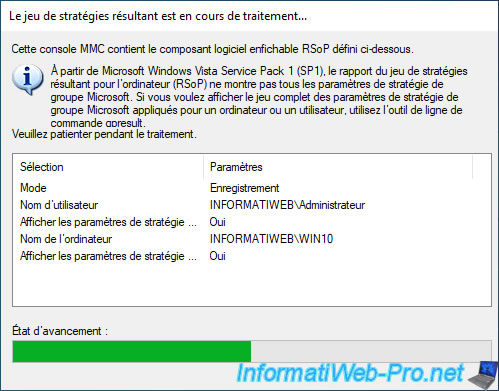
As you can see, the policies defined in our "MyGpoObject" object are applied on the client PC for the moment.
When you have a lot of GPOs in an Active Directory infrastructure, some policies may not apply.
The easiest way to find the cause (which may be due to a conflict with other GPOs) is to disable the link to this or that GPO.
Thus, these policies will not be applied, but you can restore the link very easily after your tests by simply enabling this link again.
For the example, we will disable the link to our "MyGpoObject" GPO object by right-clicking "Link enabled" on this link.
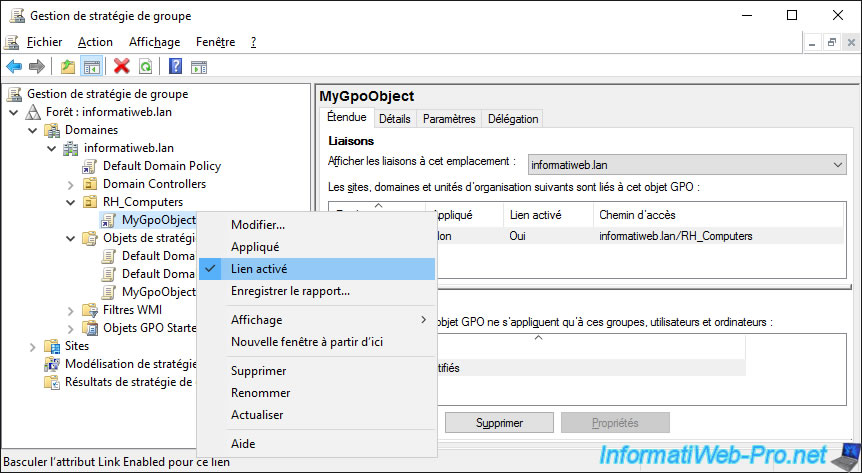
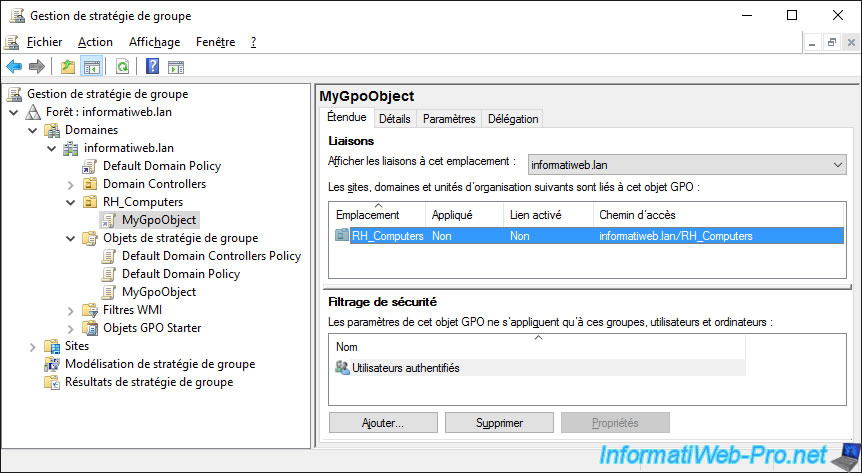
The link still appears, but it's indicated "No" in the "Link enabled" column.
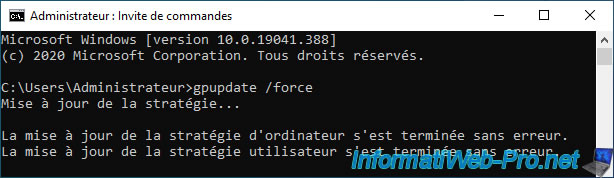
Now that the link to our GPO is disabled, we force the update of the policy on our client PC with the command :
Batch
gpupdate /force
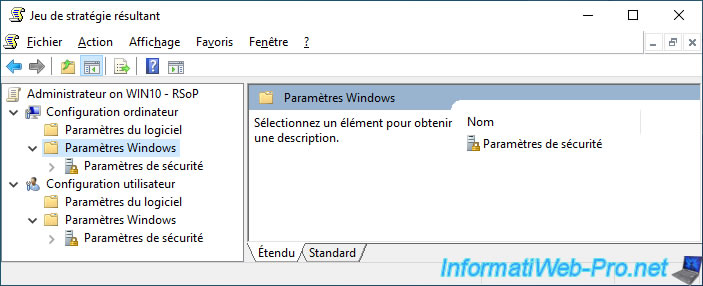
We restart the "rsop.msc" program on our client PC to re-download the new group policies to be applied to the client PC and we find that they are no longer applied.
3. Block inheritance from parent group policies
If you have an Active Directory infrastructure with a lot of organizational units nested within each other, it might be useful to block inheritance from parent group policies to resolve some conflicts (for example).
This is because by default, when you link a Group Policy Object (GPO) to a location in your Active Directory, the Group Policies defined in that GPO apply to the desired location, as well as to all children, sub-children, ...
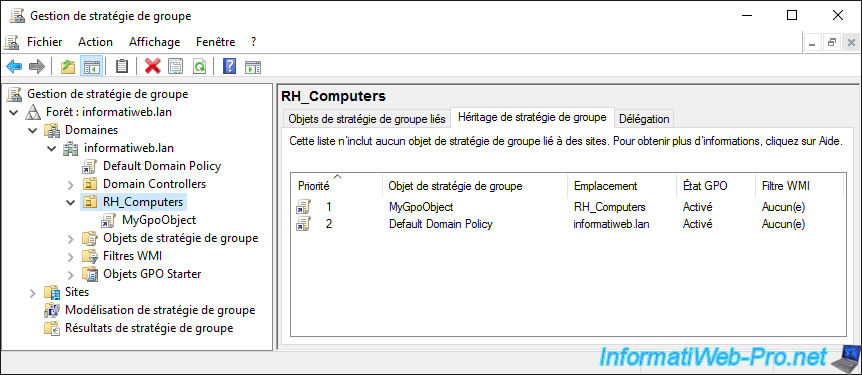
For example, if we select our "RH_Computers" organizational unit which is at the root of our Active Directory domain and we go to the "Group Policy Inheritance" tab, we see that :
- the policies of our GPO linked to this organizational unit are applied
- then, those of the "Default Domain Policy" object which is linked to our Active Directory domain
Note that, by default, the policies of the child link (RH_Computers\MyGpoObject) take precedence over the policies defined through the parent link (domain root\Default Domain Policy).
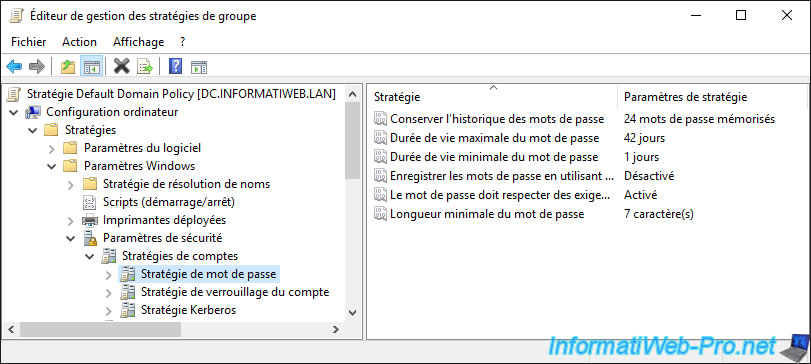
In the "Default Domain Policy" GPO created by default during the installation of the AD DS services, you will find security policies concerning password security.
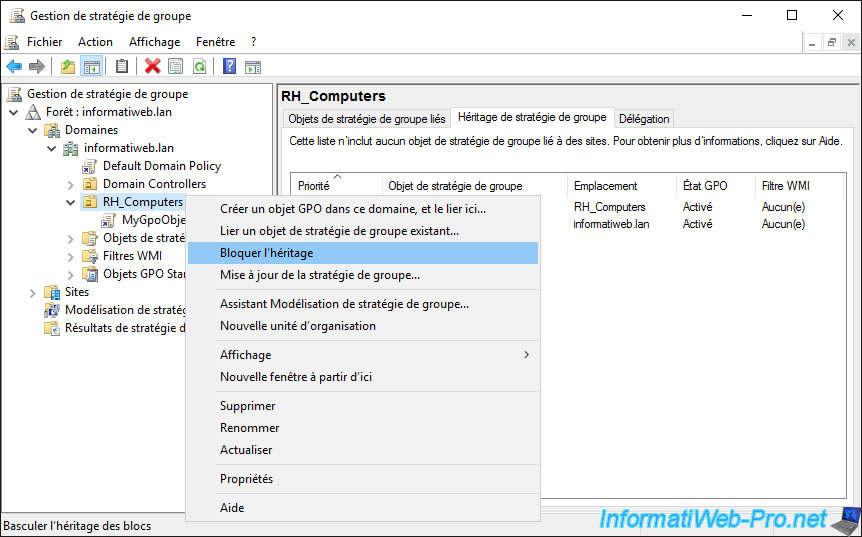
To block the inheritance of group policies linked to parents, all you have to do is right-click "Block Inheritance" on the desired location.
As indicated previously, this makes it possible in particular to resolve the problems of conflicts between some group policies that would be defined in the parent and child GPO, for example.
However, this can also pose a security problem, as it may also be blocking security policies defined by your supervisor (in case you are a multinational company, for example).
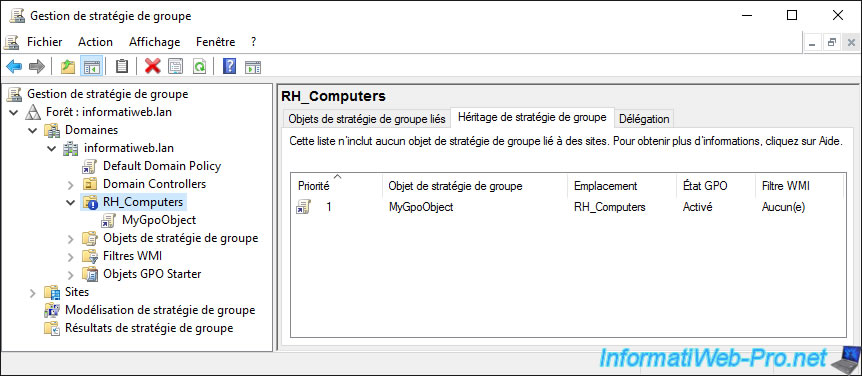
As expected, the policies defined on the parent locations are no longer enforced on our organizational unit "RH_Computers".
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain


You must be logged in to post a comment