Manage a remote DirectAccess client from the corporate network (manage out) on Windows Server 2012 / 2012 R2
- Windows Server
- DirectAccess
- 15 October 2017 at 11:47 UTC
-

- 2/3
3. Configuring the DirectAccess client firewall through Group Policy (GPO)
To test the remote access to a DirectAccess client from a local client, we will allow the ping (both IPv6 and IPv4), as well as the Windows RDP from our ISATAP clients.
To do this, we will create a new GPO that will apply to DirectAccess clients.
Note : you should not use the "DirectAccess Client Settings" GPO created by the remote access server because this GPO is handled automatically by the wizards that you use to configure DirectAccess.
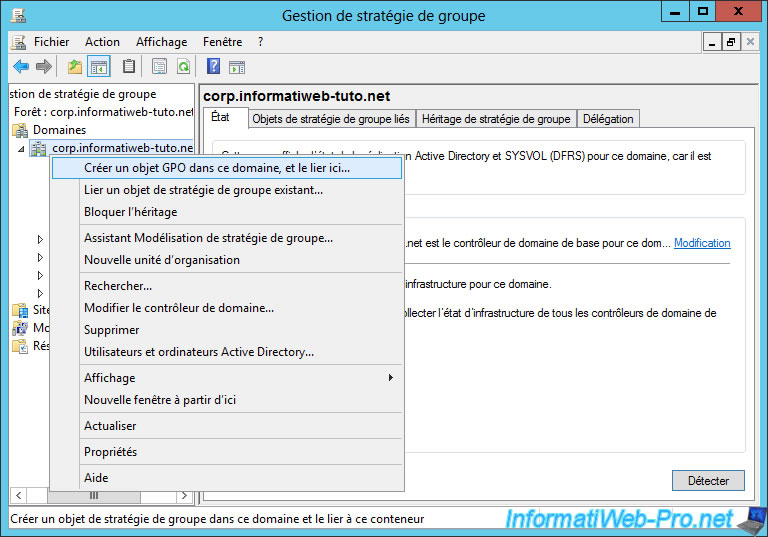
Name this new GPO : DA Clients.
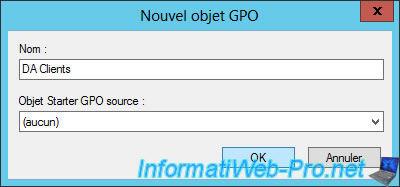
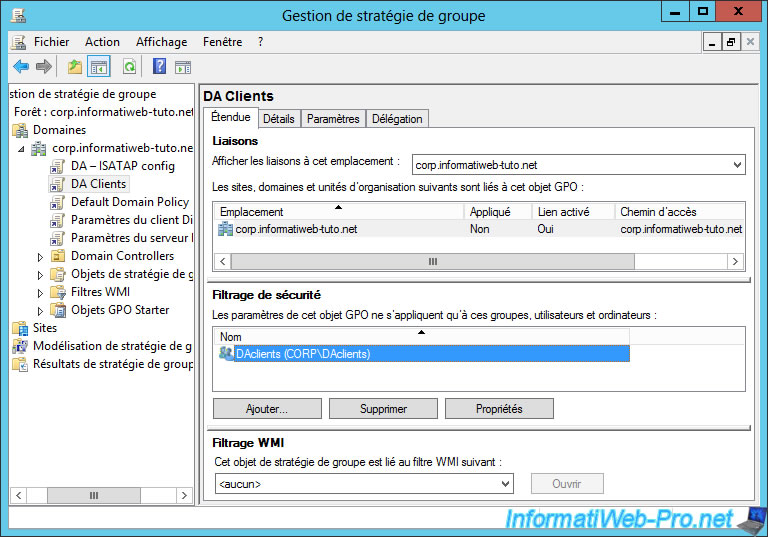
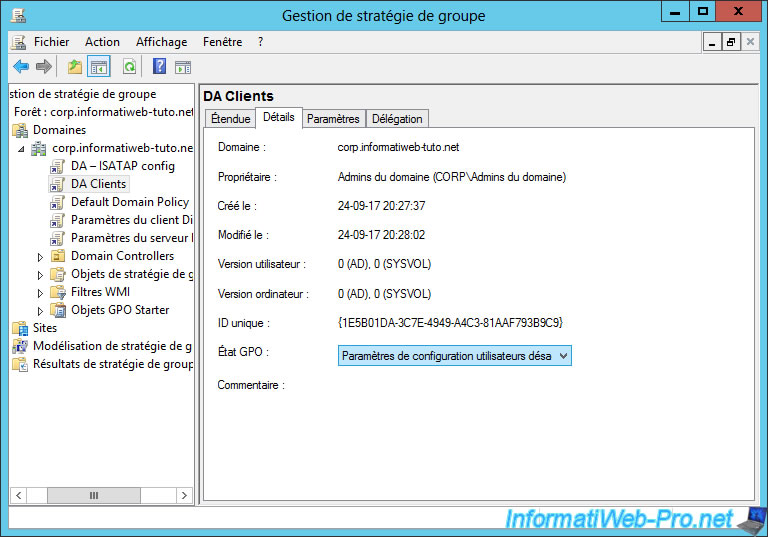
Then, use the same configuration as for the "DirectAccess Client Settings" object :
- in the Scope tab : "Security Filtering : DAclients".
- in the Details tab : "GPO Status : User configuration settings disabled".
Then, edit this GPO : DA Clients.
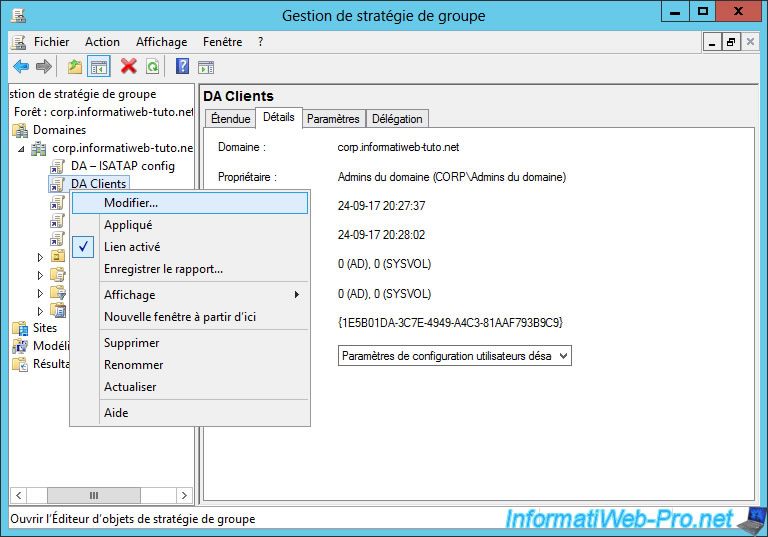
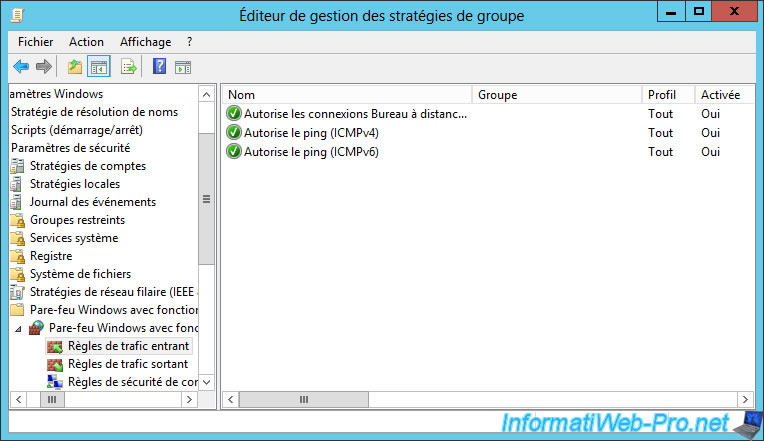
Go to "Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security -> Windows Firewall with Advanced Security -> Inbound Traffic Rules" and create a new rule.
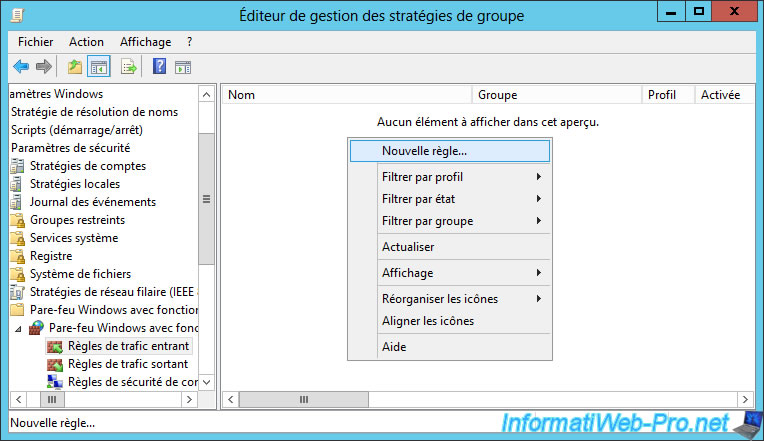
To begin, we will allow the ping. This corresponds to the ICMPv4 protocols (for IPv4 ping) and ICMPv6 (for IPv6 ping).
To do this, you will need to create a custom rule.
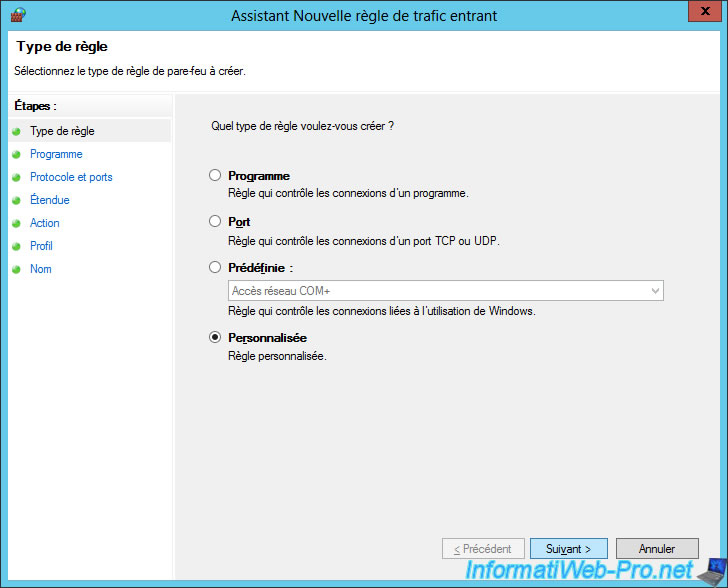
Select "All programs" and click Next.
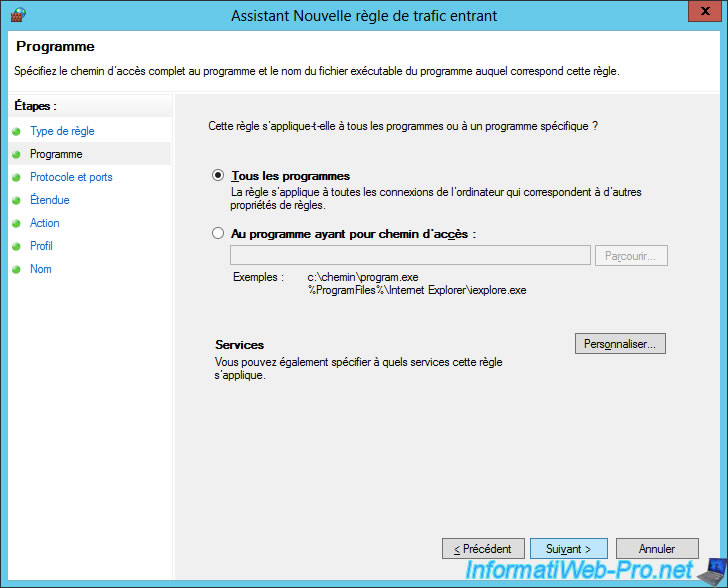
Choose ICMPv6.
Note : then, you will create a very similar 2nd rule, but selecting ICMPv4 instead of ICMPv6.
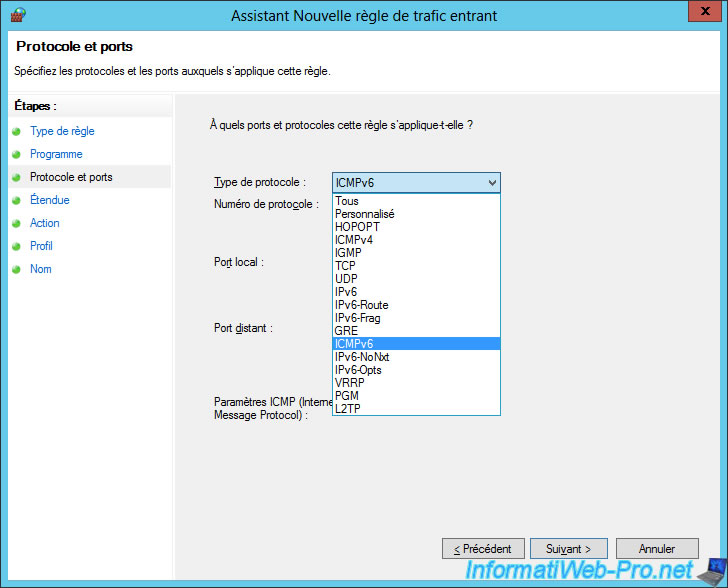
For now, just click Next.
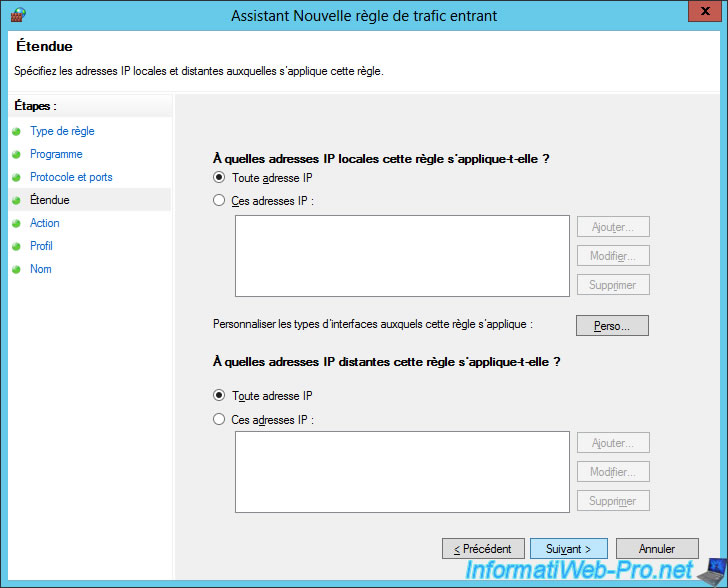
Select "Allow the connection".
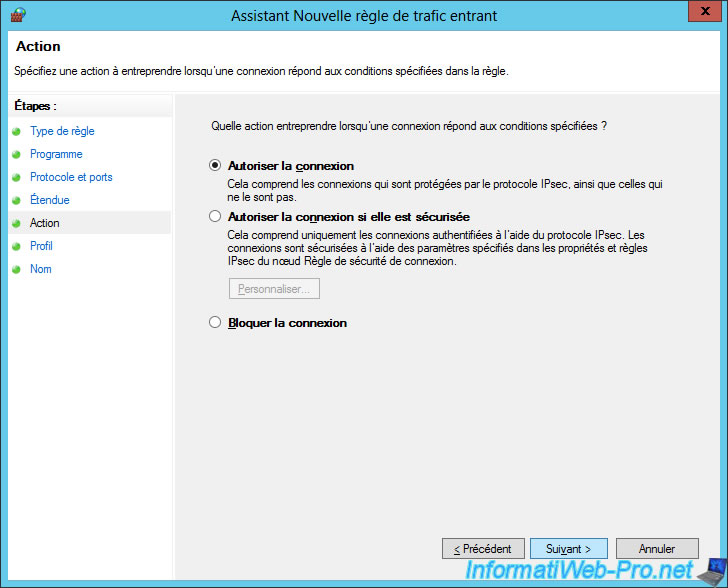
Click Next.
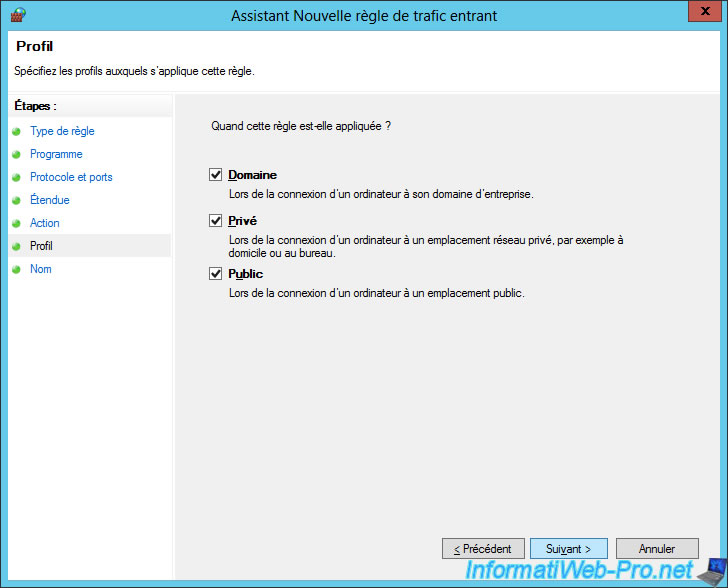
Specify "Allow ping (ICMPv6)" for the name of the rule.
Note : for the 2nd rule (ping in IPv4), specify "Allow ping (ICMPv4)".
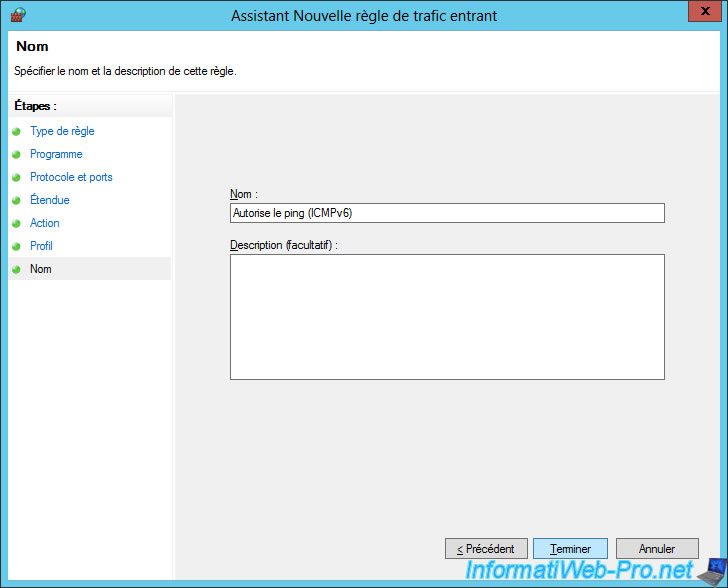
For now, the ping will be allowed on your DirectAccess clients.
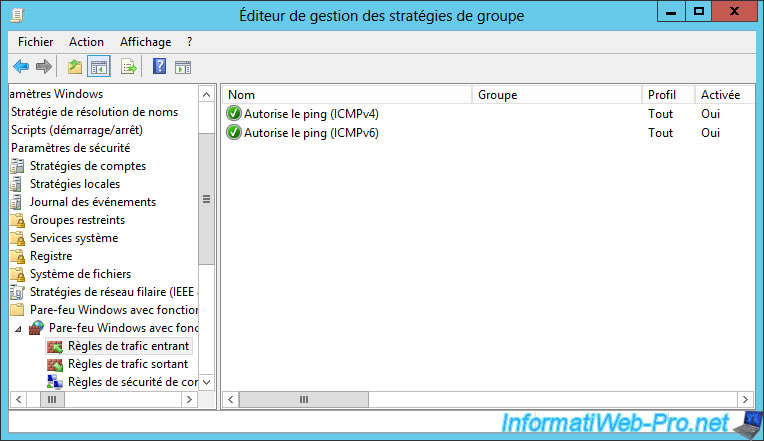
Now, we will also allow remote access through Windows Remote Desktop (RDP).
To do this, create a new Inbound Rule and select "Port" for the rule type.
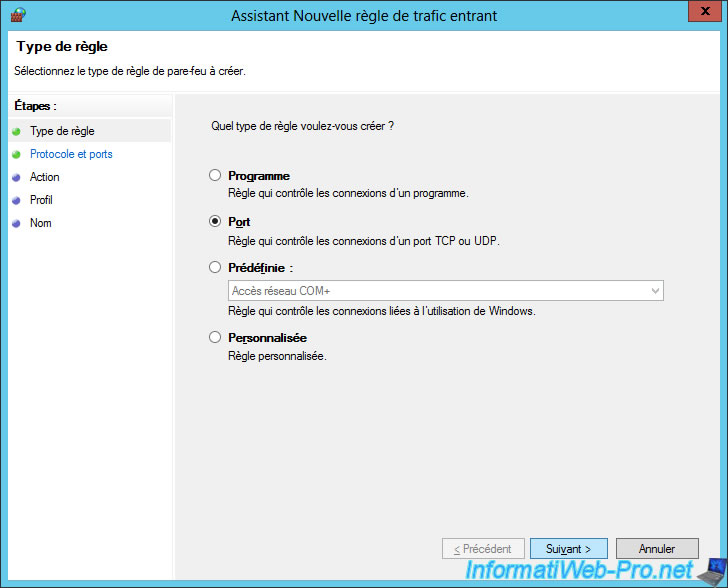
Select TCP and enter 3389 for the port number.
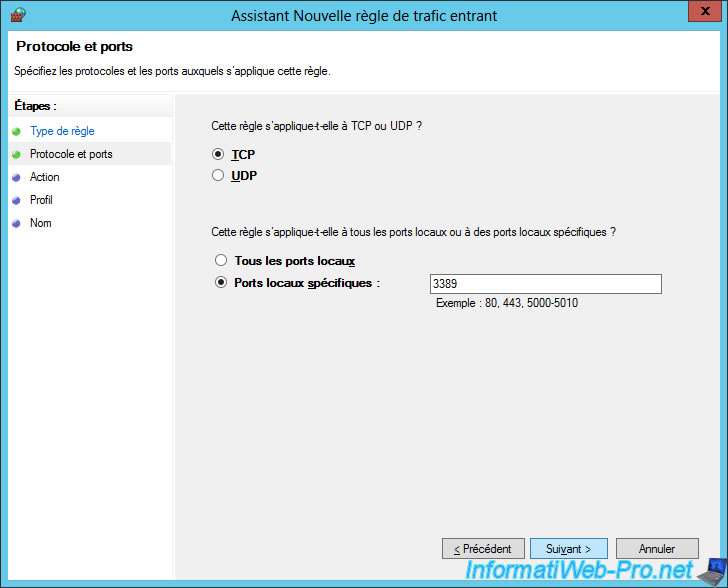
Select "Allow the connection".
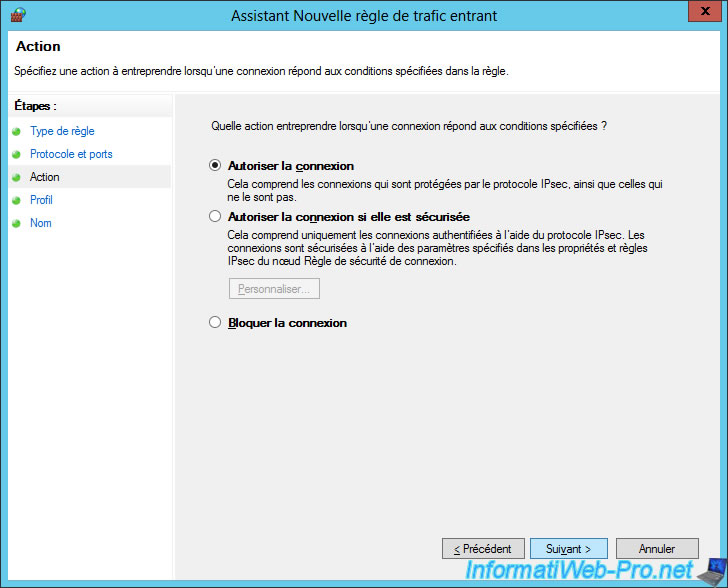
Click Next.
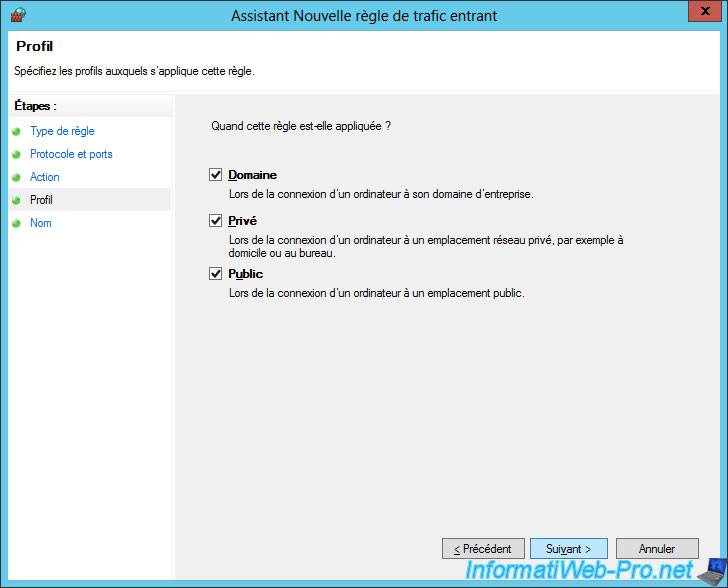
Specify "Allow Remote Desktop connections (RDP)" for the rule name.
Now, you can ping your DirectAccess clients and access them also via the Windows remote desktop.
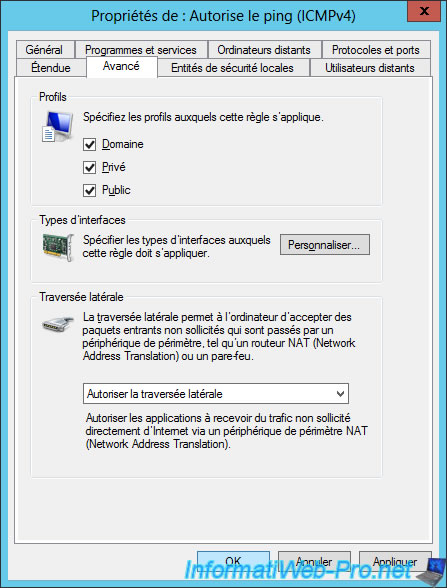
As shown on the "Configure Packet Filters to Allow Management Traffic to DirectAccess Clients" page of the Microsoft Technet, to allow inbound traffic from your company's networked computers, you will also need to allow edge traversal to support also DirectAccess clients using the Teredo IPv6 transition mechanism.
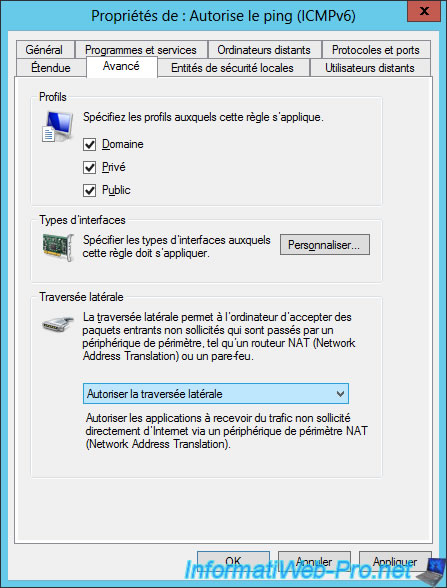
For now, the incoming traffic is allowed (for ICMP and RDP) from any remote machine.
To better secure our DirectAccess clients, we will therefore add a condition about remote IPs.
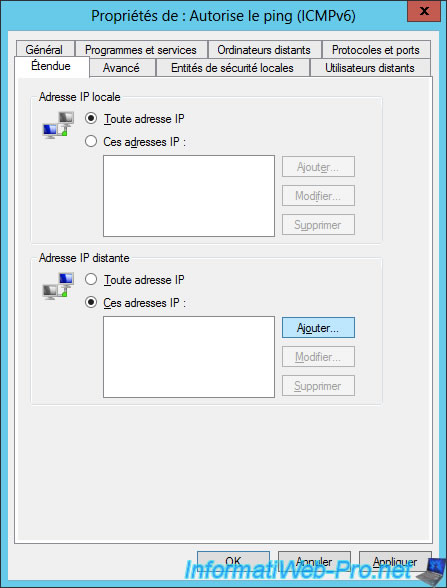
To allow only machines of our local network to access our DirectAccess clients, we will rely on the ISATAP prefix of our ISATAP clients.
As you can see, the IPv6 address generated via ISATAP consists of 2 parts : an IPv6 prefix followed by our local IPv4 address.
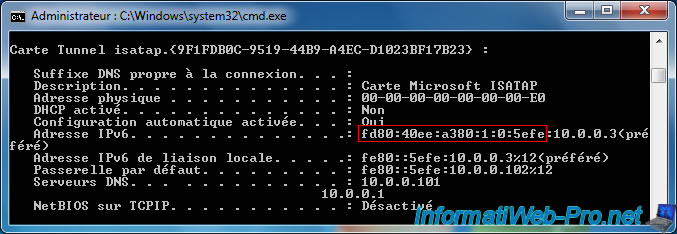
We will therefore indicate the ISATAP prefix recovered previously followed by : 0.0.0.0/96.
This will allow all IPv4 addresses whose IPv6 prefix is ours to be allowed.
In our case, this gives : fd80:40ee:a380:1:0:5efe:0.0.0.0/96
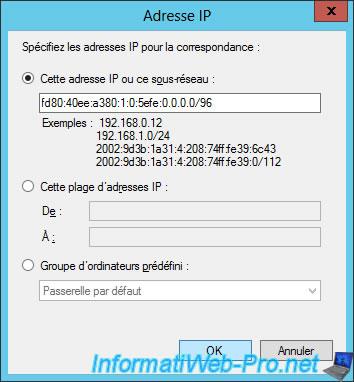
Now, click OK.
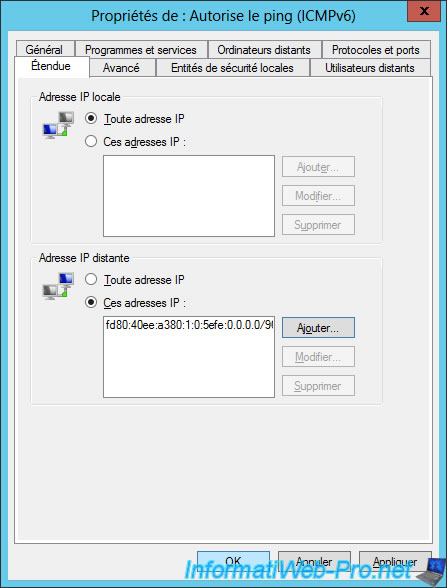
Then, do the same for the other 2 rules created previously.
Share this tutorial
To see also
-

Windows Server 9/12/2017
WS 2012 / 2012 R2 - DirectAccess - Installation, configuration and clients on Win 7 to 10
-

Windows Server 10/3/2017
WS 2012/2012 R2 - DirectAccess - Configure a Windows To Go client

No comment