Install and configure DirectAccess on Windows Server 2012 / 2012 R2 with clients on Windows 7, 8 and 10
- Windows Server
- DirectAccess
- 12 September 2017 at 18:29 UTC
-

- 4/5
9. Verify Windows client configuration
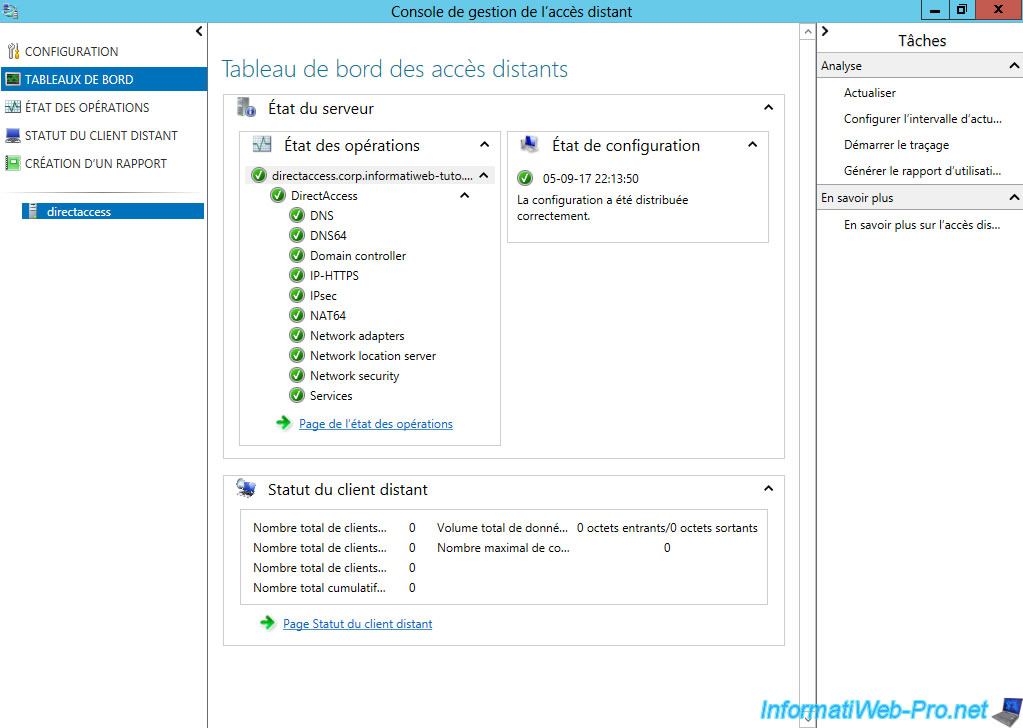
As you can see in the image below, currently, there is no client connected to our server.
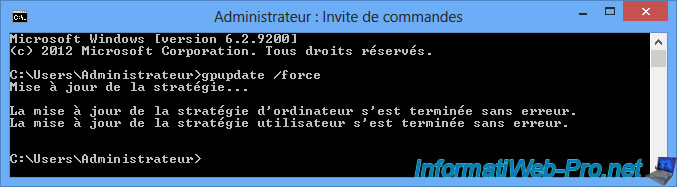
On the client PC, run a command prompt as an administrator and type this command :
Batch
gpupdate /force
Then, restart the computer.
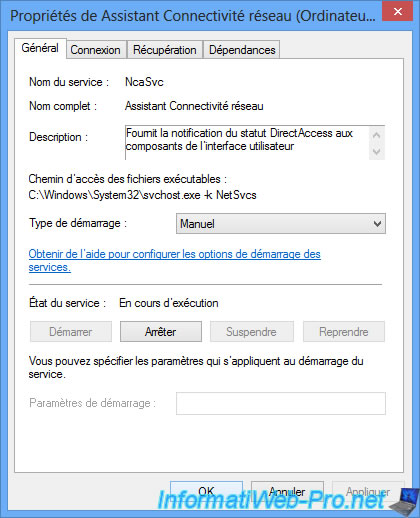
As you can see in the Windows Services list, the "Network Connectivity Assistant" service is running and allows you to connect seamlessly to the DirectAccess server.
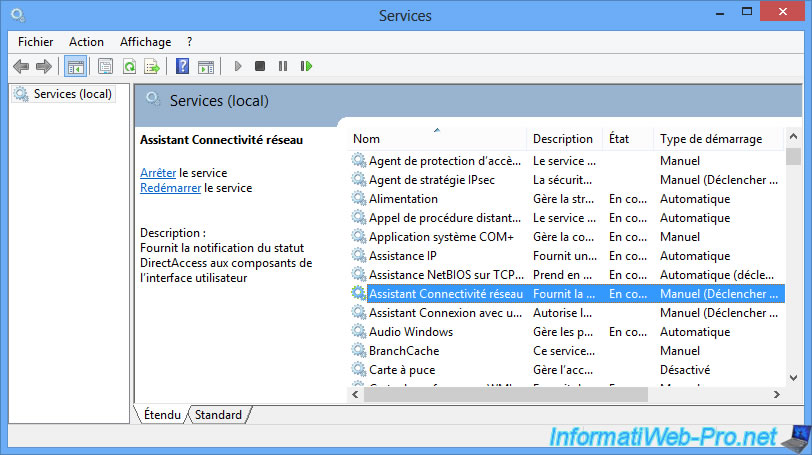
The real name of this service is : NcaSvc
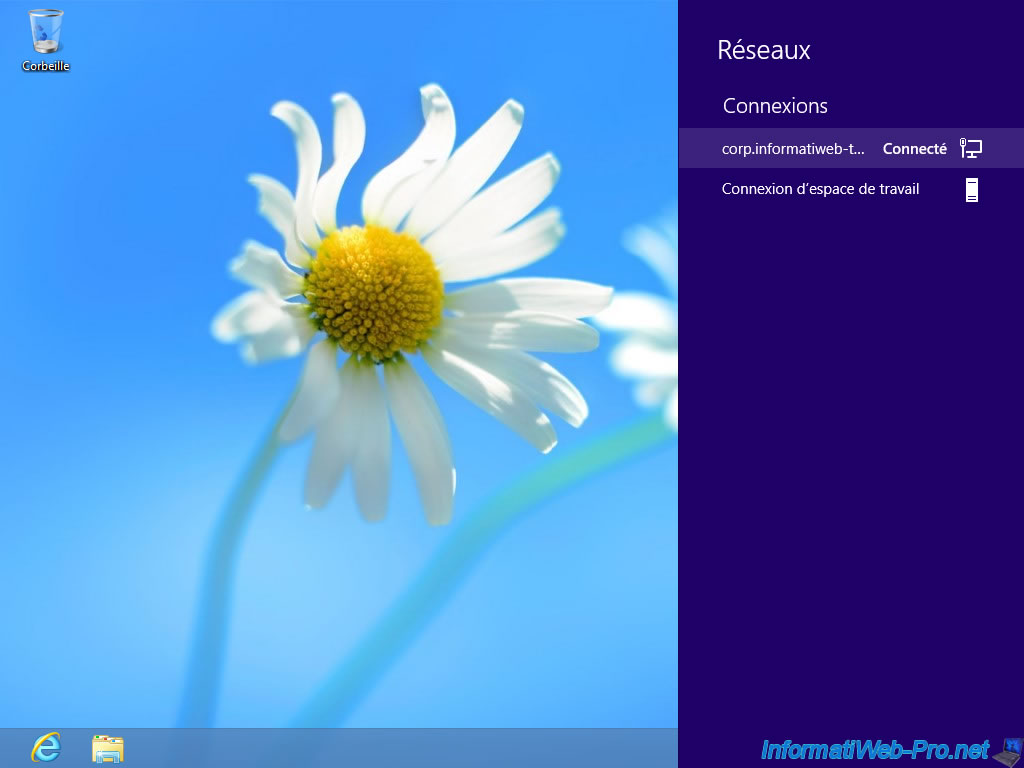
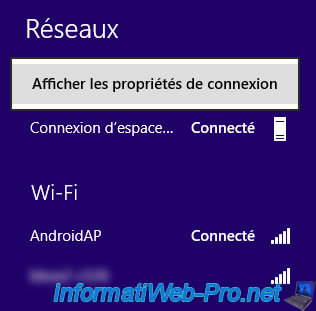
If you click on the network icon on the taskbar, you will see that Windows displays 2 connections :
- the LAN connection (which has been renamed with the name of our domain because this PC is linked to our Active Directory).
- the workspace connection (this is the connection to automatically connect to your company's DirectAccess server)
Right-click "Show Connection Properties" on the workspace connection.
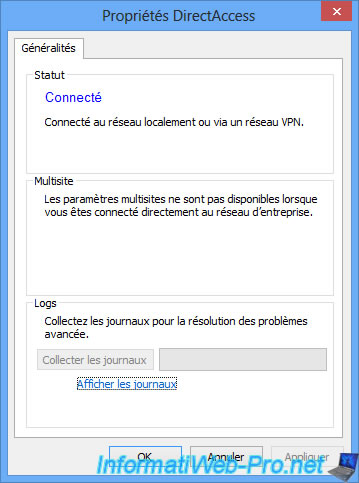
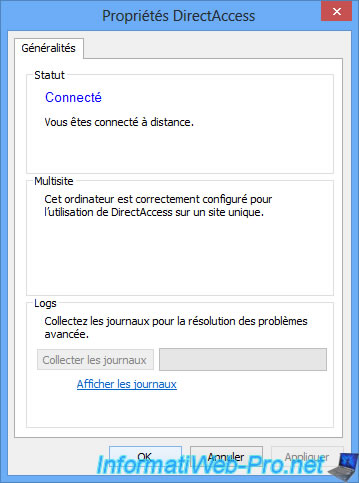
As you can see, Windows recognizes that your computer is currently connected locally to your company's network or that you are connected to it via a VPN tunnel.
To test the configuration of your DirectAccess server, we recommend that you use the Windows 8 client because :
- there are several PowerShell commands to get interesting information about client-side configuration sent by your DirectAccess server
- PowerShell is installed by default under Windows 8.
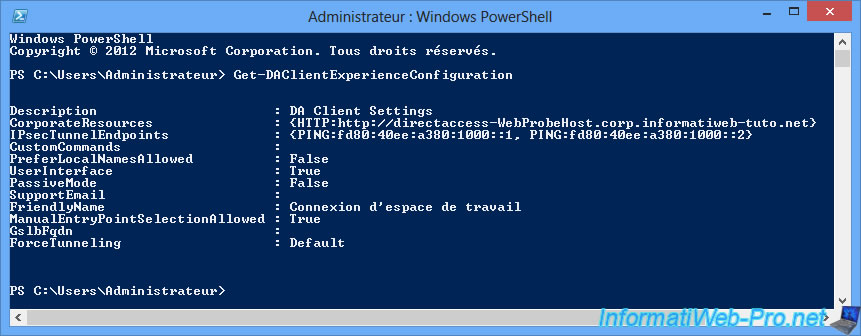
To start, you can see the configuration for the DirectAccess client experience using the PowerShell command :
PowerShell
Get-DAClientExperienceConfiguration
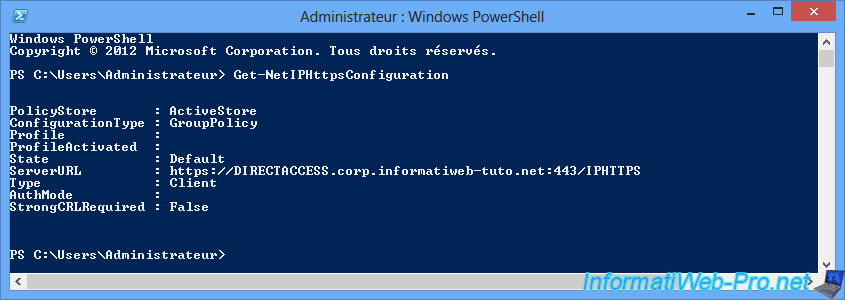
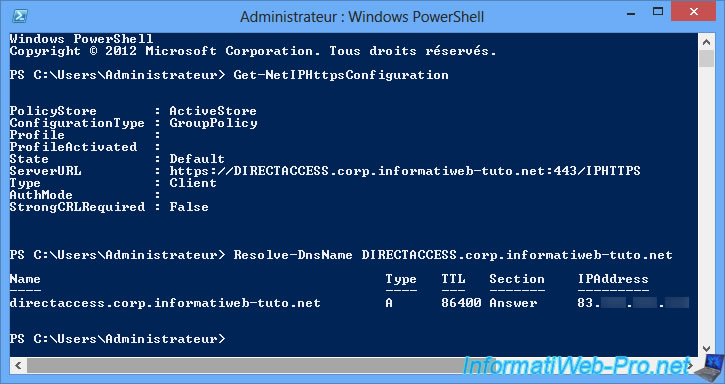
To know the IP-HTTPS configuration of the client PC, use the PowerShell command :
PowerShell
Get-NetIPHttpsConfiguration
As you can see, the client PC will connect to port 443 (HTTPS) of your DirectAccess server.
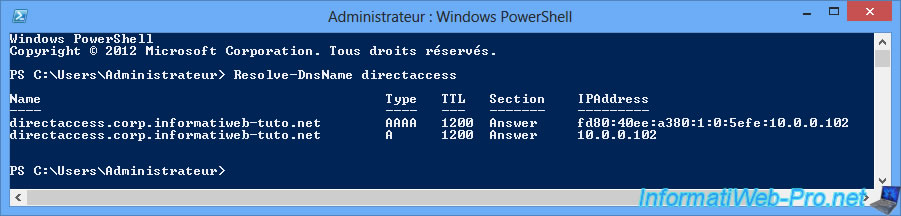
On Windows, there is a "nslookup" command to know the IP address associated with a domain name.
However, this command only uses DNS servers, but when you use the DirectAccess technology, domain names are resolved in 2 ways : with DNS servers and through the NRPT table (when necessary).
To get the correct IP address, you will need to use the PowerShell command :
PowerShell
Resolve-DnsName directaccess
Note : "directaccess" is the NETBIOS name of our DirectAccess server.
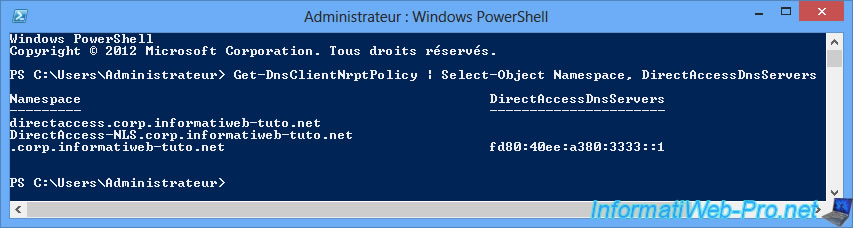
To know the NRPT table configured on the DirectAccess server, use the command :
PowerShell
Get-DnsClientNrptPolicy | Select-Object Namespace, DirectAccessDnsServers
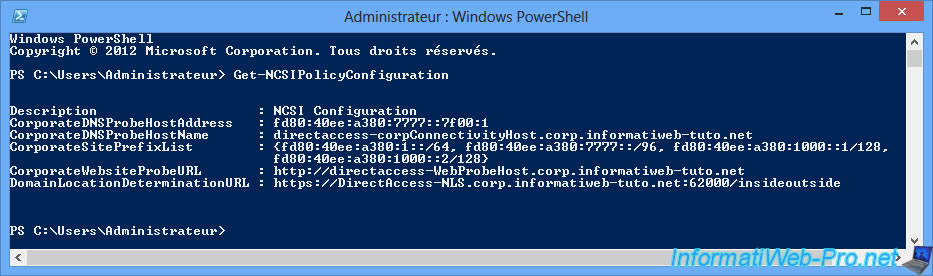
To find out the Network Connectivity Status Indicator (NCSI) configuration, use the command :
PowerShell
Get-NCSIPolicyConfiguration
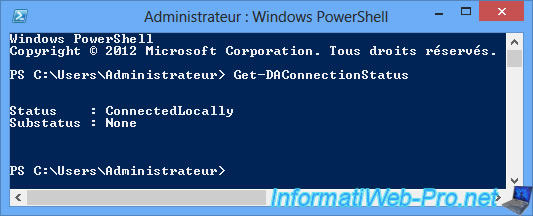
To know the status of your DirectAccess connection, use the command :
PowerShell
Get-DAConnectionStatus
If the client PC is in the company network, the status will be : ConnectedLocally
If the PC is located outside the company's network, the status will be : ConnectedRemotelly
10. Testing the DirectAccess connection from Windows 8
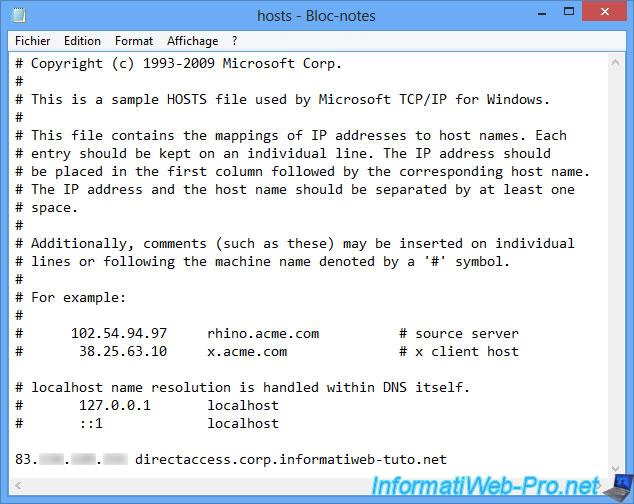
Since DNS propagation can take some time, we have added a line in the "C:\Windows\System32\drivers\etc\hosts" file of Windows 8 so that this PC finds directly the IP address associated with our "directaccess.corp.informatiweb-tuto.net" domain.
Of course, this manipulation will not be necessary in a production environment.
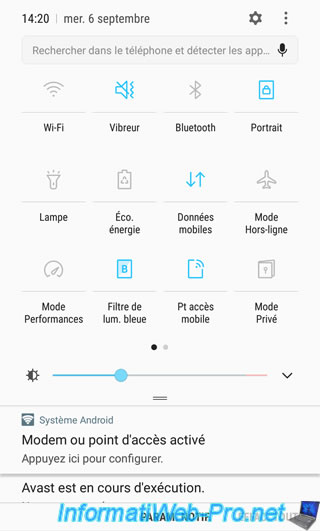
To test the remote access (from outside) to our network, we used the 3G connection of our smartphone.
Indeed, under Android, it's possible to turn your smartphone into a Wifi access point by sharing your 3G connection.
As you can see below, the mobile data (3G connection) are activated and the mobile access point is activated too.
By default, the name of the Wifi network created by our smartphone is : AndroidAP.
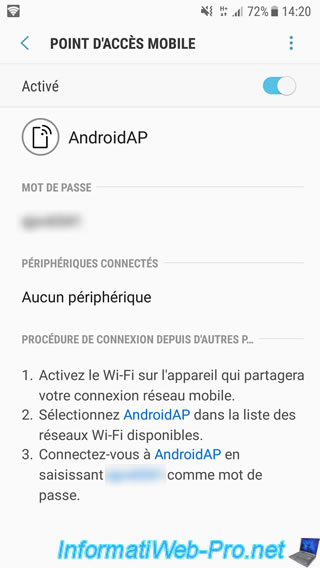
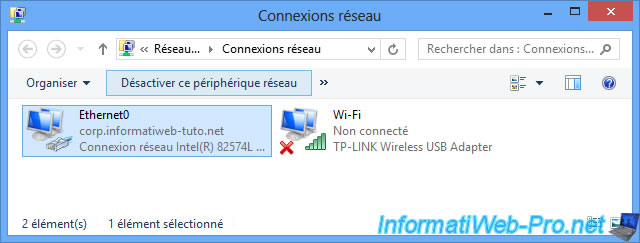
To make sure that access to our corporate intranet is done from outside, we have used a WiFi USB key and deactivated the connection to the local network.
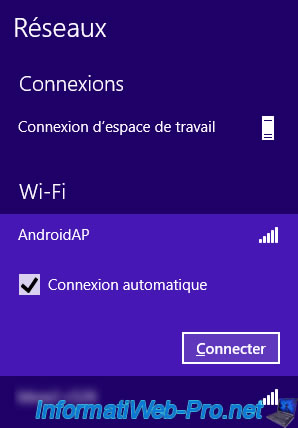
Then we connect to our "AndroidAP" Wifi network.
Once connected to this Wifi network, Windows automatically connects to our DirectAccess server (via the "Workplace Connection").
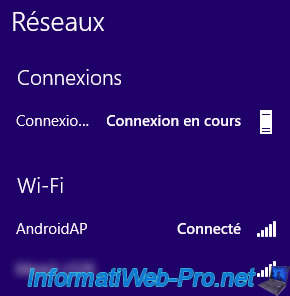
Once connected, open the properties of this connection.
As you can see, Windows detects that we are outside of our network.
Indeed, by default, we have an IP address provided by our ISP (Scarlet).
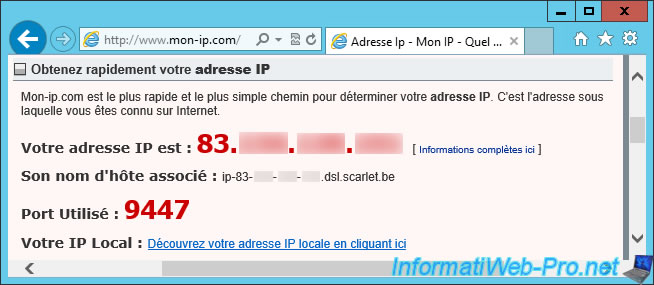
But, on this Windows 8 PC, we use the 3G connection of our smartphone.
We therefore have an IP address provided by Mobistar (our operator for mobile telephony).
In short, this little trick allows us to place this client PC outside of our network and therefore to test access from outside without leaving our home.
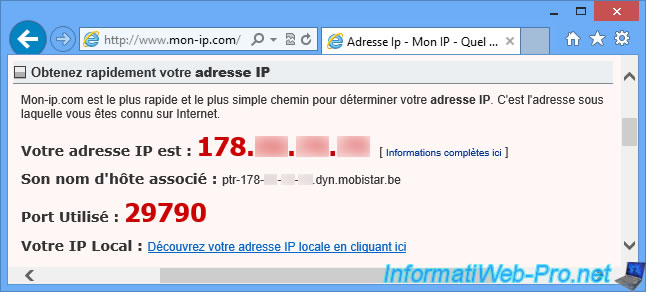
Now, if you reuse the PowerShell commands cited above, you will see that some information will change.
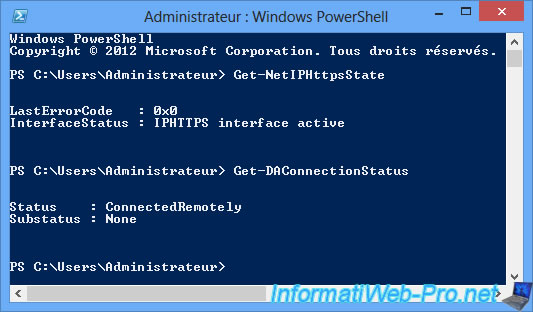
For example, using the "Get-NetIPHttpsState" command, you will see that the IPHTTPS interface is active.
PowerShell
Get-NetIPHttpsState
And the command "Get-DAConnectionStatus" will tell you that you are outside the network of your company : ConnectedRemotely.
PowerShell
Get-DAConnectionStatus
Since we installed the web interface for our CA, Windows Server also installed the IIS web server.
And as expected, this local site is displayed, even though we are physically outside the corporate network.

Network shares are also seamlessly accessible.
Note that the suffix (the domain name of your Active Directory) is not required to access network resources.
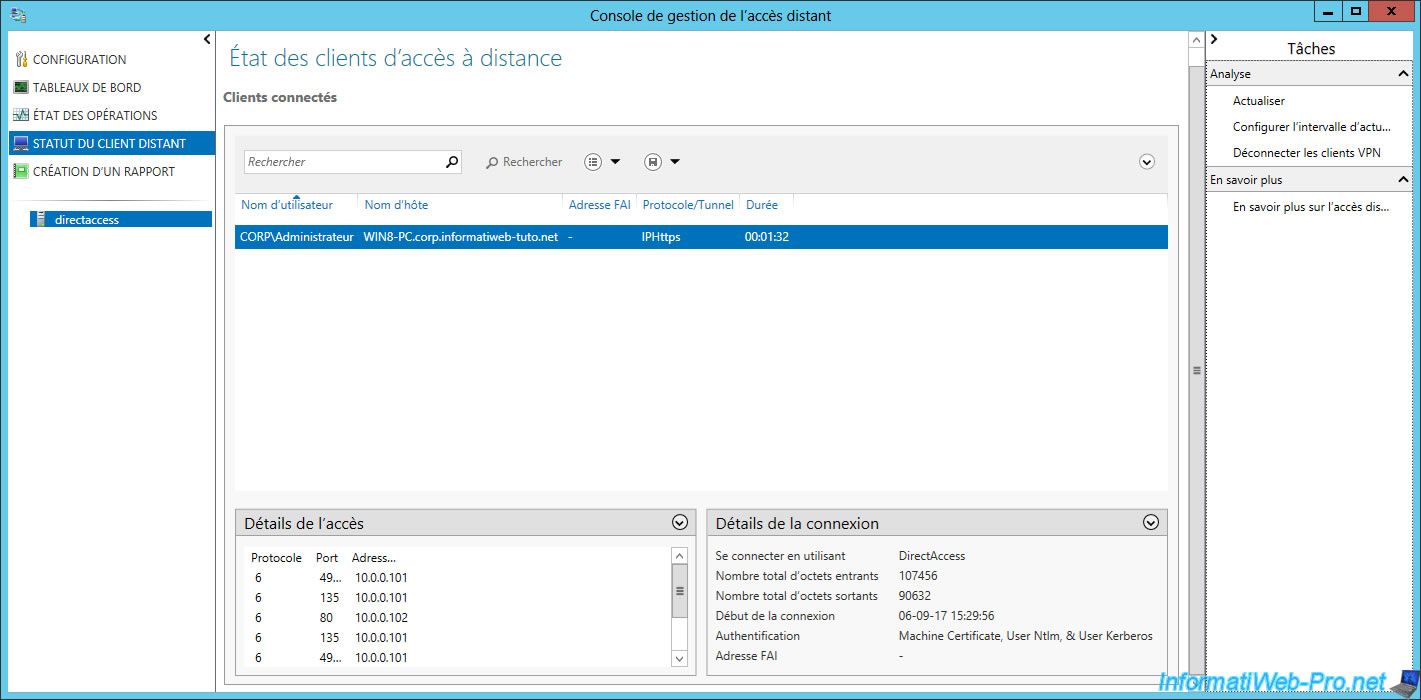
If you return on your DirectAccess server, you will see that there is an active client, including 1 DirectAccess client and 0 VPN client.
Click on the "Remote Client Status page" link at the bottom.
As you can see below, our Windows 8 PC is connected to DirectAccess via the IPHttps protocol/tunnel.
In addition, it's also indicated at the bottom that its authentication is done with machine certificate, Ntlm and Kerberos authentication.
Respectively :
- the machine certificate and NTLMv2 for the IPsec infrastructure tunnel.
- the machine certificate and Kerberos authentication (based on the user account) for the IPsec intranet tunnel.
Share this tutorial
To see also
-

Windows Server 10/15/2017
WS 2012 / 2012 R2 - DirectAccess - Manage a remote client (manage out)
-

Windows Server 10/3/2017
WS 2012/2012 R2 - DirectAccess - Configure a Windows To Go client

No comment