Create a web servers cluster with NLB on Windows Server 2012 / 2012 R2
- Windows Server
- IIS
- 22 December 2018 at 15:20 UTC
-

- 5/5
12. Configure your IIS web server for HTTPS support through the cluster
First, to secure your local IIS web servers, you will need an SSL certificate and therefore a Windows Server certification authority.
To do this, refer to our tutorial : Windows Server 2012 / 2012 R2 - Create an Enterprise Root Certification Authority (Root CA PKI)
Note that you will need the "Certification Authority" and "Certification Authority Web Enrollment" role services to submit the certificate request generated by IIS to your CA.
Important : be sure to follow the "6. Distribute the certificate to the Active Directory clients" step of the tutorial above so that your clients consider your SSL certificate as valid.
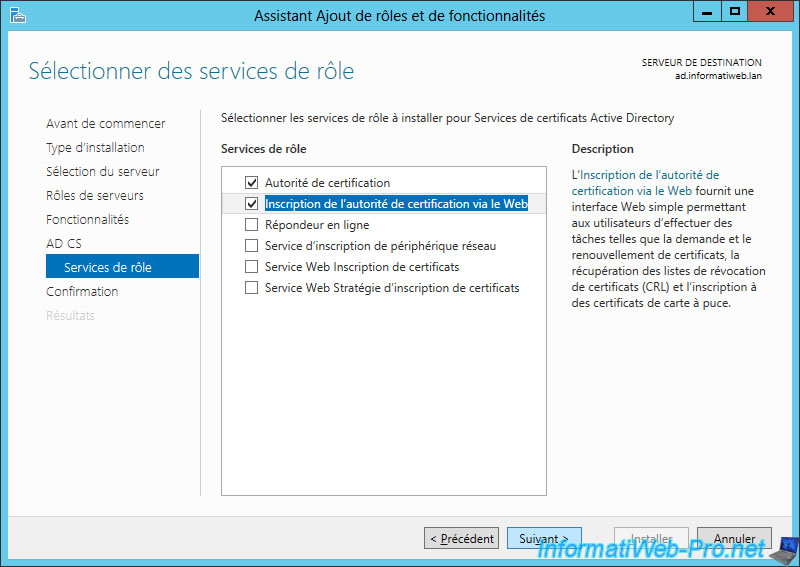
As explained earlier, when your users attempt to access your servers, they will connect to the cluster (not directly to your web servers).
Moreover, for them to be able to connect securely, they must be able to access it via a domain name.
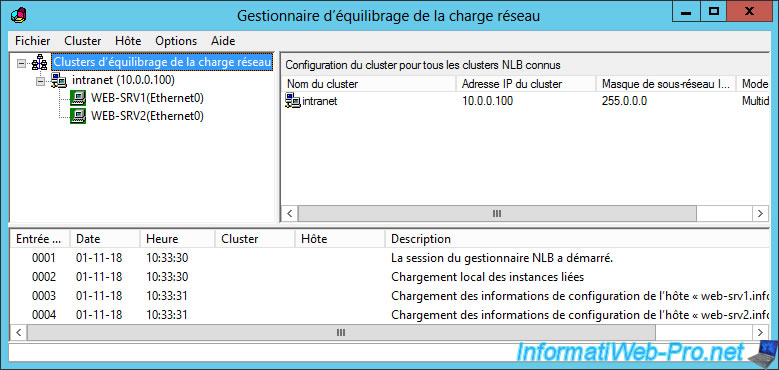
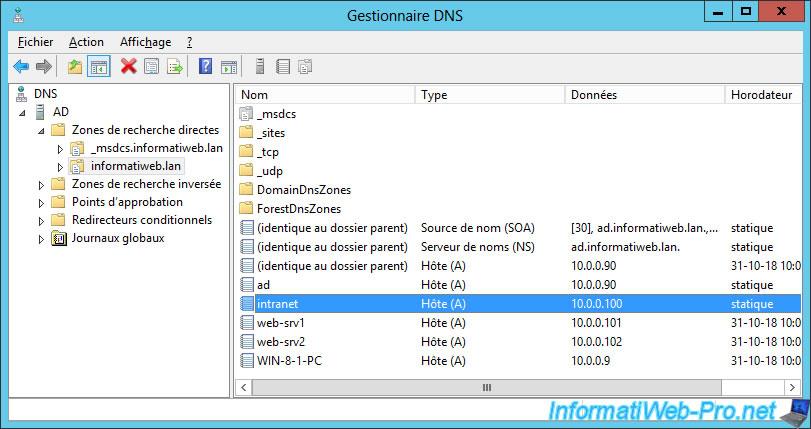
In our case, we created a subdomain (intranet.informatiweb.lan) on our local DNS server (installed during the installation of our Active Directory).
Since the procedure to secure an IIS server is almost the same (whether your web server is in a cluster or not), we will only show you what differs from the classic procedure.
If you have never secured an IIS web server, refer to our tutorial : Windows Server 2012 - Secure your web server with SSL (HTTPS)
Contrary to what you might think, the common name of the SSL certificate to be generated should not match the physical name of your web server (for example : web-srv1.informatiweb.lan), but the name used by your users to connect to your cluster.
In other words, in our case, we will need to request a certificate for this domain name : intranet.informatiweb.lan
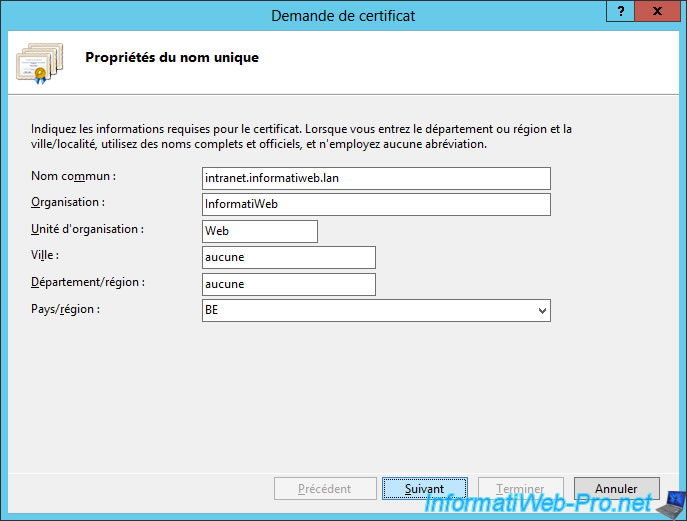
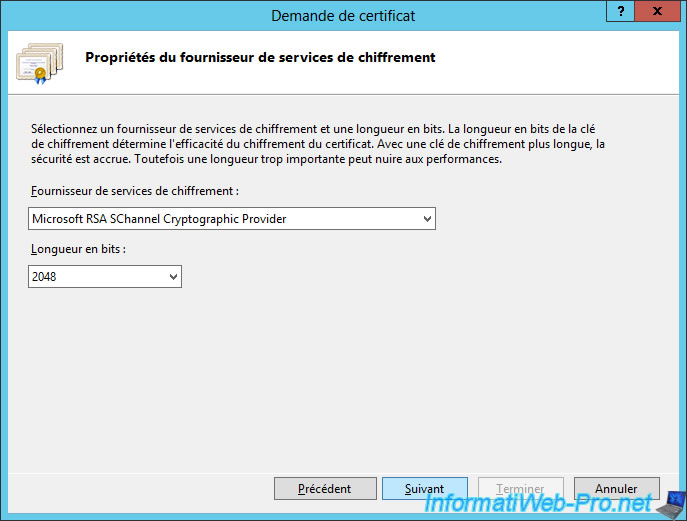
Select the key length supported by your certification authority (CA).
Note : this information was chosen during the installation of your Windows Server certification authority.
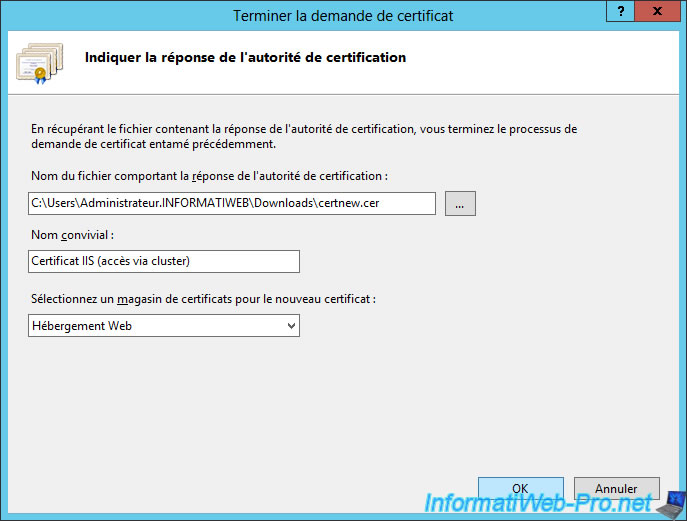
Finally, after the certificate is generated by your CA, import the certificate and specify "IIS certificate (cluster access)" as the friendly name.
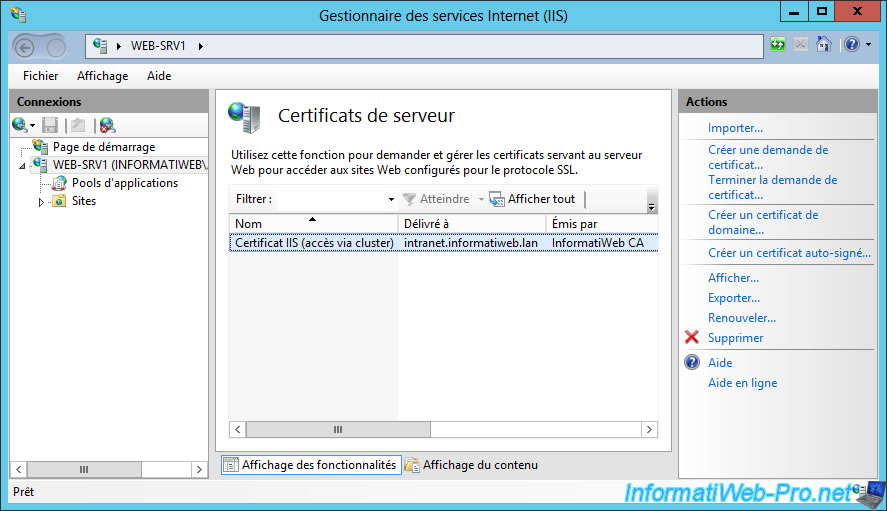
Refresh the "Server certificates" list from the Internet Information Services (IIS) Manager and you will see it appear.
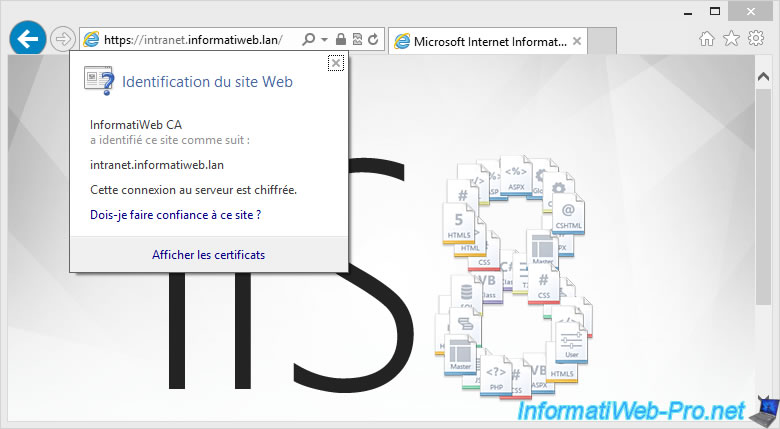
In addition, you will see that your certificate has been issued to [your cluster name] and has been issued by your CA (in this case : InformatiWeb CA).
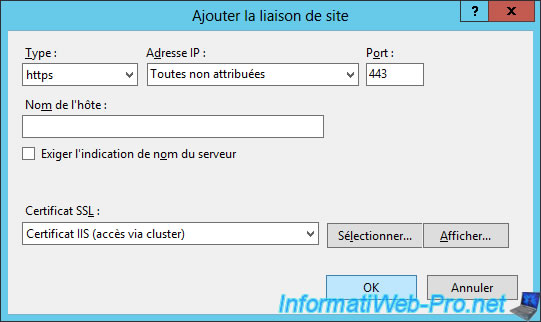
Add the HTTPS binding to your default web site and select your "IIS certificate (cluster access)" certificate.
Then, restart the default website and try to access it from a client PC.
If your authority's certificate has been added to the "Trusted Root Certification Autorities" list of your client PCs (as explained in our tutorial "Windows Server 2012 / 2012 R2 - Create an Enterprise Root Certification Authority (Root CA PKI)"), you will see that your local website is secure in HTTPS and that your authority has correctly identified this site as : intranet.informatiweb.lan


No comment