- Articles
- DNS
- 01 May 2018 at 11:18 UTC
-

DNSSEC (Domain Name System Security Extensions) certifies the response obtained from a DNS server supporting DNSSEC technology.
- How the DNS system works
- Overview of how DNSSEC works
- Why deploy DNSSEC ?
- Do I have to sign my DNS zone ?
- What is the impact of DNSSEC on the performance of your DNS server ?
1. How the DNS system works
The Domain Name System (DNS) was originally based on root DNS servers managed by a dozen different organizations in different countries.
Now, DNS is based on a hierarchical system consisting of multiple DNS servers where each server manages one or more zones.
When you try to access our site "www.informatiweb-pro.net", the DNS client installed on your computer will make several requests to different DNS servers :
- it will first ask a root server (one of them is managed by ICANN) : who manages the .net extension ?
- then, he will ask the ".net" DNS server "who manage the informatiweb-pro.net domain ?" : in this case, the server will give him the address of the DNS server of our host
- and finally, it will ask the DNS server of our host (where is the DNS zone "informatiweb-pro.net") to which IP address corresponds the "www.informatiweb-pro.net" subdomain.
Since the final answer depends on responses from the parent DNS servers, it's important to secure the DNS system on all DNS servers in the world.
It's for this reason that DNSSEC was invented. But its implementation will obviously take time since there are hundreds or even thousands of DNS servers in the world.
2. Overview of how DNSSEC works
DNSSEC (Domain Name System Security Extensions) is a series of extensions to secure the DNS system by allowing :
- DNS servers to communicate valid and authentic DNS responses to clients
- DNS clients to check if the answer is authentic or not (to avoid trusting a hacker without knowing it)
2.1. How DNSSEC works
If the authoritative DNS server supports DNSSEC, its zones can be signed using this technology.
For this, when signing the zone, DNSSEC will add multiple DNS records (digital signatures) to provide an authentic response to different DNS clients.
As you can see on this schema (retrieved from Microsoft Docs), each DNS record (including global information, such as : the Name Server (NS) list and SOA) will be digitally signed.
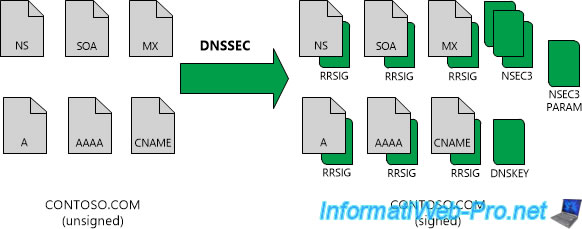
2.2. Records created by DNSSEC
As you can see, signing the zone via DNSSEC has resulted in the creation of several types of records :
- RRSIG : digital signature associated with a DNS record (SOA, NS, or even a classic A record)
- NSEC : allows the DNS server to certify to the user that a particular DNS record doesn't exist or no longer exists. This prevents hackers from providing a false answer by taking advantage of the fact that a classic DNS server would have replied : sorry I don't have the answer (since the desired subdomain doesn't exist or no longer exists).
- NSEC3 : it's simply an improvement of the NSEC mentioned above
- NSEC3PARAM : this record determines which NSEC3 record should be returned in the DNS response for DNS records that don't exist.
- DNSKEY : public key of the DNS zone used by the other DNS servers to check whether the obtained signature is valid or not. This makes it possible to validate data from one DNS server to another, which prevents hackers from doing DNS spoofing.
- DS : this type of record is used to secure DNS delegations. For example : when you delegate the management of a subdomain to another DNS server. For example : for a company present in several countries.
All these DNS records are created automatically when the zone is signed, except for "DS" records.
In addition, the type of NSEC (or NSEC3) record depends on the choice you make when signing the zone. NSEC or NSEC3 records are automatically added.
Indeed, you will not be able to combine both in the same zone.
Warning : note that the DS record (used to secure DNS delegations) is not automatically created when the zone is signed and must be created manually.
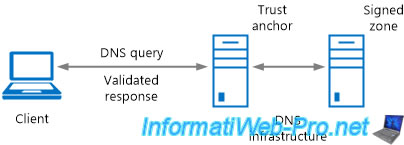
2.3. Trust points or trust anchors
DNSKEY and DS records are called trust points or trust anchors.
These trust points must be distributed to non-authoritative DNS servers in your DNS zone so that they can validate the signatures received with your DNS response.
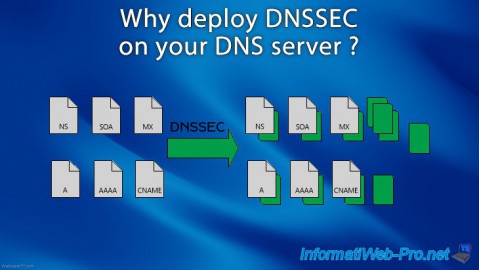
3. Why deploy DNSSEC ?
As previously explained, deploying DNSSEC will help protect DNS clients (users) from fake DNS responses sent by hackers.
But, for this to be possible, everyone needs to implement DNSSEC on its DNS servers :
- the organization managing the root zone of the DNS : ICANN (for example)
- companies managing their domains on their own DNS servers
- "intermediate" DNS servers created, for example, by ISPs
Thus, if everyone checks that the response obtained from the parent server is authentic, the user can be sure that the answer obtained will be authentic and that it has not been manipulated by a hacker.
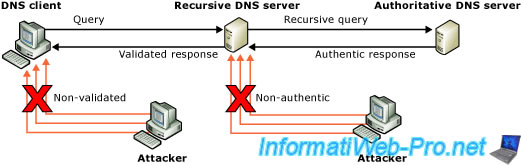
That being said, customers also need to be compatible with this technology so they can use it instead of the traditional DNS system.
With Windows Server, it's also possible to configure Windows clients (compatible with DNSSEC) to make its use mandatory through the Name Resolution (NRPT / Name Resolution Policy Table) group policy (GPO).
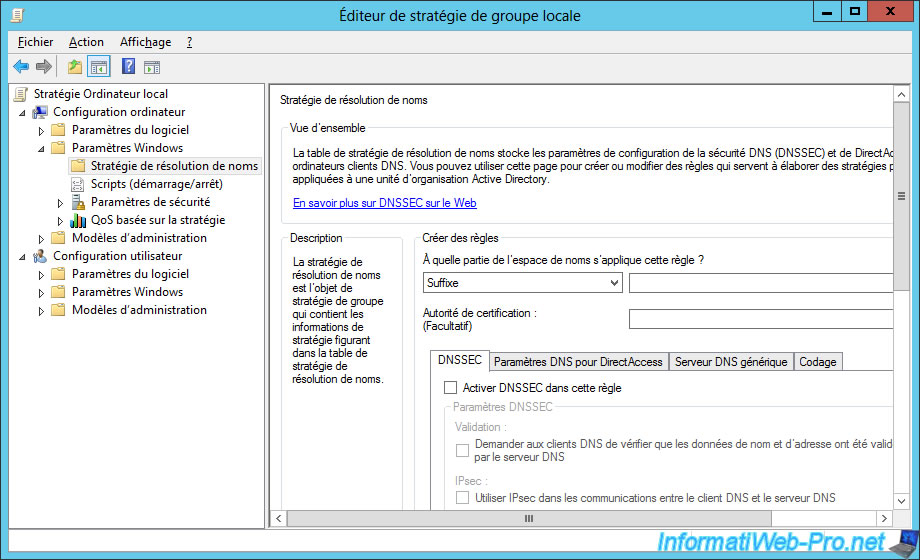
Warning : if you want to make the use of DNSSEC mandatory, be aware that DNSSEC must be supported by each DNS server needed to obtain the final response.
4. Do I have to sign my DNS zone ?
Yes and no. It all depends on your infrastructure and the zones you will manage on your DNS server.
In addition, signing a DNS zone creates additional DNS records, as well as encrypting and decrypting DNS messages.
This can make managing the DNS server more complicated and can impact the performance of your DNS server if it receives a lot of requests simultaneously.
Then, we must also take into account that it will be necessary to renew periodically the security keys used to sign the zone to prevent a hacker from guessing them.
4.1. Do I have to sign my DNS zone if my DNS server is accessible from the Interne ?
Yes, because your DNS server may be targeted by hackers and your DNS zone will be accessed by many clients over the Internet.
So it's important to sign it to be able to provide authentic answers to your clients and protect them from false DNS answers sent by hackers.
In addition, these zones are generally not part of an Active Directory infrastructure. It's therefore useful and recommended to sign your DNS zones.
4.2. Do I have to sign my DNS zone used locally (for an intranet) ?
Generally, local DNS zones are much less vulnerable to attacks, because they are not accessible from outside (the Internet) or because security protocols have been put in place in your network to protect you from them.
If you sign these DNS zones and these zones are also part of an Active Directory infrastructure, DNS server maintenance may be more complicated. Indeed, the number of DNS records can grow visibly depending on the number of computers in your network and linked to your Active Directory.
It's therefore advisable to sign them only if you consider that this is necessary or because :
- the DNS server is managed by a government agency
- or the security policy of your company requires you
5. What is the impact of DNSSEC on the performance of your DNS server ?
Enabling DNSSEC on your DNS server impacts the performance of your DNS server :
- on Windows Server 2012 and 2012 R2, signed zones will use up to 5 times more RAM than an unsigned zone
- the response to DNS queries will be longer because of the increase in the number of packets sent via the network for the validation of the chain of trust, ...
- your server's processor may also be used more often when using a signed zone because of KSK and ZSK keys.
For more information, see the Microsoft Docs DNSSEC Performance Considerations page.
Sources :
Share this tutorial
To see also
-

Windows Server 1/15/2013
WS 2008 - Create a DNS server
-

Windows Server 4/15/2018
WS 2012 / 2012 R2 - Create a DNS server and delegate subdomains
-

Windows Server 4/25/2018
WS 2012 / 2012 R2 - Create a secondary DNS server
-

Windows Server 5/11/2018
WS 2012 / 2012 R2 - Sign your DNS zones with DNSSEC

You must be logged in to post a comment