- Firewall
- pfSense
- 21 May 2025 at 13:33 UTC
-

As with a physical router, when you want to manage this type of network device, you can do so from the LAN network, but not from the WAN network.
With pfSense, it's the same. By default, you can only access the pfSense web interface from the default LAN network.
However, it may be interesting to be able to access it from outside (WAN network) in certain cases. Although this is less secure.
- Unable to access web interface from default pfSense WAN interface
- Allow access to the pfSense web interface from the WAN network
- Allow private networks on the WAN
- Access to the pfSense web interface via the WAN interface
1. Unable to access web interface from default pfSense WAN interface
As you can see below, by default, you can access the pfSense web interface from the LAN.
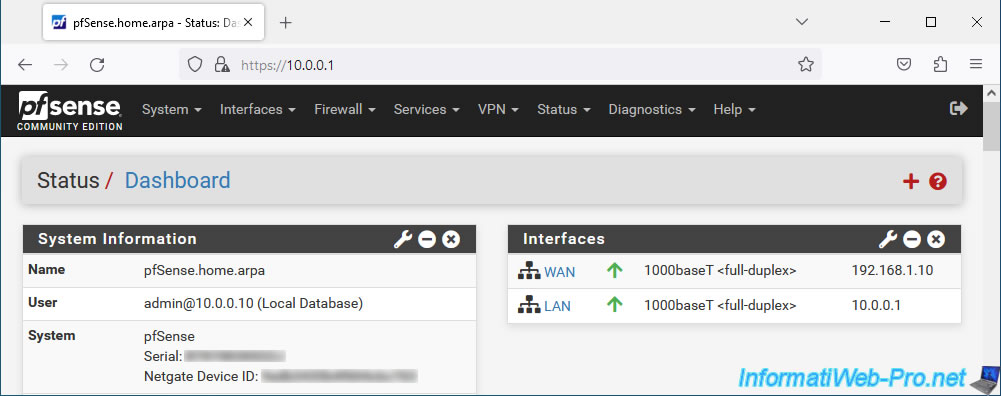
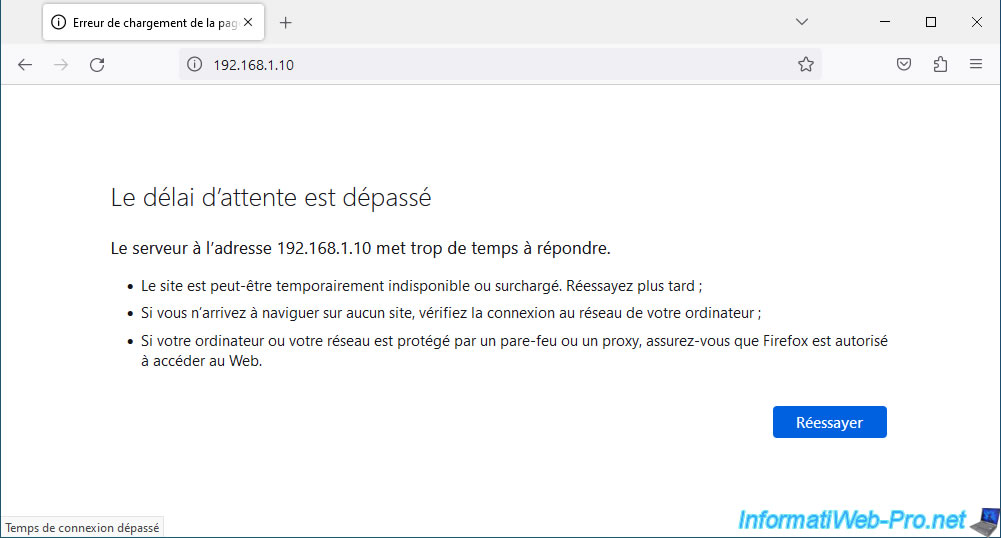
But if you try to access it through the WAN interface, you will not have access.
With Mozilla Firefox, you will receive the "Timed out" error. This is because it is the pfSense firewall that blocks the network connection by default.
2. Allow access to the pfSense web interface from the WAN network
To access the pfSense web interface from the WAN network, go to: Firewall -> Rules.
In the "LAN" tab of the pfSense firewall, you will notice that an "Anti-Lockout Rule" exists by default and allows you to access the web interface (in HTTP (port 80) and in HTTPS (port 443)) indicating the LAN IP address of pfSense.
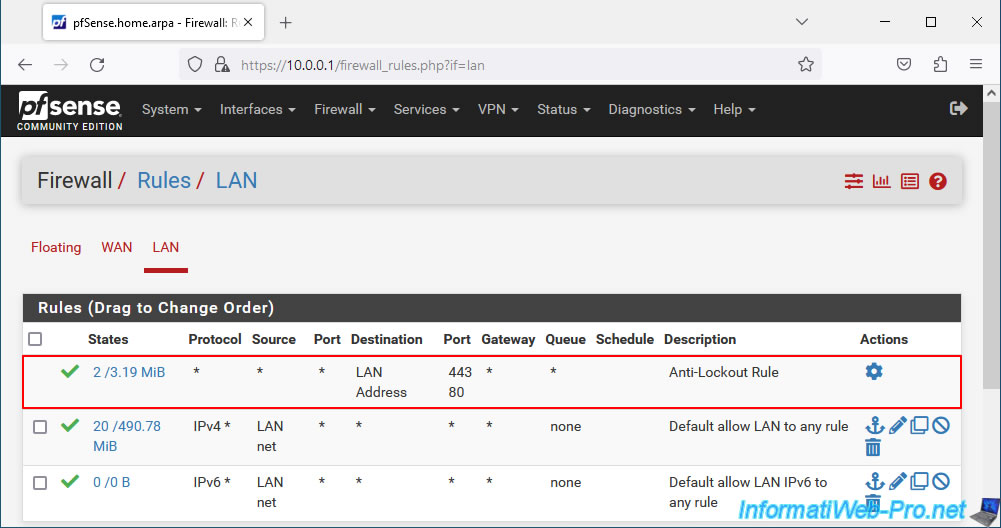
For security reasons, this rule does not exist for the pfSense WAN interface.
In the "WAN" tab of the pfSense firewall, click on: Add.
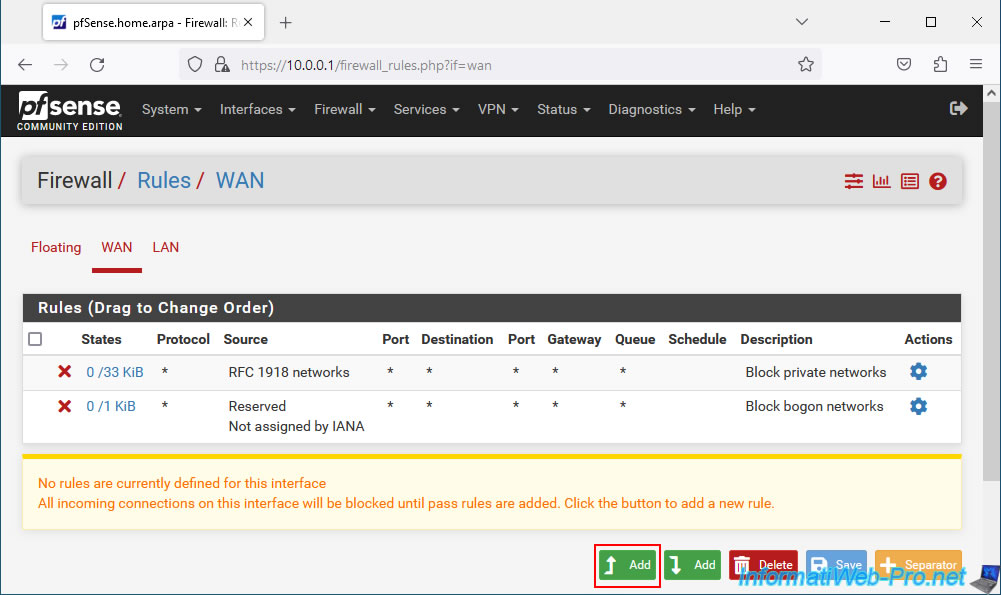
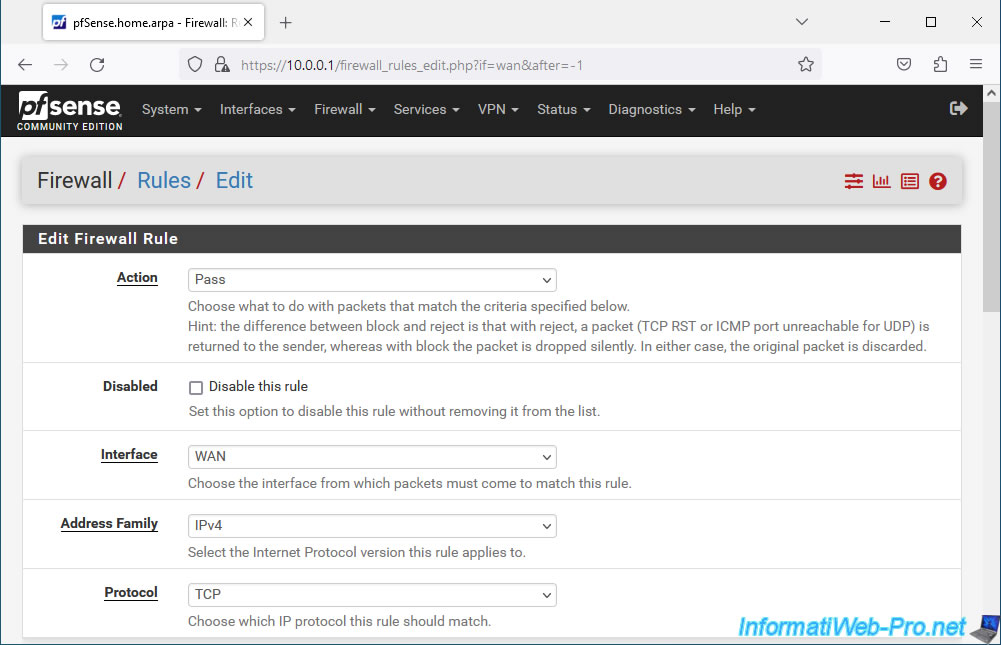
Configure this rule like this:
- Action: Pass. Allows network traffic to be allowed.
- Interface: WAN. This rule concerns the pfSense WAN interface.
- Address Family: IPv4. In our case, pfSense only uses IPv4 on its WAN interface.
But, you could also select "IPv4+IPv6" if you wish to authorize the 2 versions of the IP protocol for the WAN interface. - Protocol: TCP. The web interface is accessible in HTTP (80) and HTTPS (443) which are TCP protocols.
- Source: any. For convenience, select "any" to allow everyone to access the pfSense web interface.
For security reasons, you will be able to allow a single IP address by selecting "Single host or alias" and entering your IP address to the right.
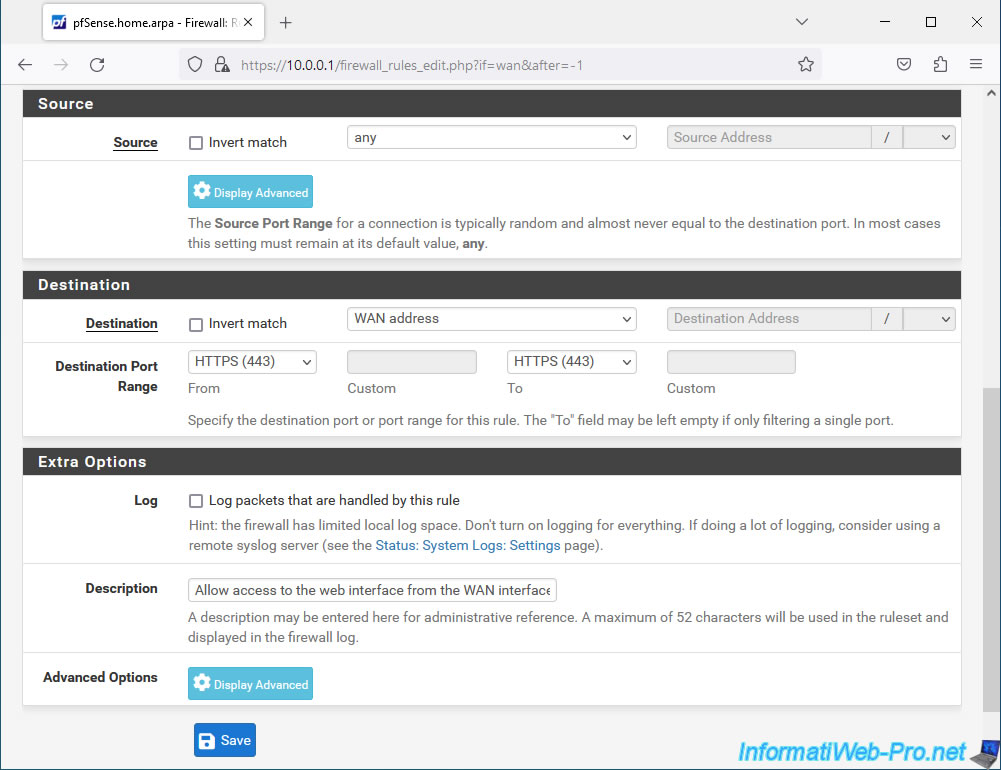
You can also choose to specify a specific network by selecting "Network" or only allow those that are part of the WAN network by selecting "WAN net". - Destination: WAN address. Indicates that the destination IP address matches the IP address of the pfSense WAN interface.
- Destination Port Range: HTTPS (443). Only allows access to the web interface via the HTTPS protocol.
If you also want to allow the HTTP protocol (which is generally redirected to the HTTPS version), create a 2nd rule for the "HTTP (80)" port. - Description: allow access to the web interface from the WAN interface.
Then, click: Save.
Source : Allowing Remote Access to the GUI | pfSense Documentation.
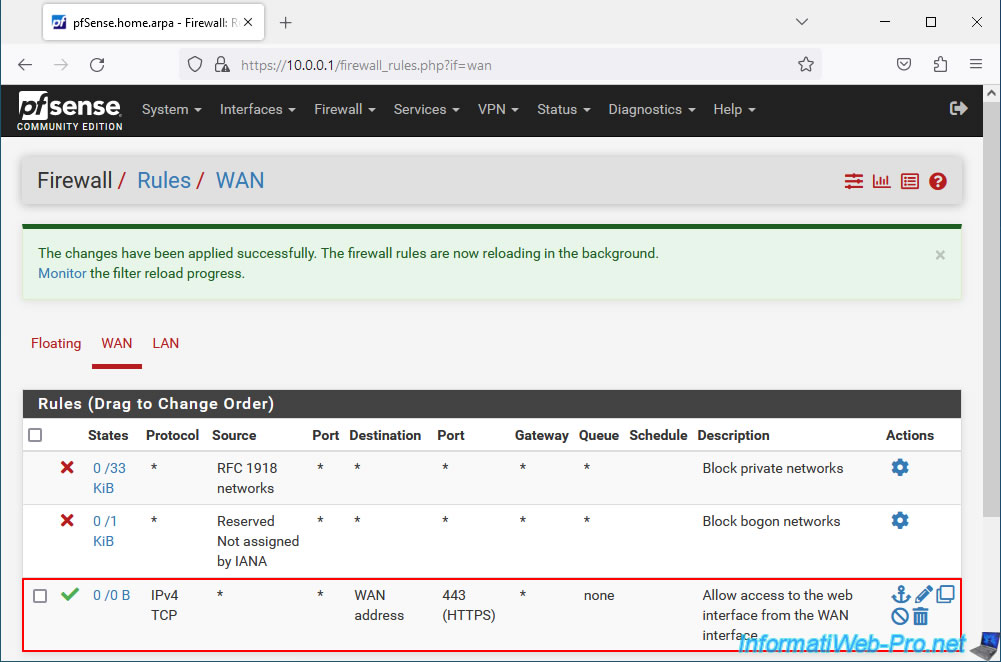
Your new rule appears.
Click: Apply Changes.
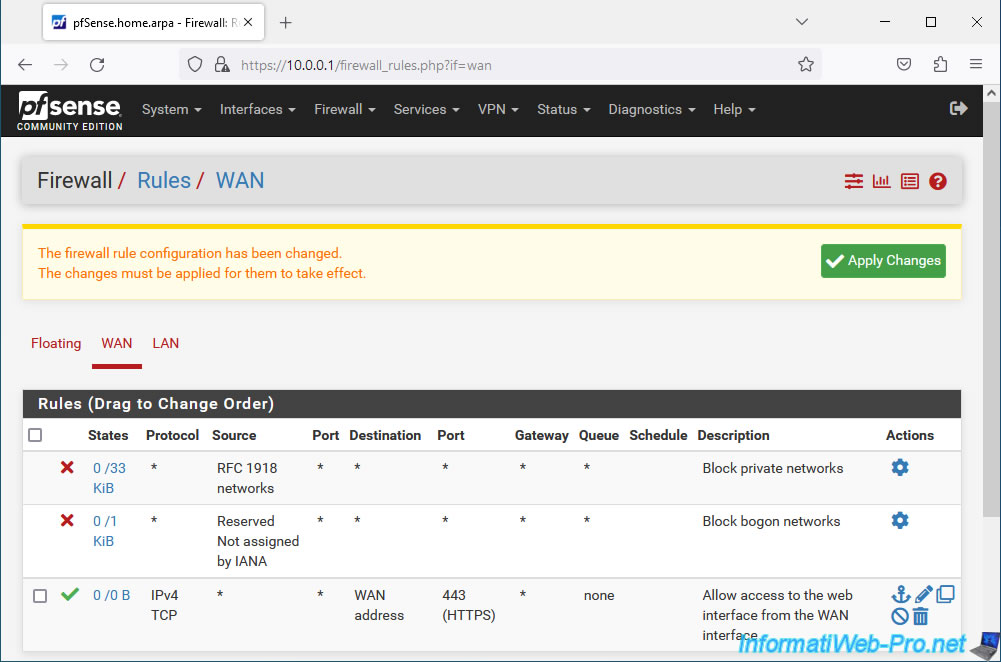
The new rule has been applied.
3. Allow private networks on the WAN
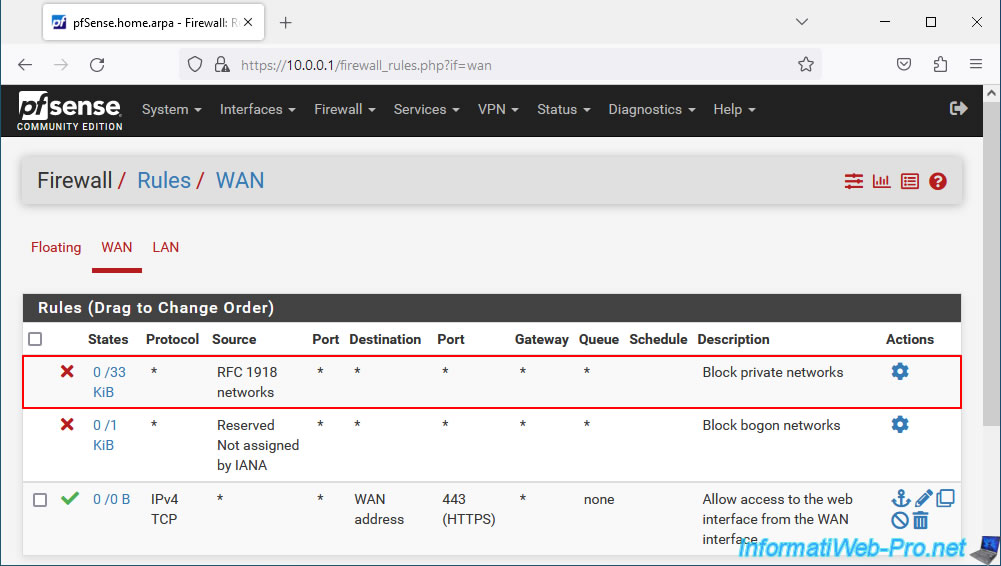
If pfSense has a private (local) IP address for its WAN interface, you must disable the rule below:
Plain Text
Source : RFC 1918 networks / Description : Block private networks.
To do this, click on the gear icon located to the right of this ruler.
Note: if this rule does not appear in your case, you do not need to do anything.
This means that the "Block private networks..." option is already disabled in your WAN interface configuration.
The WAN interface page appears.
Note: this page is also accessible via the "Interfaces -> WAN" menu.
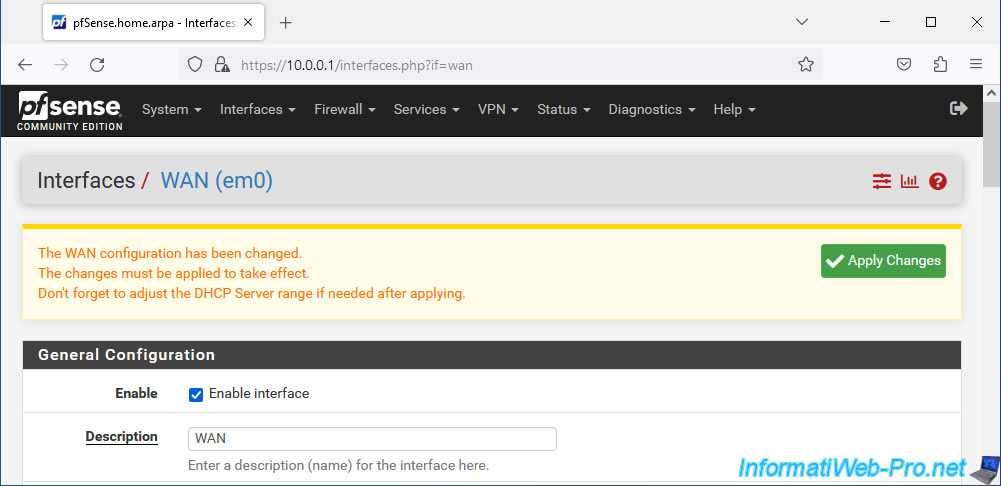
At the bottom of the page, uncheck the "Block private networks and loopback addresses" box.
Then, click Save.
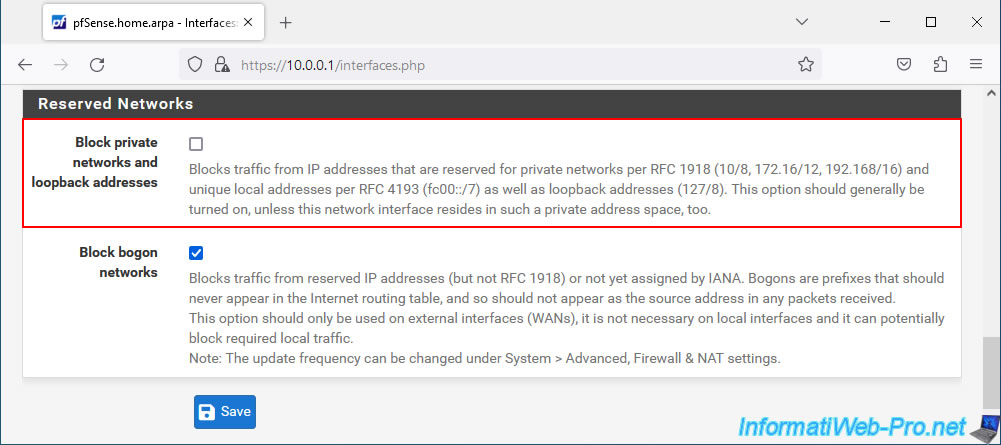
At the top of the page, click: Apply Changes.
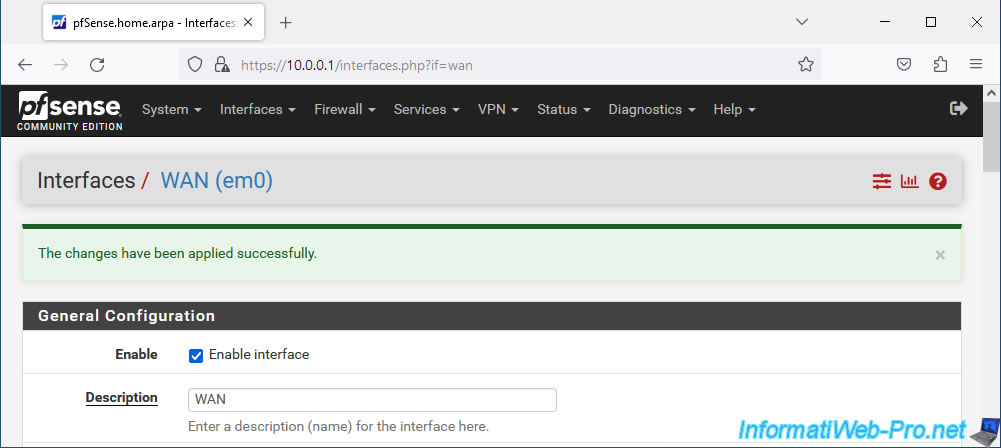
The change has been saved.
4. Access to the pfSense web interface via the WAN interface
Access the pfSense web interface through its WAN IP address using the HTTPS protocol.
Important : the rule created in this tutorial only allows access to this web interface via the WAN interface on port 443 (HTTPS). Not on port 80 (HTTP).
This is for security reasons.
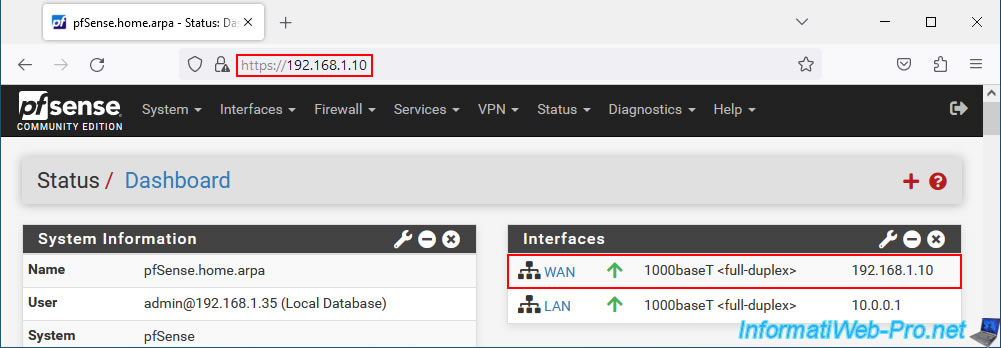
As expected, you can access pfSense's web interface via its WAN IP address.
Share this tutorial
To see also
-

Firewall 8/13/2025
pfSense 2.6 - Create a captive portal
-
Firewall 9/12/2025
pfSense 2.6 - Create a site-to-site (S2S) VPN tunnel via OpenVPN secured with shared key (PSK)
-

Firewall 5/28/2025
pfSense 2.6 - Create and use VLANs
-

Firewall 8/29/2025
pfSense 2.6 - Implement Multi-WAN (Dual-WAN)


You must be logged in to post a comment