- VMware
- VMware vCenter Server (VCSA), VMware vSphere
- 28 August 2024 at 16:24 UTC
-

In a VMware infrastructure, you have the ability to limit network bandwidth at different levels of your virtual network: at the virtual switch level and at the port group level on them.
Limiting bandwidth in a virtual infrastructure is very important to avoid service unavailability. Indeed, if network traffic is too high in your company, access to your various services can become very slow.
On VMware vSphere, you can use standard (vSS) or distributed (vDS) virtual switches.
In this tutorial, we will use a virtual standard switch (vSS). Which means that only outgoing traffic will be limited.
- Download iPerf3 (to test network bandwidth)
- Test your network bandwidth with iPerf3
- Limit network bandwidth (outgoing traffic only)
- Test bandwidth throttling
1. Download iPerf3 (to test network bandwidth)
To test the network bandwidth between 2 virtual machines under Windows, you can use the "iPerf" utility which is free and very lightweight.
Note that this utility is also available on all other platforms: Linux (Ubuntu, Debian, ...), Android, ...
In our case, we will use version 3.1.3-win64 (which is the latest version at the time we are making this tutorial).
2. Test your network bandwidth with iPerf3
For this tutorial, we used a virtual VMware infrastructure with:
- 2 VMware ESXi hosts: esxi1 and esxi2.
- 1 VMware vCenter Server (VCSA): vcsa
- 2 Windows 10 virtual machines: 1 virtual machine per VMware ESXi host
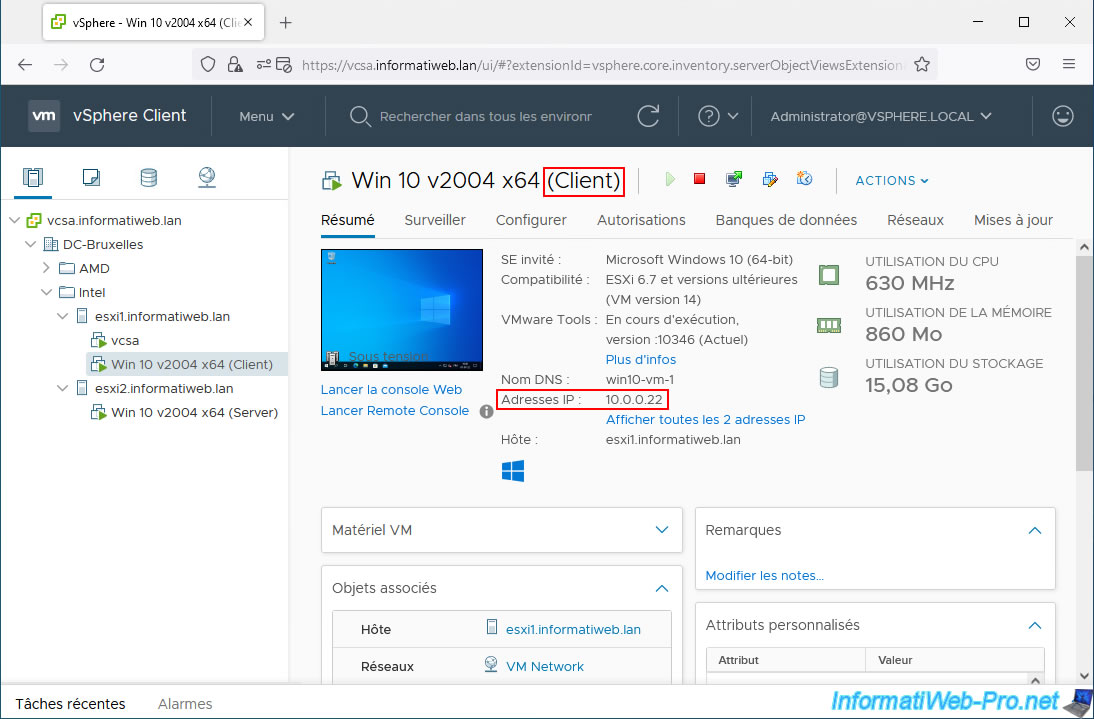
The virtual machine "Windows 10 v2004 x64 (Client)" is located on our host "esxi1" and has the IP address "10.0.0.22".
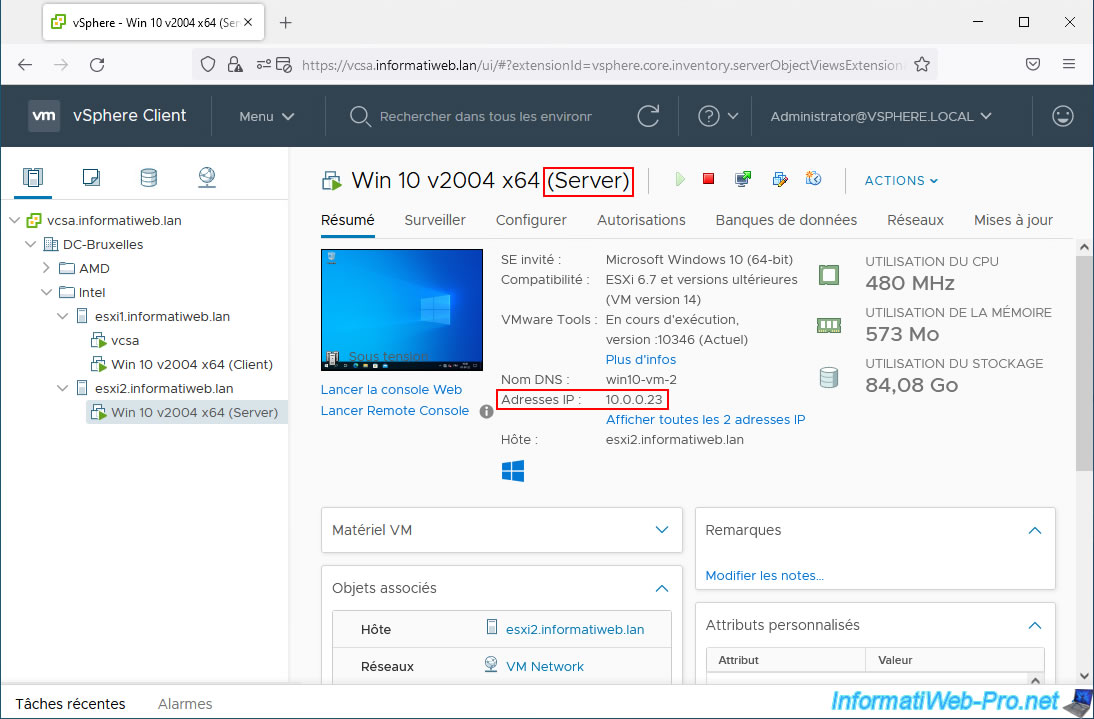
The virtual machine "Win 10 v2004 x64 (Server)" is located on the other host "esxi2" and has the IP address "10.0.0.23".
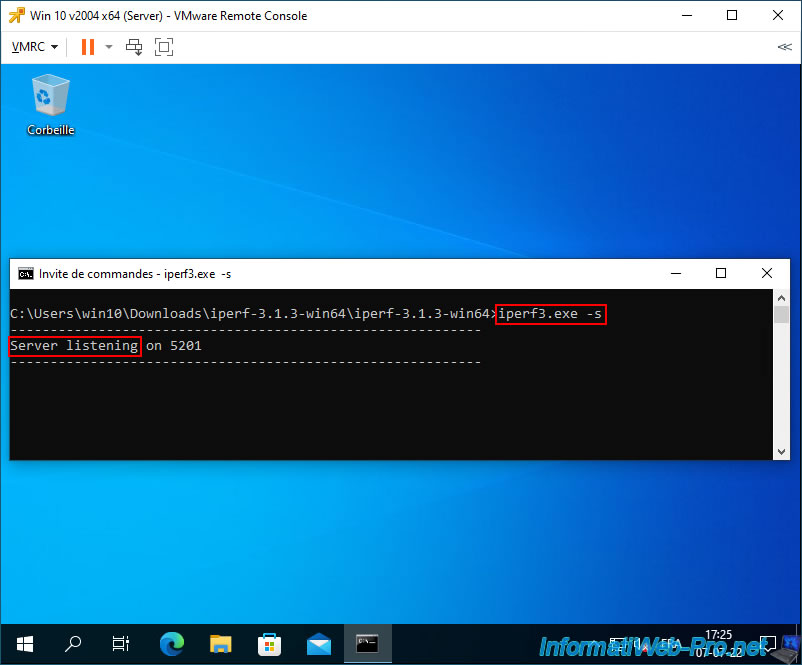
On the "Windows 10 v2004 x64 (Server)" virtual machine, launch "iPerf" as a server using the command:
Batch
iperf3.exe -s
Which will display this:
Plain Text
Server listening on 5201
When iPerf is first launched, a Windows security alert will appear.
Click "Allow Access" to allow this program in the default Windows Firewall (Windows Defender).
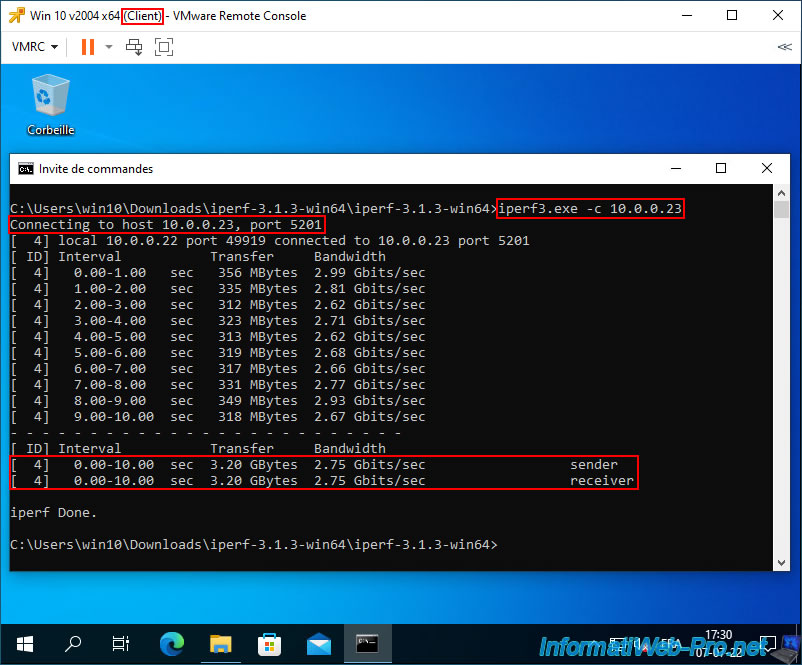
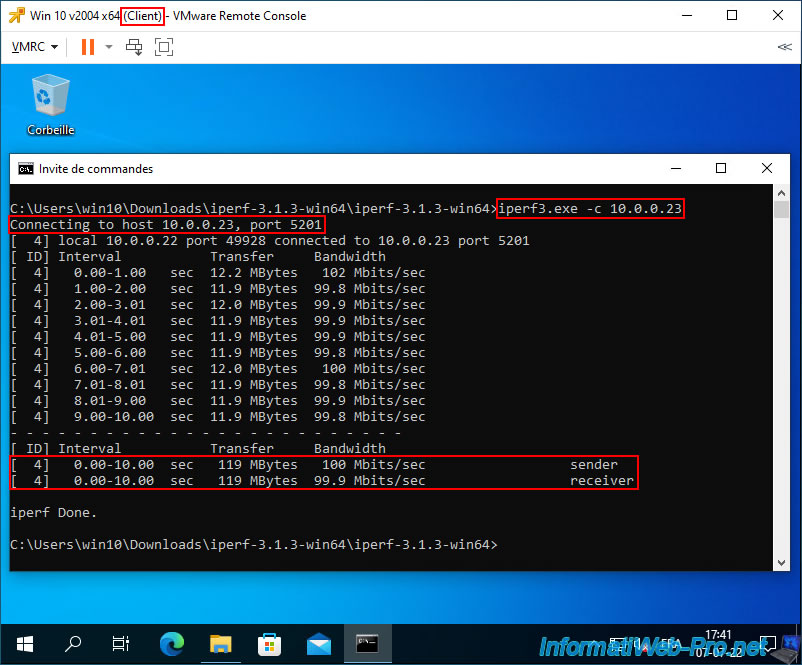
On the other virtual machine, in our case "Win 10 v2004 x64 (Client)", launch iPerf as a client so that it connects to your iPerf server.
To do this, use the command below, replacing the IP address indicated with the IP address of your iPerf server:
Batch
iperf3.exe -c 10.0.0.23
As you can see, in our case the current network bandwidth is around 2.75 Gbits/sec.
Which makes sense given that we used virtual VMware ESXi hypervisors and the network is therefore entirely virtual between our 2 virtual machines.
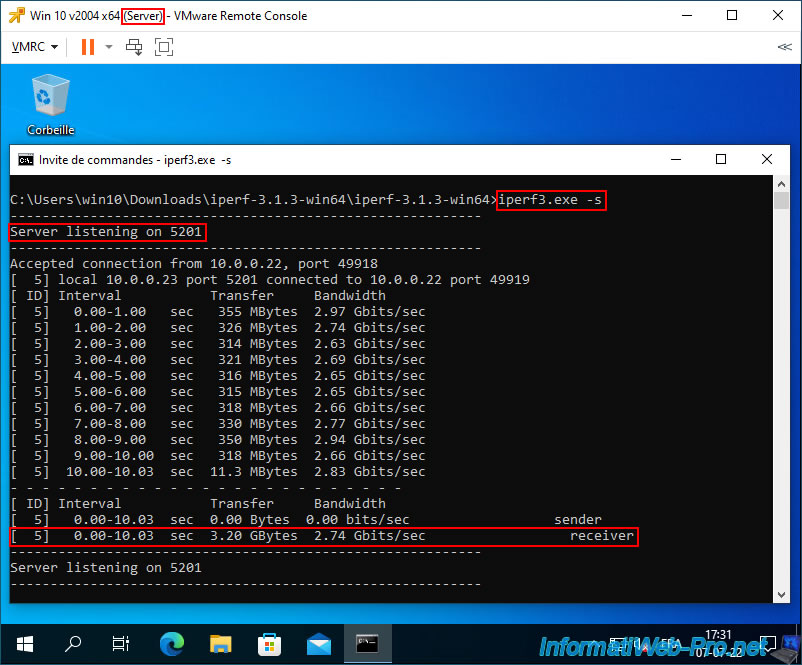
On the server side, you will see almost the same thing.
3. Limit network bandwidth (outgoing traffic only)
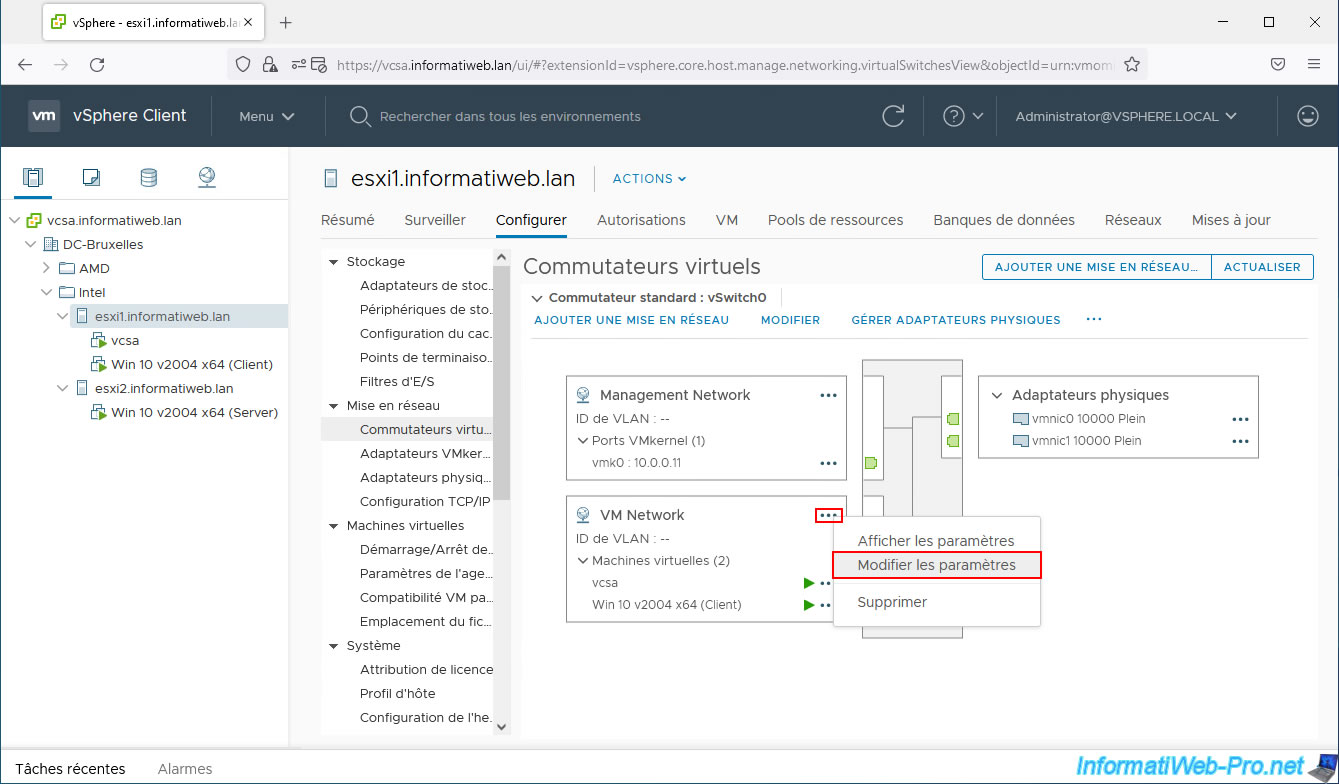
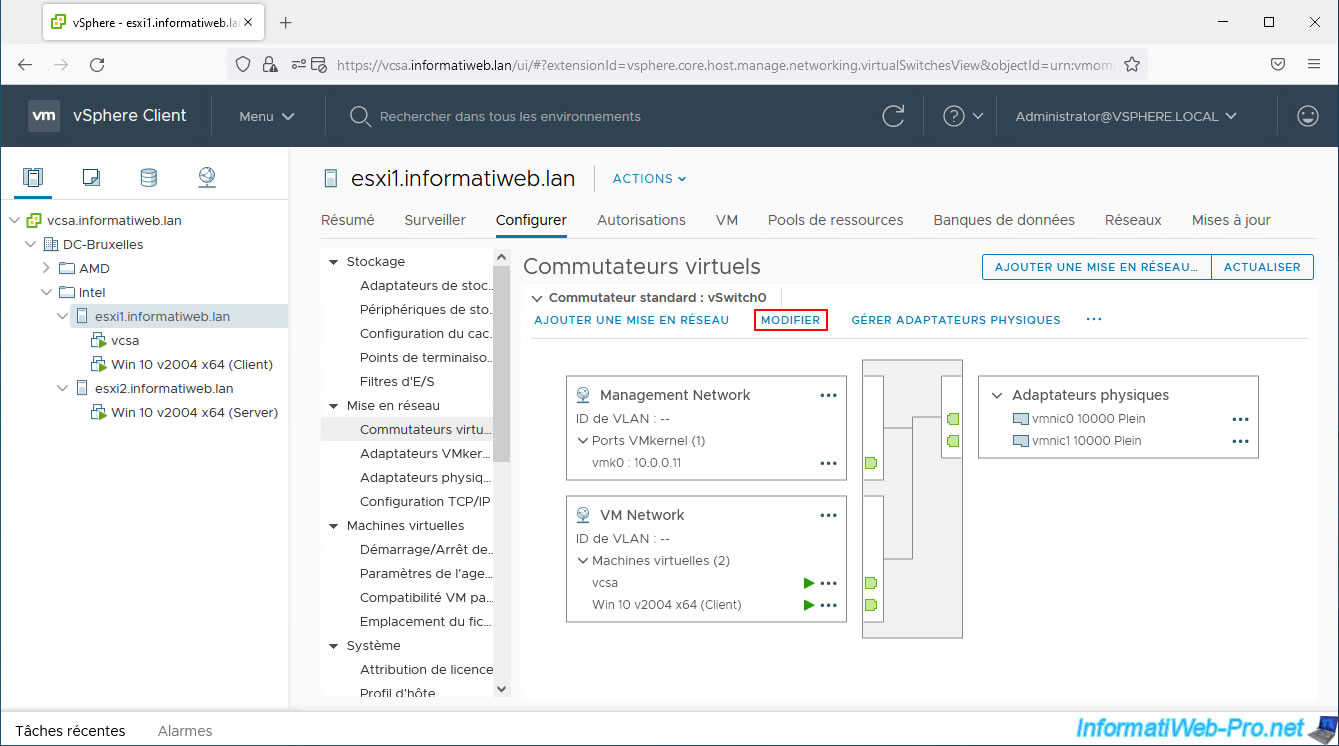
To limit the network bandwidth of your virtual machines, select the VMware ESXi host where your guest virtual machine is located and go to "Configure -> Networking -> Virtual switches".
Next, click the "..." icon of the port group where your virtual machine is connected and click "Edit Settings".
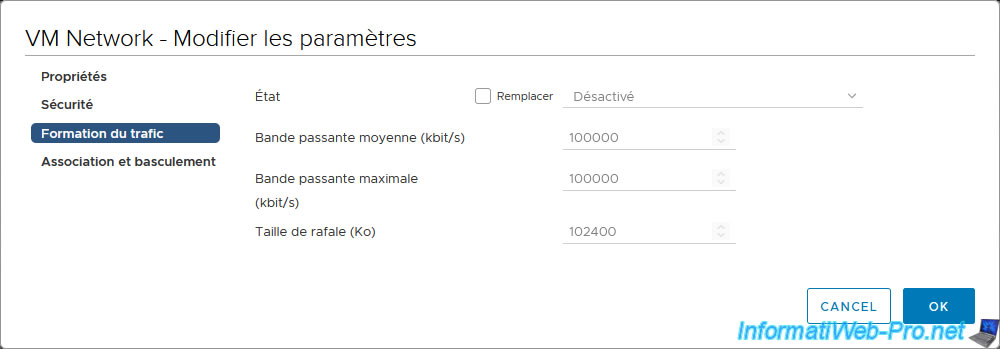
In the "Traffic shaping" section of the "[port group name] - Edit Settings" window that appears, you can enable or disable network bandwidth throttling.
Note that you can also configure network bandwidth throttling on the specific virtual switch if you wish rather than configuring it on each port group.
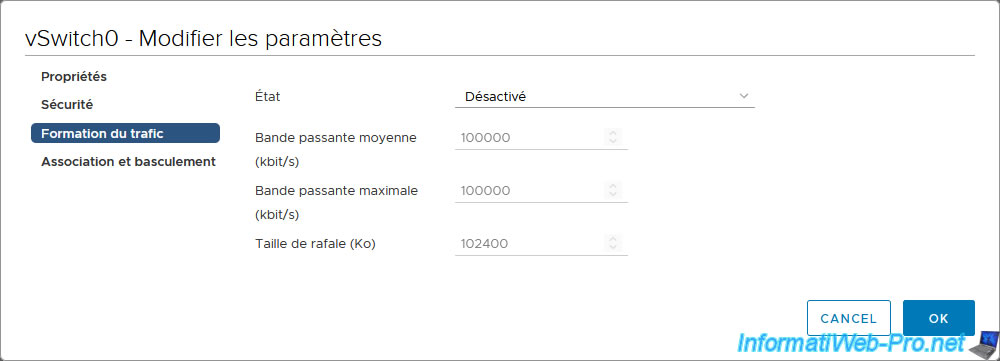
To do this, click on the "Edit" link of the desired virtual switch.
As you can see in the "Traffic shaping" section of the "[vSwitch name] - Edit Settings" window that appears, you will find exactly the same settings with the same default values.
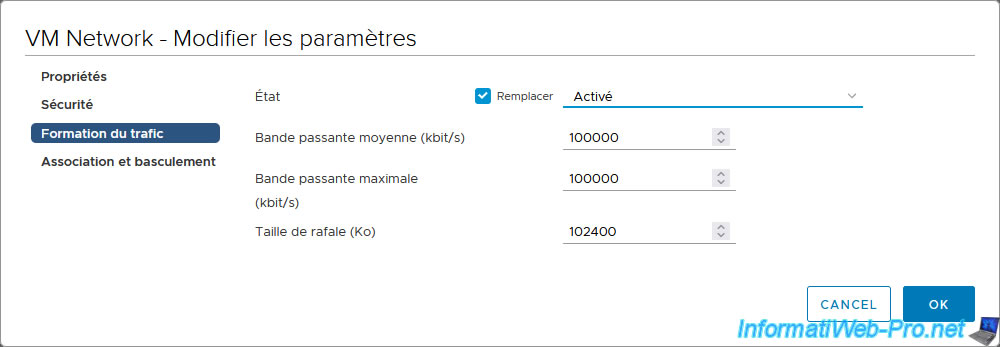
For this tutorial, we limited the network bandwidth on the "VM Network" port group of our host "esxi1".
To do this, check the "Override" box (visible only for port groups) to use these settings instead of those defined on the virtual switch, then configure the settings:
- Status: Enabled. Allows you to enable or disable network bandwidth throttling on this port group or virtual switch (depending on your case).
- Average bandwidth (kbits/s): amount of data in kbits/second to allow.
- Peak bandwidth (kbps): same as the previous setting, but when a burst bonus (defined by the setting below) is used.
- Burst size (KB): amount of data in KB that can be temporarily sent at a higher speed in a burst.
In our case, we enabled bandwidth throttling and left the default values.
Source : Edit Virtual Switch Settings in the VMware Host Client - VMware Docs.
4. Test bandwidth throttling
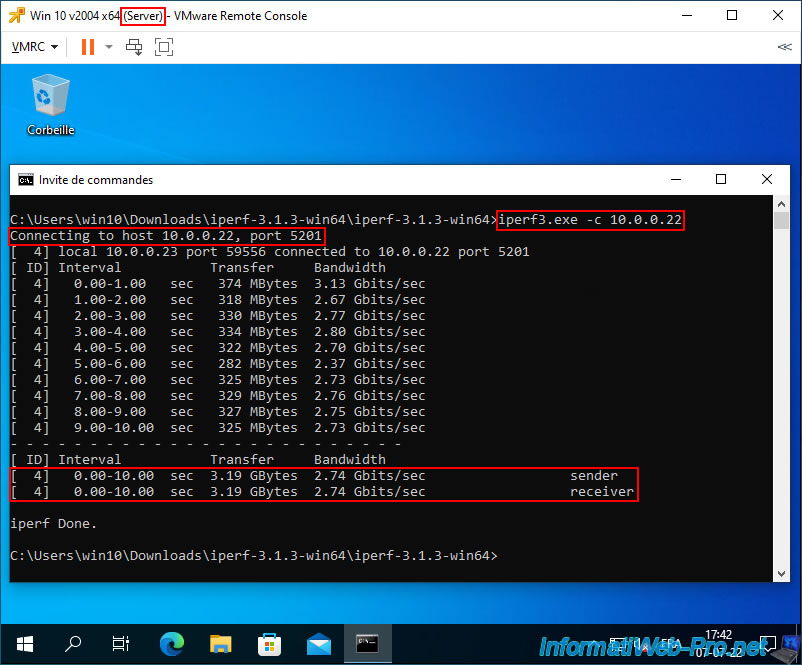
Retest the network bandwidth between your 2 virtual machines using iPerf.
As you can see, with the defaults set on VMware vSphere 6.7, the network bandwidth is limited to around 100 Mbps.
Note that when using a Virtual Standard Switch (vSS), only outbound traffic can be throttled (as explained previously).
Which means that if you test the network bandwidth in the other direction, the throttling on VMware vSphere will not be applied.
Share this tutorial
To see also
-

VMware 4/14/2023
VMware ESXi 6.7 - Best practices for creating a VM
-

VMware 7/22/2022
VMware ESXi 7.0 / 6.7 - Create a datastore
-
VMware 1/22/2025
VMware vSphere 6.7 - Export vDS switch configuration
-
VMware 1/15/2025
VMware vSphere 6.7 - Port mirroring

You must be logged in to post a comment